Note: Descriptions are shown in the official language in which they were submitted.
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
METHOD FOR PROVIDING CARDLESS PAYMENT
Field of the Invention
The system and method of the invention relate generally to performing
transactions related to an account, so as to eliminate the need for the
physical
presence of a transaction card during the transaction.
Background of the Invention
There are literally thousands of different credit cards, funds cards or other
personal cards available which provide an account-holder with a variety of
capabilities. Some provide frequent flier miles, others give a user free gas.
Still other
credit cards offer low interest rates and even insurance for purchases. Out of
all the
transaction cards that exist, none of them offer the ability to go to a store
and make
purchases, without the actual card, by utilizing convenient identifying
information
that is selected by the account-holder.
Further, conventional known techniques do not provide for conducting
business over the Internet without using the transaction card number, for
example, or
some other mandated number. That is, the conventional techniques do not
provide for
an account-holder to select convenient identifying information by which to
access and
use that account-holder's account.
2 0 To explain, it is highly desirable to use easy to remember numbers or
other
information to effect transactions. Illustratively, while it is possible to
place an order
over the phone to a catalog company, it is burdensome to have a physical card
in your
hand to read the card number to the sales person and provide some additional
information such as the expiration date. Perhaps a trivial number of people
have
1
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
memorized their transaction card number and expiration date, but most people
have
yet to commit these seldom used 20-digits, for example, to memory, i.e., the
20-digit
number including a 16 digit card number and a four digit expiration date.
Additionally, those with an active lifestyle often find it burdensome to carry
many cards with them during their everyday lives. The risk of losing one's
wallet or
purse, or having it stolen is an ongoing problem. The replacement process for
most
credit cards, a particular type of transaction card, for example, is long and
burdensome. If a credit card is stolen and unauthorized charges are discovered
on the
account, the process to rectify the situation is both time consuming and
exhausting,
often involving sworn affidavits by the cardholder.
These drawbacks, as well as others, exist with current transaction cards and
the techniques utilized in conjunction with such current transaction cards.
SUMMARY OF THE INVENTION
The disclosed method and system in accordance with embodiments of the
invention provide a technique for allowing an account-holder to select an
alias by
which an account-holder may access and use a transaction account using
convenient
and/or easy to remember information. Further, the method and system in
accordance
with embodiments of the invention provide a technique for allowing an account-
holder to select an alias, as well as a personal identification entry, by
which an
2 0 account-holder may access and use a transaction account using convenient
and/or
easy to remember information.
The present invention further provides a system and method for enabling an
account-holder to use his or her transaction card or a transaction account
without
2
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
actually having a card present at the time of purchase. This is accomplished
by cross-
linking the account-holder's phone number, or other alias that is selected by
the
account-holder, to the transaction card number, such as a credit card number,
and
providing the customer with a corresponding "personal identification entry"
(PIE) that
can be changed immediately upon receipt so that it is a number that the
account-
holder can easily remember. It should be appreciated that a PIE may take the
form of
a conventional Personal Identification Number (PIN). The PIE can also be
selected
by the account-holder from his or her home phone. As one method of
authentication,
the bank can verify the identity of the caller by their phone number, if their
phone
number is chosen as the PIE, using an Automatic Number Identification ("ANI")
system, which ensures a secure registration of the PIE. The customer can then
self
select the PIE he or she wishes to use.
These and other aspects and advantages of the invention will be apparent from
the detailed description of the exemplary embodiments which follow.
BRIEF DESCRIPTION QF THE DRAWINGS
Fig. 1 is a flow chart showing a method of use according to one embodiment
of the invention;
Fig. 2 is a flow chart showing a transaction according to one embodiment of
the invention;
2 0 Fig. 3 is a flow chart showing acceptance of an offer and set up of an
account
according to one embodiment of the invention;
Fig. 4 is a flow chart showing acceptance of an offer and set up of an account
according to one embodiment of the present invention;
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
Fig. 5 is a block diagram showing a transaction system according to one
embodiment of the present invention;
Fig. 6 is a block diagram showing the merchant portion of Fig. 5 in further
detail according to one embodiment of the present invention;
Fig. 7 is a block diagram showing the customer portion of Fig. 5 in further
detail according to one embodiment of the present invention;
Fig. 8 is a flow chart showing a method of use according to a further
embodiment of the invention;
Fig. 9 is a flow chart showing the account-holder performs account-holder
operations step of Fig. 8 in further detail according to one embodiment of the
invention;
Fig. 10 is a flow chart showing the card controller operating portion
processes
PIE and responds to merchant over the Internet step of Fig. 8 in further
detail
according to one embodiment of the invention; and
Fig. 11 is a flow chart showing the card controller operating portion
processes
PIE and responds to merchant over the Internet step of Fig. 8 in further
detail
according to a further embodiment of the invention.
DETAILED DESCRIPTION OF THE PREFERRED EMBODIMENTS
Hereinafter, various embodiments of the method and system of the invention
2 0 will be described. As used herein, a "transaction card" means a credit
card, debit
card, stored value card, smart card, or any other type of card, electronic
account, or
payment vehicle that is used by a person or an entity and that allows that
person or
entity to perform any of a wide variety of transactions, which relate to an
account,
4
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
i.e., a "transaction account," including electronically accessing funds,
mutual funds,
money market accounts, margin accounts, bank accounts, sweeps card accounts, a
line of credit, stock information, electronically accessing information such
as address
information, or performing other transactions, for example.
Further, the transaction card may be used by any of a variety of users
characterized herein as "account-holders." Accordingly, an "account-holder"
may be
any of a variety of persons or users having an account or accounts including,
for
example, a cardholder, i.e., a person who possesses a card of some type, but
who does
not need to physically carry the card with them as a result of the systems and
methods
of the invention.
