Note: Descriptions are shown in the official language in which they were submitted.
DEC-0,9-99 18:32 6136492260 P.04 R-100 Job-474
,121911999 18:34 6136492260 WORDSMITH PAGE 04
FILE! P~H'~ TNIS AME~d~EQ
TTI~AWS~ATIpN
Mobile Radio Terminal with Coupled Computer for Internet or
Network Applications and a Method for Operating such a
Combination of Equipment
The present invez'~tion relates to arrangements and .methods for
using services offered on the znternet or other networks, which
require a high level of security. Examples of apparatuses with
chip-card units are mobile radio telephones that are essentially
used for transmitting speech over mobile radio networks. The so-
called SIM module that is integrated into the mobile radio
telephone or the integrated chip card are used to authenticate
the mobile radio telephone as an apparatus that is authorised for
mobile radio and includes a key for encoding the speech
information that is transmitted, or for decoding the speech
information that is received.
Another type of apparatus with chip card units includes, for
example, remote controls for television sets, in which the chip
card is used as proof of authorisation for receiving pay-far-view
television programmes and, optionally, as a means for making
payments.
Computers, such as personal computers or laptops, that have a
connection to a fixed network or a mobile network can use
rnternet applications by means of the http protocol. In the case
of procedures in which security is particularly relevant, such
as, for exampJ.e, in the case of placing orders or making
-1-
CA 02293554 1999-12-10
DEC-09-99 1IB:32 6136492260 P.05 R-100 Job-4Z4
12/0911999 18:34 6136492260 WORDSMITH PAGE 05
payments, chip cards are used to control the particular
transactions by way of a chip-card xeader that is connected to
the computer. Connection can also be made to a mobile radio
network by way of a mobile radio telephone that is equipped with
a data connection; see, for example, PG Profess2ona~, March,
1994, pp_ 263-260, or Cash Flaw, 2/95, pp. 140-141.
In this connection, it is known from WO 96/25828 that when a
computer is connected to a mobile radio network by way of a
mobile radio telephone, using an appropriate chip card for the
mobile radio telephone, services that are available on the
computex and selected by way of the identification code can be
- controlled after inputting an identification code by way of the
mobile radio telephone.
is
In addition, it is known from DE 195 38 842 A1 that
configuration or speech~subscriber data can be transmitted by way
of the data connection to the mobile radio telephone to a memory
in the mobile radio telephone, when it is also possible to use
the memory on the subscriber-card chip. In the same way, this
data that is stared in the mobile radio telephone can be read and
amended in the computer connected to it in this way.
Also known are combinations of apparatuses made up of television
receivers and computers, in which one display is used aointly by
the television section and the computer section.
-z-
CA 02293554 1999-12-10
DEC,-09-99 18:32 6136492260 P.06 R-100 Job-4T4
12/9/1999 18:34 6136492260 WORDSMITH PAGE 06
Examples of possible applications involving a computor combined
with the chip card are authentication, generation of digital
signatures, credit/debit card transactions, and electronic purse
transactions.
A particularly high a level of security can be achieved by
asymmetric cryptographic methods in which the private key is
stored in the chip cards in such a way that it cannot be read
out, and the corresponding crypto processes can be carried out in
the chip card so that they cannot be manipulated. Chip card
components for applications of this kind are already available on
the market; one example of such a component is the SLE 44CR80S,
which is manufactured by Siemens AG.
It is the objective of the present invention to so broaden the
range of application of apparatuses and with chip card units such
that secure transactions are possible in conjunction with a
computer.
According to Claim 1, this has been achieved in that a mobile
radio terminal apparatus is so expanded by using an appropriate
chip card that it can also be used as a card terminal for a
computer. The use of a mobile radio terminal modified in this
way, in conjunction with a computer that is connected to it and
which is connected in the manner known per se to a communications
network, makes it possible to uee personal ar public network
_3_
CA 02293554 1999-12-10
DEC-0,9-99 18:32 6136492260 P.O7 R-100 Job-474
12/09/1999 18:34 6136492260 _- WORDSMITH PAGE 07
services that require a high level of security by way of the
Internet. without the computer having to have a chip card reader.
This results in a major advantage for mobile radio telephone
owners in that they can use network services from any type of
standard computer, regardless of location,
Developments of the present invention relate to methods used to
operate such a combination of apparatuses. These apply, amongst
other things, to activating the mobile radio terminal used as a
card terminal and which, in addition to using network services in
the usual manner, also permits encoding arid decoding in the
manner known per se.
