Note: Descriptions are shown in the official language in which they were submitted.
WO96/02901 a~ 1 95003 P,l, '~1611
~ ~1 IAUTHENTICATIONTECHNIQUE
This invention relates to a technique for ~..-h~l.ti~ g products, cards, tokens and
the like so as to combat illicit copying thereof.
s Copying of products. cards, tokens and the like (hereinafter referred to generally as
' "valued articles" to avoid repetition) is a major problem and various techniques have been
devised to combat such copying. In particular, techniques have been devised based upon
the inclusion, on valued articles, of twin sets of data, one set being . l. ~ of the
holder of the valued article or its producer or issuer (as the case may be) and the other set
being derived from the fu-st set by some unique route that is difficult to replicate. When the
valued article is to be: ' 1, the two sets of data included thereon are read, the
derivative set by way of a device which is conscious of the ~rul~ ' unique route,
and the two sets of data thus recovered are compared to _ ' the valued article, or
at least to show that tbe person purporting to be the owner or holder of the valued article is
not an impostor.
Techniques of this general kind are described for example in United States Patents
nos. 4,879,747 and 4,995,0S I to Leighton and Micali.
This invention au71s to further improve upon such techniques by (inter alia) taking
advantage of certain special . I ~ ,.. t. . ;~ of recording media available for ;. . ~.. p". ~nl ". in
20 valued atticles.
According to a first aspect of the invention, there is provided an:
means for an article of value, comprising first and second data-storage means being carried
by the article, each data-storage means storing data for ' 7 or identifying the
article andlor a transaction associated with the article, the first data-storage means storing
2s first data as a r~on-random ~ structured magnetic . ~ ;c which varies
from place to place on the first storage means, the second storage means storing data
obtained by operation of the secret key of a secret key/public key ~ ao~y ~ l pair upon
data comprising the first data and additional data.
Such an: ' ~lion means can make copying and ~ more difficull
30 than with a ~lllla,~.,.l~ly structured magnetic . l. ~ alone whilst enabling
' read heads to be employed to read the data in the first storage means.
According to a second aspect of the invention, there is provided a method of
-' - ~ an article of value,
SUBSTITL~E SHEET (RLILE 26)
wo 96/02901 P~l,~.. ,.' 16
.
2 21 ~5~3
a) storing A~ . ,;r~ ;rn data in a first storage means carried by the article
as a non-random ~l.ly structured magnetic ~ t~ which
varies from place to place on the storage means,
b) operating on said ,."~l...,liri, .6.", data and additional data using the
secret key of a secret key/public key l,ly~Lu~y~ pair hereby creating
encrypted data,
c) storing the encrypted data in a second storage means carried by the
article,
d) reading the encrypted data from the second storage means,
e) operating on the encrypted data with the public key of said ~ r ~
pair to give decrypted ' ' data and decrypted additional data,
amd
f) comparing the decrypted ' ~ data with the - :h.. iri.,,l;.,"
data stored in the frrst storage means thereby ' ", the article of
value and/or the additional data
In order that the invention may be clearly understood and readily carried into effect,
some, 1 ' of the invention wiU now be described (by way of example only) with
reference to the a~ a,.~ g drawings, of which:
Figure I shows a credit card which can be ~ ' by means of one example
of the invention, and
Figure 24 illustrates ~ lr and by way of example the operation of various
features of the invention in a typical transaction.
Flgure 5 shows a block diagram of a method of - :h. .,l;~ ~;.,., according to anaspect of the invention.
Referring now to Figure 1, there is shown in outline a technique in accordance with
one example of this invention.
A valued article, in this case a credit card, is shown srh!~mntirSIlly at l. The credit
card I comprises co~ Lio"al printed and/or embossed material 2 including holograms and
30 trade marks or logos l, ~ lir of the card issuing and/or handling company. There is
also open ' about the card holder and open account information and, on the
reverse side. a signature strip 3 and a magnetic strip 4.
