Some of the information on this Web page has been provided by external sources. The Government of Canada is not responsible for the accuracy, reliability or currency of the information supplied by external sources. Users wishing to rely upon this information should consult directly with the source of the information. Content provided by external sources is not subject to official languages, privacy and accessibility requirements.
Any discrepancies in the text and image of the Claims and Abstract are due to differing posting times. Text of the Claims and Abstract are posted:
| (12) Patent Application: | (11) CA 2363655 |
|---|---|
| (54) English Title: | METHOD FOR CREATING AND PRESERVING AN IDENTIFIER |
| (54) French Title: | CREATION ET CONSERVATION D'UN IDENTIFICATEUR |
| Status: | Deemed Abandoned and Beyond the Period of Reinstatement - Pending Response to Notice of Disregarded Communication |
| (51) International Patent Classification (IPC): |
|
|---|---|
| (72) Inventors : |
|
| (73) Owners : |
|
| (71) Applicants : |
|
| (74) Agent: | NORTON ROSE FULBRIGHT CANADA LLP/S.E.N.C.R.L., S.R.L. |
| (74) Associate agent: | |
| (45) Issued: | |
| (86) PCT Filing Date: | 2000-02-17 |
| (87) Open to Public Inspection: | 2000-08-24 |
| Availability of licence: | N/A |
| Dedicated to the Public: | N/A |
| (25) Language of filing: | English |
| Patent Cooperation Treaty (PCT): | Yes |
|---|---|
| (86) PCT Filing Number: | PCT/FI2000/000124 |
| (87) International Publication Number: | WO 2000049767 |
| (85) National Entry: | 2001-08-16 |
| (30) Application Priority Data: | ||||||
|---|---|---|---|---|---|---|
|
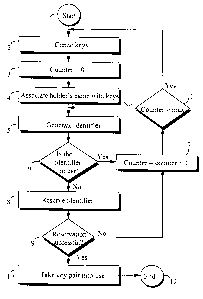
A method for creating a global unambiguous identifier for predetermined data
structures and for storing identifiers created. In the method, an unambiguous
identifier is created from a key and/or keys associated with an encryption
and/or signing procedure and/or from key holder information and/or other
information. From the identifier, an unambiguous hash code is generated using
e.g. a hash function. The hash codes thus generated are stored in a
centralized place so that each hash code is unambiguously associated with a
given juridical person and a given key pair. The hash code can be used e.g. as
a part of encrypted messages sent by a mobile station in a mobile
communication system so that the user can infer from the identifier how the
message can be decrypted into plain language.
La présente invention concerne un procédé permettant, d'une part la création d'un identificateur global univoque destiné à des structures de données, et d'autre part la conservation en mémoire des identificateurs créés. Pour créer un identificateur univoque, le procédé consiste à partir d'au moins une clé associée à une procédure de cryptage et/ou de signature, et/ou à partir d'au moins une information portant éventuellement sur le détenteur de la clé. Pour générer un code de hachage univoque, on part de l'identificateur que l'on soumet à une fonction de hachage. Le code de hachage ainsi généré est ensuite stocké dans un lieu centralisé de façon que chaque code de hachage soit associé de façon univoque à une personne morale et à une paire de clés définie. Dans le corps d'un message crypté envoyé par une station mobile d'un système de communications mobile, ce code de hachage peut être utilisé de façon que l'utilisateur puisse déduire de l'identificateur la façon dont le message peut se décrypter en langage clair.
Note: Claims are shown in the official language in which they were submitted.
Note: Descriptions are shown in the official language in which they were submitted.
2024-08-01:As part of the Next Generation Patents (NGP) transition, the Canadian Patents Database (CPD) now contains a more detailed Event History, which replicates the Event Log of our new back-office solution.
Please note that "Inactive:" events refers to events no longer in use in our new back-office solution.
For a clearer understanding of the status of the application/patent presented on this page, the site Disclaimer , as well as the definitions for Patent , Event History , Maintenance Fee and Payment History should be consulted.
| Description | Date |
|---|---|
| Inactive: Dead - No reply to Office letter | 2003-12-04 |
| Application Not Reinstated by Deadline | 2003-12-04 |
| Deemed Abandoned - Failure to Respond to Maintenance Fee Notice | 2003-02-17 |
| Inactive: Status info is complete as of Log entry date | 2003-01-10 |
| Inactive: Status info is complete as of Log entry date | 2003-01-09 |
| Inactive: Adhoc Request Documented | 2003-01-09 |
| Inactive: Delete abandonment | 2003-01-09 |
| Inactive: Abandoned - No reply to Office letter | 2002-12-04 |
| Inactive: Abandoned - No reply to Office letter | 2002-11-19 |
| Inactive: Transfer information requested | 2002-09-04 |
| Inactive: Correspondence - Transfer | 2002-08-07 |
| Inactive: Single transfer | 2002-05-06 |
| Inactive: Courtesy letter - Evidence | 2002-04-18 |
| Inactive: Single transfer | 2002-02-26 |
| Inactive: Courtesy letter - Evidence | 2002-01-22 |
| Inactive: Cover page published | 2002-01-18 |
| Inactive: Notice - National entry - No RFE | 2002-01-15 |
| Inactive: First IPC assigned | 2002-01-15 |
| Application Received - PCT | 2001-12-28 |
| Application Published (Open to Public Inspection) | 2000-08-24 |
| Abandonment Date | Reason | Reinstatement Date |
|---|---|---|
| 2003-02-17 |
The last payment was received on 2001-08-16
Note : If the full payment has not been received on or before the date indicated, a further fee may be required which may be one of the following
Please refer to the CIPO Patent Fees web page to see all current fee amounts.
| Fee Type | Anniversary Year | Due Date | Paid Date |
|---|---|---|---|
| MF (application, 2nd anniv.) - standard | 02 | 2002-02-18 | 2001-08-16 |
| Basic national fee - standard | 2001-08-16 |
Note: Records showing the ownership history in alphabetical order.
| Current Owners on Record |
|---|
| SONERA SMARTTRUST OY |
| Past Owners on Record |
|---|
| HARRI VATANEN |
| JUKKA LIUKKONEN |
| MATTI HILTUNEN |