Note: Descriptions are shown in the official language in which they were submitted.
CA 02358732 2001-10-12
METHOD AND SYSTEM FOR REMOTE AUTHENTICATION OF A DIGITAL
WIRELESS DEVICE USING A PERSONAL IDENTIFICATION NUMBER
FIELD OF THE INVENTION
The present invention relates to authenticating a subscriber on a public
network. In
particular, the present invention relates to a system for authenticating the
identity of a user
using a mobile device, such as a cellular phone, to log in to an application
provider.
BACKGROUND OF THE INVENTION
In the field of wireless telecommunications, authentication of a user's
identity is of
fundamental concern. Three of the most substantial concerns regarding identity
relate to
whether or not the wireless device is legitimately identifying itself instead
of reporting a
false identification sequence, whether or not the handset is in the possession
of the
authorised user and generating an audit trail for billing purposes.
To facilitate the solution to the second problem, and to allow user billing,
each
wireless device is assigned a unique wireless device identifier, which is
reported to the
network upon initialisation of the phone. The cellular phone service provider
can check
this wireless device identifier to ensure that the wireless device has not
been reported
stolen. Thus the assumption is made that unless reported stolen, a phone is in
the hands of
an authorised user, and that until reporting the phone missing the user is
responsible for all
charges incurred.
Digital cellular services are designed to handle digital communications. Voice
calls
on a digital cellular network are packetised prior to transmission, and are
transmitted as a
series of binary representative packets. This allows digital cellular devices
to interact with
computers without the need for a modem. It also allows digital cellular
devices to serve as
digital wireless data stations.
So called wireless web functionality, wherein cellular devices allow a user to
browse a subset of Internet web sites through a proxy server or directly if
the web site
offers wireless mark-up language (WML) services, are already commonly
implemented.
Application providers (AP), such as wireless application service providers
(WASPs j, offer
numerous services from stock pricing to sports scores. Additionally
interactive services,
such as banking transactions and stock trading can also be offered to users.
These services
-1-
CA 02358732 2001-10-12
are typically accessed through a data network that relies upon the
transmission of data as
packets. In many implementations the data is transmitted in packets conforming
to the
standards of the transmission control protocol/internet protocol (TCP/IP)
suite. To
translate between the wireless protocols of the network and the wired
protocols of data
networks, such as the Internet, a gateway, such as a wireless application
protocol (WAP)
gateway, may be employed.
These wireless application service providers typically require some form of
user or
device identification to provide customised access and to select the
corresponding account
information. Each digital wireless device, such as a digital cellular
telephone, can be
provided a unique wireless device identifier that is used by the network to
identify the
device. In many instances this identifier is an electronic serial number,
though when the
digital wireless device is communicating with data servers it is typically an
identifier
uniquely associated with the electronic serial number. The wireless device
identifier can
be discerned by a WASP through inspection of an incoming data request, and can
be
falsified by a computer with access to the WASP over a network. The data sent,
in reply,
by the WASP, is directed to the data network address of the computer that
transmitted the
packet, and not to a specific digital cellular phone. Thus an individual can
falsify a
wireless device identifier field and attempt to interact with the WASP, using
discerned
identification information, without the WASP knowing that an unauthorised
access had
been performed.
A WASP, or other content provider, can create a user database containAng the
wireless device identifier associated with each registered user. This database
can associate
a personal identification number (PIN) with each client id, so that a user can
be recognised
by the client id and still prompted for confirmation of identity. Though this
provides a
degree of certainty as to the identity of a user of a digital cellular device,
such databases
are subject to a number of data integrity and security issues as they are
accessible to users
of the network. Additionally, this solution creates problems for users who
must manage a
number of PINS for each WASP they use. This often leads users to select a
single PIN for
numerous services, which increases security risks for the user.
