Note: Descriptions are shown in the official language in which they were submitted.
CA 02371755 2001-10-24
WO 01/63545 PCT/(JS00/06826
Authorized User Verification by Sequential Pattern Recognition and
Access Code Acquisition
Cross Reference to Related Applications:
Disclosure Document Program (USPTO): 465535 23 November,1999
Background - Field of Invention:
This im~ention relates to bank cards, cred'tt cards, debit cards, smart cards,
communication
cards, financial transaction cards, student cards, employee cards, medical
cards,
identification cards and any other card based system that requires an
authorized user to
recall and enter a code in order to gain access to a protected resource,
information source or
service. This invention is also related to non-card based systems such as
Internet and
to Intranet access codes, computer codes, alarm codes, lock codes, wireless
codes or any other
non-card based code which requires an authorized user to enter a code in order
to gain
access to a protected resource, information source or service.
Background - Description of Prior Art:
y As computers have become more predominant in everyday life, it becomes
evident that
business in the near future will be transacted, in a larger part, on the
electronic
superhighway or the Internet. The convenience of shopping the Internet and the
utilization of e-~mmerce has already begun to permeate our lives. Credit card
transactions and product orders on the Internet are now commonplace. However,
along
2o with this newfound convenience, security and user identification remain
valid and primary
CA 02371755 2001-10-24
WO 01/63545 PCT/US00/06826
2
concerns.
The immediate solution to these security issues and concerns is a multitude of
PIN codes,
passwords and passcodes for each individual protected resource. In other
words, Internet
and credit card users are becoming overwhelmed with well-intended security
codes. Even
though passcodes (passwords which do not form recognizable words) are
extremely secure,
attempts to recall a meaningless jumble of upper and lower case characters is
unrealistic
and impractical for most users. The avalanche of PINS, passwords and passcodes
has
become so overwhelming that mamr users often breach the intended security by
writing
these codes in convenient places which are easily available to unauthorized
users.
io
In today's marketplace, four requirements are paramount in granting access to
an
authorized user of a protected resource: (1) authorized user identification,
(2) verification
of authorized user identification, (3) unauthorized user access rejection and
(4) an
appropriate level of security to protect the resource from unauthorized use.
For example,
when a user (authorized or unauthorized wishes to withdraw funds from an
Automated
Teller Machine (ATM), a bank card is inserted into the ATM and the authorized
user of the
card is identified via data transferred from a magnetic strip or an electronic
chip within the
card to a system database. To verify that a user is the authorized user of the
bank card
inserted into the ATM, the ATM prompts the user to enter a Personal
Identification
2o Number (PIN code) which is only issued to the authorized user by the
grantor of the bank
card. If the PIN entered by a user is identical to the PIN issued to the
authorized user, the
user is verified as the authorized user and the transaction is allowed to
proceed. The
security afforded by this transaction im~olves possession of the bank card
issued to the
authorized user, knowledge of the PIN code, and card deactivation if a
consecutive series of
incorrect PINs are entered into the ATM system. Theoretically, this security
system is
adequate to prevent an unauthorized user from gaining access to an account,
but
unfortunately, unauthorized access to protected resources has become a billion
dollar
problem. The resolution of this problem lies in understanding the weaknesses
of the
present systems and how to effectively eliminate those weaknesses while
simultaneously
go maintaining simplicity, security and efficiency.
As the PIN system of security became the standard for verification of an
authorized user in
both card and non-card based systems, authorized users were subsequently
required to
recall a plurality of PIN codes in order to gain access to protected resources
and services.
Tlvs preblem of excessive recall was resolved on the user level by recording
PIN codes in
writing and carrying a copy for easy reference in a wallet or purse. However,
this was a
direct compromise of the intended security afforded by the PIN system and
could result in
CA 02371755 2001-10-24
WO O1/G3545 PCT/US00/OG82G
3
easy unauthorized access to related accounts if the wallet or purse was
stolen. The recall
problem was addressed on the grantor level by allowing the use of personalized
PIN. In
this way, an authorized user could eliminate recalling a multitude of PIN
codes by making
all PIN codes identical. In other words, personalized PINS allowed an
authorized user to
choose a single PIN code for all protected resources, and additionally, a PIN
of personal
choice. However, if the personalized PIN was easy to guess, such as the
authorized user's
birth date or phone number, an informed unauthorized user could gain access to
all
protected resources with a single intelligent guess. Today, the major
disadvantage of
personalized PINS is the requiremern of identical code length with constant
and
to unchanging characters, usually numerals. Gaining access to the Internet and
e-commerce
environments with an increased level of security has changed access code
requirements
with respect to code length and the alphanumeric mix of code characters.
