Note: Descriptions are shown in the official language in which they were submitted.
CA 02557699 2006-08-16
2
A NETWORK BASED METHOD OF STORING AND USING WALLET OR PURSE
CONTENTS
The present invention is a method of storing, accessing, viewing and selecting
for use
contents stored on a networked computer server. The invention eliminates the
need to
carry a wallet, pocket or purse full of cards required to make transactions
and prove
membership to a merchant operated customer royalty or discounts scheme. The
invention
permits the owner to make a selection from the storage and use it for
transactions at a
brick and mortar merchant store, Automatic Teller Machine, cash dispensing,
payment
machine, or an online store
BACKGROUND OF THE INVENTION
There are various solutions aimed at reducing the number of cards one has to
carry in the
wallet, pocket or purse. However, the solutions have not been widely adopted
for reasons
such as cost to the consumer and merchants. The solutions require new hardware
and
software installations, as well as significant changes to the existing methods
of operation.
Following is a description of some of the solutions.
SpeedpassTMJ , available at some gas stations offers a service that links one
credit Card to
the Aeroplan T""2, and Esso Reward TM3 points cards. This eliminates the need
to swipe
both credit card and discount card at the pump. The system offers no option
for the
customer to make a selection of the card to use for payment, for example
should the linked
card be the over limit or customer wished to use a debit card. It is also
technology heavy,
meaning new hardware is required at the Point Of Sale. Customer carries a new
wireless
electronic key holder. A sensor is installed at every Point of Sale (POS) or
payment
machine.
Pocket Vault T""4, by Chameleon Network Inc. loads all wallet contents onto an
electronic
device that a customer carries in the pocket or purse. When needed, the touch
screen on
the Pocket Vault T""4 is used to select the item to be used from those loaded.
Owner identity
is verified by pressing a finger to the Pocket Vault T""4's fingerprint
reader. Pocket Vault TM4
CA 02557699 2006-08-16
3
50 will then release the Chameleon Card, imprinted with the information of the
card selected.
This is a technology heavy and expensive option. The information is accessed
from an
electronic device that user carries around, not from a Network Based Storage,
as is in this
invention.
There are other card- sized devices containing one or more integrated circuit
chips, which
perform the functions of a microprocessor, memory and an input/output
interface. The
cards come in different sizes and functions and may also be referred to as
"smart tokens",
"tags", "memory cards", etc. The cards have varied and differing functions,
including storing
personal information and wallet contents. They have been around for sometime
but have
6o not been widely applied for various reasons including cost of
implementation, and one may
end up having to carry multiple cards. In my invention, these type of cards
are used for
identification purposes only, as do magnetic strip cards, bar-code cards or
wireless
devices.
Electronic Wallet: Various devices have been tried in the past; for example
the following
Canadian patents:
CA 2197930 HITACHI, LTD. (Japan)
CA 2096730 MOTOROLA, INC. (United States)
They involve loading and replenishing information and funds onto an electronic
70 device that the owner carries around. My present invention does not include
storing funds
or information on an electronic device that customers carry around. Other
forms of
electronic wallets involve storing or loading funds onto a server based
storage, the funds
can then accessed, used and replenished from the storage to make purchases or
transferred to different accounts.
SUMMARY OF THE INVENTION
The present innovation maximizes returns from shopping discounts, reduces the
number of
cards carried around in the wallet, purse or pocket, while at the same time
using existing
80 and well tested technology. In some cases, firmware upgrade is required at
the Point Of
Sale (POS) terminal. There are benefits derived from having all cards in the
wallet, pocket
CA 02557699 2006-08-16
4
or purse such as knowing where the cards are at all times, having them in the
wallet
ensures that they are available when required. While shopping, merchants and
store
owners give royalty points and discounts, but one must show the relevant
membership
card e.g. Air Miles T""5, AeroplanTM2, Stapies TM6 dividends, shoppers optimum
T""7, etc to
qualify. The list is long. Stores also offer interest free credit for
purchases made using store
issued credit cards for short durations e.g. three to six months. There are
multiple issues
that are associated with carrying a wallet, purse or pocket full of cards.
These include:
= If the wallet is lost, then it is a tedious task reporting to different
issuers, maybe
90 even signing new forms and having to wait for replacements.
= If a credit card is stolen, then it can be used to defraud the card holder.
= It takes time to scan through a wallet full of cards at the check out
counter before
locating the correct payment card and relevant membership card, then having to
scan or swipe both.