Because it is not possible for a WASP to ensure that the user using the
service is
the authorised user, forming fee per use billing arrangements with cellular
service
providers is difficult. Though banking institutions are content to carry out
their own
-2-
CA 02358732 2001-10-12
authentication and billing, other financial services, or services associated
with personal
information, lack the infrastructure to either bill a client on a fee-per-
transaction. One such
example is a gaming service that allows wireless online gaming and requires
the ability to
bill small amounts of money to a carrier billing system per session. Another
example is a
stock monitoring service, where a user does not carry out a transaction, but
does require
authentication of the user to protect the privacy of a user's portfolio, that
would benefit
from the ability to offer the same levels of security as the basic network
requires.
One of the greatest challenges to an application provider (AP), such as a
WASP, is
obtaining a reliable authentication of the user to prove to a cellular service
provider that a
login was performed by a given user. Providing such a reliable authentication
is essential
if the AP wants to bill its subscribers through the cellular service
provider's billing system.
In addition, the cellular service provider requires assurance that a valid
user logged
in to an AP prior to permitting the AP to submit billing requests. This
assurance is needed
to prevent fraudulent APs from submitting invalid requests. At the present
time, no
suitable method exists for providing such an assurance save for AP and
cellular service
provider integration.
It is, therefore, desirable to provide a method and system for a data based
authentication of a user as the valid user of a digital cellular device
through use of a single
PIN for voice and data services.
SUMMARY OF THE INVENTION
It is an object of the present invention to obviate or mitigate at least one
disadvantage of previous systems and methods for authenticating the user as
the valid user
of a digital wireless device.
In a first aspect, the present invention provides a method of authenticating
the user
of a digital wireless device at an application provider connected to an
authenticator by a
data network. The digital wireless device has both an associated client
identifier and
associated secret information. The authenticator is connected to a register
having a copy of
the secret information associated with both the client identifier and the
digital wireless
device. The method consists of receiving, from the application provider, a
request for
authentication of the user of a digital wireless device. The user of the
digital wireless
device is then requested to provide the secret information associated with the
digital
-3-
CA 02358732 2001-10-12
wireless device. The requested secret information is then compared to the
secret
information stored in the connected register. If the received secret
information and the
secret information stored in the connected register are equivalent,
authentication of the
user of the digital cellular device is provided to the application provider.
In an embodiment of the first aspect of the present invention, the secret
information is a personal identification number. In another embodiment of the
first aspect
of the present invention, the register is a home location register and the
personal
identification number is a home location register personal identification
number, while in
other embodiments the register is either a visiting location register or a
RADIUS server. In
a further embodiment of the present invention there is included the further
step of
receiving a request for service containing the client identifier associated
with the digital
wireless device at the application provider prior to the step of receiving a
request for
authentication. Alternate embodiments include the steps of requesting the
client identifier
of the digital wireless device, and receiving the client identifier of the
digital wireless
device prior to the step of requesting that the user of the digital wireless
device provide the
secret information. In another embodiment of the present invention the request
for
authentication includes the client identifier of the digital wireless device.
In a further
embodiment of the present invention, the secret information request and
comparison are
repeated, if the received secret information is not equivalent to the copy of
the secret
information stored in the connected register.
In a further aspect, the present invention provides a system for
authenticating a
user of a digital wireless device. The digital wireless device has a client
identifier., and is
connected to a digital wireless network having a register for storing a secret
information
associated with the client identifier. An application provider is connected to
both the
digital wireless device and a data network. The data network includes an
authenticator,
connected to both the register and the application provider. The authenticator
includes
means to receive a request for authentication of a provided client identifier
from the
application provider. The authenticator includes means for generating a
request for a secret
information, such as the home location register personal identification number
or other
personal identification number, from the digital wireless device associated
with the
provided client identifier, and means for receiving a response from the
digital wireless
device that contains the requested secret information. The authenticator
includes means to
-4-
CA 02358732 2001-10-12
compare the secret information to a copy of the secret information stored in
the connected
register. The authenticator also includes means to transmit an authentication
message to
the application provider if the provided secret information and the stored
copy of the
secret information are equivalent.