Internet sites
may require access codes of eight characters with a minimum of two numerals or
may issue
a code of their choosing of varied lengths. Therefore, personalized PINS only
resolved the
excess PIN memory overload problem for a short period of time.
With the advent of the Internet and e-commerce, the security level intended by
the four
digit PIN code system was inadequate for the computer based environment and
became
obsolete overnight. PIN codes were replaced by passwords, or words in the
authorized
2o user's native language that were of sufficient length to increase security
and that could be
eas~7y recalled. The password system increased the level of security, but
eventually users
recorded their passwords near the computer to avoid confusion with other
passwords
associated with a multitude of other applications and protected resources. The
plurality of
FINs problem, from the not so distant past, was replaced with a plurality of
passwords.
However, this new problem of too many passwords was resolved with software
that
allowed an authorized user to record their user log-on name and password in
computer
memory for automatic submission to the protected application or resource.
However, if the
computer was stolen or sold without erasing the codes, it became easy for an
unauthorized
user to gain access to all protected resource codes held in computer memory.
Additionally,
go if an authorized user traveled on business and needed to use a protected
resource which
required the entry of an access code, and that code was only recorded in the
memory of a
home based computer, the user would be unable to gain access to that resource
unless the
correct code could be recalled. In other words, security and accessibility
were
compromised for convenience when codes were recalled by computer software.
Computer passwords were eventually replaced with passcodes that contained both
numeric
and alpha characters of an adequate length. This greatly increased the level
of security, but
CA 02371755 2001-10-24
WO 01/63545 PCT/US00/06826
4
if the highly secure passcodes were logged into computer memory for automatic
submission as mentioned previously, the intended security level and
accessibility was also
potentially diminished.
There are a multitude of examples depicting the limitations associated with
human
io
memory, code recall, and maintaining the intended level of security.
Presently, there is no
simple and effective system of authorized user verification with an adequate
level of
security to prevent unauthorized use, but attempts have been made to better
the present
systems with human limitations in mind
Method and apparatus for improving security using access codes, US Pat. No.
5,289,583 b3'
Parrillo is an attempt to increase system security by varying the four digit
credit card PIN
code in a predetermined sequence in order to thwart any attempt by an
unauthorized user
to obtain the PIN by observing the PIN key pad entry of the authorized user.
Since the PIN
i5 entered by the authorized user was only valid for the transaction in
progress, and since the
PIN for the next transaction would be different, any attempt of unauthorized
use by
observing or recording the PIN and account number key pad entries of the
authorized user
would be in vain. This patent also utilized the standardized telephone key
pad, and the
accompanying alphanumeric designations, to aid in PIN recall. A four letter
key word was
2o chosen and referenced to the alphanumeric telephone key pad to aid in PIN
recall. This
type of mnemonic aid could become very complicated with multiple PINs
requiring the
authorized user to recall specific words for specific PIN codes. Security
could be selectively
increased by changing more than one numerical digit in the PIN as the code
progressively
changed in said predetermined sequence. However, to achieve increased,
security, the
25 authorized user was required to recall complicated and unreasonable
scenarios malting the
system highly impractical. Parrillo's patent did have some of the very
important key
features used in my patent: transaction specific PINs and PIN code variation.
My patent
improves this patent by requiring the authorized user to only recall a single
sequence to
obtain a plurality of PINS from any geometric configuration, eliminating the
use of the
3o alphanumeric telephone key pad, the associated key words as mnemonic aids,
and
elimination of complicated memory steps to incxease security.
Telephone based credit card protection, US Pat. No. 5,513,250 by McAllister is
another
attempt to increase PIN system security by permitting the authorized user to
limit card or
35 ~o~ access by incorporating specified parameters such as time frame,
geographical
area, dollar limit and a temporary PIN into authorized user access
requirements. In order
for a transaction to proceed, all of the parameter requirements specified by
the authorized
CA 02371755 2001-10-24
WO O1/G3545 PCT/US00/06826
user had to first be satisfied. This system definitely increased PIN system
security, but at
the expense of the authorized user's time and energy. Since the authorized
user was
required to input the associated parameter limits prior to card use, the
proposed system
was both very impractical and inconvenient. However, McAllister, like
Parrillo, did
propose the use of a temporary PIN to increase system security. My patent
improves on
McAllister s patent by requiring no authorized user irnrolvement or
inconvenience to
enhance system security on a credit card or resource on a use-by-use basis.
