Note: Descriptions are shown in the official language in which they were submitted.
CA 02496539 2000-12-22
Encryptor, Encrypting Method, Decryptor, Decrypting Method, and
Computer Readable Recording Medium Having Program Stored Therein
This is a division of co-pending Canadian Patent Application
No. 2,366,353 filed on December 22, 2000.
Technical Field
The present invention relates to an encrypting apparatus, a decrypting
apparatus, and encryptin;g/decrypting method, in particular, to an invention
which enables to encrypt~decrypt another piece of data while a certain piece
of data is encrypted/decrypted.
Background Art
Fig. 43 shows a block diagram of an encryptor performing encryption
of Cipher Block Chaining; Mode (hereinafter, referred to as the CBC mode).
An encryption of the CBC mode is performed as follows: first,
plaintext block data M; of 64 bits is input by block unit; the input data is
encrypted by an encrypting module 51 using an encryption key K; ciphertext
block data C; and plaintext block data M;+~, subsequent to the data M;, are
XORed; and the XORed result is supplied to the encrypting module 51, for
encryption using the encryption key K, as a next input for encrypting
process. Then, this process is repeatedly chained, and the whole plaintext
data M will be encrypted into ciphertext data C.
Fig: 44 shows a block diagram of a decrypting apparatus performing
decryption of the CBC mode.
The decrypting apparatus shown in Fig. 44 is an apparatus for
CA 02496539 2000-12-22
decrypting the cipherte:~t data encrypted by the encrypting apparatus shown
in Fig. 43. The cipherl:ext block data C, is input to a decrypting module 'll
for decryption using the encryption key K, XORed with an initial value IV,
and decrypted into plai:nt;ext block data M,. When ciphertext block data C
is input, the block data C~ is decrypted by the decrypting module ?1 using
the encryption key K, XORed with the cipher text block data C,, which has
been previously input and stored in a register 111, and decrypted into
plaintext block data M~.
Here, the register 111 can be provided inside a selector 73.
The CBC mode can be represented by the following expressions
where plaintext block data is M; (i = 1, 2, ..., n), ciphertext block data C;
(i = 1,
2, ... , n), the encrypting process using the encryption key K is defined as
E~,
and the decrypting process using the encryption key ~ is defined as D~:
C, = E~ (M, EXR IV)
C; = E,; (M; EXR C;_,) (i = 2, 3, ..., n)
M, = D~ (C,) EXR IV
M; = Dk (C;) EXR C;., (i = 2, 3, ..., n)
Here, EXR represents an XOR operation. IV represents an initial
value to be used for an initial step of encrypting and decrypting processes.
The same initial value IV is used both in the encryptor and the decryptor.
Fig. 45 shows an encryptor performing encryption of Output
Feedback Mode (hereinafter, referred to as OFB mode).
Fig. 46 shows a decryptor performing decryption of the OFB mode.
Fig. 4'l shows an encryptor performing encryption of Cipher
Feedback Mode (hereinafter. referred to as CFB mode).
CA 02496539 2000-12-22
3
Fig. 48 shows a decryptor performing decryption according to the
CFB mode.
Here, the register 111 can be provided inside the selector 73.
Fig. 49 is a block diagram showing a procedure for encrypting
plaintext data M and plaintext data N using the encryptor of the CBC mode.
Hereinafter, a case in which the plaintext data M including plaintext
block data M,, plainte:xt, block data M~, and plaintext data M3, and the
plaintext data N including only plaintext block data N, will be explained.
When the encryption of plaintext block data M, is started, ciphertext
block data C, is output;, and the ciphertext block data C, is also used for
encrypting process of plaintext block data M,,. In this way, ciphertext block
data C; is fed back to the process of encrypting plaintext block data M;+"
which forms a chained process. Accordingly, it is not possible to encrypt the
plaintext block data N, 'unless encrypting process of the plaintext block data
M, through the plaintext block data M3 has been finished.
Fig. 50 shows the encrypting process of the CBC mode as well as Fig.
49.
In case of Fig. 50; it takes long to prepare each of the plaintext block
data M" the plaintext block data M~, and the plaintext block data M3.
While, the encryption has been finished before the next plaintext block data
M;+, is prepared, which g;e:nerates an idle time (time between T1 through T2,
T3 through T4). In this way, even if the idle time is generated, the chain
process has to be performed such that the ciphertext block data C; should be
fed back to the encrypting process of the plaintext data M;+,. Therefore, the
process for the plaintext block data N, cannot be performed until the
CA 02496539 2000-12-22
4
encrypting process of the plaintext block data M3 is finished.
Fig. 51 shows a data confidentiality process and a data integrity
ensuring process. The plaintext data M is, for example, encrypted into the
ciphertext data C by the encryptor of the OFB mode. A message
authentication code (MA,C) P is computed by the encryptor of the CBC mode,
and is appended to the last bit of the ciphertext data C. In case of receiving
data which is encrypteal and to which the MAC P is appended, as well as
decrypting the ciphertext data C into the plaintext data M by the decryptor
of the OFB mode, the MAC P is computed from the ciphertext data C by the
decryptor of the CBC mode. It is possible to confirm the ciphertext data C
transmitted has not tampered by comparing the obtained MAC P with the
MAC P transmitted and received.
Fig. 52 shows a procedure for the confidentiality process and the
MAC computing process shown in Fig. 51.
The plaintext block data M, through the plaintext block data M3 are
serially encrypted into the ciphertext block data C, through the ciphertext
block data C3. Subsequent, the MAC P is computed by serially inputting
the ciphertext block data C, through ciphertext block data C3.
The encryptor and the decryptor of each mode shown in Figs. 42
through 48 has a problem as follows: the data obtained by encrypting and
decrypting process of the previous block data should be fed back and used for
encrypting and decrypting the next block data; there is a problem that once
the encrypting process or the decrypting process is started, another
encrypting process or another decrypting process cannot be started unless
the whole steps of the e~lcrypting process or the decrypting process are
CA 02496539 2000-12-22
finished. Accordingly, if the encrypting/decrypting process, which is
previously started, requires much time, the subsequent
encrypting/decrypting process should wait for a long time.
Further, in case of performing the confidentiality process and the
5 integrity ensuring process, the integrity ensuring process should be
performed after performing the confidentiality process, which takes a long
processing time.
It is an object of tile preferred embodiment of the present invention to
obtain an encryptor, a decryptor, an encrypting method, and a decrypting
method which can perform encrypting/decrypting process of another piece
of data while the encrypting/decrypting process of a certain piece of data is
performed.
Further, it is another object of the preferred embodiment of the
present invention to perform encryption/decryption of the data having a
higher priority prior to other data.
Further, it is another object of the preferred embodiment of the
present invention to perform the confidentiality process and the integrity
ensuring process in parallel at a high speed.
Disclosure of the Invention
In accordance with one aspect of the present invention there is
provided an encrypting apparatus encrypting plaintext data including at least
one plaintext block data into ciphertext data using an encrypting unit and
generating a message authentication code (MAC) to ensure an integrity of
the ciphertext data, the encrypting apparatus comprising: an encrypting unit,
CA 02496539 2000-12-22
6
having a first feedback hoop for feeding back ciphertext block data C; output
by the encrypting unit to the encrypting unit when the plaintext block data is
encrypted by the encrypting unit, for inputting the plaintext data, performing
an encrypting process by feeding back the ciphertext block data C; through
the first feedback loop, and outputting the ciphertext block data; a message
authentication code (M,AC) generator, having a second feedback loop for
feeding back a computed intermediate MAC result, for inputting the
ciphertext block data whenever the ciphertext block data is output from the
encrypting unit, processing data, feeding back the computed intermediate
MAC result by the second feedback loop, and generating the MAC to ensure
the integrity of the ciphertext data.
In accordance with another aspect of the present invention there is
provided an encrypting method for encrypting plaintext data including at
least one plaintext block: data into ciphertext data using an encrypting unit
and generating a message authentication code (MAC) to ensure an integrity
of the ciphertext data, the encrypting method comprising: an encrypting
step, including a first feedback step for feeding back ciphertext block data
C;
output from the encrypting unit when the encrypting unit encrypts plaintext
block data, inputting the plaintext block data, performing an encrypting
process by feeding back the ciphertext block data C; through a first feedback
loop, and outputting a ciphertext block data; and a MAC generating step,
including a second feedback step for feeding back a computed intermediate
MAC result, inputting the ciphertext block data whenever the ciphertext
block data is output from the encrypting step, processing data, feeding back
CA 02496539 2000-12-22
l
the computed intermediate MAC result through the second feedback step,
and generating the MAC: to ensure the integrity of the ciphertext data.
In accordance with yet another aspect of the present invention there is
provided a decrypting apparatus decrypting ciphertext data including at least
one ciphertext block data into plaintext data, and generating a message
authentication code (MAC) for ensuring an integrity of ciphertext data, the
decrypting apparatus comprising: a decrypting unit, including a first
feedback loop for feeding back module output block data T; generated at
decrypting data by a decrypting module, for inputting the ciphertext block
data, decrypting the ciphertext block data using the module output block
data T; fed back through the first feedback loop, and outputting plaintext
block data; a MAC genf:rator, including a second feedback loop for feeding
back a computed internnediate MAC result, for inputting ciphertext block
data identical to the c:iphertext block data input to the decrypting unit,
processing the data, outputting the computed intermediate MAC result,
feeding back the computed intermediate MAC result through the second
feedback loop, and generating the MAC for ensuring the integrity of
ciphertext data.
