Note: Descriptions are shown in the official language in which they were submitted.
CA 02647684 2008-09-29
WO 2007/128134 PCT/CA2007/000821
SECURE WIRELESS GUEST ACCESS
FIELD OF THE INVENTION
The present invention relates generally to IP communication networks and, more
particularly, to a solution that enables ad hoc digital certificate
provisioning and
secure connectivity over wired and wireless IP communication networks while
maintaining ease of use for users and control for network providers.
1o BACKGROUND OF THE INVENTION
The continued expansion of digital networks such as the public Internet and
local area
networks (LANs) coupled to the increasing popularity of digital data
communication
have, for many users, transformed Internet and LAN connectivity from a mere
convenience to a necessity.
In their daily work, professionals have come to rely on applications such as
email,
access to a home network file server or an online database, in addition to
other
applications and communication capabilities that cannot function without web
access.
Those users expect such connectivity at their office but also when they are
guests at a
corporation with which they have no prior or permanent relation. Examples of
guests
include a consultant visiting her client's office or a student interning for a
few weeks.
Users are now also asking for wireless connectivity. In the early stages of
the Internet
and LAN expansion, users for the most part connected their personal computer
over a
wired line using standards such as IEEE Ethernet 802.3. More recently,
wireless
communications standards such as IEEE 802.11 and the upcoming IEEE 802.16 and
IEEE 802.20 have made wireless connectivity ubiquitous. It is now common for
users
to connect their portable computers such as laptops and personal digital
assistants
(PDAs) to wireless local area networks (WLANs) at airports, hotels, cafes,
corporate
offices and so on.
CA 02647684 2008-09-29
WO 2007/128134 PCT/CA2007/000821
2
As a result of the strong demand for network connectivity, a number of
corporations
have recognized the need to enable guest access within their IT
infrastructure. Most
corporations however are reluctant to meet the demand for wireless
connectivity
mainly because of the perceived security risks posed by the deployment of a
wireless
infrastructure.
In several aspects, wireless networks are more prone to security breaches than
their
wired counterparts. Data confidentiality is perhaps the most relevant issue
with
wireless transmissions since tapping onto wired links would necessitate
physical
access to the telephone and cable infrastructure of an Internet service
provider's (ISP)
network equipment; on the other hand, a malicious user with a high gain
antenna can
stand across the street from a corporation's offices and capture WLAN data
traffic.
A security breach through a wireless access point may enable malicious hackers
to
access restricted network resources, read the content of legitimate users'
data traffic
or even utilize the corporation's network as a platform for illegal
activities.
Consequently, the corporations' desire to satisfy their guests' demand for
wireless
connectivity is often outweighed by the risks we just described. This is
especially the
case for corporations handling medical, legal, financial, or government
information
since current or upcoming legislation in the United States, Canada and Europe
imposes severe penalties for mishandling such data.
Beyond the security considerations for wireless connectivity, corporations
often
demand a minimum of trust in the identity of the guests to whom they are
offering
network access. Even if guests are only allowed access to the Internet without
any
right to use the internal network, those guests are still using the host
corporation's
resources to access the web. This implies that malicious or illegal behavior
on the
guest network may raise liability issues for the corporation. For example, a
guest user
may send spam emails, initiate denial of service attacks or participate in
illegal trading.
It is therefore imperative to ensure sufficient trails are recorded to permit
tracing back
a given network traffic pattern to a particular person in real life.
CA 02647684 2008-09-29
WO 2007/128134 PCT/CA2007/000821
3
In fact, corporations sometimes like to provide some guests with controlled
access to
some parts of their firewall protected internal network; this is in addition
to regular
Internet access. Such guests may need to access a file server in the internal
network,
use the corporation's printers or query some database content. In this case,
the need
for trusting the guest identity is even more stringent.
From a system perspective, many corporations require two major components for
their guest access solution: first, a trust management capability that enables
the
identification of the guests with some level of confidence; second a network
security
capability that enables encrypting data traffic and ensuring that only
legitimate users
have access to information traversing the corporation's network, whether wired
or
wireless.
From a feature perspective, corporations may ask for a number of
characteristics for
their guest access solution. Those include limited burden to their information
technology (IT) staff; no risk to the internal network; compliance with
applicable
government regulations (especially when it comes to liability for unlawful
guest
behavior or privacy protection of sensitive information); and the ability for
guests to self
configure their accounts and connectivity without the help of corporation
staff.
