Note: Descriptions are shown in the official language in which they were submitted.
07!27!01 13 ~ 36 FAg BELL BLIYh & LCI~h LLC IQ 002
' ' CA 02360040 2001-07-27
~rR ~~ f 1129
~asrr.iption
Mat hod for secure z~c:c:ess to at leapt one variable ;n a
preemptively multitask~nc~-controlled proces5ut system
In exioting and future ~ nf~~crmation process.i.ilc~ systems,
for example rJC,'°t''.aVlldl computero, software objp~i'.~ -
usually aloo ref~rred to as processes - are dtic3 will be
administered usiry Lhe operating 3yatem in such a way
that the hardware syst-am, in particular Ll~a process
processing device wluich is provided in the information
procoosing syst~sm, for example the Y~ucassor, is
utilized unifoi~utly with the aim of high overall
efficiency. In this way, the software mCC~ules which arc
assigned to elm processor by the opexating system -
usually also referred t-.h as tasks - are processed by
the processo,c~. Here, special operating sysi:ams, for
e~amp7.c Windows 95, era provided f~t~ l:lze information
processinq sy5l.~suw which have a monoproe~ssor, i.P. the
information procag:ai ng system has ~j u5L one proce3~or,
said operai.i~lc~ systems aloo permitting m~.~ i r.i -user
operation or m»ltiple-process opet~dLian on a
monoproceasuL - see in this r~a,pect in particular '
"llrchitektur von that ri PbsSystemen" [At~c:l~itecture of
~5 uperatinq Systems], II. Wettorst~in,_ Hansar Studien
Biicher [publishinr~ house]. 1984. f~i~. :r4 et scq. The
operating muc~e which is required for than mulLiple~
process oreral~i on of a procer~aCL is known in the
speciali5l. field under the term "multirrnr~ramming" or
else "multita~ki ng" . lIl t111S way, during the execution
of d l.ask the information proeQSSinr~ system can also
carry out a f»ri:her LBSk 9uCh ds Llle reading of data
f~cmu a storage medium of the information proCeSSiny
system nr for example the dia~ldying of data on a dz~ta
viewing station in a "quasipara11a1" tashion.
furZhermOre, d distinction io made b~twePn
07/27/01 13: 3B FAg __ BEL~,"BOYD & LOYD LLC. ~~ 403
CA 02360040 2001-07-27
c;R H~ Y 1129
- 1a -
"cooperative" and "p~bemptive" multitasking. In the
ca~c of "cooperative" m»1 ti.taskiriQ. each itidlvidual
currently executed l.d~k itself determine, according to
requirements, the time pRriod for which it takes up the
processor, i.e. i.lue
47.~27/O1 19 ~ 96 FAZ, . , BELL BOYL~ & LOYIt LL~' Ii~l OOd
CA 02360040 2001-07-27
GR 99 P 1129
currently twtmimg task decides on tho time when the
processor is relaa~~cJ for the processinq UL Lurtl~Cr
tasks. In t,lie case of "preemptive" multitasking, a task
of the operating syst.~m, known in the specialia ~ ri~sld
as "SC;ti~suler", or even "tack ochoduler" interrupts thR
currently ex~cuted task attar a predefined or as5lyu~~1
time periu~i has finished, i.c. the tim~ when the
proeessor is assigned an~3 released 1s de'~ermluea using
the ~a5k 5~l~eduler.
