Note: Descriptions are shown in the official language in which they were submitted.
CA 02302999 2000-03-23
Background of the invention
There are many examples of situations where a manufacturer, vendor, end-users
or other parties would
benefit from the ability to monitor objects that are not in their immediate
purview. These examples include
a car manufacturer and its vehicles, a taxi dispatch and its fleet, security
office and a monitored premise, or
even a parent and his/her child. There are existing systems which enable such
monitoring, for example, a
home security system, or a trucking fleet monitoring system. A typical home
security system utilizes a
telephone, whereby a module in the home dials the security office when a
breach has been detected. It
requires the office to be available with sufficient phone lines, personnel,
and equipment to answer the
potential number of the calls and respond in a prescribed manner. A typical
trucking fleet monitoring
system utilizes a cellular system where a device on the truck makes a network
connection with the
monitoring station, requiring that a real-time network be available, such that
a computer can receive the
information and respond immediately to the transmitting device. Should the
host not be operable at that
immediate instance, a backup host must be available to receive and respond to
the network request,
otherwise the communication fails and a later attempt is required. Both
systems prescribe a remote device
communicating directly with an end-user, requiring the end-user to have
sufficient equipment and
capability to connect and engage in real-time communication with the calling
device.
This patent teaches a significant improvement over both systems. Firstly,
there is no direct connection
between the end-user and the remote device. All messages go through an
intermediary, which authenticates
and processes all messages. An application located at the Central Processing
Station would be programmed
to respond to monitoring information received from each device, storing the
information in a database,
sending an automatic response to the sending device, or generating a report or
alert for the end-user. The
application would also authenticate and respond to requests from end-users,
forwarding instructions on the
remote device as necessary.
Using an asynchronous method of communication such as electronic mail reduces
the equipment and
bandwidth requirements compared to other systems. Remote devices and end-users
would be connected to
any number of Internet portals, through a variety of means including but not
limited to phone lines, cable
modems, wireless e-mail pagers, and/or cellular networks. An e-mail message
containing data or requests
would be sent or received using the portal's e-mail server. As part of the
standard Internet e-mail
infrastructure, these messages would ultimately be delivered to the e-mail
servers) located at the Central
Processing Station, whenever that server is operable and able to send or
receive messages.
CA 02302999 2000-03-23
A monitored car, boat, vending machine or person could be equipped with a
wireless e-mail device that
would provide a connection to the Internet, facilitating the communication of
Internet e-mails. A home,
office, or object within a home or office could be coupled with a wired e-mail
device. These e-mail devices
would collect information about its host object and compose an e-mail message
containing this data to be
sent at pre-programmed or externally triggered intervals. These e-mails would
then be transmitted between
the monitored object and a Central Processing Station. A connection would then
be established between the
Central Processing Station and the manufacturers, vendors, owners, monitoring
stations and other parties
interested in monitoring or controlling the remote object. This connection
could be made using a
switchboard and operator, e-mail, web-page, or custom application utilizing
the Internet or a private
network.
On the remote monitored object, the e-mail device would be coupled to sensors
to provide data about
the monitored device. These inputs could include GPS or wireless location
data, instruments for measuring
performance and other telemetry data, outputs from computers, signal
processors or other logic circuits, or
switches that are triggered by an operator. In the example of an automobile,
these inputs could be signals
from the OBD-2 port of most current vehicles, anti-theft devices, odometer,
airbag deployment circuit, GPS
unit, or driver input device consisting of a keypad, touch-screen, microphone
or other apparatus.
The remote device could also be coupled with a control circuit to respond to e-
mail messages sent from
the Central Processing Station. These e-mail messages could be instructions to
start or stop transmitting
location data at specific intervals, to activate or deactivate the monitored
object, to turn on or off security,
or even to upgrade systems with data supplied in the current or subsequent
messages. These e-mail
messages could also be messages intended for the operator of the monitored
object, forwarded from a
monitoring station, dispatch, security office, or other third party, through
the Central Processing Station.
