Note: Descriptions are shown in the official language in which they were submitted.
OCR. ~1. 2001 12.17PM DDK N0. 92E4~r. 4
CA 02371135 2001-11-09
[320.1005]
MfiTHOD h'OR ESTABLISHTNCr A CONNECTION IN A TELECOM~M.UNICA,TIONS
NETWORK
[0001] The pl~sCnt invention relates to a method for cstablishitig~ a
connection from an
initiating Subscriber to a da~tirration subscriber in a tclecummunications
network without the
respeotiwc initiating sub8crlber knowing the portnanant idcutif3er of the
destination
subscriber.
[0002) A rcqucsl for a call inevitably involves the disclosure of one's own
telephone
number. Itr the ca8e of nev~rspaper advertisements, a way out presents itself
mostly via a box
number whicL, however, prevents an imrxiediate conta~;t of the interested
party with the
advertiser, resulting in delays. Moreover, the intcrestGd party then lies to
express
himsclflhcrsclf in writing. However, if the telephone cumber is indicated in a
newapapcr
ndvcrtiscmcut, then it is mostly possible to identity IIrG owner of thre
telephone nuinbcr via
electronic data bases which allow a nuxnbor search, ncsul~titag in the
possibility of abuse.
Thus, foi in5taziCe, a public offer of telling a precious object may attract
burglars. The
possibility of publishing an adverbisEnnent under a box number has to be
eompletoly ruled out
for some puLlic;ations :e~uh as in the case ofpiii rwalls W ith private
axmouneements in stores or
schools.
[0003] ThdrefOre, the object of the prc'cnt inverrtivn 18 to oprt~ to a
subscriber of a
tclcconuuuuications network the possibility of being called without the cailar
knowiur~ his/her
telephone number, hereinafter else referred to as perrxlanent identifier.
[0004 This objective is xhioved according lu the present invention
in that an anonymous identifier is assikued to the permanent identifier of the
dcstirrxlion subscriber by a confidence instance,
in that, for e~tablxshiz~ the eonncctiorr via the initiating subscriber while
using the
anonymous identifier, the utilized identifts~r is recognj~P.d by the
particular active Switching
center as an anonymous identifier and routed t0 the ennfidenee instanec,
in that. the confidence instance Qctennines the assigned permnncnt idarrtiliar
8'om the
OCT, fl 1, 2001 12:1 flPM DDK ~ ° ~ N0. 9264_x. 5_
CA 02371135 2001-11-09
t~iu. ~ ~ns~
rocoiw:d anonymous i~irntif~er and tranoamits it to the switching center,
iii that the switching center prooeeds to establish the connection to the
destination
subscriber while using the transmitted pormancnt iaaxitifier.
[OOOSj Althaugh a first field of application of iLd method according to the
present invanliun
is tslophuny, the use in other telaeomnnunicatialis networks, in particular
data. izctworks, is not
to be excluded.
[OOOG) An advantsigeous embodiment of the iuclhod acenxdiug to the present
inve~iliurt
causists in that thp coafidenoe instanco is cuuslituted by a code server ixi
coixjunction with a
sci-vicd control fimetiori of the teleeomrriunications network which is at
loast partially
dr~igned as an intelligent netwvork, and in chat the routing of the anonymous
idcnti~rr &om.
tltc ~witehing center and the tronaixiission of the permanent id«itifier to
the awitchiiig center
taka place via a. service twitching function of the inteliigrnt ~ietwork.
[0007[ To limit the stock of numbers W rich has to he kept ready for the
anonyiuuus
idtmtifer, it is provided according to a rofinement to de~Gte fihe anonymous
identifier at a
predetermined time after the sssigiuiioiit. In a practical application of the
nnetl~v~1 aceozding
lu the present invention, the prodctcri>ziuCd time will hp established in
accordaitcG with the
pcriud of tirrxe within which the destination subscribcsr will still expect
calls afixr his/her
publication, fnx example, the advertisalu~at, such aq, for example, one or two
wac;ks. ~7ue tn
this time limitation of the smonymous idculafier, moreover, an izisignificant
iiitcrest in an
unauthori~Fd intrusion into the conf dr~cice instance is to be expectod no
that siuiple projective
iueasures arF sui~cient, if indicated.