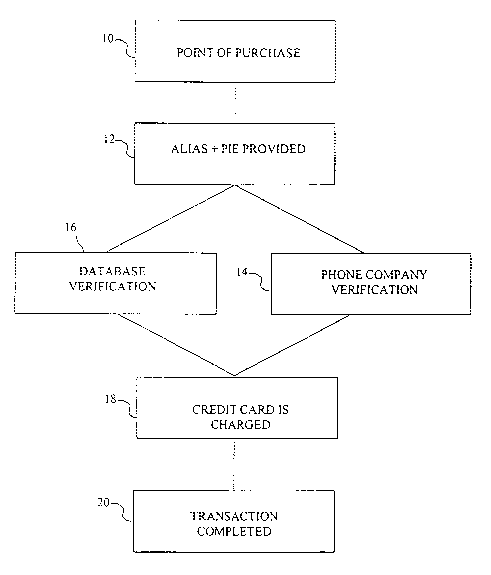
Fig. 1 shows one example of an account-holder transaction according to the
method of the present invention. In Fig. 1, a credit card purchase is
commenced at
any given "point of purchase" location in step 10. A "point of purchase
location" is
any location where it is possible to make a purchase using a credit card. For
example,
any store that accepts credit cards would be a point of purchase location. Any
telephone can be considered a point of purchase location since it is possible
to
telephone a company, such as a catalog company, and place a credit card order
over
the phone. Instead of providing the merchant with the credit card for payment,
or in
the case of a telephone order providing the card number and expiration date,
the
2 0 account-holder will enter a selected alias, such as the account-holder's
ten-digit home
telephone number, or alternatively a cellular number or personal
communications
service (PCS) number, for example, and the selected PIE, such as a home
telephone
number, into a device similar to the credit card readers in use today in step
12.
S
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
This device will connect to a database, perhaps the database already
maintained by the telephone company in step 14, and it will check for
authenticity.
Alternatively, the transaction card company may have their own database which
includes all the appropriate information and can verify the account-holder and
process
the transaction with the appropriate card in step 16.
The validation process should be fairly quick and will then retrieve the
credit card
linked to the alias and PIE the account-holder has provided. After validation
has
succeeded, the credit card will be charged and the merchant will receive
notice of this
validation in step 18. The account-holder must then sign some sort of receipt
or
authorization slip and the transaction is complete in step 20.
This entire process is very similar to current day credit card transactions
with
the exception that instead of providing a plastic card, the account-holder
need only
enter their selected alias number and selected PIE. In accordance with this
embodiment of the method of the invention, a suitable "keypad" is used by
customers
so they can enter their alias and/or their PIE. Optimally, the arrangement of
the
keypad allows the customer to enter the required information discreetly.
Alternatively, the customer can provide the alias and PIE directly to the
merchant
either verbally or in writing, for example.
Fig. 2 shows a similar transaction between an account-holder and a merchant
2 0 conducted over a telephone, or alternatively cellular phone or personal
communications service (PCS), for example. In Fig. 2, an account-holder
initiates a
transaction by calling a merchant over the telephone in step 22. After
identifying the
item to be purchased, the account-holder authorizes his card to be charged by
6
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
providing the representative with his alias, which in this case is his ten-
digit telephone
number. Alternatively, the merchant may use an ANI to determine the telephone
number of the caller in step 24, i.e., if the caller has designated their home
phone
number as the alias. This is useful in situations where the account-holder is
calling
from their home and provides an added measure of security to make sure the
authorized account-holder is the one placing the order.
The transaction is continued and the card number received by the merchant is
verified using the account-holder's PIE. In step 26, the account-holder
provides the
PIE to the merchant. This can be done by having the account-holder punch in
the PIE
on the telephone key pad or verbally indicating the PIE to the merchant, for
example.
The ten-digit number, i.e., the alias, and PIE are verified by the merchant in
step 30.
The verification process is similar to that used to verify original credit
card numbers
and expiration dates. Once the number has been verified, the merchant
processes the
transaction and the credit card is charged in step 32. After the credit card
has been
charged, the transaction is completed in step 34.
It should be appreciated that selecting an alias and selecting a PIE are
relatively easy processes in accordance with embodiments of the method of the
invention. Fig. 3 shows the activation and assignment process for a current
account-
holder. A current account-holder, in this case a card member, is a person that
already
2 0 has a credit card account with the credit card company and is merely
calling to select
their alias, as well as selecting a PIE. The process is initiated in step 36
when a
current account-holder receives the offer from the credit card company to
select an
alias. This offer can be received by mail, e-mail, telephone, or any number of
ways.
7
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
If the offer was received by any manner other than a telephone call, the
account-
holder calls the credit card company for activation in step 38 in accordance
with one
embodiment of the method of the invention. When the call is received by the
credit
card company, the caller's telephone number is automatically identified by an
ANI
system in step 40.
By determining the telephone number of the caller, the credit card company
can determine the caller's identity and account number. This can be done by
asking
the caller for his account number or, preferably, by having a system, such as
a voice
recognition unit (VRIJ~, obtain the account number from the caller and
automatically
retrieve the account-holder's account information based on the telephone
number as
shown in step 42. In step 43, the card member selects an alias. Then, the
process
passes to step 44.
In step 44, the account-holder selects a PIE to be used with his telephone
number alias. Alternatively, the credit card company can assign a PIE, as well
as
multiple PIES or multiple aliases, randomly. The activation process is
completed in
step 46 when a credit card company assigns an alias and a PIE to the account-
holder's
account and updates the appropriate database record or records. This updating
may of
course be done automatically.
In accordance with further embodiments of the method of the invention, the
2 0 activation process performed over the telephone can be totally automated
as well. For
example, a current account-holder would receive the offer in the mail
including a
telephone number for the account-holder to call for activation. The account-
holder
would then call the designated number. The credit card company could then
8
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
automatically determine the account-holder's telephone number using an ANI and
present the account-holder with a pre-recorded menu of options, such as by
utilizing a
voice recognition unit or system. By using these options the account-holder
would be
able to request selection of the alias and select a PIE using the telephone
key pad.
Registration is then completed by having the system automatically update the
account-holder's account and records with the selected alias and the selected
PIE.
The activation and registration process can also be utilized by a new account-
holder. As shown in Fig. 4, a new member would receive a credit card offer
with an
option to select an alias for the new account in step 48. The person can
accept this
offer and apply for the credit card and alias by calling a designated number
for
activation in step 50. In step 52, the credit card company can use an ANI to
determine the caller's telephone number for verification. Alternatively, a
customer
service representative can verbally obtain the information from the account-
holder.
