Note: Descriptions are shown in the official language in which they were submitted.
CA 02505051 1997-10-O1
FAST EQUALIZER TRAINING AND FRAM: SYNCHRONIZATION
ALGORITHMS FOR DISCRETE MULTI-TONE (DMT) SYSTEM
This is a divisional application of Canadian Patent
No. 2,217,073 filed October 1, 1997.
FIELD OF THE INVENTION
The present invention is related to multimode
digital modems, and more particularly, to systems
employing, methods for and hardware for multimode digital
modems.
BACKGROUND OF THE INVENTION
A conventional voice-band modem can connect computer
users end-to-end through the Public Switched Telephone
Network (PSTN). However, the transmission throughput of
a voice-band modem is limited to below about 40 Kbps due
to the 3.5 KHz bandwidth enforced by bandpass filters and
codes at the PSTN interface points. On the other hand the
twisted-pair telephone subscriber loop of a computer user
has a much wider usable bandwidth. Depending on the
length of the subscriber loop, the bandwidth at a loss of
50 dB can be as wide as 1 MHz. Transmission systems
based on the local subscriber loops are generally called
Digital Subscriber Lines (DSL).
As consumer demand for interactive electronic access
to entertainment (e. g. video-on-demand) and information
(Internet) in digital format has increased, this demand
has effectively exceeded the capabilities of conventional
voice-band modems. In response, various delivery
- 1 -
CA 02505051 1997-10-O1
approaches have been proposed, such as optical fiber
links to every home, direct satellite transmission, and
wideband coaxial cable. However, these approaches are
often too costly, and cheaper alternatives have emerged,
such as the cable modem which uses existing coaxial cable
connections to homes and various high bit rate digital
subscriber line (DSL) modems which use the existing
twisted-pair of copper wires connecting a home to the
telephone company central office (CO).
Several digital subscriber lines (DSL) technologies
have been developed for different applications. The
original 2B1Q Digital Subscriber Line technology has been
used as the ISDN Basic Rate Access channel U-interface.
The High-bit-rate digital subscriber lines (HDSL)
technology has been used as the repeaterless T1 service.
An example of prior art use of DSL techniques is the
Asymmetrical Digital Subscriber Line (ADSL) signaling for the
telephone loop that has been defined by standards bodies as
a communication system specification that provides a
low-rate data stream from the residence to the CO
- la -
CA 02505051 1997-10-O1
(upstream), and a high-rate data stream from the CO to the residence
(downstream). The ADSL standard provides for operation without
affecting
conventional voice, telephone communications, eg. plain old telephone
service (POTS). The ADSL upstream channel only provides simple
control
~ functions or low-rate data transfers. The high-rate downstream
channel
provides a much higher throughput. This asymmetrical information
flow is
desirable for applications such as video-on-demand (VOD).
ADSL modems are typically installed in pairs, with one of the
modems
installed in a home and the other in the telephone company's
central
office servicing that home. The pair of ADSL modems are connected
to the
opposite ends of the same twisted-pair and each modem can only
communicate
with the modem at the other end of the twisted-pair; the central
office
will have a direct connection from'its ADSL modem to the service
provided
(e.g., movies, Internet, etc.). Figure 2a heuristically illustrates
an
ADSL modem (Figure 2a uses "DSL" rather than "ADSL" for the modem)
installed in the central office and one in the consumer's home,
either a
personal computer or a TV set-top box. Because an ADSL modem
operates at
frequencies higher than the voice-band frequencies, an ADSL modem
may
operate simultaneously with a voice-band modem or a telephone
conversation.
A typical ADSL-based system includes a server located at the
CO
capable of providing movies or other data-intensive content,
and a set-
top-box at the residence that can receive and reassemble the
data as well
as send control information back to the CO. Meaningful display
or use of
the downstream content typically requires a sustained data rate
through
the modem. Due to the sustained data rate requirements, ADSL
systems are
primarily designed to function under certain operating conditions
and only
at certain rates. If a subscriber line meets the quality requirements,
the ADSL modem can function, otherwise new line equipment must
be
t
improved.
installed, or line quality must be
In particular, the ANSI standard ADSL calls for transmission
of up
to 6 million bits-per-second (Mbps) to a home (downstream) over
existing
twisted-pair and also for receipt of up to 640 thousand bits
per second
(Kbps) from the home (upstream).
An ADSL modem differs in several respects from the voice-band
modems
currently being used for digital communication over the telephone
system.
A voice-band modem in a home essentially converts digital bits
to
modulated tones in the voice-band (30 Hz to 3.3 KHz), and thus
the signals
can be transmitted as though they were just ordinary speech signals
generated in a telephone set. The voice-band modem in the receiving
home
then recovers the digital bits from the received signal. The current ITU
V-series voice-band modem standards (s.g. V.32 and V.34) call for
transmission at bit rates of up to 33.6 Kbps; even these rates are far too
- 2 -
CA 02505051 1997-10-O1
slow for real-time video and too slow for Internet graphics. In
contrast,
an ADSL modem operates in a frequency range that is higher than
the voice-
band; this permits higher data rates. However, the twisted-pair
subscriber line has distortion and losses which increase with
frequency
and line length; thus the ADSL standard data rate is determined
by a
maximum achievable rate for a length of subscriber lines, e.g.
9,000 feet
(9 kft) for 26 gauge lines, or 12 kft for 24 gauge lines.
voice-band modem data speeds are limited by at least the following
factors: 1) the sampling rate of the line cards in the central
office is
only 8 KHz: 2) the low bit resolution of the A/D and D/A converters
used
on the line cards reduces dynamic range; and 3) the length of
the
subscriber line (twisted-pair) and.any associated electrical impairments.
Although an ADSL modem avoids the first two factors, it also suffers
from
subscriber line length limitations and electrical impairments.
Figure 4c
illustrates how the capacity of a subscriber line decreases with
increasing line length for the two existing wire sizes. A similar
capacity decrease with length applies to any type of twisted-pair
subscriber line modem.
Figure 4a shows in block format a simple ADSL modem Whose transmit
hardware 30 includes the bit encoder 36, inverse fast Fourier
transform
38, P/S 40, digital-to-analog converter 42. filter and line driver
44 for
transmission and transformer 46. The receive portion 32 includes
a
transformer and filter 48, analog-to-digital converter 50, an
equalizer
for line distortion compensation 52, S/P 54, fast Fourier transform
56,
and bit decoder 58. An echo cancellation circuit from the transmission
portion to the reception portion may be included to suppress signal
leakage. The ADSL standard uses discrete multitone (DMT) with
the DMT
spectrum divided into 256 4-KHz carrier bands and a quadrature
amplitude
modulation (QAM) type of constellation is used to load a variable
number
of bits onto each carrier band independently of the other carrier
bands.
The number of bits 'per carrier is determined during a training
period when a test signal is transmitted through the subscriber
line to
the receiving modem. Based on the measured signal-to-noise ratio
of the
received signal, the receiving modem determines the optimal bit
allocation, placing more bits on the more robust carrier bands,
and
returns that information back to the transmitting modem.
The modulation of the coded bits is performed very efficiently
by
using a 512-point inverse fast Fourier transform to convert the
frequency
domain coded bits into a time domain signal which is put on the
twisted-
pair by a D/A converter using a sample rate of 2.048 Mhz (4x512).
The
receiving ADSL modem samples the signal and recovers the coded
bits with
a fast Fourier transform.
- 3 -
CA 02505051 1997-10-O1
Discrete multi-tone (DMT) has been chosen as the line code for
the
ADSL standard. A typical DMT system utilizes a transmitter inverse
FFT
and a receiver forward FFT. Ideally, the channel frequency distortion
can
be corrected by a frequency domain equalizer following the receiver
FFT.
~ However, the delay spread of the channel in the beginning of
the receiver
FFT block contains inter-symbol interference from the previous
block. As
this interference is independent of the current block of data,
it can not.
be canceled just by the frequency domain equalizer. The typical
solution
adds a block of prefix data in front of the FFT data block on
the
transmitter side before the block of FFT data is sent to the D/A.
The
prefix data is the repeat copy of the last section of FFT data
block.
On the receiver side, the 'received signal is windowed to eliminate
the cyclic prefix data. If the length of the channel impulse response
is
shorter than the prefix length, inter-symbol interference from
the
previous FFT data block is completely eliminated.' Frequency domain
equalizer techniques are then applied to remove intra-symbol interface
among DMT subchannels. However, since the channel impulse response
varies
on a case by case basis, there i$ no guarantee that the length
of the
impulse response is shorter than the prefix length. An adaptive
time
domain equalizer is typically required to shorten the length of
the
channel response within the prefix length.
Time domain equalizer training procedures have been studied
previously, Equalizer Training Algorithms for Multicarrier Modulation
Systems, J. S. Chow, J. M. Ciofi, and J.A.C. Hingham, 1993 International
2f Conference on Communications, pages 761-765, Geneva, (May'1993)
and the
corresponding training sequence has been specified in ADSL standard
and
Recommended Training Sequence for Time-domain Equalizers (TQE)
with DMT,
J. S. Chow, J. M. Cioffi, and J.A.C. Bingham, ANSI T1E1.4 Committee
Contribution number 93-086. ,
The following patents are related to DMT modems: U.S.Patent No.
5,400,322 relates to bit allocation in the multicarrier channels;
U.S.Patent No. 5,479,447 relates to bandwidth optimization; U.S.Patent
No.
5,317,596 relates to echo cancellation; and U.S.Patent No. 5,285,474
relates to equalizers.
Alternative DSL modem proposals use line codes other than DMT,
such
as QAM, PAM, and -carrierless AM/PM (CAP). Indeed, ISDN uses a
2bit-
lquaternary (2B1Q) four level symbol amplitude modulation of a
carrier of
160 KHz or higher to provide more data channels.
CAP line codes typically use in-phase and quadrature multilevel
signals which are filtered by orthogonal passband filters and
then
converted to analog for transmission. Figure 4b shows a block
diagram for
the transmitter 321 and receiver 325 of a DSL modem using the
CAP line
code and including both an equalizer 750 and echo cancellation
327.
- 4 -
CA 02505051 1997-10-O1
The following patents are related to CAP modems: U.S.Patent No.
4,944,992 relates to multidimensional passband transmission;
U.S.Patent
No. 9,682,358 relates to echo cancellation; and 5,052,000 relates
to
equalizers.
Modems using CAP or DMT, or other line codes, essentially have
three
hardware sections: (i) an analog front end to convert the analog
signals
on the subscriber line into digital signals and convert digital
signals,
for transmission on the subscriber line into analog signals,
(ii) digital
signal processing circuitry to convert the digital signals into
an
information bitstream and optionally provide error correction,
echo
cancellation, and line equalization, and (iii) a host interface
between
the information bitstream and it's~'source/destination.
However, these DSL modems have problems including: 1) higher
bit
rates for video that cause them to be complicated and expensive:
2) their
bit rates are optimized for a fixed distance, making them inefficient
for
short subscriber loops and unusable for long subscriber loops:
and 3)
either DMT or CAP operates better for given different conditions
(e. g.
noise, etc.) that may or may nr~t,be present in a particular
subscriber
loop to which the DSL modem is connected.
However, these and other shortcomings of the prior art are overcome
by the present invention.
- 5 -
CA 02505051 1997-10-O1
SZJMMARY OF THE INHENTION
The present invention provides a new high speed modem for use
on
standard telephone twisted-pair lines at lengths of up to 21,000
ft. This
new modem will be referred to as MDSL, mid-band digital subscriber
line.
The MDSL modem of the present invention makes use of frequency
division
multiplexing (FDM) to separate the downstream and upstream transmitted
signals. Although the modulation scheme for MDSL can be arbitrary,
two
specific modulation schemes that may be employed are QAM/CAP and
Discrete
Multitone (DMT). A startup procedure for achieving synchronization
between the MDSL modem of the present invention at the central
office (CO)
and the MDSL modem at the remote user (RU) end is provided..as
part of the
present invention.
One of the specific modulation schemes chosen for one implementation
of MDSL is Carrierless AM/PM (CAP). CAP does not make use of a
separate
tone for synchronization. Synchronization is achieved using the
transmitted data signal directly. At startup, a special data sequence
is
used to train equalizers in the. CAP receiver before real data
is
., transmitted.
The present invention provides a modem which supports both voice-
band and above voice-band (DSL) functionality using preselected
common
circuitry. Preferred embodiments use a DSP to run either voice-band
or
above-voiced-band modem software in combination with, either separate
or
combined analog front ends, and a common host interface (either
serial or
parallel). The same internal components may be employed for either
the
voice-band or the above-voice-band modem, and the modem may have
an
integral splitter to separate the voice-band for use by a telephone
set.
The present invention provides a programmable Digital Signal
Processor (DSP) implementation approach that allows different
existing
ADSL line codes, Discrete MultiTone (DMT) and Carrierless AM/PM
(CAP), to
be implemented on the same hardware platform as a voice-band modem.
With
a DSP implementation, the desired transmission rate can also be
negotiated
in real time to accommodate line condition and service-cost requirements.
This line code and rate negotiation process can be implemented
at
the beginning of each communication session through the exchange
of tones
between modems at both ends. A four-step Mid-band Digital Subscriber
Lines (MDSL) modem initialization process is used for line code
and rate
compatibility.
Although Digital Subscriber Line (DSL) signaling is used to convey
digital data over existing twisted-pair copper telephone lines
connecting
the telephone company central office (CO) to residential. subscribers,
conventional DSL data modems are designed to provide service to
a certain
percentage of residential customers at a prescribed data rate.
A new rate
- 6 -
CA 02505051 1997-10-O1
negotiation method of the present invention enables a variable-rate DSL
(vRDSL) system. Using the rate negotiation method, the, variable rate
system adapts its throughput based on line conditions, computational
capabilities, network accessibility, and application requirements. This
service can be added to a telephone subscriber loop without disrupting the
plain old telephone service (POTS). Hence, a voice-band modem connection
can also be made available independent of the DSL connection.
The rate negotiation method provides systematic control for a DSL
system that supports multiple rates. The data rates can be varied
depending on modem cost, line conditions, or application requirements.
The modem functions as a variable rate data link capable of supporting
many different applications, including vOD, videophone, multiple ISDN
links, and new network access applidations. Hy considering the capability
of a particular DSL connection, available computational power, and any
special application program requirements, the data rate can be adapted by
the negotiation method to a suitable level. This scheme provides
symmetrical or asymmetrical data links and supports simultaneous
applications requiring arbitrary mixes of symmetrical and asymmetrical
links. A part of the symmetrical portion of the DSL transmission
throughput can be used for telephone. calls or video telephone calls. A
part of the asymmetrical portion of the DSL transmission throughput can be
used for Internet access or VOD services. The rate negotiation method
supports many different network applications using DSL.
The typical implementations of DSL modems, thus far, have supported
only connectionless services bettaeen the subscriber and the network.
However, since DSL is terminated at the local central office, a telephone
network friendly DSL interface is desirable. To facilitate multiple
virtual service connections, an operations/signaling channel, similar to
the ISDN D channel, is preferred for exchanging service and control
messages. A preprocessor in the 'CO-end DSL modem is also necessary to
collect operational messages before passing signaling and data packets to
the CO control-channel server.
The DSL modem of the present invention supports connectionless as
well as connection-oriented (switched) services.
The method of rate negotiation is preferably employed with a DSL
system .capable of a varying rate. An example is a variable-rate DSL
(VRDSL) system that can provide a variable upstream transmission
throughput up to 400 Kbps and a downstream transmission throughput of from
400 Kbps up to 2.048 Mbps. (However, the invention is not constrained to
vary within the rates given by this example system.) With lower
throughput, operation With poor line conditions is supported. Lower data
rates also allow the design of less expensive modems for less demanding
applications. This is consistent with the mid-band DSL (MDSL) design
CA 02505051 1997-10-O1
phi losophy of the present invention, which can provide a symmetrical
400
Kbps link using the same hardware platform as a voice-band modem.
With
high downstream throughput, VRDSL can be made compatible with
ADSL.
Basically, the VRDSL rate negotiation method provides the capability
to
,'serve a range of price/performance DSL modems that can maximize
throughput
bas ed on individual line conditions and processing power. In
VRDSL
signaling, the POTS will still be available through the same telephone
subscriber loop.
The host interface requirements for the Mid-band digital subscriber
line (MDSL) software system is also a part of the present invention.