In a preferred implementation of this system, a wireless e-mail pager would
form the basis of a module
installed in an automobile. This pager would be integrated with a logic module
connected to a variety of
data inputs such as the OBD-2 port of the vehicle, an airbag deployment
sensor, the odometer, a GPS
receiver and/or an anti-theft unit. The module would collect data from the OBD-
2 port and compose an e-
mail whenever preprogrammed odometer values were reached. The module could
also include circuitry that
monitors the OBD-2 data and triggers a message to be composed and sent
whenever unusual values are
detected. The airbag deployment sensor could also trigger an emergency message
be sent. Should an
external event trip the anti-theft unit, this information as well as GPS
location information could be
included in a message. A small apparatus consisting of a roadside assistance
button and a 911 button could
be installed on the dash of the vehicle, enabling the operator to trigger a
message requesting a tow-truck or
emergency vehicle be sent to the location determined by a GPS receiver. As
well, a microphone connected
with a circuit that digitizes, compresses and segments the audio signals into
data that could be composed
into an e-mail message would allow an operator to send an audio message. An
external port or network
connection would allow third party devices to also compose and send messages
to the Central Processing
Station, via the e-mail pager.
The logic module could also include provisions to respond to messages from the
Central Processing
Station. These messages could be those automatically generated by the Central
Processing Station - for
instance, a request to start transmitting vehicle location data, in response
to an anti-theft alarm message.
These messages could also include those forwarded by the Central Processing
Station from owners,
manufacturers, or authorized monitoring facilities. These could be requests to
unlock the doors, deactivate
or reactivate the vehicle. They could also be audio or text messages directed
at the operator of the vehicle,
which the logic module would direct to a display panel or audio decompressor
circuit for playback over a
speaker.
The system described in this document shares some similarities with existing
patents. Some of these
are summarized below, with discussion detailing their commonalties and key
differences.
US Patent #5,732,074, entitled 'Mobile Portable Wireless Communication
System', teaches a rather
complex system whereby numerous remote stations can access an operating system
within a vehicle using
an airlink. The vehicle would consist of a wireless device and a second
network with a controller for
coordinating the communication of various devices within the vehicle, with
each device in the second
CA 02302999 2000-03-23
network having a unique designation and capable of responding to requests for
information. The patent
teaches that the vehicle would have a web-server to respond to the requests
for information from multiple
remote stations, receiving from each station an address to transmit the
response to. There is no provision for
authentication or to prevent unauthorized access to information from the
vehicle - the vehicle simply sends
information back to the address of the remote station. There is also no
provision for any functionality other
than remote monitoring - remote stations can only request information from a
vehicle. The system detailed
in this document proposes a remote monitoring AND control system whereby only
one authorized remote
server is sent data from the vehicle and is able to request information or
initiate actions. All messages are
validated to prevent unauthorized access to the system. As defined in this
document, the messaging
apparatus coupled to any fixed or mobile object would not require a computer,
operating system, or
computer network connected to other network devices in order to provide
monitoring information.
US Patent #5,432,841, entitled 'System for Locating and Communicating with
Mobile Vehicles',
relates solely to cellular telephone based systems and describes a methodology
whereby a vehicle can be
located using a cellular network. A remote computer with the specific task of
identifying vehicle locations
communicates by sending e-mail messages containing location data to a
monitoring party. The system
detailed in this document does not cover the determination of a vehicle
location - it simply accesses an
apparatus in the vehicle that provides the location data. The messaging
apparatus then transmits the
location data to a Central Processing Station, which simply receives that
information by e-mail and
communicates it on to an end-user, through e-mail or other means.
US Patent #5,539,810, entitled 'Data Messaging In A Communications Network',
and US Patent
#5,544,225, entitled 'Data Messaging In A Cellular Communications Network',
both refer to a system
utilizing a cellular telephone network whereby a cellular device mounted on a
trucking trailer conveys
location and status information. This is accomplished by altering the
identifier of the cellular transceiver. A
mobile switching unit coupled with a cellular network detects this altered
identifier and routes it to a
platform. The mobile switching unit must be available to receive when the
altered identifier is transmitted -
this is a real-time network system. The platform translates the altered
identifier to obtain location and status
information and makes this available to remote users. This system is limited
to a one way transfer of
information from a trucking trailer to a platform to users of the information.
The transmitted data is limited
to location and status information and is strictly intended for use with a
cellular network.
US Patent #5,844,473, a 'Method and Apparatus for Remotely Collecting
Operational Information of a
Mobile Vehicle', teaches a system where a cellular device attached to a
vehicle communicates vehicle use
and safety inspection data to a central server when a request for information
signal is sent by the central
server. A unique cellular identifier identifies each remote device. The
central server is required to poll each
device in order to obtain information - each device must have a data
collection unit in order to store the
usage and safety inspection data until it is polled. This is simply a one way
system - no provision is made
for a central server to command and control the remote device. The vehicle
mounted cellular must be
available to receive the polling request at the moment it is transmitted. The
central server must meet the
same condition when the information from the vehicle is transmitted.
