Note: Descriptions are shown in the official language in which they were submitted.
CA 02372810 2001-11-O1
WO 00/67483 PCT/US00/09800
1
METHOD AND APPARATUS FOR ACCESS CONTROL OF
PRE-ENCRYPTED ON-DEMAND TELEVISION SERVICES
This application claims the benefit of U.S.
provisional patent application no.60/132,366 filed
May 4, 1999.
BACKGROUND OF THE INVENTION
The present invention relates to the
communication of information services over a
communication network, and more particularly to
providing access control for signals containing
audiovisual content and services, such as on-demand
television programming. In order to render
subscription programming services and the like
commercially viable, systems must be provided for
preventing non-paying individuals from obtaining the
services. Such "access control" systems can take
various forms, but generally include some type of
modification (e.g., scrambling) or encryption of the
signals that carry the services. Only authorized
subscribers have access to the elements (e. g.,
cryptographic keys) necessary to satisfactorily
receive the signals.
Current techniques for decryption of signals
such as on-demand services may be based on real time
hardware based encryption solutions or based on pre-
encryption methods. Some configurations allow for
CA 02372810 2001-11-O1
WO 00/67483 PCT/US00/09800
2
cost effective real time encryption at the transport
level but are not as effective at a service level.
Such problems, together with the following
additional factors, require a new solution that
provides a reliable and cost-effective means for
access control of on-demand services:
1. Current real-time encryption does not meet
the cost model for on-demand services, in
that it is expensive to implement.
2. In some configurations real time encryption
requires too much real-estate at service
provider sites (currently, for example,
various video-on-demand (VOD) vendors are
consolidating their servers and signal
modulators (e. g., QAM modulators) in space
efficient packaging which bypasses a real-
time encryption stage).
3. Pre-encryption is inherently not as secure
as real-time encryption. At the same time,
on-demand content security requirements are
less stringent than those of broadcast
content. For example, there is no a priori
knowledge of when certain content will be
requested in the on-demand case. In the
broadcast case, the content is always being
sent and the schedules are known ahead of
time.
4. MPAA (Motion Picture Association of America)
has issues with clear (i.e., unencrypted)
CA 02372810 2001-11-O1
WO 00/67483 PCT/US00/09800
3
content, such as movies, and expects such
content to be protected.
5. Entitlement control should be upgradeable
without impacting content providers or
server vendors. Stronger solutions should be
able to be incorporated gradually as the
need dictates.
6. Secure content delivery of MPEG-2 (Motion
Picture Experts Group) using Internet
Protocol (IP) for point to point on demand
services or multicast services must be
facilitated.
7. Transport independent entitlement control
(e. g., MPEG-2 or IP) must be provided.
It would be advantageous to provide a method
and apparatus for access control of on-demand
services that addresses the above-noted issues. In
particular, it would be advantageous to provide a
content pre-encryption method that enables
entitlement control to be effectively implemented
independent of the transport protocol, e.g., MPEG-2
or IP.
It would be still further advantageous to
provide such a capability that can be offered as a
separate service to content providers, server
vendors, and cable system operators. The present
invention can be adapted for use with different
CA 02372810 2001-11-O1
WO 00/67483 PCT/US00/09800
4
types of provider networks, e.g. satellite and
Internet based networks.
The present invention provides a system having
these and other advantages. In particular, the
invention disclosed herein extends existing
encryption capability, such as that provided by the
Digicipher II (DCII) system available from General
Instrument Corporation of Horsham, Pennsylvania,
USA, the assignee of the present invention, to
handle pre-encrypted content that is requested on
demand by a viewer or is sent to a group of viewers.
The method of the invention is also upgradeable to
facilitate implementations of entitlement control
algorithms that vary in sophistication as the need
dictates. Additionally, the method is extensible to
enable encryption control that is independent of the
transport protocol used. Such protocols include, for
example, MPEG-2 and Internet Protocol (IP).
CA 02372810 2001-11-O1 ~/~~ U U/U ~ ,~Ob
/~~~~5 /9 ~°~ aoo i
SUMMARY OF THE INVENTION
In accordance with the present invention, a
method and apparatus are provided for access control
of pre-encrypted on-demand content. In a simplified
5 embodiment, the content is pre-encrypted by an
encryption device controlled by a pre-encryption
controller. The pre-encrypted content is forwarded
from the encryption device to a server. The server
may be a main server or a local distribution server.
The pre-encryption controller provides a first tag
to the user terminal and a second tag to the server.
The first tag is associated with hte second tag and
the second tag acts as a reference to the pre-
encrypted content and associated first tag, wherein
said first and second tags are unique to the pre-
encrypted content and are tracked by the pre-
encryption controller. The pre-encrypted content is
communicated from the server to a user terminal via
a first communication path.
