Note: Descriptions are shown in the official language in which they were submitted.
METHOD FOR CONNECTION OF SECURE CONFERENCE CALLS
Field of the Invention
This invention relates to audio teleconferencing
but more particularly to a secure conference network and
method of connection thereof.
Backqround of the Invention
One service that is required in a communication
network is audio teleconferencing. This service allows a
number of callers to talk together from a number of separated
telephone instruments. In a secure conference call, two
additional features are provided. The speech passed between
the parties is encrypted, using keys known only to the sender
and the receiver, so that the speech is not understandable by
any eavesdropper who intercepts the call. In addition the
parties in communication are authenticated so that each is
assured of the identity and clearance level of the others.
To provide the conference feature, a bridge
circuit is often employed. This circuit combines the signals
from all parties and distributes the results to each
listener. Unfortunately when the speech is encrypted the
bridge circuit can no longer sum the signals as the
encryption is typically a non-linear process.
In past implementations of secure conference
circuits, the bridge would first decrypt the incoming
signals, then sum the resulting clear speech, then encrypt
the result and distribute it to all parties in the
conference. This method requires the bridge circuit to know
the encryption keys for all parties and clear speech signals
are contained within the unit. This means that the
conference bridge itself must be considered as a part of the
security system. This introduces another point of weakness
in the system and some users may not wish to trust the
security of a bridge operating outside their direct control.
It is thus desirable to make a conference unit that can
operate without requiring recourse to clear speech.
Another approach to this problem has been
described in a paper by Brickell et al. CRYPTO '87
Proceedings, entitled "Secure Audio Teleconference". In this
$~
?Z~
method, an encryption process is used with certain linear
properties which allows the bridge circuit to sum the signals
in a normal manner for distribution. Unfortunately this
limits the number of applicable encryption techniques and not
all users would be willing to trust these schemes. This
method also restricts the speech coding techniques allowed,
produces some bandwidth expansion, and requires some
synchronization (in time) of the signals from all of the
conferees.
It is thus desirable to design a method and
apparatus which can function independently of the encryption
process being used and also does not suffer from the above
mentioned limitations.
Summary of the Invention
The primary object of the present invention is to
provide a method and apparatus of making secure conference
calls in which the bridging unit does not need to know any
encryption keys and can function independently of the
encryption process used by the communicating parties. This
means that there is no security re~uirement for the
conference unit, there are fewer restrictions on where it can
be placed, and it does not introduce any additional
weaknesses in the security system.
Description of the Drawinqs
Particular embodiments of the invention will be
understood in conjunction with the accompanying drawings in
which:
Figure 1 is an illustrative block diagram of a
secure conference system according to a first embodiment of
the present invention;
Figure 2 is an illustrative block diagram of the
conference system of F~igure 1 according to a further
embodiment of the present invention;
Figure 3 is a block diagram of a secure telephone
set used in the secure teleconference network of the present
nventlon;
Figure 4 is a block diagram of the signal
processing operation used in the secure telephone set of
5~0
Figure 3;
Figure 5 is an illustrative block diagram of a
secure telephone set accordiny to a second embodiment of the
present invention; and
Figure 6 is a block diayram of an a]ternate
conference network accordiny to another embodiment of the
present invention.
Description of the Preferred Embodiment
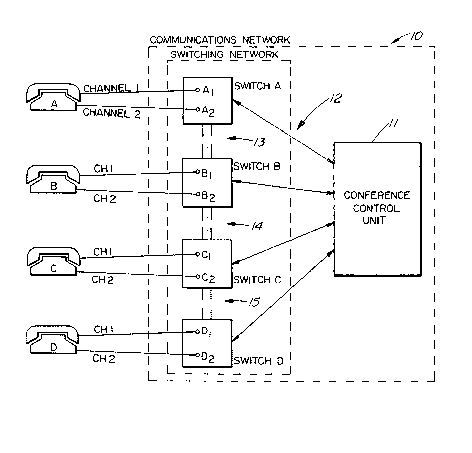
Referring now to Figure 1, we have shown generally
at reference numeral 10 an illustrative block diayram of the
conference system of the present invention. The system is
basically comprised of a conference control unit 11, a number
of telephone sets A, B, C, and D and a switching network 12.
Each telephone set has two channels ~or connection to the
switches. These channels may be multiplexed on a single
physical connection. The network 12 may consist of a number
of nodes or switching centers connected by transmission
facilities. End to end digital connectivity should be
provided through the use of the digital subscriber access
technology and a digital network or an analog network
combined with voice band modems.
