Note: Descriptions are shown in the official language in which they were submitted.
CA 02318658 2000-09-12
1
INTERFERENCE SUPPRESSION IN CDMA SYSTEMS
DESCRIPTION
TECHNICAL FIELD:
The invention relates to Code-Division Multiple Access (CDMA) communications
systems, which may be terrestrial or satellite systems, and in particular to
interference
suppression in CDMA communications systems.
BACKGROUND ART:
Code-Division Multiple Access communications systems are well known. For a
general discussion of such systems, the reader is directed to a paper entitled
"Multiuser
Detection for CDMA Systems" by Duel-Hallen, Holtzman and Zvonar, IEEE Personal
Communications, pp. 46-58, April 1995.
In CDMA systems, the signals from different users all use the same bandwidth,
so each user's signal constitutes noise or interference for the other users.
On the uplink
(transmissions from the mobiles) the interference is mainly that from other
transmitting
mobiles. Power control attempts to maintain the received powers at values that
balance
the interference observed by the various mobiles, but, in many cases, cannot
deal
satisfactorily with excessive interference. Where mobiles with different
transmission
rates are supported within the same cells, the high-rate mobiles manifest
strong
interference to the low-rate mobiles. On the downlink (transmission towards
the
mobiles) transmissions from base-stations of other cells as well as strong
interference
from the same base-station to other mobiles may result in strong interference
to the
intended signal. Downlink power control may be imprecise or absent altogether.
In all
these so called near-far problem cases, the transmission quality can be
improved, or the
transmitted power reduced, by reducing the interference. In turn, for the same
transmission quality, the number of calls supported within the cell may be
increased,
resulting in improved spectrum utilization.
Power control is presently used to minimize the near-far problem, but with
limited success. It requires a large number of power control updates,
typically 800 times
per second, to reduce the power mismatch between the lower-rate and higher-
rate users.
It is desirable to reduce the number of communications involved in such power
control
systems, since they constitute overhead and reduce overall transmission
efficiencies.
Nevertheless, it is expected that future CDMA applications will require even
tighter
CA 02318658 2000-09-12
2
power control with twice the number of updates, yet the near-far problem will
not be
completely eliminated. It is preferable to improve the interference
suppression without
increasing the number of transmissions by the power control system.
Multiuser detectors achieve interference suppression to provide potential
benefits
to CDMA systems such as improvement in capacity and reduced precision
requirements
for power control. However, none of these detectors is cost-effective to build
with
significant enough performance advantage over present day systems. For
example, the
complexity of the optimal maximum likelihood sequence detector (MLSD) is
exponential
in the number of interfering signals to be cancelled, which makes its
implementation
excessively complex. Alternative suboptimal detectors fall into two groups:
linear and
subtractive. The linear detectors include decorrelators, as disclosed by K.S.
Schneider,
"Optimum detection of code division multiplexed signals", IEEE Trans. on
Aerospace
and Electronic Systems, vol. 15, pp. 181-185, January 1979 and R. Kohno, M.
Hatori,
and H. Imai, "Cancellation techniques of co-channel interference in
asynchronous spread
spectrum multiple access systems", Electronics and Communications in Japan,
vol.
66-A, no. 5, pp. 20-29, 1983. A disadvantage of such decorrelators is that
they cause
noise enhancement.
Z. Xie, R.T. Short, and C.K. Rushforth, "A family of suboptimum detectors for
coherent multiuser communications", IEEE Journal on Selected Areas in
Communications, vol. 8, no. 4, pp. 683-690, May 1990, disclosed the minimum
mean
square error linear (MMSE) detector, but such detectors are sensitive to
channel and
power estimation errors. In both cases, the processing burden still appears to
present
implementation difficulties.
Subtractive interference cancellation detectors take the form of successive
interference cancellers (SIC), as disclosed by R. Kohno et al.,"Combination of
an
adaptive array antenna and a canceller of interference for direct-sequence
spread-spectrum multiple-access system", IEEE Journal on Selected Areas in
Communications, vol. 8, no. 4, pp. 675-682, May 1990, and parallel
interference
cancellers (PIC) as disclosed by M.K. Varanasi and B. Aazhang, "Multistage
detection
in asynchronous code-division multiple-access communications", IEEE Trans. on
Communications, vol. 38, no. 4, pp. 509-519, April 1990, and R. Kohno et al.,
"Combination of an adaptive array antenna and a canceller of interference for
direct-sequence spread-spectrum multiple-access system", IEEE Journal on
Selected
CA 02318658 2000-09-12
3
Areas in Communications, vol. 8, no. 4, pp. 675-682, May 1990. Both SIC
detectors
and PIC detectors require multi-stage processing and the interference
cancellation
achieved is limited by the amount of delay or complexity tolerated. These
detectors are
also very sensitive to channel, power and data estimation errors.
One particular subtractive technique was disclosed by Shimon Moshavi in a
paper
entitled "Multi-User Detection for DS-CDMA Communications", IEEE
Communications
Magazine, pp. 124-136, October 1996. Figure 5 of Moshavi's paper shows a
subtractive
interference cancellation (SIC) scheme in which the signal for a particular
user is
extracted in the usual way using a matched filter and then spread again using
the same
spreading code for that particular user, i. e. , the spreading code used to
encode the signal
at the remote transmitter. The spread-again signal then is subtracted from the
signal
received from the antenna and the resulting signal is applied to the next
user's
despreader. This process is repeated for each successive despreader. Moshavi
discloses
a parallel version that uses similar principles.
A disadvantage of this approach is its sensitivity to the data and power
estimates,
i. e., their accuracy and the sign of the data. A wrong decision will result
in the
interference component being added rather than subtracted, which will have
totally the
wrong effect.
For more information about these techniques, the reader is directed to a paper
by
P. Patel and J. Holtzman entitled "Analysis of a Simple Successive
Interference
Cancellation Scheme in a DS/CDMA System", IEEE Journal on Selected Areas in
Communications, Vol. 12, No. 5, pp. 796-807, June 1994.
In a paper entitled "A New Receiver Structure for Asynchronous CDMA: STAR -
The Spatio-Temporal Array-Receiver", IEEE Transaction on Selected Areas in
Communications, Vol. 16, No. 8, October 1998, S. Affes and P. Mermelstein (two
of
the present inventors), disclosed a technique for improving reception despite
near/far
effects and multi-user interference. In contrast to known systems in which the
spread-
again signal is supplied to the input of the despreader of the channel to be
corrected,
Affes' and Mermelstein's proposed system treated all of the users' signals
together and
processed them as a combined noise signal. If the components of the received
signal
from the different users were uncorrelated and all had equal power, or
substantially equal
power, this process would be optimal. In practice, however, there will be
significant
differences between the power levels at which the different users' signals are
received
CA 02318658 2000-09-12
4
at the base station antenna. The same applies to the downlink. For example, a
data user
may generate much more power than a voice user simply because of the more
dense
information content of the data signal. Also, imperfect power control will
result in
power differences, i. e. , channel variations may result in received powers
different from
their intended values, despite the best effort of the power-control process to
equalize
them.
DISCLOSURE OF INVENTION:
The present invention addresses the need for improved interference suppression
without the number of transmissions by the power control system being
increased, and,
to this end, provides a receiver for a CDMA communications system which
employs
interference subspace rejection to obtain a substantially unity response for a
propagation
channel via which a corresponding user's signal was received and a
substantially null
response to interference components from selected signals of other user
stations.
According to one aspect of the invention, there is provided a receiver
suitable for
either a base station or a user station of a CDMA communications system
comprising at
least one base station (11) and a plurality of user stations (10'...10') each
communicating
with said at least one base station via a corresponding one of a plurality of
channels, said
base station and each user station having a transmitter and a said receiver,
the receiver
receiving a signal comprising components corresponding to signals from the
different
transmitters of the base station and/or user stations. The receiver comprises
processing
means (18) for deriving an observation matrix from the received signal, the
receiver
comprising a plurality of receiver modules (21) each comprising means (19) for
deriving
from the observation matrix one or both of a corresponding observation vector
and post-
correlation observation vector and a beamformer for processing one or other of
the
observation vector and the post-correlation observation vector to provide
estimates of
symbols transmitted by a corresponding user station, and means (42,43) for
providing
at least one constraint matrix representing interference subspace of
components of the
received signal corresponding to selected ones of the user signals of the
plurality of
receiver modules, at least one (2l``) of said plurality of receiver modules
having means
(28d) responsive to at least the post-correlation observation vector for
deriving an
estimate of the channel parameters for the channel between the receiver and
the
corresponding transmitter, and a beamformer (47a) for processing one or other
of the
CA 02318658 2000-09-12
observation vector and the post-correlation observation vector to produce
estimates of the
symbols transmitted by said transmitter, the beamformer having means for
adjusting
coefficients of the beamformer in dependence upon the constraint matrix and
the channel
estimate so as to tune the beamformer to provide a substantially unity
response for that
5 portion of the received signal from the corresponding transmitter and a
substantially null
response to that portion of the received signal corresponding to predetermined
ones of
other user signals and/or base station signals also received by the receiver.
According to the present invention, there is provided a receiver for either a
base
station (or a mobile station) of a CDMA communications system in which a
plurality of
user stations (10'...10 ) each having an antenna array comprising one or more
antennas
communicate with a base station (11) having an antenna array (12) comprising
one or
more reception antennas (12'...12M), each of the user stations having
spreading means
(13'...13") for using a spreading code (c'(t)...c"(t)) unique to that station
to spread a
corresponding one of a plurality of user signals (bin...b R) and means for
transmitting
the spread user signals to the base station antenna array (12) via a
propagation channel
(14'...14") unique to that user station,
the receiver comprising preprocessing means (18) and a plurality of receiver
modules (21'. ..21 U) having their respective inputs connected in common to an
output of
the preprocessing means (18) and each corresponding to a respective one of the
user
stations,
the preprocessing means (18) being arranged to receive from the antenna array
an antenna array signal vector (X(t)) comprising a plurality of spread data
vectors (X1(t) ... X U(t)) corresponding to the signals from the different
user stations
received by the reception antenna array and having means for filtering,
sampling and
buffering the antenna array signal vector (X(t)) to produce a succession of
observation
matrices (Yõ), and supplying the observation matrices (Yd to each of the
receiver
modules (21'...21");
...21 ) comprising a despreader (19 ), a channel
each of the receiver modules (211
identification means (28 ), a beamformer (27 ) and output means (29 ,30 ),
the despreader (19 ) being arranged to despread each observation matrix using
the
spreading code of the corresponding user to form a post-correlation
observation
vector (Zu) and the channel identification means (28 ) being arranged to
derive from the
n
post-correlation observation vector a set of estimated channel parameters (H")
for the
n
CA 02318658 2000-09-12
6
channel whereby the signal from the corresponding user station reached the
antenna
array,
the beamformer (27 ) having means (51) for weighting each of the elements of
each observation vector in turn using weighting coefficients (Wn), tuning
means (50)
n
for adjusting the weighting coefficients (yyu) in dependence upon at least
said estimated
n
channel parameters, and means (52) for combining the weighted elements to
produce a
respective symbol of a corresponding one of a plurality of output
signals (bn .., bn ) corresponding to the plurality of user signals (bn .., bn
), respectively,
the receiver further comprising constraints-set generation means (42)
responsive
to a set of channel parameter estimates and either or both of an actual value
of the
symbol from at least one of the beamformers and at least one hypothetical
symbol value
for deriving a constraints-set, and
constraint matrix generation means (43) responsive to said constraints-set for
forming at least one constraint matrix and corresponding inverse matrix;
the respective tuning means of at least some of the beamformers being
responsive
to said at least one constraint matrix to adjust the weighting coefficients
(Wd) of their
n
respective beamformers such that, in successive symbol periods, the
coefficients of each
of said at least some of the beamformers are adjusted so as to tune a
substantially unity
response for that portion of the antenna array signal vector corresponding to
the user
signal from the corresponding user station and a substantially null response
to that
portion of the antenna array signal vector corresponding to the user signals
received from
those user stations corresponding to the receiver modules which contribute a
constraint
waveform to the constraint matrix generation means;
the output means of each receiver module being responsive to the output of the
corresponding beamformer for providing estimates of the symbols of the
corresponding
user signal.
Embodiments of the invention may employ one of several alternative modes of
implementing interference subspace rejection (ISR), i.e. characterizing the
interference
and building the constraint matrix. In a first embodiment, using a first mode
conveniently designated ISR-TR, each receiver module in the first group
generates its
re-spread signal taking into account the amplitude and sign of the symbol and
the channel
characteristics. The re-spread signals from all of the receiver modules of the
first group
CA 02318658 2000-09-12
7
are summed to produce a total realization which is supplied to all of the
receiver modules
in the second group.
Where each receiver module of the second set uses decision feedback, it
further
comprises delay means for delaying each frame/block of the observation vector
before
its application to the beamformer.
Whereas, in ISR-TR embodiments, just one null constraint is dedicated to the
sum, in a second embodiment, which uses a second mode conveniently designated
ISR-R, estimated realisations of all the interferers are used, and a null
constraint is
dedicated to each interference vector. In this second embodiment, in each
receiver
module of the first set, the symbols spread by the spreader comprise estimated
realisations of the symbols of the output signal. Also, the constraint
waveforms are not
summed before forming the constraint matrix. Thus, the receiver module
estimates
separately the contribution to the interference from each unwanted
(interfering) user and
cancels it by a dedicated null-constraint in the multi-source spatio-temporal
beamformer.
In most cases, estimation of the interference requires estimates of the past,
present and
future data symbols transmitted from the interferers, in which case the
receiver requires
a maximum delay of one symbol and one processing cycle for the lower-rate or
low-
power users and, at most a single null constraint per interferer.
In a third embodiment of the invention which uses a third mode conveniently
designated ISR-D, i.e. the observation vector/matrix is decomposed over sub-
channels/fingers of propagation path and the beamformer nulls interference in
each of
the sub-channels, one at a time. In most cases, the maximum number of
constraints per
interferer is equal to the number of sub-channels, i.e. the number of antenna
elements
M multipled by the number of paths P.
In a fourth embodiment using a fourth mode conveniently designated ISR-H
because it implements null-responses in beamforming over all possible
realisations of the
interference, without any delay, each receiver module of the first group
further
comprises means for supplying to the spreader possible values of the instant
symbols of
the output signal and the spreader supplies a corresponding plurality of re-
spread signals
to each of the receiver modules of the second group. In each receiver module
of the
second group, the despreader despreads the plurality of re-spread signals and
supplies
corresponding despread vectors to the beamformer. This embodiment suppresses
any
CA 02318658 2000-09-12
8
sensitivity to data estimation errors and, in most cases, requires a maximum
of 3 null
constraints per interferer.
In a fifth embodiment using a fifth mode conveniently designated ISR-RH
because
it uses the past and present interference symbol estimates, in each receiver
module of the
first group, the spreader spreads the symbols of the output signal itself and,
in each
receiver module of the second group, the beamformer then implements null-
responses
over reduced possibilities/hypotheses of the interference realization.
Conveniently,
application of the output of the first despreader to the beamformer will take
into account
the time required for estimation of the interferer's symbol. In most cases,
the
beamformer will provide a maximum of 2 null constraints per interferer.
In any of the foregoing embodiments of the invention, the channel
identification
unit may generate the set of channel parameter estimates in dependence upon
the
extracted despread data vectors and the user signal component estimate.
For each of the above-identified modes, the receiver modules may employ either
of two procedures. On the one hand, the receiver module may apply the post-
correlation
observation vector to the channel identification unit but supply the
observation matrix
itself directly to the beamformer, i.e. without despreading it. The constraint
matrix then
would be supplied to the beamformer without despreading.
Alternatively, each receiver module could supply the post-correlation
observation
vector to both the channel identification unit and the beamformer. In this
case, the
receiver module would also despread the constraint matrix before applying it
to the
beamformer.
Where the reception antenna comprises a plurality of antenna elements, the
beamformer unit may comprise a spatio-temporal processor, such as a filter
which has
coefficients tuned by the estimated interference signals.
The receiver modules may comprise a first set that are capable of contributing
a
constraint waveform to the constraint matrix and a second set that have a
beamformer
capable of using the constraint matrix to tune the specified null response and
unity
response. In preferred embodiments, at least some of the plurality of receiver
modules
are members of both the first set and the second set, i.e. they each have
means for
contributing a constraint waveform and a beamformer capable of using the
constraint
matrix.
CA 02318658 2000-09-12
9
In practice, the receiver modules assigned to the stronger user signals will
usually
contribute a constraint waveform and the beamformer units of the receiver
modules
assigned to other user signals will be capable of using it.
The receiver module may comprise an MRC beamformer and an ISR beamformer
and be adapted to operate in multi-stage, i.e., for each symbol period of
frame, it will
carry out a plurality of iterations. In the first iteration, the constraints
set generator will
receive the "past" and "future" estimates from the MRC beamformer and the
"past"
symbol estimate, i.e., from the previous frame, and process them to produce a
new
symbol estimate for the first iteration. In subsequent iterations of the
current symbol
period or frame, the constraints-set generator will use the "future" estimate
from the
MRC beamformer, the previous estimate from the ISR beamformer and the symbol
estimate generated in the previous iteration. The cycle will repeat until the
total number
of iterations have been performed, whereupon the output from the receiver
module is the
desired estimated symbol for the current frame which then is used in the
similar
iterations of the next frame.
The ISR receiver module comprising both an MRC beamformer and an ISR
beamformer may comprise means {lO1Qd} for extracting from the ISR beamformer
(47Qd) an interference-reduced observation vector and reshaping the latter to
produce an
interference-reduced observation matrix for despreading by the despreader. The
channel
identification unit then uses the despread interference-reduced observation
vector to form
interference-reduced channel estimates and supplies them to the residual MRC
beamformer for use in adapting the coefficients thereof.
The ISR beamformer may process blocks or frames of the observation vector that
are extended by concatenating a current set of data with one or more previous
frames or
blocks of data.
The different receiver modules may use different sizes of frame.
In order to receive signals from a user transmitting multicode signals, the
ISR
receiver module may comprise a plurality of ISR beamformers and despreaders,
each for
operating upon a corresponding one of the multiple codes. The channel
identification
unit then will produce a channel parameter estimate common to all of the
multicodes,
spread that channel estimate with each of the different multicodes and supply
the
resulting plurality of spread channel estimates to respective ones of the
plurality of ISR
beamformers.
CA 02318658 2000-09-12
The multicode ISR receiver module may have a despreader (19d a) which uses a
compound code comprising each of the multicodes weighted by the corresponding
symbol
estimate from a respective one of a corresponding plurality of decision-rule
units. The
despreader will uses the compound code to despread the observation matrix and
supply
5 the corresponding compound post-correlation observation vector to the
channel
identification unit. The channel identification unit will use that vector to
produce the
channel estimate and spread it using the different ones of the multicodes to
produce the
spread channel estimates.
The ISR receiver module may comprise a despreader 19Sd,', ..., I9Sd F using
10 a plurality of codes which comprise segments of a main code specified for
that user.
Each segment corresponds to a symbol, and to a symbol duration in a large
block of
data, the number of segments being determined by the data rate, i.e., number
of symbols
within a block, of that user. Each receiver module may have a different number
of
segments assigned thereto according to the data rate of the corresponding
user.
Embodiments of the invention may be adapted for use in a user/mobile station
capable of receiving user-bound signals transmitted by a plurality of base
stations each
to a corresponding plurality of users, the receiver then comprising a
selection of receiver
modules each corresponding to a different base station and configured to
extract a
preselected number of said user-bound signals. Where the particular
user/mobile station
is included in the preselected number, the receiver module may comprise a
similar
structure to the above-mentioned multicode receiver, the plurality of
despreaders being
adapted to despread the observation matrix using respective ones of a set of
codes
determined as follows: (1) a pre-selected number NB of base stations from
which the
mobile receives signals and which have been selected for cancellation -
represented by
index v' which ranges from 1 to NB; (2) a preselected number (1 to NI) of
interferers
per base station preselected for cancellation; (3) the data rates of the
selected interferers.
Where the signal destined for the particular user/mobile station is not one of
the
preselected number of signals from the corresponding base station, the
receiver may
further comprise an ISR receiver module which has means for updating the ISR
beamformer coefficients using the channel estimates from at least some of the
receiver
modules that have generated such channel estimates for the preselected signals
for the
same base station.
CA 02318658 2000-09-12
11
Where the rates of the different users are not known to the instant mobile
station,
the codes may comprise a fixed number of segments Nm which is predetermined as
a
maximum data rate to be received. Any slower rates will effectively be
oversampled for
processing at the higher rate.
The complexity of the multicode embodiments may be reduced by reducing the
number of codes that are used by the despreaders. In particular, the bank of
despreaders
may use a set of codes that represent summation of the codes of the different
NI
interferers, to form a compound code which reduces the total number of codes
being
used in the despreaders.
According to another aspect of the invention, there is provided a STAR
receiver
comprising an MRC beamformer which operates upon an observation vector which
has
not been despread.
Of course, that does not preclude having all channels feed their interference
components to all other channels.
The foregoing and other objects, features, aspects and advantages of the
present
invention will become more apparent from the following detailed description,
in
conjunction with the accompanying drawings, of preferred embodiments of the
invention.