In accordance wivth still yet another aspect of the present invention
there is provided a decrypting method decrypting ciphertext data including
at least one ciphertext block data into plaintext data and generating a
message authentication code (MAC) for ensuring an integrity of the
ciphertext data, the decrypting method comprising: a decrypting step
including a first feedback step for feeding back module output block data T;
generated at decrypting data by a decrypting module, inputting the
CA 02496539 2000-12-22
s
ciphertext block data, df:crypting the ciphertext block data using the module
output block data T; fed back through the first feedback loop, and outputting
plaintext block data; a MAC generating step including a second feedback
step for feeding back a computed intermediate MAC result, inputting
ciphertext block data identical to the ciphertext block data input to the
decrypting unit, processing the data, outputting the computed intermediate
MAC result, feeding back the computed intermediate MAC result by the
second feedback loop, and generating the MAC for ensuring the integrity of
ciphertext data.
In accordance with still yet another aspect of the present invention
there is provided an encrypting apparatus encrypting plaintext data including
at least one plaintext block data and generating a message authentication
code (MAC) for ensuring an integrity of ciphertext data, the encrypting
apparatus comprising: an encrypting unit, having a first feedback loop for
feeding back module output block data T; output from the encrypting module
to the encrypting module when the plaintext block data is encrypted by the
encrypting unit, for inputting the plaintext data, performing encrypting
process by feeding back the module output block data T; through the first
feedback loop, and outputting the ciphertext block data; a MAC generator,
having a second feedback loop for feeding back a computed intermediate
MAC result, for inputting; the ciphertext block data whenever the ciphertext
block data is output from the encrypting unit, processing data, feeding back
the computed intermediate MAC result through the second feedback loop,
and generating the MAC t:o ensure the integrity of the ciphertext data.
CA 02496539 2000-12-22
9
In accordance with still yet another aspect of the present invention
there is provided an encrypting method for encrypting plaintext data
including at least one plaintext block data into ciphertext data using an
encrypting unit and generating a message authentication code (MAC) to
ensure an integrity of the ciphertext data comprising: an encrypting step,
having a first feedback step for feeding back module output block data T;
output from an encrypting module when the plaintext block data is
encrypted, for inputting the plaintext block data, performing an encrypting
process by feeding back the module output block data T; through a first
feedback loop, and outputting ciphertext block data; and a MAC generating
step, having a second feedback step for feeding back a computed
intermediate MAC result, for inputting the ciphertext block data whenever
the ciphertext block data is output from the encrypting step, processing data,
feeding back the computed intermediate MAC result through the second
feedback step, and generating the MAC to ensure the integrity of the
ciphertext data.
In accordance with still yet another aspect of the present invention
there is provided a decrypting apparatus decrypting ciphertext data including
at least one ciphertext block data into ciphertext data using a decrypting
module and generating a message authentication code (MAC) to ensure an
integrity of the ciphertext data, the decrypting apparatus comprising: a
decrypting unit, having a first feedback loop for feeding back ciphertext
block data C; output from the decrypting unit to the decrypting unit when the
ciphertext block data is decrypted by the decrypting unit, for inputting the
ciphertext data, performing a decrypting process by feeding back the module
CA 02496539 2000-12-22
output block data T; through the first feedback loop, and outputting the
ciphertext block data; a message authentication code (MAC) generator
having a second feedback loop for feeding back a computed intermediate
MAC result, for input ing the ciphertext block data identical to the
5 ciphertext block data input to the decrypting unit, processing data, feeding
back the computed intermediate MAC result through the second feedback
loop, and generating the MAC to ensure the integrity of the ciphertext data.
In accordance with still yet another aspect of the present invention
there is provided a decrypting method for decrypting ciphertext data
10 including at least one ciphertext block data into plaintext data using a
decrypting unit and generating a message authentication code (MAC) to
ensure an integrity of the ciphertext data, the decrypting method comprising:
a decrypting step, having a first feedback step for feeding back ciphertext
block data C;, for inputting the ciphertext block data, performing a
decrypting process of the: ciphertext block data C; fed back through the first
feedback loop, and outputting plaintext block data; and a MAC generating
step, having a second feedback step for feeding back a computed
intermediate MAC result; for inputting the ciphertext block data identical to
the ciphertext block data input to the decrypting step, processing data to
output the computed intermediate MAC result, feeding back the computed
intermediate MAC result through the second feedback step, and generating
the MAC to ensure the integrity of the ciphertext data.
In accordance with still yet another aspect of the present invention
there is provided an encrypting apparatus comprising: an encrypting unit for
inputting data to encrypt and outputting encrypted data; and a message
CA 02496539 2000-12-22
11
authentication code (MAC) generator for inputting the encrypted data output
from the encrypting unit and generating a MAC for ensuring an integrity of
the encrypted data, and wherein the MAC generator starts generating the
MAC before completion of encrypting the data by the encrypting unit.
In accordance with still yet another aspect of the present invention
there is provided a decrypting apparatus comprising: a decrypting unit for
inputting data to decrypt and outputting decrypted data; and a message
authentication code (MAC) generator for inputting the decrypted data output
from the decrypting unit and generating a MAC for ensuring an integrity of
encrypted data, and wherein the MAC generator starts generating the MAC
before completion of decrypting the data by the decrypting unit.
In accordance with still yet another aspect of the present invention
there is provided an encrypting method comprising: an encrypting step for
inputting data to encrypt and outputting encrypted data; and a MAC
generating step for inputaing the encrypted data output from the encrypting
step and generating a M.AC for ensuring an integrity of the encrypted data,
and wherein the MAC generating step starts generating the MAC before
completion of encrypting the data by the encrypting step.
In accordance with still yet another aspect of the present invention
there is provided a decrypting method comprising: a decrypting step for
inputting data to decrypt and outputting decrypted data; and a MAC
generating step for inputting the decrypted data output from the decrypting
step and generating a MAC for ensuring an integrity of the encrypted data,
and wherein the MAC generating step starts generating the MAC before
completion of decrypting the data by the decrypting step.
CA 02496539 2000-12-22
12
Brief Description of the Drawings
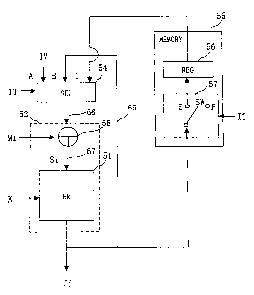
Fig. 1 shows an encryptor of the CBC mode according to the first
CA 02496539 2000-12-22
13
embodiment.
Fig. 2 shows an operation procedure of the encryptor of the CBC
mode.
Fig. 3 is a flowchart showing an operation of the encryptor of the
CBC mode.
Fig. 4 is a flowchart showing an operation of a selector 54.
Fig. 5 is a flowch.a.rt showing an interrupting process of a switch 57.
Fig. 6 shows another example of a memory 55.
Fig. 7 is a flowchart showing an interrupting process of the memory
55.
Fig. 8 shows another example of the memory 55.
Fig. 9 shows a priority processing.
Fig. 10 shows another priority processing.
Fig. 11 shows another priority processing.
Fig. 12 shows a <;ase in which the memory 55 is provided in parallel
with a feedback line 66.
Fig. 13 shows an operation procedure of the encryptor of Fig. 12.
Fig. 14 shows a ease in which the memory 55 is provided in parallel
with a feedback line 67.
Fig. 15 shows an operation procedure of the encryptor of Fig. 14.
Fig. 16 shows an encryptor of the OFB mode.
Fig. 17 shows an operation procedure of the encryptor of Fig. 16.
Fig. 18 shows an encryptor of the CFB mode.
Fig. 19 shows an .operation procedure of the encryptor of Fig. 18.
Fig. 20 shows a decryptor of the CBC mode.
CA 02496539 2000-12-22
14
Fig. 21 shows an operation procedure of the decryptor of Fig. 20.
Fig. 22 shows a decryptor of the OFB mode.
Fig. 23 shows an operation procedure of the decryptor of Fig. 22.
Fig. 24 shows a ~decryptor of the CFB mode.
Fig. 25 shows an operation procedure of the decryptor of Fig. 24.
Fig. 26 shows an encryptor of the CBC mode storing a key.
Fig. 27 shows an operation procedure of the encryptor of the CBC
mode.
Fig. 28 shows a decryptor of the CBC mode storing a key.
Fig. 29 shows an operation procedure of the decryptor of the CBC
mode.
Fig. 30 shows an operation procedure of an encryptor having an
encrypting unit 100 and a MAC generator 200.
Fig. 31 shows a flowchart of an encryptor having an encrypting unit
100 and a MAC generator 200.
Fig. 32 shows an encryptor in which an encrypting unit 100 and a
MAC generator 200 are united as one unit.
Fig. 33 shows an operation procedure of the encryptor in which an
encrypting unit 100 and a MAC generator 200 are united as one unit.
Fig. 34 shows a decryptor having a decrypting unit 300 and a MAC
generator 400.
Fig. 35 shows a cfecryptor in which a decrypting unit 300 and a MAC
generator 400 are united as one unit.