In nrc~~r to execute a function Ct elm operating
Sys~mu, i.e. for example an operating system task s~.mh
as thr~ task srhPduler, a Special operatlty mule of the
piwu~s3or for protecting tho data of the operating
system task is prnaiciPd which is known a5 supervi,~or or
ke~ul~l mode - sae in particular Andr~w S. Tanenha»m,
"BstriebssystPma - h;nrwurf and Realislei~uy" [Operating
Systems - Design and Implomentation] part 1, Prenti~s~-
Hall Tnf-.c?rnational, 1990. pp 31/32 , Tv clo this, the
~~wc;r~'sor is switched ov~cr using a supervisor call from
a user mode i nto the supervisor mode and l.Z»s cunt~:ol of
Llze processor io thuo transfers~d to the orarafiing
system or ii-g tasks. In Contrast with the supeLVisor
mode, not all instructions are acceptable in i-hR u9er
mode, int-c~r a~lia, in the user mode tyre u5~a of input and
output inatructiono and of ~somm special instrmri~ions is
prohibited. L7.kewise, in the uSr~L modo the acce3o to
all the data i3 gonerally not possible, i_P. for
PxampiP the data of the operatiticl SysCem can neither be
s:ead nor amended for non-operating system tasks-
Specifically in the c;a5c~ of information
processing oyotems which act accor~li ng to the
m"1 t i is sking principle, variak~l~s~ yr blocks of
variable3 which are accessed during the processing of a
t.agk must be protec;Lea a4ainst competing aeee~~ee, for
example by forthor tasks- This wnSUres that: for
example, the errors uu~:urring during dual cimultan~ous
variable ,access cannot lead to any blockages of fuLl.tiei
tasks or of the e~l~i~~
07/27/01 13~37 FAg__ BELL BnyD & LOYD LLC IQ 008
CA 02360040 2001-07-27
GR 99 P 1129
information processing system. Such a protection
mechanism is dPRrriht~d belOW using the fV.~'tuult~tivri
"SGCUr~d dc;c:e~s" tv at least one variable, and the tQrm
variably can rAfRr here both to a varidk~le of a
Soll.waie module which is stored in a m~mory unit and tn
a hardware-relatPrl ~~tting information item w~iiul~ is
stored iri a hardware register. Such secured accessR~
fr~qu~ntly take rlana when specific problciu~ are posed,
for example in information systems which are used tn
contrr~l rea 1 i-.i mP systems but must slay d~:c:ess data
whicri cam Lc a~clministrated, and are of short duration
in comparison i-n 1-.he average time period 't,~e~w~en two
suc:c:c~ssive tank change3 . Consequently, the probahi 1 i i-.y
of a task change during a secure access is very lvw,
k~u~ cannot at all be exvludod.
The implementation of a "sevuz~c access" by a
LaSk can be carried out using rrarious rrnta~t.i~n
mechanicm~. This includes, inter alld, llw setting of a
~d5k change inhibit in order to avoid a cnmrei-ing
access by a further task to the vdi~ldLles which are
being accessed by the task currently running On the
grocessnr. To do this, before the varad.)Jlrs to b~ read
are accessed u3ing a supervisor call, thA prnr.PSSOr is
switched wPr. into the supervisor rnOde dll~l the netting
2J of a task change inhibit is reqLtestpd firm the
vnRr~ting system in order to cLL~in exclusive access
Lur the processor, and thus also for the c~e:Sired.
variahlc~, for the currently acce55iug task. Then, the
p~uc;es5or is switched back into the user mr~r_iA and the
dRSirPd access to the variable c;dl be secured by the
previou3ly interrupted task, i.e. withrnW interruption.
After terminat~.on of the sec;ut~e access by the currently
running tank, it is necessary tn ~hanc~P 3f~a1.11 3.hto 'the
4»pervisor mode by rct~am of a supervisor call and for
the torah changQ inhibit to be ra:~~t by 'the operatlnq
system in said rtLUC.Ie. In order tv further proc~ss the
torah which is currently tn ha processed,
07/27/01 13:37 F~--,. BELL BOYD & LOYD LLC ~d4A6
CA 02360040 2001-07-27
GR 99 P 1129
- 4 -
l.tie (JtUl:hlIS.9V1 15 then changed back into the user mode
and the times monitoring activated during tree s~sLLing of
t,lm l.aak change inhibit i3 deactivated in ordor to
avoid thp processor being blocked rug an
indeterminately long time.
A .fmrt.ha~r method of implementing a ~~~:uzo
au~~~s i5 used in the 3ynchroni~ation of tasks, i.e.
the coordination of a plurality of Ld,'ks which
alL~inc~tely accede the procccoor, in order to avoid the
confli~t~ which occur in the multitaskitty j«use. Here,
the semaphore technique is frequently used for the
synrhrnni~ation of 'Che individual tasks. A~~:ording to
its mathematical-theoretical definition, a sema~hnrP is
an integral, non-negative variable assculdt.ed with a
l~ queue. IIere, the initial value of the semaphore dafi»Ps
how many t~Rkg can be located sljuullaneuusly in a
secured section controlled by a somaphore_ The d'»~a»P
rn»fiains the tasks which wait for ~l~e secuxed section
to be entered. To do this, a semaphore is checked anc~
mnrli f'i pd by the currently running l.ask in order to
implement the secure aaaess to a variable by mP~ns of
an un;ni-.prruptible read/wriLe cycle. It, Lur c~ample,
thi3 semaphore io greater than zero, it is cta~ra~mPnted
and i-hw gPCUre access to the deslred v~ar~.able is
2r subsequently aarricd out by the currently r~.~nning task.