BRIEF DESCRIPTION OF THE DRAWINGS:
Figure 1 is a schematic diagram illustrating a portion of a CDMA
communications system comprising a plurality of user stations, typically
mobile, and a
base station having a reception antenna comprising an array of antenna
elements, and
illustrating multipath communication between one of the user stations and the
array of
antennas;
Figure 2 is a simplified schematic diagram representing a model of the part of
the
system illustrated in Figure 1;
Figure 3 is a detail block diagram of a spreader portion of one of the user
stations;
Figures 4(a) and 4(b) illustrate the relationship between channel
characteristics,
power control and signal power;
Figure 5 is a simplified block schematic diagram of a base station receiver
according to the prior art;
Figure 6 is a detail block diagram of a preprocessing unit of the receiver;
CA 02318658 2000-09-12
12
Figure 7 is a detail block diagram of a despreader of the receiver;
Figure 8 illustrates several sets of users in a CDMA system ranked according
to
data rate;
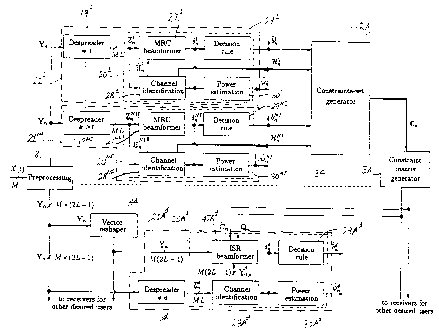
Figure 9 is a detail block diagram showing several modules of a receiver
embodying the present invention, including one having a beamformer operating
on data
that has not been despread;
Figure 10 is a detail schematic diagram showing a common matrix generator and
one of a plurality of beamformers coupled in common thereto;
Figure 11 is a block diagram corresponding to Figure 9 but including a module
having a beamformer operating upon data which has first been despread;
Figure 12 is a schematic diagram of a user-specific matrix generator and an
associated beamformer of one of the receiver modules of Figure 11;
Figure 13 is a detail block schematic diagram of a receiver using total
realisation
of the interference to be cancelled (ISR-TR) and without despreading of the
data
processed by the beamformer;
Figure 14 illustrates a respreader of one of the receiver modules of Figure
13;
Figure 15 is a detail block schematic diagram of a receiver using individual
realisations of the interference (ISR-R) and without despreading of the data
processed by
the beamformer;
Figure 16 is a simplified block diagram of a receiver which decomposes each
realisation of the interference over diversity paths (ISR-D) and without
despreading of
the data processed by the beamformer;
Figure 17 is a simplified schematic block diagram of a receiver employing
interference subspace rejection based upon hypothetical values of the symbols
(ISR-H)
and without despreading of the data processed by the beamformer;
Figure 18 illustrates all possible triplets for the hypothetical values;
Figure 19 illustrates bit sequences for generating the hypothetical values;
Figure 20 is a simplified schematic block diagram of a receiver employing
interference subspace rejection based upon both hypothetical values of the
symbols and
realisations (ISR-RH) and without despreading of the data processed by the
beamformer;
Figure 21 is a simplified schematic block diagram of a receiver similar to the
ISR-TR receiver shown in Figure 13 but in which the beamformer operates upon
the data
that has first been despread;
CA 02318658 2000-09-12
13
Figure 22 is a simplified schematic block diagram of a receiver similar to the
ISR-R receiver shown in Figure 15 but in which the beamformer operates upon
data that
has first been despread;
Figure 23 is a simplified schematic block diagram of a receiver similar to the
ISR-D receiver shown in Figure 16 but in which the beamformer operates upon
data that
has first been despread;
Figure 24 is a simplified schematic block diagram of a receiver similar to the
ISR-H receiver shown in Figure 18 but in which the beamformer operates upon
data that
has first been despread;
Figure 25 illustrates bit sequences generated in the receiver of Figure 24;
Figure 26 is a simplified schematic block diagram of a receiver similar to the
ISR-RH receiver shown in Figure 20 but in which the beamformer operates upon
data
that has first been despread;
Figure 27 illustrates an alternative STAR module which may be used in the
receiver of Figure 5 or in place of some of the receiver modules in the
receivers of
Figures 13-17, 20-24 and 26;
Figure 28 illustrates a receiver module which both contributes to the
constraint
matrix and uses the constraint matrix to cancel interference (JOINT-ISR);
Figure 29 illustrates a mulit-stage ISR receiver module;
Figure 30 illustrates successive implementaton of ISR;
Figure 31 illustrates a receiver module which uses ISR to enhance channel
identification;
Figure 32 illustrates extension of the frame size to reduce noise enhancement
and
facilitate asynchronous operation and processing of high data rates;
Figure 33 illustrates implementation of ISR with mixed spreading factors;
Figure 34 illustrates an uplink ISR receiver module for a user employing
multicode signals;
Figure 35 illustrates a modification of the receiver module of Figure 34;
Figure 36 illustrates how multirate can be modelled as multicode;
Figure 37 illustrates frame size determination for multirate signals;
Figure 38 illustrates grouping of multirate signals to correspond to a
specific
user's symbol rate;
Figure 39 illustrates an "uplink" multirate ISR receiver module for a base
station;
CA 02318658 2000-09-12
14
Figure 40 illustrates one of a plurality of "downlink" multirate receiver
modules
for a user station operating as a "virtual base station";
Figure 41 illustrates a "downlink" multirate receiver module of the user
station
of Figure 41 for extracting signals for that user station;
Figure 42 illustrates a multicode alternative to the receiver module of Figure
40;
and
Figure 43 illustrates a second alternative to the receiver module of figure
40.
BEST MODE(S) FOR CARRYING OUT THE INVENTION:
In the following description, identical or similar items in the different
Figures
have the same reference numerals, in some cases with a suffix.
The description refers to several published articles. For convenience, the
articles
are cited in full in a numbered list at the end of the description and cited
by that number
in the description itself. The contents of these articles are incorporated
herein by
reference and the reader is directed to them for reference.
Figures 1 and 2 illustrate the uplink of a typical asynchronous cellular CDMA
system wherein a plurality of mobile stations 10'...10U communicate with a
base-station
11 equipped with a receiving antenna comprising an array of several antenna
elements
12'...12'". For clarity of depiction, and to facilitate the following detailed
description,
Figures 1 and 2 illustrate only five of a large number (U) of mobile stations
and
corresponding propagation channels of the typical CDMA system, one for each of
a
corresponding plurality of users. It will be appreciated that the mobile
stations 10'...10"
will each comprise other circuitry for processing the user input signals, but,
for clarity
of depiction, only the spreaders are shown in Figure 2. The other circuitry
will be
known to those skilled in the art and need not be described here. Referring to
Figure
2, the mobile stations 10'...10" comprise spreaders 13'...13", respectively,
which spread
a plurality of digital signals gn ,,, bn of a corresponding plurality of
users, respectively,
all to the same bandwidth, using spreading codes cl (t). .. c"(t),
respectively. The mobile
stations 10'...10" transmit the resulting user signals to the base station I1
via channels
14'...14", respectively, using a suitable modulation scheme, such as
differential binary
phase shift keying (DBPSK). Each of the mobile stations 10'...10" receives
commands
CA 02318658 2000-09-12
from the base station 11 which monitors the total received power, i.e. the
product of
transmitted power and that user's code and attenuation for the associated
channel and
uses the information to apply power control to the corresponding signals to
compensate
for the attenuation of the channel. This is represented in Figure 2 by
multipliers
5 15'...15" which multiply the spread signals by adjustment factors ~` (t)...
0 "(t),
respectively. The array of M omni-directional antenna elements 12'...12M at
the base
station 11 each receive all of the spread signals in common. The channels
14'...14" have
different response characteristics H`(t)...Ht'(t), respectively, as
illustrated in more detail
in Figure 1, for only one of the channels, designated channel 14 . Hence,
channel 14
10 represents communication via as many as P paths between the single antenna
of the
associated mobile station l0i' and each of the base station antenna elements
12' ...12'".
The other channels are similarly multipath.
As before, it is presumed that the base station knows the spreading codes of
all
of the mobile stations with which it communicates. The mobile stations will
have
15 similar configurations so only one will be described. Thus, the mobile
station 10 first
differentially encodes its user's binary phase shift keyed (BPSK) bit sequence
at the rate
1/T, where T is the bit duration, using circuitry (not shown) that is well-
known to
persons skilled in this art. As illustrated in Figure 3, its spreader 13 then
spreads the
resulting differential binary phase shift keyed (DBPSK) sequence bn (or b"(t)
in the
continuous time domain as represented in Figure 3) by a periodic personal code
sequence
cl" (or c"(t) in the continuous time domain) at a rate 1/T,, where Tc is the
chip pulse
duration. The processing gain is given by L=T/T,. For convenience, it is
assumed that
short codes are used, with the period of c"(t) equal to the bit duration T,
though the
system could employ long codes, as will be discussed later, with other
applications and
assumptions. Over one period T, the spreading code can be written as:
L-1
c"(t) = E c1"O(t-lT,), (1)
1=0
where c," 1 for Z= 0, ..., L - 1, is a random sequence of length L and 0(t) is
the
chip pulse as illustrated in Figure 3. Also, with a multipath fading
environment with P
resolvable paths, the delay spread aT is small compared to the bit duration
(i.e. nT <<
T).
As illustrated in Figures 4(a) and 4(b), following signal weighting by the
poer
control factor ~pI(t)2, the spread signal is transmitted to the base station
11 via channel
CA 02318658 2000-09-12
16
14 . Figure 4(a) shows the "real" situation where the channel characteristics
comprise
a normalized value H"(T) and a normalization factor ~ch"(T) which relates to
the
"amplitude" or attenuation of the channel, i.e. its square would be
proportional to the
power divided by the transmitted power. In Figure 4(a), power control is
represented
by a multiplier 17 , and the subscript "pc ". Figure 4(b) shows that, for
convenience, the
channel characteristics can be represented (theoretically) by the normalized
value H(t)
and the normalization factor ~,h"(t) included in a single power factor V(t)
which is equal
to ~p,"(Wh"(t). >GP,"(t) is the factor by which the transmitted signal is
amplified or
attenuated to compensate for channel power gain in ~,hu(t) and to maintain the
received
power q"(t))2 at the required level.
In such a CDMA system, the signal of each of the mobile stations 10'...10"
constitutes interference for the signals of the other mobile stations. For
various reasons,
some of the mobile stations will generate more interference than others. The
components
of one of these "strongly interfering" user stations and its associated
channel are
identified in Figures 1 and 2 by the index "i" . The components of one of the
other
"low-power" user stations and its associated channel also are illustrated, and
identified
by the index "d". The significance of this grouping of "interfering" and "low-
power"
user stations will be explained later.
At the base station 11, the spread data vector signals X' (t). .. X"(t) from
the base
station antenna elements 12'...12'M, respectively, are received
simultaneously, as
indicated by the adder 16 (Figure 2), and the resulting observation vector
X(t) is supplied
to the receiver (see Figure 5). The sum of the spread data vectors (signals)
XI (t)...X"(t)
will be subject to thermal noise. This is illustrated by the addition of a
noise signal
component Nt,1(t) by adder 16. The noise signal N,,,(t) comprises a vector,
elements of
which correspond to the noise received by the different antenna elements.
Figure 5 illustrates a spatio-temporal array receiver (STAR) for receiving the
signal X(t) at the base station 11. Such a receiver was described generally by
two of the
present inventors in reference [13]. The receiver comprises a preprocessing
unit 18, a
plurality of despreaders 19'... 19", and a plurality of spatio-temporal
receiver (STAR)
units 20'...20", each having its input connected to the output of a respective
one of the
despreaders 19'... 19 . Each of the STAR units 20'...20" and the associated
one of the
despreaders 19'... 19" form part of a respective one of a plurality of
receiver modules
21'...21U. As shown in Figure 6, the preprocessing unit 18 comprises a matched
filter
CA 02318658 2000-09-12
17
22, a sampler 23 and a buffer 24. Matched filter 22 convolves the antenna
array signal
vector X(t), which is an M x 1 vector, with a matched pulse 4)(T, - t) to
produce the
matched filtered signal vector Y(t) which then is sampled by sampler 23 at the
chip rate
1/T,, element by element. The sampler 23 supplies the resulting M x 1 vectors
Yn,1, at
the chip rate, to buffer 24 which buffers them to produce an observation
matrix Yn of
dimension M x (2L-1). It should be noted that, although the present inventors'
Canadian patent application No. 2,293,097 and United States Provisional
application No.
60/ 171, 604 had a duplicate of this preprocessing unit 18 in each of the
despreaders
19' ...19", it is preferable to avoid such duplication and use a single
preprocessor 18 to
preprocess the received antenna array signal vector X(t).
The despreaders 19'...19" each have the same structure, so only one will be
described in detail with reference to Figure 7 which illustrates despreader 19
. Thus,
despreader 19 comprises a filter 25 and a vector reshaper 26". The
observation matrix
Yõ is filtered by filter 21 using the pseudo-random number sequence cL ,
corresponding
to that used in the spreader 13 of the transmitter, i.e. cl", to produce the
postcorrelation
observation matrix Zu for user u. Vector reshaper 26 concatenates the M x L
matrix Zu to form a post-correlation observation vector Zn of dimension ML x
1. It
n -n
should be noted that the vector reshaper 26 need not be a distinct physical
element but
is depicted as such to represent a mathematical function. In practice, the
function will
likely be determined merely by allocation of resources, such as memory.
Referring again to Figure 5, the post-correlation observation vectors Z1,..ZU
from
n n
despreaders 19' ...19 are processed by the STAR units 20' ... 20",
respectively, to
produce symbol estimates 6n...b corresponding to the transmitted
symbols bn ,.. gnU (see Figure 2) and power estimates (~a2,..n )z which are
supplied
to subsequent stages (not shown) of the receiver for processing in known
manner.
The STAR units 20'...20" each comprise the same elements, so the construction
and operation of only one of them, STAR unit 20", will now be described.
The STAR unit 20 comprises a beamformer 27 , a channel identification unit 28
,
a decision rule unit 29 and a power estimation unit 30 . The channel
identification unit
28 is connected to the input and output, respectively, of the beamformer 27
to receive
the post-correlation observation vector Zu and the signal component
n
estimate sn", respectively. The channel identification unit 28 replicates,
for each frame
M x L the characteristics H"(t), in space and time, of the associated user's
transmission
CA 02318658 2000-09-12
18
channel 14 . More specifically, it uses the signals Zu and Sn to derive a set
of
n
parameter estimates H", which it uses to update the weighting coefficients yyu
of the
rt n
beamformer 27 in succeeding symbol periods. The symbol period corresponds to
the
data fraine of M X L elements.
The beamformer 27 comprises a spatio-temporal maximum ratio combining
(MRC) filter which filters the space-time vector Zu to produce the despread
signal
n
component estimate sn , which it supplies to both the decision rule unit 29
and the
power estimation unit 30u. The decision-rule unit 29 outputs a binary
symbol bn" according to the sign of the signal component estimate sn . The
binary
output signal constitutes the output of the decision rule unit 30 and is an
estimate of the
corresponding user signal bn spread by spreader 13 of the corresponding user
station
10' (Figures 1 and 2).
The signal component estimate sn is processed in subsequent parts of the
receiver. For example, it may be differentially decoded and, possibly,
deinterleaved and
the data decoded--if the corresponding inverse operations were done before
transmission.
The power estimation unit 30 uses the raw signal component estimate Sn to
derive an estimate (ed2 of the power in that user's signal component sn of the
antenna
array signal vector X(t) and supplies the power estimate (ed2 to the
subsequent stages
(not shown) of the receiver for derivation of power level adjustment signals
in known
manner.
The receiver shown in Figure 5 will perform satisfactorily if there are no
strong
interferers, i.e., if it can be assumed that all users transmit with the same
modulation and
at the same rate, and that the base-station knows all the spreading codes of
the terminals
with which it is communicating. On that basis, operation of the receiver will
be
described with reference to the user channel identified by index u.
At time t, the antenna array signal vector X(t) received by the elements
12'...121
of the antenna array of the one particular cell shown in Figures 1 and 2 can
be written
as follows:
U
X(t) _ E X "(t) + N`h(t) (2)
u-1
where U is the total number of mobile stations whose signals are received at
the
base-station 11 from inside or outside the cell, Xu(t) is the received signal
vector from
the mobile station 10 , i. e. , of index u, and Nh(t) is the thermal noise
received at the M
CA 02318658 2000-09-12
19
antenna elements. The contribution X"(t) of the u-th mobile station 10 to the
observation
vector X(t) is given by:
X "(t) = q/"(t)H "(t) c u(t)b "(t)
! P / / ! (2a)
-~ult) E Gp lt) E plt) c u(t - T p(t)) b u(t -[ plt))
p=1
where H"(t) is the channel response vector of the channel 14 between the u-th
mobile
station 10 and the array of antenna elements and denotes time-convolution.
In the
right-hand term of the above equation, the propagation time-delays ,=P(t)
E[0,T] along
the P paths, p 1,==, P, (see Figure 1), are chip-asynchronous, Gp(t) are the
propagation vectors and Ep(t)2 are the fractions along each path
(i.e., Ep(t)Z = 1) of the total power ~i"(t)2 received from the u-th mobile
station
EPP-,
10 . The received power is affected by path-loss, Rayleigh fading and
shadowing. It
is assumed that GP (t) , EP(t)2 and ~u(t)2 vary slowly and are constant over
the bit
duration T.
In the preprocessing unit 18 (see Figure 6), the antenna array signal vector
X(t)
is filtered with the matched pulse to provide the matched-filtering signal
vector Yn(t) for
frame n as follows:
Yn(t) = 1 f X (aT/2 + nT + t + t ~) ~ (t ~) dt ' (3)
T, d
where D. denotes the temporal support of 0(t) and a E{ 0,1 } stands for a
possible
time-shift by T/2 to avoid, if necessary, the frame edges lying in the middle
of the delay
spread (see reference [13]). For the sake of simplicity, it is assumed in the
following
that a = 0. Note that for a rectangular pulse D. is [0, Tj. In practice, it is
the
temporal support of a truncated square-root raised- cosine.
It should be noted that the above description is baseband, without loss of
generality. Both the carrier frequency modulation and demodulation steps can
be
embedded in the chip pulse-shaping and matched-filtering operations of
Equations (1) and
(3), respectively.
Thus, after sampling at the chip rate 1/T, and framing over 2L - 1 chip
samples
at the bit rate to form a frame, the preprocessing unit 18 derives the M x (2L
-1)
matched-filtering observation matrix: 4)[Y 0 Y i..., Y,2c,-2]1
CA 02318658 2000-09-12
where
Y ~ = Y (lT ).
In the despreader 19 (see Figure 7), the post-correlation vector for frame
number
n for user number u is obtained as:
L-1
5 Zn,l - 1E Yn j+k Ck . (5)
L k=0
Framing this vector over L chip samples at the bit rate forms the post-
correlation
observation matrix:
Zn = IZno,,ZRJ,...,ZnL-11. (6)
10 The post-correlation data model (PCM) (see reference [13]) details the
structure of this
matrix as follows:
Zn = H,n,sn + NPCM,n, (7)
where Zn is the spatio-temporal observation matrix, Hn is the spatio-temporal
propagation matrix, SR = bn ~n is the signal component and NPCM,n is the
spatio-
15 temporal noise matrix. Equation 7 provides an instantaneous mixture model
at the bit
rate where the signal subspace is one-dimensional in the M x L matrix space.
For
convenience, the vector reshaper 26 of despreader 19" transforms the
matrices Zn, Hn and NPCM,n into (M x L)-dimensional
vectors Zu Hu and Zu respectively, by concatenating their columns into one
n' -n -PCM,n
20 spatio-temporal column vector to yield the following narrowband form of the
PCM
model (see reference 13):
Z" = Hus u + )V" (8)
n n n PCM,n
To avoid the ambiguity due to a multiplicative factor between Hn and Sn , the
norm
n
,
of Hn is fixed to VFM
n
The PCM model significantly reduces inter-symbol interference. It represents
an
instantaneous mixture model of a narrowband source in a one-dimensional signal
subspace and enables exploitation of low complexity narrowband processing
methods
after despreading. Processing after despreading exploits the processing gain
to reduce
the interference and to ease its cancellation in subsequent steps by
facilitating estimation
of channel parameters.
As discussed in reference 13, the spatio-temporal array-receiver (STAR) can be
used to detect each user separately at the base-station 11. In addition to
exploiting the
processing gain to reduce interference, the STAR allows accurate
synchronization and
CA 02318658 2000-09-12
21
tracking of the multipath delays and components and shows inherent robustness
to
interference. The STAR also allows coherent combining of the data. This
receiver is
found to provide fast and accurate time-varying multipath acquisition and
tracking.
Moreover, it significantly improves call capacity by spatio-temporal maximum
ratio
combining (MRC) in a coherent detection scheme implemented without a pilot
signal.
For the sake of clarity, the steps of STAR that are relevant to the
implementation of the
present invention will be reviewed briefly below, with reference to receiver
module 21
of Figure 5.
As shown in Figure 5, the despreader 19 supplies the post-correlation
observation
vector Zu to both the channel identification unit 28 and the MRC beamformer
27 of
n
STAR unit 20 . Using spatio-temporal matched filtering (yW = ly"/M) (i.e.
n
spatio-temporal maximum ratio combining, Wu"H" the STAR unit 20 provides
n -n
estimates of signal component Sn`, its DBPSK bit sequence bn and its total
received
power (,n)Z as follows:
b
u
s," = Real {~"HZ" l = Real ~~" (9)
n n
6n = Sign {sn } , (10)
(~n)2 = (1 - a)(~r.U-i)2 + a iSn 12 ~ (11)
where a is a smoothing factor. It should be noted that with ad hoc
modifications,
differential modulation and quasi-coherent differential decoding still apply
with DMPSK.
Orthogonal modulation can even be detected coherently by STAR without a pilot
(references [17] and [18]). Using the post-correlation observation vector Zu
and the new
n
signal component estimate sn from the beainformer 27 , the channel
identification unit
28 provides an estimate Hu of the channel 14 for user station 10 . The
channel
n
identification unit 28 updates the channel parameter estimate H" by means of
a decision
n
feedback identification (DFI) scheme whereby the signal component estimate SR
is fed
back as a reference signal in the following eigen-subspace tracking procedure:
Hn+l = Hn + (Zn -HnSn ~ri , (12)
CA 02318658 2000-09-12
22
where is an adaptation step-size. Alternatively, the product ~n gn could be
fed back
instead of the symbol component estimate sn, This DFI scheme allows a 3 dB
coherent
detection gain in noise reduction by recovering the channel phase offsets
within a sign
ambiguity without a pilot. Note that a reduced-power pilot can be used to
avoid
differential coding and decoding (reference [21]). The procedure that further
enhances
the channel estimate H" to obtain H" from the knowledge of its spatio-temporal
n+1 -n+l
structure (i.e. manifold) allows a fast and accurate estimation of the
multipath
time-delays l,n ~ ~TP,n in both the acquisition and the tracking modes (both
versions of
this procedure can be found in reference [13]). This improved estimation
accuracy
achieves robustness to channel estimation errors, and reduces sensitivity to
timing errors,
when STAR is used in multiuser operation.
For further information about STAR, the reader is directed to the articles by
Affes and Mermelstein identified as references [13] and [17] to [21].
If, as was assumed in reference 13, the spatio-temporal noise vector Nu is
PCM,n
spatially uncorrelated, power control on the uplink is generally able to
equalize the
received signal powers. However, the assumption that noise is uncorrelated
becomes
untenable on the downlink due to path-loss and shadowing and when the power of
particular users (e.g.,"priority links", acquisition, higher-order modulations
or higher
data-rates in mixed-rate traffic) is increased intentionally. Within a
particular cell, there
may be users having many different "strengths", perhaps because of different
data rates.
Figure 8 illustrates, as an example, a cell in which there are four different
sets of users
arranged hierarchically according to data rate. The first set I comprises
users which
have relatively high data rates, the second set M1 and third set M2 both
comprise users
which have intermediate data rates, and the fourth set D comprises users which
have
relatively low data rates. In practice, the receivers of the high data rate
users of set I
will not need to cancel any "outset" interference from the users in sets M I,
M2 and D,
but their transmissions will contribute to interference for the receiver
modules in those
sets. Intermediate data rate users in sets M1 and M2 will need to cancel
"outset"
interference from the high data rate users of the set I but not from the users
in set D.
They will themselves be contributors of "outset" interference to the users in
set D. The
receivers of users in set D must cancel "outset" interference from sets I, MI
and M2.
It is also possible for a receiver of a user within a particular set to cancel
"inset"
interference from one or more users within the same set; and itself be a
contributor to
CA 02318658 2000-09-12
23
such "inset" interference. Embodiments of the invention applicable to these
"outset" and
"inset" situations will be described hereinafter. In the description, where a
particular
user's signal is treated as interference and cancelled, it will be deemed to
be a
"contributor" and, where a particular user's receiver module receives
information to
enable it to cancel another user's interference, it will be deemed to be a
"recipient". To
simplify the description of the preferred embodiments described herein, it
will be
assumed that all users employ the same modulation at the same rate. For the
purpose
of developing the theory of operation, initially it will be assumed that,
among the mobile
stations in the cell, there will be a first set I of "strong" contributor
users, one of which
is identified in Figures 1 and 2 by index "i", whose received signal powers
are relatively
high and hence likely to cause more interference, and a second set D of "low-
power"
recipient users, one of which is identified in Figures 1 and 2 by index "d",
whose
received signal powers are relatively low and whose reception may be degraded
by
interference from the signals from the strong users. In order to receive the
low-power
users adequately, it usually is desirable to substantially eliminate the
interference
produced by the high-power users. For simplicity, most of the preferred
embodiments
of the invention will be described on the basis that the high-power users can
be received
adequately without interference suppression. It should be appreciated,
however, that the
"strong user stations could interfere with each other, in which case one
could also apply
to any interfering mobile the coloured noise model below and the near-far
resistant
solution proposed for the low-power user, as will be described later.