In step 54, the system would receive a file containing the caller's financial
information and pre-approval status. This information can be used by a
customer
service representative, or by the system automatically, to activate a new
account for
the caller. Preferably, a customer service representative would obtain
additional
financial information and confirm existing information thus providing the
credit card
company with a more thorough screening process.
2 0 Approval for the new account can then be processed in step 56 and any
updating can also be performed as well. At this time, the account-holder can
select an
alias and a PIE as shown in step 58. The registration and activation process
is
completed in step 60 when the system assigns the alias and the PIE to the
account-
9
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
holder's account and updates the account accordingly. At this point, the
system can
activate the account or hold it pending approval of subsequent credit checks
as may
be desired.
Consumers who have a plurality of transaction cards have the option of
selecting multiple PIES, each of which would correspond to a different
transaction
card, but be used with the same alias, in accordance with some embodiments of
the
invention . When making a purchase, the account-holder need only provide the
selected alias and the PIE corresponding to the card he or she wishes to
charge the
purchase on.
Security measures for the cardless payment system, in accordance with
embodiments of the method of the invention, will be nearly the same as those
used by
credit cards. Credit cards themselves are not a secure system by definition.
If a card
is lost or stolen, misuse of the credit card is quite possible. The same
systems used to
handle fraud for credit cards may be used to handle the present invention. No
new
security issues exist with the cardless payment system, in accordance with
embodiments of the method of the invention, beyond the current ones faced by
credit
cards today. In fact, perhaps even less security issues exist with the
cardless payment
system of the invention due to the fact that no transaction card is being
carried around
by the account-holder and thus the chances of having the transaction card lost
or
2 0 stolen is significantly reduced. If the account-holder decides to destroy
the plastic
card and rely solely on the cardless payment system of the invention,
providing the
capability to select an alias and a PIE, then the chances of the card being
lost or stolen
are practically zero.
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
The registration process for the cardless payment system, in accordance with
embodiments of the method of the invention, is also unique. By allowing an
account-
holder to choose the account-holder's alias and PIE, the systems and methods
of the
invention provide convenience and ease-of mind to the account-holder. That is,
the
account-holder may choose both an alias and a personal identification entry
(PIE) that
is easiest for him or her to remember, or alternatively, that is more closely
tailored to
the particular's account-holder's needs. For example, an account-holder may
desire
additional security than is normal. As a result, the account-holder might not
use her
home phone number as the alias, but rather some more obscure number.
Additionally, in accordance with further embodiments of the invention, once
consumers have entered their alias, they can select multiple payment methods.
For
example, if an account-holder has two different credit cards and a debit card,
with the
same or multiple issuers, after entering their ten-digit alias number and PIE
they can
choose which card to use for payment through some sort of self selection menu.
Alternatively, a single account-holder may have multiple PIES representing
different
credit cards. In accordance with embodiments of the method of the invention,
it is
possible to assign one PIE to their Visa card and another PIE to their
MasterCard,
both on the same alias, i.e., the same phone number, for example.
It should be appreciated that uses of the method of the invention include, but
2 0 are not limited to, any "point of sale" where there is a suitable terminal
at which point
consumers can enter in a number. The invention is also applicable to card not
present
situations including ordering a product by telephone or over the Internet, for
example.
The systems and methods of the invention allow the consumer to buy something
11
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
without giving their credit card information over the phone. That is, if the
consumer's
home phone number is selected as the alias, all that the consumer needs to do
is enter
the PIE, since the phone number is automatically detected over the phone by
the
merchant. This is added security since many people still do not like
disclosing credit
card numbers over the phone.
As described above, communication over the telephone may be utilized to
select an account-holder's alias, as well as to select a PIE. However, it
should be
appreciated that the system and method of the invention is not limited to the
telephone. An offer to select an alias may be e-mailed from the credit card
company
to the account-holder or performed using a suitable web page or other world
wide
web technology, for example. If using e-mail, once the e-mail is received, the
account-holder may then select the alias over the Internet via e-mail, as well
as select
a PIE. It should also be appreciated that other suitable forms of
communication over
the Internet, or other network, may also be utilized in implementation of the
method
of the invention other than e-mail.
As a further alternative to selection of the alias and selection of a PIE over
the
telephone, the account-holder might physically go to an office of the
transaction card
company, for example. At the transaction card company office, the alias could
be
selected and the PIE selected through human interaction. In accordance with
further
2 0 embodiments of the method of the invention, an account-holder might
utilize an
automated machine for selection of the alias and selection of a PIE, or
alternatively to
change the alias or PIE. Such automated machines may be strategically
geographically positioned in a manner similar to automated teller machines
(ATM).
12
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
Further, the processing and communications capabilities required to perform
alias
selection and PIE selection, as well as use, may be combined with the
technology
utilized in conventional ATMs, i.e., combined within the same physical
machine.
Further, it should be appreciated that selection of an alias and a personal
identification entry may not involve simply the selection of alphanumerics.
That is,
an account-holder may choose to select an alternative type of alias or
personal
identification entry. For example, such alternative types may include
fingerprint
recognition, gene identification, DNA identification, use of biometrics, i.e.,
using
biological parameters of a person, retina identification, or voice
recognition, for
example.
As described above, an account-holder selects a PIE that is used in
conjunction with the alias for a particular transaction card, for example.
However, in
accordance with further embodiments of the system and method of the invention,
one
alias may be used with multiple PIES for one transaction card. To explain, an
account-holder might rotate through three different PIES. That is, the account-
holder
would make a first purchase in the morning using her first PIE. Thereafter,
the
account-holder might make two additional purchases in the afternoon using her
second and third PIE, respectively. Then, in the evening when making a fourth
purchase of the day, the account-holder would again use her first PIE. Using
this
2 0 method, the account-holder must keep track of which PIE the account-holder
is
currently on, i.e., what PIE in the rotation the account-holder should use
next. It
should of course be appreciated that any number of PIES might be utilized in
the
rotation.
