Note: Descriptions are shown in the official language in which they were submitted.
CA 02257975 1998-12-11
WO 97/49211 PCT/SE97/01089
1
~mHOD AND APPARATUS FOR DATA PROCESSTNG
mArhnical Field
The present invention relates to the technical field
of computer-aided information management, and concerns
more specifically a method and an apparatus for data pro-
s cessing according to the preamble to claim 1 and claim 8,
respectively, for accomplishing increased protection
against unauthorised processing of data.
In the field of computer-aided information manage-
ment, it is strongly required that the protection against
unauthorised access of data registers be increased, espe-
cially against violation of the individual's personal
integrity when setting up and keeping personal registers,
i.e. registers containing information on individuals. In
particular, there are regulations restricting and prohi-
biting the linking and matching of personal registers.
Also in other fields, such as industry, defence, banking,
insurance, etc, improved protection is desired against
unauthorised access to the tools, databases, applications
etc. that are used for administration and storing of sen-
sitive information.
W095/15628, which has the same owner as the present
application, discloses a method for storing data, which
results in increased possibilities of linking and match-
ing with no risk of reduced integrity. The method, which
is illustrated schematically in Figs 1 and 2 on the en-
closed drawing sheets, concerns storing of information
comprising on the one hand an identifying piece of infor-
mation or original identity OID, far instance personal
code numbers Pcn and, on the other hand, descriptive
information DI. The information OID + DI is stored as
records P in a database O-DB according to the following
principle:
CA 02257975 2005-O1-31
2
Step 1 OID (Pcn) is encrypted by means of a first,
preferably non-reversible algorithm ALG1 to an
update identity UID;
Step 2 UID is encrypted by means of a second, reversible
algorithm ALG2 to a storage identity SID;
Step 3 SID and DI are stored as a record P in the
to database 0-DB, SID serving as a record
identifier;
Step 4 At predetermined times, an altercation of SID in
all or selected records P is accomplished by SID
of these records being decrypted by means of a
decrypting algorithm ALG3 to UID, whereupon UID
is encrypted by means of a modified second,
reversible algorithm or ALG2' to a new storage
identity SID', which is introduced as a new
record identifier in the associated record P as
2o replacement for previous SID. This results in a
security-enhancing "floating" alteration of SID
of the records.
For a closer description of the details and advantages
of this encrypting and storing method, reference is made to
W095/15628. The storing principle according to steps 1-4
above is below referred to as PTY, which is an abbreviation
of the concept PROTEGRITY which stands for "Protection and
Integrity".
A detailed technical description of PTY is also
3o supplied in the document "PROTEGRITY (ASIS) Study 2", Ver.
1.2, 1 March 1996, by Leif Jonson.
In the technical field at issue, so-called shell
protections, however, are today the predominant method of
° ' CA 02257975 2005-O1-31
2a
protection. Shell protection comprises on the one hand the
external security (premises) and, on the other hand, an
authorisation check system ACS with user's passwords for
controlling the access. ACS is used as shell protection
for main frames, client/server systems and PC,
CA 02257975 1998-12-11
WO 97/49211 PCT/SE97101089
3
but it does not give full protection and the information
at issue can often relatively easily be subjected to
unauthorised access. This protection has been found more
and more unsatisfactory since, to an increasing extent,
"sensitive" information is being stored, which must per-
mit managing via distribution, storing and processing in
dynamically changing environments, especially local dis-
tribution to personal computers. Concurrently with this
development, the limits of the system will be more and
more indistinct and the effect afforded by a shell pro-
tection deteriorates.
summary of the Invention
In view of that stated above, the object of the pre-
sent invention is to provide an improved method for pro-
cessing information, by means of which it is possible to
increase the protection against unauthorised access to
sensitive information.
A special object of the invention is to provide a
technique for data processing or managing, which makes
it possible for the person responsible for the system,
the management of the organisation etc. to easily estab-
lish and continuously adapt the user's possibility of
processing stored information that is to be protected.
A further object of the invention is to provide a
technique for data processing which offers protection
against attempts at unauthorised data processing by means
of non-accepted software.