Assuming the presence of Ni interfering users assigned the indices i = I to
NI,
then the spatio-temporal observation vector of any interfering user (u = i
E(1,...,N1))
is given from Equation 8 by:
Z' - H's' + N' (13)
n n n PCM,n
where Ni can still be assumed to be an uncorrelated white noise vector if the
PCM,n
processing gain of this user is not very low. On the other hand, from the
point of view
of any low-power user (u=d 1,...,N1}), the spatio-temporal observation vector
is:
NI
Zd = HdsR + Id + Nd = Hds,d + ~ 1~=i + Nd , (14)
n n PCM,n -PCM,n -n -PCM,n -PCM,n
i=1
CA 02318658 2000-09-12
24
where, in addition to the uncorrelated white noise vector Nd there is included
a total
PCM,n I
interference vector ld which sums a random coloured spatio-temporal
interference
-PCM,n
vector from each interfering mobile denoted by p1J for i = 1, ..., NI. At
frame
PCM,n
number n, the realization of the vector 10 results from matched-pulse
filtering, ship-
PCM,n
rate sampling, bit-rate framing, despreading with ctd, and matrix/vector
reshaping of
the received signal vector k(t) from the i-th interfering mobile using
Equations
(3) to (6).
The receiver shown in Figure 5 would receive the signals from all of the user
stations independently of each other. It should be noted that there is no
cross-connection
between the receiver modules 2l...21", specifically between their STAR units
201
...20 ...20", for suppression of interference from the signals of mobile
stations which
constitute strong interferers. While the matched beamformer of Equation (9) is
optimal
in uncorrelated white noise, it is suboptimal when receiving the low-power
users due to
spatial correlation of the interference terms. To allow the accommodation of
additional
users in the presence of much stronger interfering mobiles in the target cell,
in
embodiments of the present invention the receiver of Figure 5 is upgraded to
obtain
much stronger near-far resistance, specifically by adapting the beamformer of
Equation
9 to reject the interference contributions from the interfering strong users.
In the general case, the total interference Id experienced by a user d in set
'PCM,n
D is an unknown random vector which lies at any moment in an interference
subspace
spanned by a matrix, say CpcM,n (1=e= , Id E Vec { CPcM,n }) with dimension
-PCM,n
depending on the number of interference parameters (i.e., power, data,
multipath
components and delays) assumed unknown or estimated a priori. As will become
apparent from the following descriptions of preferred embodiments, in
practice, the
matrix CPCM,n, which will be referred to as the "constraint matrix", can be
derived and
estimated in different ways. To achieve near-far resistance, the beamformer
must
conform to the following theoretical constraints:
WdHHd 1, WdNHd 1, l-n n ~ -n n (15)
d" d d" d
CPCM,n = 0, yVn IPC'M,n = 0
The first constraint provides a substantially distortionless response to the
low-
power user while the second instantaneously rejects the interference subspace
and thereby
CA 02318658 2000-09-12
substantially cancels the total interference. This modification of the
beamforming step
of STAR will be referred to as interference subspace rejection (ISR).
With an estimate of the constraint matrix CPCM,n available (as described
later),
the ISR combiner (i. e. , the constrained spatio-temporal beamformer) Wd after
5 despreading is obtained by:
"
d
QPCM,n - ~CPCM,nCPCM,n) ~ (16)
_ d d d" ~PCM,n IM L CPCM,nQPCm,nCpCM,n ~ (17)
]gd Hd
Wd PCMn -n ,
(1 g)
~,d
f n L7 n IlPCM,n Hn
where IM*L denotes a M * L x M L identity matrix. First, the projector IIPCM,n
orthogonal to the constraint matrix CPCM,n is formed. It should be noted from
Equations
(16) and (17) that the inverse matrix QpCM,n is not the direct inverse of
constraint
matrix CpCM,n but part of the pseudo-inverse of CPCMn, For convenience,
however,
it will be referred to as the inverse matrix hereafter. Second, the estimate
of the low-
power response vector yd is projected and normalized.
n
Whereas, using the above constraints, the ISR beamformer may process the low-
power user's data vector after it has been despread, it is possible, and
preferable, to
process the data vector without first despreading it. In either case, however,
the data
vector will still be despread for use by the channel identification unit.
Although it is
computationally more advantageous to do so without despreading, embodiments of
both
alternatives will be described. First, however, the spread data model of
Equation (2)
will be reformulated and developed and then used to derive various modes that
implement ISR combining of the data, without despreading, suitable for
different
complementary situations.
Data Model Without Despreading
The observation matrix Yn of Equation (4) which provides the post-correlation
matrix Zõ of Equation (7) by despreading and framing at the bit rate, can be
expressed
as:
t,
Yn = E Yn + Nnth , (19)
n=1
CA 02318658 2000-09-12
26
where each user u contributes its user-observation matrix yn, obtained by
Equations
(3) and (4) with X(t) replaced by Xu(t) in Equation (3), and where the
preprocessed
thermal noise contributes:
N~th = [NPI1Z(nl),NPhhz(nT + T ),...,Nprn(nT + (2L - 2)T )J. (20)
Using the fact that any bit-triplet [b:1, bn , bn;,, contributing to channel
convolution (see Equation (2a) in yn can be composed as:
[b,1,b:,b,+1] = bn 1[1, 0, 0] + bn [0,1, 0] + bn:l [0,0,1] , (21)
the sequence bu(t) can be locally approximated over the n-th block by means of
the
canonic generating sequences gl(t), g2 (t) and g3(t) in Figure 22 as:
b"(t) = bn glor(t) + bn 1&`-(t) + bn lg`.,r(t), (22)
where the indices lo n, l_, n, l+, n E { 1, 2, 3} are permuted at each block
so that the
corresponding canonic generating sequences locally coincide with /0, 1, 0],
[1, 0, 0] and
[0, 0, 1], respectively. Assuming slow time-variations of ~(t) and H(t)
compared to the
symbol duration:
~~u ~~u y~ u
I n = SnuIO,n + Snu-1 `-l,n + Snu+l yl,n , (3)
where the canonic user-observation matrices yk n are obtained by Equations (3)
and (4)
with X(t) in Equation (3) replaced, respectively for k = -1, 0, +1, by:
Xk (t) = H n(t) (D gl`,.(t) c i'(t) . (24)
Good approximations of y_1 n and y+l,n can be actually obtained at each
iteration by
L simple backward/forward shifts of the columns of yo n with zero column
inputs.
It should be noted that the canonic generating sequences allow more accurate
reconstruction (e.g., overlap-add) of time-varying channels. Also,the
resulting
decomposition in Equation (23) holds for long PN codes.
It should be noted that this decomposition also holds for any complex-valued
symbol-triplet [bu1, bR , bna~. With ad hoc modifications, therefore, the ISR
approach
according to this invention applies to any complex modulation (e.g., MPSK,
MQAM,
even analog). This new signal decomposition is used to derive the different
implementations of ISR which will be described later.
With respect to the low-power user assigned the index d and the NI strong
interfering mobiles assigned the indices i= 1, ..., NI, the observation vector
obtained by
reshaping the observation matrix, before despreading, can now be rewritten as:
y= Yd Sn + Id + 1 + N, (25)
n -O,n ISI.n n -n.
CA 02318658 2000-09-12
27
where the first canonic observation vector yd appears as the "channel" vector
of the
O,n
low-power user d. The total interference vector before despreading:
NI NI NI
1 {si + S~ + - ~ {sZ + (2v)
-O,n l,n +l,n X. I SI,n
i=1 i=1 i=1
is the sum of the interfering signal vectors yi and:
n
jn n ~+ n u (27)
Sln - Sn 1 Nln Sn+l ~+ln' l 10 is the intersymbol interference (ISI) vector of
user u. In large processing gain situations,
the self ISI vector ld can be combined with the uncorrelated spatio-temporal
noise
-ISI,n
vector N~ leading to the following data vector model before despreading: d yn
= dnsn + In + Nn. (28)
Despreading the observation vector in the above equation with the spreading
sequence of the low-power user d provides the data vector model after
despreading in
Equaiton (14). It is possible to derive a finer decomposition of the date
model to allow
implementation of one or more of the ISR modes over diversities.
Finer Decomnositionof the Data Model Over Diversities
Thus, Equation (2a) can be further decomposed over the Nf = MP diversity
branches or fingers in such a way that the observation signal contribution
Xn~f(t) received
by the m-th antenna along the p-th path for f = (p - 1)M + m = 1,..., Nf can
be
separated as follows:
Nj
Xn(t) = EXnf(t). (29)
f~'
The observation signal contribution from the f-th finger is defined as:
Xnf(t) = ~n(t)Hn~f(t) c n(t)b u(t) (30)
= 'Yn(t)Gp f(t)-Cp(t)b u(t - Tp(t))C n(t - 7p(t))e
where the propagation vector from thef-th finger is:
Gpf(t) = yf(t)Rm. (31)
CA 02318658 2000-09-12
28
In the above equation, the scalar .yf(t) is the channel coefficient over the f-
th finger and
R= [0,..., 0,1, 0,..., 0f is a M x I vector with null components except for
the m-th
one. With the above definitions, one can easily check the following
decompositions of
the channel and the propagation vectors:
Nj
Hn(t) _ L H"'t(t), (32)
f=1
M
Gp (t) _ 1: Gp,~V -1)M+m(t). (33)
m=1
Accordingly, after preprocessing, the matched-filtering observation matrix can
be
decomposed as follows:
U U Nj
yn - L~ I n + trnh -E y ~nJf,nl nl +`vth,
(34)
u=1 u=1 f=1 l
where each user u contributes its user-observation matrices y,"~f from fingers
f
1,...,Nf, obtained by Equations (3) and (4) with X(t) replaced by Xnf(t) in
Equation (3).
Note that the complex channel coefficient y f(nT) _f(nT)Ep(nT) is separated
from the
matrix' y'nf which contains a purely-delayed replica of the spread-data
without
attenuation or phase offset from finger f. This matrix, which is obtained by
Equations
(3) and (4) with X(t) in Equation (3) replaced by:
X"~f(t) = RmS(t - rP(t)) b "(t)c "(t), (35)
can be further decomposed over the canonic generating sequences as follows:
rn f = bn ro n+ bri y" i + bn+l Y+i n, (36)
where the canonic user-observation matrices yk n from finger f are obtained by
Equations (3) and (4) with X(t) in Equation (3) replaced, respectively for k =
-1, 0, +1,
by:
'This matrix is real-valued in the case of a binary modulation.
CA 02318658 2000-09-12
29
Xk At) = Rmb(t - TP(t)) gl'-(t)c "(t), (37)
where b(t) denotes the Dirac impulse. Therefore one obtains:
U Nf +1
Yn = L: L~ E 'Sn+kJf,nYk n+ ~Ylh (38)
u=1 f=1 k=-1
A coarser decomposition over fingers of the total interference vector before
despreading
defined in Equation (26) gives:
NI NI Nf
In = L~ Yt =E !~ VnSf,n~n = (39)
1=1 i=1 f=1
After despreading with the spreading sequence of the low-power user d, it
gives:
NI NI Nf
Id = Id' - _ ~ >G"~" larJ
(40)
PCM,n -PCM,n ^ f=1 n f n-PCM,n
Embodiments of the invention which use the above decompositions of
interference,
denoted as ISR-D implementations before and after despreading, will be
described later
with reference to Figures 16 and 23.
ISR Combining Before Despreading
As described hereinbefore, the combining step of STAR is implemented without
despreading by replacing Equation (9) for the low-power user with:
sn = RealfE~ "Yn}, (41) where the spatio-temporal beamformer Wd now implements
ISR without despreading
n
to reject 1 by complying with the following constraints (see Equation (15)):
d
d" d K'd"Y
4V Y.n = 1, ~ -n -o,n = 1, (42)
WdHC - 0, YYdHl ~ 0,
n n n n
and Cn is the constraint matrix without despreading that spans the
interference subspace
of the total interference vector In (i.e., In E Vec { Cn}).
The constraint matrix without despreading, Cn, is common to all low-power
users.
Thus, it characterizes the interference subspace regardless of the low-power
user. In
contrast, each constraint matrix after despreading CPCM,n in Equaiton (15) is
obtained
CA 02318658 2000-09-12
by despreading Cn with the spreading sequence of the corresponding low-power
user.
Therefore ISR combining before despreading, although equivalent to beamforming
after
despreading, is computationally much more advantageous.
In contrast to the "after despreading" case described earlier, when the data
vector
5 is not despread before processing by the ISR combiner (i. e. , the
constrained spatio-
temporal beamformer) Wd the estimate of the constraint matrix is obtained by:
n
Qn - CCn Cn)-1 , (43)
Un - IM * (2L-1) - ~nQn~n ~ (44)
10 Wd = n O,n (45)
n ~,d
]_O,n n Y_O,n
where IM.(2L_l) denotes a M * (2L - 1) x M*(2L - 1) identity matrix. As
before, it can
be seen from Equations (43) and (44) that the inverse matrix Qn is not the
direct inverse
of constraint matrix Cn but part of the pseudo-inverse of Cn . It should also
be noted
15 that the above operations are actually implemented in a much simpler way
that exploits
redundant or straightforward computations in the data projection and the
normalization.
As before, the projector IIn orthogonal to the constraint matrix Cn is formed
once for
all low-power users. This would have not been possible with ISR after
despreading.
Second, the estimate of the low-power response vector yd is projected and
normalized.
-0,n
20 The estimate pdn is reconstructed by reshaping the following matrix:
Yo n= Hn g`~- c,d (46)
n
the fast convolution with the channel being implemented row-wise with the
spread
sequence. The channel estimates fid i,c. H`` is provided by STAR as explained
earlier
and includes the total contribution of the shaping pulse 0(t) matched with
itself [13}. If
25 the channel time-variations are slow, the channel coefficients can be
assumed constant
over several symbol durations [20], thereby reducing the number of
computationally
expensive despreading operations required (see Figure 9).
It should be noted that, although these ISR modes have formulations that are
analogous whether ISR is implemented with or without first despreading the
data vector,
30 ISR combining of the data without it first being despread reduces
complexity
significantly.
Receivers which implement these different ISR modes will now be described,
using the same reference numerals for components which are identical or
closely similar
CA 02318658 2000-09-12
31
to those of the receiver of Figure 5, with a suffix indicating a difference. A
generic ISR
receiver which does so without despreading of the data will be described
first, followed
by one which does so after despreading of the data. Thereafter, specific
implementations
of different ISR modes will be described.
Thus, Figure 9 illustrates a receiver according to a first embodiment of the
invention which comprises a first set I of "strong user" receiver modules
21'..,21NI
which are similar to those in the receiver of Figure 5, and, separated by a
broken line
34, a second set D of "low-power" user receiver modules which differ from the
receiver
modules of set I but are identical to each other so, for convenience, only
one, receiver
module 2 1 A d comprising a STAR module 20A' having a modified beamformer
47A1, is
shown. The outputs of the decision rule units 29...... 29NI and of the channel
identification units 28', ,28N` from the set I modules are shown coupled to a
constraints-
set generator 42A which processes the corresponding symbol estimates and
channel
parameter estimates to produce a set of N, constraints (C-The
constraints-set generator 42A may, however, use hypothetical symbol values
instead, or
a combination of symbol estimates and hypothetical values, as will be
described later.
Each individual constraint lies in the same observation space as the
observation matrix
Y,, from preprocessor 18. The constraints-set generator 42A supplies the set
of
constraints Cn to a constraint matrix generator 43A which uses them to form a
constraint
matrix Cn and an inverse matrix Q, which supplies it to the beamformer 47d and
each
of the corresponding beamformers in the other receiver modules of set D. The
actual
content of set of constraints cCn and the constraint matrix C n will depend
upon the
particular ISR mode being impleinented, as will be described later.
The receiver of Figure 9 also comprises a vector reshaper 44 which reshapes
the
observation matrix Yn from the preprocessing unit 18 to form an observation
vector Y
having dimension M(2L-1) and supplies it to the beamformer 47A' and to each of
the
other beamformers in the other receiver modules in set D.
The STAR unit 40Aa of receiver module 41 A' comprises a channel identification
unit 28Ad, a decision rule unit 27Ad and a power estimation unit 30A' which
are similar
to those of the STAR units 20'...20" described hereinbefore. In addition to
the STAR
unit 40A', the receiver module 41Ad comprises a despreader 19d. The despreader
19d
despreads the observation matrix Yn using the spreading code for user d and
supplies the
resulting post-correlation observation vector Z to the channel identification
unit 28Ad
CA 02318658 2000-09-12
32
only. The decision rule unit 27Ad and power estimation unit 30Aa produce
output
symbol estimates f d and power estimates ( ~y~2, respectively. The ISR
beamformer
n
47Ad of STAR unit 40Ad produces corresponding signal component estimates Sn
but
differs from the MRC beamformers 271...27" because it operates upon the
observation
vector Y, which has not been despread. In a manner similar to that described
with
respect to Figure 5, the channel identification unit 28A' receives the post-
correlation
observation vector Zd and the signal component estimate sri and uses them to
derive
n
the spread channel estimates yd which it uses to update the weighting
o,n'
coefficients ypn of the beamformer 47Ad in succeeding symbol periods. The
symbol
period corresponds to the spread data frame of M(2L-1) elements. The
coefficients of
the ISR beamformer 47Ad also are updated in response to the constraint matrix
Cn and
its inverse Qn, as will be described later. As shown in Figure 9, the same
matrices Cn and a are supplied to all of the receiver modules in set D,
specifically to
their beamformers.
As shown in Figure 10, the constraint matrix generator means 43A comprises a
bank of vector reshapers 48A1
, ..., 48A N~ and a matrix inverter 49A. Each of the
vector reshapers 48A 1, ..., 48A N reshapes the corresponding one of the set
of
constraints-set matrices Cn,...,e` to form one column of the constraint
matrix Cn, which is processed by matrix inverter 49A to form inverse matrix
Qn,. For
simplicity of description, it is implicitly assumed that each of the columns
of C is
n
normalized to unity when collecting it from the set of constraints ~'n.
As also illustrated in Figure 10, beamformer 47A' can be considered to
comprise
a coefficient tuning unit 50A' and a set of M(2L-1) multipliers 51; ...51M(u,-
,). The
coefficient tuning unit 50Ad uses the constraint matrix Cn, the inverse matrix
Qn and the
channel parameter estimates yd to adjust weighting coefficients Wd' ~d'
-O,n 1,n M(2L-1),n
according to Equation 45 supra. The multipliers 51; ...51~,(2L-,) use the
coefficients to
weight the individual elements y.,, y respectively, of the observation
1,n -M(2L-1),n'
vector y The weighted elements are summed by an adder 52d to form the raw
filtered
symbol estimate sn for output from the beamformer 47Ad.
An alternative configuration of receiver in which the low-power STAR units of
set D implement ISR beamforming qfter despreading of the observation matrix Yn
from
preprocessor 18 will now be described with reference to Figures 11 and 12,
which
correspond to Figures 9 and 10. The receiver shown in Figure 11 is similar to
that
CA 02318658 2000-09-12
33
shown in Figure 9 in that it comprises a preprocessing unit 18 which supplies
the
observation matrix Yn to the set I receiver modules 21'...21NI, a constraints-
set generator
42B and a constraint matrix generator means 43B. It does not, however, include
the
vector reshaper 44 of Figure 9 and each of the low-power user STAR modules in
set D
has a modified beamformer. Thus, modified beamformer 47Bd operates upon the
post-
correlation observation vector Zd from the output of the despreader 19d which
is
n
supplied to both the channel identification unit 28Bd and the beamformer 47Ba.
The
channel identification unit 28Bd generates channel estimates ftd and supplies
them to the
n
beamformer 47Bd which updates its coefficients in dependence upon both them
and a
user-specific constraint matrix CPCM,n and user-specific inverse matrix QPCM,n-
It should
be noted that the constraint matrix generator means 43B supplies user-specific
constraint
and inverse matrices to the other receiver modules in set D.
Referring now to Figure 12, the common constraint matrix generator means 43B
comprises a bank of user-specific constraint matrix generators, one for each
of the
receiver modules of set D, and each using a respective one of the spreading
codes of the
users of set D. Since the only difference between the user-specific constraint
matrix
generators is that they use different spreading codes, only user-specific
constraint matrix
43Bd is shown in Figure 12, with the associated beamformer 47Ad. Thus, user-
specific
constraint matrix generator 43Bd comprises a bank of
despreaders 55Bd ', ..., 55Bd'r", and a matrix inverter 46Bd. The
despreaders 55Bd ', ..., 55Bd'N` despread respective ones of the N, matrices
in the set
of constraints C,, to form one column of the individual constraint
matrix CPCM,n implicitly normalized to unity. The matrix inverter 46Bd
processes
individual constraint matrix CPCM,n to form inverse matrix QPCM,n, The user-
specific
constraint matrix generator 4313d supplies the constraint matrix C cM,. and
inverse
matrix QP Mn to the coefficient tuning unit 50Bd of beamformer 47Bd. As shown
in
Figure 12, the beamformer 47Bd has ML multipliers 51 i... 51ML which multiply
weighting coefficients yyd `. ., yyd' by elements Zd ,,, Zd of the post-
correlation
-1,n -ML n -t,n -ML,n
observation vector Zd. As before, adder 52d sums the weighted elements to form
the
-n
signal component estimate sri - The beamformer coefficeints are timed
according to
Equation (18).
Either of these alternative approaches, i. e. with and without despreading of
the
data vector supplied to the beamformer, may be used with each of several
different ways
CA 02318658 2000-09-12
34
of implementing the ISR beamforming, i.e. ISR modes. It should be noted that
all cases
use a constraint matrix which tunes the ISR beamformer to unity response to
the desired
channel and null response to the interference sub-space. In each case,
however, the
actual composition of the constraint matrix will differ.
Specific embodiments of the invention implementing the different ISR modes
without despreading of the data will now be described with reference to Figure
13 to 20,
following which embodiments implementing the same ISR modes after despreading
will
be described with reference to Figures 21 to 26.
Interference Subspace Rejection over Total Realisation (ISR-TR)
The receiver unit shown in Figure 13 is similar to that shown in Figure 9 in
that
it comprises a set I of receiver modules 21'...21" for processing signals of
NI strongly
interfering mobile stations and a set D of receiver modules for signals of
other, "low-
power", users. The receiver modules of set D are identical so only receiver
module
21Cd, for channel d, is shown in Figure 13. As in the receiver of Figure 9,
the
observation matrix Yn from preprocessor 18 is supplied directly to each of the
despreaders 19'...19'" of the set 1 receiver modules. Before application to
each of the
receiver modules of set D, however, it is delayed by one symbol period by a
delay
element 45 and reshaped by vector reshaper 44. The resulting observation
vector y
n -I
is supplied to the beamformer 46C`' and to each of the other beamformers in
the set D
receiver modules (not shown). In addition to beamformer 47Cd, receiver module
21Cd
comprises despreader 19' and a STAR receiver unit 20Cd comprising channel
identification unit 28Cd, decision rule unit 27Cd and power estimation unit
30Cd which
are siniilar to those shown in Figure 9. The set of channel parameter
estimates nn, which are supplied to the constraints-set generator 42C comprise
the channel estimates H',,,,,and the power estimates n~ n
n n
The constraints-set generator 42C comprises a bank of respreaders 57C'...57CNI
each having its output connected to the input of a respective one of a
corresponding bank
of channel replication units 59C'...59CNI by a corresponding one of a bank of
multipliers
58C'...58CN'. The respreaders 57C1
...57CNI are similar so only one, respreader 57C ,
is illustrated in Figure 14. Respreader 57C is similar to the corresponding
spreader 13
(Figure 3) in that it spreads the symbol bn from the corresponding decision
rule unit
29C using a periodic personal code sequence c," at a rate 1/T, where Tc is
the chip
CA 02318658 2000-09-12
pulse duration. It differs, however, in that it does not include a shaping-
pulse filter.