13
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
As the number of PIES increases, the complexity of keeping track of which
PIE to use will of course increase. Accordingly, it should be appreciated that
the
complexity of the transaction may be justified based on the desired level of
security.
In contrast, the complexity of keeping track of which PIE to use may not be
justified
by the required level of security, thus resulting in the potential for
unnecessary
confusion to the account-holder.
As described above, when using multiple PIES, the account-holder must keep
track of which PIE the account-holder is currently on. This may be problematic
since, for example, long periods of time may pass between uses of a particular
card.
To provide assistance to the account-holder in remembering their current place
in the
PIE rotation, a prompt may be provided to the account-holder during a
transaction.
For example, the prompt may be displayed subsequent to the account-holder
entering
their alias. The prompt might be in the form of "Currently on PIE rotation 2."
The
account-holder would then remember the PIE that corresponds with that
particular
rotation number. Alternatively, the prompt might say "currently on PIE 2," so
as to
provide the useful feedback to the account-holder.
Other feedback might also be provided in accordance with embodiments of
the method of the invention. As described above, a single account-holder may
have
multiple PIES representing different credit cards, from the same or different
issuers.
2 0 That is, it is possible to assign one PIE to their VTSA card and another
PIE to their
MasterCard, both on the same alias. Subsequent to performing a transaction
using the
account-holder's alias and a particular PIE, feedback may be provided to the
account-
holder indicating which account was debited, for example. For example, the
14
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
feedback may be in the form of "VISA debited using PIE '8049," wherein 8049 is
the
last four digits of the account-holder's PIE number. It should of course be
appreciated
that other useful feedback information may be provided as is necessary or
desired.
This information may be printed on an account-holder's receipt, for example,
or
otherwise conveyed to the account-holder. The information might be in the form
of a
short text message. Accordingly, the account-holder would be advised of the
authentication and verification of the transaction, and the source from which
the
funds were debited, for example.
The use of the above PIE rotation process provides an additional level of
security to the account-holder. For example, another customer behind the
account-
holder might note the PIE number entered by the account-holder into a keypad
at a
grocery store. Further, the additional customer might have heard, or be able
to
otherwise obtain the alias used by the account-holder, in particular if the
alias is the
account-holder's telephone number. However, when the additional customer
attempts
to use this information to perform a fraudulent transaction, the additional
customer's
chances of success will be substantially limited, depending on where the
account-
holder is in the PIE rotation.
In various embodiments described above, the system and method of the
invention are utilized in the context of using a credit card. However, it
should be
2 0 appreciated that the invention is not limited to use with a credit card.
Any of a variety
of other transaction cards might also benefit from use of the alias and PIE
described
herein. Accordingly, stored value cards or debit cards, for example, might be
used in
conjunction with the methods of the invention.
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
In accordance with some embodiments of the method of the invention, it
should be appreciated that multiple PIES might be used to control from which
card
requested funds are obtained. To explain, an account-holder might possess a
credit
card, a debit card and a stored value card. Further, that account-holder may
always
prefer to use his credit card, but of course only if there is available credit
thereon.
Accordingly, the particular PIE utilized by the account-holder may control the
hierarchical ranking of which card is accessed first, second, third, and so
forth. In
other words, one of a plurality of possible PIES, which is entered by the
account-
holder, may determine the hierarchical ranking of which of the plurality of
possible
funds accounts is accessed for withdrawal of funds.
For example, a PIE "BG123" might access the credit card, debit card, and
stored value card in order, obtaining the requested funds from the first card
that is
able to grant the request. A different PIE may be utilized to change the
hierarchical
order. That is, the PIE "BG231" might be used for the hierarchical order of
looking
first to the debit card, then to the credit card, and lastly, to the stored
value card in
order to obtain requested funds.
As described above, the alias and PIE may utilize numbers, such as for
example a telephone number. However, the method of the invention is not
limited to
use of numbers. That is, any of numbers, alphanumerics, names, phrases, or
2 0 combinations of numbers, alphanumerics, names or phrases, for example,
might be
utilized for either the alias or the PIE. Also, alternative techniques of
identification
might be utilized for either the alias or the PIE, such as human
characteristics. These
further forms of identification might include fingerprint recognition, gene
16
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
identification, DNA identification, use of biometrics, i.e., using biological
parameters
of a person, retina identification, or voice recognition, for example.
As described above, the person's phone number, for example, might be used as
a PIE. Illustratively, if a transaction is done over the telephone, the
caller's phone
number might be determined using an ANI system. This allows the caller's PIE
to be
immediately obtained and stored. Once the caller provides his alias, and the
association is made with the corresponding account of the caller using the
alias, the
PIE may then be retrieved from memory for authentication or authorization of
the
desired transaction.
In accordance with further embodiments of the method of the invention, a
person's signature might also be utilized as either the alias or the PIE. To
further
explain in the context of utilizing a signature as a PIE, a customer would
initially be
prompted to enter their alias, for example, their telephone number.
Thereafter, the
customer would be prompted to sign their name utilizing a digital signature
pad. That
is, the digital signature pad captures the signature digitally and stores the
signature
information in what might be characterized as a "new signature data file." The
information in the new signature data file is then compared with an authorized
signature, which is maintained at a central processing center of the bank or
other
entity, for example. That is, the new signature data file is compared with an
~ 0 authorized signature data file to determine the level of similarities. The
comparison
may be performed by comparing the data points of the new signature, i.e., an
executed signature, with the data points of the authorized signature. That is,
the new
signature might be mapped on to the authorized signature. If the similarity of
the new
17
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
signature and the authorized signature achieves a predetermined threshold,
then the
new signature is approved. It should be appreciated that the predetermined
threshold
may be determined based on a variety of parameters including weighing concern
over
potential fraudulent transactions against chronic problems of an authorized
customer's
signature not being accepted.
As described above, an account-holder uses an alias and a PIE, or
alternatively, multiple PIEs. In accordance with one embodiment of the method
of
the invention, the account-holder routinely changes, i.e., updates, his or her
PIE. This
updating of the PIE might be performed using the telephone, over the Internet,
through a sales representative at an office, by mail, or using an automated
machine
located at a convenient location, for example.