Personal Identification system, US Pat. No. 5,251,259 by Mosley is a patent
that increases
1o system security by varying a three or four digit PIN with respect to the
day of the week, the
number of card uses in a garticular day, and an alpha word key to indicate
which columns
of numbers within a matrix held the valid PIN. This system requires the use of
a matrix
decoder to obtain the correct PIN codes. If the authorized user were to lose
the decoder or
forget how many times the card was used in a particular day, even the
authorized user
i5 could not gain access to the protected resource. Mosley's patent increased
system security
by making PIN recall extremely complicated. However, Mosley did have a clear
vision of
the problem of insufficient system security, and once again, resolved the
problem by
variation of the PIN. My patent improves Mosley's patent by encompassing the
same high
level of security without the use of a decoder and the complications of
decoding a simple
2o three or four digit PIN code. My patent also does not require the
authorized user to
remember how mad times a particular card has been used in order to properly
decode the
correct PIN.
Memory Aiding Device for Credit Card PIN Numbers, US Pat. No. 5,~42,~35 by
Kohut,
25 uses a sequential pattern within a standardized geometric matrix to recall
an authorized
user's dedicated PIN code. This patent offers an adjustable level of system
security by
increasing the number of positions within the geometric matrix and the length
of the code.
Kohut simplified code recall by using a single secret sequential pattern
chosen by the
authorized user to recall a plurality of different codes across different
credit cards and
3o protected resources. However, Kohut's patent could not vary the PIN code,
allowing the
use of transaction specific codes, thus somewhat limiting system security. My
patent
improves Kohut's patent by eliminating the use of dedicated PIN codes,
passwords and
passcodes by substituting transaction specific codes only valid for the
specific transaction
in progress, and for a limited period of time. Also, my patent permits a
higher level of
35 system security through a combination of geometric matrix position size,
code length, code
time out, and the use of transaction specific codes which are random, and
therefore,
immune to observation attempts of unauthorized users.
CA 02371755 2001-10-24
WO O1/G3545 PCT/US00/0682G
6
In summary, all of the patents mentioned above are primarily designed to
increase the
present level of system security associated with protected resource code
recall, such as PIN
codes, passwords and passcodes. In many cases, system security was increased
at the
expense of practicality. The true nature of the code recall problem is that
human beings do
not remember numbers, words or a combination of alphanumeric characters for
any length
of time unless some form of constant reinforcement is applied. For example, we
can readily
recall our address and phone number because these numbers and alphanumeric
characters
are used repeatedly, and therefore reinforced almost daily. The true
resolution of this
io problem is not to use numbers or alphanumeric characters as codes to gain
access to
protected resources. Use something much more user friendly to the human brain.
Use
sequential pattern recognition. Like the sequential pattern of notes in song,
recall is
effortless and easy to recall over extended periods of time.
Summary of Invention-Objects and Advantages:
Note: From this point on, "PIN° will refer to PIN, PIN code, password
and passcode as
applicable.
The objects and advantages of my invention are as follows:
a) to provide a method of encoding and recalling an authorized user's PIN
where no
2o permanent or dedicated PIN is issued to said authorized user from a
grantor;
b) to provide a method where it is not necessary for an authorized user to
memorize or
recall a dedicated PIN for the purpose of identification or to gain access to
a protected
resource;
c) to provide an authorized user with a method of recalling multiple
transaction specific or
temporary PINS, from many different protected resources, by recognizing only a
single
sequential matrix pattern from a standardized geometric matrix for the purpose
of
identification or to gain access to a protected resource;
d) to provide an authorized user with a unique matrix position, separate from
said
sequential matrix pattern, to indicate the length of the PIN encoded within
said
3o sequential matrix pattern;
e) to allow an authorized user to readily~decode PINS and gain access to any
protected
resource which has not been accessed by the user for an extended period of
time;
f) to provide a grantor of a protected resource with a method of adjusting the
level of
system security to meet the needs of said system to adequately deter
unauthorized use;
g) to eliminate the need for personalized PINS and the security problems
associated with
PINs chosen from birth dates, phone numbers, etc.