Fig. 36 shows a:n operation procedure of the decryptor in which a
decrypting unit 300 and a MAC generator 400 are united as one unit.
CA 02496539 2000-12-22
Fig. 37 shows .an encryptor having an encrypting unit 100 and a
MAC generator 200 according to the second embodiment.
Fig. 38 shows a decryptor having a decrypting unit 300 and a MAC
generator 400.
5 Fig. 39 shows a model configuration of an encrypting module 51
using an encryption key K.
Fig. 40 shows an implementation example of a hardware of an
encryptor and a decrypt;or.
Fig. 41 shows an implementation example of a hardware of an
10 encryptor and a decrypt;or.
Fig. 42 shows a case in which an cipher program 47 is called by an
application program 46..
Fig. 43 shows a conventional encryptor of the CBC mode.
Fig. 44 shows a conventional decryptor of the CBC mode.
I5 Fig. 45 shows a conventional encryptor of the OFB mode.
Fig. 46 shows a conventional decryptor of the OFB mode.
Fig. 47 shows a conventional encryptor of the CFB mode.
Fig. 48 shows a conventional decryptor of the CFB mode.
Fig. 49 shows a conventional encrypting procedure.
Fig. 50 shows a conventional encrypting procedure.
Fig. 51 explains a confidentiality process and an integrity ensuring
process.
Fig. 52 shows an operation procedure of a conventional
confidentiality process and a conventional integrity ensuring process.
CA 02496539 2000-12-22
I6
Best Mode for Carrying out the Invention
Embodiment 1.
Fig. 1 shows an encryptor of the CBC mode according to the present
embodiment.
The encryptor of the present embodiment is configured by a selector
54, an XOR circuit 58, an encrypting module 51 using an encryption key K,
and a memory 55. An encrypting unit 52 includes the XOR circuit 58 and
the encrypting module 51 using the encryption key K. The selector 54 and
the encrypting module 51 using the encryption key K form a feedback loop
with feedback lines 65, 66, and 67. Ciphertext block data C; encrypted by
the encrypting module 51 using the encryption key K is input to the XOR
circuit 58 again through the feedback loop, and module input data S; is
generated at the XOR circuit 58. Then, the module input data S; generated
is supplied to the encrypting module 51 using the encryption key K.
The memory 55 :is provided in parallel with the feedback line 65.
The memory 55 includes a register 56 and a switch 57. The switch 57
switches inputting to the register 56 or ignoring an output of the encrypting
module 51 using the encryption key K. This switching is performed by, for
example, an interrupt IT. When the interrupt IT is generated, the switch
57 is connected to E, and when the interrupt is resolved, the switch 5 7 is
connected to F The register 56 inputs and stores the ciphertext block data
C; supplied through E. The ciphertext block data C; is output to the selector
54. The selector 54 is provided with three inputs A, B and C and selects one
out of three. This selection is dependent on the interrupt IT.
Fig.2 shows an open ation pr ocedure of the encryptor shown in Fig. 1.
CA 02496539 2000-12-22
li
Fig. 3 is a flowchart showing an operation of the encryptor shown in
Fig. 1.
The input of tlae selector 54 is set to A when the electric power is
supplied to the encryptor, and the switch 57 is connected to E. Further,
when plaintext data N is requested to encrypt, an interrupt IT is generated.
The interrupt IT keeps ON unless the request to encrypt the plaintext data
N is resolved. ~ Furthe:r, the plaintext data M is encrypted using the key K,,
and the plaintext data :1V is encrypted using the key K~. When the interrupt
IT is generated or the interrupt IT is resolved, the key K, or the key K~ is
supplied again to the encrypting module.
At the time of T0, the key K, is supplied, and the encrypting process
of the plaintext data TVI, is started. When the encrypting process of the
plaintext data M, is started at the time of T0, the input of the selector 54
is
switched to B after the initial value IT is once input from the input A of the
selector 54. Further, a.t the time of ~ during the plaintext data M, is being
encrypted using the ke;y K,, it is assumed an interrupt IT for requesting to
encrypt the plaintext block data N, is generated. The ciphertext block data
C, becomes to be stored in the memory 55 by the time of T1. Then, at the
time of T1, the key K., is supplied to the encrypting module 51 due to the
generation of the interrupt IT. Further, the selector 54 sets the input to A
at
the time of T1. The switch 57 is connected to F at the time of T1. After the
time of T1, the plaintexl~ block data N, is encrypted using the key K~, and
the
ciphertext block data D, is output. At the time of Y, it is assumed the
encryption of the plaint~ext block data N, is finished, and the interrupt IT
is
resolved. Due to the resolution of the interrupt IT, at the time of T2, the
key
CA 02496539 2000-12-22
Ig
K1 is supplied to the encrypting module 51, the input of the selector 54 is
switched to C, and the switch 57 is connected to E. By switching the
selector 54 to C, the ciphertext block data C, stored in the memory 55 is
input for encrypting the plaintext block data M~, the plaintext block data M
is encrypted by the encrypting module using the key K,, and the ciphertext
block data C~ is output. Before the time of T3, the input of the selector 54
is
switched to B. In case of encrypting the plaintext block data M3, the
ciphertext block data C,, is fed back from a feedback line 65 of a feedback
loop
and input, the plaintexi; block data M3 is encrypted by the encrypting module
using the key K,, and the ciphertext block data C3 is output.
When the same keys are used for encrypting the plaintext data M
and the plaintext data N (K, = K~), it is sufficient to supply the key only
once
at the starting time of the encrypting process.
A whole operation will be explained referring to the flowchart of Fig.
3.
At step S1, the encrypting process of the plaintext data M is started
and continued. When the final block data is finished to be processed, the
encrypting process terrr~inates. At step S2, an interrupt IT generated at an
arbitrary timing is observed. When the interrupt IT is generated while the
plaintext block data M; is processed, at step S3, the ciphertext block data C;
which is being processed is stored in the register 56 of the memory 55. At
step S4, the encrypting process of the plaintext data N, which is requested to
be encrypted by the interrupt IT, is performed. This encrypting process of
step S4 is continuously ;performed until the interrupt IT is released as shown
. in step S5. When the interrupt IT is released; at step S6, the plaintext
CA 02496539 2000-12-22
19
block data M; is encrypted using the ciphertext block data C; stored in the
register 56 of the memory 55. Afterwards, the process returns to step S1,
and the encrypting process will be continued.
Fig. 4 shows an operation of the selector 54.
When the electric power is turned ON, the input is set to A as shown
at step S11. When the encrypting process starts at step 512, the input is set
to B at step S13. Namely, the ciphertext block data C; fed back from the
feedback line 65 of the feedback loop is used. At step S14, if it is detected
the block data which is being processed is the final data, the process returns
to step S11 in which the status is the same as the electric power is turned
ON.
At step S 15, if it is detected the interrupt IT is generated, the input is
set to
A at step 516, and if the encrypting process is started, the input is set to B
at
step S18. Until the interrupt IT is resolved, the input is kept to B. That is,
the ciphertext block data C; fed back from the feedback line 65 of the
feedback loop is used. At step S19, if it is detected the interrupt IT is
resolved, the input is set to C at step 520. By setting the input to C, the
ciphertext block data C'; stored in the memory 55 is input. When the
encrypting process using' the input from C, the process returns to step S13
and the input is set to B.
As described above, the selector 54 can be switched based on the
generation of the interrupt IT.
The encrypting process of the plaintext data M can be also started at
an arbitrary time based on the generation of the interrupt IT.
Fig. 5 is a flowchart which shows processing the interrupt by the
switch 51.
CA 02496539 2000-12-22
When the electric; power is turned ON and in case of the encrypting
process of the first plaintext thereafter, the switch 57 is connected to E.
When the interrupt IT is generated at step S31, the switch 57 is switched
from E to F. Then, at step 533, it is detected the interrupt IT is resolved,
the switch 57 is switched from F to E. In this way, the switch 57 ignores the
ciphertext block data C; from the generation to the resolution of the
interrupt.
Accordingly, the register 56 of the memory 55 holds the ciphertext block data
C;, which was generated at generating time of the interrupt IT.
As described above, the operations of the encryptor illustrated in
Figs. 1 through 5 show the interrupt processing mechanism which receives
the request to encrypt the plaintext data N before completion of the
encryption of the plaintext data M in the encryptor for encrypting the
plaintext block data M; (i = 1, 2, 3, ... ) included in the plaintext data M
and
the plaintext block data N~ (j = 1, 2, 3, ...) included in the plaintext data
N.
Further, the encryptor shown in Figs. 1 through 5 includes the
encrypting module 51 for encrypting the plaintext block data M; and
outputting the cipherte~xt block data C;, the feedback loop 65 and 66 for
feeding the ciphertext block data C; output from the encrypting module 51
back to the encrypting unit 52 via the feedback line 65, and the memory 55,
provided in parallel wiith the feedback line 65 of the feedback loop, for
receiving the encryption request of the plaintext data N by the interrupt, and
storing the ciphertext block data C; fed back if the plaintext block data M;+,
is
not encrypted subsequent to the plaintext block data M; by starting the
encrypting process of any of the plaintext block data N.