US Patent #5,708,417, a 'Monitoring System for Remote Units', describes a
system whereby remote
units are connected with a radio device to transmit proximity data to a local
computer equipped with a radio
receiver. This local computer generates an alarm, contacts a security office,
and generates a report when the
remote unit leaves the security area. This system is only intended for
monitoring the presence of a vehicle
inside a specific zone within range of a local computer equipped with a radio
receiver. This is also a real-
time system, requiring the local computer to be operational and ready to
receive the signal, otherwise a
remote unit may leave the security area without an alert being triggered.
The system detailed in this document provides a comprehensive system for any
remote device, fixed or
mobile, to communicate information about itself and objects connected to it to
a Central Processing Station,
whereby that information can be accessed by authorized parties. It also
provides for authorized third parties
and automated processes to communicate, via the Central Processing Station,
requests for information and
commands to initiate actions on the part of the remote device or items
connected to it. It is based on an
asynchronous messaging methodology, using store and forward technology such as
Internet e-mail, to
transmit predefined authenticated messages from the remote device to a Central
Processing Station and vice
CA 02302999 2000-03-23
versa. Cellular identifiers are not utilized - a unique address registered
within the asynchronous store and
forward messaging system is utilized - in the case of an Internet e-mail
system, an e-mail address is used.
This system does not impose the strict requirement that the Central Processing
Station be available to
receive at every possible moment or face the possibility of losing a message -
the utilization of a store and
forward messaging system allows for system down-time. Messages would remain
stored until such time as
the Central Processing Station is able to receive it. The messaging apparatus
could also be equipped with
facilities to store a message for delayed transmission should it momentarily
be unable to transmit.
Summary of the invention
The present invention details a system that communicates commands, requests
and data in the form of
standardized Internet electronic messages between a Central Processing Station
and a remote object
coupled with a device that facilitates the transfer of messages via a
asynchronous store and forward means,
such as e-mail. The system also details the connection of interested third
parties, manufacturers, vendors,
agents and owners of the remote objects, to the Central Processing Station,
whereby they may receive alerts
and reports regarding the remote objects and request commands be sent to those
same objects. This
connection may be in the form of e-mail, web pages, telephone operator or menu
system. Third parties
would not have direct access to the remote devices.
The system includes at the remote site an Internet e-mail device capable of
receiving and/or
transmitting e-mail messages over a wireless or physical network which in turn
is connected to the Internet.
This e-mail device would be encoded with a unique e-mail address, such that
the device, and in turn its host
object, can be distinctly identified. This device would be coupled with
circuitry which would compose
specific messages based on data received from sensors, switches and other
apparatus. These messages
would be sent to the e-mail address of the Central Processing Station. This
circuitry could also include
logic to authenticate and respond to e-mail messages received from the Central
Processing Station. Possible
connections to this circuitry include but are not limited to GPS receivers,
wireless location units,
automobile data ports, anti-theft sensors and control units, LCD display
panels, touch screens, keypads,
joysticks, I/O ports, and audio compressors/decompressors.
The system details a Central Processing Station, which may be singular or
many. A Central Processing
Station would consist of one or more e-mail servers, connected to the Internet
for the purpose of receiving
messages from the remote devices and from authorized third parties. An
application would process each
message received from remote objects, authenticating and determining the type
of message. The e-mail
address of the sender would be compared with a database registering each
remote object with a unique e-
mail address. Once the remote object has been identified, the application
would respond in a pre-defined
manner, based on the type of object and the type of message. These responses
could be but are not limited
to the notification of security or monitoring agencies, the generation of
reports to be sent to manufacturers,
or storage of data for future processing.
Messages received from authorized third parties would also be authenticated to
prevent unauthorized
parties from gaining access to information regarding a remote object or to
request actions to be performed
by that same object. Authorized parties would send requests to the Central
Processing Station. These
requests would be validated and forwarded on to the remote objects.
Brief Description of the Drawings
Figure 1: A diagram of the e-mail monitoring and control system - a generic
system overview.
Figure 2: Wireless e-mail for Automobile Telemetry and Control - an overview
of a system specifically for
monitoring and controlling motor vehicles.