The software running under the host PC platform to control the
MDSL
network interface card was implemented as an NDIS 3.0 WAN mini-port
driver; it works under Windows NT/Windows 95 together with existing
networking drivers and applications.
The line connection management process for a mid-band digital
subscriber lines (MDSL) provides a simple, efficient and flexible
interface to manage the line connection between MDSL-C (MDSL in
Central
Office site) and MDSL-R (MDSL in residential site). MDSL uses
four
different line modes: leased line with single link (LLSL); leased
line
with multiple links (LLML); switched line with soft dial (SLSD);
and
switched line with hard dial (SLHD). The host interface for the
LLSL
mode, has three different line states: line drop, line disconnected
and
line connected. An internal state machine of the MDSL modem can
record
and monitor the line status and notify the state change to the
other MDSL
modem, as well as the host processbr. The protocol used for exchanging
line connection management messages of the present invention is
a
simplified point-to-point link control protocol.
The MDSL host interface includes the following basic functions:
command/control communications between the host and MDSL, line
connection
management and send/receive data packet. The MDSL host interface
provides
a simple, user-friendly, efficient and low-cost interface to the
host
controller.
In a presently preferred embodiment, the host driver software
for
MDSL is implemented as an NDIS WAN miniport driver running under
Windows
95/NT environment. The software controls and manages the Media
Access
Control (MAC) sublayer of the MDSL network system and working
with NDIS
wrapper and an upper layer protocol driver stack, any Internet
accessing
application can be run transparently.
The present invention also provides a simple algorithm to train
the
time domain equalizer of an MDSL modem. Hy the same procedure,
the FFT
frame boundary is also reliably detected.
- 8 -
CA 02505051 1997-10-O1
In accordance with one aspect of the present
invention there is provided a method for Discrete
MultiTone (DMT) modem initial synchronization, comprising
the steps of: (i) a training sequence for probing the
length of channel impulse response including repetitive
data blocks with the block polarity alternating
periodically; (ii) deriving residual channel
inter-symbol interference ~ and frame boundary by
subtracting a previously received data block from a
current received data block; (iii) time domain
equalizer training by using said training sequence and
said residual channel inter-symbol interference to update
equalizer coefficients; and (.iv) frame synchronization
by using said training sequence and said frame boundary.
- 8a -
CA 02505051 1997-10-O1
BRIEF DESCRIPTION OF THE DRAWINGS
The present invention will now be described in
detail hereinbelow in conjunction with the parent
invention described in Canadian Patent No. 2,217,073.
The Figures are schematic for clarity.
Figures la-a show a preferred embodiment multimode
modem;
Figures 2a-c show preferred embodiment modem Central
Office modems;
10~ Figures 3a-a show preferred embodiment modem
applications and ISDN signaling;
Figures 4a-c show prior art modems plus subscriber
line capacity;
Figures 5a-b show another preferred embodiment modem;
Figures 6a-f illustrate preferred embodiment
initialization;
Figures 7a-f show preferred embodiment rate
negotiation;
Figures 8a-c show preferred embodiment
synchronization;
Figures 9a-d show preferred embodiment training;
Figures l0a-h show preferred embodiment line
connection management:
Figures llb-n show preferred embodiment modem driver;
Figure 12 shows preferred embodiment downloading;
Figures 13a-g show preferred embodiment sampling rate
conversion; and
Figures 19a-a show preferred embodiment modem pool.
- 9 -
CA 02505051 1997-10-O1
DETAILED DESCRIPTION
Overview of preferred embodiment modems
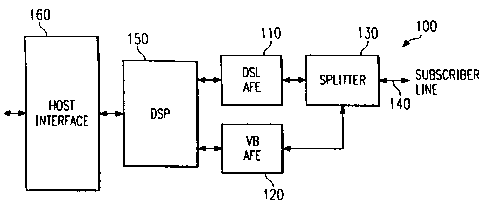
Figure la shows a functional block diagram of a first preferred
embodiment of a multimode modem 100 of the present invention.
In Figure
la, modem 100 includes both a voice-band and DSL band data path
to a
single subscriber line (twisted-pair) 140, which connects to
a telephone
company central office. A voice-band analog front end (VB AFE)
110
transmits and receives at frequencies in the voice-band (30 Hz
to 3.3
Khz). whereas the digital subscriber line analog front end (DSL
AFE) 120
transmits and receives at frequencies above the voice-band (above
4 KHz).
A Splitter 130 connects to the.s.ubscriber line 140 and separates
the
incoming signals into its voice-band and above-voice-band components.
POTS (plain old telephone service) occurs in the voice-band and
a
telephone may be connected to the subscriber line directly or
through the
splitter 130.
Modem 100 utilizes a single programmable digital signal processor
(DSP) 150 as part of the DSL band data path and as part of the
voice-band
data Bath, but typically uses two separate data input ports.
Generally,
the DSL band will have a much highex bit rate than the voice-band
data
path, so using separate DSP ports will be more convenient than
using a
single port with a buffered multiplexes; although the use of
such a
multiplexes is an alternative clearly within the scope of the
present
invention. For example, the DSL band operation modem 100 may
employ an
upstream (from residence to central office) frequency band centered
at 100
KHz with a total bandwidth of slightly less than 200 KHz, and
a downstream
(from central office to residence) frequency band centered at
300 KHz and
also of total bandwidth slightly less than 200 KHz: this frequency
allocation provides for full duplex operation of modem 100. Generally
multiple DSPs, instead of a single DSP, may be employed to increase
functions performed or to increase performance. The DSP 150 is
connected
to a host interface circuit 160.
Modem 100 can select from multiple line codes and, further, modem
100 can perform as either a high-bit-rate DSL modem in frequencies
above
voice-band or as a voice-band modem (such as V.34), either simultaneou$ly
or consecutively, just by switching programs being executed by
the DSP
150. The various line code programs can be stored in the DSP
onboard
memory or in auxiliary memory not shown in Figure la. Also, alternative
line codes for the DSL modem operations (e. g., a CAP or a DMT
line code)
can be used, again depending upon the program executed by the
DSP 150.
Figures lb-c illustrates the DSL data path portion of modem 100
which includes analog-to-digital 172 and digital-to-analog 170 converters,
filters 174,, 176, a transmission driver 178, and a receiver amplifier 180.
- 10 -
CA 02505051 1997-10-O1
Figure lb additionally explicitly shows a phase locked loop 182 clock
generator that synchronizes the modems' internal clocks with the clock
signals from the host (or the central office). Figure lc omits the
bandpass filters and instead shows various optional memory types, both
5SRAM 184 and nonvolatile EEPROM 186 which could hold line code programs.
SWhen modem 100 acts as a voice-band modem, the splitter 130 provides the
voice-band frequencies to the voice-band analog front end 120.
Figure ld illustrates the DSP software for modem 100 in DSL mode and
includes (i) an optional kernel (operating system) 190 for the DSP, (ii)
host interface 192, (iii) optional management maintenance control 194,
(iv) framing 196, (v) embedded operations control 198, (vi) channel
multiplexes 199 for multiplexing the embedded operations control with the
data stream, (vii) scrambler logic 191 for bitstream scrambling (viii) the
transceiver logic 193 such as a CAP or DMT logic which includes the bits-
to-symbols conversions, equalization, echo cancellation, and (ix)
modulator/demodulator 195 logic and optional forward error correction
(FEC) .
Figure 1e illustrates the software protocol hierarchy for
applications running on modem 100 interfacing with a host. The physical
layer 185 (layer 1) includes the DSP software for modulation, bitstream
scrambling, and multiplexing control signals with the data stream. The
data link layer 187 (layer 2) in the DSP includes embedded' operations
control and framing. The network layer 189 (layer 3) in the host includes
the modem driver (e. g. NDIS type for a Windows 95/NT) and transport
protocols such as PPP (point-to-point protocol). Applications such as
Internet browsers interact with the transport protocols.
For voice-band modes of operation, modem 100 may use software
similar to standard voice-band modems (e. g. V.34, etc.).
The present invention provides a new high speed modem 100 for use on .
standard telephone twisted-pair lines at lengths up to 21,000 ft. This
new modem 100 will be referred to as MDSL, mid-band digital subscriber
line. The MDSL modem 100 makes use of frequency division multiplexing
(FDM) to separate the downstream and upstream transmitted signals.
Although the modulation scheme for MDSL can be arbitrary, two specific
modulation schemes that may be employed are QAM/CAP and Discrete Multitone
(DMT). A startup procedure for achieving synchronization between the
modem at the central office (CO) and the modem at the remote.user (RU) end
is provided as part of the invention.'
One of the' modulation schemes selected for one embodiment of the
MDSL modem is Carrierless AM/PM (CAP). CAP can be considered as a special
case of the more conventional Quadrature Amplitude Modulation (QAM). The
main difference is that CAP performs most of its processing in the
passband, while QAM.performs most of its processing at baseband.
- 11 -
CA 02505051 1997-10-O1
CAP does not make use of a separate tone for synchronization.
Synchronization is achieved using the transmitted data signal directly.
At startup, a special data sequence is used to train equalizers
in the CAP
receiver before real data is transmitted.
One embodiment uses Carrierless AM/PM (CAP) Modulation and Discrete
'
Multiple-Tone Modulation on the same DSP platform to achieve 16
Kbps - 389
Kbps upstream speed (from MDSL-R to MDSL-C) and 384 Kbps - 2.048
tips
downstream speed (from MDSL-C to MDSL-R). The MDSL-C can also be
installed as a gateway or muter to allow the MDSL-R access to local
area
networks. Examples of the application of MDSL are described later
herein.
Prototype MDSL hardware was built upon an ISA card which can be
plugged into a PC or other platform directly. This prototype contains
the
following components: TMS320C541 DSP to implement modulation/
demodulation: network physical layer framing and interfacing with
the
HOST, 16-bit wide EEPROM and RAM: Combined D/A and A/D Converter
capable
of supporting the sampling rates, resolution, and other characteristics
necessary for implementation of MDSL: Analog Front-End circuitry
required
for connection to a POTS interface: and an ISA bus interface circuit.
Figure 2a shows modem 100 in a home 210 communicating with another
modem 100 in the central office 220. This central office 220 modem
100
may have various capabilities and loads, and the subscriber loop
140 may
be in a particular condition, so the modems execute an initialization
process to select the line code (CAP, DMT or others), the bit-rate,
and
train the equalizers. Then the modems begin data communication.
'
Figures 2b-c illustrate alternative central office connections
to
subscriber lines with DSL modems: each subscriber line has a DSL
AFE
(analog front end) and an analog switch connects an AFE output
to a DSL
processor, either a DSP similar to the DSP in the residence modem
or a
single DSP for multiple AFEs. The central office monitors the AFE
outputs
and a digital switch assigns an available DSP to communicate with
the
corresponding residence DSL modem. The central office polls the
AFEs to
find active modems in the residences. As Figures 2b-c show, the
central
office DSL modem connects to a remote access server on a local
area
network with packetized information (e. g., Internet) or a wide
area
network with constant bit rate data which is sent directly across
the
public switched telephone network trunk lines. The information
sent by
the residence modem would be identified or signaled via an out
of band
signaling method (e.g, similar to ISDN Q.931 signaling), rather
than an
off-hook signal, plus telephone number sent in the voice-band to
the
analog switching and line cards. Figure 2c illustrates the major
functional blocks of a central office DSL modem (the DSL band is
already
separated from the voice-band) as an AFE 240, DSP 260, Communications
Controller 280 and ARM or RISC processor 290. The modem has a connection
- 12 -
CA 02505051 1997-10-O1
to both the constant bit rate transmissions (voice, video conferencing,
etc.) being forwarded to a time division multiplexed (TDM) bus
and
packetized data (Internet, Intranet, private networks, etc.) being
forwarded to a control bus (and then to the trunk lines). Figure
2e
~'ciepicts the terminology "xDSL" which may be ADSL or any other
type of DSL
modem. These various functions could be all performed in a single
DSP
260.
The AFEs 240 could be separated from the central office 220 and
placed in the pedestals connected to the central office via optical
fiber
or coaxial cable: each pedestal would tap off a bundle of subscriber
lines
with residences within a short distance, such as 5 kft or less.
In this
manner, the attenuation at high frequencies for long subscriber
lines can
be avoided.
An alternative is for the central office to monitor each subscriber
line with a DSL modem in the above-voice-band frequencies and when
the
line becomes active, an analog switch connects the subscriber line
to a
DSL modem in the central office. This mimics Figure 2b except a
simpler
monitoring and an analog switch replace AFE monitoring and a digital
switch. The same approach may also be used in conjunction with
the local
pedestal to shorten the subscriber line distance from residence
DSL modem
to the AFE on the central office end (physically located in the
remote
pedestal) '.
Figure 3a shows a system with modem 100 in a personal computer
310
running Windows 95 (or Windows NT) with standard protocol stacks
communicating over a subscriber line 140 with a corresponding modem
100 in
the central office 220, which may be connected to an Internet access
server via an Ethernet (10/100 Hase T) interface. Modem 100 allows
for
both POTS or voice-band modem communication with another voice-band
modem
at the same time as the DSL portion,pf modem 100 connects to the
Internet
over the DSL portion.
Similarly, Figure 3b shows a DSL modem acting as a router 330 for
a
local area network (LAN) 320 and coupling to devices 340, 342,
344 with
corresponding DSL modems.
Figure 3c shows half of a teleconferencing system based on modem
100
in a PC 350. Each teleconferencing end has modem 100 communicating
at
384+16 Kbps with a modem in a central office 220. The central office
modem transmits data between a concentrator and packetizer 360,
and the
packetizer converts to the 16 Kbps signaling channel into ISDN
like
signaling messages and applies the 384 Kbps stream to the T1/T3
service
across the public switched telephone network. The central office
220 for
the receiving party inverts these operations to feed the receiving
modem
100. Traffic in the opposite directions proceeds similarly. Note
that
POTS can simultaneously be used with modems 100 for the voice in
the
- 13 -
CA 02505051 1997-10-O1
teleconferencing. An analog delay can be inserted in the POTS
output to
synchronize with the video.
Figures 3d and 3e show ISDN-type signaling protocols and messages:
modem 100 sends voice or data over the public switched telephone
network.
The SS7 network provides the backbone for carrying the ISDN user's
part
(ISUP) messages for call set-up and tear-down through the network.
Figure 5a shows multimode modem 500, which includes the modem
100
features of both a DSL AFE 110 and a VB AFE 120, with a splitter
130 for
subscriber line 140 connection together an ISDN front end 510
for
connection to an ISDN line 142 plus an audio front end 520 for
driving a
speaker 146 and receiving a microphone 144 output as could be
used for
supporting a hands-free speakerphone. External RAM 530 may be
nonvolatile
(EEPROM or Flash EPROM) and/or volatile (SRAM or DRAM). The external
RAM
530 may contain various programs for different line codes that
may be used
by the DSP 150. Such line codes may be DMT, QAM, CAP, RSK, FM,
AM, PAM,
DW(~l'I' , a t c .
The transmit part of modem 100 consists of in-phase and quadrature
passband digital shaping filters implemented as a portion of QAM
transceiver logic; and the receive part consists of a fractionally
spaced
complex decision feedback equalizer (DFE) with in-phase and quadrature
feedforward filters and cross-coupled feedback filters implemented
as a
portion of QAM transceiver logic, optionally, the QAM transceiver
logic
may include a Viterbi decoder.
When modem 500 is active, modem 500 may provide voice-band modem
functionality, DSL band modem functionality, ISDN functionality,
audio
functionality, other line code functionality, etc., or any combinations
of
the foregoing.
The present invention also includes a system where multiple like
and
different modems are simultaneously implemented in a single DSP
hardware
device. For example, voice-band (e.g., V.34), DSL, cable, terrestrial
and
other wireless, and/or satellite modems are implemented simultaneously
by
the same DSP device. This is now becoming possible with increased
processing capabilities of DSP devices. The advantages of this
approach
are to reduce overall system cost where the system requires multiple
modems (e.g., Remote Access Systems (RAS): processing requirements
are
reduced due to reductions in processing overhead and program and
data
memory are reduced by sharing program and data memory buffers.
For
example, program memory is reduced when multiple like modems are
executed
simultaneously by a single DSP device. Interface and other miscellaneous
4p glue logic are reduced by sharing the same logic between multiple
modems,
as well as better facilitating for statistical multiplexing and
rate
control.