Particular advantages result from the fact that highly sensitive
data, such as personal identification numbers (PIN) and sums of
money can be input at the mobile radio terminal using the keypad
and, given an available display, can be shown unencoded before
they are coded and passed on to the computer. This avoids having
to use the computer keyboard for input, so that viruses that may
be resident in the computer cannot falsify the data that is
input_
It is also an advantage that control words can be input by way of
a microphone and used as proof of authorisation; these words and
then digitized and transferred to a control section of the
communications network, where they are compared with a reference
-4-
CA 02293554 1999-12-10
DEC-0.9-98 18:32 6136482260 P.08 R-100 Job-4T4
12/09/1999 18:34 6136492260 ---,WORDSMITH PAGE 08
the basis of a personal biometric feature, which is in keeping
with the increased demands for security.
In addition, data and/or control :Enformation can be transmitted
through the connection interface to the memory in the mobile
radio terminal, whexe it can be stored. Thus, it is possible to
modify or store data on the chip card. Such data can, for
example, be keys for encoding or decoding, or oan be a sum of
money for a cashcard. The latter provides the possibility of a
card telephone when, if it is used as a telephone, incoming fee
Pulses can deduct the appropriate amount of money in each
particular instance.
Details of present invention are described in greater detail
below on the basis of one embodiment that shown in the drawings
appended in hereto. These drawings show the following:
Figure 1: a schematic overview of a computer with a connection to
a network and a connected mobile radio telephone as a
card terminal, for using network services;
Figure 2: a schematic representation of a chip card used for
various applications.
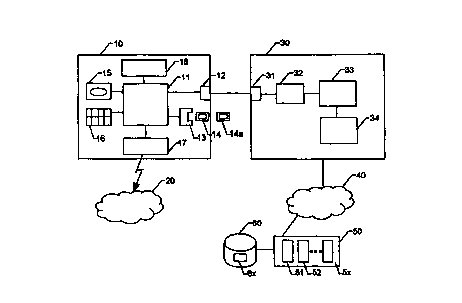
Figure 1 shows a mobile radio telephone 10 as an apparatus with
the chip card unit, this being connected by way of a standard
interface 12, ~.g., an Rs 232 interface, to a Computer 30 that is
-- 5 -
I
CA 02293554 1999-12-10
DEC-09-99 18:32 6136492260 P.09 R-100 Job-474
12/09/,1999 18:34 6136492260 WORDSMITH PAGE 89
interface lz, e.g., an Rs 232 interface, to a computer 30 that is
a conventional PC. Within the mobile radio telephone 10, the
interface 12 is connected to a control unit 11 to which a
contacting unit 13 for the SIM module/the chip card 1,4/14a, a
display 15, the keypad 16, a speech and radio module 17, as well
as a memory 18 are also connected. The speech and radio module 17
has access to the mobile radio network 20 in the usual way,
Only the interface 31 for the mobile radio telephone 10 with the
associated driver 32, which are part of the computer 30, are
shown, together with the so-Galled browser 3z and computer
applications 34 for using network services, for examp~.e, the
Internet; these are connected by way of the communications
network b0 to an appropriate provider 5A, e.g., in the form of
the so-called server. -
mhe applications that are accessible with a key are stored on the
SIM module or the chip card 14, 14a. Individual chip cards can be
provided for the various applications. However, as is shown in
Figure 2, the mobile radio applications for GSM/DCS 141 as well
as the various Internet/network applications 142, 7.43, 14x can be
stored on a chip card with their various keys,
Before using one of the network services, an appropriate chip
card is to be sexected and inserted into the contacting un~.t 13
of tire mobii~e radio telephone 1o that is coupled to the computer
-6-
_T ...~~~,...~ .
-_
CA 02293554 1999-12-10
DES-Q9-98 16.32 6136482260 P.10 R-100 Job-474
12/0911999 18:34 6136492260 WORDSMITH PAGE 10
telephone 10 as a card terminal is to be loaded with the
appropriate driver software by way of the connecting interface
31. This can be done from a diskette. However, in order to
prevent manipulation at the driver 32, it is expedient that the
driver software--signed With a private key by the mobile radio
network operator--be loaded from an appropriate server on demand
from the computer 30 and loaded into the driver 32 by way of the
communications network. Subsequent~.y, verification of the driver
software can be effected automatically on the basis of a
to corresponding public key of the mobile radio network operator
located in an application area, e.g., 14x, on the chip card
14/14a.
zt is expedient that the driver software operate according to an
established standard, such as ISO 7826-3 and the rcC
specification developed jointly by the PC/Sc workgroup and
Microsoft (http//:smartcardsys.com).
The network application can be started within the computer 30,
~Q for example, by calling up the browser 33 and inputting a so-
called "Uniform Resource Locator" (URL). This establishes a
connection to the service provider 5o by way of the network 40,
When the desired services 51, 52, ..., 5x can then be used. The
mobile radio telephone ZO or the control unit 11 that is
2S connected then acts as a conventional card terminal. Depending on
the services 51, 52, ..., 5x that are available from the servlCe
CA 02293554 1999-12-10
i
DEC.-0,9-99 18:32 6136492260 P.11 R-100 Job-4t4
12/09/1999 18:34 6136492260 WORDSMITH PAGE 11
the services 51, 52, ..., 5x that are available from the service
provider, chip card applications 1,42, 143, .., 14x can be
selected and used, for example, for mutual client-service
authentication, for verification of access rights, for providing
digital signatures for sensitive data, for the generation of keys
for encoding data, far proof of ordering, and for payment from an
electronic purse.