Generally speaking, corporations regard guest access as a courtesy offering
that IT
staff needs to have visibility into and control onto should anything go wrong
but which
they can leave functioning with little or no intervention under otherwise
normal
circumstances.
In short, many corporations ask for trust management and network security as
the
underlying building blocks for their guest access solution. Since those
building blocks
can be implemented in multiple manners, corporations further ask for a number
of
features such as the ones listed above, that make some implementations
preferred
over others.
A number of wireless guest access solutions are presently available to
corporations.
One of the most popular approaches is to simply open network access to any
user,
CA 02647684 2008-09-29
WO 2007/128134 PCT/CA2007/000821
4
whether known or unknown. While such a scheme enables ease of use and instant
connectivity for guests, it does not offer any form of identity verification,
and therefore
poses security threats to the underlying corporate network.
In terms of trust management, one approach consists in forcing guests who
attempt
access within a wireless local area network (WLAN) hotspot to go through a web
based registration page. Users are instructed to provide varying levels of
personal
information such as name, email address, telephone number, and others. Users
are
then granted access through the account that has been created for them by the
system based on the information they have provided. While convenient for the
users
and IT staff, such a setup in fact provides no verification of guest identity
since users
may intentionally provide false information upon registration and no attempt
is made
by the system to validate their identity.
Another approach to ensure trust management consists in IT staff on site
providing
temporary guest identification tokens. This method may provide identity
verification
since guests may have to at least provide their name to obtain a token.
However, it
introduces the cost of assigning IT staff to this task and may also not be
convenient for
a number of users.
In terms of network security, one approach is to restrict guest access to a
dedicated
virtual local area network (VLAN) or a separate network altogether. Although
such a
scheme significantly reduces the threat to the internal corporate network, it
makes it
complicated to enable controlled guest access to specific parts of the
internal network.
Still in terms of network security, one method is to use the wired equivalent
privacy
(WEP) standard to secure wireless communication. Although WEP has been around
for a several years, a number of flaws have recently been identified in its
key
management and encryption techniques. As a result, the WEP authentication and
encryption scheme is currently considered insecure by most experts.
CA 02647684 2008-09-29
WO 2007/128134 PCT/CA2007/000821
Another approach to secure wireless links is to use Wi-Fi protected access
(WPA) or
its more recent version WPA2. Those wireless security standards address the
vulnerabilities of WEP and are standardized by the institute of electrical and
electronics engineers (IEEE) in standard IEEE 802.11 i. IEEE 802.11 i includes
IEEE
5 802.1x, an authentication protocol which prevents unauthorized access to the
network
and protects from a number of security attacks. IEEE 802.1x supports several
authentication schemes including EAP-TLS. The strength of EAP-TLS lies in the
fact
that a compromised password is not sufficient to break into the system. EAP-
TLS is
widely considered as the highest grade civilian security technology available
to date
and is supported by a large part of major wireless equipment manufacturers.
The IEEE 802.11 i technologies and EAP-TLS are well suited to provide network
security across a wireless network access.solution; however, EAP-TLS requires
each
user to possess his own digital certificate. This brings into the picture an
additional
component: the public key infrastructure (PKI).
PKI refers to the set of software, protocols and policies that enable users to
communicate securely over a public, non-trusted, network using public key
encryption
technology. At the heart of PKI is the need to provide each individual user
with a
private and public key pair. Those keys usually consist of strings of letters
and
numbers mathematically chosen such that a message encrypted with one of them
can
only be decrypted using the other. In addition, for security purposes, public
keys must
be unequivocally linked to identities in the real world. This is accomplished
using
digital certificates.
Digital certificates are text files organized in special format (e.g. using
the X.509
certificate standard by the International Telecommunication Union) containing
a public
key and unique identification information of its owner. Certificates are
issued by
trusted third parties known as certificate authorities and are
cryptographically signed
by those authorities in a way that does not allow tampering.
CA 02647684 2008-09-29
WO 2007/128134 PCT/CA2007/000821
6
To issue a trustworthy digital certificate within a secure wireless access
system, the
PKI component of the system needs to verify the identity of the guest. This is
where
trust management joins network security and where one of the advantages of the
present invention lies.