In accordance with this example of the invention, the magnetic strip 4 is formedwitn a magnetic watermark in the manner described, for example, in UK patent no.1331604 whereby a structural variation of a magnetic ~ 5 .;~I;r from place to place
SiJBSTlTUTE SHE~ (RULE 26)
WO 96/02901 PCTIGB95/01611
'' " '~ 3 2 f 95bo3
along the stnp is indelibly forrned into the strip. This inforrnation can be read quite readily
but the structural vatiation is exceedingly difficult to replicate in any manner which is not
immediately rejected by the technique used to read the relevant information. Thus the
; r.."...,i.,~, stored on the card I in strip 4 although overt is secure. Tape containing the
5 structural function described above is marketed by THORN Secure Science T
Ltd under the trade mark Watermark Magnetism and thus the structural variation aforesaid
will be referred to hereinafter as a magnetic watermark.
To add further security, however, this example of the invention provides that the
infnrrnq~inn recorded indelibly in strip 4, together with further; ~ , is operated on,
10 as described hereinafter, to generate a second piece of information which (hereinafter caUed
a "certificate") is also recorded on the card 1, but in a Cul~v~.u~ullal "soft magnetic" form;
either on the strip 4 itself or on a further strip (not shown). It will be ~ rl ' I that
can be recorded cu..v~,~..iu..ally on strip 4, ~ d upon the structural
variations which have been referred to 1- ~; -1,- f~.-- UsuaUy, there are two or more tracks
15 of the strip 4 which are assigned to .,u..v, ~ ''S, recorded data, and the strip is read by a
composite head which contains normal magnetic heads for the ~,UIIV. '- ~ly recorded
mformation and one or more special heads for the ' recorded by structuraT
vatiation.
The operation upon the r ~ recorded indelibly in strip 4 referred to above
20 comprises, in its most basic form, signature by the secret key of a ~Iyptuay ,t~lll pair. The
signed hlru~ Liun is recorded on the card 1, in this example on one of the tracks of stnp 4
read by a conventional head. It can thus be reproduced and, after being operated on by the
public key of the ~.lyl~uayab,lll pair to "de-sign" it, compated with the ;..f.., ~ ;.... indelibly
recorded as described earlier, to confum that the "de-signed" i.,f.. ~;.. contains
25 ' which matches that recorded indelibly as the magnetic waterrnark.
Thus not only is the card ~ r....1;. -~d as genuine because it contains the magnetic
waterrnark but also the transaction infnrrnq~inn recorded less securely on the card is
' ~ because it contains the signed version of the watermark.
This prevents ~ ' ' cards being acquited illegally and false inforrnation~0 entered in the accessible, ~ullv~ iundl recording tracks. It also enables the logistics of card
and distribution to be made more secure, because card stock is useless without
the vv ' ' magnetic stripe and vice versa, and even if the two are acquired together,
they cannot be used without knowledge of the secret code used to sign the vv '
~ ' for; ~r.. I .... ~ i.. in the certificate to be recorded conventionally on the card.
SIJBSTITLITE SHEET (RULE 26)
WO 96/02901 PCr/G~95/0l6l1
2 1 9 5 0 0 3
Thus, in principle. the watermarked inforrnation is easy to read but difficult to
replicate in a manner that wiii not be rejected on reading, and the uu~ ~iull~liy recorded
information, whilst casiiy read and replicated. does not reveal its connection through the
secret key to the ~.~n,l~nO~Led information.
The ~.UII.. '' "S recorded information need not be recorded on the strip 4. It
couid, for example, be recorded on a separate magnetic strip on the card, or in a different
medium altogether, such as an integrated circuit chip. In this latter event, the chip can be
relatively cheap since it is not required to contain high levels of security or complex anti-
copying procedures. In essence it operates as a low-level storage medium only.
The certificate infnrn~qrir~n which is cu~" "y recorded, eg., on strip 4 or on aseparate strip or in a chip, can usefully comprise a ~ date for the card's utiiity
and aiso other ' such as the expiry date, credit iimit, transaction avaiiabiiity and
one or more pieces of 'UlllldtiUII about the card-holder and/or biometric information
derived from and ~ ;r to the holder.
In particular, the maiden name of the holder's mother might be included, as may
basic IrLr";uiog;~ li information such as height, hair colour, eye colour, etc., or a scan of a
fingerprint or some other data pecuiiar to the card holder. In this latter respect, a
particularly beneficiai technique for deriving fingerprint data in a form that readiiy lends
itseif to recordai as described above is described in European Patent Application
No.91302280~ (Publication No. 450786), the contents of which are hl~ul~Jl ' herein by
reference.
The nnvention may, as mentioned previously, be used on a wide variety of vaiue
articles, such as (without limitation) sound recordings, spirits, vehicle ~ , and a
wide range of secure documents, such as passports, identity cards, driving licences and the
like.