[0008] In the method aeoording to tam present lnvPtttiori, moreover, provision
can be made
for the annriymous idaiitificr to be dGletable by an input of the destination
subscriber. 1n tkzis
mantaet, it is possible, for example, to prevent the destination subaczib~
fi~oui rc~cciving
f~ucther calls concerning an advcitiacxi object after it has been sold. The
delrtion of the code
can bo indicated to further callers by an approrriatc spoken meosage.
l
OCT. ~1. 2001 12.10~M DDK ----N0. 9264__x. 6. _
CA 02371135 2001-11-09
[~ZU.1005]
[0009] Anotlicr berte$eial e~mbodirtxent of the prcseirt invention cnrtisists
in that a pcrn~aueut
idantif~cr eau be assigned only one anonymous identi$er at s time. In this
mcmncr, an abusive
extension of the assignment of anonymous idcnti$em is prevented.
(0010] Zn au expedient embodiment of the prescitt invention, pmvision is made
for an
authorizatiau ckteck tn k~e carried out before tli~s con$dence inst2ince
assigns the anonyr~iuus
idcntifior. This check can prevent, for oxampld, au uuauthori~ed person from
gcneratity an
anonymous identi$er fir a call cumber.
[0011 j Moreover, provtsiou can be made for the conflder~ce instance to output
erivr
messages whets ate aaaa~ment is not possible. Such error messages can says
- au anonymous identifier already c~;ists fur the entered call number,
the entered call aunaber was not co~rcca,
the request crn~ld riot be csuricd out due to a System error.
[0012) According tn an advantageous ombwliment of thA present in~rentior~, a
user-friendly
asaigruiieut of the anonymous zdentificr eau be effected in that the request
for the assignment
of the a~ruuymous ide~ntif~er and the commutuccttiori thereoftake place over
the iiilernet.
Consoquenlly, the user can be advantageously guided ma suitable graphical usrr
interfaces,
infomualion and entries coruplemcntiz~tg ouc another in 2n expedient naanncr.
[0013) Further ways to request the assi~nmetlt of they anonymouo identifier
and to
conLtiunicate it to the destination subsct~ibcx are, in the 1SDN', preferably
via the D-channel
or, in the case t~f other digital subscriber lines via suitable channels, in
analuk and alas digital
r~ctwurks via the rrxultifrequsr~oy mcfihod, by short messages (SMS),
electrons mail (F-mail),
and via voice input and output. Dcpetiding on the individual aonditio~ns, ii
is also posaihle to
use mixed forms such as requesting by means of transmission via the
naultifrequency method
and communication via voico output, which allows the use of a. sintplc
telcph011e with arl
a~~alug subscrihex line.
OCT, ~I, 2001 12;10PM DDK ~ ---~-~ _N0. 9264_~P~
CA 02371135 2001-11-09
[520.1005)
[0014] When using the ax~thod according to ihn present invention for the
applicatiotrs
mcntiutted at the outset, the method is prcfetdbly designed m such a manner
that tlia
asStgillllCttt is requested by an input of the daslirtdtiori suhcrxiber. It is
then coraplctaly up to
the dcstiuttlion subscriber whether hc/ahc wants to use an anonyncious
identifier, hereinafter
also referred tv ac code.
[00x31 Tn modern telephone networl,;s, tltc call tlumher of the calliztg
subscriber is
autonxatically transnxitted to the called subscriber. Fur legal provisions on
dais becuzity and
privacy, a Calling subscriber has the possibility of suppressing the
ttxnsmisaioix of his/her own
call number to the called subscriber. l3ccause of thi s, the called subscriber
will later not he
able ~o call back the caller unlo~s hcJslxc knows the call number of the
caller anyway.
[0016) In sonxe cases, however, it cart be desirable tbr both subscribers
tlxdt such a retittn
cuttnection can he established on request of the called subscriber without the
calling
subscriber disclosing his/her call nutubcr.