One more object of the invention is to provide a
technique for data processing according to the above-
mentioned objects, which can be used in combination with
the above-described PTY principle, for providing a safety
system with an extremely high level of protection.
These and other objects of the invention are achiev-
ed by the method according to claim 1 and the apparatus
according to claim 8, preferred embodiments of the inven-
tion being stated in the dependent claims.
CA 02257975 2005-O1-31
4
Thus, the invention provides a method for processing
of data that is to be protected, comprising the measure of
storing the data as encrypted data element values of
records in a first database, each data element value being
linked to a corresponding data element type.
The inventive method is characterised by the following
further measures:
storing in a second database a data element
protection catalogue, which for each individual data
element type contains one or more protection attributes
stating processing rules for data element values, which in
the first database are linked to the individual data
element type,
in each user-initiated measure aiming at
processing of a given data element value in the first'
database, initially producing a compelling calling to the
data element protection catalogue for collecting the
protection attribute/attributes associated with the
corresponding data element type, and compellingly
controlling the processing of the given data element value
in conformity with the collected protection
attribute/attributes.
The invention further provides an apparatus for
processing data that is to be protected, comprising a first
database for storing said data as encrypted data element
values in records, each data element value being linked to
a corresponding data element type, characterised by a
second database for storing a data element protection
catalogue, which for each individual data element type
contains one or more protection attributes stating
CA 02257975 2005-O1-31
4a
processing rules for data element values, which in the
first database are linked to the individual data element
type, means which are adapted, in each user-initiated
measure aiming at processing a given data element value in
the first database, to initially produce a compelling
calling to the data element protection catalogue for
collecting the protection att.ribute/attributes associated
1o with the corresponding data element types, and means which
are adapted to compellingly control the user's processing
of the given data element value in conformity with the
collected protection attribute/attributes.
In the present application the following definitions
are used:
~ "Processing" may include all kinds of measures which mean
any form of reading, printing, altering, coding, moving,
copying etc. of data that is to be protected by the
inventive method.
~ "Data element type" concerns a specific type of data
having a meaning as agreed on.
~ "Data element value" concerns a value which in a given
record specifies a data element type.
~ "Record" concerns a number of data element values~which
belong together and which are linked to the respective
data element types, optionally also including a record
identifier, by means of which the record can be
identified. Example:
CA 02257975 1998-12-11
WO 97/49211 PCT/SE97/01089
DATA ELEMENT TYPE
RECORD ID SOCIAL ALLOWANCE CAR
7pppC 7pOpQCencrypted data elementencrypted data element
value value
YYYY YYYYY encrypted data elementencrypted data element
value value
~ "Protection attribute indicating rules of processing"
may concern:
- data stored in the data element protection catalogue
5 and providing complete information on the rule or
rules applying to the processing of the corresponding
data element, and/or
- data stored in the data element protection catalogue
and requiring additional callings to information
stored in some other place, which, optionally in com-
bination with the protection attributes, states the
processing rules involved.
~ "Collection of protection attributes" may concern:
- collection of the protection attributes in the form
as stored in the data element protection catalogue,
and/or
- collection of data recovered from the protection
attributes, for instance by decryption thereof.
~ "Encryption" may concern any form of encryption, tri-
cryption, conversion of coding of plain-text data to
non-interpretable (encrypted) data, and is especially
to concern also methods of conversion including hash-
ing.
The inventive method offers a new type of protec-
tion, which differs essentially from the prior-art shell
protection and which works on the cell or data element
level. Each data element type used in the records in the
first database is thus associated with one or more pro-
tection attributes, which are stored in a separate data
element protection catalogue and which protection attri-
CA 02257975 1998-12-11
WO 97/49211 PCT/SE97/01089
6
butes state rules of how to process the corresponding
data element values. It should be particularly noted that
the calling to the data element protection catalogue is
compelling. This means that in a system, a.n which the
method according to the invention is implemented, is such
as to imply that a user, who for instance wants to read a
certain data element value in a given record in the first
database, by his attempt at access to the data element
value automatically and compellingly produces a system
calling to the data element protection catalogue in the
second database for collecting the protection attributes
associated with the corresponding data element types. The
continued processing procedure (reading of data element
value) of the system is also controlled compellingly in
accordance with the collected protection attribute/attri-
butes applying to the corresponding data element types.