It wili be appreciated that, sinOE the hl~ulllldliull recorded together with the signed
- version of the magnetic waterrnark, in the certificate contains a number of ,.----r~ y
and/or; m~ ' pieOEs of information, ail of that illrUlllldfiUII can be trusted as being
genuine, sinOE it was signed together with the watermark information, using the secret key.
30 Thus nothing that is outside the control of the card ;~1,1 ' nceds to be treated
secretly or kept in confidence.
The strength of the magnetic watermark and the use of the secret icey is aii that is
required to obtain the ~ ~ ~- 15~ improved level of security provided by this invention.
SlJBSTITUrE SHEET (~ULE 26)
WO 96/02901 r~ 'cl6ll
2 1 9~0~3
,,,.~"~ s
Thus. the tecbnique ensures that valued articles cannot be used before they haveoffficially been issued, or after they have expired. For off-line i - the reader can
be sure that card expiry data and credit limits, for example are genuine. Lf the off-line
reader includes biometric sensing, the reader can also be sure that the registered card holder
s is present. During on-line operations, the credit limit, expuy date and PIN (if present) can
be up-dated if required since the central computer can generate a new signed certificate to
be written on the card.
Conveniently RSA public key l,lyl~u~ Jhy is used, but altemative procedures can
be used if desired. In any event, a patticular "certificate" (ie., signed r ' including
o the watermark data) is relevant only to one specific card and could only have been
generated by one specific issuer - the one with ~cess to tbe secret key of tbe RSA (or
other) ~,ly~ y~.ll pair. As a result, the certificate can be stored on a soft magnetic tr~k
with no loss of security.
Some ' of and ~. ' to the invention will now be described in
s order to explain more fully the operation of a typical system.
Secure operation of an extended system is largely concerned with
among system ~- , , some of which are more trusted than others. The r .. ~ ~J
of several of those data links whicb are patticularly relevant to valued articles, protected as
described l ~ r , will now be described.
A simplified diagram of key usage is shown in Flg. ~. As it is based on RSA public
key cryptography, only the public keys are, 1 E~h secret key remains in a
bighly secure location, within the, ~ nn that generated it.
The system provider's public key (PPK) is stored within each card reader (CAD), in
a memory location which cannot be overwritten. It is used by the CAD to check other data
that has been signed by the provider, and is therefore trustworthy.
An example of this is each issuer's public key (IPK), which is signed by the system
provider's secret key (PSK), as shown above.
In practice. there will be large numbers of CADs, each holding the same data. Inaddition, e~h CAD holds its own unique key (not shown), which d:~; v. h ~ it from all
other CADs, and enables it to ~.. :. . l ' ~ 'y with the issuer.
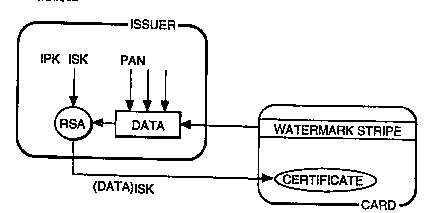
To initialise a card, the issuer frrst collects all the data that the CAD might need to
know about the card holder and the card, as shown in Fig. 3 in a block marked DATA.
This includes the number recorded as the magnetic watermark, the PAN, expuy date, PIM
S~18STITIJTE SHEET (RULE 26)
, . . .. , _ . . . . . . _ _
WO 96/02901 PCI~/GB9S/01611
2~ 9~0~3
policy, and so on, and is sufficient for the CAD to decide when an off-line t}ansaction is
.l~j)lV~I
The DATA block, when signed by the issuer's secret key (ISK), becomes the securecertificate, which is then copied onto a soft data area on the card.
In normal use, the CAD reads the cerLificate from the card, and decrypts the
original data.
The production of updated ceriificates on-line also follows the above prooedure, the
CAD acting as ' y between the issuer and vhe card.
The card is preferably provided with a transaction counter, which resides on thecard, and the main purpose of which is to restrict the number of off-line n, ~
allowed before a new oertificate is required In addition, the availability of a transaction
count allows the issuer to carry out further checks against attempted fraud. Printing the
transaction number on each receipt gives the card holder a convenient indication of card
usage.