[0017J A .ft~rther embodimcrtt of ittG present invention makes this possible
in that then request
fvr the asaigrtment botween the atxuttytnous and the permanent idcntifieta
lakes place during
the dialing of z pertnnnent identifier of a later initiating subscriber by
lltcs destination
subscriber, and in that the anonymous identifier is transnnitted to the lat~sr
initiating
subscriber. ''This procedure enn be started by the destirxation subacribar by
enterfng an
appxopri atc~ prefix.
[0018] The return eontaacction is then preferably established in that the
anonymous identifier
is eonvertc~d by the confidence iltstanee into the pe~tnatnent identifier of
the destination
subscriber upon request of the initiating suhscsiber, and in that the tctum
connection to tire
destination subscriber is cgtablisLad using the permanent identifier.
[0019) 'this e~tnbodimc~nt of the present invention allows a subSCribCr IO
receive return etilts
d
OCT.31.2001 12:18PM DDK --. N0.9264.~P. 8
CA 02371135 2001-11-09
($20.1 tltrl]
wlvlc keeping his/her anonynuty. For imstaxice, in the case rrfrsyehologieal
counseling
telephone serviocs, the itec:rssiry cart atioe to prowidc r:rrtnpreher~sive,
qualified counsel by
way of a returxa call wittumt having to xemove the armnyrnity of tlto caller.
Arun.her
application case c:an be the query of a data haw. Irr spite ofthe tclcphorric:
transmission of the
query results by means of a return call, no ccmclusions about the inqui ri ng
person are
possible.
[OOZOj In n refincrrtent crf ne present inveu~tior~, prevision is made tbr the
destirrH~ian
subscriber to be ialforme~.ci of this tact by a perceiv~ahle sigaaling rwhan a
rotor rr c:all is
established usip ~.'fxe antonymous idcntifioc. Ti. is then posexble for the
dcvinarion subscriber
to adapt lii~fher behavior, in particular, to a<:cept or reject the return
call.
[0021] In a further rcfuic«rant ofthis specific cmbodiurcnt, a return call
between the
initiating subsetibor and ~.he destination subscriber varx also be aohievcd.
in that a. c:onrtection
requested by flat icri~i.rting subscriber is automdl.ir:ally established from
the degtitlation
subscriber upon ccrmpletiozt of the si~czaliiig after the destination
subscriherr has confirmed
that a conna:~.ion is to be e3tablishcd, LhH connection beizy autoirrnLically
effected from the
destination subscriber to the initiatirr~ subscriber.
[(1022] '!he conversion of ~hc ponnanent identifier crf the destination
subscriU~sr iuto the
anonymous idcnti f rr can be effected in that ihrs permaxxent identifier is
i.rsrnsmitted to a code
server linked to the network, in that the codh server converts the pcrrnsnent
identifier into a
test ar~onyrnr~us identifier arid stores the anonymou, identifier firr the
period of validity
thcrerrf with the perxnrutont idcrrlilier being assigned thereto, aruJ in that
the node acrvcr
outgun the anonymous identilicr which is transmitted to the initiating
subscriber.
[0023] '1'hc oo>zvomirrn of the anonymous idcni.i:0er of the doatination
suhacxtber into the
permancrat idcm.ifier for the purpose of the return ca]] case, be effeclxd in
that the anony;nous
identifier is lrrnstztitted to the code serve, and iu that the code ~c:rver,
by way of the atorGrl
assigrrrnents, retrieves and outJms the permanent idcntifrcr.