An entitlement authorization associated with
'-'~ the encrypted content is communicated to a user
terminal (e.g., a client device" such as a set-top _
box) via a second communication path independent of
said first communication path. Authorization to
access the pre-encrypted content is determined based
on said entitlement authorization and said first tag
upon demand of said content by a user.
The user terminal may be a set-top box, a
CA 02372810 2001-11-O1
WO 00/67483 PCT/US00/09800
6
digital television or a host with point-of-
deployment (POD) capability, or a personal computer
(PC) or the like that provides the functionality of
a set-top box.
The pre-encryption controller acts to set up
the encryption device for pre-encrypting the
content. The set up of the encryption device is
outside the scope of this invention. For background
purposes, it will suffice to state that the pre-
encryption controller, through bi-directional
communication with the encryption device, configures
the encryption device with appropriate parametric
values and commands to enable the encryption device
appropriately to encrypt the content.
In an alternate embodiment, the server is a
main server (e. g., a head-end server) which
communicates the pre-encrypted content and first tag
to the user terminal via a local distribution
server. The pre-encryption controller is in
communication with a local distribution controller
(e. g., a head-end controller in a cable television
implementation), which local distribution controller
communicates the entitlement authorization to the
user terminal.
In a preferred embodiment, the first tag is an
opaque data block (ODB) and the second tag is a
unique reference handle (URH). The URH may be
generated as a function of the ODB.
In one embodiment, the ODB and URH are both
CA 02372810 2001-11-O1
WO 00/67483 PCT/US00/09800
7
forwarded to both the local distribution controller
and the server from the pre-encryption controller.
In an alternate embodiment, only the URH is
forwarded to the main server and the ODB is
communicated from the local distribution controller
to the local distribution server.
In one embodiment the ODB or the URH may be
stored as an attribute of the encrypted content.
Alternatively, both the URH and the ODB are stored
as an attribute of the encrypted content.
The ODB may be processed at the local
distribution controller to generate a second ODB,
which second ODB is forwarded from the local
distribution controller to the local distribution
server. This processing at the local distribution
controller may include algorithmically modifying the
ODB. Such reprocessing of the ODB at the local
distribution controller provides an added level of
security since the post-processing ODBs are no
longer the same across multiple local distribution
controllers.
The ODB itself may be coded in a manner that is
not readily discernable by third parties.
Alternatively, the ODB content may include an
encryption key to be used for decryption or used to
derive the key for decryption. The ODB may also
include a hierarchy of encryption keys whose
ultimate use is the derivation of the relevant key
for decryption but with added levels of security. In
CA 02372810 2001-11-O1
WO 00/67483 PCT/US00/09800
8
this manner the ODB content is securable as deemed
necessary without burdening the content providers or
service vendors. In the on-demand case, the ODB
itself may also be encrypted, using, for example,
the recipient's public key.
The pre-encrypted content may be broadcast,
multicast, or singlecast such that only a user
terminal with appropriate entitlement authorization
will be able to decrypt the broadcast, multicast, or
singlecast content. Alternatively, the pre-encrypted
content may be accessed via the Internet.
The entitlement authorization may comprise at
least one of (i) an entitlement authorization for a
service carrying the content, (ii) an entitlement
authorization for the content itself, and (iii) an
entitlement authorization for using ODB.
In a preferred embodiment, a client application
(typically software residing in a user terminal such
as a set-top box) then requests specific content
from the server, such as a video on demand (VOD)
movie or any other interactive content. The ODB is
forwarded from a server application to the client
application software that typically resides in a
central processor (CPU) of the user terminal. After
this set-up is completed, the server starts sending
the pre-encrypted content to the user terminal. The
ODB is then forwarded from the client application
via an application program interface in the CPU to a
kernel located in the user terminal. The ODB is then
CA 02372810 2001-11-O1
WO 00/67483 PCT/US00/09800
9
processed in the user terminal in conjunction with
the received entitlement authorization to determine
whether to decrypt the received pre-encrypted
content.
Processing may be provided by a secure
processor located in the user terminal or a software
task included in the user terminal CPU. The pre-
encrypted content is received by the user terminal
and decrypted when authorization is granted. Upon
authorization, the content will be processed for
display.
The pre-encrypted content may be received by
the secure processor via a conventional receiver
circuit. Alternatively, the pre-encrypted content
may be received by the secure processor via direct
memory access from device memory.
CA 02372810 2001-11-O1
WO 00/67483 PCT/US00/09800
BRIEF DESCRIPTION OF THE DRAWINGS
Figure 1 is a block diagram of the functional
components of the flexible pre-encryption
architecture of the invention;
5 Figure 2 is a block diagram of another
embodiment of the functional components of the
flexible pre-encryption architecture of the
invention; and
Figure 3 is a block diagram of the relevant
10 components of a user terminal in accordance with the
invention.