In accordance with this embodiment, a user selects an initial alias and PIE
during activation. Also at activation, the account-holder selects the option
of
routinely changing her PIE number. As a result, after five transactions, for
example,
using the alias and first PIE, such first PIE then becomes invalid. As a
result, the
account-holder must contact the credit card company or other entity in order
to obtain
a new, i.e., a refreshed, PIE. Once this new PIE is obtained by the account-
holder,
then the account-holder uses this second PIE for the next five transactions.
Thereafter, the second PIE becomes invalid. Such periodic changing of the PIE
based
2 0 on the number of transactions provides an added level of security, which
may be
preferred to some account-holders, balanced against the inconvenience of
renewing
the PIE. It should be appreciated that rather than every five transactions,
any suitable
number of transactions might be utilized prior to a particular PIE becoming
invalid.
18
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
Upon activation, for example, the account-holder might choose how many
transactions may be performed prior to a particular PIE becoming invalid.
It should be appreciated that rather than the number of transactions
determining when a particular PIE becomes invalid, other operating parameters
may
alternatively be utilized. For example, at the end of every month, or at some
other
predetermined time in each month or year, an account-holder might be required
to
renew her PIE.
It should be appreciated that in accordance with some embodiments of the
method of the invention, a personal digital assistant (PDA) might be utilized.
Illustratively, a customer wishing to check out of a store with her purchases
may
initially enter the alias into her PDA. In turn, the PDA communicates the
alias
information to the processing system of the cashier. This communication may be
performed utilizing suitable communication technology, such as infrared
technology.
Upon receiving the alias, the cashier's processing system then prompts the
customer
for the customer's PIE. This prompting may be performed in any suitable
manner.
The customer may then enter the PIE into her PDA, which is then communicated
to
the cashier's processing system. It should be appreciated that such an
arrangement
may serve to limit the hardware requirements, for example, of the cashier by
not
requiring a keypad.
2 0 Once the alias and PIE are transferred to the cashuer's processing system,
authorization of the transaction is performed. Once the authorization is
complete, the
cashier's processing system may again communicate with the customer's PDA to
transmit a digital receipt to the PDA. Accordingly, a paperless transaction is
effected.
19
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
It should be appreciated that in the context of this example, a PDA is
utilized.
However, this embodiment of the method of the invention might utilize any
handheld
computer or other processing system, which is capable of the processing as
described
above. That is, handheld computers or other processing systems, which are not
characterized as "personal digital assistants" might also be utilized in
conjunction
with this embodiment of the invention.
As described above, a telephone number might be conveniently used as a PIE
or as the alias. However, one possible shortcoming of utilizing a telephone
number is
that the telephone number is easily obtained by other persons. As a result, it
may be
preferable to use alternatives to a person's telephone number including
numbers,
alphabetical letters, alphanumerics, phrases, or combinations of such items as
may be
desired. In accordance with further embodiments of the system and method of
the
invention, various other operating parameters might be utilized as the alias
and/or the
PIE. For example, when performing an on-line transaction, the user
identification
parameters of an account-holder's computer, which may be obtained by the
credit
card company upon login may be used. Accordingly, an account-holder's user log-
on
information, for example, may be utilized in a manner similar to use of an
automatic
number identification (ANI) system, as described above. Further, such user
identification based on the user identification parameters of an account-
holder's
2 0 computer may be utilized as a level of security in addition, rather than
in substitution,
of an alias and/or a PIE.
In accordance with further embodiments of the method of the invention, the
alias and/or the PIE may include both static portions as well as dynamic
portions, i.e.,
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
changing portions. Illustratively, the first ten digits of an account-holder's
alias may
be the account-holder's telephone number. However, the last two digits change.
The
change of the last two digits adds a further level of security. It should be
appreciated,
this further level of security may also add complexity to the transaction,
which may
not be desired or necessary.
In further explanation of the dynamic portion, the dynamic portion may be
dependent upon the time of day, the month, or the geographic area in which the
customer is effecting the purchase, for example. If dependent upon the time of
day,
the customer might enter her phone number as the first ten digits of the alias
and "02"
as the last two digits of the alias, assuming that the time is in the 2
o'clock hour, i.e.,
2:45 p.m., for example. It should of course be appreciated that the dynamic
portion
of the alias and/or the PIE may be dependent upon a wide variety of parameters
as is
necessary or desired.
In accordance with a further embodiment of the method of the invention, an
account-holder may routinely use a particular alias and PIE, but in addition
possess
specialty PIES. In accordance with this embodiment, the specialty PIES are
entered in
lieu of the routine PIE to effect certain predetermined options. For example,
a
specialty PIE might be utilized to deactivate the account-holder's debit card
permanently, or alternatively, for a predetermined time. This might be
particularly
2 0 useful in the situation where one misplaces her debit card but then finds
the debit card
two days later. Other specialty PIES might be utilized to provide a variety of
options.
For example, a specialty PIE might be utilized to adjust the available balance
on the
credit card utilized by a teenager under a parent's supervision. Thus, using a
suitable
21
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
account-holder interface, the account-holder would enter the alias and
specialty PIE
number. Thereafter, the user interface would prompt the parent account-holder
to
enter the desired credit limit.
In accordance with some of the exemplary embodiments described above,
processing to effect authorization was performed upon the entry of the alias
and PIE.
However, it should be appreciated that the method of the invention is not
limited to
such immediate processing. That is, a merchant operating in the setting of a
fair, for
example, may not have capabilities to communicate with a particular account-
holder's
banking institution. As a result, the merchant may accept the alias and PIE
from a
customer and perform the processing of the alias and PIE at some later time,
i.e., at
the end of the day. Such business operation is of course dependent upon the
merchant's risk assessment, i.e., weighing the desire to make the sale against
the
possibility of a fraudulent purchase.
Hereinafter, further considerations relating to use of multiple PIEs will be
described. As described above, an account-holder may rotate through different
PIES
for added security. Also, the account-holder may be prompted for a particular
PIE,
i.e., depending on where that account-holder is in the rotation of the PIES.