S
OCT, 31. 2001 12:10PM DDK h0. 9264"-.~. 9
CA 02371135 2001-11-09
(520.1005]
[0024] The ostaLlishment of an anoxiyirious connev;tion between tho
destination subscriber
and a oallcd initiating subscriber can be carriod trot in that the identi$er
of the dcstiiiation
subscribor is motel to a servftc.e control function by an appmpriate switohing
center, in that
the aervieo control #linetinn obtains an aaon~riuous identifier teorti a code
server while
indicating the i~lCntifier of the destination subscriber, in that the code
setvcr converl~ the
identifier into a free anonymous identifier an s stores the anonymous
identi$cr fvr the period
of validity the~GUf with the permanent identifier bCing assignAd thereto and
outputs the
anonymous idciztilier to the cexvice control furictiou" in that the service
eontml ftuicliort
routoa the anonymous identifier to the switching centex,and iii that the
switohing center
establishes the co~aneCtfon with the called initiating subscriber while
indicating lliC
anonymous adatltiflcT.
[002S] To allow the code server to bo idcntifiedr another refinezri~nt of the
piasnnt invention
makes provia~ion ibr an idP.ntifier which identifies the code server to be
added for the
ano,nyn~ous iQentlfier.
[0026] Tho cslablighment of a connection-back betwPGn the initiating
subscriber and the
destination subscriber sari be carried out in that the anonymous identifier of
iha destination
subscriber is routed rn a service contml fuiictiora by an appropriate
switcliiux center of the
network, iu that the service control fixnctiou obtains the permaTion~t
idontifiat of the
deatinatioi~ subscrfber from the appropriate wde server while indiaatirig tits
anonymous
idcntifiei, in that the service control function routes this identifier to the
switching center, and
in. that the switching cexiter ertablishcs the uunnectinti with the
dostinYatiou subsCrlber.
[002~J Tlie method according to the present in'venti~n can advaritagcously bo
used in such a
marina' drat the teleaommunicationa network is a eircuit.switehed network for
voice or data
transrnissiun, and that the identifiers arc tclephono numbers. In this
comirn:lion, preferably,
prowisiun is made for the anonymous t~slaphone number to include a dialing
pieBx for dialing
up the wnfidence instance.
1i
OCT. ~1. 2001 12.19PM DDK - N0. 9264.~.~. 10_
CA 02371135 2001-11-09
X520.11105]
[0028) Other apNlications can consist in that the tclecutnmunieations network
is a network
~or trnnsmittil~ data of any .kind, including vidw attd audio data and/or
textual massaKas and
in that the identi~crs era user addressee of dais network.
[00Z9] Bxculplary embodiments of the present uivention are depicted in tho
dravwing with
reference to several Figures and will be cxplaiucQ in greater detail in the
following
deocriptiou.
[0030) Fig. 1 shows a ~chematie roprcsentatiott of a first erabodiment of the
presdtu
invezttion,
Pig. 2 depic2S a. flow chart on the assigtrment of thes finonyrtious
identifier iti
accorrianco with the method au;ording t~ the present invention,
Fik. 3 repree~ts a flew chart on tltG astablisbment of a eonrreatYOn in
accordance
with the method according to ttte present invention,
Fig. ~ shown a schematic roprcacutaliun t0111uqtr~te a second embodiment of
the
precept invention,
Fik. 5 is a flow chart on the cstablislunent of a. forward connection,
Fig. 5 shows a. xlovcr chart on the ostablishment of a return cormcctio4l
ac:cordfng tc~
the second exnbodimcnt, and
FYg. 7 depicts a flow chart ort tho c;ummunication in an eleatxonic news
system in
aeenrdanee with the metliod accol'ding tn the present invcrttiou.
[0031) Itt the Figures, id~ntieal pacts are provided with the same refcro~ucG
symbols.
7
OCT. 71. 2001 12.19PM DDK -"'-.~~ N0, 9264-~, 11 ._
CA 02371135 2001-11-09
[520.1005]
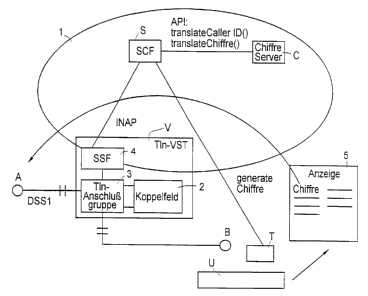
[0032] Fig. 1 shows an intelligent network 1, for example a digital network
with a digital
subscriber lint, of which are represented xn individual switching cGillc~r V'
having a switching
unuit 2, a subacubm line group 3, and a service switching function 4
(wnfotxtling to TI't.l_T
Q.1211) for coupling the intetligtnt network to the distributed switched
network as weal as a
service control function S and a code server C which is conistitutr.~l by a
computer which
carries out the couver~slon ofthe~ anonymous identifies into pa~unanent
identifiers and vice
versa and ~uvhiel~ stores the assignments of the identifiers to the
subsc.7cibers in a data base. To
the example, two subscriber lines A and B are linked to the same switching
center V'.