Further, the encryptor shown in Figs. 1 thr ough 5 includes the
CA 02496539 2000-12-22
21
selector 54 for selecting the ciphertext block data C;, fed back by the
feedback
line 65 of the feedback loop, and supplying the ciphertext block data C;
through the feedback loop when the plaintext block data M ;+, is encrypted
subsequent to the plaintext block data M;, and for selecting the ciphertext
block data C; stored in i;he memory 55 and supplying to the encrypting unit
52 through the feedback: loop when the plaintext block data M;+, is not
encrypted next to the :plaintext block data M;, and the any piece of the
plaintext data N.
The memory 55 stores the status of the encryptor in case of the
interrupt IT is generated. By storing the status of encrypting process, it
becomes possible to return to the original status of encrypting a certain
piece
of data even if the encryption of another piece 'of data is performed during
the certain piece of data is encrypted. Namely, by using the data stored in
the memory, the status of the encryptor can return to the status which is
completely identical to the status at the time when the encryption is
interrupted, which enables to continue the interrupted encrypting process.
Fig. 6 shows another configuration example of the memory 55.
The memory 55 includes an interrupt control unit 52, an input switch
96, an output switch 97., and plural registers (REG l, 2, 3). By providing
the plural registers in this way, it becomes possible to receive plural
interrupts.
Fig. 7 shows processing the interrupt performed by the memory 55.
When the interrupt IT is generated, at step 541, the number k, which
is the number of the register k being currently used, is stored. At step S42,
the input switch 96 and t;he output switch 9 7 are connected to the register
l,
CA 02496539 2000-12-22
9~
which is one of the registers except the register k. At this status, the
encrypting process of the plaintext data N is performed. Further, it is
observed if another interrupt is generated during the plaintext data N is
encrypted. When it is detected another interrupt IT is generated at step
S43, the step 540, which is the process for processing the interrupt, is
called
again. In this way, whenever the interrupt IT is generated, the step S40 is
recursively called. Consequently, plural hierarchical processes for
processing the interrupt can be performed. At step S44, it is checked if the
interrupt is resolved. When the interrupt is resolved, the input switch 96
and the output switch 97 are switched to the register k using the number k
stored in the memory. In case of Fig. 6, the memory 55 includes three
registers, so that 3 layer hierarchical processes for processing the interrupt
can be performed.
Fig. 8 shows another configuration example of the memory 55.
The memory 55 includes a stack 64. The stack 64 is a register of
first-in last-out (FILO). When the interrupt IT is generated during a stack
1 is used, the data stored in the stack 1 is transferred to a stack 2, and the
data thereafter is stacked in the stack 1. When the interrupt IT is resolved,
the stacked data in the stack 1 is output, and the data stored in the stack 2
is
returned to the stack 1. Fig. 8 shows a case in which 4 layer hierarchical
processes for processing the interrupt can be performed.
As shown in Fig. 6, when it is possible to perform plural hierarchical
processes for processing the interrupt, a priority can be assigned to each of
the interrupts. For example, a priority- 1 is assigned to the interrupt ITl,
and a priority 2, which means a lower priority than the priority 1, is
assigned
CA 02496539 2000-12-22
23
to the interrupt IT2. E~y assigning the priority in this way, it is possible
to
postpone the process fo:r the priority 2 when the interrupt IT1 having the
priority 1 is generated.
Fig. 9 shows a case in which the encrypting process having the
priority 1 is performed prior to the encrypting process having the priority 2.
In this case, the encrypting process having the priority 1 is finished first.
Fig. 10 shows a case in which both encrypting processes have the
same priorities.
When the priorities are the same, each of the plaintext block data of
the both encrypting processes is encrypted alternately.
Fig. 11 shows a case in which data having the priority 1 and data
having the priority 2 are encrypted.
By assigning the priority to each interrupt as shown in Figs. 9
through 11, it is possible to perform the encrypting process which is
desirable
for the user. In case of processing data of an urgent matter or data with a
short length, effective processing can be performed by assigning a higher
priority to such data.
Fig. 12 shows a case in which the memory 55 is placed in parallel
with the feedback line 66.
The XOR circuit 58 and the encrypting module 51 using the
encryption key K constitute the encrypting unit 52.
Fig. 13 shows an operation procedure of the encryptor of Fig. 12.
When the following connections are selected by the first selector 61
and the second selector f 2, which enables these selector s to operate in the
same manner as the selecaor 54 of Fig. 1.
CA 02496539 2000-12-22
24
the first selector 61 + the second selector 62 = the selector 54
A + D - A
B + D - B
A + C - C
B + C - C
In Fig. 13, when the second selector 62 selects D, the selection (A or
B) of the first selector 61 becomes effective, and when the second selector 62
selects C, the contents of the memory 55 is output. Namely, the second
selector 62 should select C if the contents of the memory 55 is desired to be
used (when the encrypting process is returned from the plaintext data N to
the plaintext data M due to the resolution of the interrupt IT).
Fig. 14 shows a case in which the memory 55 is placed in parallel
with the feedback line 67.
Fig. 15 shows an operation procedure of the encryptor of Fig. 14.
If the time X when the interrupt IT is genes ated is before XOR
operation by the XOR circuit 58, the memory 55 stores the module input data
S; XORed by the XOR circuit 58. Then, the plaintext block data N, is
encrypted. Subsequent., the second selector 62 is made to select and input
the module input data S; to the encrypting module 51 using the encryption
key K, and encrypted to output the ciphertext block data C,.
As shown in Fi~;s. 1, 12, and 14, the memory 55 can be placed in
parallel with any one of the feedback line 65, the feedback line 66 and the
feedback line 67. The memory 55 stores the status which is just before the
encryptor starts encrypting another piece of data during encrypting a certain
piece of data. The memory 55 can be placed at any place as long as the
CA 02496539 2000-12-22
'~ 5
encryptor can return to the original status using the data stored in the
memory 55 when the encryptor finishes encrypting the other data. Further,
the memory 55 can be provided at plural locations.
As described above, the encryptor according to the present
embodiment performs encrypting process of the first processing data
(plaintext M) including at least one block data M; (i = 1, 2, 3, ..., m) and
the
second processing data (plaintext N) including at least one block data N~ (j =
1, 2, 3, ..., n) and the encryptor includes the memory 55 for storing the
status
of encrypting process. The encryptor starts encrypting the first block data
of the second processing data before encrypting all of the block data (M,-Mm)
of the first processing data. And at the time when the encryptor starts
encrypting the first block data N, of the second processing data, the state of
the encryption of the first processing data (for example, ciphertext block
data
C;) is stored in the memory 55. When the encryptor restarts encrypting the
first processing data, the status of the encryption of the encryptor is
returned
to the stored status of the encryption of the first processing data, and then
the encryptor restarts processing encryption of the first processing data.
Further, the encryptor restarts encrypting the first processing data
before completing the encryption of data of all blocks (N,-Nn) of the second
processing data, and simultaneously the memory 55 stores the status of the
encryption of the second processing data (for example, ciphertext block data
D~) when the encryptor restarts encrypting the first processing data. When
the encryptor restar is encrypting the second processing data, the status of
the encryption of the encryptor is returned to the stored status of the
encryption of the second processing data, and then the encryptor restarts
CA 02496539 2000-12-22
26
encrypting the second processing data.
Fig. 16 shows a configuration of the encryptor of the OFB mode.
The figure is characterized by additionally including the memory 55.
The memory 55 stores module output data T, supplied from the encrypting
module 51.
Fig. 16 shows an encryptor for encrypting plaintext block data M; (i =
1, 2, 3, ...) included in the plaintext data M and plaintext block data N~ (j
= 1,
2, 3, ...) included in the plaintext data N. The encryptor includes a
processing mechanism of the interrupt that receives the request to encrypt
the plaintext data N during the encryption of the plaintext data M before the
completion of encrypting the plaintext data M and the encrypting module 51
for outputting encrypted data as the module output block data T;. The
encryptor further includes feedback loops 65 and 66 for feeding back the
module output block data T; supplied from the encrypting module 51 to the
encrypting module through the feedback line 65, and the memory 55
provided in parallel with the feedback line 65 of the feedback loop and for
receiving a request to encrypt the plaintext data N and storing the module
output block data T; fed back when the plaintext block data M;+, is not
encrypted subsequent to the plaintext block data M; because the encryptor
starts encrypting any plaintext block data of the plaintext data N. Yet
further the encryptor :includes the selector 54 which selects the module
output block data T; fed back by the feedback line 65 of the feedback loop to
supply to the encrypting module 51 through the feedback loop when the
plaintext block data M; is encrypted subsequent to the plaintext block data
M;, and selects the module output block data T; stored in the memory 55 to
CA 02496539 2000-12-22
2I
supply to the encrypting module 51 through the feedback loop when the
plaintext block data M;.+, is not encrypted subsequent to the plaintext block
data M; but after any plaintext block data of the plaintext data N.
Fig. 17 explains the encryptor of the OFB mode shown in Fig. 16.
In Fig. 17, the operation of the CBC mode of Fig. 2 is changed to the
operation of the OFB mode, and the other operations are the same to the one
of Fig. 2.
Fig. 18 shows an encryptor of the CFB mode.
Compared with Fig. 47, the encryptor of Fig. 18 additionally includes
the memory 55. The memory 55 stores ciphertext block data C; output from
the XOR circuit 58.