The effects of filtering both at transmission with the shaping-pulse (see
Figures 2 and 3)
and at reception with the matched shaping-pulse (see Figures 5 and 6) are
included
baseband in the channel estimate or Hn~ as disclosed in reference [13].
n
5 Referring again to Figure 13 and, as an example, receiver module 21C',
replication of the propagation characteristics of channel 14' is accomplished
by digital
filtering in the discrete time domain, i.e. by convolution at the chip rate of
the channel
estimate Hl with the respread data bn cf . This filtering operation
immediately provides
n
decomposed estimates of the signal contribution of user station 10' to the
observation
10 matrix Y. Thus, respreader 57C' respreads the symbol Ln' from decision rule
unit
29C', multiplier 58C1 scales it by the total amplitude estimate ,,n and
channel
replication filter 59C' filters the resulting respread symbol using the
channel
estimate Hl from channel identification unit 28C'. The symbol estimates from
the other
n
STAR units in set I are processed in a similar manner.
15 It should be noted that the respreaders 57C'...57CN', multipliers
58C'...58CN' and
channel filters 59C'...50CN' correspond to the elements 13', 15' and 14' in
the interfering
user channel of Figure 2. The coefficients of the channel replication filter
units
59C'...59CN' are updated in successive symbol periods by the channel
identification units
28C'...28CN' using the same coefficients gn... Hn 1, corresponding to the
transmission
20 channels 14'...14N', respectively, used to update their respective MRC
beamformers
27C'...27CN'. It will be appreciated that the re-spread signals Yri 1 yn 1
from the
channel replication filter units 59C...59CN', respectively, include
information derived
from both the sign and the amplitude of each symbol, and channel
characteristics
information, and so are the equivalents of the set I strong interferer's
spread signals as
25 received by the base station antenna elements 12'...12M.
The constraint-set generator 42C also comprises an adder 60 coupled to the
outputs of the channel replication units 59C'...59CN'. The adder 60 sums the
estimates yn 1 y'1 of the individual contributions from the different
interferers to form
the estiinate In-1 of the total interference from the NI interferers in the
received
30 observation matrix Y,,. The sum can be called total realization (TR) of the
interference.
In this embodiment, the constraint matrix generator simply comprises a vector
reshaper
43CB which reshapes the total realization matrix In-1 to form the vector I
which,
n-1
in this embodiment, constitutes the constraint matrix C. It should be noted
that, because
CA 02318658 2000-09-12
36
the constraint matrix really is a vector, the inverse matrix Q, reduces to a
scalar and,
assuming implicit normalization, is equal to 1. Hence, no matrix inverter is
needed.
The reshaped vector I is supplied to the ISR beamformer 47Cd of receiver
n-1
module 21 C' and to the beamformers of the other receiver modules in set D.
The
beamformer 47Cd uses the reshaped vector I and the channel estimates yd to
-n-1 -o,n-1
update its coefficients, according to Equation (45), for weighting of the
elements of
observation vector y
n-1
The beamformer 47Cd adjusts its coefficients so that, over a period of time,
it will
nullify the corresponding interference components in the observation vector y
from
n-1
the vector reshaper 44 and, at the same time, tune for a unity response to the
spread
channel. vector estimate so as to extract the raw signal component
estimate sR , substantially without distortion.
ISR-TR constitutes the simplest way to characterize the interference subspace,
yet
the most difficult to achieve accurately; namely by a complete estimation of
the
instantaneous realization of the total interference vector I in a
deterministic-like
approach. The constraint matrix is therefore defined by a single null-
constraint (i.e.,
N, =1) as:
NI
C = I n = ` ' (47)
IIInII I~TrI ~II
i=1 n
where each estimate y` is reconstructed by reshaping the following matrix:
n
f;, = ~n Ha bhcl` . (48)
For each interfering user assigned the index i = 1, ..., NI, this mode uses
estimates of its received power (~,R)2 and its channel H` , both assumed
constant over
-n
the adjacent symbols and made available by STAR. This mode also requires a bit-
triplet
estimate {h, bR, b;,,,, of each interfering user (see Equation (23)). To
obtain estimates
of the signs of the interferer bits for both the current and next
iterations (i.e., bn and bn,,), the ISR-TR inode requires that the processing
of all the
low-power users be further delayed by one bit duration and one processing
cycle (pc),
respectively. The one-bit delay is provided by the delay 45 in Figure 13.
In the ISR-TR mode and in the alternative ISR modes to be described hereafter,
the interference (due to the strongest users) is first estimated, then
eliminated. It should
CA 02318658 2000-09-12
37
be noted that, although this scheme bears some similarity to prior
interference
cancellation methods which estimate then subtract the interference, the
subtraction makes
these prior techniques sensitive to estimation errors. ISR on the other hand
rejects
interference by beamforming which is robust to estimation errors over the
power of the
interferers. As one example, ISR-TR would still implement a perfect null-
constraint if
the power estimates were all biased by an identical multiplicative factor
while
interference cancellers would subtract the wrong amount of interference. The
next mode
renders ISR even more robust to power estimation errors.
The receiver illustrated in Figure 13 may be modified to reduce the
information
used to generate the interfering signal estimates y' ... yNj specifically by
omitting the
n-1 n-11
amplitude of the user signal estimates, and adapting the ISR beamformer 47Cd
to provide
more (NI) null constraints. Such a modified receiver will now be described
with
reference to Figure 15.
Interference Subspace Rejection over Realisations (ISR-R)
In the receiver of Figure 15, the receiver modules in set I are identical to
those
of Figure 13. Receiver module 21Dd has the same set of components as that
shown in
Figure 13 but its beamformer 47Dd differs because the constraint matrix
differs. The
constraints-set generator 42D differs from that shown in Figure 13 in that it
omits the
multipliers 58C'...58CN' and the adder 60. The outputs from the power
estimation units
30'...30N` are not used to scale the re-spread signals from the respreaders
57C'...57CN1,
respectively. Hence, in the receiver of Figure 15, the signals 6n... bnl from
the STAR
units 20'...20N', respectively, are re-spread and then filtered by channel
replication filter
units 59C'...59CN1, respectively, to produce user specific observation
matrices
yn 1 ynll, respectively, as the constraints-set C. In contrast to the receiver
of Figure
13, however, these respread matrices are not summed but rather are processed
individually by the constraint matrix generator 43D, which comprises a bank of
vector
reshapers 48D' ... 48DN' and a matrix inverter 49D (not shown but similar to
those in
Figure 10). The resulting constraint matrix C0 comprising the column
vectors yl .., yNr is supplied, together with the corresponding inverse matrix
Q~, to
n-1' '-n-1
each of the receiver modules in set D. Again, only receiver module 21Dd is
shown, and
corresponds to that in the embodiment of Figure 13. Each of the
vectors P ... ~I represents an estimate of the interference caused by the
n-1 n-1'
CA 02318658 2000-09-12
38
corresponding one of the strong interference signals from set I and has the
same
dimension as the reshaped observation vector y
n-i
In this ISR-R mode, the interference subspace is characterized by normalized
estimates of the interference vectors y` , Consequently, it spans their
individual
n
realizations with all possible values of the total received powers (0n)2. The
constraint
matrix is defined by NI null-constraints (i.e., N,=NI) as:
~ n~ Cn = ~ ,..., ~l , (49)
~~-n ~~ ~~ n ~~
where each estimate y` is reconstructed by reshaping the following matrix:
n
Yn = Hn bn C,` (50)
It should be noted that, in the reconstruction of y` , the total amplitude of
the
n
i-th interferer ~n (see Figure 15) has been omitted intentionally; hence the
higher
robustness expected to near-far situations as well as the enlarged margin for
power
control relaxation.
Interference Subspace Rejection over Diversity (ISR-D)
The ISR-D receiver shown in Figure 16 is predicated upon the fact that the
signal
from a particular user will be received by each antenna element via a
plurality of sub-
paths. Applying the concepts and terminology of so-called RAKE receivers, each
sub-
path is termed a "finger". In the embodiments of Figures 9, 11, 13 and 15, the
channel
identification units estimate the parameters for each finger as an
intermediate step to
estimating the parameters of the whole channel. In the ISR-D receiver shown in
Figure
16, the channel identification units 28E'...28E" supply the whole channel
estimates
Hl HNI respectively, to the beamformers 27'...27N', respectively, as before.
In
R n
addition, they supply the sets of channel parameter estimates Y{n NI of each
individual sub-channel or finger to the constraints-set generator 42E. The set
of channel
parameter estimates y{' comprises the sub-channel estimates g' H''Nj, The
n n~"' ~ n
constraints-set generator 42E is similar to that shown in Figure 15 in that it
comprises
a bank of respreaders 571 ...57" but differs in that the channel replication
units
59D'...59DN' are replaced by sub-channel replication units 59E1
...59EN', respectively.
The sub-channel replication units 59E'...59EN' convolve the respread symbols
with the
sub-channel estimates H1 1 H1'N; ;H^'I,1 ,gNr'D1f respectively, to produce
n n n , n
CA 02318658 2000-09-12
39
normalized estimates yl,l y1n'; ;y'''rl, of the sub-channel-specific
n-i n-1 n-1 n-1
observation matrices decomposed over fingers. Hence, the matrices span the
space of
their realizations with all possible values of the total received powers (~n)2
and complex
channel coefficients ~'fn, The estimates are supplied to a constraint matrix
generator
43E which generally is as shown in Figure 10 and produces the constraint
matrix
accordingly.
The constraint matrix Cn is simply defined by NflVl null-constraints (i.e., N,
_
NfxNI=MxPxN1)as:
~,l,l 1 ~,],Nf .~VI,1 ~iV/Nf
C' -~n -n I-~ -n ]-= -n (51)
I
n FIVII 71r, ~~ ~'1 IrFl, Eac
h estimate yf is reconstructed by reshaping the following matrix:
n
Ynf = Cl n bn Cl~. (52)
It should be noted that, in the reconstruction of the total amplitude of the
i-th interferer ~a as well as the channel coefficients f~ (see Figure 1) are
intentionally omitted; hence the relative robustness of ISR-D to power
mismatch, like
ISR-R. Unlike other modes, it additionally gains robustness to channel
identification
errors and remains sensitive only to the estimated channel parameters
remaining, namely
the multipath time-delays, and to symbol estimation errors.
It should be noted that, in the receivers of Figures 13, 15 and 16, estimation
errors of the interference bit signs may introduce differences between the
estimated
constraints and the theoretical ones. Hence, although ISR-D, ISR-R and ISR-TR
modes
are satisfactory in most situations, it is possible that the realisation could
be erroneous,
which would affect the validity of the interference cancellation.
Additionally, estimation
of the signs of the interference bits for reconstruction in the ISR-D mode, as
in the ISR-
R and ISR-TR modes, requires that the processing of all of the low-power users
be
further delayed by one bit duration, i.e., by delay 45, and one processing
cycle (pc).
To avoid these drawbacks, alternative ISR approaches to implementation of the
constraints of Equation (42) are envisaged and will now be described,
beginning with
ISR-H which avoids processing delays and is completely robust to data
estimation errors.
CA 02318658 2000-09-12
Interference Subspace Rejection over HYpotheses (ISR-H)
It is possible to use a set of signals which represent all possible or
hypothetical
values for the data of the interfering signal. Each of the interfering signals
constitutes
a vector in a particular domain. It is possible to predict all possible
occurrences for the
5 vectors and process all of them in the ISR beamformer and, therefore,
virtually guarantee
that the real or actual vector will have been nullified. As mentioned, the
strong
interferers are relatively few, so it is possible, in a practical system, to
determine all of
the likely positions of the interference vector and compensate or nullify all
of them.
Such an alternative embodiment, termed Interference Subspace Rejection over
10 Hypotheses (ISR-H) because it uses all possibilities for the realisations,
is illustrated in
Figure 17.
The components of the "interferer" receiver modules of set I, namely the
despreaders 19'...19" and STAR units 20'...20N', are basically the same as
those in the
receiver of Figure 15 and so have the same reference numbers. In the
embodiment of
15 Figure 17, however, the constraints-set generator 42F differs because the
symbol
estimates b' .,, b` from the outputs of the decision rule units 29'. ..29N'
are not supplied
n n
to the respreaders 57F...57FN', respectively, but are merely outputted to
other circuitry
in the receiver (not shown).
Instead, bit sequence generators 63F...63FN' each generate the three
20 possibilities g~, g2 n, g3 which cover all possible estimated values of the
previous, current
and next bits of the estimated data sequences n..,bn including the realisation
itself (as
explained later), and supply them to the respreaders 57F'...57FN',
respectively, which
each spread each set of three values again by the corresponding one of the
spreading
codes. The resulting re-spread estimates are filtered by the channel
replication filters
25 59F...59FN', respectively, to produce, as the constraint set, the matrix
estimates
^1 " "1
Y ~,NI YNI YNI The bit sequence generators could, of course, be
on, Y._1~, Y+1~; ... 10n _1,n, +1,n*
replaced by storage units.
The constraint matrix generator 43F is generally as shown in Figure 10 and
processes the set of estimate matrices to form the column vectors
30 yl , y , yl ;... ;~`'r, krvl , yN' of constraint matrix Cn, which it
supplies with
-O,n --1,n -+1,n -O,n 1,n -+1,rt
corresponding inverse matrix Q,,, in common to the beamformer 47Fd and the
beamformers of the other set D receiver modules.
CA 02318658 2000-09-12
41
Receiver module 21Fd comprises similar components to those of the receiver
module 21E`' shown in Figure 16. It should be noted, however, that, because
the "next"
bit is being hypothesized, it need not be known, so the delay 45 is omitted.
As mentioned above, the two bits adjacent to the processed bit of the i-th
interferer contribute in each bit frame to the corresponding interference
vector (symbol)
to be rejected. As shown in Figure 18, enumeration of all possible sequences
of the
processed and adjacent bits gives 23 = 8 triplets, each of three bits. Only
one of these
triplets could occur at any one time at each bit iteration as one possible
realization that
generates the user-specific observation matrix yn, These eight triplets can be
identified
within a sign ambiguity with one of the four triplets identified as (a)... (d)
in the left-hand
part of Figure 18, since the four triplets (e)... (h) are their opposites.
It should be appreciated that the bit sequence generators 63'...63N1 (Figure
17)
each supply only three values, gl , g2, g3 because the dimension of the
generated signal
n n n
subspace is 3. It should be noted that frames of duration 3T, taken from these
sequences
at any bit rate instant, reproduce the eight possible realisations of the bit
triplets of
Figure 18. Therefore, at any bit iteration, the bit sequence bn of the
interfering mobile
station can be locally identified as the summation of the generating sequences
g~, k = 1,..., 3 weighted by the bit signs bn-1, bõ and b,;,l. Replacing the
estimate
in Equation (50) by gn, k 1,..., 3, , yields canonic observation matrices that
span all possible realisations of the received signal vector from the i-th
interfering mobile
within a sign ambiguity.
In the ISR-H embodiment of Figure 17, the interference subspace is
characterized
by normalized estimates of the canonic interference vectors y` . Accordingly,
it spans
k,n
their individual realizations with all possible values of the total received
powers (0n)2 and bit triplets [b1, bn ,bn+lThe constraint matrix is defined by
3NI
null-constraints (i.e., N,. = 3NI) as:
2 l" I" l" ~ 2" 1 1" 1
C = O'n --l,n -+l.n -p,n --l,n -+l,n (53)
n > > >..., ~ , ~ '
M ~,n (lIl~l,nll II~nII Il~l.nll 30 where each estimate is reconstructed,
respectively, for k = -1, 0, + 1 by reshaping
k,n
the following matrix:
(54)
Yk n= Fln gn'- c,`.
CA 02318658 2000-09-12
42
It should also be noted that, in the reconstruction above, only the channel
estimates (assumed stationary over the adjacent symbols) are needed for
complete
interference rejection regardless of any 2D modulation employed (see Figure
19); hence
the extreme robustness expected to power control and bit/symbol errors of
interferers.
The ISR-H combiner coefficients are symbol-independent and can be computed
less
frequently when the channel time-variations are slow.
Merging of the D mode with the H mode along the decomposition of Equation
(38) yields ISR-HD (hypothesized diversities) with a very close form to the
decorrelator.
This ISR-HD mode requires a relatively huge number of constraints (i. e. , 3Nf
NI).
Consequently, the ISR-HD mode is not considered to be practical at this time.
In fact, it wotild be desirable to reduce the number of constraints required
by the
ISR-H receiver described above. This can be done using an intermediate mode
which
is illustrated in Figure 20 and in which the receiver modules of both sets I
and D are
similar to those of Figure 15; most of their components are identical and have
the same
reference numbers. In essence, the constraint-set generator 42G of the
receiver in Figure
combines the constraint-set generators of Figures 15 and 17 in that it uses
estimated
symbols and hypothetical values. Thus, it comprises a bank of respreaders
57G'...57G",
a corresponding bank of channel replication units 59G'...59GN` and a bank of
bit symbol
generators 63G'...63G". In this case, however, each of the bit symbol
generators
20 63G'...6GEN' supplies only one bit symbol to the corresponding one of the
respreaders
57G'...57GN', which receive actual bit symbol estimates bn ... b n',
respectively, from
the decision rule units 29...... 29', respectively. It should be appreciated
that, although
the bit symbol generators 63G...... 63GN' each supply only one bit symbol for
every
actual symbol or realization from the corresponding one of the decision rule
units
29',...,29"', that is sufficient to generate two hypothetical values of
"future" symbols
gri+l ,===, bn i for every one of the symbol estimates gn+l bn'1 since only
two
hypothetical values of the symbols, namely 1 and -1, are required. The
respreaders
57G...... 57GN' supply the spread triplets to the channel replication units
59G'...59GNI
which filter them, using the channel parameter estimates Hl =.. g"",
respectively, to
n rt
produce pairs of matrices yr,n, y+l n, .., yNn', yN ~ and supply them to the
constraint matrix
generator 43G which is configured generally as shown in Figure 9. The
constraint
matrix generator 43G reshapes the matrices y1 y+l n; yNn, yN,n to form
vectors y' yl y~" y"'' which then are used as the column vectors of the
constraint
r n~ -+1n~ rn~ -+1n
CA 02318658 2000-09-12
43
matrix Cn. The constraint matrix generator 43G supplies the constraint matrix
Cn and
the corresponding inverse matrix Q,t in common to the beamformer 47Ga and the
beamformers of other receiver modules in set D.
Hence, the beamformer 47Gd uses the past symbol estimate bn_1 of the
interference data as well as the present one bn (delayed by one processing
cycle, i. e.
the time taken to derive the interference estimates), and the unknown sign
of bn+l reduces the number of possible bit triplets and the corresponding
realisations for
each interference vector to 2.
The receiver of Figure 20, using what is conveniently referred to as ISR-RH
mode for reduced hypotheses over the next interference bits, rejects reduced
possibilities
of the interference vector realisations. Compared to the receiver of Figure 17
which
uses the ISR-H mode, it is more sensitive to data estimation errors
over bn-1 and brs and requires only 2 constraints per interferer instead of 3.
Using the previous and current bit estimates of interferers, uncertainty over
the
interference subspace can be reduced and it can be characterized by the
following matrix
of 2NI null-constraints (i.e., N, = 2NI):
I I I" 1 r!
C, = r,n -+1,n r,n -+1,n (55)
where: n Il~,nll' Il~l,nll' ' II r,nll' II-+1,nll '
b` Y` + b` ~ (56)
r,n n-On n 1--1,n'
and where each estimate is reconstructed by reshaping the matrices in Equation
k,n
(38), respectively for k=-1,0,+1. It should be noted that this mode requires a
delay
of one processing cycle for the estimation of the current interference bits.
The ISR-RH mode has the advantage of reducing the number of null-constraints
as compared to the ISR-H mode. A larger number of null -constraints indeed
increases
complexity, particularly when performing the matrix inversion in Equation
(43), and may
also result in severe noise enhancement, especially when the processing gain L
is low.
As the number of strong interferes NI increases in a heavily loaded system,
the number
of null-constraints (2N1 and 3NI) approaches the observation dimension M x(2L -
1) and
the constraint-matrix may become degenerate. To reduce complexity, guarantee
stability
in the matrix inversion of Equation (43), and minimize noise enhancement, the
constraint
CA 02318658 2000-09-12
44
matrix Cn in Equations. (43) and (44) is replaced by the orthonormal
interference
subspace of rank K that spans its column vectors as follows:
Vn = VeC{Cn} _{V i,...,V k,...,V K} (57)
In practice, V n can hardly reflect the real rank of C n . It corresponds to
the
subspace of reduced rank k with the highest interference energy to cancel. To
further
minimize noise enhancement, one can also increase the observation dimension M
x(2L -
1), as will be described later as "X option", and so on.
It should be noted that each of the receivers of Figures 13, 15, 16, 17 and 20
could be modified to perform ISR "after despreading" of the observation vector
Yn, in
effect in much the same way that the generic "after despreading" receiver of
Figure 11
differs from the generic "without despreading" receiver of Figure 9. Such
modified
receivers will now be described with reference to Figures 21 to 26.
Thus, in the ISR-TR receiver shown in Figure 21, which corresponds to that
shown in Figure 13, the delay 45 delays the observation matrix Yn from the
preprocessing unit 18 by 1 bit period and supplies the resulting delayed
observation
matrix Yn_,, in common, to each of the low-power user receiver modules in set
D. Only
one of these receiver modules, 21 H', is shown in Figure 21, since all are
identical. The
observation matrix Yn_, is despread by despreader 19a and the resulting post-
correlation
observation vector Zd is supplied to both the channel identification unit 28Hd
and the
n-1
beamformer 47H . The receiver modules of set I and the constraints-set
generator 42C
are identical to those in the receiver shown in Figure 13, and supply the
matrices
Yl YNI to an adder 60 which adds them to form the total interference
n-1 "' n-1
matrix I_1 which it supplies to each of the receiver modules in set D.
Receiver module 21Hd is similar to that shown in Figure 13 but has a second
despreader 43Hd which uses the spreading code for user d to despread the total
interference matrix In 1 to form the user-specific constraint matrix as a
single column
vector id This despreader 43Hd, in effect, constitutes a user-specific
constraint
PCM,n-1
matrix generator because the constraint matrix is a vector and an inverse
matrix is not
needed. Also, in this case, the channel identification unit 28Hd supplies the
channel
estimate Hd to the beamformer 47Hd.
-n-1
It should be noted that the despread data vector Zd is equal
n-1
to Hd Sri + Id + Nd, where Hd is the channel response for user station 10d,
Sri is
n PCM,n n n
the signal transmitted by the mobile station 10d of user d, and Id is the
interference
-PCM,n
CA 02318658 2000-09-12
component present in the signal Zd as a result of interference from the
signals from the
n
other user stations 10' in set I, where Id is as defined in Equation (14). The
-PCM,n
value s d is additional noise which might comprise, for example, the summation
of
PCM,n
the interference from all of the other users on the system at that time, as
well as thermal
5 noise. "Other users" means other than those covered by the channels in set
I.