N'umcrous switchi~rtg centers exist in the network. ~ the event tlu~t lWO
subscribers to be
conracctod are xiut linked t0 the carne switching oentex, the proce~bars
deserlhe~i in the
following take place analegnnsly.
[0033] Murcvver, user'tJ ~t'subscriber line B possesses a lcxnZinal T, for
exarinple a
computer, wvlrich has access to tk~e Internet and which permits a dale
exchange with, service
control fiuiciaon S of intelligent network 1, possibly via furihur components
wtueh are not
shown (fur example SMF). Moreover, service switching function 4 is connected
with service
control fiuictiun S via an INAY interface.
[003~4~ Service control furtctiox~ S hey, access to code server C via an A rPl
interface or via a
logically equivalent e~m~munieatians protocol. Dccausa of this, x'eque.Sta
c»ch as
''translatcCaller mQ" anti "translateCodeU" which basically means "translate
the permanent
idcutifitsr of the caller indicated in brackets" and "traalslale the anonymous
identifier" oan b~
routed lu code server f:.
[0035) For i~tat~ce, it' user U of subscriber liztc H wants to place a
newspaper advertisement
without thereby rublishing hislhar telephone nuuiber in connection with the
advertised
oUjecl, heJshe can rerluest the assignment of an auouymvus identifier via
teaxniaal T and the
Zuterztet which i9 not shown. For this purpose, hel'hG is prcwided by servic~
control function
S or an interposed eornpoaent with an iiyu~ mask via which he/she enters
his/her own call
8
OCT, 31. 2001 12.19PM DDK ~~ -N0, 9264--'~, 12-
CA 02371135 2001-11-09
~s2o. ~ en5~
number and tliG request to be pmvidod with an anonymous identifier. Sorvicc
control
function F foA wards this request to the cn~le server. Provided that so code
has been stored yet
for flue sub~cniber lfne B and that n~ other reasons exist for xofu3ing an
anonymous idcutifier.
such an auouyuiuus identifier is generatESet and eo~mmuaicated to uoor U via
hislhcr tcrniiual
T. The user can thou malts the ettde known in the newspaper ndvertiecxncnt or
another
publication.
[003G] Fur instance, if the user of suhscriber Tins A wants to get iatv
contact with the
advertiser, he/she dials the code indicated ire the advertisement. The code
iaoludcs a diuliug
prefix (for example 015 I) fmrn which switchixtg center V (Fig. 1) recognizes
tlral this is an
anoityiuuus identifier. Therefnrn., srarvice switchi~ function 4 inquires of
code smvGr C via
service control ~.cnction S which permanent ideaitifier is assigrtcd to this
anonymuus identifier
and receives in response the perrt~anent identifier ~cwhich iE then routed to
the switclury unit
fur establishullg the connecaion to subscriber line B.
(0037] Fig. 2 shows the procedure for assigning an onor~ymous adcntifim.
Tuitia,Ily, request
AhT far an anonymous identttier is transmitted from teimirral T to sczvice
coulrul function S
vu~Iuch returns a mask tQ the terminal into which user U enters his/lier
Nanuenent sub6criber
number PCB (that is the call number of subscriber line B). The aubscribci
number reaches
wde server C: via. RArvice control function S, the eodc server gcneratiy tm
axtonym0us
subscriber number A~K ii of subscriber line B and returning it to tcnn~aal T
vid S.