The term "data element protection catalogue" and
the use thereof according to the invention must not be
confused with the known term "active dictionary", which
means that, in addition to an operative database, there
is a special table indicating different definitions or
choices for data element values in the operative data-
base, for instance that a data element value "yellow" in
terms of definition means a colour code which is within
a numeric interval stated in such a reference table.
Preferably, the processing rules stated by the pro-
tection attributes are inaccessible to the user, and the
read or collected protection attributes are preferably
used merely internally by the system for controlling the
processing. A given user, who, for instance, wants to
read information stored in the database regarding a cer-
tain individual, thus need not at all be aware of the
fact that certain protection attributes have been acti-
vated and resulted in certain, sensitive information for
this individual being excluded from the information that
is made available on e.g. a display. Each user-initiated
measure aiming at processing of data element values thus
CA 02257975 1998-12-11
WO 97/49211 PCT/SE97/01089
7
involves on the one hand a compelling calling to the data
element protection catalogue and, on the other hand, a
continued processing which is compellingly subjected to
those processing rules that are stated by the protection
attributes, and this may thus be accomplished without the
user obtaining information on what rules control the pro-
cessing at issue, and especially without the user having
any possibility of having access to the rules.
By altering, adding and removing protection attri-
butes in the data element protection catalogue, the per-
son responsible for the system or an equivalent person
may easily determine, for each individual data element
type, the processing rules applying to data element
values associated with the individual data element type
and thus easily maintain a high and clear safety quality
in the system.
According to the invention, it is thus the indivi-
dual data element (date element type) and not the entire
register that becomes the controlling unit for the way in
which the organisation, operator etc. responsible for the
system has determined the level of quality, responsibi-
lity and safety regarding the management of information.
To obtain a high level of protection, the data ele-
ment protection catalogue is preferably encrypted so as
to prevent unauthorised access thereto.
As preferred protection attributes, the present
invention provides the following possibilities, which,
however, are to be considered an incomplete, exemplify-
ing list:
1. Statement of what "strength" or "level" (for in-
stance none, 1, 2...) of encryption is to be used
for storing the corresponding data element values
in the database. Different data element values with-
in one and the same record may thus be encrypted
with mutually different strength.
CA 02257975 1998-12-11
WO 97149211 PCT/SE97101089
8
2. Statement of what "strength" or "level" (for in-
stance none, 1, 2,...) of encryption is to be used
. for the corresponding data element values if these
are to be transmitted on a net.
3. Statement of program and/or versions of program that
are authorised to be used for processing the corre-
sponding data element values.
4. Statement of "owner" of the data element type. Dif-
ferent data element values within one and the same
record can thus have different owners.
5. Statement of sorting-out rules for the correspond-
ing data element values, for instance, statement of
method and time for automatic removal of the corre-
sponding data element values from the database.
6. Statement whether automatic logging is to be made
when processing the corresponding data element
values.
According to a specially preferred embodiment of the
invention, the above-described PTY storing method is used
for encryption of all data that is to be encrypted a.n
both the database (i.e. the data element values) and the
data element protection catalogue (i.e. the protection
attributes). In the normal case where each record has a
record identifier (corresponding to SID above), prefer-
ably also the record identifier is protected by means of
PTY. Specifically, a floating alteration of the record
identifiers in both the operative database and the data
element protection catalogue can be made at desired in-
tervals and at randomly selected times, in accordance
with the above-described PTY principle. In the preferred
embodiment, especially the encapsulated processor which
is used for the PTY encryption can also be used for im-
CA 02257975 1998-12-11
WO 97!49211 PCT/SE97/01089
9
plementation of the callings to the data element protec-
tion catalogue and the pracedure for processing according
to the collected protection attributes.
The invention will now be explained in more detail
with reference to the accompanying drawings, which sche-
matically illustrate the inventive principle implemented
in an exemplifying data system.
BT"ief Descrinti nn of the Drawi nrrc
Fig. 1 (prior art) schematically shows the principle
of storing of data information according to the PTY prin-
ciple in W095/15628.