Tt the semaphore is already eduai to zero, the ta3k
which reque3to a secure access is changed intq the
waiting state and the 5elua~kmi~s variable is not
changed. At the and of th~ secure ar_.cess r.n r_he
at) variable, it is checked whether tasks ar~ waiting on
thi3 ~cmaphore, and if appropriate, nnP of the tasks
Located in the waiting state is activated, i.e. the
proccacor is assigned. If there is nn i-.agk waiting on
the semaphore. Lh~ s~um~rhore i5 incremented again by
35 mcana of an uninterruptiblP .rPa~l/write cycle. These
uninterruptlk~le ~~sad/write cycles to the semaphore
variabl~ can either be iznplamRntPd, in 3 way similar i.u
O,Z/27/01 13 ~ 3'~ FA.g BELL BOYD & L~IYD LLC IQ t147
' CA 02360040 2001-07-27
GR 99 P 1129
_ 4~ _
Llze method o~ the task chango inhibit, by a supervisor
~a11 end the subsequent handling by l.tle upcrating
system or in the user modc with epeaial
07/27/01 13 ~. 39 FAg BELL BOYD & LOYL~ LLr.. IQ 02i
i
s
a
~i
,GR 99 P 1129
_ 5 ~ii
support by the processor hardware anrl ~,r~c:aa:5cr hus
t~ard~ua~e. Hraie Lou, time moriitoring, whose function
consists in avoiding the prc~cP~ssn.r, hAi ng h1 cr_kPd for a
1U11C~t'L l.haii average time, i5 provided fox the duration
cf the 9eourr~ aw:ras:~ _
Im ~lre previously de5c~ribed implemontation3 of
a s~acure ar_.ra~s t~ vari ~h1 Pq, '~a plurality of operating
IILUC~C ~:lldlit~~3 including the associated technical
operating task ~rn~R~~ing or special support by
lO processor hardware and pros~asor buo hardware are
necessary ~iurin~ a~rh ,~r_r.Pgs, i.e. secure accesses to
variables increase the loading on tho procegeor or
raquiro ar~ditiona.l ann ~par.i ~1 l~~y supporting hardware.
The object on which 'the invention io based
rnnRi~tR in improving the implementatian of a secure
y
access to at least one variable in a precmptivcly
muftita~king-ncntrcLlPd processor system. The object is
achieved by means of the fcaturco of patont claim 1.
Tha PQ9Pnti.al aspect of the method according to
the invention is that an aceaoa otatua mQmory is
nrovina~l in a preemptively: multitasking-con~.cwlled
processor system for 3eeure ~accoca to at least onQ
variable, into which access status memory a blockliic~
information i.t~m is input by the accessing task b~foro
a current access 'CO at least one variable. Furthermore,
when thcrc is n task change int~ndod by the task
scheduler during the current access, the task sermaule~~
check3 the aaoeaa status memory for a blocking
intnrmatinn item which has been input and when the
blocking information itom has bean input the task
scheduler delays the intended task change. >rludlly, the
teak change information atom i.a input into tho access
status memory usin~t said blocking informs l.lcm i Lr~w. At
the cnd o~ tho current sac~ss, a release information
item is input into the acc:G~S ~~aLua memory by the
currently accessing task (T1); 2n~1 whwn ~ task change
information item is icyu~
AMENDED SAGE
CA 02360040 2001-07-27
07/27/01 13 ~ 39 FAX BELL BOYD & ~ ~IYD LL~' td 422
. '
.GA '39 P 1129 i
- 6 -
the roquoated task change i,s irnitiated by the currently
accessing task (L1). The use ~of an additional accc~s
ctatu~ memory has the advantage that the Swir.ahinQ over
of the processor ittLc elm supervisor mode, which, for
example, is necessary with tliR task changing inhibit
method, and the subsequ~ul. Gxdcuticrn of an operating
oy~tcm task are dispensed with, an~1 ~ c:onsiderable
dynamic reliev.~uy ut the leading on the prooeaaor is
thus achieved, especially since ~ProrP accesses to
variables oc;uur v~ty frequently when certain problems
which occur during the orerati~n ~fi an information
processing aysLE3llt dtl5°lS. Iiz addition, the inputting of
the blocking informat i nn i 1-.Pm, the task change
information item vi' L1-ie release information item
r~quiros only a few ma~hina in9tructions and is Lhus
easy La implement in terms of programming technology.