Further, en encryption unit 52 is configured by the XOR circuit 58
and the encrypting module 51 using the encryption key K.
Fig. 18 shows an encryptor for encrypting plaintext block data M; (i =
1, 2, 3, ...) included in the plaintext data M and plaintext block data N~ (j
= 1,
2, 3, ...) included in the plaintext data N. The encryptor includes a
processing mechanism of the interrupt that receives the request to encrypt
the plaintext data N during the encryption of the plaintext data M before the
completion of encrypting the plaintext data M and the encrypting unit 52 for
encrypting the plaintext block data M; and outputting the ciphertext block
data C;. The encryptor further includes feedback loops 65 and 66 for feeding
back the module output block data T; supplied from the encrypting module
51 to the encrypting module through the feedback line 65, and the memory
55 provided in parallel with the feedback line 65 of the feedback loop, for
receiving a request to encrypt the plaintext data N and storing the module
CA 02496539 2000-12-22
28
output block data T; fed back when the plaintext block data M;+, is not
encrypted subsequent t,o the plaintext block data M; because the encryptor
starts a certain plainte~a block data of the plaintext data N. Yet further,
the
encryptor includes the selector 54 which selects the module output block
data T; fed back by the feedback line 65 of the feedback loop to supply to the
encrypting module 51 through the feedback loop when the plaintext block
data M; is encrypted subsequent to the plaintext block data M;, and selects
the module output bloc.l~ data T; stored in the memory 55 to supply to the
encrypting module 51 through the feedback loop when the plaintext block
data M;+, is not encrypted subsequent to the plaintext block data M; but after
a certain plaintext block: data of the plaintext data N.
Fig. 19 explains the encryptor of the OFB mode shown in Fig. 18.
In Fig. 19, the operation of the CBC mode of Fig. 2 is changed to the
operation of the OFB mode, and the other operations are the same to the one
of Fig. 2.
Fig. 20 shows a clecryptor of the CBC mode.
Compared with l?ig. 44, the decryptor of Fig. 20 additionally includes
the memory 75.
The memory 75 includes a register 76 and a switch 77.
Further, a decrypting unit 72 is configured by an XOR circuit 78 and
a decrypting module 71 using the key K.
A register 111 can be provided inside a selector 74.
The decryptor shown in Fig. 20, which decrypts the ciphertext block
data C; (i = l, 2, 3. ...) included in the ciphertext data C and the
ciphertext
block data N~ (j = 1. 2, 3. ...) included in the cipher text data D and
includes a
CA 02496539 2000-12-22
29
processing mechanism of the interrupt that receives a request to decrypt the
ciphertext data D during decrypting process of the ciphertext data C.
Further, the dec;ryptor shown in Fig. 20 further includes the
decrypting module 71 for outputting decrypted data of the ciphertext block
data C; as module output block data T;, feedback loops 85, 111, 82, and 86 for
feeding back the ciphertext block data C; to the decrypting unit 72 through
the feedback lines 85, 11:1, and 82 for decrypting ciphertext block data C;+,.
The decryptor further includes the memory 71 provided in parallel with the
feedback line 85, 111, 82, and 86 of the feedback loop and for receiving a
request for decrypting the ciphertext data D and storing the block data fed
back when the cipherte:xt block data C;+, is not decrypted subsequent to the
ciphertext block data C; because the decryptor starts decrypting any of
ciphertext block data of the ciphertext data D.
Further, the decryptor shown in Fig. 20 includes the selector 74
which selects the ciphertext block data C; fed back by the feedback lines 85,
111, 82 of the feedback :loop to supply to the encrypting unit 72 through the
feedback loop when the ciphertext block data C; is encrypted subsequent to
the ciphertext block data C;, and selects the ciphertext block data C; stored
in
the memory to supply to the encryption unit 72 through the feedback loop
when the ciphertext block data C;+, is not encrypted subsequent to the
ciphertext block data C; but after any of ciphertext block data of the
ciphertext data D.
"Feedback line" and "feedback loop" used in the above explanation of
Fig. 20 do not mean "feedback" which "inputs data output from itself'. Here,
"feedback" means to supply ciphertext block data C; again for decrypting the
CA 02496539 2000-12-22
ciphertext block data C;a., after decrypting the ciphertext block data C;.
Fig. 21 shows an operation procedure of the decryptor shown in Fig.
20.
When the interrupt IT is generated during decrypting the ciphertext
5 block data C; using the encryption key (also called decryption key) K,, the
ciphertext block data C; is stored in the register 76 of the memory ?5.
Thereafter, the ciphertext block data D; is decrypted using the encryption
key (also called decryption key) K~ into the plaintext block data N,. Then,
the ciphertext block data C, stored in the register 76 of the memory 75 is
10 read, the ciphertext block data C., is decrypted into the plaintext block
data
M~. The operation of the selector 74 is the same as one shown in Fig. 4.
Further, the operation o:f the switch 77 is the same as one shown in Fig. 5.
Fig. 22 shows the decryptor of the OFB mode.
The decryptor shown in Fig. 22, which decrypts the ciphertext block
15 data C; (i = 1, 2, 3, ...) included in the ciphertext data C and the
ciphertext
block data D~ (j = 1, 2, 3, ...) included in the ciphertext data D, includes a
processing mechanism of the interrupt that receives a request for decrypting
the ciphertext data D during decrypting the ciphertext data C at an arbitrary
timing point. The decryptor further includes the decrypting module 71 for
20 outputting decrypted data as module output block data T;, feedback loops
85,
86 for feeding back the module output block data T; to the decrypting module
71 through the feedback lines 85. The decryptor further includes the
memory 75 provided in par allel with the feedback line 85, of the feedback
loop, and for receiving a request to decrypt the cipher text data D and
storing
25 the module output block data T; fed back when the cipher text block data
C;+,
CA 02496539 2000-12-22
31
is not decrypted subsequent to the ciphertext block data C; because the
decryptor starts decrypting any of ciphertext block data of the ciphertext
data D. Further, the decryptor shown in Fig. 20 includes the selector 74
which selects the module output block data T; fed back by the feedback line
85 of the feedback loop to supply to the decrypting module 71 through the
feedback loop when the ciphertext block data C; is encrypted subsequent to
the ciphertext block data C;, and selects the module output block data T;
stored in the memory 75 t;o supply to the decrypting module 71 through the
feedback loop when the ciphertext block data C;+, is not encrypted
subsequent to the ciphertext block data C; but after any of ciphertext block
data of the ciphertext data D.
Fig. 23 explains the operation of the encryptor of the OFB mode
shown in Fig. 22.
The operation of Fig. 23 is the same with the one of the encryptor of
the CBC mode shown Fig. 21 except that the operation is performed in OFB
mode instead of the CBC mode.
Fig. 24 shows a dec;ryptor of the CFB mode.
A decrypting unit 72 is configured by the FOR circuit 78 and a
decrypting module 71.
Here, the register 111 can be provided inside the selector 74.
The decryptor shown in Fig. ~24, which decrypts the ciphertext block
data C; (i = 1, 2, 3, ...) included in the ciphertext data C and the
ciphertext
block data D~ (j = 1, 2, 3, ...) included in the ciphertext data D, includes a
processing mechanism of the intern upt that receives a request to decrypt the
cipher text data D duringv decrypting the ciphertext data C at an arbitrary
CA 02496539 2000-12-22
32
timing point. The decryptor further includes the decrypting module 71 for
outputting decrypted data as module output block data T;, feedback loops 85,
111, 82, 86 for feeding back the module output block data T; to the decrypting
module 71 through the feedback lines 85, 111, 82. The decryptor further
includes the memory 7 5 provided in parallel with the feedback line 85, 111,
82 of the feedback loop and for receiving a request to decrypt the ciphertext
data D and storing the module output block data T; fed back when the
ciphertext block data C;." is not decrypted subsequent to the ciphertext block
data C; because the decryptor starts decrypting any of ciphertext block data
of the ciphertext data L1. Further, the decryptor shown in Fig. 24 includes
the selector 74 which selects the module output block data T; fed back by the
feedback line 85 of the feedback loop to supply to the decrypting module 71
through the feedback loop when the ciphertext block data C; is encrypted
subsequent to the ciphertext block data G" and selects the module output
block data T; stored in the memory 75 to supply to the decrypting module 71
through the feedback loop when the ciphertext block data C;+, is not
encrypted subsequent ro the ciphertext block data C; but after any of
ciphertext block data of the ciphertext data D.
"Feedback line" and "feedback loop" used in the above explanation of
Fig. 24 do not mean "feedback" which "inputs data output from itself'. Here,
"feedback" means to supply ciphertext block data C; again for decrypting the
ciphertext block data C;+, after decrypting the ciphertext block data.
Fig. 25 explains an operation of the encryptor of the CFB mode
shown in Fig. 24.
In Fig. 25; the operation in the CBC mode shown in Fig. 21 is
CA 02496539 2000-12-22
33
replaced with the operation in the CFB mode, and the other operations are
the same as ones shown in Fig. 21.
Fig. 26 shows an improvement example of the encryptor of the CBC
mode shown in Fig. 1.
A selector 154 and a memory 155 are added to the encryptor of Fig.
26. Fig. 1 shows a case in which the key K, is supplied from the outside if
the interrupt IT is resolved, while the K, supplied from the outside is stored
and used again here.