Fig. 2 (prior art) schematically shows the principle
of producing floating storing identities according to the
PTY principle in W095/15628.
Fig. 3 schematically shows a computer system for
implementing the method according to the invention.
Fig. 4 schematically shows the principle of data
processing according to the invention with compelling
callings to a data element protection catalogue.
Fig. 5 shows an example of a display image for
determining of protection attributes in the data element
protection catalogue.
Description of the Preferr d Embodiment
In the following, the designation IAM (which stands
for Information Assets Manager) will be used for the
components and applications which in the embodiment are
essential to the implementation of the invention.
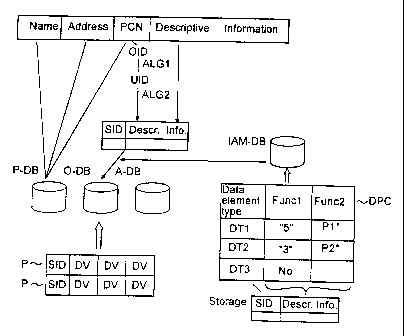
- Reference is first made to Fig. 3, which schemati-
cally illustrates a data managing system, in which the
present invention is implemented and in which the follow-
ing databases are included for storing information, in
this example person-related information:
- An open database P-DB which contains generally
accessible data, such as personal name, article
CA 02257975 1998-12-11
WO 97/49211 PCT/SE97/01089
name, address etc. with the personal code number
Pcn as plain text as record identifier;
- An operative database O-DB, which contains data that
is to be protected. Encrypted identification, in
5 this case an encrypted personal code number, is used
as record identifier (= storage identity SID). O-DB
is used by authorised users for processing of indi-
vidual records, such as reading and update;
- An archive-database A-DB, which contains data trans-
10 ferred (sorted out) from the operative database O-DB
and which is used for statistic questions, but not
for questions directed to individual records. The
transfer from O-DB to A-DB may take place in
batches.
- A database IAM-DB, which is a database essential to
the implementation of the invention. This database
contains a data element protection catalogue with
protection attributes for such data element types as
are associated with data element values in records
in the operative database O-DB. This database IAM-DB
is preferably physically separated from the other
O-DB and is inaccessible to the user. However, two
or more sets of the data element protection cata-
logue may be available: on the one hand an original
version to which only an authorised IAM operator has
access and, on the other hand, a copy version which
imports the data element protection catalogue from
the original version and which may optionally be
stored on the same file storage as the operative
database O-DB. The two versions may be remote from
each other, for instance be located in two different
cities.
The data system in Fig. 3 further comprises a hard-
ware component 10, a control module 20 (IAM-API), and a
program module 30 (PTY-API). The function of these three
components will now be described in more detail.
CA 02257975 1998-12-11
WO 97/49211 PCT/SE97/01089
11
The hardware component 10 acts as a distributed pro-
cessor of its own in a computer. It has an encapsulation
that makes it completely tamper-proof, which means that
monitoring by so-called trace tools will not be possible.
The hardware component 10 can as an independent unit
perform at least the following functions:
- Creating variable, reversible and non-reversible
encrypting algorithms for the PTY encryption
and providing these algorithms with the necessary
variables;
- Initiating alterations of storage identities (SID)
in stored data according to PTY, on the one hand
data in O-DB and, on the other hand, data in the
data element protection catalogue of IAM-DB;
- Storing user authorisations having access to records
in O-DB; and
- Linking original identities OID to the correct
record in 0-DB.
Control Modul 20 (IAM- PI)
The control module controls the handling of the
types of data protection that the system can supply.
The control module carries out the processing
requested via API (Application Program Interface) pro-
gramming interface.
Program Module 30 (PPTY API) 0
The program module (PTY-API) 30 handles the dialogue
between the application 40 involved (including ACS) and
the hardware component 10. This module may further log
events and control sorting out/removal of data from the
operative database O-DB.