Furthermore, in the mathcci according to the invention,
j,tl C:UIIL~~st to the semaphore ~tcahniquc, no additional.
hardware supgort in thA farm bt processor hardware or
ZO rJ.IUC:~55UZ Lus hardware is nec~asary, which leads to a
cost-effective irnplAmPntation ,of the secure access Lc
variables which is net tied to apeeific hardwar~.
Furthermore, W.~ring 1-.hP secure access the accessing
task .LS advantageously not interrupted by a tack change
which is intendarl by a further task, and in addil,lcn
Lhe intended task change io snot reject~d but rather
delayed so that afi-.ar the evaluation. of the task chance
lmr~L~nation item at the end of the secure access the
intended task chanr~R r.~n he directly retrieved Ly the
Lark scheduler.
turther essential aspect of ~lr~s umthod
according to the invention ~ic that in addition to
ingz~i:ti ng the task change information lletu a time
monitoring 3ywtcm with s, time period comer;aing at
last the duration of the secure ac:c:ess is activated,
and that the current access :is terminata~l otter the
pxpiry of the defined l.l~m N~siioa - claim 2. The time
AMENDED PAGE
CA 02360040 2001-07-27
4T/2T/4i i3 ~ 39 F.4g BELL BOYD & ~~ 4YD LLr_. IQ 423
GR 99 P 1129
- 63 -
uwili~c:ming system in the mothod according t~ the
inv~ntinn i ~s advan'Gageously hot c~a~s~~a7.ly activated
du~~iu~ tha initializatior~ of a'~ s~cure access h»t. rather
only when there is a task ch~.nqe imL~nd~d during the
current acce~3, and
.;
i
AMFNDE~ ~IYHtJ~
' .i
CA 02360040 2001-07-27
-_ 07/27/01
13: 39 FA7C
~._ BELL
B41YD & ILOYD
LLG td 02d
i
~I
' ~ ;
~GR 99 P 1129
_ ,I _ i~
I~
i
the dynamic loading, which is
i~usually nac-.Pgsary during
the use nfi the already krmwmvethods,
for oxampl~
SleittdptluZe teohniquE or the
setting of ~ task Charige
inhibit-, is thus dispensed lith.
Thi3 lcad~ to an
additional dynamic roliQVinr~j~
of the load on Laic
information processing systew
~t tl-~e processor.
, I
According to a furtheri i refi nament o~ the mettrCd
accordinr~ i-n the iriventiori, e c:ur~temts of the access
tl~
a~dl.us memory arc check~d a ~ the any of the secure
i
re the i iutting of the r~loase
b
f
y
o
e
accass and
iufo~:mation item ao that when l task change information
i
itam is present Lhe ac~ivaLed; ~time monitoring system is
deactivated and a t~ehnieal o rarafii.ng iri~ormal.iur~ item
i '
whi nh initiates the inl.el~cicdiask change is transmitted
t
1~ to the took scheduler by the
~rrently acCessinc~ ~dsk -
rlaim a. The CheCklnq UG LlZui'
contents of th~ access
status memory advantagoouqJyll
PnsurCS that. directly
2ttRr termination ut the ~ocurc
access, the task
scheduler is informed abo~~t
the intended tank change
9f1 which is in,dicaLec3 Ly the tas~C
change information i t.Pm,
i on o~ l.lie technical
~r
indi c-
t th
h
i
. .
e
t
ou
because w
nppratiric~ informativ~l item ch indicates the intPn~lR~l
whl~
task change th~ task srhR~lo r Would riot cas'ry out the
I e~
riR I ayed task Change. xustead,;lthe intended task chanr~A
25 would bo carri~d out at the ti me at which t)ae c:uZrently
accessing task is interruptc~ ~ by th~ task s~-hRduler,
i.c. the ~.ntendvd task rhanlq~ e would be u~rrmcesaarily
i
delayed beyC~l~t the time periodof th~ secure 2n~~gs.
Further advantac~PCUS ' ~e~inements ur the method
:iU according t~ l.ne invention ca xi be found in thR further
claims.