As before, the coefficients of the beamformer 47Hd are tuned according to
Equations (16) to (18) and the constraint matrix is defined by a single null-
constraint
(i.e., N,=1) as:
NI
d F Id,i
I -PCM,n )
10 .d _ PCM,n _ i=1 (58) 1~PCM,n ~~ N' P,i
-PCM,n
where the estimate Id is obtained by despreading the matrix I(See Equations
(47)
-PCM,n n
and (48)) with the spreading sequence of the desired low-power user.
15 Figure 22 shows a similar modification to the low-power (set D) receiver
modules
of the "without despreading" ISR-R receiver of Figure 15. In this case, the
output of
the constraint-set generator 42D, as before, comprises the matrices yn 1 yn'1
As
before, only receiver module 21Jd is shown in Figure 22 and is identical to
that shown
in Figure 21 except that the second despreader 43Hd is replaced by a user-
specific
20 constraint matrix generator 43Jd of the kind shown in Figure 12. The
channel
identification unit 28Jd again supplies the vector Ad to the beamformer 47Jd.
The
n-1
bank of despreaders in the user-specific constraint matrix generator 43Ja
despread the
respective ones of the matrices Y. 1 yn'1 to form the vectors
PJ which constitute the columns of the user-specific constraint
PCM,n-1' -PCM,n-1
25 matrix C' cM,_1 and the matrix generator 46Gd produces the corresponding
inverse
matrix QpCM,n-1, Both of these matrices are supplied to the associated
beamformer 47Jd
which uses them and the channel estimate ftd 1 to adjust its coefficients that
are used
to weight the elements of the post-correlation observation vector Zd . As
before, the
-n-1
coefficients are adjusted according to Equations (16) to (18) and the
constraint matrix is
30 defined by NI null-constraints (i.e., N,=N1) as:
;d,l id,Nl
~+d _ [PCM,n PCM,n (59)
PCM,n ~t ,d
~~-PCM,n11 ~ ' ~~-PCM,n~~
CA 02318658 2000-09-12
46
where each estimate Id ` is obtained by despreading the matrix y` of Equation
(50)
-PCM,n n
with the spreading sequence of the desired low-power user.
Figure 23 illustrates the modification applied to the low-power user receiver
module of the ISR-D receiver of Figure 16. Hence, there is no common matrix
inverter.
Instead, in the receiver of Figure 23, each of the receiver modules of set D
has a user-
specific constraint matrix generator 43K which recevies the constraints from
the
constraints-set generator 42E. As illustrated, user-specific constraint matrix
generator
43Kd processes the sets of matrices yn 1,,, yn'"1f , .., ; y,~-il ,~Ii'f to
form the set of
vectors j1 l wf = ~t~`'r,l PN 'f which constitute the columns of user-
-PCM,n-1 -PCM,n-1' -PCM,n-1' '-PCM,n-1'
specific constraint matrix CPCM,n-1~ and the corresponding inverse
matrix QPCM,n-1 which it supplies to the beamformer 47Kd. As before, the
beamformer
47Kd tunes its coefficients according to equations (16) and (18). The
constraint matrix
is defined by N,,NI null-constraints (i. e. , N, = Nf X NI = M x P x NI) as:
d,1,1 id,1,Nl id,N1,1 l~d,M,NJ
j,d /-PCM,n -PCM,n -PCM,n -PCM,n (60)
l. -
PCM,n ^d 1 l
I,1 PCM,I
I PCM n II III PCM,n II II I PCM,n
where each estimate Id,'J is obtained by despreading Pf of Equation (52) with
the
PCM,n -n
spreading sequence of the desired low-power user.
Figure 24 illustrates application of the modification to the ISR-H receiver of
Figure 17. Again, the common constraint matrix generator (43F) is replaced by
a user-
specific constraint matrix generator 43L' in receiver module 21Ld and
similarly in the
other receiver modules of set D. The constraints-set generator 42L' differs
from
constraints-set generator 42F of Figure 17 because its bit sequence generators
63L...... 63LNI use different generating sequences. The sets of matrices
y, n, y>,nl y3,n; =. ; yl ,,, y2 ~, ys ~ from the constraints-set generator
42F' are processed
by the user-specific constraint matrix generator 43Ld to form the
vectors P 1 ~,1 ~r,l= =~,~vr ~.^'r ~,n'' which constitute the columns of the
user-specific
l~, -2~ -3~> >_ln ~ 2,n ' 3,n
constraint matrix CpCMn, and the matrix inverter (not shown) produces the
corresponding inverse matrix QPCM,n. The constraint matrix CPCM,n and the
inverse
matrix QpCM,n are used by the beamformer 470, together with the channel
estimate #d, to adjust its coefficients that are used to weight the elements
of the post-
n
correlation observation vector Zd received from despreader 19a. As before, the
n
CA 02318658 2000-09-12
47
coefficients are adjusted according to Equations (16) and (18) and the
constraint matrix
is defined by 3N1 null-constraints (i. e. , N, = 3N1) as:
l,l ^ ,1,2 ^ ,I,3 ,Nl,l [;d,N1,2 ;d,N1,3
\
Cd _ PCM,n -PCM,n -PCM,n !-PCM,n -PCM,n !-PCM,n (61)
PCM, n d 1 1 I 2 ' I 3 II' ' N1,1 ~I ' I) ^d N1,2 II ' II ^d N1,3 II ' 5
~~~PCM,n~~ CM,nJJ~~tCM,n ~~CM,n ~PCM,n I ~PCM,n
where each estimate Id,`,k is obtained by despreading the matrix y" `k n with
the
-PCM,n
spreading sequence of the desired low-power user.
In this case, each of the bit sequence generators 63L...... 63LN' uses four
generating bit sequences 9 1 (t), g 2(t), 9 3(t) and g 4(t) as shown in Figure
25.
It should be noted that, in any frame of duration 3T in Figure 25, a bit
triplet of
any of the four generating sequences is a linear combination of the others.
Therefore,
any one of the four possible realisations of each interference vector is a
linear
combination of the others and the corresponding null-constraint is implicitly
implemented
by the three remaining null-constraints. The four null-constraints are
restricted
arbitrarily to the first three possible realisations.
Figure 26 illustrates application of the modification to the ISR-RH receiver
of
Figure 20. Again, the common constraint matrix generator 43G of Figure 20 is
replaced
by a set of user-specific constraint matrix generators, 43M' in receiver
module 21Md and
similarly in the other receiver modules of set D. The constraints-set
generator 42M
shown in Figure 26 differs slightly from that (42G) shown in Figure 20 because
each of
the bit sequence generators 63M',...63M" in the receiver of Figure 26 generate
the bit
sequence g t.l^,
n
The user-specific constraint generator 43Md processes the pairs of constraint-
set
matrices ykl~, y~~; ...; yk ~, y"~ n from the channel identification units
59M...... 59MN',
respectively, by to produce the corresponding set of
vectors P, 1AI P l~ ..= f~1~`l f~1,"2 which constitute the columns of the user-
specific
PCM,n' PCM,n' ' PCM,n' -PCM,n
constraint matrix CpCM,n.? and to produce the corresponding inverse matrix
QPCM,n=
are used by the
The constraint matrix Cd and the inverse matrix QP~Mn
PCM,n
beamformer 47Md, together with the channel estimate Hd, to adjust its
coefficients that
n
are used to weight the elements of the post-correlation observation vector Zd
received
n
from despreader 19 . As before, the coefficients are adjusted according to
Equations
CA 02318658 2000-09-12
48
(16) to (18) and the constraint matrix is defined by 2NI null-constraints
(i.e., N, = 2NI)
as follows:
id,l,k, l ;d,l,kz jd,Nl,k, ;d,Nl,ki
d -PCM,n -PCM,n -PCM,n /-PCM,n (62)
> >,d > ,.d l !
1~, CM ,n II `I PCM,n I` II -PCM n II II -PCM n II
where each pair of estimates Id ` k, and Id `,k2 is obtained by despreading
the
-PCM,n -PCM,n
matrices yk n and yk n, respectively, with the spreading squence of the
desired low-
~
power user.
Inter-Symbol Interference (ISI) Rejection
In any of the above-described embodiments of the invention it may be desirable
to reduce inter-symbol interference in the receiver modules in set D,
especially when low
processing rates are involved. As noted in the PCM model where despreading
reduces
ISI to a negligible amount, for a large processing gain,
yd" yd = 0 and yd _yd 0, Hence, the before despreading spatio-temporal
-O,n--1,n -O,n +1,it
beamformer yyd approximately implements the following additional constraints:
n
Wd"~ - 0,
n --l,n (63)
Wd"Yd - 0.
-n -+l,n
Accordingly, it rejects interference and significantly reduces ISI. Complete
ISI
rejection can be effected by modifying the receiver to make the set of the
channel
parameter estimators available to the constraints-sets generator 42 for
processing
in parallel with those of the set I receiver modules. The resulting additional
constraint
matrix and inverse matrix would also be supplied to the beamformer 47d and
taken into
account when processing the data.
In such a case, the following matrix can be formed:
II Y II ~'
d _ n l,n n -+l,n
CISI,n ~ ~ ~ ~ ~ ~
II n- l,nll II n+l,nll (64)
and the following 2 x 2 matrix
CA 02318658 2000-09-12
49
/] (~' H 1 (
7~ISI,n ~ Shn CSl,n 65)
inverted to obtain the constrained spatio-temporal beamformer yyd before
despreading
n
by:
iiSl,n - IM = (ZL-u - CS1,n Li I,n ~' Sl,n 1 AdH (66)
(67)
d d ~n - ~ISI,n ~n '
nd ,d
Wd = n I-o,n (68)
-n 1. ~,dH Hd kd
-O,n n-O,n
The projector IIn is produced in the manner described earlier according to
Equations (43) and (44). The projector nn orthogonal to both C, In and C'n, is
formed
and then the low-power response vector yd projected and normalized to form the
O,n
beamformer which fully rejects ISI from the processed user d and interference
from the
NI users in set I.
It should be noted that, if the suppression of strong interferers is not
needed, ISI
can still be rejected by the following beamformer:
d
Wd _ H1SI,n--O n (V7Ln)
-n
[Xd x
~'nHISI,n-O,n
where projector II n in equations 47 - 49 would be set to identity and hence
would have
no effect. This is the same as setting the matrix Cn to null matrix. If the
projector ii~lSjn in the above equation is replaced by an identity matrix,
(equivalent to
setting matrix Csln to null matrix) then a simple MRC beamformer is
implemented
before despreading. A receiver module using such an MRC beamformer is
illustrated
in Figure 27 and could be used to replace any of the "contributor" only
receiver
modules, such as receiver modules 21', ..., 211' in Figure 9 et seq. The
receiver
module shown in Figure 27 is similar to receiver module 21Ad of Figure 9
except that
the ISR beamformer 47A' is replaced by an MRC beamformer 27Nd which implements
the equation
yyd - ~ (70)
n 11 i`` 112
o,n
CA 02318658 2000-09-12
It is also envisaged that the receiver module of Figure 27 using the MRC
beamformer denoted Wd in the following, could be incorporated into a STAR
which
MRC,n
did not use ISR, for example the STAR described in reference [13].
5 Joint ISR Detection
In the foregoing embodiments of the invention, ISR was applied to a selected
set
D of users, typically users with a low data-rate, who would implement ISR in
respect
of a selected set I of high-rate users. Although this approach is appropriate
in most
cases, particularly when the number of high-rate users is very low, there may
be cases
10 where the mutual interference caused by other high-rate users is
significant, in which
case mutual ISR among high-rate users may be desired as well. Such a situation
is
represented by user sets M 1 and M2 of Figure 8. Hence, whereas in the
foregoing
embodiments of the invention, the receiver modules of set I do not perform ISR
but
merely supply constraints sets for use by the receiver modules of set D, it is
envisaged
15 that some or all of the receiver modules in set Ml and M2 also could have
beamformers
employing ISR. Such a Joint ISR (J-ISR) embodiment will now be described with
reference to Figure 28, which shows only one receiver module, 21', as an
example. In
any symbol period, each such receiver module 21' (i) receives a constraint
matrix Cn 1 and an inverse matrix Qn_I and uses them in suppressing
interference,
20 including its own interference component, and (ii) contributes constraints
to the
constraint matrix n and inverse matrix Qn which will be used in the next
symbol
period. In the case of ISR-H mode receivers, which use hypothetical symbols,
it is
merely a matter of replacing the receiver modules in set I with receiver
modules 21d
having ISR beamformers, since the constraints sets are generated by the
hypothetical
25 symbols from the bit sequence generators 63...... 63N'. Contrary to other
ISR modes
which require decision-feedback, in the ISR-H mode receiver module, no
processing
delay is required for one user to cancel another. Hence, ISR-H can be
implemented to
cancel strong interferers without successive interference cancellation or
multi-stage
processing, which will be described later.
30 Using Cn and Qn already computed, the ISR combiner for each interferer can
be obtained readily by:
~
Wn = CnQn R3 . (i_,) +, 9 71
CA 02318658 2000-09-12
51
where Rk =[0, ..., 0, 1, 0, ..., 0]T is a(3NI)-dimensional vector with null
components
except for the k-th one. This implementation has the advantage of implicitly
rejecting
ISI among strong interferers with a single 3N1 x 3NI-matrix inversion.
For the ISR-TR, ISR-R and ISR-D modes, each receiver module, in effect,
combines a receiver module of set I with a receiver module of set D, some
components
being omitted as redundant. Referring again to Figure 28, which shows such a
combined
receiver module, the preprocessor 18 supplies the observation matrix Y,, to a
1-bit delay
45 and a first vector reshaper 44/1, which reshapes the observation matrix Y,,
to form
the observation vector L. A second vector reshaper 44/2 reshapes the delayed
observation matrix Yõ_, to form delayed observation vector Y_,. These matrices
and
vectors are supplied to the receiver module 21 P' and to others of the
receiver modules,
together with the constraint matrix Cn_1 and the inverse matrix Q,_I from a
common
constraint matrix generator 43P, which generates the constraint matrix Cõ_,
and the
inverse matrix Q,_, from the constraints-set Cn_I produced by constraint set
generator 42P.
The receiver module 21 P' comprises a despreader 19', a channel identification
unit
28P', a power estimation unit 30P', and a decision rule unit 29P', all similar
to those of
the above-described receiver modules. In this case, however, the receiver
module 21P'
comprises two beamformers, one an ISR beamformer 47P' and the other an MRC
beamformer 27P', and an additional decision rule unit 29P/2' which is
connected to the
output of MRC beamformer 27P'. The ISR beamformer 47P' processes the delayed
observation vector Y to form the estimated signal component estimate sn_1 and
supplies it to the first decision rule unit 29P', the power estimation unit
30P', and the
channel identification unit 28P', in the usual way. The decision rule unit
29P' and the
power estimation unit 30P' operate upon the signal component estimate sn to
derive
the corresponding symbol estimate gn_1 and the power estimate and supply them
to other parts of the receiver in the usual way.
The despreader 19' despreads the delayed observation matrix Yn_, to form the
post-
correlation observation vector Zn 1 and supplies it to only the channel
identification unit
28P', which uses the post-correlation observation vector Zi and the signal
component
n-i
estimate to produce both a spread channel estimate and a set of channel
parameter
o,n-1
estimates At the beginning of the processing cycle, the channel identification
unit
28P' supplies the spread channel estimate y` to both the ISR beamformer 47P'
and
O,n-1
~....a..m.w......,.W.~..w..~.,,~..._...._
_.......m~,,..~.~~..,.~~..~.____...___ _
CA 02318658 2000-09-12
52
the MRC beamformer 27P' for use in updating their coefficients, and supplies
the set of
channel parameter estimates to the constraints-set generator 42P.
The MRC beamformer 27P' processes the current observation vector Y to
produce a"future" signal component estimate sMRC,n for use by the second
decision rule
unit 29P/2' to produce the "future" symbol estimate MRC,W which it supplies to
the
constraints-set generator 42P at the beginning of the processing cycle. The
constraints-
set generator 42P also receives the symbol estimate bn 1 from the decision
rule unit 29',
but at the end of the processing cycle. The constraints-set generator 42P
buffers the
symbol BMRd,n from the decision rule unit 29P/2' and the symbol estimate f ~ 1
from
the decision rule unit 29P' at the end of the processing cycle. Consequently,
in a
particular symbol period n-1, when the constraints-set generator 42P is
computing the
constraints-set Cn-1 it has available the set of channel parameter estimates
J<_,, the
"future" symbol estimate b` the "present" symbol estimate b` and the "past"
MRC,W MRC,n-1
symbol estimate bn 2, the latter two from its buffer.
Each of the other receiver modules in the "joint ISR" set supplies its
equivalents
of these signals to the constraints-set generator 42P. The constraints-set
generator 42P
processes them all to form the constraints set ccrt-1 and supplies the same to
the
constraint matrix generator 42P, which generates the constraint matrix C n and
the
inverse matrix a and supplies them to the various receiver modules.
The constraints-set generator 42P and the constraint matrix generator 43P will
be
constructed and operate generally in the same manner as the constraints-set
generator 43
and constraint matrix generator 42 of the embodiments of the invention
described
hereinbefore with reference to Figures 9 to 27. Hence, they will differ
according to the
ISR mode being implemented.
When the constraints-set generator 42P of the receiver of Figure 28 is
configured
for the ISR-D mode, i.e. like the constraints-set generator shown in Figure
16, the
constraint matrix Cn supplied to the ISR beamformer 47P' contains enough
information
for the beamformer 47P' to estimate the channel parameters itself. Hence, it
forwards
these estimates to the channel identification unit 28P' for use in improving
the channel
parameter estimation and the set of channel estimates produced thereby.
An ISR-RH receiver module will use a similar structure, except that the one-
bit
delay 45 will be omitted and the constraints-set generator 42P will use the
previous
symbol, estimate bn_,, the current MRC symbol estimate bMRC.n and the two
CA 02318658 2000-09-12
53
hypothetical values for "future" symbol b~+l to produce current symbol
estimate bn,
Modification of the receiver module shown in Figure 28 to implement such a
"ISR-RH
mode" will be straightforward for a skilled person and so will not be
described hereafter.
In order to implement J-ISR, a more general formulation of the constraint
matrix
is required. The general ISR constraint matrix counting N, constraints, is as
follows:
' N` (72)
C= C'1 c C
n II Cn l I~ ,..., II C~ II '..., II Cn N II
where thej-th constraint C is given by:
-n,~
(73)
n j k,n
(u fk)E5.
where S; defines a subset of diversities which form the j-th constraint when
summed.
As shown in Table 2, the sets Sj, j = 1, ===, N, are assumed to satisfy the
following
restrictions:
S = S1US2U...USN={(u,f,k)I uNl;f=1,=-=,N~ k=-1,0,+1},
and
S1nS2n...nSN = 0
0 being the empty set. Table 1 defines the sets S;, j=1, ===, N, for all
presented ISR
modes of operation.
The objective signal belongs to the total interference subspace as defined by
the
span of the common constraint matrix C n . Therefore, to avoid signal
cancellation of
the desired user d by the projection:
nd d H n - IM * (2L-1) - ~nQnCn , (74)
the desired-signal blocking matrix Cd is introduced, as given by:
n
~'d = "''1 ni n'~` !75)
n nj ~i A
where:
s ~ Yn , (76)
nj k,n
(a,f,k)ES.AS
CA 02318658 2000-09-12
54
with Sd ={(u,f,k) I u = d; f = 1, ..., N; k = 0}. Normally Sd is a small
subset of S
and Cd is very close to C,
n n
Joint multi-user data estimation and channel gain estimation in ISR-D
Neglecting the signal contributions from the weak-power low-rate users, and
limiting to the signals of the NI interferers, yi can be formulated as:
n
NI n'i
y = E WnJf,nn + Npth (77)
i=1 f=1
1j-~ ~/~ NIj~ I =,' Nj~ T A
p
= ~'n I~nJl.n~ ~ ~nJNfn~... `Yn Jl,n~ ...'Yn JNn, + ~ (78)
= C r + (79)
n-n. n
where r is a NfNI x 1 vector which aligns channel coefficients from all
fingers over
n
all users. Estimation of r' may be regarded as a multi-source problem:
n
Pn = QnCn y . (80)
This constitutes one step of ISR-D operations and allows joint multi-user
channel
identification.
Multi-stage processing may be used in combination with those of the above-
described embodiments which use the above-described joint ISR, i.e. all except
the
receivers implementing ISR-H mode. It should be appreciated that, in each of
the
receivers which use decision-feedback modes of ISR (TR,R,D,RH), coarse MRC
symbol
estimates are used in order to reconstruct signals for the ISR operation.
Because they
are based upon signals which include the interference to be suppressed, the
MRC
estimates are less reliable than ISR estimates, causing worse reconstruction
errors.
Better results can be obtained by using multi-stage processing and, in
successive stages
other than the first, using improved ISR estimates to reconstruct and perform
the ISR
operation again.
CA 02318658 2000-09-12
Operation of a multi-stage processing receiver module which would perform
several iterations to generate a particular symbol estimate is illustrated in
Figure 29,
which depicts the same components, namely constraint-sets generator 42P,
constraint
matrix generator 43P, ISR beamformer 47P' and decision rule unit 29P/1', MRC
5 beamformer 27P' and decision rule unit 29P/2', in several successive symbol
periods,
representing iterations 1, 2,...,NS of frame n which targets the symbol
estimate 6 n _1 for
user station 10'. Iteration 1, if alone, would represent the operation of the
receiver
module 21' of Figure 28 in which the constraints-set generator 42P uses the
coarse
symbol estimates g`RCn-1 previously received from the second decision rule
unit 29P/2'
M
10 (and others as applicable) and buffered. In each iteration within the
frame, the other
variables used by the constraints-set generator 42P remain the same. These
variables
comprise, from at least each "contributor" receiver module in the same joint
processing
set, the previous symbol estimate 6 n_2, the set of channel parameters and the
current MRC symbol estimate LMRCn, Likewise, the spread channel estimate and
o,n-1
15 the delayed observation vector Y_, used by the ISR beamformer 47P' will
remain the
same.
In iteration 1, the constraint matrix generator 42P generates constraint
matrix C_1(1) and the inverse matrix Qõ_,(1) and supplies them to the
beamformer 47P'
which uses them, and the spread channel estimate y' to tune its coefficients
for
o,n-1
20 weighting each element of the delayed observation vector Y_,, as previously
described,
to produce a signal component estimate which the decision rule unit 29P/ 1'
processes to
produce the symbol estimate 6 n_1(1) at iteration 1, which would be the same
as that
generated by the receiver of Figure 28. This symbol estimate bn_1(j) is more
accurate
than the initial coarse MRC estimate bMRC,n i(0) so it is used in iteration 2
as the input
25 to the constraints-set generator 42P', i.e., instead of the estimate coarse
MRC
CA 02318658 2000-09-12
56
beamformer 27P' estimate. As a result, in iteration 2, the constraint matrix
generator
42P produces a more accurate constraint matrix Cn_1(2) and inverse matrix a_I
(2).
Using these improved matrices, the ISR beamformer 47P' is tuned more
accurately, and
so produces a more accurate symbol estimate gn_1(2) in iteration 2. This
improved
symbol estimate is used in iteration 3, and this iterative process is repeated
for a total
of NS iterations. Iteration NS will use the symbol estimate b;~_1(N -1)
produced by the
preceding iteration and will itself produce a symbol estimate bn 1(NS) which
is the target
symbol estimate of frame n and hence is outputted as symbol estimate fn 1
This symbol estimate bn 1 will be buffered and used by the constraints-set
generator 42P in every iteration of the next frame (n+1) instead of symbol
estimate 6 n_2. Other variables will be incremented appropriately and, in
iteration 1 of
frame n+], a new coarse MRC beamformer 27P' symbol estimate bMRC,n+I will be
used
by the constraints-set generator 42P. The iterative process will then be
repeated,
upgrading the symbol estimate in each interation, as before.