SUMMARY OF THE INVENTION
The present invention discloses a network authentication mechanism that
enables
and facilitates ad hoc and trusted digital certificate provisioning coupled to
secure
user access to wireless and wired IP communication networks through state of
the
art security communication standards. The system includes a user equipped with
an electronic terminal and a personal characteristic where the electronic
terminal
initially creates a temporary unsecured connection to the network. The user
typically accesses an authentication interface through his electronic terminal
to
provide a unique identifier associated with his personal characteristic. The
authentication interface communicates with a validation entity that verifies
the
user's privileges based on his unique identifier and if authorized grants the
user a
digital certificate linking his asymmetric cryptography public key to the
unique
identifier associated with his personal characteristic. The user's electronic
terminal
will subsequently utilize the digital certificate to establish a secure
connection with
the network and gain secure access to network resources. The unique identifier
is
characterized by the fact that it relates to a personal characteristic whose
relationship with the user had previously been established through a trusted
third
party. A preferred embodiment is for the authentication interface to be one or
more web pages and users' personal characteristic to be a cellular telephone
account whereby the unique identifier is the cellular telephone's number. The
relationship between the user and his cellular telephone account must have
been
previously established with his mobile telephony provider. The user
communicates
through a laptop computer, or personal digital assistant (PDA) or IP telephone
with a web based authentication interface to provide his cellular telephone
number. The validation entity consists of database servers; authentication,
authorization and accounting (AAA) servers and PKI servers. The validation
entity
CA 02647684 2008-09-29
WO 2007/128134 PCT/CA2007/000821
7
will verify the existence of an account indexed by the cellular telephone
number. If
no account exists, it will create one, and generate a corresponding password.
If an
account exists, it will retrieve the password. In both cases, the password is
then
transmitted to the cellular telephone number of the user through SMS. The user
will now enter both his cellular telephone number and received password into
the
web authentication interface. Transparently to the user, his electronic
terminal will
generate one private key and the corresponding public key as necessitated by
the
particularities of public key cryptography. The user's electronic terminal
will further
transmit the public key to the validation entity through the authentication
interface.
The validation entity will verify that the cellular telephone number and
password
match those specified in the account. If they do, the validation entity will
utilize the
public key sent by the electronic terminal to generate and digitally sign a
digital
certificate linking the user's cellular telephone number to his public key.
The
validation entity then transfers the digital certificate to the authentication
interface
which in turn seamiessly installs it on the user's electronic terminal. The
user's
electronic terminal will disconnect the existing unsecured connection with the
network and re-authenticate with the authentication interface using the newly
acquired digital certificate. As a result, the user will establish a secure
connection
that enables him to gain access to network resources such as the Internet or
other
local servers and electronic equipment. An additional result is that the
network
administrators have established some trust in the identity of the user since
he has
proven possession of the cellular telephone associated with the cellular
telephone
number he indicated (otherwise he could not have retrieved the password);
moreover, a cellular account is generally granted by mobile telephony
operators
after a minimum level of user identity verification using utility bills, bank
statements, identity cards and so on.
In another embodiment, a variation of the mechanism detailed above involves a
personal characteristic as being a personal relationship between the user and
some person affiliated to and trusted by the corporation. Such a person is
also
known as a sponsor. In this case, users do not provide their cellular
telephone
number to the authentication interface but instead use as unique identifiers
their
CA 02647684 2008-09-29
WO 2007/128134 PCT/CA2007/000821
8
own email address along with the name, or the email address, or the cellular
telephone number of the sponsor. In parallel a notification message is sent by
the
system to the sponsor requesting approval for the user's utilization of
network
resources. If the sponsor validates the request, a one time password is
generated
by the system and sent to the user's email address. The user then uses his
electronic terminal to retrieve the one time password and provide it to the
authentication interface. Depending on the implementation, the user may also
be
asked to enter again his own email address and that of the sponsor.
Transparently
to the user, his electronic terminal will generate one private key and the
corresponding public key as necessitated by the particularities of public key
cryptography. The user's electronic terminal will further transmit the public
key to
the validation entity through the authentication interface. The validation
entity will
verify that the user's email address and password match those specified in the
account. If they do, the validation entity will utilize the public key sent by
the
electronic terminal to generate and digitally sign a digital certificate
linking the
sponsor's name, or email address, or cellular telephone number to the user's
public key. The digital certificate will preferentially include other
information that
may have provided by the user to the authentication interface such as a name.