= There are rewards to be made by utilizing available discounts, but the
management of the resulting multiple membership cards is cumbersome.
This invention also increases revenue for the retail stores. With the new
convenient
way of managing the wallet, customers are better positioned to take advantage
of retail
loo store incentives such as short-term interest free credit. This will result
in an increase on the
use of store issued credit cards, which means a reduction in the interchange
fees that
stores presently have to pay, as well as increased revenue from interest
charged on credit
card balances.
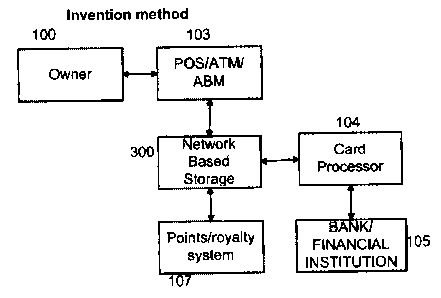
Referring to FIG 1 which represents the existing scenario, the owner 100,
while
paying for goods or services, reaches into the wallet 101, twice to get the
paying card 102,
and the discount or royalty card 106. The payment card is then swiped or
scanned on the
paying machine 103, and the information transmitted to the card processors
104. The
owner then presents the royalty or discount card 106, which is then scanned or
swiped
110 separately; the information is then transmitted to the discounts system
107.
The new invention leverages on the existing infrastructure to provide value
solutions
to both the card holder and merchants. The concept provides a safe and
convenient way of
managing the wallet, purse or pocket contents. Referring to FIG 7, in order to
subscribe to
CA 02557699 2006-08-16
the service, the owner 100, navigates to the Network Based Storage 300,
service
provider's website, pays the annual subscription fee, logs onto a secure
storage server and
enters required card numbers such as credit, debit, discount, air-miles, aero-
plan miles or
the like.
Referring to FIG 3, with the present invention in place, at a retail store or
gas station
while paying for the purchases; the owner 100, swipes, scans or provides a
designated
120 identification card at a payment system 103. The customer's Network Based
Storage 300,
is accessed through the communication systems. A list of pre-selected cards is
then
displayed to the customer on the payment system 103. The customer selects
which card to
use for payment (debit or credit). The Network Based Storage Manager will then
send
details on the selected card to relevant card processor 104. Discount, points,
or rewards
card details if any, are sent to the relevant system 107.
In the drawings, which form a part of this specification;
FIG. 1 is the existing setup, where the payment card and royalty cards are
handled
130 separately at the check out counter
FIG. 3 is the new setup (the invention), where only one card is swiped or
scanned
FIG. 5 is the network model
FIG. 7 is the setup and maintenance model network; this corresponds to the
network
represented by lines 504 on FIG. 5
FIG. 9 is a model for the transaction network; this corresponds to the to the
network
140 represented by lines 505 on FIG. 5
FIG. 10 shows the model server layout, corresponds to the to the network
represented by
line 506 on Fig. 5
FIG. 11 is the software flowchart
CA 02557699 2006-08-16
6
FIG. 13 is the software model, indicating the system actors
FIG. 15 is a use case, indicates when customer wants to open an account. It
corresponds
150 to 'owner 100' in FIG. 13
FIG. 17 is a use case, indicates customer at the checkout counter, ready to
pay for goods.
It corresponds to 'owner' in FIG 13
FIG. 19 is a use case, which indicates the merchant discount or royalty
program. It
corresponds to 'Royalty System 107' in FIG.13
FIG. 21 is a use case, which corresponds to the messaging devices 501 in FIG.
13
16o FIG. 23 is a use case, which corresponds to 'POS 103' in FIG. 13. This
represents
payment machines including Automatic Teller Machine (ATM), cash dispensing
machines,
and gas station machines.
FIG. 25 is a use case, which corresponds to the 'administrator 503' in FIG.
13. This
indicates the functions and tasks carried out by the administrator.
FIG. 29 and 31 are code listings in Visual Basic 2005.
Table 5 lists the server hardware specifications.