Figure 3: In-car unit for Automobile Telemetry and Control - a diagram of the
modules and connections
within the car.
CA 02302999 2000-03-23
Figure 4: Central Processing Station for Automobile Telemetry and Control -
flow diagram of the Central
Processing Station of an automobile monitoring and control system.
Figure 5: Using Digital E-Mail Paging as a 2-way Digital Radio - a block
diagram illustrating how a digital
e-mail pager based system can be utilized for 2-way audio communications.
Figure 6: Some sample e-mail messages sent and received by in-car telemetry
devices to illustrate how data
and requests are formatted.
Detailed Description of the preferred embodiments
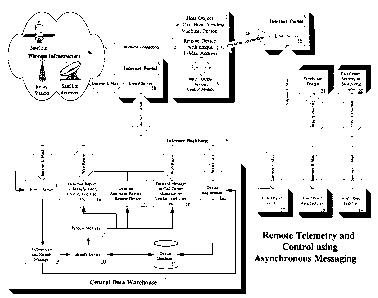
With reference to Figure 1, an apparatus labeled 2 is coupled would a host
object 1 such as a car, or a
vending-machine. This apparatus would be programmed with a unique e-mail
address, such that every host
object could be uniquely identified. Any number of sensors 3 could be
connected to the apparatus, such as
GPS receivers, wireless location units, automobile data ports, anti-theft
sensors and control units, LCD
display panels, touch screens, keypads, joysticks, I/O ports, and audio
compressors/decompressors. The
apparatus would be capable of composing an e-mail message to be sent to the
Central Processing Station 7,
containing data gathered from the input sensors. The apparatus would have a
logic circuit programmed to
determine which events would trigger a message to be sent. This logic circuit
would also embed an
authentication code into every e-mail message and possibly encrypt the message
if required. The e-mail
message would be communicated via a wireless connection 4, such as an e-mail
pager, or a physical
connection 4b, such as a telephone line and a modem. The wireless connection
would utilize a wireless e-
mail infrastructure consisting of land-based transceivers, relay stations,
and/or satellites 4c. As is required
by all Internet communications, the physical and the wireless connection would
be routed through an
Internet portal 5 at which an e-mail server would be situated 5b. The Internet
portal would have one or
more connections to the Internet backbone 6. The e-mail message from the host
object would ultimately be
forwarded to one or more e-mail servers 8 which are part of the Central
Processing Station. An automated
process would be initiated whereby each message would be authenticated 9 as
being one sent by a valid
device. The procedure would then identify the type of message as being one of
any number of predefined
standard messages to be sent from a remote host object. Next, the host object
would be identified 10 by
looking up a device database 11 and comparing the e-mail address of the sender
(which is contained within
the message) with that registered in the database. Finally, the message is
processed 13 by an application
that selects a task based on the message type. These tasks may be: Generate a
report to a manufacturer,
vendor, end-user or other authorized party 14; Generate an automatic reply to
the remote host device 15;
Forward the message to a call center, manufacturer, vendor, end-user, or other
authorized party 16.
Generated reports and forwarded messages could then be e-mailed to the vendor
of the host object 17, the
manufacturer 18, the end-user 19, or a call center 20. Using the Internet,
these parties could also access the
reports or notifications via a web site, provided proper measures are taken to
prevent unauthorized access.
When a host device is manufactured or sold, it would be registered through a
device registration web page
12, so that the device and its e-mail address are added to the device database
11.
When a vendor, manufacturer, end-user or call center desires a specific action
to be performed by a
remote object, they would make a request of the Central Processing Station 7,
through an e-mail, web-page
or custom Internet application. This would result in a message being sent to
the e-mail server 8, which
would be authenticated and identified 9. The device to be controlled would
also be determined 10 and its e-
mail address would be used when the message is processed 13 to generate a new
e-mail 15 to be sent to the
desired device. This new e-mail would go through the Internet to the portal
and through the physical or
wireless connection to the e-mail apparatus 2 on the host device. The logic
circuit within the apparatus
would authenticate and identify the message, and process it, sending a signal
to the appropriate control
module 3 or output device. In this manner, a device could be made to start or
stop transmitting location
data, lock or unlock doors, activate or deactivate itself, or perform other
functions.
Using the same system, a third party such as family and friends of the host
device operator 21 could
request a message to be sent to the operator of the remote object, and
messages generated by the operator of
the device could be forwarded to other parties.