CA 02372810 2001-11-O1
WO 00/67483 PCT/US00/09800
11
DETAILED DESCRIPTION OF THE INVENTION
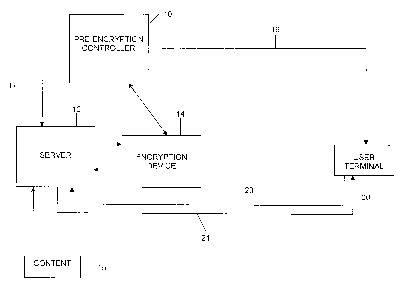
Figure 1 illustrates the main components of an
on-demand content communication system in accordance
with the present invention. In particular, a method
and apparatus are provided for access control of
pre-encrypted on-demand content. The video encoder
and post encoding processors are not shown, since
they are well known in the art. As will be
appreciated by those skilled in the art, any type of
post processing to be done on the content file/data
stream is performed prior to encryption.
Referring to Figure 1, a pre-encryption
controller 10 sets up an encryption device 14 for
encryption of the content 15. A server 12 forwards
the content file/stream to the encryption device 14
for encryption of the content prior to distribution
("pre-encryption"). The encryption device encrypts
the content file and forwards the pre-encrypted
content back to the main server 12.
The pre-encryption controller 10 acts to set up
the encryption device 14 for pre-encrypting the
content. The set up of the encryption device 14 is
outside the scope of this invention. For background
purposes, it will suffice to state that the pre-
encryption controller 10, through bi-directional
communication with the encryption device 14,
configures the encryption device 14 with appropriate
parametric values and commands to enable the
CA 02372810 2001-11-O1
WO 00/67483 PCTNS00/09800
12
encryption device 14 appropriately to encrypt the
content.
In one embodiment as shown in Figure 1, the
pre-encrypted content is forwarded from the
encryption device 14 to a server 12. The server may
be a main server or a local distribution server. The
pre-encryption controller provides a first tag and a
second tag to the server 12 via line 17. The first
tag is also provided to a user terminal 20 via line
19 or 21 depending upon the particular
implementation, the first tag being associated with
said second tag. The second tag acts as a reference
to the pre-encrypted content and associated first
tag, wherein the first and second tags are unique to
the pre-encrypted content and are tracked by the
pre-encryption controller 10. The pre-encrypted
content is communicated from the server 12 to a user
terminal 20 (e. g., a ~~client device" such as a set-
top box) via a first communication path 21.
An entitlement authorization associated with
the encrypted content is communicated to the user
terminal 20 via a second communication path 19
independent of the first communication path.
Authorization to access the pre-encrypted content is
determined at the user terminal 20 based on said
entitlement authorization and the first tag upon
demand of the content by a user. Communication from
the user terminal 20 back to the server 12 is
provided on line 23.
CA 02372810 2001-11-O1
WO 00/67483 PCT/US00/09800
13
The user terminal 20 may be a set-top box, a
digital television or a host with point-of-
deployment (POD) capability, or a personal computer
(PC) or the like that provides the functionality of
a set-top box.
In an alternate embodiment shown in Figure 2,
the server is a main server 12' (e.g., a head-end
server) which communicates the pre-encrypted content
and first tag to the user terminal 20 via lines 25
and 27 and a local distribution server 18. The main
server 12' can distribute the encrypted content to
various local distribution servers (at various
service provider locations, e.g., head-ends). The
pre-encryption controller 10 is in communication
with a local distribution controller 16, which
controls, e.g., a cable television system or the
like in a well known manner (e.g., a head-end
controller in a cable television implementation).
The local distribution controller 16 communicates
the entitlement authorization to the user terminal
20 via line 29.
In a preferred embodiment, the first tag is an
opaque data block (ODB) and the second tag is a
unique reference handle (URH). The URH may be
generated as a function of the ODB.
In one embodiment, the ODB and URH are both
forwarded to both the local distribution controller
16 (via line 11) and the main server 12' (via line
13) from the pre-encryption controller 10. In an
CA 02372810 2001-11-O1
WO 00/67483 PCT/US00/09800
14
alternate embodiment, only the URH is forwarded to
the main server 12' and the ODB is communicated from
the local distribution controller 16 to the local
distribution server 18 via line 22.
Either the ODB or the URH may be stored as an
attribute of the encrypted content. Alternatively,
both the URH and the ODB may be stored as an
attribute of the encrypted content.
The ODB may be processed at the local
distribution controller 16 to generate a modified,
second ODB, which second ODB is forwarded from the
local distribution controller 16 to the local
distribution server 18. This processing at the local
distribution controller 16 may include
algorithmically modifying the ODB. This may be done
as an offline process. Such reprocessing of the ODB
at the local distribution controller 16 provides an
added level of security since the post-processing
ODBs are no longer the same across multiple local
distribution controllers.