170
CA 02557699 2006-08-16
7
List of trade marks and owners
Trademark Owner
1 SpeedpassTM ExxonMobil Oil Corporation
5959 Las Colinas Boulevard
Irving, Texas
75039-2298
UNITED STATES OF AMERICA
2 AeroplanTM AIR CANADA,
P.O. BOX 7000,
POSTAL STATION ST-LAURENT,
MONTREAL,
H4Y 1J2
QUEBEC
3 Esso RewardsTM IMPERIAL OIL LIMITED,
111 ST. CLAIR AVENUE WEST,
TORONTO,
M5W 1K3
ONTARIO
4 Pocket VaultT"" Chameleon Network, Inc.
30 Monument Square,
Concord,
MASSACHUSETTS, 01742
Air MilesTM Air Miles International Trading B.V.
Papelaan 85-W
2252 EG Voorschoten
NETHERLANDS
6 StaplesTM Staples, Inc.
500 Staples Drive
Framingham, Massachusetts, 01702
UNITED STATES OF AMERICA
CA 02557699 2006-08-16
8
7 Shoppers OptimumTM SHOPPERS DRUG MART INC.,
243 Consumers Road,
Toronto,
ONTARIO M2J 4W8
8 Microsoft TM, WindowsTM, Windows MICROSOFT CORPORATION,
ServerTM, ONE MICROSOFT WAY,
Visual BasicTM, Visual StudioTM, REDMOND, WASHINGTON 98052-
6399,
UNITED STATES OF AMERICA
DETAILED DESCRIPTION OF INVENTION
The invention consists of two basic steps, the first being setup and
maintenance, the
second is usage. The basic steps vary between the customer and merchant. The
first step
is represented by Fig 7, Fig 9's owner 100, Fig 15 and Fig 17. The second step
is
represented by Fig 9's POS 13, Fig 11, Fig 19, Fig 21, Fig 23, Fig 25, and Fig
27.
180
The key operational elements shown in FIG. 9 are network access, routers and
access Control, storage database and application servers. 'Failover' is
implemented for
each of the critical elements. Users access the service from the internet
using protocols
such as the widely used TCP/IP. The merchants access the system by a variety
of
protocols including Plain old telephone service (POTS) analog modems, ISDN and
TCP/IP.
The system interfaces with existing payment processing systems. The network is
implemented to meet the following key requirements:
Total availability by enabling services and applications in the server cluster
to
continue providing service during hardware or software component failure or
during
190 planned maintenance
High scalability by implementing servers that can be expanded with the
addition of
multiple processors and additional memory
Superior manageability by enabling administrators to manage devices and
CA 02557699 2006-08-16
9
resources within the entire cluster as if they were managing a single computer
Hardware implementation of the Network Based Storage is shown on FIG 10, based
on Windows Compute Cluster Server 2003 Architecture. A Server cluster provides
high
availability by making application software and data available on several
servers lin~ed
together in a cluster configuration. If one server stops functioning, failover
process
automatically shifts the workload of the failed server to another server in
the cluster. The
200 failover process is designed to ensure continuous availability of critical
applications and
data. Table 5 lists the hardware specifications. This list is not exhaustive
and may vary
depending on available technology and changing system requirements.
Security is of critical importance for this service. The 'Payment Card
Industry Data
Security Standard' guidelines are followed for setting up the network. Windows
TM8
Communication Foundation provides the security features that the distributed
system
needs. These are confidentiality, integrity, and authentication. Authorization
Manager
(commonly known as AzMan) is a role-based security architecture for Microsoft
Windows
TM8 Role-based authorization is used on the various middle-tier components
including
21o ASP.NET Web applications.
The process starts when the customer or cardholder navigating to the NETWORK
BASED
STORAGE provider's website, Fig7. The website has information relating to the
service
that is of interest to the customer such as how the system works, online
security, and sales
pitch. The customer then navigates to a shopping cart, selects from a list of
features, those
that they wish to pay for.
The customer is then directed to a secure website, Fig 15 Banking System 1500,
and pays
the required service fees by any acceptable form of online payment. The system
then
creates an account for the customer. The customer is then asked to enter a
primary
220 contact email address. This email address is important and can only be
changed through a
two step processes. An email is then sent to this address, with instructions
on how to
proceed and an account number. The Customer is requested to check for a link
to enable
them complete the setting up of the account. On navigating through the link,
the customer
is connected to a sure server and prompted to create a user name and password.
The
password must have at least three different types of characters and be six or
more
CA 02557699 2006-08-16
characters in length. The customer will designate an identification card, one
that has a
photo on it, as the one card they will be using to access the NETWORK BASED
STORAGE at a merchant's store, Automatic Teller Machine (ATM), payment
machines or
cash dispensers. An account can have more than one designated card. They will
then
230 enter details on other cards such as numbers, dates, names, phone numbers
etc.