CA 02302999 2000-03-23
Figure 2 illustrates a system designed for monitoring and controlling
automobiles. A Central
Processing Station 1 communicates with automobiles 2 using a wireless e-mail
system 3 such as wireless e-
mail paging. The automobile 4 sends and receives wireless e-mails 5, which is
made possible by a wireless
e-mail pager 6 with a unique e-mail address. Circuitry 7 connected to the
paging subsystem processes
incoming e-mails and generates outgoing ones. Incoming e-mails instruct the
circuitry to generate signals to
data switches 8 which cause the car to unlock doors, disable the fuel pump, or
perform other actions.
Outgoing messages are triggered by and contain information provided by data
sensors 9 connected to the
car's various systems. The e-mails are transmitted by the pager to the e-mail
paging infrastructure 10 which
consist of a network of repeater stations connected to the Internet 11. The e-
mails ultimately arrive at the
Central Processing Station 12 which processes the incoming messages and
replies as necessary.
Figure 3 details the proposed device within an automobile. A standard e-mail
pager consists of items 1
through 5. An e-mail paging chipset 2 is utilized to send and receive wireless
e-mails. Incoming e-mail 3 is
displayed on a LCD panel which is part of the pager user interface 5. Outgoing
e-mail 4 is entered via
buttons on the pager user interface and sent via the pager chipset. In the
proposed device, the pager user
interface is optional. Incoming e-mails are redirected to a circuit which
authenticates the message 6 to
determine if it is a valid e-mail sent from the Central Processing Station. If
the e-mail fails this test, it is
deleted, otherwise, additional circuitry processes the message 7. Depending on
the message from the
Central Processing Station, the circuitry could be triggered to display the
message text on an LCD display
situated in a dash mounted user interface module 8, or cause the vehicle to
unlock the doors, disable the
starter or fuel pump, or perform other functions. Other systems present within
the vehicle 9 can be
connected to the e-mail processing circuitry - for example, the airbag
deployment sensor or the OBD-2
data port. The airbag deployment sensor would trigger the circuitry to
transmit an emergency message to
the Central Processing Station. The OBD-2 data port provides performance data
and a GPS receiver 10
provides the location data that can be sent in an e-mail. The user interface
module could include a button to
trigger a road-side assistance request message, and another to generate an
emergency message. This would
provide the operator of the vehicle with a quick, easy method for requesting
assistance. Other buttons and
controls could be included to enable the operator to generate custom e-mails
to be sent to a third party via
the Central Processing Station.
Central Processing Station processing flow for an automobile telemetry and
control system is
diagramed in Figure 4. An e-mail server 2 receives messages from the in-car
device 1. A process 3
authenticates the validity of the message and identifies the type of message
received. Next the identity of
the vehicle sending the message is determined 4 by looking up the unique e-
mail address of the sender
(which is contained in the e-mail) in a device database 5. This database
registers the unique-email address
assigned to the in-car device with the serial number and specifications of the
vehicle - details which are
registered by the manufacturer 6 when the automobile assembly has been
completed. When a dealer sells a
vehicle, the contact information of the purchaser can be registered in the
database as well 7. After
identifying the message type and the vehicle, the message is processed 8 and
the appropriate task is
triggered. If a 'service interval reached' message was received, it could be
included in a report of clients
requiring regular servicing, which could be e-mailed to the local dealer 9.
This would enable a dealer to
contact a client and inform him/her, for instance, that the vehicle has
reached 100,000km and recommend
that they come in for a timing belt change. If a 'telemetry data' message is
received, the data would be
compiled into a report and forwarded to the manufacturer 10. Automatic
confirmations 11 could be sent to
the vehicle upon receipt of a message. A 911 or roadside assistance request
message would generate an
alert to be sent to an attendant at a call center 12, who would then
communicate via e-mail (which could
contain voice messages - see Figure 5) with the driver of the vehicle 13. It
is worth noting that this same
system would authenticate and process messages sent by manufacturers, owners,
and call-centers to be
forwarded to a vehicle. For instance, an owner could request that a vehicle be
unlocked - he could do this
by dialing a phone number of a voice menu operated system, enter in an
appropriate password, id and
command code. This system would generate an e-mail to be sent to the Central
Processing Station. The
message would be verified and an automatic message would be generated and sent
to the vehicle requesting
that a door be unlocked.