h) to eliminate the need for an authorized user to carry recorded PINs
concealed in a purse
CA 02371755 2001-10-24
WO O1/G3545 PCTlUS0010G82G
7
or wallet increasing the level of personal PIN system security;
i) to increase the monetary intake level of a grantor with respect to an
increase in
transactions or resource usage;
j) to reduce a grantor's labor associated with personalized PIN account
distribution,
maintenance and re-informing authorized users of forgotten PINS;
k} to increase the ease-of use and user friendliness of any protected resource
transaction.
Further objects and advantages associated with my invention is the possibility
to provide
users with a single standardized geometric matrix for decoding PINs of
different lengths
io from a plurality of protected resources. This is a distinct advantage
because credit card
PIN codes, computer passwords or passcodes can all utilize a single
standardized geometric
matrix with adjustable system security. The authorized user only needs to
recall a single
sequential matrix pattern and the location of the matrix position designating
PIN length to
gain access to all protected resources. The level of system security can be
adjusted by
i~ varying PIN length in a standardized geometric matrix of sufficient
position size to
adequately provide the security desired. This can be accomplished through the
use of a
centralized computer data base in which the authorized user's personal and
secret
sequential matrix pattern resides. Grantors of card based systems, such as
bank cards,
credit cards, debit cards, smart cards and communication cards, and grantors
of non-card
2o based systems, such as Internet Service Providers, Internet Application
Providers, financial
transaction services and any protected resource on the Internet, could
subscribe to this
service where dedicated PINS are eliminated and system security is adjusted to
an
appropriate level to deter unauthorized use and fraud.
2g My system for recalling PIN codes differs from other methods as follows:
a) My invention utilizes sequential pattern recognition within a standardized
geometric
matrix to recall a transaction specific or temporary PIN code.
b) My invention eliminates dedicated PINS, and therefore, does not require the
grantor of a
protected resource to issue a PIN to an authorized user for the purpose of
gaining access
3o to said resource.
c) My invention does not require the authorized user to memorize or recall any
predetermined sequence of alternate PINs for the purpose of PIN variation to
increase
system security.
d) My invention can accommodate PINS of different lengths by incorporating a
unique
35 geome~c matrix position not associated with the authorized user's
sequential matrix
pattern to indicate PIN length. As PIN length is increased, system security is
also
increased. For example, a 5 by 5 geometric matrix could accommodate a 4 digit
CA 02371755 2001-10-24
WO 01/63545 PCT/USOO/OG82G
8
numerical PIN with a probability of guessing at i in gog,6oo attempts, or an 8
digit
alphanumeric PIN with a probability of guessing at 1 in 43,6o9,io~,ooo. The
security
level afforded by the matrix greatly exceeds the natural probability of
guessing correctly
which is uin io,ooo and i in ioo,ooo,ooo respectively.
e) My invention can be used with any existing system which has a key pad or
touch screen
for PIN entry and which has the capability to display a geometric matrix of
appropriate
size. My invention is not the only system which utilizes pattern recognition
to gain
access to protected resources. Others have used patterns consisting of human
faces,
elements in the periodic table and even ingredients to cook a meal. However,
displays
to on some devices can not accommodate such a complex array of items within a
convenient time frame. My system can be used on a cell phone or a computer
without
compromising security or time to access a resource.
The existing PIN systems suffer from the following disadvantages:
i5 a) Both card based and non-card based PIN systems require the user to
recall a specific
dedicated PIN of varying length for each different protected resource. This is
a
formidable task for airy authorized user, and highly impractical for
maintaining the
intended level of security.
b) The existing credit card PIN code systems uses a non-adjustable level of
security.
2o c) An unauthorized user can gain access to an account by observing the key
pad entry as an
authorized user enters an Account Number and PIN. This is especially true with
respect
to telephone credit cards.
d) The present PIN system suffers from excessive complexity causing authorized
users to
record PINS in computer memory or on paper reducing the intended level of
security.
25 e) PINS which form familiar words or birth dates are easily guessed by
unauthorized users.
f) If a personalized PIN is compromised in the present credit card PIN system,
and ali
personalized PINS are identical, all protected resources could be at risk if
an
unauthorized user gained access to a wallet or purse.
g) Humans have difficulty recalling PINS that are used infrequently.