In Flg. 4 the CAD has read the DATA block from the certificate, as described
above. Held within the data block is the issuer's off-line policy, and the maximum off-line
transaction count. The CAD also reads the card transaction count (CTC) from the card. It
then has enough information to decide whether the transaction can continue off-line or not.
In either case, provided that the transaction is approved, the CAD increments the
~0 CTC on the card, and prints the CTC as part of the card holder's reoeipt.
The increment line to the card has been shown m Fg. 4 as a separate connection,
for clarity. In practice, it would be part of a digital interface, whose operation could not
readily be blocked. To check that the transaction count has indeed i ~, the CAD
re-reads the new transaction count from the card.
It is highly unusual for systems to be provably secure. Even when a system is
believed to be secure, it is wise to plan for the ~ ,y that supposedly secret
information might become public knowledge. In the system described, the secret key of the
system provider, and the secret keys of the issuers, should be kept securely. However,
even if these keys become known, the system provided by this invention can be re-
configured, quickly and "y to use new key sets.
For jnstanoe, suppose that an issuer's secret key becomes known. The consequent
threat is that a fraudster might produce oertificates purporting to come from the issuer, and
thereby use out-of-date cards for off-line n ~
SUBSTITUTE SHEET (RllLE 26)
wo 9610290~ 6ll
To recover from this situation, the issuer ~enerates a new key seL, and gets thepublic key signed by the system provider. As each CAD comes on-line, the suspect public
key is replaced by the new one. To allow this, the CAD must have a protocol which allows
issuer keys to be updated. As the new key is signed by the system provider, it can be
5 accepted by the CAD as genuine.
Then, as each c-ard is presented to the updated CAD. any card using the old public
key is given an on-line transaction, which results is its next certificate being signed with the
new public key. F~h~ lulc, an updated card, when presented to a CAD which was still
using the old public key, would result in an on-line transaction during which the CAD
10 would be updated.
Thus tbe procedure required to change the issuer's public key is secure, fast,
1, and transparent to the user.
The procedure for updating the system provider's key is similar, but somewhat more
complex, since the system provider is the centre of trust. One option is to store a choice of
system provider public keys in each CAD, when the system is initialised. If one key
becomes cul~ ullli~cd, the system can move over to the next key. This involves re-signing
all the issuer's keys, and updating the CADs as and when they come on line. The cards
need not be updated. As before, the change is transparent to the user.
In the event that the article contains a PIN, that ;,.r.,...,Afi,~ may be secured within
20 a relatively ;. ~ f. ~ ~.L region of an integrated circuit chip. In this case, the card itself can
check the PIN when keyed in. Alternatively. an encrypted PIN may be stored withrr. the
"certificate" on the article and the CAD can then check the PIN, as is presently done at off-
line ATMs.
In another ," ,i .. - 1: " ....1 the integrated circuit chip is replaced by a two
25 bar code which can be read optically.
Figure 5 shows a flow diagram of a method accûrding to the second aspect of the
invention. The blocks have the following cignifir-An~-c Block 50 denotes storingdata in a first storage means carried by the article as a non-random
p~ '~!/ structured magnetic .1.,,.~ I;r which varies from place to place on the
3û storage mèans.
Block 51 denotes operating on said _ 1.. ;r~ data and additional data using
the secret key of a secret keylpublic key ~,ly~JtU:~y:>~lll pair hereby creating encrypted dat;~.
This will normally be performed by, for example, the card issuing authority in the case of
credit or other cards.
SULSrlTU~E SHEEr IRUL~ 26)
. .
WO 96/02901 PCT/GB9S101511
2 1 9 5 o o 3
, ~ 8 ~
Block 52 denotes storing thc cncryptcd data in a second storage means camed by
the article.
Block 53 denotes reading the encrypted data from the second storage means.
Block 54 denotes operating on the encrypted data with the public key of said
~lylJiO~y~ pair to glve decrypted ~.. ~;.. :iri.~-;.. data and decrypted additional data. -J
This wiD normaDy be performed by, for example, the card reading machine in the field in
the case of credit or other cards.
Block 55 denotes compafing the decrypted ~l~thPnfifi~tinn data with the
1....~ ;.... data stored in the fust storage means thereby ~ the atticle of
10 value and/or the additional data. This will normaUy also be performed by the card reading
system.
Ln general, the data stored in the second storage means may be read ~ 11y,
optically or electronically depending upon the nature of the storage means employed.
SUBSTIME SHEET (RULE 2~)