- 19 -
CA 02505051 1997-10-O1
In the near-term, the following situations will predominate, but
these combinations will expand as DSP MIPS capabilities increase as a
natural progression in the semiconductor industry: multiple voice-band
modems in same DSP; voice-band and DSL modems in same DSP; voice-band and
,cable modems in same DSP; multiple DSL modems in same DSP; multiple cable
modems in the same DSP; and/or any combination of the above.
Figure 5b shows a passive splitter circuit for separation of voice-
band and higher frequency DSL band. The splitter also performs impedanc a
matching and ensures an acceptable return loss value for POTS.
Referring now to Figure 6a, there may be seen a schematic diagram of
the interconnection of a telephone 212 and modem 500 to a central office
220, via a subscriber loop 140. ,
Systems based on the DSL technology and available today are ISDN
Hasic Rate Access Channel and Repeaterless T1. DSL systems under
development are Asymmetrical Digital Subscriber Lines (ADSL), Symmetrical
Digital Subscriber Lines (SDSL), and Very-high-bit-rate Digital Subscriber
Lines (VDSL). The transmission throughput of a DSL system is dependent on
the loop loss, the noise environment, and the transceiver technology.
The noise environment can be,a combination of self or foreign Near
End Crosstalk (NEXT), Far End ~Crosstalk (FEXT), and background white
noise.
Figure 6b depicts multiple subscriber loops 140 and. schematically
how NEXT and FEXT are generated.
The transmission throughput of DSL for ISDN Basic Rate Access
Channel is 160 Kbps. The transmission throughput of HDSL for repeaterless
T1 is 800 Kbps. The transmission throughputs of ADSL are between 16 Kbps
to 640 Kbps in the upstream (from a subscriber to a telephone central
office) and between 1.544 Mbps to 6.7 Mbps in the downstream. The
transmission throughputs of MDSL are presently believed to be 384 Kbps in
the upstream and between 384 Kbps tlo 2.048 Mbps in the downstream.
A passband DSL system can be implemented with a single carrier using
Quadrature Amplitude Modulation (QAM) or Carrierless AM/PM (CAP) line
codes. A single carrier system depends on the adaptive channel equalizer
to compensate for the channel distortion. The channel equalizer usually
operates at a multiple of the signaling baud rate. Figure 6c depicts a
block diagram of a CAP transceiver.
More particularly, D/A 614 is connected to transmitter fitters 610,
612 and to filter 616. Filter 616 is connected to channel 620. Channel
620.is connected to filter 630 which is connected to A/D 632. A/D 632 is
connected to equalizers 634, 636. A portion of the circuitry 638 recovers
the time.
A DSL system can also be implemented with multiple carriers using
the Discrete MultiTone (DMT) line code. A DMT system divides the channel
- 15 -
CA 02505051 1997-10-O1
into many subchannel carriers to better exploit the channel capacity and
to reduce the channel distortion in addition to allowing for a relatively
simple adaptive channel equalizer which only compresses the time spread of
the channel impulse response rather than correcting it. A simple frequency
,domain equalizer completes the channel equalization. The signaling band
rate of the DMT subchannels is much lower than the band rate of a single
carrier system. ,
Figure 6d depicts a block diagram of a DMT transceiver. More
particularly, IFFT block 640 is connected to DlA 644, which is connected
to transmit filter 696 which is connected to channel 650. Channel 650 is
connected to filter 660 whiehwis connected to A/D 632 which is connected
to equalizer 664, which is connebt~d to FFT block 666. Startup 642 and
time recovery 668 circuitry is also included.
One MDSL modem embodiment uses frequency division full duplex for
lower hardware cost and lower crosstalk noise level. Such an MDSL modem
will provide a minimum of 384 Kbps full duplex transmission link between
a central office and a subscriber for a loop length of up to 21 kf t. Under
favorable subscriber loop conditioqs, this MDSL modem can provide a much
higher transmission throughput which is limited by channel capacity or the
hardware capabilities of the subscribe~r-end modem. A full feature version
of a subscriber-end MDSL modem communicates with ADSL modems at the
central office end. The transmitter and receiver parts of the MDSL modem
are capable of implementing either CAP or DMT line codes.
Figure 6e depicts a block diagram of an MDSL modem 600. Modem 600
has a transmitter 676 connected to a D/A 674 which is connected to a
filter 672 which is connected to hybrid circuit 670 which is connected to
splitter 130. Hybrid circuit is also connected to filter 678 which is
connected to A/D 680. A/D 680 is connected to receiver 682 which outputs
the received signal. Timing recovery block 684 is used to recover the
central office clock timing.
The purpose of the initialization process is to confirm the MDSL
capability of the telephone subscriber loop 140 at both the central office
220 and the subscriber-end 210. The initialization process probes the
channel 620, and produces information useful for transceiver training.
' The process then selects the line cdde, assuming multiple choices are
available, and negotiates the transmission throughput based on the channel
limit, traffic condition, or usage tariff.
The initialization process which is described later herein is:
channel probing, line code selection, rate negotiation, and transceiver
training.
An MDSL modem at the subscriber-end sends probing tones in the
upstream band far a certain duration, with or without phase alternation
for a part of these tones, according to a predefined time sequence. After
- 16 -
CA 02505051 1997-10-O1
the first time duration. the MDSL modem at the central office
end responds
with channel probing tones in the downstream band, again, with
or without
phase alternation for a part of these tones. This initial channel
probing
period may be repeated, if desired or necessary. .
After the initial channel probing period, the MDSL modem at the
subscriber-end has determined the line coda capability of the
central
office end modem and has a channel model for the downstream band
and.
similarly, the MDSL modem at the central office end has determined
the
line code capability of the subscriber-end modem and hae a channel
model
for the upstream band.
After the channel probing period, the MDSL modem at the subscriber-
end should indicate/confirm its line code capability/preference
by sending
signature tones for a predefined time duration. Similarly, the
MDSL modem
at the central office end should respond/confirm the line code
selection
by sending signature tones for a predefined time duration. This
signature
tone exchange process is preferably repeated for a limited number
of times
to determine a particular line code choice.
Another set of signature tones is then exchanged between MDSL
modems
at both ends for the transmission rate negotiation. The MDSL
modem at the
subscriber-end sends its rate capabilities and its prefe;ence.
The MDSL
modem at the central office end responds with its capabilities
and its
rate selection. MDSL modems determine a rate choice with a predefined
rate change procedure described later herein. The transmission
rate
preference at the subscriber-end depends on the line condition,
hardware
capability, and user choice or application requirements. The
transmission
rate preference at the central office end depends on the line
condition
and the traffic load. Preferably, rate change during a communication
session due to line condition change or user choice is allowed.
After the rate negotiation, the MDSL modems at both ends start
transceiver training according to the conventional methods. Different
time domain training sequences may be used for different line
codes. It
is an option to use the channel models obtained during the channel
probing
step to speed up the transceiver training process.
The spectra of upstream and downstream probing tones are depicted
in
Figure bf. The upstream CAP tones 690 and downstream CAP tones
692 are
depicted on the left side, while the upstream DMT 694 and downstream
DMT
696 are depicted on the right. The "broken" lines in the DMT
spectra
represent phase shifts.
For simplicity, all frequency tones are assumed to be equally
spaced
with frequencies isf, amplitude a~, and phase G~i (usually it
is either 0
or n1. At the receiver, the amplitude and phase of the received tones may
be detected. The detected amplitude snd phase of i-th frequency tone are
b~ and q~ respectively. Assuming that there are N probing tones, the
- 17 -
CA 02505051 1997-10-O1
frequency response of the equivalent channel including filters at
frequency idf is '
bi e_p (ms-~~~ ~ i = p,..,,N- 1. (A)
a1
The impulse response of the equivalent channel can be calculated by
a fast Fourier transform as
hk = ~ Vj e-j2xdfTik ~ k = Q, . . . ,It1
where T is the sampling period. The frequency spacing Of depends on the
spread of the channel impulse response. For a channel impulse response
spread of n sampling periods,
Of s a / n = N~f / n (C)
to
where B is the total bandwidth of interest.
To distinguish from two different line codes, the phase of adjacent
tones may be reversed by 1800 for one of the line codes. This line code
could be DMT. To identify different line codes after channel distortion,
0 f =
select 2n .
For a channel spread of 30 samples and a bandwidth of 100 Khz,
select 0 f fi 1,7 KHZ and N as 64.
The channel probing tones should at least last more than a few times
of the channel spread. With possible phase alternation, the channel
probing tone duration should be 4 to 10 times of that necessary f or the
channel model recovery.
Using N tones, we can represent M = 2N different messages in a unit
time period with constant tones. Because the available vocabulary grows
exponentially with the number of tones used, the useful messages may be
~~ sent with a small set of tones, e.g. only two, three, or four different
frequencies.
The following is a Iist of example messages.
384 Kbps/CAP
768 Kbps/CAP
1.544 Mbps/CAP
2.098 Mbps/CAP
384 Kbps/DMT
- 18 -
CA 02505051 1997-10-O1
768 Kbps/DMT
1.544 Mbps/DMT
2.048 Mbps/DMT
Prefer Highest Rate
Prefer Best Price
Packet Multiplexing Allowed
Only Low Rate Available
Tones can be generated by an IFFT operation as used for the DMT
line
code. A unit magnitude and zero/1800 phase vector signal is fed
in to the
IFFT operation for the channel probing purpose. Selected zero
phase
vectors are used for the generation of signature tones.
Tones can be recovered by an FFT operation also ae used for t
he DMT
line code. The amplitude and phase information of each tone is
recovered
as a complex vector. A common phase difference due to the random
sampling
phase is calculated. Compensation produces a complex vector which
i s then
used for calculating the channel transmission throughput and the
channel
impulse response, which might be used for transceiver training.
If the MDSL service is available through the telephone loop, the
MDSL modem at the central office end should be on and monitor
the upstream
frequency band for probing tones.
Once power is on or a user service request is made, the MDS L
modem
at the subscriber-end sends upstream probing tones for a predefined
time
period and then monitors downstream probing tones. The MDSL modem
at the
central office end detects the probing tones, compensates for
the random
phase, stores them, and calculates the upstream channel transmission
throughput. Meanwhile, the central office end MDSL modem sends
the
probing tones in the downstream frequency band.
The MDSL modem at the subscriber-end detects the probing tones,
compensates for the random phase, stores them, and calculates
the
downstream channel transmission throughput. The subscriber-end
MDSL modem
then sends signature tones in the upstream band to indicate line
code and
transmission rate preferences.
The MDSL modem at the central office end detects the signature
tones
and responds with signature tones corresponding to its preferred
offering.
The subscriber-end MDSL modem then sends signature tones to confirm
the
offering or to request offering modification. The MDSL modems
go into a
transceiver training period after the confirmation of modem offering.
The throughput capacity of the DSL communication channel will
change
with line conditions and/or network accessibility. Line conditions
dictate the achievable throughput of the physical connection between
the
CO and the residence. Network accessibility describes the capability
of
the service provider's connection linking the DSL channel to the
backbone
_ 19 _
CA 02505051 1997-10-O1
network. The invented rate negotiation method incorporates a detailed
understanding of the capacity-limiting factors of a DSL system.
DSL systems are traditionally engineered for the worst-cas a line
condition for Which service is to be provided. This approach simplifies
,the general installation procedure for telephone companies. However,
restricting the DSL transmission throughput to that achieved in
the worst-
case line condition leaves most DSL systems operating well below
their
,
potential. The invented method provides a systematic procedure
for
maximizing the physical transmission throughput of each local loop,
enabling most DSL modems to operate at much higher rates than
traditionally engineered. In fact, this method enables a majority
of DSL
modems to achieve a transmission throughputs which are only limited
by the
capabilities of the modem hardware'. The rate negotiation method
also
provides time-varying adaptation in order to maintain the highest
possible
throughput as line conditions or network accessibility changes.
The physical throughput of the twisted-pair DSL channel is 1 invited
by the receiver's ability to reliably distinguish the transmitted
signal
in the presence of noise and interference. The maximum possible
throughput is upper bounded by the theoretical channel capacity
of the
. physical link, such as depicted in Figure 4c. The channel capacity
of the
link is determined by the bandwidth used, the received signal
characteristics, and the noise and interference. The rate negotiation
method will increase the DSL reach by providing low-rate options
that can
be supported by extremely long telephone subscriber loops while
providing
high-rate options that allow DSL 'modems operating on shorter loops
to
achieve a higher throughput.
The rate negotiation method considers the dynamic nature of t he
DSL
transmission medium. The DSL is a time varying channel whose capac
i ty may
change due to improving/degrading channel conditions. As the channel
conditions change, the theoretical maximum throughput also changes.
The
time-varying nature of the channel characteristics dictates the
need for
rate negotiation techniques to.achieve the most efficient use of
the
channel over time. This provides the capability for maintaining
a DSL
connection during periods of difficult channel characteristics
by lowering
the throughput, This also enables the modem to increase the throughput
and make the best use of the connection during periods of favorable
channel characteristics. Ideally, the transceivers at each end
can
monitor the channel and maximize their throughput as conditions
vary. A
practical transmitter/receiver can be designed that increases or
decreases
throughput of the physical channel based on the available capacity,
the
available signal processing resources, and the requirements of
the
specific applications. Several rate adaptation methods exist (e.g,
the
standard CCITT V.34 Voiceband Modem Standard), but two particularly
- 20 -
CA 02505051 1997-10-O1
convenient techniques are discussed later herein for two dist i
nctly
different modulation methods. However, the techniques for rate
adaptation
are easily extended to other modulation and coding schemes, and
such
extensions are considered part of the present invention.
,5 Network accessibility in this context describes the rate and/or
delay associated with the transfer of data from the local loop
to the
backbone network. This measure might be affected by the specific
backbone
network used (e.g. Internet, ATM, etc.), the bandwidth given by
the
service provider, and the amount of network traffic. The techniques
defined in this invention are not restricted to use on a part i
cular
backbone network.
Although a VRDSL connection is capable of certain transmission
throughput, the total throughput might not be connected to corresponding
CO backbone networks at times. For VRDSL-provided services going
through
the PSTN (Public Switched Telephone Network), connections will
b a made
only when services are initiated. For VRDSL-provided services terminated
at the local C0, such as Internet access, leased line or dial-up
line
connections with certain throughputs can be made depending on the
preferred cost structure. The available CO backbone throughput
to each
VRDSL modem can be different at different times. The subscriber-desired
throughput could also vary for different applications .
with actual throughputs lower than that provided by the VRDSL
physical transmission link, traffic concentration can be realized
at CO
backbone networks. Statistical multiplexing can also be realized
by using
a separate analog front end for each CO VRDSL modem. The required
number
of corresponding digital portions can be less than the number of
analog
front-ends, depending on the traffic behavior. In the extreme case,
the
digital portion of the CO VRDSL modem can be multiplexed among
active
VRDSL links by using the voice-band as a traffic indicating channel
and
keeping a copy of the digital state portion of the modem inside
RAM.
The VRDSL communications'model is depicted in Figure 7a. The sole
purpose of this model is to aid in understanding the disclosed
rate-
negotiation technique. The model is composed of separate residence
7210
and central office 7220 layered representations of functional separation.
The functionality of the residence terminal 7210 is shown on the
left.
The lowest layer 7330 is the Communication Hardware Layer, which
contains
the modulator/ demodulator, signal conditioning, timing, synchronization,
and error-correction coding. This layer can also be referred to
as the
data pump layer. The second layer 7320 is the Hardware Contro 1
Layer.
This layer provides framing control and other data packaging functions
that better organize the data received by the lower layer. The
third
layer 7310 is the Software Driver Layer. This layer provides an
interface
between the hardware levels and the application programs run at
the
- 21 -
CA 02505051 1997-10-O1
residence. The fourth (top) layer 7300 is the Application Software
Layer,
which contains all functions provided by the application programs
run at
the residence. This layer encompasses both the software to manage
the
throughput allocated to different simultaneous applications as
well as the
application programs themselves. Conventional software applic
a n on
1
programs request a channel and accept the available throughput
provided by
the lower layers (no negotiation). Future generations of software
application programs might have the requirement and capability
for rate
negotiation.
The CO 7220 portion of the model also contains four layers. The
bottom three layers 7430, 7420, 7410 are very similar to the residence
side of the model. (However, the ,actual implementation can be
radically
different.) The fourth (top) layer 7400 in' the CO is called the
Network
Access Software Layer. This layer provides the functions required
for
interfacing the DSL connection to the backbone network.