The tuel.Zlu~l according ~~to the invention wi I1 be
explain~d in mnra detail b ,~lOW wilt ~efvrence to 3
i
figure. '
I.
AMJ;NUJrU;I PAGE
CA 02360040 2001-07-27
07/27!01 13' 98 FA7C BELL BnYi~ & LOYD LLC Id p19
CA 02360040 2001-07-27
~Ft 99 P 1129
- R -
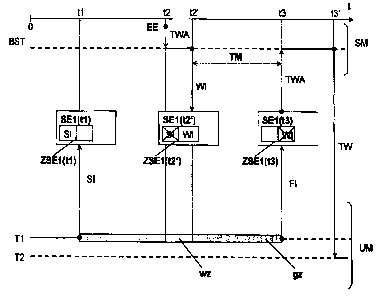
In 1:'iqure 1, a first and a occond us~r task T'I ,
T2 and an operating sy~tPm task tiST are represented by
way of example ac:c:~~dilzg to their procoseing ovQr time
by th~ processor of an information proeer55irrg system
which ac:t~ according to the pre~mptive molt; t~.a9king
method. Furthermore, ~ 9npervisor mode SM and a user
mode UM of Llm processor and the associated taskq are
indicated by two sPp~rate areas. Hire, in the
supervisor jLLUCl't.~' sM the operating cyst~m task BST, 1 at:er
also called s~hPduler ox task scamciuler D3T, i3
represented toi processing by the procmssor, and in the
user mode a firm-. and a second user ldsk T1, T2 for tho
prcvessing by the processor are illustrat.ad by Way of
~YamplQ_ A task which ~.s Currently in the waiting
stale - frrr example in particular thQ operating system
task BST at the time zero in figuL~~ 1, and the 3ccond
user ~ld5k T2 - is indicated using a hr~k~n line
designated by 13ST 8rid T2, and et c;uirently e~ecutcd
task - Llr~ first user tank Tl at the timR Pro in
FigurQ 1 - i ~ i.ndicazed by an unlat~ukem line designatod
Ly T1.
zn order to represent ~ltm Liming sequenec of
the method according to the invention of a secure
aceQSS 7z tn ~t least one variable, a time aacis t is
p~uvidod on which a first, second, third, tourth and
fifth time tl, t2, t2', t3, t3' arc mark~d.
Fuztha~-more, a momory unit SEl with an access status
mam~ry unit GSE1 at the rust, third and fourth time
l1, t2', t3 is illuotrated, information relating to l.lm
first, currently running ld~k T7. being input in the
memory unit ZSE1, and the memory can be implemented,
for Rxample, a9 part of a v~la~ile memory. Aaaording to
the method according to the i.nvwni:ion, inter alia, d
b.Wc~.ki ng iriformatlvu item SI, a ta3k chang~ information
item WI and a rolaase informai~.i nn item FI Can be lyut
into Lhe access status memory unit ZSEl whir~h ig
aasignod to th~ first, r»rrently running user task T1.
47/27/41 13 ~ 38 FA7C BELL Bf~YD & LOYD LLC IQ Oid
~. _. ,
CA 02360040 2001-07-27
c;H 99 F 112s
Furthermore, Lhe duration of a oocur~ access r~z
to at least onQ 'vari ah1 P by the first uses' L.ask T1,
Which eXtendS r~'um the first time t1 to th~ fourth timR
t3, is illustrated_ At the time Zero, tW Lirst user
'Cask T1 i~ already currently assigned to the prcr.PSSOr
and the second user i-.~ s k '1'2 and the opera Lir~g system
task BST aiw in the waiting Mate. At the first- time
tl, the first user task 'I' I initialises a Secure acces3
to aL least elm variable, i.c. the blocking information
item SZ is inr»i-. into the aCCeSS stdLu~ memory unit
ZSE1 (tl) key the first u3cr task T1 instead ni~ the
r~laase infnrm~fiion item FI which ie input into it.
Then, Llue first, currently e.~ecuted user task T1 i8 in
3n uninterruptible axPC:ution state and c;acs thus access.
the desitwsl variables in a oocured fashion.