Reference is now made to Fig. 4, which illustrates
the same four databases (P-DB, 0-DH, A-DB, IAM-DH) as in
Fig. 3 and which schematically illustrates how the pro-
CA 02257975 1998-12-11
WO 97/49211 PCT/SE97/01089
12
cessing of individual data elements are, according to
the invention, controlled according to the rules that
are stated by protection attributes in the data element
protection catalogue, which is stored in the database
IAM-DB.
The data that is to be stored concerns in this exam-
ple a certain individual and contains: (1) generally
accessible data such as name and address, (2) identifying
information, such as personal code number (Pcn), and (3)
descriptive information (DI). The generally accessible
data name and address is stored together with personal
code number (Pcn) in the open database P-DB, said storage
being performable as plain text since this information is
of the type that is generally accessible.
For storing the identifying information in combina-
tion with the descriptive information DI, the following
steps will, however, be made, in which the following
designations are used to describe encrypting and decryp-
ting algorithms. Generally speaking, the encrypting and
decrypting algorithms can be described as follows:
FType(Random number, Input data} - Results
wherein:
F designates a function.
Type indicates the type of function as follows:
FKIR = Non-reversible encrypting algorithm
FKR - Reversible encrypting algorithm
FDKR = Decrypting algorithm
Random number
represents one or more constants and/or
variables included in the function F.
Input data
are the data to be encrypted or decrypted, and
Results indicate a unique function value for a given
function
CA 02257975 1998-12-11
WO 97/49211 PCT/SE97/01089
13
Step 1 D~vis~on of the informat~in"
Identifying information is separated from
descriptive information;
Step 2 PreDarat~on of ~toraQ~ idenfi~t« S w:
An original identity OID is selected based on
the identifying information. OID is here select-
ed to be equal to the personal code number Pcn
of the individual. OID is encrypted by means of
a non-reversible encrypting algorithm ALG1, pre-
pared randomly by the hardware component 10, to
an update identity UID as follows:
ALG1: FKIR(Random number, OID) - UID
ALG1 is such that attempts at decryption of UID
to OID result in a great number of identities,
which makes it impossible to link a specific UID
to the corresponding OID.
Then UID is encrypted by means of a reversible
algorithm ALG2, which is also produced at random
by the hardware component 10, for generating a
storage identity SID as follows:
ALG2: FKR(Random number, UID) - SID
ALG2 is such that there exists a corresponding
decrypting algorithm ALG3, by means of which SID
can be decrypted in order to recreate UID.
The storage identity SID is used, as described in
step 4 above, as encrypted record identifier when
storing encrypted data element values DV in the
operative database O-DB.
CA 02257975 1998-12-11
WO 97/49211 PCT/SE97101089
14
Step 3 Production of encrypted data element values D
The descriptive information DI associated with
the original identity OID is converted into one
or more encrypted data element values DV linked
to a data element type DT each.
The encryption takes place as described below
with a reversible encryption function FKR, which
like the algorithms ALG1 and ALG2 above is also
produced at random by the hardware component 10.
The invention is distinguished by a compelling
calling here being sent to the data element pro-
tection catalogue in the database IAM-DB for
automatic collection of the protection attribute
which is linked to the data element type at issue
and which indicates "strength" or degree with
which the encryption of the descriptive data is
to be performed so as to generate the data ele-
ment value DV.
The table, which in Fig. 4 is shown below the
database IAM-DB, symbolises an exemplifying con-
tent of the data element protection catalogue,
here designated DC. As an example, it may here be
assumed that the protection function Funcl corre-
sponds to "degree of encryption". If the descrip-
tive information DI at issue is to be stored as a
data element value associated with the specific
data element type DT1 in the data element pro-
tection catalogue, the protection attribute "5"
registered in the data element protection cata-
logue is collected automatically in this case.
The descriptive information DI at issue will
thus, automatically and compellingly, be encrypt-
ed with the strength "5" for generating an en-
crypted data element value DV as follows:
CA 02257975 1998-12-11
WO 97/49211 PCT/SE97/01089
FKR(Random number, DI) - encrypted data element
value DV
For storing a less sensitive data element, for
5 instance a data element of the data element type
DT3, the compelling calling to the data element
protection catalogue in IAM-DB would instead have
resulted in the protection attribute "no" being
collected, in which case no encryption would have
10 been made on the descriptive data at issue, which
then could be stored as plain text in the opera-
tive database ODB.