In the rate negotiation method, each layer of the model communicates
and interacts with the layer below and above. A standard protocol
for
comanunication between layers is defined. As shown in Figure 7a,
a layer
can indicate R (Rate request) to a lower layer in order to initiate
a rate
negotiation; "R" is depicted in Figure 7a along with a corresponding
downward arrow. The lower layer can indicate A (Available Rate
Notify) to
the upper layer to inform the upper layer of the achievable rates;
"A" is
depicted in Figure 7a along with a corresponding upward arrow.
The
meaning of the R and A information is different for the different
layer
interfaces, however, the process of negotiating is similar.
A rate table is defined as a common syntax for the R and A signaling
between layers. The rate table defines the rates that a particular
layer
can attempt to achieve. (In general, this will be defined by the
hardware
limitations of the modem.) During a rate request (R), an upper
layer
might signal a lower layer of a desire to change the rate structure.
If
the lower layer is able to reconfigure itself to a new set of
operating
parameters and achieve the requested rate, then it will do so
and indicate
this to the upper layer. If the lower layer determines the requested
rate to be unacceptable, the upper layer is informed along with
information about the rates that are available under the present
operating
conditions (A).
A lower layer can also initiate rate negotiation if the operating
conditions change due to lower or higher achievable throughputs.
The
upper layer is informed of the new set of achievable rates (A).
The upper
layer can then respond with a rate request based on the new conditions
(R) ,
- 22 -
CA 02505051 1997-10-O1
This common layer interface simplifies the rate negotiation method.
Although the. parameters of the rate table are different at each layer
interface, the interaction methods are similar.
Each layer can conceptually view the communication link as being
between it and the corresponding layer at the other end of the DSL
connection. As shown by the lines connecting the corresponding layers in
the residence and central office:
1. The Communication Hardware Layers 7330, 7430 in the residence
and CO are connected by a non-virtual 'Raw' connection. This
is the physical connection over which the actual modulation
occurs.
2. The Hardware Control:, Layers 7320, 7420 can view the
communication link as a virtual ' Corrected' data stream. This
is the actual throughput of the channel after the physical
timing, synchronization, control, and error-correction coding
redundancy symbols have been removed.
3. The Software Driver Layer 7310, 7410 views the connection as
a virtual channel called the data link channel (DLC) . For
convenience, the DLC may be a frame structure that represents
multiple N kbit/sec channels (N - 16 or 64 e.g.). In
addition, a control channel may be specified. This control
channel may either be embedded in the lower layer channels or
can be completely separated. from the DSL connection. For
example, the control signaling might be implemented in the
voice-band via a v.34 modem connection.
4. The Application Software Layer 7300 sees a virtual
'Application Link' 7500to some data providing location of
interest in the CO or the backbone network.
The basic requirement for rate adaptation is the rate table, a well
defined set of achievable rates that can be communicated to the upper
layers of the DSL communication model. The rate-table is determined by
the capabilities of the hardware at both ends of the connection. During
startup or reset, a pair of modems must agree upon the rate table entries
which they are both capable of supporting. The allowed rates under a
given channel condition are then represented as legal states in the table.
The different levels of the model can communicate via the rate-table
syntax without concern for detail in other layers. This rate table can
vary substantially from one modulation and/or coding scheme to the next,
but the concept of allowed and disallowed rates depending on channel
conditions does not change.
The following describes how rate negotiation between the Hardware
Control Layer 7320, 7420 and the Communication Hardware Layer 7330, 7430
is performed in accordance with the teachings of the present invention.
- 23 -
CA 02505051 1997-10-O1
Modulation parameters are allowed to vary to accommodate various
rates,
and the layers interact using the rate. The following describe
s two
possible modulation based rate adaptation techniques and examples
of rate
tables that can be shared between the bottom two layers in the
DSL
communication model.
In the case of high-rate serial transmission of digital data,
digital symbols are chosen to represent a certain number of bits,
s ay N.
Groups of N bits are mapped into symbols which are transmitted
over the
channel. At the decoder, a decision is made to determine the transmitted
symbols. If the correct decision is made, the transmitted bi t
s are
decoded correctly.
A method of changing the throughput changes the number of bits
represented by each symbol while keeping the symbol rate constant.
Increasing the number of bits represented in each symbol increases
the
number of transmitted bits, albeit at lower noise immunity. Decreasing
the number of bits per symbol increases the noise immunity and
improves
the robustness of the transmission, but at the expense of a lower
throughput. The bandwidth remains the same in either case.
Another straightforward method of varying the throughput is changing
the bandwidth used in.the transmission channel. By expanding the
bandwidth, a greater number of symbols can be transmitted over
the channel
in a given interval. The symbol rate is roughly proportional to
the
bandwidth.w However, the processing requirements of the DSL modem
also
increase with the bandwidth: higher bandwidth requires greater
computation
for modulation/ demodulation. The maximum usable bandwidth might
either
be restricted by channel conditions or modem hardware processing
capability constraints.
First, a set of parameters describing the communicationlink and
the
set of values which the parameters may assume is defined.
Let the nominal serial transmission rate be R. Define the minimum
rate step by which a DSL modem can change as dR. If the minimum
rate is
R - 2*dR and the maximum rate is R + 2*dR, then the set of achievable
rates is given by {R-2*dR,R-dR, R, R+dR,R+2*dR}. For example, let
R = 300
kilo-symbols/second, and dR = 100 kilo-symbols per second. The
set of
achievable rates become {100, 200, 300, 400, 500} kilo-symbols/second.
Let N represent the number of bits conveyed by each transmitted
digital symbol. For example, a VRDSL modem might support operation
with
N in the set {2,3,4,5}. The higher values of N will convey more
bits in
a given period, but will also result in lower tolerance to noise.
Using the R and N rate parameters and assuming they are allowed
to .
independently assume the values above, a rate table can be deffi
ned as
follows:
- 24 -
CA 02505051 1997-10-O1
R = le5 R = 2e5 R R = 4e5 R = 5e5
= 3e5
N = 2 200 kbits/s 900 __ 800 1000
600
N = 3 300 600 900 1200 _
~~ 1500
N = 4 400 800 1200 -1600 200 0
N = 5 500 1000 1500 2000 250 0
Table 1 Serial transmission (e. g. CAP) rate table example.
The rates R in Table 1 are given in units of symbols/second and
are
illustrated in scientific notation in the table for brevity. The
table
entries show the achievable transmission throughputs in kilobits/s
econd
for a given rate R and N bits represented by each symbol.
Discrete multi-tone (DMT) modulation transmits low-rate data symbols
over parallel subchannels. Hy splitting a high-rate serial data
stream
into multiple low-rate data streams that are transmitted in separate
subchannels, the system can be tailored to better match a frequency
selective channel. Good portions of the overall bandwidth (those
subbsnds
with high signal-to-noise ratio (SNR)) are used to transmit symbols
with
a larger number of bits/symbol. An unequal number of bits are
assigned to
different subchannels, depending ''on the available capacity of
each
subchannel. Essentially, the data can be distributed among subchanne
is in
a manner allowing very efficient use of the overall bandwidth.
As with the high-rate serial data stream, the overall bandwidth
of
a DMT system can be increased or decreased according to the overall
desired throughput, channel conditions, and modem hardware capabili
ties.
Additionally, DMT modulation provides the capability of dropping
or adding
bandwidth a single subchannel at a time. For a DMT system with
a large
number of subchannels, this creates a very large selection of
possible
bandwidths. If desired, the number of subchannels can be varied
while
keeping the overall bandwidth fixed.
For simplicity, consider a DM'~'~system where the subchannel bandwidth
remains constant, but the overall channel bandwidth used is control
led by
the number of subchannels used. Let T represent the number of
subchannels
or tones used in transmission. Let N represent the average number
of
bits/symbol across the subchannels. N is no longer restricted
to be an
integer as with the high-rate serial transmission system. For
this
example, however, consider N to be approximately an integer valued:
The
following is an example of a rate table for DMT:
T = 32 T = 64 T = 96 T = 128 T = 160
N = 200 kbits/s 400 600 800 1 000
2
N = 300 600 900 12 0 1 00
3
N = 40 800 12 0 1 00 2000
4
N = 00 1000 1 00 000 2 00
5
Table 2 DMT transmission rate table example.
- 25 -
CA 02505051 1997-10-O1
The parameter T represents the number of subchannels where each
subcharinel has a bandwidth of approximately 3.3 Khz. N represent s the
average number of.bits/symbol represented in all the subchannels. The
table entries are given in kilobits/second.
An actual DMT rate table might add or drop subchannels by increments
of one. Also, the number of bits assigned to each subchannel c an be
independently controlled. Thus. the DMT rate table has the potenti a 1 for
very small rate increment adjustments.
The Software Driver Layer 7310, 7410 communicates with the Hardware
Control Layer 7320, 7420 by means of a rate .table very similar to those
previously discussed. However, the table parameters and table en tries
will be different. After synchronization, demodulation, error-correction
decoding, and the stripping of hardware control bits, the resulting rate
table for either of the underlying modulation schemes considered above
might be:
crl cr2 cr3 cr4 cry
N = 192 kbits/s 384 576 _ _
2 i~ 960
N = 288 864 1152 1440
3
N = 384 68 1152 1~ 1 0
4
N = 480 960 1440 1920 00
5
Table 3 Rate Table Used for Interaction Between
the Software Driver Layer and the Hardware Control Layer
The column parameters are labeled as different channel resource
modes (crl, cr2... cr5), while the row parameters correspond to the
average number of bits represented by each symbol. The entries rep resent
the achievable rates for the 'Corrected' data stream in the VRDSL model.
Rate adjustment information between the Application Software Layer
7300, 7400 and the Software Driver Layer 7310, 7410 can either be
specified in terms of a rate table or the total available throughput. For
simplicity, the Software Driver Layer can indicate the total available
rate to the Application Software Layer. Management functions in the
Application Software Layer allocate portions of the total throughput to
various software application programs. The following provides a
conceptual view of partitioning and managing the total data throughput.
Rate negotiation in the data link layer is initiated by the
following events in VRDSL:
- A request for changing the current allocation of the data
connection or channels in VRDSL such as requesting a new
channel or changing an existing channel rate
- When VRDSL physical layer detects a total channel capacity
change either total channel capacity increase or decrease
- 26 -
CA 02505051 1997-10-O1
After the initialization of VRDSL, a control channel (for example,
of 16 Kbps) has been allocated as an initial channel connection.
This
control channel will be reserved during the whole physical line connection
time. It is used to send/receive all the control information including
rate negotiation information.
Rate negotiation in the data link layer can be described as a number
of signal data formats and a finite-state automaton.
The rate negotiation signal data are encapsulated in the Data Link
Control Protocol such as the information field of the PPP data link
layer
frame structure. The protocol field indicates type Oxc024 for VRDSL
rate
negotiation protocol. The packet format is depicted in Figure 7b.
Code: The Code field is one octet and identifies the kind of rate
negotiation packet. Code 1 - 11 has been reserved for PPP LCP. It
has
the following special definitions for VRDSL:
13 Channel map change Request
14 Channel map change Nak
15 Channel map change Reject
16 Channel map change Ack
ID: The ID field is one octet and aids in matching requests and
replies
Length: The Length field is two octets and indicates the length of
the whole rate negotiation signal data packet.
Channel Map Data: The Channel Map Data Field is 2 or more octets
which reflects the current channel allocation in the VRDSL line and
the
request for a channel change. It contains its own header and two
parts of
information represented by channel entry field:
- Current channel map
- Channel map change request
These two parts of information are all described by the 2 octet
l
tinguish them is that for channel map
channel entry field. The way to dis
change request, the most significant bit of the channel entry is
set high.
The Channel Map Data field is depicted in Figure 7c.
When the code is 14 (Channel Map Change Nak), the Channel Map Data
field contains: Total Capacity, Available Capacity, the current channel
map and one or more channel entries which have been Naked. These
Naked
channel entries are flagged by their most significant bit (msb) .
When the
code is 15 or 16, the Channel Map Data field contains: Total Capacity,
Available Capacity and current channel map data.
Checksum: The Checksum field is computed using the standard TCP/IP
algorithm: the one's complement of the sum of a11.16-bit integers
in the
message (excluding the checksum field).
The Link Layer Rate Negotiation is also called Channel Map Change
(CMC) in VRDSL. A CMC procedure is described by the state change
- 27 -
CA 02505051 1997-10-O1
triggered by a specific event and action. Figures 7d and 7e depict
state
diagrams for the link layer rate negotiation during an active
and passive
CMC process, respectively.
Based on the VRDSL communication model, modem hardware capable
of
varying the transmission rate, and variable-rate management software,
the
rate negotiation method shown in Figure 7f may be employed. Figure
7f
depicts a simplified functional diagram of the overall rate negotiation,
method.
Current QAM based voice-band modems make use of a handshake sequence
between calling and answering modems to initialize their communications.
To gain synchronization, the answering modem transmits alternating
symbols
of the corresponding constellatiot~'~oints. As an example, V.32
modems use
the constellation points A,B,C, and D in Figure 8a in the synchronization
process. The answering modem transmits alternating symbols ABABAB...for
a duration of 256 symbols. After 256 symbols, the alternating
symbols
CDCDCD.., is transmitted for 16 symbols. The transition period
between
the two symbol sequences provides a well-defined event that may
be used
for generating a time reference in the calling modem receiver.
After the
second symbol sequence the answering modem will start transmitting
a
symbol sequence that is known by both modems. This sequence is
used to
train the equalizer at the calling modem receiver. Figure 8a depicts
a
V.32 training constellation.
The frequency response of the voice-band channel (30 Hz to 3.3
KHz)
is nominally flat. The alternating ABAH... and CDCD... symbols
can be
reliably detected before equalization of the channel. However,
this is
not the case for the MDSL modem. For a 1/4 T1, modems use the
spectrum up
to 500 KHz of the telephone line. Figure 8b shows the frequency
response
of a telephone CSA loop 6. A startup procedure that allows for
partial
equalization of the line is requi,r,ed before timing synchronization
is
attempted.
A preferred embodiment uses a startup handshake procedure f or the
MDSL modem. It uses an algorithm for implementation of the receiver
portion.
Figure 8c shows the time line for the proposed startup procedure for
the CO and RU MDSL modems using CAP line code. The table below identifies
the various segt~ents of Figure 8c.
_ 28 _
CA 02505051 1997-10-O1
Segment Description
A.D One orthogonal channel is a repeating K-symbol
sequenc a
using the maximum value of the CAP constellation.
For .16
constellation points, the channel can take on the
values
of +/- 3.
The other orthogonal channel is a random sequence
using
all possible points of the CAP constellation. For
16
constellation points, the channel can take on the
values
of +/-1, or +/-3.
B,E One orthogonal channel is a length K sequence that
is the
inverted version of the K-symbol sequence used
in segment
A.
The other orthogonal channel is a length K random
sequence using all possible points of the CAP
constellation. For 16 constellation points, the
channel
can take on the values of +/-1, or +/-3.
C,F One orthogonal channel is a length L random sequence
using all possible points of the CAP constellation.
For
16 constellation points, the channel can take on
the
values of +/-1, or +/-3.
The other orthogonal channel is a length L random
sequence using all possible points of the CAP
constellation. For 16 constellation points, the
channel
can take on the values of +/-1, or +/-3.
The startup procedure is as follows:
CO MODEM
1. The CO modem is assumed to be always 'on' , but in an idle state. It
continuously transmits segment A and listens for segment D.
RU MODEM
1. The RU modem comes on line and starts listening for segment A
from the CO modem.
2. Once it detects segment A, it begins transmitting Segment D.
CO MODEM
2. Once the CO modem detects segment D from the RU modem, it transmits
segments H,C, and valid data without further handshaking from the RU
modem.
RU MODEM
3. The RU modem listens for segment H and once detected, it
transmits segments E, F, and valid data without further
handshaking from the CO modem.
4. The detection of segment B is the critical timing instant in
the synchronization procedure. After it is detected, the RU
modem begins training its equalizer using data from segment C.
- 29 -
CA 02505051 1997-10-O1
CO MODEM
3 . The CO modem listens for segment E from the RU modem. The detection
of segment E is the critical timing instant in the synchronization
procedure. After it is detected, the CO modem begins training its
equalizer using data from segment F.