In embodiments of the system of the present invention, the data network, such
as
the Internet, uses a data protocol such as the TCP/IP suite. In further
embodiments of this
aspect of the present invention, the digital wireless device is connected to
the application
provider by the digital wireless network and the data network. In another
embodiment of
the present invention the authenticator is connected to the application
provider by the data
network. In alternate embodiments, the authenticator is connected to the
register by either
the data network, a connection using standard telephony protocols, or a secure
private
network. In yet another embodiment, the register is one of a home location
register, a
visiting location register or a RADIUS server. In an alternate embodiment the
authenticator includes means for redirecting the digital wireless device to
connect to the
authenticator using only the digital wireless network, and means for
redirecting the digital
wireless device to reconnect to the application provider.
In a third aspect of the present invention there is provided a method of
obtaining non-
repudiable authorisation for a transaction from a digital wireless device,
having both an
associated client identifier and associated secret information by an
application provider, at
an authenticator connected to a register having a copy of the secret
information associated
with both the client identifier and the digital wireless device, comprising
the steps of
receiving a request for a non-repudiable transaction from the application
provider,
receiving a response from the digital wireless device, including the
associated secret
information and providing a non-repudiable transaction verification to the
application
provider upon receiving agreement to the transaction from the digital wireless
device. In
an embodiment of the third aspect of the present invention, the request for a
non-
repudiable transaction includes the terms of the transaction. In another
embodiment of the
third aspect of the present invention the response from the digital wireless
device includes
indication of the agreement to the terms of the transaction. Another
embodiment of the
present aspect of the invention includes the step of providing a non-
repudiable transaction
verification to the digital wireless device upon receiving agreement to the
transaction from
the digital wireless device.
-5-
CA 02358732 2001-10-12
Upon review of the following description of specific embodiments of the
invention
in conjunction with the accompanying figures, other aspects and features of
the present
invention will become apparent to those of skill in the art.
BRIEF DESCRIPTION OF THE DRAWINGS
Embodiments of the present invention will now be described, by way of f;xample
only, with reference to the attached Figures, wherein:
Fig. 1 is an illustration of a prior art network connecting a cellular device
on a
roaming network to the HLR of its home network;
Fig. 2 is an illustration of a system of the present invention; and
Fig. 3 is an illustration of a system of the present invention employing a
redirected
HLRPIN transmission.
DETAILED DESCRIPTION
Generally, the present invention provides a method and system for data based
authentication of a user as the valid user of a digital cellular device.
1 S Currently all digital cellular service providers provide support for a
home location
register (HLR). The HLR is accessible to other carriers with whom the digital
cellular
service provider has roaming agreements. To facilitate modifying services, or
sharing of
accounting information for a user account, a digital cellular service provider
offering
roaming service to a digital wireless device can create a visiting location
register (VLR)
entry. Typically the visiting location register entry is populated with data
from the
subscriber's home HLR.
The HLR's account information details subscribed services, information
regarding
call-forwarding status, and other information such as a personal
identification number,
hereinafter referred to as the HLRPIN. The HLRPIN is commonly used to
activate, or de-
activate, such features as call forwarding and do not disturb, as well as to
login to user
voicemail and corner billing systems.
The transmission of the HLRPIN is commonly performed via a signalling system 7
(SS7) out of band transmission. One of skill in the art will appreciate the
integration of the
HLR in a network supporting SS7 is beneficial to the development of a wireless
intelligent
network.
-6-
CA 02358732 2001-10-12
Refernng to Figure l, the current state of the art regarding transmission of
the
HLRPIN is shown. When a roaming user activates a supplementary feature or
modifies a
profile on a visiting network the request is transmitted by a digital cellular
device 100 and
is received by base station 102 in the roaming network 104 as an out of band
SS7
transmission. This is performed out of band to minimise the bandwidth of the
communication, as out of band transmission use fewer resources than an actual
call based
connection. The base station connects to the HLR on the cellular device's home
network
through the mobile switching center 106 and the visiting location register
108, to transmit
the modification or supplementary service request. Included in the request is
a mobile
device identifier. The request is routed to the home network 110 of the
digital cellular
device 100. The home network 100 routes the connection request to the HLR 112.