As compared to a conventional chip card reader, the present
invention permits additional functions that ensure a considerably
higher level of security:
In principle, computers that axe connected to the Internet are
exposed to imported viruses. For example, a sum of money that is
to be transferred between accounts and which ~.s input by way of
the computer keyboard can be falsified by such a virus before the
transaction sari Concluded correctly with the Internet server.
rf the mobile radio telephone ar another apparatus is used as a
card terminal, this manipulation can be prevented in that--as a
result of the computer/server application--sensitive data such as
the sum to be transferred is input by way of the keypad 16 on the
apparatus 10. The control unit 11 is informed of this amount by
way of a code, so that the data that is input can, on the one
hand, be shown unencoded on the display 15, where it can be
checked. on tJh,e other hand, this data is eslcoded or signed by a
_g_
CA 02293554 1999-12-10
DEC-09-99 18:32 6136492260 P.12 8-100 Job-4t4
12/09./1999 18:34 6136492260 WDRDSMITH PAGE 12
chip card application 14x, and then transferred to the computer
30 or the responsible servex for further processing.
In the same way, in the event that a PIN number required by a
computer/network application is input, the PIN that is input by
way of the keypad 16 is encoded in the chip card before it is
passed on to the computer/network application.
Applications that require a high level of security frequently
require authentication that is based on biometric features. Using
the present invention as described herein, this can be done in
the following way:
After successful, mutual client-server authentication based on
asymmetric crypto methods, the user, as the so--called client, is
required to provide a speech sample, e.g., an agreed upon
recognition word, which is spoken three times, orie after the
other, into the microphone 17 of the mobile radio telephone 10.
Then, the control unit 11, triggered far example by a control
code transmitted from the application 5x or from the browser 33,
passes the digitised flow of speech to the responsible
application, e.g., 5x, in the form of a bit string. This extracts
the personal speech features from the bit string that has been
received, and compares these with reference patterns 6x stored
on the hard disk 60 in order to verify the identity of the user
on the basis of his speech sample.
CA 02293554 1999-12-10
DEC-09-99 18:32 6136492260 P.13 R-100 Job-4t4
12/09/1999 18:34 6136492260 WDRDSMITH PAGE 13
mhe present invention also makes provisions such that within the
framework of a computer application 34, data such as telephone
lists, address lists, sale dates, price lists, etc., can be
loaded into the memory 18 of the mobile radio telephone and can
be shown on the display 15, with selection also being possible
by way of the keypad 16.
In another computer application 3~, digitised data that is keyed
in or input by voice at the mobile radio telephone to oan be
transferred into the computer 30 and further processed either
there or in a network server, or else subsequently recalled by
othex users.
In addition, it is also possible for programmes to be loaded into
the memory 18 of the mobile radio telephone to by way of the
connection interface 31/12 as a result of a command from a
computer application 3.~; these can then be run--separated by
time-~.»in the control unit 11.
Finally, applications/3ceys can be modified, erased, or loaded on
the chip card itself as a result of a command from a computer
application 34.
In all cases, data, programmes, or applications can be
transferred between the mobile radio telephone 10 or the chip
card la/14a and the computer 30 or the network server either
_ ~ o.~
CA 02293554 1999-12-10
. DES-Q9-99 18:32 6136492260 P.14 8-100 Job-474
12/09/1999 18:34 6136492260 WORDSMITH PAGE 14
encoded or so that their integrity is secured. The )keys required
to do this are either already stored on the chip card or were
exchanged previously between the aomputer/network server
application arid the chip card, e.g., by using the l~iffy-Hellman
method. Furthermore, the mobile radio telephone 10 can generally
be used in a similar manner for encoding or decoding data.
A further version of the present invention is the general use of
a chip card application in GSM and fixed networks. An example of
this is the electronic purse. It can be loaded, for example, as
application 14x on the chip card 14/14a installed in the mobile
radio telephone lo, by way of a computer/network application
33/34/5x and then decremented according to long-distance tariffs
during a subsequent GSM telephone conversation, e.g., by a pulse
emitted by the radio exohange at regular time intervals. This
sort of ~~pre-paid« telephoning reduces the risk of fraud to which
the users of mobile radio are exposed today. The same thing
applies to any other apparatus that is comparably equipped with
chip card units, e.g., remote controls that are used in
connection With pay-fox-view television.
-11-
CA 02293554 1999-12-10