It should be noted that, in Figure 29, the inputs to the channel
identification unit
28P' use subscripts which reflect the fact that they are produced by a
previous iteration.
These subscripts were not used in Figure 28 because it was not appropriate to
show the
transition between two cycles. The transition was clear, however, from the
theoretical
discussion.
One stage ISR operation can be generalized as follows:
Sn(l) = SMRC,n WMRC,n~n(I)yn(1)' Un(1) = Qn(1)6n(1)H~' (81)
where Sn(1) is the ISR estimate from first ISR stage, SMRCn is the MRC signal
estimate,
and the constraint matrices 6n(1), 6n(1), and Qn(l) are formed from MRC
estimates
at the first stage. Generalizing notation, the signal estimate at stage NS may
be derived
after the following iterations:
CA 02318658 2000-09-12
57
Sn(2) = SMRC,n - WMRC,n~n(2)Un(2), Un(2) - Qn(2)Cn(2)HY ~
(82)
Sn(N) = SMRC,n - Wdx C n(N)U lNs~. U(N) - Qn(N9l..nlN)y~ ,
MRC,n n n n
The multistage approach has a complexity cost; however, complexity can be
reduced because many computations from one stage to the next are redundant.
For
instance, the costly computation õo) could instead be tracked because u(j) -
õ(j-1) if
the number of symbol estimation errors does not change much from stage to
stage, which
can be expected in most situations.
In practice, the receiver of Figure 28 could be combined with one of the
earlier
embodiments to create a receiver for a "hierarchical" situation, i. e. , as
described
hereinbefore with reference to Figure 8, in which a first group of receiver
modules, for
the weakest signals, like those in set D of Figure 8, for example, are
"recipients" only,
i. e. , they do not contribute to the constraint matrix at all; a second group
of receiver
modules, for the strongest signals, like the receiver modules of set I in
Figure 8, do not
need to cancel interference and so are "contributors" only, i. e. , they only
contribute
constraints-sets to the constraint matrix used by other receiver modules; and
a third set
of receiver modules, for intermediate strength signals, like the receiver
modules of sets
M2 of Figure 8, are both "recipients" and "contributors", i.e. they both use
the
constraint matrix from the set I receiver modules to cancel interference from
the
strongest signals and contribute to the constraint matrix that is used by the
set D receiver
modules. Generally, this approach is referred to as "Group ISR" (G-ISR) and
the
equations for the constraint matrices and inverse matrices comprising the set
K C C used by the ISR beamformers in the different
n { AOutset,n ~ QOutset,n ~ Inset,O Qlnset,n
receivers are as follows:
CA 02318658 2000-09-12
58
(83)
" ' QOutset,n ~COuset,n~Outset,n~ 9
H HOutset,n IM * (2L-1) - COutset,nQOulset,nCOutset,n~ (84)
Clnset,n 11Outset,ncInset,n, (85)
d" 1 86
(?Inset,n ~CInset,Slnset,n) ( )
d = /rd H 87 HInset,n - IM * (2L-1) - ~"lnset,nQlnset,nelnset,n1 ( )
d d n (88)
~n ~Inset,nOutset,n
d^
Wd = ~~'n = Ild X -o,n . (89)
~,d n ~ ,d
-n ~,d x, d2 2 jld:,d
I"_O,n n'_o,n n n 1"-O,n
It should be noted that normalization of the columns of Clnset,n and Couuet,n
is
implicit.
A receiver module for set D will set IIInset in Equation (88) to identity
which
means that only "outset" interference will be cancelled. Otherwise, the
processing will
be as described for other receivers of set D.
A receiver in set M1 does not need to cancel "outset" interference, but does
need
to cancel "inset" interference. Consequently, it will set IIouUet in Equation
(88) to
identity so that only inset interference will be cancelled. This corresponds
to the joint
ISR embodiment described with reference to Figure 28.
Finally, a receiver in set I does not need to cancel any interference.
Consequently, it will set both IIrnset and IIouftet to identity, which means
that nothing
will be cancelled. This corresponds to the group I receiver modules 21'...21"I
described
with reference to Figures 9, 11, 13, 15-17, 20-24 and 26.
Successive versus Parallel Detection
Although the embodiments of ISR receivers described hereinbefore use a
parallel
implementation, ISR may also be implemented in a successive manner, denoted S-
ISR,
CA 02318658 2000-09-12
59
as illustrated in Figure 30. Assuming implementation of successive ISR among
NI
interferers, U users, and assuming without loss of generality that are sorted
in order of
decreasing strength such that user 1 is the strongest and user NI is the
weakest user,
when processing user i in S-ISR, the ISR estimate can be computed as:
Sn = SMRCn - WMRC,n~>nUn(Z) Un(Z) = Qn Cin ~~ (90)
where Ci n spans only the subspace of users 1, -==, i-1 Z, Qn is the
corresponding inverse
and where C` is the user specific constraint matrix. Clearly, C` is no longer
yn t,n
common for all users, which entails expensive matrix inversion for each user.
However,
with ISR-TR this inversion is avoided, since C"ff CI is a scalar, and S-ISR-TR
is a good
alternative to its parallel counterpart, ISR-TR. Other ISR modes may take
advantage of
the conimon elements of Cd . n from one processing cycle to the next using
matrix
inversion by partitioning.
It should also be appreciated that the different ISR modes may be mixed,
conveniently chosen according to the characteristics of their signals or
transmission
channels, or data rates, resulting hybrid ISR implementations (H-ISR). For
example,
referring to Figure 8, the sets I, M 1 and M2 might use the different modes
ISR-H, ISR-
D and ISR-TR, respectively, and the receiver modules in set D would use the
different
modes to cancel the "outset" interference from those three sets. Of course,
alternatively
or additionally, different modes might be used within any one of the sets.
In all of the above-described embodiments of the invention, the channel
identification units 28d in the ISR receiver modules use the post-correlation
observation
vector Zn to generate the spread channel estimate ~ -n
(by spreading H ).
Unfortunately, the interference present in the observation matrix Yn is still
present in the
Z And also user i if ISR rejection is desired.
CA 02318658 2000-09-12
post-correlation observation vector Zi (see Equation (14)) and, even though it
is
n
reduced in power by despreading, it detracts from the accuracy of the spread
channel
estimate yd , As has been discussed hereinbefore, specifically with reference
to
-o,n
Equations (83) to (89), the ISR beamformer 47d effectively constitutes a
5 projector ~ lid and a tuning and combining portion
'-0n
I`HW- I`
,d
10 which, in effect, comprises a residual MRC beamformer Ed = o,n
n IIf' IIZ
,n
Figure 31 illustrates a modification, applicable to all embodiments of the
invention
described herein including those described hereafter, which exploits this
relationship to
improve the spread channel estimate yd (or unspread channel estimate Hd) by
using
~,n -n
15 the projector IIn to suppress the interference component from the
observation vector Y.
In the receiver module of Figure 31, the ISR beamformer 47Qd is shown as
comprising
a projector 100d and a residual MRC beamformer portion 27Qd. The projector
100d
multiplies the projection ~ jid by the observation vector , to produce the
"cleaned"
observation vector yIId and supplies it to the residual MRC beamformer 27Qd,
which
n
20 effectively comprises a tuner and combiner to process the "cleaned"
observation
vector yn,d and produce the signal component estimate sn from which decision
rule
n
unit 29Qa derives the symbol estimate bn d in the usual way.
The "cleaned" observation vector ylLd is reshaped by matrix reshaper 102Qd to
n
form "cleaned" observation matrix yII d which despreader 19d despreads to form
the
CA 02318658 2000-09-12
61
"cleaned" post-correlation observation vector ZII,d for application to the
channel
n
identification unit 28Qd for use in deriving the spread channel estimate yd ,
The new "cleaned" vector resulting from the projection of the observation
vector y by nn is defined as follows:
n
Y",d = Ildy = IId y" + N (IId yd )S d +(IIdN ) = Y ,dS d + Nn,d. (91)
_n '~n n _n -n n~n n n-n _O,n -n
uE (1,...,N/)U{d}
The new observation vector is free from the interferers and ISI and contains a
projected version of the channel vector yn,d. Without being a condition, it is
reasonable
-O,n
to assume that the projector nn is almost orthogonal to the channel vector,
especially
in high processing gain situations and/or in the presence of few interferers,
and therefore
consider that yn,d _ yd , When despreader 19a despreads yr-,d with the
spreading
-O,n -O,n n
sequence of the desired user d, it produces an interference-free projected
post-correlation
observation vector zfl,n which the channel identification unit 28Qd uses to
create the
n
channel estimate n
` to use in updating the coefficients of the residual MRC
beamformer portion 27Qd.
With respect to the new observation vectors yn,d and _7fl,n, before and after
-n -n
despreading, respectively, the ISR and DFI steps in STAR are modified as
follows:
FT1,d i,d
Wd = 2~" O,n c I-"0'n (92)
-n II `~Idll2 I +~dl
10,n -O,n n-O,n
sn = Real{Wd" -Yn R=d}, (93)
n
tY = Hd + (~T'd - l7 gIs~. (94)
-n+ n n n
The equivalence between the two expressions of the beamformer coefficients in
Equation (92) due to the nilpotent property of projections should be noted. In
more
adverse near-far situations, the modification illustrated in Figure 31 allows
more reliable
channel identification than simple DFI and hence increases near-far
resistance. If
CA 02318658 2000-09-12
62
necessary, this new DFI version will be termed II-DFI. It is expected to be
suitable for
situations where the interferers are moderately strong and when the null
constraints cover
them all. For simplicity of discussion, projection of the observation will
become implicit
without reference to yd
n~ Znn
or to the corresponding modifications in STAR-ISR
operations.
Expanding Dimensionality (X-option)
When the number of users becomes high compared to the processing gain, the
dimension of the interference subspace becomes comparable to the total
dimension (M(2L
-1)). The penalty paid is an often devastating enhancement of the white noise.
Unlike
ISR-TR, which always requires a single constraint, other DF modes, namely ISR-
R and
ISR-D, may suffer a large degradation because the number of constraints these
modes
require easily becomes comparable to the total dimension available. However,
the
dimension may be increased by using additional data in the observation. This
option also
allows for complete asynchronous transmission and for the application of ISR
to Mixed
Spreading Factor (MSF) systems.
The matched-filtering observation vector Y is generated to include additional
past
spread data which has already been processed. If the model is expanded to
include past
processed NX symbols and arrive at a total temporal dimension N,. =(NX+1)L-1,
the
observation becomes:
y N )u f Apth N
-n NX+1 U -n NY+1 n-NX+1 U f
Y + Y"f + 1rh (95)
n =n
=n Y u_1 f_1 mth u_1 f1
_n _n _n
CA 02318658 2000-09-12
63
where double underlining stresses the extended model. It should be noted that
yuf is
-i
overlapping temporally ynJ and only the first ML samples of the past frames n-
1, n-2,
Jf1
etc. are used; however the same syntax is used for simplicity of notation.
As an example, application of the X option to ISR-D, referred to as ISR-DX,
requires the following constraint matrix:
- 2cn cn 2=n _n
Cn (96)
- `,~
II l 1 II ~...~ II I,Nfll ~...~ II 1 11 1 1 NjII
-n -n -n -n
The extended vectors in Equation (96) have been treated in the same way as
those in
Equation (95), i.e., by concatenating reconstructed vectors from consecutive
symbols in
the extended frame and by implicitly discarding overlapping dimensions in the
concatenated vectors. Clearly, extension of the observation space leaves
additional
degrees of freedom and results in less white noise enhancement. However, it
may exact
a penalty in the presence of reconstruction errors.
Although the X-option was illustrated in the case of ISR-D, its application to
the
remaining DF modes is straightforward. It should also be noted that the X-
option allows
for processing of more than one symbol at each frame while still requiring one
matrix
inversion only. The duration of the frame, however, should be small compared
to the
variations of the channel.
In the above-described embodiments, ISR was applied to a quasi-synchronous
system where all temporal delays were limited to 0 < T< L. Although this model
reflects well the large processing gain situation, where the limit (L - oo),
allows for
placing a frame of duration 2L - I chips which fully cover one bit of all
users, including
delay spreads. With realistic processing gains, and in particular in the low
processing
CA 02318658 2000-09-12
64
gain situation, this model tends to approach a synchronous scenario. Using the
X-option
serves as a method supporting complete asynchronous transmission.
Referring to Figure 32, assuming that the users of the system have processing
gain L as usual, the transmitted signal of any user is cyclo-stationary and a
possible time-
delay of the primary path Tl is therefore 0 < T, < L where possible time
delays of
remaining paths are T, < r2 < ... < L + OT where OT is the largest possible
delay
spread considered. To ensure that the frame covers at least one bit of all
users, the
frame must at least span L + OT in the despread domain and therefore 2L + OT
in the
spread domain. The observation should be extended slightly beyond that to ease
interpolation near the edges of the frame.
Multi-Modulation (MM), Multi-Code (MC), and Mixed Spreading Factor (MSF)
are technologies that potentially can offer mixed-rate traffic in wideband
CDMA. MSF,
which has become very timely, was shown to outperform MC in terms of
performance
and complexity and is also proposed by UMTS 3 third generation mobile system
as the
mixed-rate scenario. Application of ISR to MSF as the mixed rate scenario
considered
herein will now be discussed.
In MSF, mixed rate traffic is obtained by assigning different processing gains
while using the same carrier and chip-rate. In a system counting two groups of
users,
a low-rate (LR) and a high rate (HR) group, this means that every time a LR
rate user
transmits 1 symbol, a HR user transmits 2r + 1 HR symbols, r = Li/L,, being
the ratio
of the LR processing gain to HR processing gain. This is illustrated in Figure
33 with
r = 2.
Therefore, fitting the ISR frame subject to LR users or in general the lowest-
rate
users ensures that also at least r HR symbols are covered when HR and LR have
the
same delay spread. The ISR generalizes readily to this scenario regarding
every HR user
._.. . . __~ ~ _~.....~~..~,~.,,~ M. Y .. . . .._ ....,~n~.....,..~.__.~..-
..._.. _ _
CA 02318658 2000-09-12
as r LR users. In Figure 33, the grey shaded HR/LR bits symbolize the current
bits to
be estimated; whereas, former bits have already been estimated (ISR-bits) and
future bits
are unexplored. It should be noted that current HR bits should be chosen to
lie at the
end of the frame.
5
Multicode
It is envisaged that a user station could use multiple codes, N,,, in number,
each
to transmit a different stream of symbols. Figure 34 illustrates this
modification as
applied to a"without despreading" receiver module 2 1 R d for receiving such a
multicode
10 signal and using ISR cancellation to cancel interference from other users.
The receiver
module shown in Figure 34 is similar to that shown in Figure 9 except that,
instead of
a single ISR beamformer 47d; the receiver module of Figure 34 has a bank of
ISR
beamformers 47Rdj ... d " for extracting si nal com onent estimates s a,l
dr''"
,47R g P n ,...,sn
respectively, and supplying them to a bank of decision rule units
29Rd,',...,29Ra'NT,
15 respectively which produce a corresponding plurality of symbol estimates
bn'1nN^'.
Likewise, the receiver module 21 Rd has a bank of despreaders 19d,1 '_õ '19d>^
m each of
which uses a respective one of the multiple spreading codes of the
corresponding user
d to despread the observation matrix Yõ from the preprocessing unit 18 to
produce a
corresponding one of a multiplicity of post-correlation observation
20 vectors which are supplied to a common channel identification unit 28Rd.
n n
It should be appreciated that the post-correlation observation vectors share
the same
channel characteristics, i. e. , of the channel 14d between user station 10d
and the base
station antenna array. Consequently, only one channel identification unit 28Rd
is
required, which essentially processes the plural signal component
25 estimates sn ~' ,,..,gn'N"' and the post-correlation observation vectors
and, in essence,
CA 02318658 2000-09-12
66
averages the results to produce a single channel estimate I~-'d representing
the physical
n
channel 14d. The channel identification unit 28Rd has a bank of spreaders (not
shown)
which spread the channel estimate #d using the multiple spreading codes to
create a set
n
of spread channel estimates yd=1 .,. ~~'^" which it supplies to the ISR
o~, ,---On ,
beamformers 47Rd ',...,47Rd,' T, respectively. Likewise, the power estimation
unit 30Rd
is adapted to receive plural signal component estimates sd,l d'^'. and
essentially
n ,...,Sn average their powers to produce the power estimate ,T, nd,
While using all of the multiple codes advantageously gives a more accurate
channel estimate, it requires many expensive despreading operations. In order
to reduce
the cost and complexity, the receiver module 21 Md may use only a subset of
the
spreading codes.
It can be demonstrated that the multiple spreading codes can be replaced by a
single spreading code formed by multiplying each of the multiple spreading
codes by the
corresponding one of the symbol estimates 6n 1,...,6nN'^ and combining the
results.
Figure 35 illustrates a receiver module which implements this variation. Thus,
the
receiver module 21R' shown in Figure 35 differs from that shown in Figure 34
in that
the bank of despreaders 19d.1,.,.,19d,N are replaced by a single despreader
19d 1 which
receives the symbol estimates f n ',,..,6n N'" and multiplies them by the
multiple spreading
codes to form a compound spreading code, which it then uses to despread the
observation matrix Yõ and form a single post-correlation observation vector
Zd,a, The
n
channel identification unit 28Rd does not receive the signal component
estimates but
instead receives the total amplitude ,n from the power estimation unit 30Rd.
This
serves as a compound signal component estimate because the use of the compound
code
is equivalent to modulating a constant " 1" or a constant "-1 " with that
code, as will be
formulated by equation later. The channel identification unit 28Rd processes
the single
CA 02318658 2000-09-12
67
post-correlation observation vector Zd>a to produce a single channel estimate
Hd and
n n
spreads it, as before, using the multiple spreading codes to form the multiple
spread
channel estimates ? 1 ... ~~'^~ for use by the beamformers 47Rd '...,47Rd N as
before.
O,n' '-o,rz
The theory of such multicode operation will now be developed. Assuming for
simplicity that each user assigned the index u transmits Nstreams of DBPSK
data b",1(t), ,,,, b" N~(t), using Nn, spreading codes c" '(t), ..., c"'N-(t),
each spread stream
can be seen as a separate user among a total of U x Naccess channels, assigned
the
couple-index (u,l). The data model can then be written as follows:
u N +1 U N Nf +1
n n+k k,n n n n+k rt k,n n~
Yn ~~ub u'1 I'1 + NP~ ~ub u'1 '/~ ~lf + Np~ (97)
u=1 1=1 k=-1 u=1 1=1 f=1 k=-1
where the canonic u-th user l-th code observation matrices yk,n,f from finger
f are
obtained by Equations (3) and (4) of with X(t) in Equaiton (3) replaced,
respectively for
k = -1,0, +1,
by:
Xk'1 At) = Rm8(t -7p(t)) g1Rr(t)c " l(t). (98)
In the equation above, R=[0, ...., 0, 1, 0, ..., 0J' is an M-dimensional
vector with
null components except for the m-th one and b(t) denotes the Dirac impulse.
Reshaping
matrices into vectors yields:
U N +1 U N Nf +1
Y = E E E ~"b "'l + NPth = E E E E ~"b ",l y"'lJ + N ``` (99)
n n n+k_k n n n n+k f n-k n n~
u=1 1=1 k=-1 u=1 1=1 f=1 k=-1
The particularity of the above multi-code model, where N. codes of each user
share the same physical channel H" and the same total received power (On)2
should be
n
noted. Exploitation of these common features will be discussed hereinafter in
relation
to adapting of the power-control and the channel-identification procedures to
the multi-
code configuration. The ISR combining step will now be explained.
Considering first joint ISR combining among the group of N interferers, the
regular ISR modes, namely TR, R, D, H and RH easily generalize to the new
multi-code
CA 02318658 2000-09-12
68
configuration of N,,,NI users instead of NI, as shown in Table 3. ISR
combining
operations are carried out as usual using the constraint and blocking
matrices Cn and &n ,1', respectively. It should be noted, however, that a
further
dimension of interference decomposition and rejection arises over the codes of
each user,
yielding two additional ISR modes. The new modes depicted in Table 3 and
referred to
as MCR and MCD (multi-code R and D) characterize interference from the entire
set of
codes of each user by its total realization or by the decomposition of this
total realization
over diversities, respectively. They combine the R and D modes, respectively,
with the
TR mode by summing the corresponding constraints over all the multi-codes of
each
user.
Although these modes partly implement TR over codes, they are still robust to
power estimation errors. Indeed, the fact that the received power of a given
user is a
common parameter shared between all codes enables its elimination from the
columns
of the constrain matrices (see Table 3). The MCR and MCD modes inherit the
advantages of the R and D modes, respectively. They relatively increase their
sensitivity
to data estimation errors compared to the original modes, since they
accumulate symbol
errors over codes. However, they reduce the number of constraints by N
For a desired user assigned the index d, the constraint matrix Cn is used to
form
the projector nn . The receiver of the data stream from a user-code assigned
the couple-
index (d,l) can simply reject the NI interfering multi-code users by steering
a unit
response to Pd1 ` and a null response to the constraint matrix with the
p,n
projector nn. It can further reject ISI by steering nulls to Pd,` and However,
-l,n -+l,n
the signals received from other multi-codes contribute to self-ISI. This
interference,
referred to here as MC-ISI, is implicity suppressed when receiving an
interfering user.
It can be suppressed too when receiving the desired low-power user by joint
ISR among
_ ._..~ _.~.~....~...~._ .....,,~._~ .. ... ..w.,.. ......,~._~. ,~........_~ -
.L. ._ __, , __
CA 02318658 2000-09-12
69
the codes of each mobile with any of the ISR modes. The multi-code constraint
and
blocking matrices CMC,n and CM~ n, respectively, as shown in Table 4 are
formed, and
derive the ISR beamformer coefficients for user-code (d,l) derived, as
follows:
" 10
QMCn = (CMCnCMCn) 1 ( O)
1 1 d d"
~MC,n - IM = cu I> - AMC,nQMC,nCMC,n ~ (101)
r
n ~ ~iNrCnHn' (102)
.-rd,l X rs1,1
1 lln --O'n
n ~'1H~ 1~ l = (103)
~~,n n -O,n
The projector ~'1 that is orthogonal to both MC-ISI and to the NI interferers
is formed
and then its response normalized to have a unity response to ~d `
-O,n
The above processing organization of ISR among the high-power or low-power
user-codes themselves or between both subsets is a particular example that
illustrates G-
ISR well. The fact that joint ISR among the high-power users and joint ISR
among the
codes of a particular low-power user may each implement a different mode is
another
example that illustrates H-ISR well. In the more general case, ISR can
implement a
composite mode that reduces to a different mode with respect to each user. For
instance,
within the group of NI interferers, each user-code assigned the index (i, l)
can form its
own multi-code constraint and blocking matrices CMc,n and CMcn along a user-
specific
mode (IIõ should be set to identity in Table 4). The constraint and blocking
matrices
then can be reconstructed for joint ISR processing by aligning the individual
constraint
and blocking matrices row-wise into larger matrices as follows:
Cn - {MC,fl'==.',n}' (104)
(~ ' ` (~+' (~ 105
`"n CMC,n~"'1 ~MC,n' ~MC,n1`"MC,n~"'~"MC,n]' ( )
CA 02318658 2000-09-12
This example illustrates the potential flexibility of ISR in designing an
optimal
interference suppression strategy that would allocate the null constraints
among users in
the most efficient way to achieve the best performance/complexity tradeoff. It
should
be noted that, in the particular case where the TR mode is implemented, the
matrices in
5 Equations (104) and (105) are in fact vectors which sum the individual multi-
code
constraint vectors CM~n and C`cn, respectively.