Drawing Figures~
In the drawings, closely related figures have the same numbers but different
alphabetic
suffixes.
FIG. i shows a nine position geometric matrix in the shape of a square with an
encoded
transaction specific PIN.
FIG. 2 shows a twenty five position geometric matrix in the shape of a square
with an
encoded PIN, password or passcode. This geometric matrix contains four shaded
matrix
CA 02371755 2001-10-24
WO 01/63545 PCT/USOO/OG826
9
positions to serve as reference points to aid an authorized user in locating
their secret
sequential matrix pattern.
FIG. 3A demonstrates the first step in choosing a sequential matrix pattern:
choosing a
pattern within a standardized geometric matrix.
FIG. gB demonstrates the second step in choosing a sequential matrix pattern:
adding a
specific sequence to a matrix pattern forming a sequential matrix pattern.
FIG. gC demonstrates a fully encoded geometric with a sequential matrix
pattern in
parenthesis.
FIG. 3D shows a fully encoded geometric matrix without the parenthesis.
lo FIG. 4A shows a fully encoded geometric matrix with a second transaction
specific PIN.
FIG. 4B shows a fully encoded geometric matrix with a third transaction
specific PIN.
FIG. 4C shows a fully encoded geometric matrix with a forth transaction
specific PIN.
FIG. 5A demonstrates the first step in choosing a sequential matrix pattern
within a
twenty five position geometric matrix: choosing a pattern within a
standardized geometric
15 matrix.
FIG. 5B demonstrates the second step in choosing a sequential matrix pattern
within a
twenty-five position geometric matrix: adding a specific sequence to a matrix
pattern
forming a sequential matrix pattern.
FIG. 6 shows a diagram of the preferred embodiment of my imrention.
Reference Numerals in Drawing:
lo Geometric matrix
m Matrix square
i2 Shaded reference matrix square
~3 Matrix square indicating length of transaction specific PIN code
i4 Character underlined indication lower case character
Description of Figures l to 5:
go My invention is a system that verifies the identity of the authorized user
of a protected
resource which requires the use of a Personal Identification Number (PIN),
Password, or
Passcode to gain access to said resource. For brevity, I shall refer
collectively to FIN,
Password and Passcode as "PIN", and also, collectively to any computer based
networks)
and associated databases as "System(s)".
When a PIN protected resource transaction is initiated by a user, the Service
Provider
System (System) displays a standardized geometric matrix to said user with all
matrix
CA 02371755 2001-10-24
WO 01/63545 PCT/USOO/OG826
positions filled with random alpha and/or numeric characters (FIG. i). Within
the
displayed geometric matrix, a transaction specific PIN, or a PIN valid only
for the specific
transaction in progress, is encoded within said user's personally chosen
matrix sequential
pattern. A user must recall their personal and secret sequential matrix
pattern located
5 within the displayed geometric matrix in order to obtain or decode the
transaction specific
PIN and complete the authorized user verification phase of the transaction.
Once a user
obtains the transaction specific PIN from the displayed geometric matrix, that
user must
enter said PIN into the System within a specified time limit. If the PIN
entered by a user
matches the transaction specific PIN encoded by the System software, and also
held in
io System RAM memory, the user is granted access to the service. If the PINS
do not match,
or the time limit has expired, user access is denied.
All user's personal and secret sequential matrix patterns are resident in the
System's highly
is secure central data base and all transaction specific PINS are encoded into
the standardized
geometric matrix by System software. When a user initiates a second
transaction, the
transaction specific PIN is randomly changed by the System software, but the
user's
personal sequential matrix pattern remains constant and unchanged. Each time
the user
initiates a transaction, the transaction specific PIN is different and valid
only for that
2o specific transaction in progress. For additional security, a time limit is
imposed from the
time the geometric matrix is first displayed until the full transaction
specific PIN is entered
into the System by the user. In this way, unauthorized users are discouraged
from trial and
error techniques of PIN identification through repeated entry.
25 Therefore, by use of my invention, it will no longer be necessary to issue
a permanent PIN,
password or passcode to an authorized user of a PIN protected resource.