Step 4 Storing of records in the operatiVP d~itaba~P DB:
15 The encrypted storage identity SID according to
step 2 in combination with the corresponding en-
crypted data element value or data element values
DV according step 3 are stored as a record in the
operative database O-DB.
As appears from the foregoing, a stored information
record P has the following general appearance:
Descript. information in the form
of encrypted data element values
(Storage identity (SID)/ DV1 ~ DV2 ~ DV3 ~ DV4
The original identity OID is encrypted according to
the PTY principle in two steps, of which the first is
non-reversible and the second is reversible. Thus, it
is impossible to store the descriptive information DI
along with a storage identity SID that never can be link-
ed to the original identity OID, as well as to create
"floating", i.e. which change over time, storage iden-
tities SID while retaining the possibility of locating,
for a specific original identity OID, the associated
descriptive information DI stored.
CA 02257975 1998-12-11
WO 97149211 PCTISE97101089
16
The descriptive data DI is stored in accordance with
protection attributes linked to each individual data ele-
ment. This results in a still higher level of protection
and a high degree of flexibility as to the setting up of
rules, and continuous adaptation thereof, of how sensi-
tive data is allowed to be used and can be used, down to
the data element level.
To increase the level of protection still more, the
data element protection catalogue DC is preferably stor
ed in IAM-DB in encrypted form in accordance with the
PTY principle, in which case for instance the data ele-
ment types correspond to the above storage identity and
the protection attributes correspond to the descriptive
information or data element values above, as schemati-
tally illustrated in Fig. 4. This efficiently prevents
every attempt at circumventing the data element protec-
tion by unauthorised access and interpretation of the
content of the data element protection catalogue.
In the illustrated embodiment, PTY can thus have the
following functions:
- Protecting the original identity OID in encrypted
form (SID) on the operative database O-DB (as is
known from said W095/15628},
- Protecting information in IAM-DB, particularly the
protection attributes of the data element protection
catalogue and the associated record identifier, and
- Protecting descriptive information DI in the form of
encrypted data element values DV for the data ele-
ment types that have the corresponding protection
activated in the data element protection catalogue,
and in accordance with the corresponding protection
attributes.
Functionality Protection
In the above embodiment of the procedure for input-
ting data in the operative database O-DB, only "degree
of encryption " has so far been discussed as data element
CA 02257975 1998-12-11
WO 97/49211 PCT/SE97/01089
17
protection attribute in the data element protection cata-
logue DC. However, this is only one example among a num-
ber of possible protection attributes in the data element
protection catalogue, which normally offers a plurality
of protection attitudes for each data element. Preferred
protection attributes have been indicated above in the
general description.
A particularly interesting protection attribute is
"protected programs". The use of this data element pro
tection attribute means that the data system may offer a
new type of protection, which is here called "functiona-
lity protection" and which means that only accepted or
certified programs are allowed to be used and can be used
in the system in the processing of data. It should be
noted that this type of protection is still, according to
the invention, on the data element level.
Now assume for the purpose of illustration that
Func2 in the data element protection catalogue DC in
Fig. 4 corresponds to this protection attribute and
that data elements of the data element type DTl and DT2,
respectively, are only allowed to processed with the
accepted applications or programs P1 and P2, respective-
ly. Unauthorised handling of the corresponding data ele-
ments by means of, for instance, a different program P3,
or a modified version P1' of Pl, should be prevented. As
protection attribute in the data element protection cata-
logue, data identifying P1 and P2 is therefore stored. In
a preferred example, an encryptographic check sum P1* and
P2*, respectively, is created, in a manner known per se,
based on every accepted program P1 and P2, respectively.
These check sums may be considered to constitute a unique
fingerprint of the respective accepted programs, and
these fingerprints can be stored as protection attributes
in the data element protection catalogue as illustrated
schematically in Fig. 4. It should however be noted that
such check sums for accepted programs can optionally be
stored in a data element protection catalogue of their
CA 02257975 1998-12-11
WO 97/49211 PCT/SE97/01089
18
own for registering of accepted programs, separately from
the data element protection catalogue with protection
attributes for encryption strength.