After deriving the beamformer coefficients, each MC user assigned the index u
estimates its Nm streams of data for l= 1, ..., Nm as follows (see Figure 34):
s"" = Real{W"'`"Y }, (106)
n
l7nl = .SlgiZiSn'l1, (107) u
and exploits the fact that its N. access channels share the same power, and
hence
smooths the instantaneous signal power of each data stream over all its codes
as follows:
N.
E lsn,l1 2
(~n)2 = (1-a)(~n-~)2 + a `-' N (108)
m
It should be noted that the multi-code data-streams can be estimated using
MRC,
simply by setting the constraint matrices to null matrices. This option will
be referred
to as MC-MRC.
After despreading of the post-correlation observation vector y by the Nm
spreading codes of a user assigned the index u, the following post-correlation
observation
vectors for Z= 1, ..., Nm are obtained as follows:
u./'u u,l + N" = Hu u,l + ,l /109)
~'1 = HnY~nbn NPCM,n nSn NPCM n' l
n The fact that all user-codes propagate through the same channel is exploited
in the
following cooperative channel identification scheme (see Figure 34):
N
Hn+~ = Hn + ` ~ (Zu'1 - Hnsn'l)Sn'` (110)
N r=i
CA 02318658 2000-09-12
71
which implements a modified DFI scheme, referred to as multi-code cooperative
DFI
(MC-CDFI). MC-CDFI amounts to having the user-codes cooperate in channel
identification by estimating their propagation vectors separately, then
averaging them
over all codes to provide a better channel estimate. It should be noted that
implicit
incorporation of the II-DFI version in the above MC-CDFI scheme further
enhances
channel identification.
Since the STAR exploits a data channel as a pilot, it can take advantage of a
maximum of N. expensive despreading operations. To limit their number in
practice,
MC-CDFI can be restricted to a smaller subset of 1 to Nuser-codes. A
compromise
can be found between channel estimation enhancement and complexity increase.
Another solution that reduces the number of despreading operations
reconstructs
the following data-modulated cumulative-code after ISR combining and symbol
estimation i Equations (106) and (107):
N
Ck b",l~u,l (111)
k ~ n Ck
1=1
K
A single despreading operation with this code yields:
Nm Nm
u'~l,n>l Nn,f
n Un PCM,n
7'~ = ~j~~n + ~j"Hn + M'S (112)
n n ~J ~J n-n PCM,n-
m m
It has the advantage of further reducing the noise level by N,,, after
despreading, while
keeping the signal power practically at the same level3. The data-modulated
cumulative-
code can be used to implement channel identification as follows:
a = sign Re {ftuhlzu.8}} ,
-n
n
There is a small power loss due symbol estimation errors (very low in
practice).
CA 02318658 2000-09-12
72
Hn+~ = Hn + (Z`6 - Hna~rt)a~n. (113)
This CDFI version is referred to as S-CD1FI (see Figure 35).
Whereas multicode operation involves user stations transmitting using multiple
spreading codes, but usually the same data rate, it is also envisaged that
different users
within the same system may transmit at different data rates. It can be
demonstrated that
the receiver modules shown in Figures 34 and 35 need only minor modifications
in order
to handle multirate transmissions since, as will now be explained, multicode
and
multirate are essentially interchangeable.
Multi-Code Ap,proach to Multi-Rate
Reconsidering now the conventional MR-CDMA, in this context, STAR-ISR
operations previously were implemented at the rate 11T where T is the symbol
duration.
As described earlier, with reference to Figure 32, the "X option" extensions,
enables
reduction of noise enhancement by increasing the dimension of the observation
space and
provides larger margin for time-delay tracking in asynchronous transmissions.
A
complementary approach that decomposes the observation frame into blocks
rather than
extends it using past reconstructed data will now be described.
This block-processing version of STAR-ISR will still operate at the rate 1/T
on
data frames barely larger than the processing period T. However, it will
decompose
each data stream within that frame into data blocks of duration Tr where T, is
a power-of-
2 fraction of T. The resolution rate 1/T, can be selected in the interval
[1,T,1/T,].
Hence, a receiver module that processes data frames at a processing rate 11T
with a
resolution rate 1/T, can only extract or suppress data transmissions at rates
slower than
or equal to 1/T, Also, the channel parameters of the processed transmissions
must be
almost constant in the interval T, the processing period. This period should
be chosen
CA 02318658 2000-09-12
73
to be much larger than the delay spread AT for asynchronous transmissions, but
short
enough not to exceed the coherence time of the channel.
In one processing period, STAR-ISR can simultaneously extract or suppress a
maximum N,õ = T/T, blocks (N,n is a power of 2). In the n-th processing period
of
duration T, a stream of data bu(t) yields N,,, samples b~~',,.,,bn"'Nm sampled
at the
resolution rate. Over this processing period, therefore, the spread data can
be developed
as follows:
c u(t)b "(t) b,,'UT(t - n7-)c u(t), (114)
r=i
where UT(t) is the indicator function of the interval [(1 - 1)Tr, lTr). This
equation can
be rewritten as follows:
cu(t)bu(t) = Ebu,'(t)cu,r(t), (115)
r=1
where bu '(t),...,b"'Nm(t) represent Nn data-streams at rate 1/T spread by N.
vlrtUal
orthogonal codes c" `(t),...,c"'" (t) (see Figure (36).
With the above virtual decomposition, one arrives at a MC-CDMA model where
each of the processed users can be seen as a mobile that code-multiplexes N,,,
data-
streams over N,, access channels. This model establishes an equivalence
between MC-
CDMA and MR-CDMA and provides a unifying framework for processing both
interfaces simultaneously. In this unifying context, codes can be continuous
or bursty.
Use of bursty codes establishes another link with hybrid time-multiplexing
CDMA (T-
CDMA); only the codes there are of an elementary duration Tr that inserts
either symbols
or fractions of symbols. A larger framework that incorporates MR-CDMA, MC-CDM,
and hybrid T-CDMA can be envisaged to support HDR transmissions for third
generation wireless systems.
CA 02318658 2000-09-12
74
Exploiting this MC approach to MR-CDMA, the data model of MR-CDMA will
be developed to reflect a MC-CDMA structure, then a block-processing version
of
STAR-ISR derived that implements estimation of a symbol fraction or sequence.
The multi-code model of Equation (97) applies immediately to MR-CDMA.
However, due to the fact that codes are bursty with duration T, < T, the self-
ISI
vectors k,` and yn,` and the spread propagation vector j* ` of a given user-
code do
-1,n -+l,n 0,n
not overlap with each other. If yr denotes an arbitrarily enlarged delay-
spread
(reference [20]) to leave an increased uncertainty margin for the tracking of
time-varying
multipath-delays (i. e., pT <yr < T), and if Nr =`J-,r/T 1 denotes the maximum
delay-spread in Tr units, then only the last Nr symbols bn'i '"'',,,,,b,"im
among the past
symbols in the previous frame may contribute to self-ISI in the current
processed frame
(see Figure 37):
u N. N~ Nm
Yn, = Oubn,l a + ~nbn,rvu,l + ~ ~/,nbu,r l + fftn (116)
n n-l l l,n n n 10,n Wn n+l +l,n n
u=1 1=N -N+1 1=1 l=1
m
In this frame of duration 2T - T,, the desired signals' contribution from the
Ncurrent
symbols is contained in the first interval of duration T+Yr, whereas the
remaining
interval of the frame contains non-overlapping interference from the last Nn -
Nr future
symbols in the next frame, namely bn,~ =+' 9 ,.,,bn"m (see Figure 37). The
remaining part
of the frame can be skipped without any signal contribution loss from the
current bits.
Hence, the duration of the processed frame can be reduced to T+Er- - T as
follows:
Y=[ic, o, Y 1,..., Y,c,+r,,-2,1 (117)
CA 02318658 2000-09-12
where Lo =FTRT ] is the maximum length of the enlarged delay-spread in chip
samples. With the data block-size reduced to M x (L + Lo - 1), the matched-
filtering
observation matrix reduces to:
N N N
u
5 _ u u,l u,~~u u u,l~~u [ + ~~ th 118
Yn - ~ ~ ~nbn-1 rll,n + n~n I O,n + k Onbn+l l +1 n IV , ~ ~
u=1 [=N -N+1 l=1 1=1
where ffth is the noise matrix reduced to the same dimension. This data model
equation can be rewritten in the following compact vector form:
U N +l
Y onbn+k_~'1Xk +'~~ (119)
n k,n -n
u=1 1=1 k=-1
where Xk = 0 if k = - 1 and l E{],...,N,) or if k=+1 and l E{Nõt - Nr + 1,...,
,
NJ, and 1 otherwise.
The constraint matrices can be formed in an MC approach to implement joint or
user-specific ISR processing in any of the modes described in Tables 3 or 4,
respectively. In contrast to the conventional MC-CDMA, the factor Xk discards
all non-
overlapping interference vectors in the processed frame and somehow unbalances
ISI
contribution among the virtual multi-code streams. In the DF modes, only the
central
streams of each user (i. e. , l= Nr + 1, ..., N,n - Nr) sum symbol
contributions from the
previous, current and future symbols; whereas the remaining streams sum signal
contributions from either the current and the previous or the current and the
future
symbols. Indeed, the 2(N,,, - N) ISI terins discarded from summation
contribute with
null vectors to the processed frame. In the ISR-H mode, the columns previously
allocated to individually suppress these vectors are eliminated from the
constraint
matrices, thereby reducing the number of its columns to N. = Nn, + 2N,
constraints per
_ _ -_. _.__ _ . _~..~.~...~..~.._A.W.,..~,. ~_.~.... ~...~. _
CA 02318658 2000-09-12
76
user4 (see Tables 3 and 4). ISR-H hence approaches ISR-R in computational
complexity
when N, is small compared to N,,,.
After derivation of the beamformer coefficients of each virtual user-code
assigned
the couple-index (u,!), its signal component Sn ' is estimated using Equation
(106). In
this process, each ISR combiner rejects the processed interferers regardless
of their exact
data rates, which only need to be higher than the resolution rate. This
feature finds its
best use when implementing ISR at the mobile station on the downlink where
data rates
of suppressed interferers are not necessarily known to the desired mobile-
station. For
instance, orthogonal variable spreading factor (OVSF) allocation of Walsh
spreading
codes is no longer necessary. On the uplink, each transmission rate is known
to the base
station. However, one can still gain from this feature by allowing joint and
well
integrated processing of mixed data traffic at a common resolution rate.
Indeed, the estimation of the signal components provides sequences oversampled
to the resolution rate 1/Tr. Hence, after a given data stream is decomposed at
this
common rate, its signal component estimate must be restored to its original
rate in an
"analysis/synthesis" scheme. To do so, the data rate 1/Tu 5 1/T, of user u is
defined
and it is assumed temporarily that it is faster than the processing rate (i.
e. , 1/Tõ >_ 1/T).
Hence, one can extract from each frame Fu = TIT,, < Nn, signal component
estimates
out of Nn, by averaging the oversampled sequence Sn =` over consecutive blocks
of size
B,, = N,,,/Fõ = Tn/Tr for n' = 0,..., F,, - I as follows:
(n' +1)B.
E SI
!=n'B +1 (120)
S,Fu+n ' - B
u
4ISR may be equally reformulated with Nn, + 2N, generating sequences that
process
all the contributing symbols as if they were independent streams without MC-
ISI. Only
the N. current symbols are estimated then; the 2N, remaining symbols being
corrupted
by the edge effect.
CA 02318658 2000-09-12
77
bnF.Y+ni = Slg/2{ nFu+n'}, (121)
F -1
I" Z
snP +n' I
(On)2 - (1 - (.)(~n 1)2 + Ly n'=o F (122)
u
In the particular case where the data rate is equal to the processing rate (i.
e. , 1/Tu =
1/T), the equations above have simpler expressions with Fn = I and Bn = N.:
N
r ge,[
L n
n (123)
Sn - N ~
bn = S1g12fSnl, (124)
l~n)1 - ll - ~)(0n-l)1 + a I Sn 12. (125)
If the data rate is slower than the processing rate, the signal component
estimate Sn of Equation (123) is further averaged over consecutive blocks of
size Fõ = T/T to yield the following subsampled sequence:
F.-1
u
S LnIF,,.f Fõ+n'
Su = n' -0 (126)
F
Ln/FJ
u
Symbol and power estimations in Equations (124) and (125) are on the other
hand
modified as follows:
b 1Ln/F'j = Sign {s ~~n/F,~ 11 (127)
CA 02318658 2000-09-12
78
2 2
Ln/Fv~, a)(ip'~n/F,~ -1) + a 1 S Ln/F~j 1z. (128)
It should be noted that a higher value is needed for the smoothing factor to
adapt to
a slower update rate of power estimation. If the channel power variations are
faster than
the data rate, then it is preferable to keep the power estimation update at
the processing
rate in Equation (125). In this case, Equation (126) is modified as followss:
Fy-1
t~~ u u
T Ln/F f Fõ +n ' S Ln/F,,.f Fu +n ~
Ln/FJ - n'-O F.~-1 (129)
S ~
u 2
L~ (T Ln/FyjF,+n',
to take into account channel power variations within each symbol duration.
It should be noted that the multi-rate data-streams can be estimated using
MRC,
simply by setting the constraint matrices to null matrices. This option may be
referred
to as MR-MRC.
It should be also noted that combination of Equations (106) and (120), along
with
Equation (128) for data rates slower than the processing rate, successively
implements
the processing gain of each user in fractioned ISR combining steps.
In general, regrouping the symbol-fractions back to their original rate can be
exploited in the design of the constraint matrices; first by reducing
reconstruction errors
from enhanced decision feedback; and secondly by reducing the number of
constraints
5 This signal component estimate is not used for power estimation. Only its
sign is
taken in Equaiton (127) as the estimate of the corresponding bit. Hence, power
normalization given here for completeness is skipped in practice.
CA 02318658 2000-09-12
79
of a given user u from Nto Fu in the modes implementing decomposition over
user-
codes (i. e. , R, D, and H). For these modes, the common factor N,,,NI
appearing in the
NI
total number of constraints N, reduces to by regrouping the constraint vectors
over the user-code indices that restore a complete symbol within the limit of
the
processing periodb.
Regrouping the constraints of user u to match its original transmission rate
amounts to regrouping the codes of this user into a smaller subset that
corresponds to a
subdivision of its complete code over durations covering its symbol periods
instead of
the resolution periods. In fact, user u can be characterized by Fu
concatenated multi-
codes instead of N,,,. Overall, MR-CDMA can be modeled as a mixed MC-CDMA
system where each user assigned the index u has its own number Fu of multi-
codes (see
Figure 38). Therefore, the ISR-combining and channel-identification steps can
be carried
out in one step along the MC formulation of the previous section, using user-
codes
simply renumbered from 1 to Fu for simplicity. Hence, as shown in Figure 39,
the only
change needed to the receiver module of Figure 34 is to the bank of
despreaders. In the
receiver module shown in Figure 34, the spreading codes used by the
despreaders 19d,1,,,,,19d,Fd comprise segments of the spreading code of user
d, i.e., the
segments together form the part of the code used in a particular frame. The
number of
code segments Fu corresponds to the number of symbols bn ",,,,,bn 'FU
transmitted in the
frame. The estimates of these symbols, and the signal component
estimates sn'~ sn F map with those of Equations (120), (121), (123) and (124)
within
a parallel/serial transform.
6 Feedback of symbols with rates slower than the processing rate to the
constraints-
set generator is feasible.
CA 02318658 2000-09-12
This illustrates again the flexibility afforded by using ISR in designing
optimal
interference suppression strategies that suit well with MR-CDMA. It enables
simultaneous processing of blocks of symbols or fractions of symbols in an
integrated
manner at two common resolution and processing rates.
5 To carry out channel identification operations, the M x Lo reduced-size post-
correlation observation matrix of user-code (u,l) is defined as follows:
(130)
r_[z:z::,...,z::J_1], -
where the columns of this matrix are given for j= 0,...,Lo - 1 by:
Zu,l 1 u,l 1 u n,; = L ~ Y ;+j,cj, = L Y j j ,cj , . (131)
rJl =O r 1~=(l-1)*L.
This correlation with the virtual user-code (u,l) amounts to partial
despreading by a
reduced processing gain Lr = T,1 T= L/1V , using the l-th block of length Lr
of the
user's code cj", It should be noted that, in contrast to conventional MC-CDMA,
the
above partial despreading operations are less expensive in terms of complexity
per user-
code.
The reduced-size post-correlation observation vector ZUJ resulting from vector-
reshaping of 4,1 has the same model expression of Equations (109), except that
vectors
there all have reduced dimension (MLo) x 1. It should be noted that the post-
correlation window length Lo was fixed long enough to contain the delay-spread
with an
enlarged margin for asynchronous time-delay estimation from the reduced-size
propagation vector Hn (reference [20]). Identification with post-correlation
windows
n
shorter than L, investigated in [6], reduces complexity and proves to work
nearly as well
as the original full-window version of STAR (i. e, Lo = L).
Channel identification with the MC-CDFI scheme of Equation (110) can be
readily implemented using the user-code post-correlation observation vectors
Zu,'.
CA 02318658 2000-09-12
81
However, this procedure would feed back symbol fractions without taking full
advantage
of the complete processing gain. Instead, the vectors z-,l are regrouped and
averaged
n
in the same way the signal component estimates are restored to their original
rate in
Equations (120, (123) or (126), and Z~ n, Zn or Z~n/FJ ~ respectively' are
obtained.
Hence, the CDFI channel identification procedure, renamed MR-CDFI, is
implemented
as follows:
F
n n+ fC u~u n 132
= H ~ H snF ,n 5,f. ,n ( )
n+l n F nFM+n n ~
u n'=o
when the data-rate is faster than the processing ratea, or by:
Hn = Hn + ~A,IZn -)g" n~ (133)
n+1 n \ n n
in the particular case where the data rate is equal to the processing rate, or
by:
u n 134
Ln/F~ - H Ln/F,~ s Ln/F,~ s Ln/FJ I ( )
Ln/F,~ - Ln/Fõ~ +~ (Zu
when the data-rate is slower than the processing rate. It should be noted that
channel
identification at data rates faster than the processing gain in Equation (132)
has a
structure similar to MC-CDFI. Averaging over Fn despread observations there
can be
reduced to a smaller subset to gain in complexity like in MC-CDMA. Use of the
S-
CDFI version described in Equations (111) to (113) instead of, or combination
with, the
above scheme are other alternatives that reduce the amount of complexity due
to
despreading operations.
By regrouping codes to match the original data transmission rates as discussed
earlier (see Figure 38), channel identification can be easily reformulated
along a mixed
' In practice, these vectors are computed directly from Y. in regular
despreading
steps which exploit the entire spreading sequences in one step along a mixed
MC-CDMA
scheme.
gImplementation of Fõ channel updates (with time-delay tracking) instead of
averaging
is computationally more expensive.
CA 02318658 2000-09-12
82
MC-CDMA model where each user is characterized by Fu multi-codes and Fu
despread
vectors as shown in Figure 39.
9
To reduce further the number of expensive despreading operations, slower
channel identification (reference [20]) can update channel coefficients less
frequently if
the channel can still show very weak variations over larger update periods.
However,
high mobility can prevent the implementation of this scheme and faster channel
identification update may even be required. For data rates faster than the
processing
rate, updating at a rate higher than the processing rate is not necessary. The
processing
period T is chosen to guarantee that the channel parameters are constant over
that time
interval. For data rates slower than the processing rate, the channel update
rate could
be increased above the data rate up to the processing rate using Equation
(133) and
partial despreading to provide Zu, In Equation (133), S~n~F~ from Equation
(126)
n
should be fed back instead of Sn to benefit from the entire processing gain in
the
decision feedback process.
Although the foregoing embodiments of the invention have been described as
receiver modules for a base station, i. e. , implementing ISR for the uplink,
the invention
is equally applicable to the downlink, i. e. , to receiver modules of user
stations.
Downlink ISR
To implement ISR rejection, the user/mobile station needs to identify the
group
of users (i. e. , interferers) to suppress. Assuming temporarily that
suppression is
restricted to in-cell users, served by base-station v, and that the number of
suppressed
interferers is limited to NI to reduce the number of receivers needed at the
desired base-
station to detect each of the suppressed users, in order to identify the best
users to
suppress, the user station can probe the access channels of base-station v,
seeking the NI
CA 02318658 2000-09-12
83
strongest transmissions. Another scheme would require that the strongest in-
cell
interfering mobiles cooperate by accessing the first NI channels (i. e. , u =
i (E
{1, . . . , NI}) of base-station v.
Once the NI suppression channels have been identified, the desired user-
station
can operate as a "virtual base-station" receiving from NI mobiles on a
"virtual uplink".
If the desired user is not among the NI interferers, an additional user
station is
considered. Similar NI channels may be identified for transmissions from the
neighbouring base-stations. Accordingly, consideration will be given to the NB
base-
stations, assigned the index v' E{],...,NB}, which include the desired base-
station with
index v' = v without loss of generality. This formulation allows the user-
station to
apply block-processing STAR-ISR with specific adaptations of ISR combining and
channel identification to the downlink.
In essence, each "virtual base station" user station would be equipped with a
set
of receiver modules similar to the receiver modules 21...... 21", one for
extracting a
symbol estimate using the spreading code of that user station and the others
using
spreading codes of other users to process actual or hypothesized symbol
estimates for the
signals of those other users. The receiver would have the usual constraints-
set generator
and constraint matrix generator and cancel ISR in the manner previously
described
according to the mode concerned.
It should be appreciated, however, that the signals for other users emanating
from
a base station are similar to multicode or multirate signals. Consequently, it
would be
preferable for at least some of the user station receiver modules to implement
the
multicode or multirate embodiments of the invention with reference to Figures
34 and
39. Unlike the base station receiver, the user station's receiver modules
usually would
not know the data rates of the other users in the system. In some cases, it
would be
_ _._~_.. ~...~.~...._.,,~..,......_. _ _ _
CA 02318658 2000-09-12
84
feasible to estimate the data rate from the received signal. Where that was
not feasible
or desired, however, the multirate or multicode receiver modules described
with
reference to Figures 34 and 39 could need to be modified to dispense with the
need to
know the data rate.
Referring to Figure 40, the user station receiver comprises a plurality of
receiver
modules similar to those of Figure 39, one for each of the NB base stations
whose NI
strongest users' signals are to be cancelled, though only receiver module 21"
is shown
in Figure 38. Recognizing that one or more of those NI signals could be
multirate or
multicode, and hence involve not only different spreading codes but also
different code
i =N7
segmentations, the number of despreaders equals i.e.