The memory 155 includes a register 156 and a switch 157. The
switch 157 switches ignoring or inputting the encryption key K to the
register 156. This switching is performed by, for example, the interrupt IT.
When the interrupt IT is generated, the switch 157 is connected to E, and
when the interrupt IT i.s resolved, the switch 15I is connected to F. The
register 156 inputs the key K supplied through E and stores it. The key K
stored in the register l5fi is output to the selector 154. The selector 154
has
two inputs of A and C, out of which the selector 154 selects one. This
selection depends on the interrupt IT, which will be described later.
Fig. 27 shows an operation procedure of the encryptor shown in Fig.
26.
When the electric power of the encryptor is supplied, the inputs to
the selector 54 and the selector 154 are set to A, and the switch 57 and the
switch 157 are connected to E. Further, while a request to encrypt the
plaintext data N exists, the interrupt IT is generated and kept ON until the
request to encrypt the plaintext data I~T is resolved. Further, the plaintext
data M is to be encrypted using the key K,, and the plaintext data N is to be
CA 02496539 2000-12-22
34
encrypted using the key K,,. The keys K, and K~ are supplied to the
encrypting module 51.
At time T0, the key K, is supplied from the outside as the key KI.
As the switch 157 is connected to E, the key K, is stored in the register 156.
Then, the encrypting process for the plaintext block data M, is started.
When the plaintext block data M, is started at time T0, the selector 54 inputs
an initial value IV through A, and then the selector 54 is switched to B. At
time X during the encrypting process of the plaintext block data M, using the
key K,, it is assumed that the interrupt IT for requesting to encrypt the
plaintext block data N,. Until time T1, the ciphertext block data C,
becomes stored in the memory 55. Then, the key K., is supplied to the
encrypting module 51 from the outside as the key KI at time T1 due to the
generation of the interrupt IT. At time T1, .the input to the selector 54 is
set
to A. And at time T1, the switch 57 and the switch 157 are connected to F
Accordingly, the key K., is not stored in the register 156. After time T1, the
encryption of the plaintext block data N, is performed using the key K~, and
the ciphertext block data D, is output. At time Y, the encryption of the
plaintext block data N, is finished, and the interrupt IT is resolved. Due to
this resolution of the interrupt IT, at time T2, the input to the selector 54
is
switched to C, and the switch 57 is connected to E. Consequently, the key
K, is output to the selector 154 from the register 156 as the key KI,. and the
key K, is supplied to the encrypting module 51 from the selector 154 as the
key K,. Further, as the selector 54 is switched to C, the ciphertext block
data C, stored in the memory 55 is input for encrypting the plaintext block
data M~, the plaintext block data M~ is encrypted by the encrypting module
CA 02496539 2000-12-22
51 using the key K" and the ciphertext block data C~ is output. Before time
T3, the input to the selector 54 is switched to B, and when the plaintext
block
data M3 is encrypted, the ciphertext block data C~ fed back from the feedback
line 65 of the feedback loop is input, the plaintext block data M3 is
encrypted
5 by the encrypting module 51 using the key K,, and the ciphertext block data
C3 is output.
Further, before time T3, the input to the selector 154 is switched to
A.
An operation of the selector 154 will be described.
10 When the electric power is turned ON, the input to the selector 154 is
set to A. Further, also when the generation of the interrupt IT is detected,
the input is kept setting to A. Until the interrupt IT is resolved, the
selector
154 operates with setting its input to A. When the resolution of the
interrupt IT is detected, the selector 154 sets the input to C. Due to setting
15 the input to C, the key K, stored in the memory 55 is input to the
encrypting
module 51 as the key K. When the encryption using the key input from C is
started, the selector sets the input to A.
As described above, the selector 154 can be switched based on the
generation of the interrupt IT.
20 Next, an operation of processing the interrupt of the switch 157 will
be explained.
When the electric power is turned ON, and at the first encrypting
process of the plaintext data M, the switch 157 is connected to E, and the key
K, for the plaintext M is stored in the register 156. And when the interrupt
25 IT is generated at time Vii, the switch 15 7 is connected to F from E at
time T,;
CA 02496539 2000-12-22
36
and the key K~ for the plaintext N is ignored. Further, when the resolution
of the interrupt IT is detected at time Y, the switch 157 is connected to E
from F at time T2. In this way, the switch 157 ignores the key K~ for the
plaintext data N from the genes ation until the resolution of the interrupt
IT.
Accordingly, the key K, for the plaintext data M is kept storing in the
register 156 of the memory 155.
Fig. 28 shows a configuration of the decryptor shown in Fig. 20 when
the key K, is stored to be reused.
Fig. 28 shows a case in which a selector 174 and a memory 175 are
added to the decryptor of Fig. 20. The operations of the selector 174 and the
memory 175 are the same as the ones of the selector 154 and the memory 155
shown in Fig. 26.
The memory 55 and the memory 155 are examples of the memory for
storing the status of the encryptor when the interrupt IT is generated. In
this way, the status of the encrypting process is stored in the memory 55 and
the memory 155, which enables the encryptor to return to the status of
encrypting a certain data even when the encryption of another data is
performed during the certain data is encrypted. Namely, using the data
stored in the memory 55 and the key K stored in the memory 155, the status
of the encryptor can be returned to the identical status when encryption is
interrupted, and the interrupted encrypting process can be continued.
The memory 155 and the memory 175 can be configured as
identically to the memory 55 shown in Figs. 6 and 8. Or, the key K, can be
stored by adding the configuration such as ones shown in Figs. 26 and 28 to
Figs. 16; 18, 22, and 24.
CA 02496539 2000-12-22
37
Further, since the memories 55 and 155 shown in Fig. 26 operate the
same, these memories can be integrated into one memory.
As has been discussed, the decryptor in relation to the present
embodiment performs decryption of the first processing data (ciphertext data
C) including at least one block data C; (i = 1, 2, 3, ..., m) and the second
processing data (ciphertext data D) including at least one block data D~ (J =
1,
2, 3, ... , n). The decryptor includes the memory 75 storing the status of
decrypting process. The decryptor starts decrypting process of an initial
block data D, of the second processing data before the completion of the
decrypting process of all block data (C, through Cn) of the first processing
data. When the decryptor starts the decrypting process of the initial block
data D, of the second processing data, the decryptor makes the above
memory store the decrypting status of the first processing data, and when
the decryptor restarts decrypting the first processing data, the status of the
decryptor is returned to the decrypting status of the decryptor stored in the
memory 75 and the decryptor restarts the decrypting process of the first
processing data.
Further, the decryptor restarts the decrypting process of the first
processing data before the completion of all block data (D, through D") of the
second processing data, and the memory 74 stores the decrypting status of
the second processing data when the decryptor restarts the decrypting
process of the first processing data. When the decryptor restarts the
decrypting process of the second processing data, the status of the decryptor
is returned to the decrypting status of the second processing data stored in
the memory and the decryptor restarts the decrypting process of the second
CA 02496539 2000-12-22
38
processing data.
Here, the status of the encrypting process is, for example,
Encrypted block data C; (and the key K,) in case of the CBC mode
shown in Fig. 1,
Module output data T; (and the key K,) in case of the OFB mode
shown in Fig. 16, and
Encrypted block data C; (and the key K,) in case of the CFB mode
shown in Fig. 18. The decrypting status is, for example,
Encrypted block data C; (and the key K,) in case of the CBC mode
shown in Fig. 20,
Module output data T; (and the key K,) in case of the OFB mode
shown in Fig. 22, and
Encrypted block data C; (and the key K,) in case of the CFB mode
shown in Fig. 24.
In the above description, the encryptor and the decryptor have been
explained in cases of three modes, respectively. The three modes are only
examples, the present embodiment can be applied to the encryptor and the
decryptor in other mode such as improved mode or transformed mode. In
particular, the characteristics of the embodiment is that in the
encrypting/decrypting method, in which the block data C;, M;, or T; generated
at the encrypting/decrypting time of the previous data are used for the
encrypting/decrypting process of the next block data M;+, or C;+, as the
feedback data, the memory 55 is provided for storing the status of the
encrypting/decrypting process, so that the status of the encryptorldecryptor
can be returned back to the original status using the block data C;, M;, or T;
CA 02496539 2000-12-22
39
after encrypting/decrypl;ing process of another piece of data. Accordingly,
which encrypting/decrypting mode is used is out of question.
Here, instead of the interrupt IT, the request for encryption using
other mechanism such as poling system or token obtainment system can be
received, and an interactive parallel processing of at least two
encrypting/decrypting processes can be performed.
Further, in the above embodiment, the encryption key K is used for
encrypting/decrypting process, however, the embodiment can be applied to
the encrypting/decrypting process without using the encryption key.
Embodiment 2.
In the following embodiment, another case will be explained, in
which the encryptor performs a confidentiality process and a data integrity
ensuring process.
The data confidentiality process means to encrypt data in order to
make the data meaningless even when the data is wiretapped or stolen.
Further, the data integrity ensuring process means to ensure that the data is
not replaced by anybody. In case of transferring data, the integrity of data
sometimes needs to be ensured as well as performing the confidentiality
process of data. The dai;a confidentiality process is performed by encrypting
the data. The data integrity ensuring process is performed by appending a
MAC (Message Authentication Code) to the last bit of the data and checking
the MAC to detect the tempering.