The validation entity then transfers the digital certificate to the
authentication
interface which in turn seamiessly installs it on the user's electronic
terminal. The
user's electronic terminal will disconnect the existing unsecured connection
with
the network and utilize the newly acquired certificate to re-authenticate with
the
authentication interface. As a result, the user will establish a secure
connection
that enables him to gain access to network resources such as the Internet or
other
local servers and electronic equipment. In addition, the network
administrators
have established some trust in the identity of the user since a sponsor has
vouched for him.
Other systems, methods, features and advantages of the invention will be, or
will
become, apparent to one with skill in the art upon examination of the
following
figures and detailed description. It is intended that all such additional
systems,
CA 02647684 2008-09-29
WO 2007/128134 PCT/CA2007/000821
9
methods, features and advantages be included within this description, be
within
the scope of the invention, and be protected by the following claims.
BRIEF DESCRIPTION OF THE DRAWINGS
The novel features which characterize the invention are set forth in
particular in
the appended claims. The invention itself both in terms of construction and
ways
of operations will be best understood from the following description of
specific
embodiments read in pair with the accompanying drawings.
FIG. I is a system-level block diagram of the ad hoc and secure guest
authentication
mechanism.
FIG. 2 provides a high-level view of the buildings blocks underlying a
wireless guest
access infrastructure.
FIG. 3 provides a high-level view of an alternate way to assemble building
blocks
within a wireless guest access infrastructure.
FIG. 4 provides a flowchart for a user obtaining a digital certificate using a
cellular
telephone number as unique identifier.
FIG. 5 depicts a system-level block diagram of a variation on the ad hoc and
secure
guest authentication mechanism in FIG. 1.
FIG. 6 provides a flowchart for a user obtaining a digital certificate using a
sponsor's
email address as unique identifier.
FIG. 7 illustrates the establishment of a secure wireless session with EAP-
TLS.
FIG. 8 shows a system-level block diagram of a user accessing internal
resources
within a corporation's network within the framework of the wireless guest
access
infrastructure.
DETAILED DESCRIPTION OF THE PREFERRED EMBODIMENTS
OF THE INVENTION
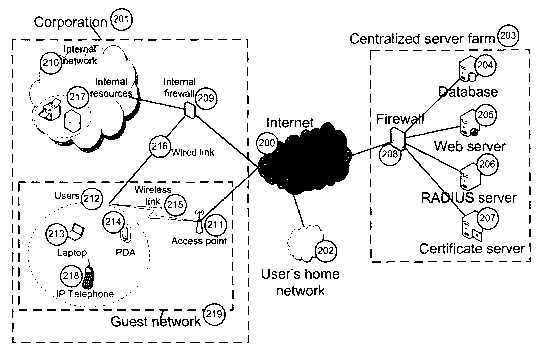
Referring collectively to FIGs. I and 2, the present invention discloses an ad
hoc and
secure guest authentication system 100, for use in a controlled corporation
network
CA 02647684 2008-09-29
WO 2007/128134 PCT/CA2007/000821
201, which is preferentially an IP access network. The ad hoc and secure guest
user
authentication system 100 includes an authentication interface 104, which
allows a
user 101 to authenticate with a validation entity 105, install a personal
digital certificate
on his electronic terminal 103 and use it to gain access to network resources
106 such
5 as the Internet 200. The authentication interface 104 and validation entity
105
exchange information about the user 101. Electronic terminals 103 typically
consist of
a computing device capable of accessing network resources 106 over a variety
of
network connections such as wired 216 or wireless 215 links. Various types of
electronic terminals 103 are also supported by the system 100 such as laptop
10 computers 213, personal digital assistants (PDAs) 214 or IP telephones 218.
In order
to access network resources 106, a user 101 provides a unique identifier
associated
with his personal characteristic 102 to the authentication interface 104. In
turn, the
authentication interface 104 communicates with the validation entity 105 that
verifies
the existence of an account associated with the personal characteristic 102,
or creates
an account and password if no previous one exists. The validation entity 105
then
communicates the password to the user 101 using his unique identifier. The
user 101
then provides the unique identifier described above and the newly acquired
password
to the authentication interface 104. At the same time, and preferentially
seamlessly to
the user, the electronic terminal 103 generates a private key and the
corresponding
public key as necessitated by the particularities of public key cryptography.