The receiver makes use of cyclical equalization techniques to obtain
~
initial timing synchronization. On startup, the RU modem sets up
a
fractional spaced adaptive equalizer that is equal in time duration
to K
symbol periods, for example, K may be 15. This will be called the
sync
equalizer. If the sync equalizer is operated at two times the symbol
period, the number of taps required~:is 2xK. For four samples per
symbol
period, the number of taps required is 4xK, and so on.
The receiver uses the same K-symbol sequence as the transmitt a
r for
the training data of the sync equalizer. Because the length of
the
equalizer is a multiple of the symbol sequence length, the relative
phase
between the transmitted sequence and the receiver reference sequenc
a does
not matter.
Once the sync equalizer mean square error falls below a thre s
hold,
segment A has been detected. The receiver stops the adaptation
process
and analyzes the coefficients. It then rotates the coefficients
in a
circular manner so that the N. consecutive coefficients with the
most
energy are grouped at the front of the sync equalizer filter. N
i.s the
length of the orthogonal adaptive filters used in CAP demodulation,
(see
the following paragraphs). This aligns the symbol period of the
receiver
with the symbol period of the transmitter.
After rotation, the receiver continues to filter the signal, but
does not update the sync equalizer coefficients. The output of
the sync
equalizer is then passed to a length K matched filter. The matched
f filter
is used to detect segment B. Its coefficients are the transmitted
channel
sequence B. Since this sequence has only two values, a binary corre
lator
could also be used.
When the output of the matched filter (correlator) is greets r
than
a threshold. The receiver knows that the next symbol is the start
of the
training data. The receiver now implements the orthogonal adaptive
filters used in CAP demodulation. They again are fractionally spaced
.
adaptive equalizers whose lengths depend on the impulse response
of the
actual physical channel. These demodulation equalizers are trained
using
the known training data of segment C. After training has completed
the
demodulation equalizers enter a decision directed mode where the
reference
data comes from the CAP slicer.
Referring now to Figure 9a, there may be seen a time domain
equalizer training sequence for use with DMT line code.
- 30 -
CA 02505051 1997-10-O1
The portion of this invention for DMT, instead of using the usual
frequency domain training sequence, uses a time domain training sequence
depicted in Figure 9a. The basic unit of the training sequence is a
random data block ( x~ }, 0 < n < N. The entire sequence is arranged so
the random data block ( x~ } repeats in time with the sign of data b lock
alternating every two blocks as shown in Fig. 9a.
For easy description purposes, the following notations are a sed:
time domain equalizer taps w~ ; channel impulse response (including time
domain equalizer) hk; the receiver data before the equalizer ym[n], and
after the equalizer zm[n], where m denotes the label on data block. The
received signals corresponding to the transmitted signals in Fig. 9a are
as follows:
frame number
n
1 . Z1 (I1] Xn_k ' l1k + ~ XN_k ' hn~k + Fn
~o k=i
n
2 . ZZ (Il~ - -~ Xn_k ' hk + ~, X1V-k ~ hn~k + pn
k=1
n
3 . Z~ (Ilk - - ~ Xn_k ' tlk - ~ XN_k ' hn~k + P
o i
n
4 . Z4 [1!] _ ~ Xn_k ' hk - ~ XH_k ' f1n~k + pn
k=0 k=1
5. ZS (I1] - ZI (I!]
where, p~ is the pilot tone superimposing on the training sequence. The
second terms on the right hand side of the equations are attribute to the
inter-symbol interference from the previous frame. The second term can be
separated from the first term by performing the operation: frame 4. -
f r ame 1 .
err [n] - z, (n) - zl [n] - - 2 ~~ X~, k ' hn~k)
k=i (1)
Assuming prefix length is L, the ideal channel impulse response is
- 31 -
CA 02505051 1997-10-O1
_ ~ hk k < L
hk 0 k 2 L (2)
The condition (2) can be satisfied if the time domain equalizer w~ is
chosen such that
err[n] - 0, for n 2 L - 1. (3)
It is easy to prove that equation (3) leads to a set of linear equations
xnt-i Xm-a ht
0 Xp_~ Xr_a hL,y
xl1-1 hyig ° 0
0 ... ~ XN 1 .
(4)
If the trainin se uence is chosen such that XN 1 a
g q , the unique
solution of equations (4) will be hk = 0, for k > L. Which is the same as
(2) .
as
2 (11~ - ~ yn_k ' Wk
Since k'° , equation (1) can be alternately written .
err [n1 = ~ (Ya (n-kl - Y1 [n~kJ ) ' wk
(5)
Combining (3) and (5) and using general LMS algorithm, w~ may be found by
doing iterations:
wl [k+17 = wl [k1 - 2 ~ ~ ~ err,~n1 ~ (Ya [n-11 - Yl [n-11 ) . n 2 L-1 . (6)
The frame boundary information can also be derived from above
training sequence. As seen in Eq. (1), if the block of the training
sequence is much longer than the channel impulse response, err[nJ
approaches zero as hH=k ~ ~ when n increases to the end of f rams 4.
However, when data starts in frame 5,
n
err [nl = zs [n) - zz [n] - 2 ( ~ xn_k ' hk
(7 )
For ADSL applications, since there is high attenuation in copper wire st
high frequency, the channel impulse response hk does not expect to flip the ,
sign very frequently. If the values of x~ at the beginning of the
training block (x~] have the same sign, the siu~nnation in equation 7 will
- 32 -
CA 02505051 1997-10-O1
be constructive. Consequently the amplitude of err(n] starts to increase
at frame boundary n = 0. Fig 9b shows the time sequence of err(nJ. As
shown in Fig. 9b, the rising edge of the derived sequence err(n) can be
used for frame synchronization, and the trailing edge of err(n] can be
used for time domain equalizer training. For the same reason as that of
in the rising edge of err(nj, to make the summation in equation (1)
constructive the elements of the training sequence at the end of block xN_k
should also have the same sign.
The above sequence can also be easily detected by doing the
operation
det [n] = z3 [n] + z~ [n] = 2 ' pn. (8)
Comparing the power of frame det [n] pwr det to the power of frame z(nJ
pwr, if pwr det«pwr, it indicates that the training sequence has been
detected. To end the training sequence, one can send the data block
pattern as shown in Figure 9c. Then the corresponding received signal
are:
Frame:
n
3 . Z~ ~n] - ~Xn_k ' hk ' ~ XH k ' hnk t pp
k~0 k=1
n
S . Zs [n] - X~_k ' hk + ~ Xp_k ' hn.k + pa
~° k~1
In this case the detection signal is
n
det Inl - zs [n] + z~ [n] _ -2 ' ~ Xn_k ' hk + 2 ' p"
k'° . (9)
The power of this detection frame is greater than that of the data frame,
pwr det > pwr. Once pwr det > pwr'is detected in the received data
stream, the DMT receiver determines that it is the end of training
sequence. Since the data pattern for the end of the training sequence is
inserted in the frame 5, which is used for frame boundary detection rather
than time domain equalizer training, it will not affect time domain
equalizer update.
Following the time domain equalizer training, the transmitter should
send another sequence {y~} to train the frequency domain equalizer. The
frequency domain equalizer training sequence can be made of exactly the
- 33 -
CA 02505051 1997-10-O1
repeatable block {y~j. Figure 9d shows the entire training sequence.
In
the regime of training sequence {y~l pwr det remains high.
The line management part of the MDSL allows the host software to
pre-configure .the MDSL to work under Leased Line with Single Link
mode.
','Currently, MDSL uses the following modes:
Leased line with single link (LLSL)
Leased line with multiple Links (LLML)
Switched Line with soft dial (SLSD)
Switched line with hard dial (SLHD)
Under the LLSL mode, the telecommunication line is solely committed
to the MDSL communications with a remote MDSL system. Only one
data link
is allowed under this line connection mode. So the link management
is the
same as the line management.
The LLML mode works the same as the LLSL except that it allows
multiple link connections at different speeds within the same leased
line.
The number of links and the link speed can be configured dynamically
to
the capacity of the line speed. Under this mode, each link works
like an
independent Leased line and follows the same line management scheme,
except that it is link oriented.
The SLSD mode works on a switched MDSL line on which the MDSL-R
modem is dialed automatically by the MDSL-C which is controlled
by a
remote server. Under this mode, the line management follows a special
MDSL dial-up procedure that is independent from the Plain Old Telephone
Service (POTS) line. The MDSL modem dial-up procedure is defined
by the
MDSL modem's internal initialization process. It has 2 dial-up
IDs, one
related to the MDSL-C port and the other related to the MDSL-R
modem. The
ID for MDSL-C port could be just the subscriber phone number plus
1 digit;
by choosing it tv be 0 and the ID for the MDSL-R modem could be
the
subscriber phone number also plus 1 digit selected to be 1. The
other 8
1
values, from 2 to 9, are reserved.
The SLHD mode works in a way similar to that of voice-band modem
but
with MDSL dial-up procedure. The MDSL modem will either store a
phone
number or be dialed manually by an application.
The following sections will describe the MDSL line connection
management under Leased Line with Single Link mode as an example
of mode
operations.
The MDSL Line Management Host Interface allows the host software
to
configure a line to be ready to send/receive data packets. Host
software
can also manually halt the line connection to stop the data flow.
The line configuration command in MDSL Line Management Host
Interface is used for host software to configure a line into one
of the
MDSL supported line modes. Under LLSL mode, it also sets up the
sending/receiving data rate, maximum frame size and data link protocol.
- 34 -
CA 02505051 1997-10-O1
This command is usually called during the MDSL initialization o~r error
recovery process. After a successful execution of this command, the MDSL
under configuration is ready to send/receive data packets through the
line. For LLML, a data link has to be opened/created to allow the data
5,flow. The line configuration of MDSL is an asynchronous procedure. The
HOST will be notified tY.at the line has been successfully configured by
the "line connected" interrupt generated by MDSL. The line configuration
process in MDSL is depicted in Figure 10a.
Host Interface:
MdslLineConfigure(IN LineMode, IN TxSpeed, IN RxSpeed, IN MaxTx
FrameSize, IN MaxRxFrameSize, IN TxProtocol, IN RxProtocol)
The LineMode input parameter-specifies which line mode the MDSL is
to be configured for. It has the following definitions:
0 - leased line with single link
1 - leased line with multiple links
2 - switched line with soft dialup
3 - switched line with hard dialup
The TxSpeed and RxSpeed give the upstream and downstream line speed.
The MaxTxFrameSize and MaxRxFrameSize parameters specify the maximum
frame for sending and receiving data..
The TxProtocol and~RxProtocol define the physical layer framing
protocol used for transmitting data. Currently it has the fol lowing
definitions:
Bit 0 - Bit 1 define framing protocol name:
00 - Raw MDSL (no data'packetizing)
O1_- MDSL specific packetizing
10 - HDLC (High-level Data Link Control)
Bit 2 indicates if there is packet header compression.
Bit 3 indicates if there is packet data compression.
Bit 4 indicates if the data is encrypted.
In MDSL Line Management Host Interface, the Halt Line command tells
MDSL to stop sending/receiving data for the data flow control. It f lushes
all the internal data transmit buffers and status flags and s ends a
message to the remote MDSL to notify the request and manually put the line
into "line disconnected" state, This command will take effect only when
the line is in "line connected" state. Otherwise, it will return error.
Halt Line is an asynchronous process, the HOST will be notified when the
line has been put into the "line disconnected" state as depicted in Figure
lOb.
Host Interface: .
MdslHaltLine()
- 35 -
CA 02505051 1997-10-O1
Inside MDSL there is a line state engine used to monitor the line
status for reporting line hanging or unexpected incidents. In MDSL leased
line mode the following line states are defined:
~ Line Drop - line is unplugged or broken, no physical signa 1 is
received
Line Disconnected - line is physically connected but is not
ready for data transmission
~ Line Connected - line is ready for sending/receiving data
packets
MDSL Line Management Host Interface provides two ways to get the
line status information.
One way is calling Get Line Status.command:
MdslGetLineStatus(OUT LineStatus, OUT LineConfigure)
The LineStatus parameter returns the MDSL line status informs Lion
described above. The LineConfigure is a structure which is used to s tore
the line configuration information set by MdslLineConfigure() command.
The other way for the host software to be notified of the line
status change is by registering the line management events. MDSL will
allow host software to be interrupted when certain events happened. The
events related with line management are:
~ Line connected: A line connection has just been establi shed
~ Line disconnected: A previously connected line has been
disconnected by either Mdslhaltline () call or some un-expected
incidents.
~ Line dropped: A line has been physically disconnected. No
signal can be received in the line.
There is also a timer interrupt provided by MDSL to allow the host
software to poke the line status periodically, as depicted in Figure lOc.
The line connection messages need to be exchanged between two MDSL
ends connected to each other. These messages are defined as specie 1 link
management packets in MDSL.
In order to exchange Line Connection Management Information between
MDSL-C and MDSL-R, the following kinds of Line Control Message Packet s are
defined:
~ Line Configuration Command Packet
Line Halt Command Packet .
~ Acknowledgment Packet
Referring now to Figure lOd, there may be seen a depiction of the
format for the line configuration command packet.
ID is 1 octet and aids in matching commands and replies.
Length is the packet length in octets.
Configuration Data Contains the following information:
~ Line Mode defined previously
- 36 -
CA 02505051 1997-10-O1
Data Sending Speed
Data Receiving Speed
Maximum Sending Frame Size
Maximum Receiving Frame Size
Data Sending Protocol defined previously
Data Receiving Protocol defined previously
Checksum is computed using the standard TCP/IP algorithm: the one's
.
complement of the sum of all 16-bit integers in the message (excluding
the
checksum field).
Referring now to Figure 10e, there may be seen a depiction of the
format for the line halt command packet.
ID is 1 octet and aids in matching commands and replies.
Length is the packet length in octets.
Checksum is computed using the standard TCP/IP algorithm: the one's
complement of the sum of all 16-bit integers in the message (excluding
the
checksum field).
Referring now to Figure lOf, there may be seen 'a depiction of
the
format for the acknowledgement packet.
Code defines what kind of acknowledgment packet it is. It has the
following definitions:
2 - Line Configuration Acknowledgment
4 - Line Configuration Reject
Line Halt Acknowledgment
ID is 1 octet and aids in matching commands and replies.
Length is the packet length'in bytes.
Status Code has the following definitions:
SUCCESS
Unrecognized packet ID
Part of the configuration data is not acceptable
Configuration is completely rejected
Checksum error
Data contains 0 or even number of octets specifying which part
of
the configuration data is not acceptable on the remote end.
Checksum is computed using the standard TCP/IP algorithm: the one's
complement of the sum of all 16-bit integers in the message (excluding
the
checksum field).
After power on, the MDSL-R automatically precedes with its internal
initialization process. This process contains four steps: channel
probing, line code selection, rate negotiation and transceiver
.training.
After the initialization procedure, the MDSL-R transitions to a
s t and-by
mode. The line state at this moment is "disconnected" as defined
before.
Upon detecting that the line has been physically connected, the
HOST
software will send a MdslLineConfigure() command to MDSL-R f or
line
- 37 -
CA 02505051 1997-10-O1
configuration. MDSL-R then sends out a.line configuration command
packet
to MDSL-C with the configuration data. After receiving the line
configuration command and checking the configuration data, MDSL-C
will
send out an acknowledgment packet to confirm the line configuration.
If
the MDSL-C cannot accept the configuration data, it will send a
configuration reject packet. It will also give the status message
specifying what kind error it is. If only part of the configuration
data
is not acceptable, the data field will contain the configuration
data
which is not acceptable, as depicted in Figure lOg.
After the connection is established. it stays connected until the
following events happen:
The line is unplugged or broken
The MDSL-R is powered down
The MDSL-C is out of service
Whenever MDSL-C is going to shut down or MDSL-R is powered down,
a~
Line Halt command packet will be sent out. The command sender will
keep
sending out the Line Halt command packet until either an acknowledgment
packet has been received or Line Halt command timed out. At the
receiver
site, after sending an acknowledgment packet back to the message
sender to
2p confirm that the line is disconnect, it clears up all the internal
data
buffers and status flags. The line state then changed into "line
disconnected" state. Figure lOh gives an example of the MDSL-C
sending
out a Line Halt Command before it is out of service.
The MDSL host interface is intended to provide a simple, user
friendly, efficient and low-cost interface to a 16-bit host controller.