Figure 5 details a process for transmitting and receiving voice messages using
e-mail paging. In the
example of an automobile system, a microphone 1 would be installed on the
dash. Some event (a button,
CA 02302999 2000-03-23
voice recognition, or other) would trigger the recording of a message. This
audio signal would be converted
to a digital signal and compressed 2. It would then be segmented 3 into data
blocks of a maximum size
determined by the e-mail system - ie. a e-mail pager may restrict message
length to 2000 bytes. Next e-
mails would be generated, one for each data block, with a header to identify
that this is block #1, block #2,
etc. These e-mails would then be transmitted by the in-car device 4 to the
Central Processing Station 5,
which would receive these messages and determine if the messages are to be
forwarded on to a call-station,
another vehicle or some other third party. If the target is not another
vehicle, the segmented audio messages
would be combined into one and forwarded. If the target is another vehicle,
the segmented messages would
be forwarded untouched. If a call center or third party were to send an audio
message to a vehicle, these
would have to be compressed and segmented before forwarding to a vehicle. When
the in-car device
receives 6 these segmented messages, it would recombine 7, decompress and
decode 8 them. They would
then be played back over a speaker 9 mounted in the vehicle.
iF~gure 6 illustrates the composition of some sample e-mail messages sent and
received by the in-car
devices. The first e-mail 1 is a message sent from the in-car device to a
Central Processing Station. In this
example, the address of the in-car device is 91293294332Ca?paQer.com. The
address of the server is
serverCa?autoserver.com. The subject line identifies the type of message,
which in this case is
ServiceInterval. This message is generated at a predetermined odometer
interval and contains the odometer
reading and vehicle sensor data within the body of the message. A line
containing the authentication code is
also included in the message. This authentication code would vary with each
message and would be based
on a complex verification algorithm. This message is shown with english
keywords for ease of
understanding but that may not be the case in actual practice. The message
could also be encrypted to
reduce the chance of fraudulent messages. E-mail 2 shows a service fault
message, which would be
generated if the in-car device detects abnormal values in the vehicle sensor
data. E-mail 3 is a sample of a
vehicle location message, containing the present coordinates of the vehicle.
Messages 4 to 6 illustrate one
single audio message - 4 is the first e-mail of audio message 01223 (01223 is
to identify this particular
audio message as opposed to one which could be sent moments later). The '-1'
in the subject line indicates
this is the first of a number of e-mails. Message 5 is the second e-mail of
audio message 01223 and
message 6 is the last e-mail. Each of these messages would contain a segment
of the compressed audio file
within the message body. A 'Forward=' line is included to show that this
message was intended to be sent
to a third party - the Central Processing Station would receive these
messages, reconstitute them and
forward it on to myfriendCc~email.com. E-mails 7 to 9 illustrate instructions
from the Central Processing
Station. Message 7 is an instruction for the in-car device identified as
91293294332Ccana er.com to start
transmitting location data. Message 8 instructs the vehicle to stop
transmitting location data and message 9
causes the vehicle to unlock its doors.
Figures 2 to 6 illustrate a preferred system, whereby the messaging apparatus
is installed in an
automobile. Other implementations could involve the messaging apparatus being
installed and connected to
systems within boats, motorcycles or airplanes. The messaging apparatus could
also be installed in
premises such as homes, warehouses and other buildings. Motion sensors,
contact switches and other
sensors could be physically wired or connected via a wireless network to the
apparatus, providing the
telemetry data that could be transmitted to the Central Data Warehouse. A
proximity sensor attached to a
messaging device could be mounted in a bracelet, to enable remote monitoring
of a child, pet, or individual
under house arrest or in a secured area. A GPS unit coupled with the messaging
unit could assist in the
tracking of animals under scientific study. A satellite television receiver
coupled with the messaging device
would allow a program provider to disable units when programming dues have
lapsed, upgrade system
software when these become available, and identify units with fraudulent
enabling codes. These are just
some examples of alternative embodiments of the present invention. There could
be a single Central
Processing Station to service all the embodiments, or multiple stations could
exist, each one serving one or
more embodiments of this invention.
While the present invention has been described and illustrated in various
preferred and alternative
embodiments, such descriptions are merely illustrative of the present
invention and are not to be construed
to be limitations thereof. In this regard, the present invention encompasses
any and all embodiments with
the scope of the present invention being limited only by the claims which
follow.