The user's
electronic terminal 103 will further transmit the public key to the validation
entity 105
through the authentication interface 104. The validation entity 105 will
verify that the
unique identifier and password match those specified in the account. If they
do, the
validation entity 105 will utilize the public key sent by the electronic
terminal 103 to
generate and digitally sign a digital certificate linking the user's unique
identifier to his
public key. The validation entity 105 then transfers the digital certificate
to the
authentication interface 104 which in turn installs it on the user's
electronic terminal
103. Those skilled in the art will recognize that digital certificates may
also be installed
on other media such as external hard disk drives, USB keys, floppy disc
drives, DVD
discs, compact discs and others. The electronic terminal 103 will utilize the
newly
acquired certificate to authenticate with the authentication interface 104,
create a
secure network connection and gain access to network resources 106.
CA 02647684 2008-09-29
WO 2007/128134 PCT/CA2007/000821
11
The ad hoc guest user authentication system 100 could be used with various
types of
personal characteristics 102 such as a cellular telephone account or a
personal
relationship with someone affiliated to and trusted by the corporation network
201 and
known as a sponsor. In effect, the trust relationship previously established
between
the user 101 and her mobile telephony provider or her acquaintance in the
corporation
network 201 enables the system 100 to issue the user 101 a trustworthy digital
certificate. The digital certificate will link the user's public key to the
unique identifier
associated with her personal characteristic. The user 101 can utilize the
digital
certificate to authenticate with the system 100 and gain access to network
resources
such as the Internet 200 or internal resources 217 situated within the
internal network
210 of the corporation 201.
Referring to FIGs. 1 and 2, the user 101 is preferentially a guest user 212
within the
guest network 219. The guest user 212 may utilize a variety of electronic
terminals
103 such as a laptop 213, a PDA 214 or an IP telephone 218. Those skilled in
the art
should recognize that other types of electronic terminals may be used as well.
The
guest user 212 may connect through a wired link 216 or a wireless link 215
powered
by an access point 211. Through those links, the guest user 212 can access the
Internet 200. The guest user 212 may also use his electronic terminal 103 to
connect
to his home network 202 over a virtual private network connection or other
remote
network connection techniques (not illustrated).
Referring collectively to FIGs. 1, 2, 3 and 4, in a preferred embodiment, the
authentication interface 104 can be seen as a web interface residing on web
server
205 that belongs to a centralized server farm 203. The validation entity 105
is also
preferably implemented through a combination of a database server 204, a
RADIUS
server 206, and a certificate server 207 that all belong to the centralized
server farm
203. The database 204, web 205, RADIUS 206, and certificate 207 servers are
preferentially centralized in the server farm 203, but can also be distributed
across a
number of locations communicating over the Internet 200; some or all of the
servers
may also be located within the corporation network 201 in an internal server
farm 304.
CA 02647684 2008-09-29
WO 2007/128134 PCT/CA2007/000821
12
Those skilled in the art will recognize that the servers do not necessarily
need to be
physically separate entities; furthermore, the RADIUS server which serves at
the
backbone for authentication, authorization and accounting (AAA) within the
system
100 may be replaced by other AAA protocols such as PANA or DIAMETER. The user
101 establishes a temporary unsecured connection with the network. Such
connection
is preferentially restricted to a dedicated network that does not permit
access to the
Internet or other network resources; instead, the dedicated network only
permits a
user to authenticate with the system 100 and obtain a digital certificate. The
user 101
initially starts a web browser session on his electronic terminal 103 and
requests some
web page at step 401. The web server 205 redirects the user's browser request
to the
authentication web interface at step 402. At step 403, the user 101 inputs the
unique
identifier associated with his personal characteristic 102 on the web
interface residing
on web server 205. This latter then communicates the unique identifier to the
RADIUS
server 206 at step 404. At step 405, the RADIUS server 206 verifies with the
database server 204 whether an account for this user 101 already exists. If
not, an
account is created at the database server 204 and a password for this account
is
generated. If an account already exists, the associated password is retrieved.