If the last-mentioned type of protection "protected
programs" is used, it should also be noted that the sys-
tem, in connection with a user-initiated measure aiming
at processing of a given data element, for instance in-
putting a new data element value in a certain record,
need not carry out a complete examination of all programs
accepted in the system. If, for instance, the user tries
to use a program P3 for inputting in the operative data-
base O-DB a new data element value, a compelling calling
is sent to the data element protection catalogue in con-
nection with the corresponding data element type, for
instance DT1. The associated protection attribute P1*
is then collected from the data element protection cata-
logue, which means that such a data element value is only
allowed to be stored by means of the program P1. The
attempt at registering the data element value by means of
the program P3 would therefore fail.
By periodic use of the above-described functionali-
ty protection, it is possible to reveal and/or prevent
that an unauthorised person (for instance a "hacker")
breaks into the system by means of a non-accepted program
and modifies and/or adds descriptive data in such a man-
ner that the descriptive data will then be identifying
for the record. The data element values are thus not
allowed to become identifying in the operative database
O-DB.
Traceability logging
"Logging" or "traceability" is another type of pro-
tection which according to the invention can be linked to
a data element type in the data element protection cata-
logue. If this protection is activated for a certain data
element type, each processing of the corresponding data
element values in the operative database O-DB will auto-
CA 02257975 1998-12-11
WO 97/49211 PCT/SE97/01089
19
matically and compellingly result in relevant information
on the processing ("user" "date" " "
record , user pro-
gram" etc.) being logged in a suitable manner, so that
based on the log, it is possible to investigate after-
s wards who has processed the data element values at issue,
when, by means of which program etc.
Readings of Data from the Ooerati~ro Dataha~P DB
In connection with a user-initiated measure aiming
at reading/altering data element values in the stored
records in the operative database O-DB, the following
steps are carried out, which specifically also comprise
a compelling calling to the data element protection cata-
logue and "unpacking" of the data which is controlled
automatically and compellingly by collected protection
attributes.
Step 1 The record is identified by producing the storage
identity SID at issue based on the original iden-
tity OID, (Pcn) that is associated with the data
element value DV which is to be read, as follows
FKR(FKIR(OID)) - SID
Step 2 When the record has been found by means of SID,
the encrypted data element value DV (i.e. the
encrypted descriptive data that is to be read)
is decrypted as follows by means of a decrypting
algorithm FDKR~
FDKR(DV) - descriptive data (plain text)
The carrying out of this decryption of the data
element value, however, requires that the encryp-
tion-controlling protection attribute of the data
element is first collected by the system from the
data element protection catalogue DC, i.e. the
CA 02257975 1998-12-11
WO 97/49211 PCT/SE97/01089
attribute indicating with which strength or at
which level the data element value DV stored in
O-DH has been encrypted. Like in the above proce-
dure for inputting of data in O-DB, also when
5 reading, a compelling calling thus is sent to the
data element protection catalogue DC for collect-
ing information which is necessary for carrying
out the processing, in this case the unpacking.
10 It will be appreciated that such a compelling
calling to the data element protection catalogue
DC, when making an attempt at reading, may result
in the attempt failing, wholly or partly, for
several reasons, depending on the protection
15 attribute at issue, which is linked to the data
element value/values that is/are to be read. For
instance, the attempt at reading may be inter-
rupted owing to the user trying to use a non-
accepted program and/or not being authorised to
20 read the term involved.
If the data element protection catalogue is encrypt-
ed, the decoding key can be stored in a storage position
separate from the first and the second database.
Fig. 5 shows an example of a user interface in
the form of a dialogue box, by means of which a person
responsible for IAM, i.e. a person responsible for secu-
rity, may read and/or alter the protection attributes
stated in the data element protection catalogue. In the
Example in Fig. 5, the data element types "Housing allow-
ance" and "Social allowance" have both been provided with
protection attributes concerning encryption, sorting out,
logging and owner. Moreover, registration of authorised
users and protected programs linked to the data element
type "Social allowance" has taken place in submenus.
T