Upon
receiving the request and mobile device identifier the HLR 112 transmits to
the cellular
device 100 a request to provide a password, the HLRPIN. Typically the HLRPIN
is a
value chosen by the user, usually four digits in length. Upon providing a
valid HLRPIN
the supplementary feature is enabled, and the HLR 112 notifies the VLR 114 to
update the
VLR profile and also sends confirmation to the cellular device 100.
All communication, between the base station 102 and the cellular device 100,
is
performed in an encrypted out of band channel, while all other communication
is
performed using standard telephone protocols such as the ANSI-41 HLR standard.
Thus,
carriers have established the HLR 112 as valid proof of identity when simple
possession of
digital cellular device 100 is insufficient.
Carriers already recognize the HLRPIN as a method of authenticating the user
of
the digital wireless device, while other means are employed to authenticate
the actual
digital wireless device. An HLR, storing the HLRPIN, that is accessible to an
authenticator used to authenticate users in a data environment, can provide a
means to
authenticate a user of a digital wireless device through a data network.
Additionally other
secured and trusted sources of personal identification numbers can be
substituted for the
HLR while remaining within the intended scope of the present invention. ~f the
aforementioned three substantial concerns, the present invention seeks to
obviate the
problem of ensuring that a handset is in the possession of the authorised
user.
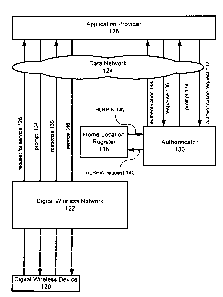
Figure 2 illustrates an embodiment of the system of the present invention
where the
application provider is a trusted identity relative to the carrier. A digital
wireless device
CA 02358732 2001-10-12
120, such as a digital cellular phone or other wireless device capable of data
transmission,
is connected to a digital wireless network 122. Digital wireless device 120
has a uniquely
associated client identifier (client id). Associated with the client id is
secret information
such as a personal identification number (PIN). In a presently preferred
embodiment the
secret information is the HLRPIN. Typically, digital wireless network 122 is a
digital
cellular network designed to allow data transmissions to and from terminal
nodes such as
digital wireless device 120. Digital wireless network 122 is connected to data
network 124
so as to allow connections to a variety of servers including application
provider 126. The
connection between digital wireless network 122 and application provider (AP)
126 uses a
data packet based protocol such as a component of the TCP/IP suite of
networking
protocols. In one embodiment the data network, based upon TCP/IP, is the
Internet. AP
126 provides data based services to digital wireless device 120 through
conventional
wireless data protocols. The authenticator and HLR are normally resident
within the
secure network of the carrier.
In order to authenticate the user of digital wireless device 120, AP 126 is
connected, through data network 124 to an authenticator 130. Authenticator 130
is a series
of software applications running on computer hardware designed to compare
information
provided by digital wireless device 120 to information stored in an attached
register 138,
such as an HLR in a presently preferred embodiment. Register 138 is a database
application, running on computer hardware, that stores client identifiers and
the personal
identification number associated with each. If register 138 is an HLR, the
personal
identification number is the HLRPIN. Authenticator 130 can be provided with a
PIN by
the user of the digital wireless device, which can then be compared to a PIN
associated
with the client id of the digital wireless device that is stored in the
register 138. If the two
values are equivalent, authenticator 130 generates an authentication message
that it
transmits to AP 126 containing information that the user of digital wireless
device 120 has
been authenticated and that service to digital wireless device 120 should be
started.