(0038] Fig. 3 depicts the establishment of a oonacction fmm subsvribrr A to
subscriber B
with the assistance ~f anonymous identifier AKB. To this end, the auuuynvus
identifier
AKB is initial 1y dialed by subscriber ~1, and thus routed tv switvluug center
V which, after
recognizing that this is an anonyx~.oue identifier, queries fihc perrttaumt
identifier from code
server C;, aq desscribed above. Subsequently, the conrr,oction establishment
is completed cn
that the call reaches sabseribor lire B.
[OO:i9~ The cot~figuratxvn shown is Fig. 4 is similar Lu ttia.t according to
Fig. I ; hnvve:ver,
9
~NO. 9264-~. 1 ~
OCT. 71. 2001 12;19PM DDK
CA 02371135 2001-11-09
[52~.1UU$]
subscriber B not 11C1I1~, allocated a separate terminal. .A. configuration
o~that kind can, on one
hand, be used to rcquesl lhc assignment of the anonym~nc identifier aver' the
telephone of
subscriber B via auiLable data transmission tyPea so that subscriber B can
make lonown a
code, similarly as ui Fi,g. 1. On the other hand, the cnntigtuation according
to Fig. 4 can also
ba used to anonynize ilic idcrrtifier of suhscrih~r T3 for cextam
conversations, which will be
explained in. the fulluwixxg with reference to Figurns 5 and 6.
[0040] Wlxeu ~lcslanation subscriber B calls later the initiating subscriber
A, th~n the
connection requGyt of ddstination subscriber F3 is transmitted (Hl) to
connected svvitchiag
center V via tl'ie layer 3 protocol DSc I of the 15DN network as shown in Fig.
5. 'lo activate
the code service, destinati0ri subscriber'fi rlaces a prefix (for example
0150) before the call
nuiuLcr of initiating subscriber A. Thereupon, at H3, s<witehing center V
aenda a request to
service cvtitrul function S 'via service switching fimction 4 under the INAP
protocol. The
dialed call number of initiating suhscrihAr A is partially input along with
the request at ZI2 as
an arguntGUt. Then, at H3, additional digits of Initiating subscriber A are
requested
suvscy,utx~tly. At H4. the quantity of subsequently requested digits io
traasmuittod. The call
uutuvcr routed by destination suhacriber 13 at H4 aria switc)ning center V at
HS is uacd at II6
by tire scrvice~ control function to request an anonymous identifier from code
server C, the
a~xuuytaous identifier being transmitted to service control function S at H7
and, at IIB, fuially
to the swilctung center rwhieh, rat Ii9, establishes a connection to
initiating subscriber A wlailc
t<a~xautilting the anoDymous identifier of destination subscriber H.
[0041] As shown in Fig. c;, atesps kl through R9 are carried out
cortospondingly if iutiatuy
subscriber A requests a return connection to subscribar B who is unknown to
himlhcr with We
aid of the anonymous identifier and of a preceding dialing prof~~c (for
example 0151). At R6,
service control flanetion S requests the ananymous identifier to be translated
back into tire
identifier of destination suhsrnber B. Code server C delivers the identifier
of dcstittatiutr
subscriber B from its data ha.Re, and the connection can be established at
IZ9.
[0042] Fig. 7 shows how a destination sub3eribcr B mutes a rcqueal lo a code
sclver C at
l0
ocT. ~1. 2001 12:19PM DDK - No. 9264'-~. 14
CA 02371135 2001-11-09
[520.1003]
N1. Cods server C converts ilic iQcnlafier of destination subscriher H iuato
an. aaonymouc
identifier and, at N2, routes flat ir~ucsl, together With the at~onymrn~s
identifier, to news
sc~nrcr N of the news syslGiti requested by destination suhcerih~.r 13 where
it is published. Aa
initiating subscriber A wlm lu~~ vn to the system at N3 reads the re~tiest of
destination
subscriber B at N4. Tf initiating suvsuribrr A wants to reply rhe3rAco, then
heJshe, while
indicating the anonymous idautifirr of destination subscriber H, ~entis
hislher aaswer to coda
server C at N5 which routes it tv ~lcsliztation subseriher R at Nti.
11