The
RADIUS server 206 then transmits this password to the user 101 using the
unique
identifier associated with his personal characteristic 102; in a preferred
embodiment,
the personal characteristic is a cellular telephone account whose unique
identifier is
the cellular telephone number; the password is sent by the RADIUS server 206
through the short message service (SMS) at step 406. At step 407, the user 101
inputs his cellular telephone number and the password just received by SMS
into the
web interface residing on the web server 205. In parallel, the user's
electronic terminal
103 generates a private and public key pair in accordance with the rules of
public key
cryptography. The electronic terminal 103 further transmits the public key to
the
authentication interface 104 at step 408. At step 409, the web server 205
transfers the
cellular telephone number and password input by the user 101 to the RADIUS
server
206. In turn, the RADIUS server validates the credentials with the database
server
204 at step 410. If the information matches the existing account, the RADIUS
server
206 communicates the cellular telephone number and the user's public key to
the
certificate server 207 at step 411. In turn the certificate server 207
generates and
CA 02647684 2008-09-29
WO 2007/128134 PCT/CA2007/000821
13
digitally signs a digital certificate linking the user's public key to his
cellular telephone
number. The certificate server 207 then transmits the certificate to the web
server 205
at step 412. The web server 205 installs the certificate on the user's
electronic terminal
103 at step 413. Finally, the electronic terminal 103 disconnects the
temporary
unsecured connection and uses the newly acquired digital certificate to
authenticate
again with the centralized server farm, establish a secure networking session
and gain
access to network resources 106 such as the Internet 200 through his
electronic
terminal 103 that is preferentially a laptop 213 or PDA 214 or IP telephone
219. Those
skilled in the art should recognize that other arrangements between the
various
servers in the centralized server farm 203 can also be used to achieve the
same
functionalities disclosed above. For example, the database server 204 may hold
the
logic necessary to communicate with the certificate server 207 instead of
going
through the web server 205 and so on.
In the preferred embodiment disclosed above, the personal characteristic 102
is a
cellular telephone account and the unique identifier is a cellular telephone
number.
Those skilled in the art will recognize that the personal characteristic can
also consist
in a variety of personal communication accounts with unique identifiers such
as pager
accounts with unique pager numbers, mobile fax machine accounts with unique
cellular fax numbers, email accounts with unique email addresses, mobile IP
telephone accounts with unique IP telephone numbers and so on.
In another preferred embodiment and referring to FIG. 5, the personal
characteristic
102 of the user 101 is a relationship with a person known both to the user 101
and the
corporation 201. Such a person can be referred to as a sponsor 500. In this
embodiment the unique identifier is preferentially the email address of the
sponsor.
The authentication interface 104 asks the user for his unique identifier
associated with
his personal characteristic, in other words, the authentication interface 104
asks the
user for the email address of his sponsor. The authentication interface 104
also asks
the user 101 for his email address. The authentication interface 104 transmits
the
email address of the sponsor and that of the user 101 to the validation entity
105. In
turn, the validation entity 105 notifies the sponsor 500 using his email
address. The
CA 02647684 2008-09-29
WO 2007/128134 PCT/CA2007/000821
14
sponsor 500 replies to the email message to recognize or not his relationship
with the
user 101. The validation entity 105 receives the sponsor's response and if
positive
generates a one time password and sends it to the user's email address. The
user
101 retrieves the one time password and submits it to the authentication
interface 104
along with his email address. In addition, the user's electronic terminal 103
generates
a private and public key pair along the rules of public key cryptography and
submits
the public key to the authentication interface 104. The email address and
password
input by the user are then transferred to the validation entity 105. If they
match an
existing account, the validation entity 105 generates and digitally signs a
digital
certificate linking the user's public key to the email address of the sponsor.
In other
preferred embodiments, the digital certificate may link the user's public key
to the
name of the sponsor, or his phone number, or his postal address or any other
piece of
information that enables the corporation 201 to uniquely identify the sponsor.
Once
the digital certificate is generated, it is transferred to the authentication
interface 104
which in turn installs it on the electronic terminal 103. Finally, the
electronic terminal
103 uses the digital certificate to authenticate with the system 100,
establish a secure
networking session and use it to gain access to network resources 106.
Referring to FIGs. 2, 3, 5 and 6, the authentication interface 104 can be seen
as a
web interface residing on web server 205 preferentially located within a
centralized
server farm 203 but that may also reside within an internal server farm 304.