Fig. 29 shows a case in which an encrypting unit 100 of the OFB
mode performs the confidentiality process; and a MAC generator 200 of the
CA 02496539 2000-12-22
CBC mode generates the MAC.
Fig. 29 shows the encryptor which encrypts the plaintext data
including at least one plaintext block data using the encrypting module and
generates the MAC for ensuring the integrity of the ciphertext data. The
5 encryptor includes an encrypting unit 100 having a first feedback loop 65
which feeds back the module output block data T; supplied from the
encrypting module 51 at encrypting the plaintext block data by the
encrypting module 51 to the encrypting module 51. The encrypting unit 100
inputs the plaintext block data, feeds back module output block data T; using
10 the first feedback loop 65 to perform the encrypting process to output
ciphertext block data C;. The encryptor includes a MAC generator 200
having a second feedback loop 66 which feeds back a computed intermediate
MAC; result T;. The MAC generator 200 inputs the ciphertext block data C;
at every output of the ciphertext block data C; from the encrypting unit 100,
15 computes the MAC, makes the computed intermediate MAC result T;
feedback using the second feedback loop 66, and generates a MAC P to
ensure the integrity of the ciphertext data.
Fig. 30 shows an operation procedure of the encryptor shown in Fig.
29.
20 The plaintext block data M, is first encrypted into the ciphertext
block data C,. Next, the plaintext block data M~ is input to be encrypted
into the ciphertext block data C.,. Simultaneously to the encryption of the
plaintext block data M,, the ciphertext block data C, is input and the
computation of the MAC is started. Between time T1 and time T2, the
25 encrypting process of the plaintext block data M~ and the computation of
the
CA 02496539 2000-12-22
~1
MAC based on the ciphertext block data C, are performed. Between time
T2 and time T3, the encrypting process of the plaintext block data M3 and the
computation of the MAC based on the ciphertext block data C,, are performed.
At time T3, the computation of the MAC based on the ciphertext block data
C3 is performed and the MAC P is output.
The configuration of Fig. 29 is characterized by that the ciphertext
block data C; output from the XOR circuit 58 is input to the XOR circuit 59
by a feed line 69. The feed line 69 combines the encrypting processes of the
OFB mode and the CBC mode, so that the confidentiality process and the
integrity ensuring process are performed by pipeline processing. In case of
Fig. 52, the process at time T6 requires much processing time, however, in
case of Fig. 30, the procE~ssing is finished at time T4, which shows a high
speed processing has been done.
Fig. 31 is a flow diagram showing the operation of the encryptor
shown in Fig. 29.
At S51, a block data counter i is initialized to 1. S52 shows the
operation of the encrypting unit 100. The encrypting unit 100 inputs the
plaintext block data M;, encrypts the plaintext data M; into the ciphertext
block data C;, and outputs the ciphertext block data C;. S53 shows the
operation of the MAC generator 200. The MAC generator 200 inputs and
encrypts the ciphertext block data C; and computes the MAC. S54 checks if
the block data counter i indicates the last block data n. When the counter
doesn't, the block data counter i is incremented at 555, and the operation is
returned back to the process of 552. NamelS-, the processes of the
encrypting unit 100 and the NIAC generator 200 are repeated. VVhen it is
CA 02496539 2000-12-22
4 '?
detected at S54 that the process of the last block data is completed, the last
MAC computed at S53 becomes the final MAC, and the final MAC is
appended to the last bit. of the ciphertext block data C; at 556. As shown in
Fig. 31, at every genes ation of the ciphertext block data C; by the
encrypting
unit 100, the MAC generator 200 inputs the ciphertext block data C; to
compute the MAC, which enables the pipeline processing at a high speed.
Fig. 32 shows a configuration combining the encrypting unit 100 and
the MAC generator 200 shown in Fig. 29. That is, the encrypting module 51
is shared by the encrypting unit 100 and the MAC generator 200, and the
XOR circuit is used as the XOR circuit 58 of the encrypting unit 100 and the
XOR circuit 59 of the MAC generator 200. Further, the feedback line is
used as both the feedback line 65 of the encrypting unit 100 and the feedback
line 66 of the MAC gener<~tor 200.
A first selector 61 selects an initial value IV at starting time of the
confidentiality process. A second selector selects the initial value IV at the
starting time of the integrity ensuring process. A third selector 63
alternately selects the confidentiality process and the integrity ensuring
process. The confidentiality process can be performed by setting the input
of the third selector to E. Further, the integrity ensuring process can be
performed by setting the input of the third selector to F.
A memory 93 stores the module output data T; output from the
encrypting module 51 using the encryption key K. The memory 93 includes
an input switch 96, an output switch 9 l, a fir st register 98, and a second
register 99. The input switch 96 and the output switch 9 r are synchronized
v~~ith switching the third selector 63. At every switching of the third
selector
CA 02496539 2000-12-22
43
63, both the input switch 96 and the output switch 9'7 are switched.
Fig. 33 shows an operation procedure of the encryptor shown in Fig.
32.
Between time 'r0 and time T1, the confidentiality process of the
plaintext block data M, is performed. The module output data generated
. during the confidentiality process is stored in the first register 98.
Between
time T1 and time T2, l;he MAC is computed based on the ciphertext block
data C,. The computed intermediate MAC result generated by the integrity
ensuring process is stored in the second register 99. Next, between time T2
and time T3, the confidentiality process of the plaintext block data M~ is
performed based on the module output data stored in the first register 98
and the plaintext block data M~. Then, between time T3 and time T4, the
computed intermediate MAC result stored in the second register 99 and the
ciphertext block data C., are input and the MAC is computed. By repeating
these operations, the confidentiality process and the integrity ensuring
process are completed and the ciphertext data and the MAC P are output.
In case of Fig. 33, the process is finished at time T6 and the processing time
is not reduced. However, as shown in Fig. 32, the encrypting module 51
using the encryption key K, the xOR circuit 58, and the feedback line 6'l, 68
(feedback loop) are shared by the encrypting unit and the MAC genes ator, so
that the circuit scale can be reduced.
Fig. 34 shows a decryptor including a decrypting unit 300 of the OFB
mode and a MAC generator 400 of the CBC mode.
The MAC generator 400 is configured the same as the MAC
generator 200.
CA 02496539 2000-12-22
4~
Fig. 34 shows the decryptor which decrypts the ciphertext data
including at least one ciphertext block data into the plaintext data and
generates the MAC for ensuring the integrity of the ciphertext data. The
decryptor includes a dec;rypting unit 300 having a first feedback loop 65
which feeds back the module output block data T; generated at decrypting
process of the ciphertext block data C; using the decrypting module 71. The
decrypting unit 300 inputs the ciphertext block data C; makes the module
output block data T; feedback by the first feedback loop 65 to decrypt and
outputs the plaintext block data M;. The decryptor further includes a MAC
generator 400 having a second feedback loop 66 which feeds back the
computed intermediate NIAC result T;. The MAC generator 400 inputs the
same ciphertext block data with the ciphertext block data C; input to the
decrypting unit 300, performs the MAC computation to output the computed
intermediate MAC result, makes the second feedback loop 66 feedback the
computed intermediate MAC result T;, and generates the MAC fa for
ensuring the integrity of the ciphertext data.
The ciphertext block data C; is input to the XOR circuit 78 of the
decrypting unit 300, and at the same time, the ciphertext block data C; is
input to the MAC generator 400 by the feed line 69. By this configuration,
the processes of the decrypting unit 300 and the MAC generator 400 are
performed simultaneously, so that the processing speed can be increased.
Fig. 35 shows a configuration to which the decrypting unit 300 and
the MAC generator 400 of the decryptor shown in Fig. 34 are integrated.
Fig. 35 shows a case in which the decrypting module 71 and the
feedback lines 8 r, 88 (feedback loop) are shared.
CA 02496539 2000-12-22
~5
A first selector 81 selects the initial value IV at starting time of the
decrypting process. A second selector 82 selects the initial value IV at
starting time of the integrity ensuring process. A third selector 83
alternately selects the decrypting process and the integrity ensuring process.
The decryption can be performed by setting the input of the third selector 83
to E. Further, the integrity ensuring process can be performed by setting
the input of the third selector 83 to F.
The memory 93 stores the module output data T; output from the
encrypting module 51 using the encryption key K. The memory 93 includes
an input switch 96, an output switch 97, a first register 98, and a second
register 99. The input switch 96 and the output switch 97 are synchronized
to switching of the third selector 83. At every switching of the third
selector
83, the input switch 96 and the output switch 9 7 are also switched.
Fig. 36 shows an operation procedure of the decryptor shown in Fig.
35.
The decryptor inputs the ciphertext data and the MAC P.