For example, in Figure 1, switching network 12 is
comprised of telephone switches A, B, C and D. Each switch
may be connected to another switch by means of trunk lines
25 13, 1~ and 15. In Figure 1, telephone sets A, B, C and D are
each connected to their own switch, i.e. switch A, B, C and
D. However, it will be known to those knowledgeable in the
art that a number of telephone sets within the teleconference
network may be interconnected via the same switch. The
number of switches will of course depend on the location of
teleconference users. For example, sets A and B could be
interconnected via the same switch if these are located in
the same office or local area network. These switches can be
any typical telephone switches supporting digital loops on
voice band data modems such as the DMS-100 (trademark)
switch.
A DMS-100 is currently adaptable to provide the
con~erence control unit.
54~
In Figure 1, four parties are connected in a
teleconference network. ~Iowever, any number of parties can
be connected in a similar manner. To ~orm the conference,
the parties are connected together by means of the switching
network 12 under the control of the conference control unit
11. This connection pattern is established by having a first
party initiate the conference call feature. In this example,
channel 2 of phone A connects to channel 1 of phone B,
channel 2 of phone B connects to channel 1 of phone C, and
channel 2 of phone C connects to channel 1 of phone D, see
Figure 2. Note that channel 1 of phone A and channel 2 of
phone D are not used. As the channels to each phone are
interchangeable, the designations channel 1 and channel 2
could be reversed on the phones without affecting the
operation of the system. Once this connection pattern has
been established, each phone can then initiate a secure call
with a connected neighbor using the encryption process of
their own choice. Once the secure calls are established on
each channel the signal processing circuits of phones B and C
will operate to combine the speech from each active channel
and the user speech and to distribute it to other channels
and the user. The speech or messages from each phone user is
thus heard at all other phones in the conference. The voice
from phone A, for example, is heard at phone D after passing
though phones B and C.
Because of the digital techniques used in the
switching network and the transmission lines, there will be
no practical accumulation of noise to degrade the speech
signal. Quantization noise does not accumulate with
successive codings in the chain if conferencing and coding
functions are partitioned properly. This results in
synchronous coding at each station and is practical with the
common pulse code modulation (PCM), adaptive differential PCM
(ADPCM) and the CCITT standard wide band audio (WB~) coding
schemes.
The telephone sets in this arrangement are
connected to the network in the manner of ordinary telephone
sets. However, in the most practical arrangement, digital
communication techniques are used for access, transmission
and switching. ~he method can still be applied to an analog
or a mixed analog/digital switching/transmission network if
suitable low bit rate speech coding and voice band data
modems are employed to provide digital signals for use by the
secure telephone sets. Note that these modems can be
incorporated within the secure telephone sets to permit the
conference method to operate on either analog or digital
networks.
The conference control unit 11 acts to set up and
supervise the interconnection between the secure telephones
to form the conference. The role of the conference control
unit 11 is to request connections in the switching network
12. No processing of speech by the conference unit or by ~he
network is needed. The secur~ conference feature is made
possible by having each secure telephone set connected to the
switching network 12 with two or more logical channels
depicted generally at reference numeral 16. This may be done
practically in a number of ways. It is possible to simply
use two pairs of wires for each set and then make two network
connections as shown in Figures 1 and 2. It is also possible
to combine two logical communication channels on a single
pair of wires or network connection by the use of speech
coding techniques which multiplex a number of channels as
shown in Figure 6.
ISDN (Integrated Services Digital Network), for
example, supports two full speech channels (64 Kb/s each) and
one data channel (16 Kb/s) for a total of 144 Kb/s on a
single standard telephone wire pair. ISDN thus directly
supplies two logically separate speech channels on a single
subscriber pair.
Referring now to Figure 3, we have shown a block
diagram of a secure telephone set used with the
teleconference system of Figures 1 and 2. In this
embodiment, the two logical connections 20 and 21 from the
set to the switching network 12 are labelled channel 1 and
channel 2 respectively. These channels are connected to
encryption/decryption circuits 22 and 23 respectively. These
~2S~
are used to encrypt the messages or speech sent and decrypt
those received over each logical communications channel.
A description of speech encryption/decryption
techniques which may be used with this invention is disclosed
in a paper by W. Diffie et al., Third Annual Symposium on
Physical/Electronic Security, August ~987, entitled "Secure
Communications with the Integrated Services Digital Network
(ISDN)".