The host interface will provide the following functions:
Command/control communications between the host and the MDSL
Network Interface Card (NIC)
Line connection management
Send/receive data packets
The host command/control communication functions include
initializing the device, downloading DSP code to the local RAM
if it is
not in the EEPROM, sending commands to MDSL, monitoring and reporting
status changes.
The line connection signaling between two MDSL-C and MDSL-R can
be
different according to different line modes: dialup-line mode and
leased-
line mode. The dialup-line mode will provide the basic telephony
- a
guaranteed set of functions that correspond to POTS. Under this
mode, the
system software and hardware has to work with the Telephony Application
Programming Interface (TAPI) on the MDSL-R site and Telephony Service
Provider Interface (TSPI) on the MDSL-C site to establish the connection.
Under the leased-line mode, the connection will be established
immediately
- 38 -
CA 02505051 1997-10-O1
after the initialization of the MDSL. Hut it does not provide standard
POTS service.
Physical layer packetizing is preferably used for MDSL (suc h as
HDLC). The maximum packet size for the PPP is 1500 bytes, but it should
;allow 32 bytes overhead for the frame. MDSL will send data from packet
buffer to the line and notify the host that the packet has been set out.
It will also notify the host when a new packet has been put into the
receiving buffer. The sending and receiving buffer ran be a shared memory
on MDSL .
The following commands and controls may be employed:
1. Reset
Syntax: Reset()
Description: Halts all of the command executions in the system. Flushes
the transfer/receive buffer and performs an internal reset.
Parameter: None
Return: None
2. Load DSP Module
Syntax: LoadDspModule(ModuleAddr, ModuleSize)
Description: Loads the DSP module into the MDSL
Parameter: ModuleAddr - DSP module start address '
Module8ize - DSP module size
Return: None
3. Set Interrupt Mask "
Syntax: SetinterruptMask(EventMssk) '
Description: Enable interrupt of host processor, based on occurrence of
selected events)
Parameter: EventMssk is a 16 bit integer value for the interrupt mask.
Table 1 identifies the bits in the mask. A value of 1 for a bit enables
the interrupt corresponding to that bit. All bits not defined in the
table are reserved for future use and should be set to zero.
- 39 -
CA 02505051 1997-10-O1
TABLE 1. Hit Definitions for
EventMask Parameter
Bit ~ Demonic Event Event Definition
0 INTE Interrupt Enable This bit enables the interrupt
set by the EventMask
t LNC Line Connected A line connection has been established
1 2 LNDC Line Disconnected A previously connected line has
0 been disconnected
3 BFOVF Rx Buffer overrun The line receiving buffer is overrunning
T BFEMP Tx Buffer Emptya 'The line transfer buffer is empty
9 PKARV Packet Arrival A packet has been put into the
line receiving buffer
10 PKST Packet Sent A packet has been moved out of
the data line sending
buffer
15 TINT Timer Expires ~ A preset timer count goes to 0
a This interrupt is redundant
with the packet sent interrupt
if transmit buffer can only
hold one
packet at a time.
4. Get Interrupt Status
Syntax: GetInterruptStatus()
Description: Get the interrupt status, based on the occurrence
of the
selected event(s).
Parameter: None
Return: EventStatus. MDSL wil l return a 16 bit status number
which
corresponds to the definition f .t,he EventMask parameter in
o Tab le 1.
Calling this function will clearthe interrupts just fired.
The following Line Connection
Management commands are available:
1. Line Configuration
Syntax: LineConfigure(LineMode)
Description: Configure the line to be ready to receive and send data
packets
Parameter: LineMode indicates what kind of line mode MDSL is going to be
configured. It is has the following bit definitions. All the undeffined
bits will be reserved for future use.
TABLE 2. Bit Definitions For LineMode Parameter
- 40 -
CA 02505051 1997-10-O1
Bit ~ Mndnonic Event Event Definition
0 Line Mode When this bit set, the data line will work under the
leased line mode. lfien this bit is cleared, the
data
line will work under dial-up mode.
10
1 Voice line Flag When this bit is set, the voice signal transmission
will function at the same time with the data signal
transmission in MDSL. When this bit is cleared, the
voice-band cannot f~mction at the same time.
2-6 Speed Definition These bits define the speed for sending and
receiving
data. Bit 6 indicates if the speed is for sending
or
receiving. Bit 2 to 5 define 16 different speeds.
Return: None
2. Get Line Status
Syntax: GetLineStatus()
Description: This command will return a 16 bit number to indicat a the
current line status.
Parameter: None
Return: LineStatus. The definition of this returned number is in Table
3.
- 41 -
CA 02505051 1997-10-O1
TABLE 3. Bit Definitions For LineStatus
Bit ~ Mnemonic Event Ev~t Definition
0-1 Line Status These two bits indicate the following line sta tea:
1. Line is down (no physical signal is received)
2. line is disconnected (line is not ready for
sending and receiving data)
. 3. Line is connected (line is ready for sending
data)
2 Line Mode lfien this bit set, the data line will work under the
teased line mode. l~hen this bit is cleared, the
data
line will work under dial-~ mode:
3 Voice Line Flag when this bit is set, the voice signal transmission
will function at the same time with the data signal
transmission in MDSL. lfien this bit is cleared, the
voice-band cannot function at the same time.
4-8 Speed Definition These bits define the speed for sending and
rdceiving
data. Bit 8 indicates if the speed is for sending
or
receiving. eit 4 to 7 define 16 different speeds.
3. Halt a Connected Line
Syntax: HaltLine()
Description: Tell MDSL to stop sending/receiving data for the data flow
Zp control. It will flush all the internal buffers and manually put tha line
into a "disconnected" state.
Parameter: None
Return: None .
The following Sending/Receivirg Data Packet commands are available.
1. Send Packet
Syntax: SendPacket(DataPtr, Size)
Description: This command tells MDSL that one data packet has been copied
into MDSL sending buffer. An interrupt will be generated after the packet
has been moved out of the buffer.
Parameter: DataPtr Points to the memory address of the sending buffer
where the data packet is stored. The length of the packet should be less
than or equal to the maximum allowed packet size.
Return: None
2. Check Receive Information
- 42 -
CA 02505051 1997-10-O1
Syntax: CheckReceiveInfo(DataPtr, Size, ErrorFlag)
Description: This command returns TRUE (1) or FALSE (0) depending on if
there is a packet in the receiving buffer.
Parameter: DataPtr is used to return the memory address where the packet
is stored. Size is used to return the size of the packet rec a ivied.
ErrorFlag is set to non-zero if there is any error happened during the'
transmission.
Return: 1 - There is data in the receiving buffer
0 - No data is in the receiving buffer.
3. Check Sending Information
Syntax: CheckSendInfo()
Description: This command returns 0 if MDSL transmit buffer is empty.
otherwise, it returns the number of bytes left in the buffer.
Parameter: None
Return: Sending buffer data size. It is 0 when the transmit buf f er is
empty. Otherwise it is the number of bytes left in the transmit buffer.
Figure llb illustrates the software structure of the driver for
modem 100 used with a host having a Windows 95 or Windows NT environment,
as commonly would be the situation for a personal computer in a
residence.
Figuxe ilc illustrates the software driver structure more generally.
The system software of the MDSL NIC has been implemented as an
NDIS
3.0 WAN mini-port driver for Windows NT 3.5 and Windows 95 Operating
Systems.
The following is broken down from the following three perspectives:
1. The functionality of the system by virtue of the system
software being implemented ss a mini-port device driver under
Windows NT 3.51 and Windows 95
2. The input and output data processing that the system performs
3. The interaction of the system software with NDIS library
The MDSL driver will be implemented as an NDIS miniport driver
to
control and manage the Media Access Control (MAC) sub-layer of
the network
system. It's structure is described in Figure llb. It will be a
component within the Windows NT or Windows 95 Internet system software.
The MDSL driver will follow the definitions of the interface and
data
structures specified in NDIS 3Ø The driver needs to be installed
or
integrated into the system in order to make it function.
The MDSL driver will function as a WAN Network Interfac a Card
driver. It interacts with protocol drivers on the upper edge and
controls
the MDSL NIC on the lower edge. All these interactions and controls are
going through the NDIS library or NDIS wrapper in Windows NT/Windows 95.
- 93 -
CA 02505051 1997-10-O1
Figure lld depicts the data flow path in the system software.
Figure lld depicts how incoming data is received by the NIC card and
passed to the driver where it is passed to the transport interface via
various functions and how it is returned to the driver.
The MDSL driver will come with the MDSL network adapter. It..c an be
installed together with the MDSL-R into a PC at home and connected with
the MDSL-C running the same driver although the MDSL-C modulation
algorithm could be different. With an Internet router on the MDSL-C site,
the MDSL-R can run a lot of Internet applications such as TELNET, FT P and
NetScape through MDSL NIC. The data communication and voice communication
can occur simultaneously.
The following entry points or functions are completely compliant
with NDIS 3.0 specification.
Driver Entry Point (Driver Entry) is the main entry point called by
the operating system when the driver is loaded into memory.
In uts
DriverObject: Pointer to,driver object created by the operating
system.
RegistryPath: Pointer to registry path name used to read registry
parameters.
Outputs
Return Values: STATUS SUCCESS or STATUS UNSUCCESSFUL
DriverEntry will do:
1. Call NdisMInitializeWr~pper to initialize the NDIS WAN
wrapper.
2. Initialize the characteristics table and export the MDSL
driver's entry points to the NDIS WAN wrapper.
3. Call Ndisl~tegisterMiniport to register the MDSL driver to the
NDIS WAN wrapper.
Figure lle depicts the interaction between the OS, NDIS library and
MDSL driver for Driver Entry.
The initialization entry point (Mdsllnitialize) will be called by
NDIS library to initialize the MDSL modem.
Inputs '
MediumArray: All the networking media the NDIS library supported
MediumArraySize: The number of elements in the medium array
MdslAdapterHandle: A handle identifying the MDSL driver assigned by
the NDIS library
NdisConfigContext: A handle for NDIS configuration
Outputs
- 44 -
CA 02505051 1997-10-O1
OpenErrorStatus: MDSL driver will set this parameter to a status
value specifying information about the error if the return value
is
NDIS STATUS OPEN ERROR.
SelectedMediumIndex: MDSL driver sets this index to the MediumArray
,5 that specifies the medium type of the MDSL driver.
Return Values: MdslInitialize returns NDIS STATUS SUCCESS or
it can
return the following status values:
NDIS STATUS ADAPTER NOT FOUND
NDIS STATUS FAILURE
NDIS STATUS NOT ACCEPTED
NDIS STATUS OPEN ERROR
NDIS STATUS RESOURCES
NDIS STATUS UNSUPPORTED MEDIA
Processing
The MdslInitialize will:
1. Search through the MediumArray to find its medium match. If
no match is found NDIS STATUS UNSUPPORTED MEDIA is returned.
Z. Get all the configuration information of MDSL NIC (interrupt
number, board name, channel address or line address, switch
type, etc.)
3. Allocate and initialize memory for MDSL driver data
structures.
9. Inform NDIS wrapper the physical attributes of MDSL NIC
including associate the MdslAdapterHandle with MDSL NIC
5. Map MDSL NIC's physical location into the system address
space.
6. Reset or initialize the MDSL NIC
7. Setup and initialize the transmit queues
8. Initialize interrupt
9. Initialize line
Figure llf depicts the interaction between the NDIS library and
the
driver for MdslInitialize.
Entry point (MdslReset) issues a hardware reset to the MDSL NIC and
resets its software state.
Inputs
MdslAdapterContext: The handle initialized by MiniportInitialize
Outvuts
AddressingReset: Set to TRUE if the NDIS library needs to call
90 MdslSetInformation to restore addressing information to the current
values.
Return Values: None
Processing
- 95 -
CA 02505051 1997-10-O1
MdslReset will issue a software reset on the MDSL NIC. It may also
reset the parameters of MDSL NIC. If a hardware reset of MDSL NIC resets
the current station address, the MDSL driver automatically restores the
current station address following the reset.
.5 , Figure 11g depicts the interaction between the NDIS library and the
driver for MdslReset.
Entry point (MdslReconfigure) is called by NDIS library to
reconfigure the MDSL NIC to new parameters available in the NDIS library
functions. It is used to support plug and play adapters and software
configurable adapters, which may have the parameters changed during run
time.
Inputs
MdslAdapterContext: The handle initialized by MiniportInitialize
WrapperConfigurationContext: The handle of NDIS configuration.
Out,~uts
OpenErrorStatus: This parameter is set by MDSL driver to specify
the information about the error if the return value is NDIS STATUS OPEN
ERROR.
Return Values:
NDIS STATUS SUCCESS
NDIS STATUS NOT ACCEPTED
NDIS STATUS OPEN ERROR
Processing
Returns NDIS STATUS NOT ACCEPTED.
Entry point (MdsHalt) is called by NDIS library to halt the MDSL
NIC.
Inputs
MdslAdapterContext: The handle initialized by MdslInitialize
Outputs
None.
Process
The MdslHalt will:
1. Reregister the interrupt handling
2. Unmap the MDSL memory from the system
3. Free system memory
Figure llh depicts the interaction between the NDIS library and the
driver for MdslHalt.
Entry point (MdslCheckForHang) is called by NDIS library
periodically to check the state of MDSL NIC.
Inputs
- 46 -
CA 02505051 1997-10-O1
MdslAdapterCOntext: The handle initialized by MdslInitialize
Outputs
Return Value: TRUE if the MDSL NIC is not operating
Processing
Checks the MDSL NIC status.
Entry point (MdslEnableInterrupt) is called by NDIS library to
enable the MDSL NIC to generate interrupts.
Inputs
MdslAdapterContext: The handle initialized by Mdsllnitialize
Outputs
Return Value: None
Process
Enable the MDSL NIC hardware to generate interrupts.
Entry point (MdslDisableInterrupt) is called by NDIS library to
disable the MDSL NIC from generating any interrupts.
Inputs
MdslAdapterContext: The handle initialized by MdslInitialize
Outfluts
Return Value: None
Process
Disable the MDSL NIC hardware from generating any interrupts.
MdslISR is the MDSL driver interrupt service routine entry poin
t .
Inputs
MdslAdapterContext: The handle initialized by MdslInitialize
Outputs
InterruptRecognized: If the MDSL NIC is sharing an interrupt 1
i ne
and it detects that the interrupt came from its NIC, MDSL driver
will s ~ t
this parameter to be TRUE.
QueueMdslHandleInterrupt: If MDSL NIC is sharing an interrupt
13..rie
and if MdslHandleInterrupt must be called to finish handling of
t he
interrupt, this parameter will be set to be TRUE.
Return Value: None.
Processinv
This function runs at a high priority in response to an interrup
t
It leaves lower priority work to MdslHandleInterrupt. It will
do:
1. Get interrupt reason
2. Clear interrupt in hardware
3. Set InterruptRecognized and QueueMdslHandleInterru p t
accordingly.
- 47 -
CA 02505051 1997-10-O1
Entry point (MdslHandleInterrupt) is called by the def a rred
processing routine in the NDIS library to process, an interrupt.
Invuts
MdslAdapterContext: The handle initialized by MdslInitialize
.5 Outputs
Return Value: None
Processing
The MdslHandlelnterrupt will do:
1. Check MDSL NIC to get the reason for the interrupts
2. Process the following possible interrupts one by one:
- A packet hss just been put into the receiving buf f er
- A packet has just been sent out
- Line has just been connected
- Line is disconnected
- Line has been down
receiving buffer overrun
Entry point (MdslQueryInformation) is called by NDIS library to
query the capabilities and status of the MDSL driver.
Invuts
MdslAdapterContext: The handle initialized by MdslInitializ~
OID: Object ID of a managed object (or information element) i n the
Management Information Block where the driver stores dynamic configuration
information and statistical information. Refer to NDIS 3.0 specifi
c ation
for its formats and definitions. ,
InformationBuffer: A buffer that will receive information
InformationHufferLength: The length in bytes of InformationHuffer
Outputs
HytesWritten: The number of bytes actually written to
InformationBuffer
~BytesNeeded: The number of additional bytes needed to ge t the
complete information for the specified object. ~ w
Return Values: MdslQueryInformation returns NDIS STATUS- SUCCESS or
the following status values:
NDIS STATUS,I1WALID DATA
NDIS STATUS INVALID LENGTH
NDIS STATUS INVALID OID
NDIS STATUS NOT ACCEPTED
NDIS STATUS NOT SUPPORTED
NDIS STATUS_PENDING
NDIS STATUS RESOURCES
Processing
MDSL driver will only acknowledge the following OIDS synchronously:
- 48 -
CA 02505051 1997-10-O1
OID GEN HARDWARE STATUS: check the hardware status of MDSL NIC
OID GEN MEDIA SUPPORTED: return NdisMediumWan
OID_GEN MEDIA INUSE: return NdisMediumWan
OID GEN MAXIMUM LOOKAHEAD: return maximum packet size (1532 bytes).