Instead, the
authorized user's personal sequential matrix pattern, as recalled from System
data base by
System software, will encode the transaction specific PIN within a
standardized geometric
matrix. An authorized user only needs to recall their personal sequential
matrix pattern,
30 obtain the transaction specific PIN within the specified time limit, and
enter said PIN into
the System. It should be emphasized that a user only needs to recall one
sequential pattern
to gain access to a plurality of PIN protected resources which subscn'be to
this service.
Also, the transaction specific PINS are always changing with each and every
subsequent
transaction greatly increasing the overall security of the System.
The System consists of a centralized computer database, within a network
(intranet or
Internet) environment, that contains the personally chosen sequential matrix
patterns of a
CA 02371755 2001-10-24
WO 01163545 PCT/US00l0682G
1l
plurality of authorized users. The sequential matrix patterns are chosen by
said authorized
users within a standardized geometric matrix of defined size and shape
determined by
application requirements and the level of security desired by System
management. For
example, a Credit Card PIN, which is presently standardized at four numbers,
may require
a minimum security geometric matrix consisting of only nine positions in the
shape of a
square (FIG. i). On the other hand, a twenty-five position, high security,
geometric matrix
in the shape of a square may be required to accommodate a PIN, password or
passcode
consisting of eight characters (FIG. 2). The number of positions in the
geometric matrix
need only be standardized to accommodate the character length of the PIN,
password or
io passcode, to achieve the desired intended level of security, and for user
reference in
recalling their personal sequential pattern.
Choosing a Sequential Pattern:
A sequential matrix pattern within a geometric matrix is defined as a pattern
that is not
i5 only matrix position specific, but also matrix sequence specific. For
example, a typical
authorized user would choose a four position sequential matrix pattern within
a
standardized, nine position, square geometric matrix as follows:
i) First, choose a specific pattern within the standardized geometric matrix.
2) Second, select a specific sequence within the chosen matrix pattern.
20 3) Memorize the chosen sequential matrix pattern within the standardized
geometric
matrix so said pattern can be recalled from an encoded geometric matrix where
all
matrix positions are filled with random characters or numbers.
Figures 3A, 3B and 3C demonstrate the process of choosing and encoding a
personal
25 sequential matrix pattern. Figure 3D demonstrates how that fully encoded
geometric
matrix, with said chosen sequential matrix pattern, looks to both an
authorized user and
also an unauthorized user.
First, a user must choose a specific pattern within the geometric matrix as
seen in FIG. 3A
go and indicated by the matrix squares marked by an "X". Next, a user must
select a specific
sequence within that chosen pattern as indicated by the ascending numerals and
arrows in
FIG. 3B. By following the ascending numerals within the chosen matrix pattern,
a user's
selected sequential matrix pattern can be observed. This is a user's personal
sequential
matrix pattern known only by that specific user and the System's central
database.
Encoding a Sequential Pattern:
An authorized user's sequential matrix pattern is then fully encoded by
filling in the vacant
CA 02371755 2001-10-24
WO 01/63545 PCT/US00106826
12
geometric matrix positions with random numbers. With knowledge of the
sequential
matrix pattern, an authorized can easily recall said sequential matrix pattern
and decode
the transaction specific PIN as indicated by the numerals within parenthesis
in FIG. gC.
Only the fully encoded sequential matrix pattern and standardized geometric
matrix are
presented or displayed to a user for decoding. An unauthorized user, without
knowledge
of an authorized user's sequential matrix pattern, only sees a random array of
numerals or
characters as seen in FIG. 3D, and therefore, can not decode the transaction
specific PIN.
On the other hand, an authorized user can easily decode airy transaction
specific PIN
within the allotted time limit by recalling their personal sequential matrix
pattern within
io the displayed standardized geometric matrix. Using the sequential matrix
pattern chosen
in Figures 3A to 3D, other subsequent transaction specific PINS encoded in
Figures, qA, 4B
and 4C, are "5632", "893" and "g8io" respectively. This demonstrates that by
recalling
only a single sequential matrix pattern, an authorized user can recall an
unlimited number
of transaction specific PINS.
With respect to a twenty-five position geometric matrix in the shape of a
square, a
sequential matrix pattern within this geometric matrix can accommodate both
the e~asting
four numeral credit card PINS and the more complex passwords and passcodes
which
2o usually consist of a minimum of six characters. A twenty-five position
geometric matrix is
much more secure than the nine position counterpart, but requires the user to
recall a more
complex sequential pattern. However, the additional level of security attained
by the
twenty-five position matrix is substantial and justifies the extra effort in
recalling a more
complex sequential matrix pattern.