The customer will be able to administer their Network Based Storage by
entering user
name and password. Each time the account is accessed from the internet, an
email will be
sent to the primary email address, notifying the account holder of the same.
The customer
can add or remove any other information by simply logging into the account
except the
primary email contact. To change the email contact, the customer will first
make a request,
and then a link will be sent to the primary email address. By following this
link, the
customer can then change the primary email address.
Referring to Figure 5, the customer accesses the system over the internet from
any
internet-enabled device such as PC, laptop, Personal Digital Assistant (PDA)
or wireless
240 phone.
Thus far, the technology, software, database design and normalization and the
steps
described above can be implemented with various changes and modifications
without
departing from the scope of the invention as defined in the claims.
The owner, at a brick and mortar or walk in store; will pick up items then
proceed to
the checkout counter. The items will be scanned, and the total displayed. At
this point the
customer will indicate that they will be using the Network Based Storage to
retrieve
payment card. The customer's designated identification card, will then be
swiped,
scanned or the number keyed-in. referring to FIG3, FIG5, and FIG 9 at the POS
(103). The
250 store system will setup a call or link to the Network Based Storage.
Authentication on the
server is carried out by way of any of the well established methods.
Referring to FIG 11, the software flowchart, the Network Based Storage
software,
step 1100, retrieves the designated identification card number and the store
ID number.
With the designated identification card number, the customer's list of paying
cards is
retrieved, step 1101, and the store ID is used to retrieve the list of cards
acceptable to the
store, step 1102. The two lists of cards are then compared; step 1103,
matching owner list
to the store list, and a pre-selected list is made up. This list is then sent
to be displayed to
CA 02557699 2006-08-16
11
the customer, step 1104. During the pre-selection process, the system carries
out several
pre-defined steps before displaying Storage contents to the owner. Such steps
include if no
260 matches are found, then customer will be notified. If the customer selects
to use a debit
card, or it is the only option in the pre-selected list, the customer will be
prompted to enter
PIN number. This information is then sent to card processing companies, step
1105.
During the pre-selection process, if the customer has a rewards account that
is associated
with the merchant, this information is retrieved and sent to the relevant
system, step 1106.
If not, and the store operates such a scheme, then the store clerk is alerted
by a message
so they can introduce the customer to the scheme.
If the customer has subscribed to the notification feature, then a message
will be sent to
the relevant interface device e.g. email server, fax server, phone system, or
Short Message
Service (SMS) server.
270
The software model is shown on FIG 13. The following are the functions of the
system.
1. Store owner 100's information and provide it on request, necessitate
selection
of payment cards and send relevant messages
2. Interact with a POS 103 or payment, banking or cash machines: receive owner
card number, send back multiple card numbers
3. Provide store system 107 with royalty membership information
4. Send transaction details to (e.g. card number, date, amount etc) to card
processing company 104. Switch (connect) POS 103 to card processing server
104.
280 5. Administrator 503 enters manual data, monitors and maintains system
6. Messaging system 501: notify owner 100 each time service is accessed by
email, Short Message Service (SMS) , phone, fax
7. Logic 1300: makes decisions e.g.: customer service entitlements, account
status
etc
Scope of work for each character:
Owner 100: provides and receives data
POS 103: provides and receives data
Royalty system 107: receives data
CA 02557699 2006-08-16
12
290 Card processing company 105: provides and receives data
Messaging devices 501: receives data
Administrator 503: provides and receives data
Logic 1300: provides, receives and processes data
Key features of the software:
Security is a key and critical feature; it is incorporated at every stage of
the software design
and development
High transaction speed and performance at the lowest cost
Continuous availability and zero latency, keeping pace with industry trends of
increasing
300 transaction volumes, demand for higher transaction speed and security
Key components:
Infrastructure connectivity services
Processing services
The software can be implemented using a variety of software tools, databases,
operatirlg
systems, and connectivity and security tools running on hardware from
different venoQrs.
The high performance required for this innovation is achieved on a
MicrosoftT""$ software
plafform comprising Windows ServerTM$, NET framework, IIS and SQL Server.
The database consists of different tables containing customer contacts and the
Storage contents. Tables' tbl walletcontents, tbI_ transactcards and tbl_
merchantcards
310 are accessed during the use stage of THE NETWORK BASED STORAGE MANAGER.