The encryption/decryption circuits 22 and 23 are
connected to speech coding/decoding circuits 24 and 25,
respectively. These may operate under any suitable coding
scheme. Although some coding schemes may result in excessive
coding delay, there are practical coding schemes, notably
companded PCM, ADPCM, and the CCITT wideband audio standard,
where the coding delay is insignificant.
The two coding/decoding circuits 24 and 25 are
connected to an authentication, control and signal processing
circuit 26 (ACSP). This circuit performs several functions.
One operation is to connect the user output and input signals
27 and 28 of the microphone 29 and speaker 30 forming part of
user interface 31, to the communication channels via
encryption circuits 22 and 23. The circuit also acts to
perform the security authentication tasks, to activate the
encryption circuits 22 and 23 and to provide them with
encryption keys.
The ACSP circuit 26 can perform signal processing
tasks involving the speech decoded from the two logical
communication channels 20 and 21 and user interface 31. This
signal processing involves, for example, summing the decoded
speech and presenting the sum to the user interface 31 to be
heard over speaXer 30. The signal from the user interface
would be monitored with a speech detector. U.S. patent
4,410,763 which issued to applicant describes such a speech
detector. If the detector determines the signal to be
speech, then this signal would be summed with the signals
sent to the communications channels. These three summiny
operations form a simple three-party conference bridge.
The operations discussed above performed by the
s~
circuits 22 through 26 are illustrated in Figure 4. The ACSP
circuit consists of three adders ~1, 42 and 43, a speech
detector, code transla~ion and automatic gain control circuit
44 connected at the output 45 of the user interface 46 and a
code translation circuit 47 connected at the input 48 of the
user interface.
The incoming signal received at the input 49 of
logical channel 1 is first decrypted at decryption circuit 50
and then decoded at decoding circuit 51. Similarly, the
lo incoming signal received at the input 52 of logical channel 2
is first decrypted at decryption circuit 53 and then decoded
at decoding circuit 54. The resulting linear speech signals
received from channels 1 and 2 are forwarded to adder 42.
The sum is presented to the input 48 of user interface 46
through code translation circuit 47 to be heard on speaker
55. The translation of signals may be required if for
example, the unit uses a mu-law codec, then the linear sum
will need to be mu-law encoded before being sent to the codec
to drive loudspeaker 55. Similarly the output 45 from
microphone 56 would need to be translated to linear form by
code translation circuit 44 if, for example, a mu-law codec
was used.
Adder 41 is used to add the speech signal from
input 52 of channel number 2 with a speech signal detected
from the output 45 of user interface 46. If the speech
detecting circuit 44 detects a speech signal, it is summed by
adder 41 with the incoming speech signal received at the
input 52 of logical channel 2 and presented first to coding
circuit 57 and then to encryption circuit 58 for transmission
at output 59 of logical channel 1. Similarly, adder 43 will
add a detected speech signal from microphone 56 with an
incoming speech signal received from input 49 of logical
channel 1. The sum will be coded and accepted by circuits 60
and 61 respectively and appear as the outgoing signal at
output 62 of logical channel 2. The automatic gain control
circuit 44 would be used to adjust the signal level of the
speech from the microphone 56 to attain a uniform volume
level for the conference.
The use of automatic gain control (AGC) in
teleconferencing is described in a paper by John Ellis and
Bruce Townsend in TELESIS 1987 ONE, pages 23-31, entitled
"Conference Bridge: State o~ the Art in Teleconferencing".
If speech coding is being used, and the speech
detector indicates no user input from microphone 56, then the
signals from the channels need not be decoded and recoded to
be passed between channels.
In some cases different speech coding rules may be
lo used by different sets that wish to be included in a
conference. For example, some phones may use mu-law PCM
speech coding while others may use A-law PCM coding. These
different terminal types could be accommodated in this
conference method in the following way. In Figure l, if
telephone sets A and B used the mu-law coding technique and
telephone sets C and D used the A-law coding technique, then
they would be connected as shown with groups of like
terminals connected together. Telephone set C (or possibly
telephone set B) will then operate its signal processing
circuit to perform a translation between the two coding types
as part of its conference summing operations. The separate
parts of the conference are thus able to communicate with the
other through the translation capabilities of one of the
telephone sets.
Perhaps some terminals may use the CCITT wide band
audio standard. This audio standard is described in a paper
by P. Mermelstein in IEEE Communications, Volume 26, No. 1,
Jan. 88, and is entitled "A New CCITT Coding Standard for
Digital Transmission of Wideband Audio Signals".