19v''`'F~, , 19 ' "1=', , 19"''"''FN, In any given base station, the NI
users are power-controlled independently and so are received by the
mobile/user station
with different powers. Consequently, it is necessary to take into account
their power
separately, so the power estimates from power estimation means 30T" are
supplied to
the channel estimation unit 28T". The channel identification unit 28T"'
processes the
data in the same way as previously described, spreading the resulting channel
estimate H' to form the spread channel estimates and supplying
o,n -O n ,..., -o.n
them to the ISR beamformers 47T`,1 ',..., 47Tv''"4'Fv respectively, for use in
processing the observation vector K.
n
The resulting signal component estimates sn sv"N"FN, are similarly fed
back to the channel identification unit 28V to update the channel parameter
estimates
and to the decision rule units 30Tv' ''', ..., 30T "N"'^'1 for production of
the
corresponding symbol estimates b ''^",FN In all modes except ISR-H, these
n n
symbol estimates are supplied to the constraints-set generator, together with
the set of
channel parameter estimates from channel identification unit 28T"' for use in
..~_~.. ~~.~.... ~..~.,~..,
CA 02318658 2000-09-12
forming the set of constraints C. The set of channel parameter estimates
includes the
power estimates from the power estimation units.
If the desired user is not among the NI strong users of the serving base
station
v, the user station receiver will also include a separate receiver module
which could be
5 similar to that shown in Figure 39. However, bearing in mind that the
channel estimate
derived by the receiver modules for the serving base station's strong users in
Figure 40
will be for the same channel, but more accurate than the estimate produced by
the
channel identification unit of Figure 39, it would be preferable to omit the
channel
identification unit (29F,) and despreaders 19d ',..., 19d'F' (Figure 39), and
supply the
10 spread channel estimates from the channel identification unit of the
receiver module for
serving base station v, as shown in Figure 41.
The receiver module shown in Figure 40 is predicated upon the data rates of
each
set of NI users being known to the instant user station receiver. When that is
not the
case, the receiver module shown in Figure 40 may be modified as shown in
Figure 42,
15 i. e. , by changing the despreaders to segment the code and oversample at a
fixed rate that
is higher than or equal to the highest data rate that is to be suppressed.
It is also possible to reduce the number of despreading operations performed
by
the receiver module of Figure 42 by using a set of compound segment codes as
previously described with reference to Figure 35 to compound over segments.
However,
20 as shown in Figure 43, a set of different compound codes could be used to
compound
over the set of NI interferers. It would also be possible to combine the
embodiment of
Figure 43 with that of Figure 35 and compound over both the set of interferers
and each
set of code segments.
A desired user station receiver receiving transmissions on the downlink from
its
25 base-station and from the base-stations in the neighbouring cells will now
be discussed.
CA 02318658 2000-09-12
86
Each base-station communicates with the group of user stations located in its
cell.
Indices v and u will be used to denote a transmission from base-station v
destined for
user u. For simplicity of notation, the index of the desired user station
receiving those
transmissions will be omitted, all of the signals being implicity observed and
processed
by that desired user station.
Considering a base-station assigned the index v, its contribution to the
matched-
filtering observation vector y of the desired user station is given by the
signal vector
of the v-th base-station r defined as:
n
y`' Y"'n, (135)
-u,n u,n
u=1
where the vector y=u denotes the signal contribution from one of the Uv users
u,n
communicating with base-station v and assigned the index u. Using the block-
processing
approach described in the previous section, the vector y,R can be decomposed
as
u,n
follows:
N +l
n v u r r v u lb v u l~' N,u,l,/X!
~n n+k JJ,R-k n k= (136)
Y1=k k=-1
It should be noted that the channel coefficients rfn just hold the index of
the base-station
v. Indeed, transmissions from base-station u to all its mobiles propagate to
the desired
user station through a common channel. Base-station signals therefore show a
multi-code
structure at two levels. One comes from the virtual or real decomposition of
each user-
stream into multiple codes, and one, inherent to the downlink, comes from
summation
of code-multiplexed user-streams with different powers. As will be described
hereinafter, this multi-code structure will be exploited to enhance
cooperative channel
identification at both levels.
CA 02318658 2000-09-12
87
In a first step, the desired user-station estimates the multi-code constraint
and
blocking matrices of each of the processed in-cell users (i. e. , u E{],...,
NI} U{d}).
Table 4 shows how to build these matrices, renamed here as CMC,n and CMC n to
show
the index v of the serving base-station. Indexing the symbol and channel
parameter
estimates with v in Table 4 follows from Equation (136). In a second step, the
user-
station estimates the base-specific constraint and blocking matrices CBS,n and
CBS n using
Table 5. These matrices enable suppression of the in-cell interferers using
one of the
modes described in Table 5. For the downlink, a new mode BR, for base-
realization,
replaces the TR mode of Table 3. Suppression of interfering signals from
multiple base-
stations adds another dimension of interference decomposition and results in
TR over the
downlink as shown in Table 6. Therefore, in a third step the mobile-station
estimates
the base-specific constraint and blocking matrices CBS,n and CBS; ` from the
interfering
base-stations and concatenates them row-wise to form the multi-base constraint
and
blocking matrices denoted as C and C ",1 respectively. In the TR mode, the
base-
n n ~
specific constraint and blocking vectors in the BR mode now are summed over
all
interfering base-stations, leaving a single constraint. For the other modes,
the number
of constraints N, in Table 3 is multiplied by the number of interfering base-
stations NB.
The receiver module dedicated to extracting the data destined to the desired
mobile-
station # d from the serving base station # v is depicted in Figure 38.
It should be noted that the multi-rate data-streams can be estimated using MRC
on the downlink, simply by setting the constraint matrices to null matrices9.
This option
will be termed D-MRC.
9 In this case, ISR processing is not needed and the desired signal is
expected to be
strong enough to enable reliable channel identification for its own.
__ _.....~. ..~.~.~..~.~.~_....~. ....~.. ~._-_.._,.~..._. _.....___ ____.
CA 02318658 2000-09-12
88
If the user-station knows10 the data rates of the suppressed users, it can
estimate
their symbols" as long as their symbol rate does not exceed the processing
rate. As
mentioned hereinbefore, this block-based implementation of the symbol
detection
improves reconstruction of the constraint matrices from reduced decision
feedback
errors12. Otherwise, the user-station can process all interfering channels at
the common
resolution rate regardless of their transmission rate. It should be noted that
estimation
of the interferers' powers is necessary for reconstruction in both the BR and
TR modes,
for channel identification as detailed below, and possibly for interference-
channel probing
and selection. It is carried out at the processing rate.
Identification of the propagation channels from each of the interfering base-
stations to the desired user station is required to carry out the ISR
operations.
Considering the in-cell propagation channel, its identification from the post-
correlation
vectors of the desired user is possible as described hereinbefore with
reference to Figure
39. It exploits the fact that the multi-codes of the desired user propagate
through the
same channel. However, the in-cell interfering users share this common channel
as well.
Therefore, the MC-CDFI and MR-CDFI approaches apply at this level as well.
Indeed,
the user-station has access to data channels which can be viewed as NI x
Nvirtual
pilot-channels with strong powers. It is preferable to implement cooperative
channel
identification over the interfering users whether the desired user is among
the in-cell
10Data-rate detection can be implemented using subspace rank estimation over
each
stochastic sequence of Nsymbol fractions.
" In the ISR-H mode, only the signal component estimates are needed for power
and
channel estimation (see next subsection).
12 Recovery of the interfering symbols at data rates slower than the
processing gain
could be exploited in slow channel identification. However, selection of a
user as a
strong interferer suggests that its transmission rate should be high.
CA 02318658 2000-09-12
89
interferers or not. The same scheme applies to the neighbouring base-stations
and
therefore enables the identification of the propagation channel from each out-
cell
interfering base-station using its NI interfering users.
If the data rates are known to the base-station, identification of the
propagation
channel from a given base-station v' E{],...,NB} can be carried out
individually from
each of its NI interfering users, as described in the previous section. To
further enhance
channel identification, the resulting individual channel estimates are
averaged over the
interfering users. Both steps combine into one as follows:
T~v i + I 1 Fi ~ ..v, v~i I37
N
L? + 1 - !I NI HnSnP +n n ( )
This downlink version of MR-CDFI, referred to as DMR-CDFI, is illustrated in
Figure
40. It should be noted that averaging over the interferers takes into account
normalization by their total power. To reduce the number of despreading
operations,
averaging over interferers can be limited to a smaller set ranging between 1
and NI.
If the data rates of the interfering users are unknown to the user-station,
identification can be then carried out along the steps described with
reference to Figure
34 to process interfering signals at the common resolution rate as follows:
NI Nm
H"I + r ~,"1 - H" (138)
lsv "1 sv~'`'1.
n+l n NI u~ n n n n
N E z
~~ l n
This downlink version of MC-CDFI, referred to as DMC-CDFI, is illustrated in
Figure
42. To reduce the number of despreading operations, averaging over interferers
and
user-codes can be limited to smaller subsets ranging between 1 and NI and 1
and N,,,,
respectively.
CA 02318658 2000-09-12
An alternative solution that reduces the number of despreading operations
utilizes
the following cumulative multi-codes for l=
NI
Ck 'E'1 = 1 r Ck 't'/ (139)
JNI ~=t
5
Despreading with these cumulative codes yields:
Nl NI
V/,i.l
S Nv',','
n -PCM,n
-n = _~ ~ t + i 1 = HvS v' E l + Nv',E,l (140)
n n NI NI -n n -PCM,n10 Averaging the user-codes over interferers does not
reduce noise further after
despreading. However, the composite signal Sn''1 collects an average power
from the
NI interferers and therefore benefits from higher diversity. The cumulative
multi-codes
can be used to implement channel identification as follows:
= 3 ~ + /zv',E,1 ft'SR sn ,E,tI
~ (141)
n+t n N(~v, 2 1 t 1 n
15 n
where:
NI
Sv'tl
n
s '~'` (142)
R NI '
20 N NI
L.~ L I SRv/ ,1 I 2
(~v' E 2 2+ a 1=t ~=t (143)
n ' ) = (1 ) n t ~ 1V NI
This downlink version of MC-CDFI, referred to as DSMC-CDFI, is illustrated in
Figure
43. Again, averaging over a smaller set of user-codes reduces the number of
25 despreading operations. Use of the S-CDFI version described in Equations
(I11) to
CA 02318658 2000-09-12
91
(113) instead of, or combination with, the above scheme13, are other
alternatives that
reduce the amount of complexity due to despreading operations. Their
implementation
on the downlink is ad hoc and follows from the given descriptions.
13 Summing user-codes over resolution periods does not increase diversity.
However, use of the S-CDFI version further reduces noise after despreading.
CA 02318658 2000-09-12
.~ ,
O >,
ti
G)
s..
U
a > > o
~
o an
~ a 2 v a a ay, a
Q + + a ,~ + + + av.
t4-. bn U o
v' U
cn
N Fr ~
Qn = 1~-r = ~ vl .~ Ln
~+ 1- U 3 ==~ ~ U ~ -~ U
O
Cl
cn
cn z z z z
a cn ~ x x H
cn COO
cn
cn
~
~,....,.._ ~.._, _ _.,~,~~_.... ~..
CA 02318658 2000-09-12
M$ 2h
.,~ , .
.
.--a
O w, O
M '-i
.,~
~ = J ~
.-i
=
II I ~
I M = J
II ~I II
~-~a a'
II II II
Q! C1~. {Yi
UO
W rõ~ -~ --1
r-a
H
CA 02318658 2000-09-12
2` ~ z 2 <~..,"'
\\\ Y
rn
r--~ r----i
i-----~ &
V - + W li
W~I
I 1
H
.~.,_.....o....~..w..~.~..._. _ _ .__ ~..._.....,~,,
._..~,~...r,,.,.~a....~......~.. .._..__. _ _. _~.~~... _._.._.. _ _
._.____._._.
CA 02318658 2000-09-12
~
a~ =
~ ^ U O z.,
~ O ~
14~
w u o
-14
<'=~.~+ ~3,,~ ~~,, >, ~ Q Z~
`'~J~ <.p" <=~.~`ti N I"~O" U
It cd
M
ct cd
~C <Ur
p~ an
n
F"
~ =~
cn
~
o .~
'i=~,'i ~ :e ^fl
y y <,3=1 ~, 'y:, ~ .~
~^ . !"` ~,.= Q~
<.f~ y r-i = .~.i
CHa
+~,y *~ n z~1/V"i v` II N
y u ~ ~ 2s o~
W`ti 1 I
CIS
oa
U U ~ W S~-i
Cl*
U +
H ~ o
a Q x ~
~n o
CA 02318658 2000-09-12
r--i r--~
O y ~t
^ + ~2 ~
V vl x C
+ + W _
y I
_ + W II
~ 1 ~ti ~ y
Wyl ~ W.~.~
l ~(~~I I =
I 1
st
14~
C C l '
S~ E- (~IC (vIC t- S^C ~ ( C S C (~at
+ W
~ + õ
+ W II
w W
~ 1I/~`11 .
1 ryI ~ I .
1 1
94
H
_..v_ --~..~.~,..~....,.~..~...w._..~.,...~..._w~.
CA 02318658 2000-09-12
o II ' ~
II
o u C
A. I ~O Q .~ h
U O
'C Q U O
o U ~ N
,^ Y G~ y L: O =~L'
: W ~~ z~W~ r =o /-= =~
U M .-+
W V~ rn ~ o
cli
Q u ~=; C
U =~ `V
cn
(U
C ~'< ~ ~o _ W on
< Y at C~ 'V L~"
~= ' a C rn O 'b
r~l U i-~i U
4d ~ U O +
~ w. ~ i ' UO c~ v II OU
E
O E
Cld
Z'\
_ __ --=---~ _..~..~...,.+.~._.~,.~.__........,.~.
.Y....,._.....,....------ ....~. ..,..__ ..
CA 02318658 2000-09-12
98
TABLE 5
BR
F NI N NJ +1
v ~q u~ E E w,i,l v ~,i,,f~
6BSn n
1~/ n+k~fn-kn k
u=1 1=1 f=1 k=-1
FM N Nj
v uE F E v a l ~' t,l f-i',!' 0 1
~BS,n n bn+k .fn=k,n i,l,k Xk
u=l 1=1 f=1 k=-1
N, 1
TABLE 5
Table 5 shows base-specific constraint and blocking matrices CBS,n and ~s nl
which
will apply to the modes shown in Table 3 except for TR, replaced by BR.
Indices of
remaining modes in Table 3 should be modified to include the index of the base-
station
v as shown for the TR mode. It should be noted that channel coefficients ~-fn
hold the
index of the base-station u instead of the user i. Transmissions to all user-
stations from
base-station u propagate to the desired user station through a common channel.
It should
also be noted that summation over users is weighted by the estimate of the
total
amplitude due to user-independent power control. Definitions of ~ ~,k and Xk
are
given in Table 3.
TABLE 6
TR
NB NI N NJ +1
Cn G ~'j~ 'urr rb 'i' " ~'i'` X1
E ~ Y~ n L~ L~ G i ~ f
n+k f n-k k
v=1 U=1 1=1 f=1 k=-1
NB NI N NJ +1 P ll ~~ T nu~ E E w,iLAv tw,t,lbv,i,0~1
n+k f,nl-k,n v,i,1,k k
v=1 u=1 1=1 f=1 k=-1
_-,_- .~,.Y..,. .........~..~,......~...mw.. _
.._...._u..~.,..,..~....,.....,......,,,
CA 02318658 2000-09-12
99
N, 1
BR
Ni Nm Nf +1
~n"E F E bv ` l~v k
n n+k f,n-k,n
L u=1 1=1 f=1 k=-1
+
jw't~,l1 E _q_vn,uE f E E bv,i,lTv ~w,i,l~v',t1,1~,0X1
l.n 1~/ n+k f,nIk n v,i,l,k k~
u=1 1=1 f=1 k=-1
N, NB
TABLE 6
and C"'' i'j' which apply
Table 6 shows multi-base constraint and blocking matrices Cn n
to the modes of Table 3 by row-wise aligning the constraint and blocking
matrices Css,n and ~sin,' from base-stations into larger matrices Cn and in
the way suggested by Equations (104) and (105). The number of constraints in
Table
5 is multiplied by NB as shown here for the BR mode. The additional TR mode
sums
the constraint-vectors of the BR mode over all base-stations. The definition
of Xk is
given in Table 3 and S~,i,rkl '1 0 if (v,i,l,k) = (v', i', l', k') and 1
otherwise.
It should be appreciated that, when ISR is used for the downlink, it will
function
where the mobile station has a single antenna.
Embodiments of the invention are not limited to DBPSK but could provide for
practical implementation of ISR in mixed-rate traffic with MPSK or MQAM
modulations
without increased computing complexity. Even orthogonal Walsh signalling can
be
implemented at the cost of a computational increase corresponding to the
number of
Walsh sequences.
It should also be noted that, although the above-described embodiments are
asynchronous, a skilled person would be able to apply the invention to
synchronous
systems without undue experimentation.
__ ~ .._..~..~__ _ _ ...._ ~.........~..W.....~..,...._........~..~..____.. _
_
CA 02318658 2000-09-12
100
It should be appreciated that the decision rule units do not have to provide a
binary output; they could output the symbol and some other signal state.
The invention comprehends various other modifications to the above-described
embodiments. For example, long PN codes could be used, as could mixed rate or
mixed
modulations, large delay-spreads and large inter-user delay-spreads. Also, the
invention
can be used in CDMA systems employing pilot signals.
CA 02318658 2000-09-12
101
REFERENCES
For further information, the reader is directed to the following documents,
the contents
of which are incorporated herein by reference.
1. F. Adachi, M.Sawahashi and H. Suda, "Wideband DS-CDMA for next
generation mobile communications systems", IEEE communications Magazine,
vol. 36, No. 9, pp. 55-69, September 1998.
2. A. Duell-Hallen, J. Holtzman, and Z. Zvonar, "Multiuser detection for CDMA
systems", IEEE Personal Communications, pp. 46-58, April 1995.
3. S. Moshavi, "Multi-user detection for DS-CDMA communications", IEEE
Communications Magazine, pp. 124-136, October 1996.
4. S. Verdu, "Minimum probability of error for asynchronous Gaussian multiple-
access channels", IEEE Trans. on Information Theory, vol. 32, no. 1, pp. 85-
96,
January 1986.
5. K.S. Schneider, "Optimum detection of code division multiplexed signals",
IEEE
Trans. on Aerospace and Electronic Systems, vol. 15, pp. 181-185, January
1979.
6. R. Kohno, M. Hatori, and H. Imai, "Cancellation techniques of co-channel
interference in asynchronous spread spectrum multiple access systems",
Electronics and Communications in Japan, vol. 66-A, no. 5, pp. 20-29, 1983.
7. Z. Xie, R.T. Short, and C.K. Rushforth, "A family of suboptimum detectors
for
coherent multi-user communications", IEEE Journal on Selected Areas in
Communications, vol. 8, no. 4, pp. 683-690, May 1990.
8. A.J. Viterbi, "Very low rate convolutional codes for maximum theoretical
performance of spread-spectrum multiple-access channels", IEEE Journal of
Selected Areas in Communications, vol. 8, no. 4, pp. 641-649, May 1990.
___..._,._ ......~..~~....~._~.~.......~~._.~ _~,-
CA 02318658 2000-09-12
102
9. M.K. Varanasi and B. Aazhang, "Multistage detection in asynchronous code-
division multiple-access communications", IEEE Trans. on Communications, vol.
38, no. 4, pp. 509-519, April 1990.
10. R. Kohno et al, "Combination of an adaptive array antenna and a canceller
of
interference for direct-sequence spread-spectrum multiple-access system", IEEE
Journal on Selected Areas in Communications, vol. 8, no. 4, pp. 675-682, May
1990.
11. A. Duell-Hallen, "Decorrelating decision-feedback multi-user detector for
synchronous code-division multiple-access channel", IEEE Trans. on
Communications, vol. 41, no. 2, pp. 285-290, February 1993.
12. A. Klein, G.K. Kaleh, and P.W. Baier, "Zero forcing and minimum mean-
square-error equalization for multi-user detection in code-division multiple-
access
channels", IEEE Trans. on Vehicular Technology, vol. 45, no. 2, pp. 276-287,
May 1996.
13. S. Affes and P. Mermelstein, "A new receiver structure for asynchronous
CDMA
: STAR - the spatio-temporal array-receiver", IEEE Journal on Selected Areas
in Communications, vol. 16, no. 8, pp. 1411-1422, October 1998.
14. S. Affes, S. Gazor, and Y. Grenier, "An algorithm for multisource
beamforming
and multitarget tracking", IEEE Trans. on Signal Processing, vol. 44, no. 6,
pp.
1512-1522, June 1996.
15. P. Patel and J. Holtzman, "Analysis of a simple successive interference
cancellation scheme in a DS/CDMA system", IEEE Journal on Selected Areas
in Communications, vol. 12, no. 5, pp. 796-807, June 1994.
16. J. Choi, "Partial decorrelating detection for DS-CDMA systems",
Proceedings
of IEEE PIMRC '99, Osaka, Japan, vol. 1, pp. 60-64, September 12-15, 1999.
CA 02318658 2000-09-12
103
17. S. Affes and P. Mermelstein, "Signal Processing Improvements for Smart
Antenna Signals in IS-95 CDMA", Proceedings of IEEE PIMRC '98, Boston,
U.S.A., Vol. II, pp. 967-972, September 8-11, 1998.
18. S. Affes and P. Mermelstein, "Performance of a CDMA beamforming array-
receiver in spatially-correlated Rayleigh-fading multipath", Proc. of IEEE
VTC'99, Houston, USA, May 16-20, 1999.
19. H. Hansen, S. Affes and P. Mermelstein, "A beamformer for CDMA with
enhanced near-far resistance", Proc. of IEEE ICC'99, Vancouver, Canada, Vol.
3, pp. 1583-1587, June 6-10, 1999.
20. K. Cheikhrouhou, S. Affes, and P. Mermelstein, "Impact of synchronization
on
receiver performance in wideband CDMA networks", Proc. 34th Asilomar
Conference on Signals, and Computers, Pacific Grove, USA, to appear, October
29-November 1, 2000.
21. S. Affes, A. Louzi, N. Kandil, and P. Mermelstein, "A high capacity CDMA
array-receiver requiring reduced pilot power", Proc. of IEEE GLOBECOM
'2000, San Francisco, USA, to appear, November 27-December 1, 2000.
22. S. Affes, H. Hansen, and P. Mermelstein, "Interference subspace rejection
in
wideband CDMA - part I: Modes for mixed power operation", to be submitted.
23. H. Hansen, S. Affes, and P. Mermelstein, "Interference subspace rejection
in
wideband CDMA - part II: Modes for high data-rate operation", to be submitted.
24. E.H. Dinan and B. Jabbari, "Spreading codes for direct sequence CDMA and
wideband CDMA cellular networks", IEEE Communications Magazine, vol. 36,
no. 9, pp. 48-54, September 1998.
CA 02318658 2000-09-12
104
25. R. Lupas and S. Verdu, "Near-far resistance of multiuser detectors in
asynchronous channels", IEEE Trans. on Communications, vo138, no. 4, pp.496-
508, April 1990.
26. A. Duell-Hallen, "A family of multiuser decision-feedback detectors for
asynchronous code-division multiple-access channels", IEEE Trans. on
Communications, vol. 43, no. 5, pp. 796-807, June 1994.
27. C. Schlegel, P. Alexander, and S. Roy, "Coded asynchronous CDMA and its
efficient detection", IEEE Trans. on Information Theory, vol. 44, no. 7, pp.
2837-2847, November 1998.
28. L.K. Rasmussen, T.J. Lim, and A.-L. "A matrix-algebraic approach to
successive interference cancellation in CDMA", IEEE Trans. on Communications,
vol. 48, no. 1, pp. 145-151, January 2000.
29. M. Latva-aho and M.J. Juntti, "LMMSE detection for DS-CDMA systems in
fading channels, IEEE Trans. on Communications, vol. 48, no. 2, pp. 194-199,
February 2000.