At a later., gPaond time 1.2, a task change
request TtnTA is indicated sac 3 result, for Pxamp I P, of
an external Pvent bE, for exartyle the presence of
extermdl messages or ac 3 result of the t.imP period
which 1R aR~igned to the first user Cask T1 by the tack
Sul~~eduler DST being exc~eded and the currently
executed, first user Lask Tl is Llien changed into a
quasi-waiting state wx by the task sched,~1 ~r B5'f. '!'hen.
before the task scheduler BST inii.ldles a task chango
Tw otter the task change r~quast TWR hay hPPn received,
said i-.~gk scheduler BST cliec:ks the contents of the
ac;ur~ss status memory unit ZSE1 (t2' ) - Tt a blocking
information item SI relating Lu a third time t2' is
input in the acces3 memory unit ZSE1(tW ') for the
currently axPCUted, first user Lask T1, the requested
Ldsk change TWA i~ delay~d by the t~!ak scheduler 85T
and ins'tRaci of the bloCkinq lut~rmation SI a task
change informotion item WI is i np»1-. into the acce5a3
stat,m memory unlL Z3E1(t2'~. Then, the first,
3~ currently cxeauted user task T1 is further proc:c~ssed
and the quasi-waiLiy state wz i3 thus terminated a~~in
by the task sch~dulwr BST . 'I'hP first usew l.ask T1 can
thus
07/27/41 13 ~ 38 FAg BELL BOYtt & LOYD LLr_. IQ 415
CA 02360040 2001-07-27
VH 99 p 1129
_ 1
Carry on Ltitt ,secure acces3 (gz) for thQ de~i red
variables withnW it being forced l.v release the
proCeSSOr by Lhe task scheduler HST. In addition, at
the third time t~', the task scheduler BST activates a
time mcillCoring system TM in order to avoid the
processor being blr~rka~l by the secure access gz of the
first uset~ ~d'k T1 for an unaacoptably long time.
At the end r_,t trtP secure access c~z - indicated
by way ct example in Figuro 1 as the fourth time
t3 - the cnntRnts Ot the aCCe55 SldLus memory unit
ZSEl(L3) are firstly eheo)sod for th~ presancp of a task
changQ information item Wr. IL nu task chango
inr~rjudtion item WI hac boen input in the a~~PSS status
memory unit ZSF1 (t:i) , the currently dc;cdc~sing, first
user ~d'k T1 inputs the releas~ information item fI
in>stgad of the present blockirl~t lrifurmation item SI,
and l.he secure acccac gx ie thus terminat.e~.d, i.e, the
currently accessing. first uset task T1 can then b~
iiil.ei.cupted again. The currently acc~sssind, first user
task T1 r_.an then access the pt~cc:rsssol until the task
5clm~luler DST provides fox a task chanc~R TW, i.e. the
time of use ~f the processor which is assigned to tho
titst user task T1 by tho task scha~ltller J35'1' has
expired or ~ task change request TWA is indicated to
l,lw task scheduler HST by an external AvPnt 1';E.
I t . on the c l.~ld~ hand, a tae k change
ir~formation item WT is input, a task ~h~nge request 2WA
is rli rPCaly indicated to l.tm teak scheduler BST - as
Illustrated in Figure 1 - ao that, attar r.he procesaitiy
of the agsociazed technical uYcrating task3, it can be
used to carry out a task change TW. In addition, Ltie
re)aa4e! information ~.tem Fr is input into the accmss
status memory unit ZSE1(t3) by the first user task T1
instead of the iyuL task change information item WT
and after the s~cure access c~~ has been termirm~~~l the
time monitoring ~y~~em TM is deactivated. Furthermore,
the ta3lt scheduler BST which is exevuLes in the
supervisor mode SM
07127101 13 ~ 3$ FAZ BELL BOYD & LOY11 LLC I~ 01B
CA 02360040 2001-07-27
'GR 99 P 1129
- 11 -
extxact5 Ltxc~ ,proaeasor from the first uc~ar tack T1 any)
changes .it to tha wai.tinQ State.
Theu, in the time period between the fourth anc~
the fifth times t3, t:i~ , i:he technical o~e~~dLinr~ tasks
whic;ti die provided by thc~ task aah~duler BST fnr a task
change TW are prn~Pgsed within the sup~rvisvr mode,
i.e. d task change TW is carried out by the ~~Prating
cystam. For the pxPautiori of'the 5~c:und user task T2
whlcal Lhe processor has 3asignad at that ~~ri~.i c:ular
time, the prcaPSSOr is switched over into the user modo
and l.lie ~e~::vnd user task T2 can thus be assigneri t.~ the
processor start~.i ng t=om the fifth time L3' .