Between time TO and time T1, the ciphertext block data C; is
decrypted and the ciphertext block data C; is stored in the register 111. The
module output data generated during the decrypting process is stored in the
regisi:er 98. Between time T1 and time T2, the MAC is computed based on
the ciphertext block data C; stored in the register 111. The computed
intermediate MAC result generated during the integrity ensuring process is
stored in the second register 99. Next, between time T2 and time T3, the
ciphertext block data C~ is stored in the register 111, the decrypting process
of the plaintext block data M~ is performed based on the module output data
CA 02496539 2000-12-22
46
stored in the first register 98 and the cipher text block data C.,. Then,
between time T3 and tirr.~e T4, the computed intermediate MAC result stored
in the second register 99 and the ciphertext block data C~ stored in the
register 111 are input and the MAC is computed. By repeating these
operations, the plaintext; data and the MAC Q are output. The MAC Q is
compared with the MAC P.. If the MAC P matches the MAC Q, the integrity
of the data can be ensured. Thus, the decrypting process and the integrity
ensuring process are completed.
Fig. 3? shows a configuration in which the encrypting unit 100 of the
CBC mode is used instead of the encrypting unit 100 of the OFB mode shown
in Fig. 29.
Fig. 3? shows the encryptor which encrypts the plaintext data
including at least one plaintext block data using the encrypting module and
generates the MAC for ensuring the integrity' of the ciphertext data. The
encryptor includes an encrypting unit 100 having a first feedback loop 65
which feeds back the ciphertext block data C; output from the encrypting
module 51 at encrypting time of the plaintext block data by the encrypting
unit 52. The encrypting unit 100 inputs the plaintext block data M;, makes
the ciphertext block data C; feedback using the first feedback loop 65 to
perform the encrypting process, and outputs the ciphertext block data C;.
The encryptor further includes a MAC generator .200 having a second
feedback loop 66 which feeds back a computed intermediate MAC result T;.
The MAC generator 200, inputs the ciphertext block data C; at every output
of the ciphertext block data C; from the encrypting unit 100, computes the
MAC, makes the computed intermediate MAC result T; feedback using the
CA 02496539 2000-12-22
4i
second feedback loop 66, and generates a MAC P to ensure the integrity of
the ciphertext data.
Fig. 38 shows a configuration in which the decrypting unit 300 of the
CBC mode is provided instead of the decrypting unit 300 of the OFB mode
shown in Fig. 34.
Fig. 38 shows the decryptor which decrypts the ciphertext data
including at least one ciphertext block data into the plaintext data and
generates the MAC for ensuring the integrity of the ciphertext data. The
decryptor includes a decrypting unit 300 having a first feedback loops 85, 82
for feeding back the ciphertext block data C;, and the decrypting unit 300
inputs the ciphertext block data C; and makes the ciphertext block data C;
feedback by the first feedback loops 85, 82 to decrypt, and outputs the
plaintext block data M;. The decryptor further includes a MAC generator
400 having a second feedback loop 66 for feeding back the computed
intermediate MAC result T;, and the MAC generator 400 inputs the
ciphertext block data C; being identical to the ciphertext block data C; input
to the decrypting unit 300, computes the MAC, outputs the computed
intermediate MAC result 'r;, makes the computed intermediate MAC result
T; feedback by the second feedback loop, and generates the MAC for ensuring
the integrity of the ciphertext data.
As described above, Figs. 29 and 37 show the encryptors, each of
which includes the encrypting unit inputting data to encrypt and outputting
the data and the MAC generator inputting the encrypted data output from
the encrypting unit and generating the MAC for ensuring the integrity of the
ciphertext data, ~~herein 'the MAC generator starts generating the NL~.C
CA 02496539 2005-11-23
48
before the encryption of the data is completed by the encrypting unit.
Further, Figs. 34 and 38 show the decryptors, each of which includes
the decrypting unit inputting the data to decrypt and outputting the data
and the MAC generator inputting the data input by the decrypting unit and
generating the MAC for ensuring the integrity of the ciphertext data,
wherein the MAC generator starts generating the MAC before the
decryption of the data is completed by the decrypting unit.
The encrypting unit 100 or the decrypting unit 300 of the OFB mode,
which are not shown in the figures, can be used in the above
encryptor/decryptor.
The MAC generator 200 of the OFB mode or the CFB mode, which
are not shown in the figures, can be used in the above encryptor/decryptor.
Fig. 39 shows a configuration of the encrypting module S1 or the
decrypting module 71.
The encrypting module 51 includes a key scheduler 511 and a data
randomizer 512. The key scheduler 511 inputs one key K to generate n
number of extended keys ExtK, through ExtK". The data randomizer 512
generates a random number using a function F and an XOR circuit. The
function F inputs the extended key and performs non-linear transformation
of the data.
In the encrypting module 51 of the above encryptor, the block cipher
algorithm such as:
(1) DES (Data Encryption Standard),
(2) MISTY, the block cipher algorithm disclosed by the International Patent
1'ablication No. W097/09705,
CA 02496539 2000-12-22
49
(3) hASUMI, 64-bit block cipher developed based on the block cipher
algorithm MISTZ; which was determined to be applied to the International
standard cipher for next generation cellular phone (IMT2000) (more in detail,
please visit http://www.i3gpp.org/About_3GPP/3gpp.htm), or
(4) Camellia, the block cipher algorithm disclosed in the Japanese patent
application No. 2000-6467.4 (filed on March 9, 2000).
Further, in the decrypting module of the decryptor, the block cipher
algorithm such as DES, MISTY, KASUMI, or Camellia can be applied.
Fig. 40 shows an implementation form of the encryptor or the
decryptor.
Fig. 40 shows a case in which the encryptor and the decryptor are
installed in FPGA, IC, or LSI. Namely, the above-mentioned encryptor and
decryptor can be implemented by the hardware. Further, the encryptor and
the decryptor can be implemented by a printed circuit board, which is not
shown in the figure.
Fig. 41 shows a case in which the encryptor and the decryptor are
implemented by the software.
The above encryptor can be implemented by a cipher program 47.
The cipher program 4 7 is stored in ROM (Read Only Memory) 42 (an
example of the storage). The cipher program 47 can be stored in other kind
of storage such as RAM (Random Access Memory), a flexible disk, or a fixed
disk. Further, the cipher program 47 can be downloaded from a server
computer. The cipher X>rogram 4I operates as a sub-routine. The cipher
program 47 is called from an application program 46 stored in the RAM 45
b~= a sub-routine call and t;he cipher program 4 7 is executed. Or, the cipher
CA 02496539 2000-12-22
program 4 7 can be activated by generation of an interrupt received by the
interrupt control unit 43. The memory 55 can be a part of the R.AM 45.
The application program 46 and the cipher program 47 are programs
executed by the CPU.
5 Fig. 42 shows a mechanism by which the application program 46
calls the cipher program 47.
The application program 46 calls the cipher program 47 using the
key K, the initial value IV, the plaintext data M, and the ciphertext data C
as
parameters. The cipher program 47 inputs the key K, the initial value IV,
20 and the plaintext data M and returns the ciphertext data C. When the
cipher program 47 and the decipher program are the same, the cipher
program is called using the key K, the initial value IV, the ciphertext data
C,
and the plaintext data M as parameters.
The cipher program 47 can be implemented by a digital signal
15 processor and a program which is read and executed by the digital signal
processor. Namely, the cipher program 4 7 can be implemented by the
combination of the hardware and the software.
Figs. 40, 41, and 42 mainly explain cases for the encryptor, however,
the decryptor can be implemented in the same manner.
20 The encryptor and the decryptor shown in Figs. 40 and 41 can be
installed in an electronic device. For example, the encryptor and the
decryptor can be installed in all kinds of the electronic devices such as a
personal computer, a facsimile machine, a cellular phone, a video camera, a
digital camera, a TV camera. In particular, the characteristics of the
25 present embodiment can be effectively drawn in case of
CA 02496539 2000-12-22
51
encrypting/decrypting the data from plural channels. Or the application of
the embodiment is effective when plural pieces of data are received from
plural users to be decrypted, when plural pieces of data are generated from
plural users at random and the data should be encrypted in real time.
Namely, the encryptor and the decryptor of the embodiment are really
effective when the number of the devices for encrypting/decrypting is small
compared with the number of pieces of data to be encrypted/decrypted. For
example, the encryptor and the decryptor are very effective for the server
computer which requires to support many client computers, a base station or
l0 a line controller which requires to collect data from lots of cellular
phones.
Instead of parallel processing of encrypting processes and decrypting
processes, the encrypting process and the decrypting process can be
performed in parallel.
Further, the above explanation shows a case of the combination of
the encrypting unit (or the decrypting unit) of the OFB mode and the MAC
generator of the CBC mode, however, any combination of modes can be used
such as the OFB mode, the CBC mode, the CFB mode; improved mode of
these modes, and so on.
Further, the above explanation shows a case in which the MAC
generator performs encryption using the encryption key K, however, the
MAC generator can perform the data scrambling, the data calculation, or
other data processing.
Industrial applicability
As has been described, according to the preferred embodiment of the
CA 02496539 2000-12-22
52
present invention, the encrypting process of the plaintext data N can be
started during the encrypting process of the plaintext data M. Further, the
decrypting process of the ciphertext data D can be started during the
decrypting process of the ciphertext data C.
Further, according to the preferred embodiment of the present
invention, priorities can be assigned to the data to be encrypted/decrypted, a
high speed processing can be performed based on the priorities of the data.
Yet further, according to the preferred embodiment of the present
invention, the confidentiality process and the integrity ensuring process can
be performed in parallel, which enables a high speed processing. Further,
the confidentiality process and the integrity ensuring process can be
performed by one integrated hardware.