However,
it should be appreciated that considerations must be taken into account when
utilizing
multiple PIES in conjunction with batch techniques of processing. For example,
the
2 0 above described merchant operating in the setting of a fair may well
utilize batch type
processing at the end of the day to submit acquired alias and PIE numbers.
Also,
merchants in other situations may well utilize batch techniques. Thus, an "out
of
sequence" situation may arise from such batch processing. For example, the
account-
22
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
holder may have provided their alias and appropriate PIE number, based on the
rotation status, but that PIE has not yet been processed. As a result, if the
account-
holder attempts a second transaction of the day, the account-holder may be
prompted
yet again for the same PIE. This can cause problems with verification and
authorization of such an out of sequence transaction.
In accordance with one embodiment of the method of the invention, the above
out of sequence problem is addressed by accepting any PIE number coming from
certain vendors on a particular day. That is, the generally required order
sequence of
the PIE will be disregarded.
Alternatively, the verification and authorization of the transaction may
consider both the PIE number, as well as the time of the transaction. That is,
each
transaction is time-stamped. Thus, the time of each sequential transaction
would
progress in a manner corresponding with the particular PIE utilized.
. Further, a set of rules may be established to address specific situations.
For
l 5 example, a rule might indicate that if an alias and PIE are submitted
utilizing batch
processing techniques and no time of the transaction is provided, then that
transaction
will be authorized so long as the alias and PIE successfully fill a "slot" of
the day. To
explain, assume that PIE number 1 was used at one o'clock, PIE number 3 was
used at
three o'clock, and PIE number 1 was again used at five o'clock. Also assume
that an
2 0 untimed transaction was also submitted in that same day, and that the
untimed
transaction was done using the number 2 PIE. Then, in this case, the
activities of the
day match with the untimed PIE.
23
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
As described above and in accordance with one embodiment of the method of
the invention, it should be appreciated that an account-holder may utilize the
PIE and
alias of the invention in a first transaction of the day and later perform a
transaction
using the same card in the conventional manner, i.e., utilizing the magnetic
strip of
the card followed by the common signature. As should be appreciated, use of
the
alias and PIE may be highly desirable in some transactions. As a result, the
issuing
bank of the card may impose a fee for this added convenience. The fee may be
triggered by any suitable processing step such as authorization of an alias
and PIE.
Further, suitable fees may be imposed based on various other parameters as is
necessary or desired.
In further explanation of the system and method of the invention, Fig. 5
illustrates an exemplary transaction system 100, which utilizes the method of
the
invention. As shown in Fig. 5, the transaction system 100 includes a customer
110, a
merchant portion 120 and a card controller operating portion 130.
The customer 110, the merchant portion 120 and the card controller operating
portion 130 perform a variety of activities utilizing the processes of the
invention
described above. That is, the customer 110 interacts with the merchant portion
120
utilizing a communication interface 142. The communication interface 142 may
be in
the form of a network or over the Internet, for example. Alternatively, it
should be
2 0 appreciated, the communication interface 142 may simply be in the form of
verbal
communication between the customer 110 and the merchant portion 120.
The customer 110 and the merchant portion 120 interact utilizing the
processes of the invention as described above. Accordingly, during the course
of a
24
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
transaction, the customer 110 provides both an alias and PIE to the merchant
portion
120. In response, and at predetermined times during the transaction, the
merchant
portion 120 may communicate with the card controller operating portion 130.
The
communication between the merchant portion 120 and the card controller
operating
portion 130 may utilize a suitable communication interface 144 such as a
network or
the Internet 146, as shown in Fig. 5. The merchant portion 120 may also be
characterized as an "interface portion" in that it interfaces with the
customer.
Fig. 6 is a block diagram showing further details of the merchant portion in
accordance with embodiments of the methods and systems of the invention.
Specifically, Fig. 6 shows the various components a merchant may utilize by
which
an account-holder may enter an alias or a PIE. That is, the merchant portion
120 of
Fig. 6 includes a keypad 121, a forger print recognizer 122, a gene identifier
123, a
DNA identifier 124, a retina identifier 125 and a voice recognizer 126. The
merchant
portion 120 may use one of such components or more than one, as is desired, to
identify either the alias or the personal identification entry (PIE).
The merchant portion 120 may also include a digital signature pad, by which a
customer's signature may be digitally obtained, as is described above. The
merchant
portion 120 may also include a selection menu 128. The selection menu 128
allows a
user to enter various selections, as described above, such as which payment
method
2 0 might be utilized, for example.
Further, Fig. 7 is a block diagram showing further details of the customer 110
in accordance with one embodiment of the methods and systems of the invention.
Specifically, the customer 110 may include a personal digital assistant (PDA)
112.
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
The PDA may be utilized in conjunction with a cashier, for example, as
described
above.
As described above, the invention is discussed in the context of a purchasing
individual interacting with a business entity. However, the method of the
invention is
not limited to such interaction. Specifically, the alias and PIE technique of
the
invention may also be utilized in conjunction with other transactions, such as
business
to business interactions, for example.
In accordance with further aspects of the invention, the methods of using an
alias and PIE of the invention may also be applied to a situation where two or
more
approvals need to be provided prior to granting a transaction. This might
apply to a
transaction of a more substantial nature, for example. For instance, a major
purchase
by a company might require two approvals, or alternatively, a parent approving
a
major purchase of a teenager, for example. In these situations, multiple
approvals are
needed to execute the transaction. In other words, the account-holder may be
thought
of as being two persons.
In accordance with one embodiment of the invention, such multiple approvals
may utilize what might be characterized as a "partial PIEs," or alternatively,
the
multiple approvals might be characterized as "double PIEs." To explain, the
partial
PIES are submitted together, but probably at different times, so as to form a
complete
~ 0 PIE. The partial PIES include a first partial PIE and a second partial
PIE, for
example. The first partial PIE may be received and stored. Thereafter, in
order to
effect the transaction, the second partial PIE is required. Alternatively, the
second
26
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
partial PIE might be received first and then the first partial PIE, i.e., the
order of the
receipt of the first and second partial PTEs does not matter.