As in the nine position geometric matrix, the user must first choose a pattern
within the
matrix. The shaded areas within the matrix are provided as reference points to
aid the user
in recalling their chosen personal sequential matrix pattern. For example, the
pattern
chosen in FIG. 5A is indicated with an "X" in the appropriate geometric matrix
positions.
3o Next, in FIG. 5B, the selected pattern is sequenced by the authorized user
as indicated by
the ascending numerals and arrows within the matrix pattern chosen in FIG. 5A.
Also,
included in FIG. 5B, is a non-sequential matrix pattern position indicated by
a "#". This is
a fixed, non-sequential matrix pattern, matrix position that informs the
authorized user of
the exact length of the PIN, password or passcode encoded within said user's
sequential
matrix pattern. FIG. 5C demonstrates an encoded eight position Passcode, while
FIG. 5D
demonstrates an encoded seven position Password. The inclusion of the fixed,
non-
sequential matrix pattern, matrix position indicating PIN length would depend
upon the
CA 02371755 2001-10-24
WO 01/63545 PCTlUS00/OG82G
13
application and intended versatility of the System. If no matrix position
indicating PIN
length is utilized, all PINS and sequential patterns would be a standard
length. The
capability to change both the code and the associated code length with each
and every
transaction specific PIN, password or passcode greatly increases security of
the system
while simultaneously deterring fraud.
The passcode and password encoded in FIGS. SC and 5D are "tle~M6Br" and
pLAMBERT"
respectively.
to Operation of Preferred Embodiment: FIG. 6
The following is to be considered one of many typical embodiments of my
invention and is
presented here only to serve as an example of how my invention would identify
and verify
the authorized user of a PIN protected resource. My invention can be applied
to many
different Systems that presently or potentially require PIN, password or
passcode
i5 protection.
The embodiment described below is one of the most common Systems available in
the
marketplace today: the Automated Teller Machine (ATM) / bank card. system for
off site
financial transactions.
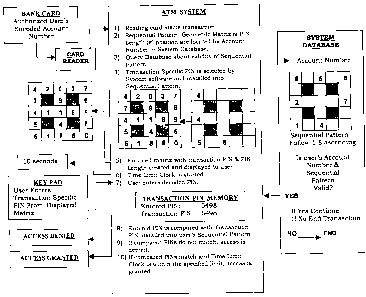
i) When a user wishes to use an ATM System to execute a financial transaction
or access
account information, the user must first insert a bank card into the ATM card
reader to
initiate the transaction (FIG. 6, Item i). The card contains the authorized
user's account
number and other necessary information encoded electronically or magnetically
to help
locate said authorized user in the System database.
2} The card reader extracts and transfers the encoded data from the user's
bank card into
the ATM System where System software relates the decoded account number with
the
authorized user's secret sequential matrix pattern and standardized geometric
matrix
located within ATM System database files (FIG. 6, Item 2).
3) Once the authorized user's account number is positively linked to a
specific database file,
the authorized user's secret sequential matrix pattern and standardized
geometric
matrix are available to ATM System software.
4) The ATM then queries the System database as to the validity of the user's
sequential
matrix pattern and card status. If the sequential pattern and/or card are
considered
invalid, the process is terminated and the card is rendered unusable by ATM
System
software. If the user's sequential pattern and card are considered valid, the
ATM System
software proceeds with the authorized user verification pmcess (FIG. 6, Item
3).
CA 02371755 2001-10-24
WO O1/G3545 PCT/US00/0682G
14
5) A transaction specific PIN is randomly chosen by the System software and
installed into
the authorized user's secret sequential matrix pattern within the standardized
geometric
matrix obtained from the System database (FIG. 6, Item 4).
6) The transaction specific PIN is also recorded in ATM System RAM memory
(FIG. 6,
Item 8).
~) All vacant geometric matrix positions are filled with numerals not used in
the
transaction specific PIN. The fully encoded geometric matrix, with all matrix
positions
filled, is then displayed to the user (FIG. 6, Item 5).
8) The time limit clock is reset to "io.o" seconds (FIG. 6, Item 6).
io 9) The user recalls their secret sequential matrix pattern, and from the
fully encoded
displayed geometric matrix, decodes the transaction specific PIN by following
said
pattern and obtaining the PIN numerals in the predetermined order.