Figure 2 additionally illustrates the flow of data between elements to perform
the
authentication. For the purpose of the following example, the register is
assumed to be an
HLR, and the PIN is assumed to be the HLRPIN, though it could be other
registers
holding personal information hosted by a digital wireless network provider,
including by
not limited to the visiting location register. Digital wireless device 120 is
initialised on
_g_
CA 02358732 2001-10-12
digital cellular network 122 using conventional means. Digital wireless device
1.20 then
initiates a data call by connecting to data network 124, and through data
network 124 to
AP 126. The connection to AP 126 is initialized with a request for service
128. Typically
this request for service includes the client id associated with digital
wireless device 120,
but if it does not, AP 126 can request the client id from digital wireless
device 120 and
await a reply from digital wireless device 120 prior to proceeding with the
rest of the
connection. Alternately AP 126 can redirect the digital wireless device 120 to
authenticator 130, and request authenticator 130 to provide a client id for
the digital
wireless device 120. Other elements of digital wireless network 122 could be
used in
place of authenticator 130, so long as the element is accessible to AP 126 and
is capable of
identifying the client id of digital wireless device 120.
Upon receiving the client id, typically upon receipt of the request for
service 128,
AP 126 connects to authenticator 130 through data network 124, and requests
authentication of the digital wireless device based upon the provided client
id 132.
Authenticator 130 responds by transmitting an prompt for the HLRPIN 134 to AP
126.
The AP 126 transmits the prompt 134 to the digital cellular device 120 through
data
network 124 and digital wireless device 122. In response to the prompt for the
HLRPIN
134, the user of digital wireless device 120 inputs the requested HLRPIN. The
HLRPIN
forms the authentication response 136 which digital wireless device 120
transmits to AP
126 through digital wireless network 122 and data network 124. AP 126
transmits the
received response 136 to authenticator 130. Authenticator 130 compares the
received
response 136, which contains the HLRPIN, to an HLRPIN provided by the HLR 138.
After transmitting the authentication prompt to AP 126, authenticator 130
requests
the HLRPIN 140 associated with the client id, from the HLR 138. The HLR 138
replies to
the authenticator 130 with its copy of the shared the HLRPIN 144.
Communications
between the HLR 138 and the authenticator 130 can use standard telephony
protocols, or
in a presently preferred embodiment can use data communication protocols, such
as
TCP/IP. When the response 136, containing the user input HLRPIN, arnves from
digital
wireless device 120, the authenticator 130 compares the two copies of the
HLRPIN. If the
two copies are equivalent then a message is transmitted to the AP 126
containing
information about the successful authentication 144. AP 126 then can begin
service 146 to
the digital wireless device 120. If an incorrect HLRPIN is supplied, the
authenticator 130
-9-
CA 02358732 2001-10-12
can inform AP 126 that an invalid login was attempted, and service can be
denied by AP
126. Alternatively, authenticator 130 can repeat the request for the HLRPIN.
Figure 3 illustrates a further embodiment of the present invention where the
application provider is not a hwsted entity to the carrier. The secret
information, such as
the HLRPIN, is provided by the user of digital wireless device 120 to
authenticator 130
through digital wireless network 122, bypassing data network 124 and AP 126.
This is
done to prevent AP 126 from gaining access to the HLRPIN. The method operates
in a
similar manner to that illustrated in Figure 2, but after authenticator 130
receives
authentication request 132, redirection instructions for the digital wireless
device 120 are
transmitted. Redirect 148 requests that digital wireless device 120 connect
through digital
wireless network 122 and directly into authenticator 130. Upon receiving a
cormection
from digital wireless device 120 authenticator 130 issues a prompt for the
HLRPIN 152.
Prompt 152 can be presented directly by authenticator 130, and can contain
additional
requests for personal information or other identifiers from the user, if
desired. Response
136, including the HLRPIN, is then transmitted to authenticator 136. Upon
receiving ,
response 136, authenticator 130 redirects digital wireless device 120 to AP
126; as shown
by flow 154. Digital wireless device 120 reconnects to AP 126, as shown by
flow 156,
and the rest of the method of Figure 2 is used to authenticate the HLRPIN and
report the
results to AP 126. Response 136 can be transmitted through an internal secure
network.