However, in accordance with one embodiment of the invention, there is a time
limit placed on how much time can pass between receipt of the two partial
PIES. For
example, when a first person submits her partial PIE, i.e., the first of two
needed
partial PIEs, she can specify the time limit or expiration period. To explain
further,
the elapsed time period between accepting entry of the first partial PIE and
accepting
entry of the second partial PIE is determined. If the elapsed time period is
greater
than a predetermined time period, for example the time period set by the first
person,
then the second partial personal identification entry is nulled, i.e., is made
invalid. As
a result, the transaction will not be authenticated nor performed.
Illustratively, college tuition is due for $5000. A father tells his son that
he
will pay for the tuition. The father calls in the alias, for the account from
which the
funds will be taken, and the father's partial PIE. The father provides an
expiration
date of five days. Subsequently, the son goes through the college finance
department
and sets up his courses. The son determines that the courses cost $4200 and,
after
four days, submits this amount using the alias of his father, or some other
password,
as well as the son's partial PIE. The transaction has both partial PIEs and is
authorized accordingly.
2 0 In accordance with embodiments of the method of the invention as described
above, a customer or business entity, for example, utilizes an alias and PIE
to perform
a transaction. The processing of the transactions as described above commonly
may
include transmission of data, including confidential information, over the
Internet or
27
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
other network. It should be appreciated that known techniques may be utilized
in
conjunction with the method of the invention. For example, conventional
encryption
techniques may be utilized to protect the confidentiality of data during
transmission.
Fig. 8 is a flowchart showing further aspects of the invention in accordance
with one embodiment of the methods of the invention. It should be appreciated
that
the process of Fig. 8, as well as Figs. 9-11 may be performed using the system
of
Figs. 5-7, or another suitable system.
As shown in Fig. 8, the process starts with step 100. Then, the process passes
to step 200. In step 200 the account-holder performs account-holder
operations,
l 0 which are described in further detail below. Then, in step 300, the card
member
submits an alias to a merchant. In step 400 the merchant submits the alias to
a card
controller operating portion over the Internet, or some other communications
network, for example. After step 400, the process passes to step 500.
In step 500, the card controller operating portion processes the alias,
charges a
fee and responds to the merchant over the Internet. Then, in step 600 the
merchant
queries and accepts a PIE from the customer. After step 600, the process
passes to
step 700. In step 700, the merchant submits the PIE to the card controller
operating
portion over the Internet, private network, or wireless network, for example.
In step
800 the card controller operating portion processes the PIE and responds to
the
2 0 merchant over the Internet, private network or wireless network, i.e., the
merchant
approves or denies the request. Then, in step 900, the merchant proceeds based
on
the response from the card controller operating portion. After step 900, the
process
passes to step 950. In step 950, the process ends.
28
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
Hereinafter, further aspects of the "account-holder performs account-holder
operations" step 200 of Fig. 8 will be described in further detail with
reference to Fig.
9. Specifically, Fig. 9 shows further aspects of use of a specialty PIE. As
shown in
Fig. 9, this sub-process starts in step 200. Then, the process passes to step
210. In
step 210 the account-holder changes the available balance on an account using
specialty PIE number 1. After step 210, the process passes to step 220.
In step 220 the account-holder deactivates an account using specialty PIE
number 2. Further, in step 230 account-holder activates an account using
specialty
PIE number 3. It should be appreciated that such deactivation and activation
may be
performed on different accounts or may be performed at different times, for
example.
After step 230, the process passes to step 240. In step 240 the account-holder
changes his or her personal identification entry (PIE) using specialty PIE
number 4.
Then, in step 250 the process returns to step 300.
Fig. 10 is a flowchart showing in further detail the "card controller
operating
portion processes PIE and responds to merchant over the Internet" step 800 of
Fig. 8
in accordance with one embodiment of the methods and systems of the invention.
As
shown in Fig. 10, the process starts in step 800. Then, in step 805 the card
controller
operating portion determines which account is selected by the entered PIE.
That is, it
should be appreciated that the account-holder may have multiple accounts which
may
2 0 be selected. Then, the process passes to step 810.
In step 810 the card controller operating portion determines which of three
PIES in rotation is the current PIE to be used. That is, the account-holder is
using a
security measure in which the account-holder rotates through three different
PIES.
29
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
Then, the process passes to step 820. In step 820 the card controller
operating
portion compares the current PIE to be used with the PIE entered by the
account-
holder. Then, in step 830 the process determines "is the PIE entered correct?"
If the
answer is "yes," i.e., the entered PIE is correct, then the process passes to
step 840.
In step 840 the process determines whether the PIE has expired?, i.e., whether
the PIE has been used too many times before renewing the PIE. If the
subsequent
determination is "No," in step 840, then the processes passes to step 842.
In step 842, the card controller operating portion approves the transaction,
and
may provide feedback information. Such feedback information may then be
conveyed on to the customer, i.e., such as by printing on the customer's
receipt. After
step 842, the process passes to step 860.
Alternatively, the process may determine that the PIE has expired in step 840.
Then, the process passes to step 844. In step 844 the transaction is denied.
After step
844, the process passes to step 860.
In step 830, if the entered PIE is determined to be incorrect, then the
process
passes to step 850, rather than step 840 as described above. In step 850, the
card
controller operating portion denies the transaction, but prompts the account-
holder by
providing the PIE rotation number. That is, for example, the card controller
operating
portion provides helpful feedback information to the account-holder which may
assist
2 0 the account-holder. After step 850, the process passes to step 860. In
step 860, the
process returns to step 900.
Fig. 11 is a flowchart showing the "card controller operating portion
processes
PIE and responds to merchant over the Internet" step 800 of Fig. 8 in
accordance with
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
a further embodiment of the methods and systems of the invention. As shown in
Fig.
10, the process starts in step 800. After step 800, as shown in Fig. 1 l, the
process
passes to step 870. In step 870 the process recognizes that the PIE is
actually the
signature of a customer. As a result, the card controller operating portion
retrieves a
verified signature from a database, for example. Then, the process passes to
step 872.