~o) The user enters the decoded transaction specific PIN into the ATM System
via an ATM'
keypad (FIG. 6, Item ~).
15 11) The ATM System software compares the transaction specific PIN entered
by the user
with the transaction specific PIN resident in ATM System RAM memory. If the
PINS
match exactly, and if the time limit clock has not timed out at o.o seconds,
access to the
PIN protected resource is granted (FIG. 6, Item io). If the PINS do not match,
or the
time limit clock has time out, access is denied and the card is returned to
the user (FIG.
20 . 6, Item 9).
12) The user may subsequently reinitiate a second transaction, but the
transaction specific
PIN will be different. Upon several consecutive unsuccessful attempts to
decode a
transaction specific PIN, the user's card may be rendered unusable and/or
confiscated if
the entered transaction specific PIN is incorrect.
Ramifications and Scope of Invention:
My invention is a computer-based system that eliminates permanent or dedicated
credit
card PIN codes and computer passwords or passcodes issued to an authorized
user, by a
grantor, for the purpose of gaining access to a protected resource. Instead of
a user having
to recall a plurality of access codes, with my im~ention a user only needs to
recall a single
secret sequential matrix pattern. When a transaction is initiated by a user, a
standardized
geometric matrix filled with random characters is displayed to said user. In
order to
obtain the encoded transaction specific or temporary access code from the
displayed
matrix, the user must recall their secret sequential matrix pattern. The code
resides within
said secret sequential matrix pattern which is also contained within a
standardized
geometric matrix, like a small box within a larger box Once the code is
obtained or
decoded, a user enters that code into the System where said entered code is
compared to
CA 02371755 2001-10-24
WO O11G3545 PCT/USOO/OG826
1S
the transaction speafic code held in computer RAM memory. If the two codes are
identical, access is granted and the transaction is allowed to proceed. If the
codes do not
match, access is denied and the user must initiate a second transaction and
decode a
different transaction specific code from the displayed geometric matrix in
order to gain
access to the resource. Ail authorized user secret sequential matrix patterns
are stored in a
central database for System recall when a user initiates a transaction with a
credit card or
user log-on name. Since said transaction codes change with each different
transaction, and
are valid for a limited time period (approximately io seconds), system
security is greatly
increased and user verification highly validated.
io
Although the descriptions above contain many specificities, these should not
be construed
as limiting the scope of my invention, but as merely providing illustrations
of some of the
presently preferred embodiments.
i5 For example, another embodiment of my invention could verify the identity
of a returning
user that exited the cyber security firewall of a banl~s web site to view
items associated with
a non-bank billing entities web site. By sending a random set of characters
from a secret
sequential matrix pattern within a standardized geometric matrix in a
predetermined
order, along with algorithmic parameters describing matrix scrambling
instructions to the
2o billing entity as the authorized user exits the bank and transfers across
the cyber firewall, a
return code can be generated by the billing entity according to the bank
scrambling
insh~uctions. The billing entity loads the random set of characters into the
standardized
geometric matrix in proper order and begins scrambling the matrix data
according to
instnictions transferred in the algorithmic parameters from the bank. The
scrambling cycle
25 is repeated at the rate instructed in a transferred parameter. However, the
billing entity
can cycle the scrambling for a variable period of time of its own
determination. When the
billing entity finishes the scrambling cycles, the total time scrambled at the
specified rate is
recorded. The code is extracted from the entity's scrambled geometric matrix
via a
sequential pattern and transferred to the bank along with the total time of
cycling when the
3o user returns across the banl~s cyber firewall. Since the bank is aware of
the entity's
sequential pattern, the algorithmic parameters sent to the billing entity and
the time
statement returned by the entity, a corresponding code can be calculated by
the bank since
both institutions are using identical calculation prngrams. If the code
returned by the
entity is equivalent to that calculated by the bank, the user is verified and
allowed to cross
35 the bank's firewall and gain access to said user's account without entering
a PIN code. In
this way, my im~ention can verify that the user re-entering the firewall
security of the bank,
is the authorized user returning from the billing entity's web site.
CA 02371755 2001-10-24
WO O1/G3545 , PCT/US00/OG82G
16
Thus the scope of this invention should be determined by the appended claims
and their
Legal equivalents, rather than by the examples provided.
10
20
30