In an alternate embodiment, push technology can be used to redirect the
digital
wireless device 120 to the authenticator 130. Upon receiving a request to
authenticate the
digital wireless device 120 from AP 126, authenticator 130 pushes a prompt to
the digital
wireless device 120, and receives a reply, at which point it informs AP of the
authentication results.
It will be apparent to one of skill in the art that the connection between
digital
wireless network 122 and authenticator 130 can use a direct link using
standard telephony
based data protocols, or can use a data packet protocol, or be managed
directly through
data network 124. Those of skill in the art will appreciate that a variety of
encryption
methods can be used, and are fully contemplated by the present invention.
These include
encryption of the HLRPIN to provide security against eavesdropping or
detection of the
HLRPIN by a third party or by AP 126.
Additionally a clearinghouse can be employed to connect a plurality of
application
-10-
CA 02358732 2001-10-12
providers to a plurality of authenticators, particularly where there are a
number of
application providers, and a number of digital wireless networks with
associated
authenticators. Such a clearinghouse, not shown, can be regarded as an element
of the data
network 124.
In present wireless infrastructures, a VLR is populated with the account
information for a roaming user that is traditionally stored in the HLR. Thus,
while
roaming, the user of a digital wireless device can be authenticated by the
authenticator of
the roaming network using the information in the VLR, instead of being
authenticated by
the authenticator of the home network using the HLR. In embodiments with
clearinghouses as elements of data network 124, authentication can be
redirected to the
home network. Preferably, such redirection will occur over a secure inter-
carrier network.
It will be evident to one of skill in the art that the register, which in a
presently
preferred embodiment is an HLR, is fulfilling the role of an secure database
used to store
and protect user identification and password information. As a result it would
be possible
to substitute a number of similar systems in the place of the register without
departing
from the scope of the present invention. One such possible substitution would
be to
replace the register with a RADIUS server.
The present invention permits authentication of a digital wireless device in
both the
telephony domain, using dual tone multiple frequency (DTMF) signals and SS7
transmission standards, and the data networking domain, using data packets and
such
standard protocols as those in the TCP/IP suite, using a single HLRPIN. The
acceptance of
the HLRPIN as a method of authenticating the user can allow application
providers to
authenticate the user of a digital wireless device with carrier grade
security. Because
carriers are unwilling to allow application providers to bill users through
carrier billing
systems without a sufficient level of security, earner grade security in the
authentication of
the user can remove an obstacle to allowing carrier billing for application
provider
services on a fee per use basis. The cost of implementation is limited to a
one time
modification of the manner in which pre-existing HLRs interact within the
network, and
the manner in which authenticators interact with external networks.
The present invention can also be used to provide non-repudiation for
transactions.
A prompt can be provided to digital wireless device 120 when a transaction is
initiated by
AP 126. The transaction can be approved by entering the HLRPIN, which is then
-11-
CA 02358732 2001-10-12
authenticated by authenticator 130. Alternatively, a payment prompt can be
provided to
authenticator 130 and the digital wireless device 120 can be redirected to
connect to
authenticator 130 directly, whereupon it receives the transaction prompt and
reply with the
HLRPIN as above. The redirection of the authentication can be effected by
means similar
to those used for authentication as illustrated in Figure 3.
The system and method described above, require no drastic changes to current
digital wireless network topology, and as such provide an affordable and
incremental
solution. Additionally the present invention provides a method of
authenticating the user
of a digital wireless device 100 at an application provider 108, without
requiring the
application provider 108 to maintain a database of user identification and
password
information. Additionally it provides the user of a digital wireless device
100 with the
ability to access the services of numerous application providers with the same
secret
information used to verify identity. Due to the use of the client id as a part
of the
authentication it is possible for AP 108 to associate digital wireless device
100 with a
particular user by default, negating the need for the user of digital wireless
device 100 to
key in a difficult user identification sequence.
The above-described embodiments of the present invention are intended to be
examples only. Alterations, modifications and variations may be effected to
the particular
embodiments by those of skill in the art without departing from the scope of
the invention,
which is defined solely by the claims appended hereto.
-12-