In step 872, the PIE, i.e., the signature of the customer, is compared with
the
retrieved verified signature. Then, in step 874, a determination is made as to
whether
a comparison between the PIE signature and verified signature is above a
threshold.
For example, the pixel data representing both the verified signature and the
submitted
signature may be compared. If the comparison is not above the threshold, then
the
process passes to step 876. In step 876, the transaction is denied. After step
876, the
process passes to step 879.
Alternatively, if above the threshold in step 874, then the process passes to
step 878. In step 878 the card controller operating portion approves the
transaction
requested. After step 874, the process passes to step 879. In step 879, the
process
returns to step 900.
It should be appreciated that various features in accordance with embodiments
of the methods and systems of the invention are described in conjunction with
use of
an alias and use of a PIE, respectively. However, it should further be
appreciated that
2 0 those features relating to an alias, as described above, may also be
applied to a PIE.
Further, those features relating to a PIE, as described above, may also be
applied to an
alias. For example, in accordance with embodiments of the methods and systems
of
31
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
the invention, the user may select an alias in the same manner as selection of
a PIE,
and vice-a-versa.
As described above, embodiments of the system of the invention as shown
above may be in the form of a computer or computer system. As used herein, the
term "computer" or "computer system" is to be understood to include at least
one
processor utilizing a memory or memories. The memory stores of the system of
the
invention retain at least portions of an executable program code at one time
or another
during operation of the processor portion of the computer. Additionally, the
processor executes various instructions included in that executable program
code. An
executable program code means a program in machine language that is able to
run in
a particular computer system in an environment to perform a particular task.
The
executable program code processes data in response to commands by a user. As
used
herein, it will be appreciated that the term "executable program code" and the
term
"software" mean substantially the same thing for the purposes of the
description as
used herein.
It is to be appreciated that to practice the system and method of the
invention,
it is not necessary that various processors and/or the memories used in the
practice of
the invention be physically located in the same place. That is, it should be
appreciated that each of the processors and the memories may be located in
2 0 geographically distinct locations and connected so as to communicate in
any suitable
manner, such as over a suitable network or the Internet, for example.
Additionally, it
should be appreciated that each of the processors and/or the memories may be
composed of the same or different physical pieces of equipment. Accordingly,
it is
32
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
not necessary that the processor be one single piece of equipment in one
location and
that the memory be another single piece of equipment in another location. That
is, it
is contemplated that the particular processor may be two pieces of equipment
in two
different physical locations. The two distinct pieces of equipment may be
connected
in any suitable manner. Additionally, a particular memory used in the
invention may
include two or more portions of memory in two or more physical locations.
Further,
the memory could include or utilize memory stores from the Internet, Intranet,
Extranet, LAN, satellite interface or some other source or over some other
network,
as may be necessary or desired.
As described above, the method of the invention may illustratively be
embodied in the form of a computer or computer operating system. It is to be
appreciated that the software or programs that enable the computer operating
system
to perform the operations described above may be supplied on any of a wide
variety
of media to hold data. Further, it should be appreciated that the
implementation and
operation of the system and method of the invention may be in the form of
computer
code written in any suitable programming language or languages, which provide
instructions to the computer by which the computer may manipulate data.
It should be appreciated that the software code or programming language that
is utilized in a computer system to perform the above described invention may
be
2 0 provided in any of a wide variety of forms. Illustratively, the software
may be
provided in the form of machine language, assembly code, target language,
object
code, source code or source language, as well as in other forms. Further, the
software
33
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
may be in the form of compressed or encrypted data utilizing a suitable
compression
or encryption algorithm.
Additionally, it should be appreciated that the particular medium utilized to
hold either the software used in conjunction with the invention or the data,
which is
manipulated by the software, may take on any of a variety of physical forms.
Illustratively, the medium may be in the form of a compact disk, a DVD, an
integrated circuit, a hard disk, a floppy diskette, a magnetic tape, a RAM, a
ROM, or
a remote transmission, as well as any other medium or source of information
that may
be read by a computer or other operating system.
Accordingly, the software of the method of the invention may be provided in
the form of a hard disk or be transmitted in some form using a direct
telephone
connection, the Internet, an Intranet, or a satellite transmission, for
example. Further,
the programming language enabling the system and method of the invention as
described above may be utilized on all of the foregoing and any other medium
by
which software or executable program code may be communicated to and utilized
by
a computer or other operating system.
As described herein, the system and method of the invention may utilize an
application program, a collection of separate application programs, a module
or
modules of a program, or a portion of a module of a program, for example. As
noted
2 0 above, it should be appreciated that the computer language used in the
system and
method of the invention may be any of a wide variety of programming languages.
Further, as is also noted above, it is not necessary that a single programming
language
be utilized in conjunction with the operation of the system and method of the
34
CA 02460886 2004-03-17
WO 03/027798 PCT/US02/29649
invention. Rather, any number of different programming languages may be
utilized
as is necessary or desirable.
As described above, in the system and method of the invention, a variety of
user interfaces may be utilized such as by a customer, for example. A user
interface
may be in the form of a key pad, for example. As used herein, a user interface
includes any software, hardware or combination of hardware and software used
in an
operating system that allows a user, or other person, to interact with the
operating
system. A user interface may also include any of a touch screen, keyboard,
mouse,
voice recognition device, dialogue screen, menu box, a list, a checlcbox, a
toggle
switch, a pushbutton or any other object that allows a user to receive
information
regarding the operation of the program and/or provide the operating system
with
information. Accordingly, a user interface used in conjunction with the system
and
method of the invention may be any device or collection of devices that
provides
cormnunication between a user, i.e., an account-holder for example, and a
computer.
The information provided by the user to the computer through the user
interface may
be in the form of a command, a selection of data, or other input, for example.
While the foregoing description includes many details and specifications, it
is
to be understood that these have been included for purposes of explanation
only, and
are not to be interpreted as limitations of the present invention. Many
modifications
2 0 to the embodiments described above can be made without departing from the
spirit
and scope of the invention, as is intended to be encompassed by the claims and
their
legal equivalents.