5, OID GEN MAXIMUM FRAME_SIZE: return maximum frame size for MDSL
(1500 bytes).
OID GEN LINK SPEED: return link speed of MDSL (384000 bps).
OID GEN TRANSMIT BUFFER SPACE: return maximum packet size (assuming
there is only one packet allowed in the transmit buffer).
OID GEN RECEIVE BUFFER SPACE: return maximum packet size in
receiving buffer (assuming only one packet is allowed).
OID GEN TRANSMIT BLOCK SIZE:~~ return maximum packet size.
OID GEN RECEIVE BLOCK SIZE: return maximum packet size.
OID GEN VENDOR ID: return vendor ID.
OID GEN VENDOR_DESCRIPTION: return vendor description string.
OID GEN CURRENT LOOKAHEAD: return maximum packet size.
OID GEN MAC OPTIONS: The following bits will be set:
NDIS MAC OPTION RECEIVE SERIALIZED,
NDIS MAC OPTION NO LOOPHACK and
NDIS MAC,OPTION TRANSFERS NOT_PEND
OID GEN DRIVER VERSION: return MDSL driver major and minor version
number.
OID_GEN_MAXIMUM TOTAL_SIZE: return maximum packet size.
OID WAN MEDIUM SUBTYPE: Since MDSL is not yet defined by Microsoft,
NdisWanIsdn is returned. '
OID WAN GET INFO: return NDIS WAN info structure.
OID WAN PERMANENT ADDRESS: return WAN address.
OID WAN CURRENT ADDRESS: return WAN address.
OID WAN GET LINK INFO: return MdslLinkContext
For all the other Oids returnlNDIS STATUS INVALID OID
Figure lli depicts the interaction between the NDIS library and the
driver for MdslQueryInformation.
Entry point (MdslSetInformation) is called by NDIS library to change
the information maintained by the MDSL driver.
Inputs
MdslAdapterContext: The handle initialized by Mdsllnitialize
~OID: Object ID of a managed object (or information element) in the
Management Information Block where the driver stores dynamic configuration
information and statistical information. Refer to NDIS 3.0 specification
for its formats and definitions.
InformationBuffer: A buffer that stores information
InformationBufferLength: The length in bytes of InformationBuffer
- 49 -
CA 02505051 1997-10-O1
OutDUtS
BytesRead: The number of bytes read from InformationBuffer
HytesNeeded: The number of additional bytes needed to satisfy the
OID.
Return Values: MdslQueryInformation returns NDIS~STATUS_ SUCCESS
or
the following status values:
NDIS STATUS INVALID DATA
NDIS STATUS INVALID LENGTH
NDIS STATUS INVALID OID
NDIS STATUS NOT ACCEPTED
NDIS STATUS NOT SUPPORTED
NDIS STATUS PENDING ~_
NDIS STATUS RESOURCES
Processincr
MDSL driver will only acknowledge the following OIDs synchronously:
OID GEN CURRENT LOOKAHEAD: return NDIS STATUS SUCCESS' directly
without doing anything since WAN drivers always indicate the
entire packet
regardless of the lookahead size. ,
OID GEN WAN SET~LTNK: copy the MdslLinkContext stored i n the
InformationBuffer into MDSL WanLinkInfo structure.
For all the other OIDs return NDIS STATUS INVALID OID
Figuze llj depicts the interaction between the NDIS library and
the
driver for MdelSetlnformation.
Function (MdslReceivePacket) is called by MdslHandleInterrupt to
handle a packet receive interrupt. This function is used to replace NDIS
MdslTransferData entry point since MDSL driver does not call
NdisTransferData to transfer data from receiving buffer to the protocol
stack.
InDUts
MdslAdapterContext: The MDSL adapter handle initializ~d by
MdslInitialize
Outputs
None
Return Value: None.
Process
MdslReceivePacket will do:
1. Check receive status to see if there is any error during data
transmission. Drop the bad packets and indicate the error to
the NDIS wragper.
- 50 -
CA 02505051 1997-10-O1
2. Call NdisMWanIndicateReceive to indicate that a packet has
arrived and that the entire packet is available for
-. inspection.
3. If the above call returns NDIS STATUS SUCCESS, call
' NdisWanIndicateReceiveComplete to indicate the end of a
receive event.
Figure llk depicts the interaction between the NDIS library and the
driver for MdslReceivePacket.
Entry point (MdslWanSend) is called by NDIS library to instruct
MDSL
NIC driver to transmit a packet through the adapter onto the medium.
If
the medium is busy at the moment when this call comes, MDSL driver
will
queue the send command for a later' time or lower the Maximum
Transmit
value.
In uts
MdslBindingHandle: The handle returned from Mdsllnitialize
MdelLinkHandle: The handle returned from NDIS MAC LINK UP
indication when line is connected.
WanPacket: A pointer to the NDIS WAN_PACKET structure containing
a
pointer to a contiguous buffer.
OutDUts
Status: A status value specifying information about the error
if
the return value is not NDIS STATUS SUCCESS or NDIS STATUS PENDING
Return Values; MdslWanSend returns NDIS STATUS SUCCESS or the
following status values: '
NDIS STATUS PENDING
NDIS STATUS FAILURE
Processing
MdslWanSend will do:
l
make sure it is valid
1. Check the packet size to
2. Check if the line is currently connected
3. If medium is not currently busy, send the packet right away
and return NDIS_STATUS SUCCESS. If it is busy, put the packet
in the transmit list and return NDIS STATUS PENDING. After
the this packet has been sent out, MDSL driver will call
NdisWanSendComplete to indicate the completion of the sending
event.
Figure 111 depicts the interaction between the NDIS library and the
driver for MdslWanSend.
System Integration
- 51 -
CA 02505051 1997-10-O1
Under windows NT or Windows 95, the various network software
components are linked together, or bound into a logical hierarchy as
depicted in Figure llm.
When network components are installed, information is written to the
trlindows NT Registry that describes the order in which the network
components should be loaded, and how those network components are to be
bound together. The Windows NT Control Panel Network Applet (NCPA)
manages the network component installation and binding. The driver
binding works as depicted in Figure lln.
The External Interfaces for the system are as follows:
User Interfaces '
MDSL driver does not expose to the end users directly. It is
bound
with the protocol stack in the system through NDIS wrapper. Application
will use it though different standard protocol APIs such as window
socket.
NetBIOS, RPC, etc.
Hardware Interfaces
The hardware interfaces of. MDSL driver is described in MDSL
Host
Interface Requirement Specification.
Software Interfaces -
MDSL driver provide 13 Upper-Edge Functions and one driver main
entry point to the Operating System. It will call functions defined
in
ndis.lib and ndiswan.lib to implement a lot of tasks which are
independent
of a specific Network Interface Card (NIC).
Communication Interfaces, '
Packets being received and sent are in any format provided by
NDIS
WAN library. It can be IP data gram or other frame with or without
header
compression, Microsoft Point to Point compression, and encryption.
It can
also be a simple HDLG frame if the Simple HDLC Framing switch
is turned on
in NDIS WAN library. All these higher layer framing are transparent
to
the MDSL driver.
Design Constraints
The design must be compliant with NDIS 3.0 WAN driver specification.
Attri---bates,
Avai~ab~.itv/Recoverv
Errors during entry point processing will not result in catastrophic
failure of the driver. The error will be passed to the calling
entity and
NDIS will perform appropriate processing. Failures in initializing
the
MDSL NIC or establishing a line connection will result in an
error being
returned to the calling entity. Errors during receiving/sending
packets
are logged.
Software acauisition
- 52 -
CA 02505051 1997-10-O1
The software to configure a multimode modem as to its DSL band
operation can be acquired by downloading into a Flash EPROM (see Figure 5a
of a board version of a DSL modem enhanced to include Flash EPROM). This
downloading can be performed by using the voice-band configuration (V.34)
already in the multimode modem. In particular, a host can use voice-band
modem operation to call a source telephone number which then can down load
the software for DSL band operation over the voice-band to the Flash
EPROM. In the same manner, updates of the DSL band software can be
downloaded either over voice-band or over DSL band. Figure 12 illustrates
such a downloading process.
Referring now to Figure 13a, there may be seen the MDSL frequency
division for upstream and downstream. In voice-band modems, the
highest
frequency of interest is only 3.3 KHz. In MDSL, the highest frequency
of
interest can be hundreds of KHz. For example, for 1/4 T1 rates,
the
center frequency of the upstream channel F~~ is 100 KHz while
the center
frequency of the downstream channel Fez is 300 KHz. The bandwidth
of each
channel is 200 KHz and the highest frequency of interest is FZ+
=400 KHz.
The challenge is to be able to process the data with a low cost
programmable digital signal processor (DSP).. This invention addresses
how
to reduce the processing requirements by making either paseband
signal
depicted in Figure 13a appear identical to the DSP.
The MDSL modem has two modes, the central office (CO) and remote
user (RU) modes. In the CO mode, the modem transmits in the upper
frequency band and receives in the lower frequency band. In the
RU mode
the reverse occurs. The modem transmits in the lower frequency
band and
receives in the upper frequency band,
Using the normal interpretation of the Nyquist Sampling Theorem,
a
minimum sampling rate twice the highest frequency of interest
is required
to process the data. For the CO modem, the analog-to-digital converter
(ADC) can sample the received signal at twice F~+. However, it
must
generate samples for the digital-to-analog converter (DAC) at
twice FZ+.
For the RU modem, the DAC can run at twice F~+. However, the ADC
must run
at twice Fz+'
This invention makes use of digital sampling rate conversion to
decrease the sampling rate and consequently the processing requirements
for the implementation of the MDSL modem.
For the RU modem, the high sampling rate is connected with the
analog-to-digital conversion process. The 1/4 T1 example modem
receiver
front end is shown in Figure 13b at the RU modem. The incoming
analog
signal, centered at 300 KHz is first bandpass filtered to maximize the
signal to noise ratio by isolating the bandwidth of interest. The signal
53 -
CA 02505051 1997-10-O1
is then sampled by the ADC at the normal Nyquist rate of twice f 2+, 800
KHz.
The sampled spectra. in the digital domain is shown in Figure
13c.
Because there is no signal below Fs~~t~/4=200 KHz, the sampling
rat a can
'be safely reduced to 400 KHz by decimating the samples by two.
Decimation
by two generates an inverted image centered at 100 KHz as shown
in Figure
13d.
The original image can be obtained by multiplying every other
sample
of the decimated data stream by (-1). Since every other output
from the
ADC is being discarded, there is no need to generate them, i.e.
the ADC
can run at 400 KHz instead of 800 KHz.
For the CO modem, the high b'utput sampling rate is required i
n the
digital-to-analog process. It would require a minimum a sampling
rate of
800 KHz to directly generate the output samples corresponding
to the upper
passband signal. It would be much better if the CO modem could
generate
the output samples in the lower frequency band, and somehow automatically
translate the spectrum to the upper band. Figure 13e shows the
spectrum
of the low band signal in the digital domain.
Translation can be accomplished by making use of the aliased images
produced by digitally upsampling to a higher rate. Upsampling
by two to
800 KHz consists of inserting a zero valued sample between the
computed
output samples. This generates images at harmonics of the original
400
KHz sampling frequency. When the~new modified output data stream
is
passed to a DAC, the analog output spectrum shown in Figure 13f
is
generated. (The sinc roll-off characteristic imparted by the conversion
process has been left out of the figure). By the use of an appropriate
analog bandpass filter, the inverted image centered at 300 KHz
can be
selected. Since the inserted values are zero, they need not be
computed
by the DSP. The inversion can be either corrected by multiplication
of
odd samples by (-1) or disregarded completely, since the spec
t rum is
inverted again by the decimation process at the RU modem. As show
in
Figure 13g, the zero sample interleaving process can be implemented
by
simple external logic outside the DSP.
In conclusion, the application of sampling rate conversion allows
the DSP in the MDSL modem to assume that it is always transmitting
and
receiving only in the lower frequency band. Its computations are
therefore based on a much lower sampling rate than would normally
be
dictated by the actual analog signal frequency content.
Discrete Multitone (DMT) has been chosen as the standard for
Asymmetric Digital Subscriber Loops (ADSL) by the ANSI Standards
Committee
T1E1.4. Previous contributions to the T1E1 standards activity
have made
claims that 19-bit precision in the fast Fourier transforms FFT's
is
necessary to achieve adequate dynamic range for ADSL-2 bitrat~es
(6-7
- 54 -
CA 02505051 1997-10-O1
Mbps). The problem is how to implement the FFTs in a fixed point 16-bit
processor and provide adequate dynamic range for the ADSL-2 bitrat es.
Normally when implementing fixed point FFTs, the data is blindly
down scaled down at each stage to prevent the fixed point values from
'overflowing during the multiply and add operations. If the range of data
values is such that no overflow could occur during the stage, down scaling
results in the unnecessary loss of precision.
The approach for solving this problem in accordance with the
teachings of the present invention is preferably to implement both forward
and inverse FFTs in 16-bit fixed point using a variable scaling scheme
which examines the data before each FFT stage and scales down the data
only if an overflow is possible'Yiuring the stage. This removes the
unnecessary loss of precision which would be caused by the 'blind' down
scaling when an overflow would not occur. The need for scaling is
determined by looking at the number of sign bits in the FFT data before
each stage. The data is scaled by right shifting. Tests were conducted
by shifting by 1 bit or 2 bits at a time. Although, in general, both
shift amounts worked, in certain,cases where the data values were a
maximum value and with specific sine/cosine values, the single shifted
value could still overflow.
The total amount of scaling during the FFT is maintained so that the.
FFT output data can be normalized (rescaled) at the completion of the FFT.
Attached as an Appendix is the test version of C code used to test the
solution. The variable scaling method does require more processing power
than the 'blind" scaling, since all the data must be examined before each
stage of the FFT. Simulation results show that 19-bit fixed point fixed
scaling FFTs axe only marginally better, in the expected signal-to-noise
operating range, than the 16-bit variable scaled fixed point FFT.
The variable scaling of the fixed point FFT provides an advantage in
any application which the data range is such that an overflow would not
occur on every stage and additional' processing power is available for
improved precision.
In the central office end, a modem pool can be used to handle
multiple MDSL lines. Although a dedicated line coupling and front end
circuit is necessary fox each MDSL line, the signal processing power of a
high performance DSP chip can be shared among multiple MDSL lines. The
multiple line capability of an MDSL modem pool can be further enhanced by
incorporating multiple DSP ships within a single modem pool unit.
Figure 14a shows that an MDSL modem gool can have N logical MDSL
modems, each consisting of a transmitter part and a receiver part. Due to
the location of the modem pool, transmitters can be synchronized to the
same central office clock. Because of the MDSL line concentration and the
shared modem pool architecture, data symbols of the transmit signal and
- SS -
CA 02505051 1997-10-O1
samples of the received signal are readily accessib 1e among all
logical
modems. The transmit signal synchronization and the transmit and
received
signal accessibility enable the adaptation of NEXT cancellation
technique.
A multiple input-multiple output NEXT canceller can be implement
ed in
conjunction with an MDSL modem pool.
To avoid the NEXT and the cost of echo cancellation hardware, a
preferred MDSL modem uses frequency division duplex f or transmission
from .
a central office to a subscriber in the downstream direction and
vice
versa in the upstream direction. The downstream transmission normally
occupies the higher frequency part of the MDSL spec tram. The frequency
separation between the downstream and the upstream da.rections
is based on
the use of high order bandpass filters. Figure 14b shows that a
guardband
is used between the upstream frequency band and the downstream
frequency
band spectrum. Furthermore, the bandwidth of each downstream sp~ctrum
can
be different for different modems. This might be n eceseary because
the
spectral allocation could be optimized according to the individua
1 line
conditions and downstream to upstream throughput rat io.