Table tbl walletcontents contains Storage owner cards, table tbl_
transactcards contains
list of cards the storage owner uses to make purchases and table tbl_
merchantcards
contains list of cards accepted by the merchant.
For faster access and execution, the application is implemented as a service,
and
the data resides in memory. Figure 9 shows the Transaction network layout
while Figure 11
shows the software flowchart.
Creating the service
A Windows TM8 service is a special type of application that runs in the
background
:32o and has no user interface. The service runs with no user logged onto the
service, as soon
as the operating system is started.
CA 02557699 2006-08-16
13
A Windows TM8 Service project in Visual Basic NET is created by selecting
File, New
Project, and then Windows T""$ Service. The system provides overrides for the
OnStart and
OnStop methods. The relevant code is added to these methods. Other additional
overrides
that are necessary such as for the OnContinue and OnPause methods are also
implemented. The proper parameters, for instance, CanPauseAndContinue must be
set to
True for the service to be able to accept those events. The code to initialize
and start the
NETWORK BASED STORAGE MANAGER is inserted in the OnStart method.
An installer is required to register the service on the system registry. To
add an installer,
330 right click on the windows TM8 service design palette. The service run on
the LocalSystem
account, and set to automatic start-up.
A deployment project is required to deploy the service to the required server.
To create a
deployment project, first, a deployment project is added to the solution
containing the
service project. Then a Custom Action for the primary output of the Windows
TM8 Service
project is created. To do this: Right-click on the deployment project and
select View I
Custom Actions. Then right-clicking on the 'Custom Actions' and selecting 'Add
Custom
Action'. When the dialog box opens, double-click the Application folder and
select the
primary output from the Windows TM8 Service project. It will add this custom
action to all
four installer actions: Install Commit, Rollback, and Uninstall.
340 The invention software is implemented using a wide range of class objects
for well
known reasons such as: Calculations or operations are encapsulated (wrapped-
up) into an
easy-to-use interface. It is easy to change the internal workings of a class
object to make it
perform better as demands and requirements change. Multiple instances of a
class object
can be active in memory at one time. It is possible to implement inheritance
without
changing the original classes.
The service initializes a class object clsWalletContents. The class is
designed to
open the database, read relevant data from table tbl walletcontents and keep
it in memory.
Creating a class in Visual BasicTM$.NET
350 Begin by creating a windows application with a form as follows:
1. Opening Visual Studio TM8 NET.
2. Selecting Visual Basic TM8 Project from the tree-view on the left-hand side
of the
screen.
CA 02557699 2006-08-16
14
3. Selecting Windows T""$ Application as the project template.
4. Setting the name of the application
Next creating the class object:
1. Open the 'Add New Item' dialog box by clicking 'Project' and then clicking
'Add
Class'.
360 5. Set the Name property and click OK.
2. A new file appears in the project and a code window within the Visual
Studio TM8
.NET environment. In the Code window, there will be some code that looks like
this:
3. Public Class (Name)
End Class
All of the properties and methods created for this class must be entered
between
these lines of code.
Creating class object properties:
The keyword 'Property' is used, followed by a name of the property, and then
the
370 type of data this property will return or set. To return the data
contained in a private
variable, code to be executed is placed in a'Get... End' block. The 'Return'
statement is
used to return data.
The class is compiled as a DLL by right clicking on the project name and
selecting
'Build'. The DLL that results from the build command is placed into the \bin
directory
immediately below the.NET project directory.
The new class object (.dll) is implemented in an application as follows: On
the
'Project' menu, 'Add Reference.' is selected. The 'Projects' tab is selected
followed by
'Browse tab' to locate the component DLL required. Example of code to
initialize class
object:
380 Dim listofcards As New clsWalletContents.walletcontents
Where cisWalletContents is the class object (.dll) and walletcontents is a
method in the
class.
The service also initializes and opens standard TCP/IP communications port.
Connections
from merchants are directed to this port. Reference FIG 11, 'receive call' and
Code Listing
5. The code to handle incoming request is a class object which retrieves
information such
CA 02557699 2006-08-16
as storage owner ID and merchant ID from the request. Reference FIG 11, 'get
list of
customer cards' and code listing 7. These pieces of information are then
forwarded to other
class objects that carry out varying functions such as authentication and
storage contents
pre-selection.
390