In a wide band audio terminal application, the
code translation circuits 44, 47 of Figure 4 would include
the analysis and synthesis quadrature mirror filters (QMF).
The coding/decoding circuits 51, 54, 57, 60 handle the low
sub-band and high sub-band components. The pair of low and
high band components of the signal are summed separately.
This method is preferable to avoid accumulation of delay in
QMF filters and to prevent accumulation of quantization
noise.
When mixing narrow band and wide band terminals,
the narrow band terminals should first be converted to wide
band.
Referring now to Figure 5, we have shown an
illustrative block diagram o~ a secure telephone set
according to a second embodiment of the present invention.
In particular, this set can be used when a single physical
connection is used to connect the telephone set to the
switching network. In this embodiment, an ACSP circuit 70 is
connected to user interface 71 and the two speech channels 72
and 73 are connected to speech coding/decoding circuits 74
and 75. These are connected to encryption/decryption
circuits 76 and 77 respectively, to permit the encryption of
the two speech channels.
Once coded and encrypted, the logical channels can
then be combined by means of a multiplexing circuit 78 and
forwarded to a switching network via a single communication
path 79.
For example, this could involve using the CCITT
ADPCM algorithm in the coder/decoder 74, 75 to provide two 32
Kb/s speech signals which can be combined by multiplexer 78
(after encryption) onto one standard 64 Kb/s channel. Using
multiplexing techniques of this sort permits the secure phone
and the conference feature to be implemented easily within
the existing communications networks.
Referring now to Figure 6, we have shown an
illustrative block diagram of an alternate conference network
for use with the secure telephone set of Figure 5. In
particular, each set is connected to a switch via a single
access channel. In this arrangement, the role of the
conference control unit 80 also includes the demultiplexing
of each input channel into two logical channels and the
redistribution and multiplexing of these among the
participants. For example a single 64 Kb/s channel would
demultiplex into two 32 Kb/s logical channels.
In principle, it is possible for one encryption
process to be used, for example, between phones A and B, but
a different process could be used between B and C if they so
25 ~(~
choose (see Figure 1). This permits flexibility in the types
of terminals used with the system. Also it can be noted that
if a symmetric key encryption technique is being used, it is
possible to use different encryption keys on each segment of
the conference circuit. If this is done, then the bit
patterns on the two channels to a secure telephone set will
be different even if the user has no input i.e. is not
speaking. An eavesdropper would thus be unable to determine
which party of the conference is speaking. This may be
considered an additional security feature by some users.
Otherwise it is most practical for all segments of the
conference to be encr~pted with the same key. As the entire
conference can be decoded by breaking the cryptosystem on any
one link between users, there is no advantage in having
separate keys for each link.
With this arrangement, the clear text or speech
appears only at the telephone sets where it must appear
anyway for the user. Thus there is no additional security
weakness in the system due to the presence of the conference
feature. The conference control unit 11 is responsible for
administering the connections between the parties but it does
not need to know any encryption keying information or operate
on any clear text. The encryption and authentication process
is all under the direct control of the user's secure
telephones and they need not trust the conference unit with
any of their security information.
With this method, if one party wishes to drop out
of the conference, then it is the responsibility of the
conference control unit 11 to reconnect the remaining parties
by instructing the communication and switching network 12.
For example, in Figure 2, if phone C wished to drop out of
the conference, then the conference unit would instruct the
network to reconnect channel 2 of phone B to channel 1 of
phone D. These two phones would then reinitiate a secure
call between themselves, after this was established, the
conference could continue among the remaining phones i.e.
phones A, B and D.
If another party wished to be included in the
Z5~1~
conference, then the conference unit would instruct the
network to connect channel 2 of phone ~ to channel 1 of the
new party. These two phones would then initiate a secure
call and the new party would be included in the conference.
As is customary in conference calls, one party or
an operator, acts as a controller to administer the
conference and issue the instructions to the conference unit
to include or remove parties from the conference. This
conference manager would communicate with the conference
control unit using a separate logical communication channel
established between the manager and the conference unit. As
an option, this communication channel could be secure. The
conference manager would also be responsible for
authenticating the identities of all participants in the
conference and perhaps also distributing the identities of
the participants to all of the conferees. A number of
techniques known in the art can be used for this and need not
be discussed further. Other techniques can also be used in
which every party performs his own authentication of every
other party in the conference.
A secure conference network could also be provided
by interconnecting users through two or more conference
control units in geographically separated regions.