Because of the finite amount of attenuation in the bandpass ffi
lter
stopband and the closeness between downstream and up stream spectra,
there
will always be some residue noise from the reverse channel. Due
to the
heavy subscriber line attenuation, the relative strength of residual
noise
might not be negligible compared with that of t he received signal.
Because of the possibility of upstream and downstream spectra overlapping
among different MDSL lines, the NEXT noise can occur within the
region of
guardband. Hence, the NEXT cancellation can be a sed to minimize
the
interference of reverse channel residual noise of the same MDSL
line and
the interference of reverse channel NEXT noise from adjacent MDSL
lines.
Figure 14c shows that a reverse channel NEXT c anceller bank can
be
implemented within the same MDSL,modem pool un it with or without
additional DSP chips. The NEXT canceller bank needs the access
~to the
transmit signal and the digitized received signal of all modems.
The NEXT
canceller bank has N NEXT cancellers as depicted in Figure 14d
corresponding to N MDSL modems. Each canceller has N adaptive filters
of
size M. Outputs of all N adaptive filters are appropriately combs
ned to
form the NEXT cancellation signal for the corresponding modem.
Each
adaptive filter is adapted according to the error signal between
the
received signal and the NEXT cancellation signal and the corresponding
transmit signal as the correlation vector as depict ed in Figure
14 e.
The following Terminology/Definitions has been used herein.
MDSL - Mid-band Digital Subscriber Line.
MDSL-C - The MDSL running on the Central Offic a site
MDSL-R - The MDSL running on the residential site
- 56 -
CA 02505051 1997-10-O1
POTS' - Plain Old Telephone Service. It only makes and receives
phone calls.
NDIS - Network Device Interface Specification. A specific etion
defined by Microsoft to provide a standard interface for network drivers
to interact with each other and with Operating System.
NIC - Network Interface Card
WAN - Wide Area Networking
mini-port NIC driver - A network interface card driver developed as
an extension to the NDIS 3.0 specification to allow developers to write
only code that is specific to the hardware, merging the common concerns
into the NDIS library or wrapper..
- 57 -
CA 02505051 1997-10-O1
. . APPENDIX
6fINPUT DECLARATIONS:
STATIC Double I_clock;
STATIC in;
Ovector I_real
STATIC _
Double I_reset
STATIC valid_in;
Double I
~OUTPUT _
DECLARATIONS:
STATIC Ovector O_img_out;
STATIC Ovector O_real_out:
STATIC Double O staler:
STATIC Double O_valid_out;
PARAMETER
DECLARATIONS:
STATIC Long P-fft math;
~STATE DECLARATIONS:
I
STATIC Long size ;
STATIC Double *f real ;
STATIC Double *f img
STATIC short *i real ;
STATIC short *i img
STATIC long *l real ;
STATIC long *l img
STATIC Double *in r
STATIC Double *out i
STATIC Double *out_r
STATIC long flag ;
STATIC long clock ;
STATIC long ltemp ;
STATIC long lmax
STATIC int scale ;
STATIC int i ;
STATIC int j ,
STATIC int 1 ;
STATIC int max bttr ;
STATIC int j2
STATIC int jll ;
STATIC short temp ;
STATIC int k ;
STATIC double twopi ;
STATIC double tmp real
STATIC double tmp-img
STATIC int doit ;
STATIC int Sine[256J ;
STATIC int Cosine(256] ;
STATIC FILE * filel ;
STATIC int lmm ;
STATIC int lix ;
STATIC double scl;
STATIC int bttr;
STATIC int li ;
STATIC int power ;
STATIC int stage ;
STATIC double tl ;
STATIC double t2 ;
STATIC double arg t
STATIC double c ;
STATIC double s
STATIC int itl ;
STATIC int it2 ;
STATIC int is ;
STATIC int is
- 58 -
CA 02505051 1997-10-O1
STATIC int arginc ;
STATIC int iarg ;
STATIC r ;
short tmp
STATIC _
short tmp i ;
STATIC int itmplre ;
STATIC int itmplim ,
,STATIC int itmp2re ,
STATIC int itmp2im ,
STATIC double pi ;
STATIC double cl ;
STATIC double c2 ;
STATIC double wpr ;
STATIC double wpi ;
STATIC double wi ;
STATIC double wr ;
STATIC double wtmp ;
STATIC double tmplre "
;
STATIC double tmplim
;
STATIC double tmp2re
;
STATIC double tmp2im
;
STATIC int length ;
STATIC int half ;
STATIC int halfpow ;
STATIC int DEBUG ;
STATIC long ltl ;
STATIC long lt2 ;
STATIC long is ,
STATIC long lc
STATIC long ltempl ;
STATIC long ltemp2 ;
STATIC long ltemp3 ;
STATIC long ltemp4 ;
STATIC long l tmp r
STATIC long 1 tmp
i ;
STATIC _
long ltmplre
;
STATIC long ltmplim
;
STATIC long ltmp2re
;
STATIC long ltmp2im
;
STATIC double ftemp
,
)
BLOCK DECLARATIONS:
~INITI ALIZATION CODE: '
t
DEBUG = 0 ;
size = 512
power = 9 ;
if(P_ fft math =- 1
)
t
f real - (double malloc (size * sizeof(double))
*) ;
f _ malloc (size * sizeof(double))
img - (double ,
*)
else
i real - (short malloc (size * sizeof(short))
*) ,
i _ malloc (size * sizeof(shozt))
img - (short ;
*)
1 real - (long malloc (size * sizeof(long))
*) ,
1 _img - (long malloc (size * sizeof(long))
*) ;
)
twop i= 3.1415926536 .0 ;
* 2
pi = 3.1415926536
;
file l = fopen("/home/mannerin/sincosl.txt"~"r")
for( j=0 ; j < 256
; j++)
- 59 -
CA 02505051 1997-10-O1
fscanf(filel, "%08x \n",&Cosine(j])
for (j=0 ; j < 256 ; j++)
fscanf(filel, "%OBx \n",&Sine [j]) ,
I
(close (filel) ,
I
RUN OUT CODE:
-
/* start of run code */
( -
flag = 0 ;
O valid out = 1.0 ;
scaler = 0.0 ;
O
_
CIF (I clock =- CONNECTED)
clock = (long) I clock
flag ;_ (-clock & 1) ,
~ENDIF
CIF (I valid_in =- CONNECTED)
flag ._ (long) I valid in ;
~ENDIF
CIF (I reset =- CONNECTED)
if (I reset =- 1.0)
f
]
~ENDIF
if (!flag)
( /* start of process input/output */
/* read in input */
in r - (double *) OvGetStart(I real in) ,
i = (double *) OvGetStart(O_img_out) ;
out
_
out r = (double *) OvGetStart (O-real out) ,
size = 512 ;
power = 9 ;
if (P-,fft math == 1)
[ /* start of if floating */
/*
for(i=0; i < size ; i++)
{ f real [i] =in-r [i] ;
90 ]
*/
/********************************************************/
length = 512 ;
half = 256 ;
halfpow = power - 1;
cl = c2 = 0.5;
for (i = 0, j = 0; i < half; i++, j += 2)
(
f real [i] - in r (j ]
f_img(i] - in r[j + 1] ;
1
c2 = -c2;
/* start of do floating fft */
/****************************************x***************/
size = 256 ,
power = 8 ,
bttr = size ;
max
_
for (stage = 1; stage <= power: stage++) [
bttr;
lix = max
_
max_bttr /= 2:
lmm = max bttr;
scl = ((double) (- twopi) / (double) lix);
for(bttr = 1; bttr <= lmm; bttr++)
arg = (bttr - 1) * scl;
- 60 -
CA 02505051 1997-10-O1
c = cos (arg) ,
s = sin (arg);
for(li = lix; li <= size : li += lix) (
jll = li - lix + bttr - 1:
j2 = jll + max bttr;
tl = f_real [jll] - f. real [j2] ;
t2 = f img[jllj - f img[j2j
f_real (jllj = f real [jll] + f real [j2] ,
f_img[jll] = f img[jll] + f img[j2] ,
f_real(j2) _ (c*tl + s*t2);
f img[j2] _ (c*t2 - s*tl):
]_
J
is ~ = o
for(i = 0: i < (size - 1): i++) (
if (i < j) ( , "
tmp_real = f real[j] :
tmp img = f_img[j] :
f_real [j ] = f real [i] :
f_img[j] - f img[i]
f real [i] = tmp real:
f_img(ij - tmp-img:
k = (size / 2) :
while (k < (j + 1)) ( j -- k: k /~ 2: ]
j += k:
/********************************************************/
/********************************************************/
/* Perform even/odd separation algorithm. */
/* Form an array with N/2 + 1 elements. */
/********************************************************/
arg = pi / half:
wtmp = sin (0.5 * arg):
wpr = - 2.0 * wtmp * wtmp;
wpi = sin (arg): '
wr = 1.0 + wpr:
wi = wpi;
for (i = 1, j = (half - 1): i <= j; i++, j--)
real[j]) * cl:
tmplre = (f real[i] + f
_
img[j]) * cl;
tmplim = (f img[i] - f
_
img [j ] ) * -c2:
tmp2re = (f img [i] + ~
_
tmp2im = (f real[i] - f real[jJ) * c2:
real[i] _ (tmpire + wr * tmp2re - wi * tmp2im):
f
_
img[i] - (tmplim + wr * tmp2im + wi * tmp2re):
f
_
real[j] _ (tmplre - wr * tmp2re + wi * tmp2im):
f
_
f img[j] - (- tmplim + wr * tmp2im + wi * tmp2re):
wtmp = wr:
wr +_ (wr * wpr - wi * wpi):
wi +_ (wi * wpr + wtmp * wpi):
l
/********************************************************/
/* Compute the first pair of frequency cells, */
/* at the do and the Nyquist point */
/********************************************************/
wr = f real[0] ;
real[OJ = wr + f img[0] :
f
_
f img[Oj = f img[Oj - wr :
/********************************************************/
for(i=0 : i < size ; i++)
out r [i] = f real [i] ;
- 61 -
CA 02505051 1997-10-O1
out i [i] - -f img [i] ;
_ _
)
/* end of if floating */
/********************************************************/
else
if(P fft math =- 2 )
- _
(
/* start of int fft */
length = 512 ;
half = 256 ;
halfpow = power - 1;
for (i = 0, j = 0; i < half; i++, j += 2)
1 real[i) _ (long) (in r[j] * 65536,0) ;
1_img[i] - (long) (in_r[j + 1] * 65536.0 ) ;
)
lmax = 0 ;
for (i = 0 ; i < half; i++ )
(
ltemp = 1 real[i] ;
if(ltemp < 0) ltemp = - ltemp ;
if (ltemp > lmax) lmax - ltemp ;
ltemp = 1 img[i] ;
if(ltemp < 0) ltemp = - ltemp ;
if (ltemp > lmax) lmax - ltemp ;
1
scale = 0 ;
for(i=O;i < 32 : i++)
(
lmax C= 1 ;
if (lmax < 0)
break ;
else
scale++ ;
)
scale--
~
scl = 1.0
;
for(i=0 ; i < scale ; i++)
scl *= 2.0 ;
lmax = 65536/(long)scl ;
for (i = 0 ; i < half; i++ )
(
i real[ij = (short) (1 real[iJ/lmax) ,
i_img[i] _ (short) (1 img'[i]/lmax) ;
)
/* do fft */
size = 256 ;
power = 8 ,
arginc = 2 ;
max bttr = size ;
scale = 0 ;
for (stage = 1; stage <= power; stage++) (
doit = 0 ;
for(j=0 ; j < size ; j++)
[ temp = (i real [j ] & (short) Oxc000) ;
if((temp != 0) && (temp !_ (short) Oxc00fl)j
( doit = 1 ;break; )
temp = (i img[j] & (short) Oxc000 ) ;
if((temp != 0) && (temp !_ (short)Oxc000))
( doit = 1 ;break; )
)
if (doit)
(
scale++ ;
- 62 -
CA 02505051 1997-10-O1
for(j=0 ; j < size ; j++)
real[j] /= 2 ,
( i
_
i_img[j] /= 2 ;
l
~ )
for(j=0 ; j < size ; j++)
{ temp = (i real[j] & (short) Oxe000)
if((temp != 0) && (temp !_ (short) Oxe000))
{ doit = 1 ;break; }
temp = (i img[j] & (short)Oxe000 ) ;
if((temp != 0) && (temp !_ (short)Oxe000))
{ doit = 1 ;break; }
if (doit)
scale++ ;
for (j=0 ; j < size ; j++)
real[j] /= 2 ;
( i
_
i_img(j] /= 2 ;
1
}
iarg = 0 ;
lix = max bttr;
max
bttr %= 2;
_
lmm = max bttr;
for(bttr = 1; bttr <= lmm; bttr++) {
is = (int) Cosine [iarg] ;
is = (int) - Sine [iarg] ;
iarg += arginc ;
for(li = lix; li <= size; li += lix) (
jll = li - lix + bttr - 1;
j2 = jll + max bttr;
real[jll} - i r~al(j2] ,
itl = i
_
it2 = i img[jll] - i img[j2] ;
real[jll] = i real[jll] + i real[j2] ,
i
_
img(jll] = i img[jli] + i img[j2] ;
i
_
real[j2] - (short) (((ic*itl) + (is*it2)) / 32768
i
_
i img(j2] _ (short) (((ic*it2) - (is*itl)) / 32768 ) ;
}-
}
arginc *= 2 ;
}
j = 0
for(i = 0; i < (size - 1); i++)
if (i < j ) (
tmp r = i
real[j] ,
_
tmp i = i
img [j ] ;
_
real[j] = i real[i] ;
i
_
img[j] = i img[i] ;
i
_
i real[i] = tmp_r ;
i_img [ i ] - tmp-i ;
}
k = (size / 2);
while (k < (j + 1) ) { j -- k; k /= 2; ]
j += k;
}
/********************************************************/
/********************************************************/
/* Perform even/odd separation algorithm. */
/* Form an array with N/2 + 1 elements. */
/********************************************************/
. k = 1 ;
for (i = 1, j = (half - 1); i <= j; i++, j--)
{
- 63 -
CA 02505051 1997-10-O1
/* wr => Costable[1..) wi => Sintable[1...] */
is = Sine[k]
is = Cosine(k] ;
itmplre = (int) ( (i real [i] + i_real [j ] ) 1 ) ;
itmplim = (int) ( (i img [i] - i img [j ] ) 1 ) ;
itmp2re = (int)((i img[i] + i-img(j]) 1 ) ;
itmp2im = (int) (- ( (i real [i) - i real [j] ) 1) )
~
i real [i] _ (short) (itmplre + ( (ic * itmp2re - is * itmp2im)
/ 32768));
i img[i] - (short) (itmplim + ( (ic * itmp2im + is * itmp2re)
/ 32768 )):
i real[j] - (short) (itmplre - (( is * itmp2re - is
itmp2im)/ 32768));
t) (- itmplim + ((ic * itmp2im + is
h
or
i img[j] - (s
itmp2re)/ 32768));
k++ ;
/***************************,~*~~**************************/
/* Compute the first pair of frequency cells, */
/* at the do and the Nyquist point */
/********************************************************/
is = i real [0] ;
real [0] = is + i img [0] ;
i
_
i img [0] = i img [Oj - is ;
/*********************~**********************************/
scl = 1.0 ;
for(i=0 ; i < scale ; i++)
sc1 *= 2.0 ;
for(i=0 ; i < size ; i++)
[
/*
r[i) _ (double) (i real[i] scale) ,
out
_
out i(i] _ (double) (-i-img[i] scale)
_
*/
out_r(i] _ (double) (i real[i] ) ;
i(i] _ (double) (-i img[i] )
out
_
r[i] *_ ((scl * (float)lmax)/65536.0) ;
out
_
out i [i] *_ ( (scl * (float) lmax) /65536.0) ;
_
/*
out_r(i] *= scl/(float)lmax ;
out_i [i] *= scl/ (float) lmax ; */
)
] /* end of int fft */
O valid out - 0.0 ;
q5 0 scales = (double) scale ;
) %* end !flag */
] /* end of run code */
~T'ERMINATION CODE:
I
if(P_fft math =- 1)
free (f real) ;
free (f img) ;
-
]
else
[
free (i real) ;
free (i img) ,
f see ( 1 real)
free (1 img) ;
)
- 64 -