The system manufacturer specifies the ODB
content and, for security reasons, the ODB itself
may be coded in a manner that is not readily
discernable by third parties. Alternatively, the ODB
content may include an encryption key to be used for
decryption or used to derive the key for decryption.
The ODB may also include a hierarchy of encryption
keys whose ultimate use is the derivation of the
relevant key for decryption but with added levels of
CA 02372810 2001-11-O1
ll~ !Js l~l~~~DD/
security. In the on-demand case, the ODB itself may
also be encrypted (with an additional level of
implementation complexity) using, for example, the
recipient's public key. In the case of broadcast or
5 multicast content, the ODB may be made available in
advance since it is associated with the event or
content to be viewed or received. Encryption of the
ODB using the user's public key is extremely useful
_ for the IP transport case where the system
10 administrator has the option to make known what
events are available when, e.g. via an Electronic
Programming Guide (EPG). In this manner the ODB
content is securable as deemed necessary without
burdening the content providers or service vendors.
15 In addition, the entitlement control is upgradeable
without impacting the content providers or service
vendors.
The pre-encrypted content may be broadcast,
multicast, or singlecast such that only a user
'°"'. 20 terminal 20 with appropriate entitlement
:-~ authorization will be able to decrypt the broadcast,
multicast, or singlecast content. Alternatively, the
pre-encrypted content may be accessed via the
Internet.
The entitlement authorization may comprise at
least one of (i) an entitlement authorization for a
service carrying the content, (ii) an entitlement
authorization for the content itself, and (iii) an
entitlement authorization for using the ODB.
R~-iC~~
CA 02372810 2001-11-O1
/~E~-~llS / ' ~P/~ J?D~ /
16
Figure 3 depicts the processing that takes
place at the user terminal 20. The client
application 40 (typically residing in a user
terminal 20 such as a set-top box) requests specific
content from the server (either the server 12 of
Figure 1 or local distribution server 18 of Figure
2), such as a video on demand (VOD) movie or any
other interactive content. The server then sends the
ODB to the client application device 40. After this
set-up is completed, the server 18 starts sending
fq° the pre-encrypted content to the user terminal 20.
The client application 40 (e. g. software)
running in the user terminal processor (CPU) 36
receives the ODB from a server application in the
server 12 or local distribution server 18, as
described in connection with Figures 1 and 2, and
forwards it via an application program interface
(API) 42 to the user terminal processor kernel 44.
In the broadcast and multicast modes, the ODB may be
made available ahead of time, before the actual
W
broadcast or multicast event commences. In this
case the ODB may be requested by and sent to the
user by the local distribution controller (16). The
ODB is then processed in the user terminal 20 in
conjunction with the received entitlement
authorization (as described in connection with
Figures 1 and 2) to determine whether to decrypt the
received pre-encrypted content.
CA 02372810 2001-11-O1
WO 00/67483 PCT/US00/09800
17
Processing may be provided by a secure
processor 32 located in the user terminal 20 or a
software task included in the CPU 36. The pre-
encrypted content is received by the user terminal
20 and decrypted when authorization is granted. Upon
authorization, the content will be processed for
display.
The pre-encrypted content may be received by
the secure processor 32 via a conventional receiver
circuit (i.e. receiver output of Figure 3).
Alternatively, the pre-encrypted content may be
received by the secure processor 32 via direct
memory access from device memory 30. The decrypted
output from the secure processor 32 is written back
to memory 30 for further use by the CPU 36, or is
forwarded to a demultiplexer/decoder 34 for further
processing in a conventional manner.
It should now be appreciated that the present
invention provides an improved method and apparatus
for the delivery and access of pre-encrypted on-
demand television services. In particular, the
present invention provides a content pre-encryption
method and apparatus that enables entitlement
control to be effectively implemented independent of
the transport protocol, e.g., MPEG-2 or Internet
Protocol (IP), and to some extent independent of
transmission mode (i.e., singlecast (e.g., on-
demand), multicast, or broadcast). Additionally, the
present invention provides encryption and access
CA 02372810 2001-11-O1
WO 00/67483 PCT/US00/09800
18
control capability that can be offered as a separate
service to content providers, server vendors, cable
system operators, and/or Internet service providers,
or the like. The present invention enables
entitlement authorization that can vary in
sophistication as deemed necessary without burdening
the content providers or service vendors. In
addition, the entitlement control is upgradeable
without impacting the content providers or service
vendors.
Although the invention has been described in
connection with certain preferred embodiments, it
should be appreciated that numerous adaptations and
modifications may be made thereto without departing
from the scope of the invention as set forth in the
claims.