The user
101 initially opens his browser on his electronic terminal 103 and requests
some web
page at step 401. The web server 205 redirects the user 101 to the
authentication web
interface at step 402. The user 101 inputs his email address and unique
identifier at
step 600; in a preferred embodiment, the personal characteristic is a personal
acquaintance with a sponsor 500 and the unique identifier is the email address
of the
sponsor 500. The web server 205 then communicates the information submitted by
the user 101 to the RADIUS server 206 at step 601. At step 602, the RADIUS
server
206 verifies with the database server 204 whether an account for this user 101
already exists. If not, an account is created at the database server 204 and a
password for this account is generated. If an account already exists, the
associated
password is retrieved. The RADIUS server 206 then transmits this password to
the
CA 02647684 2008-09-29
WO 2007/128134 PCT/CA2007/000821
user's email address at step 603. At step 604, the user 101 inputs his email
address
and password in the web interface residing on the web server 205. In parallel,
the
user's electronic terminal 103 generates a private and public key pair in
accordance
with the rules of public key cryptography. The electronic terminal 103 further
transmits
5 the public key to the web server 205 at step 408. This latter transfers the
email
address and password input by the user 101 to the RADIUS server 206 at step
605. In
turn, the RADIUS server 206 validates the credentials with the database server
204 at
step 410. If the credentials match the existing account, the RADIUS server 206
communicates the email address of the sponsor 500 and the user's public key to
the
10 certificate server 207 at step 606. In turn the certificate server 207
generates and
digitally signs a digital certificate linking the public key to the email
address of the
sponsor 500. The certificate server 207 then transmits the certificate to the
web server
205 at step 607. The web server 205 installs the certificate on the user's
electronic
terminal 103 at step 413. Finally, the electronic terminal 103 uses the newly
acquired
15 digital certificate to authenticate with the centralized server farm and
gain secure
network access to resources 106 such as the Internet 200 through his
electronic
terminal 103 that is preferentially a laptop 213 or PDA 214 or IP telephone
219. Those
skilled in the art should recognize that other types of unique identifiers may
be used to
identify the sponsor such as his cellular telephone number, his landline phone
number, his fax number, his postal address and so on. Furthermore, the system
100
may use a different method than email to communicate the one time password to
the
user 101. For example the one time password may be sent back by SMS in which
case the authentication interface 104 will ask the user 101 for his cellular
telephone
number, conveyed in person by IT staff in the corporation network 201 and so
on.
Referring collectively to FIGs. 1, 2 and 7 the user 101 uses a personal
digital
certificate to authenticate over EAP-TLS and secure her wireless session. The
user's
laptop 213 utilizes an IEEE 802.1x client embedded in its operating system to
exchange EAP messages 700 with the access point 211. In turn, the access point
211
communicates the information from the EAP messages to the RADIUS server 206;
this is accomplished at step 701. The RADIUS server 206 further transmits his
own
digital certificate to the user 101 at step 702. At step 703 the user 101
sends to the
CA 02647684 2008-09-29
WO 2007/128134 PCT/CA2007/000821
16
RADIUS server 206 her personal digital certificate which she obtained from the
ad hoc
and secure guest authentication system 100 as disclosed above. This
certificate
exchange between user 101 and RADIUS server 206 enables the creation of a
secure
link 704 between the user's laptop 213 and the access point 211. The user 101
can
utilize the secure link to communicate with the Internet 200 or even access
internal
resources 217 located within the internal network 210.
Referring collectively to FIGs. 1, 2 and 8, the guest user 212 may access
internal
resources 217 located within the internal network 210 which is protected by an
internal
firewall 209. The user 212 connects through the wired link 216 or wireless
link 215 to
the internal resource 217. The intemal resource 217 requests the user's
certificate.
The user 212 submits his certificate 900. The internal resource 217 validates
the
certificate in step 901 by retrieving a certificate revocation list (CRL) from
the
certificate server 207. This list is a collection of all certificates issued
by the certificate
server along with their validity status. When system administrators revoke a
certificate,
the CRL reflects that change. Those skilled in the art will recognize that
technologies
other than the CRL may be used to validate certificate authenticity including
the online
certificate status protocol (OCSP). If the certificate is valid, the internal
resource 217
may exchange other challenge messages with the user's electronic terminal 103
before finally granting access.
Referring to FIG. 1, 2, 4, 6 and 7 another preferred embodiment would include
electronic security verifications of the electronic terminal 103 prior to
granting access
to network resources 106 at step 704. This will include virus and spyware
verification
in addition to general observation of electronic terminal behavior on the
network to
prevent security breaches within the system 100.
Referring to FIGs. 1, 2 and 7, user 101 would not be a human person, rather an
electronic user consisting of software, hardware or combination thereof and
residing
on the electronic terminal 103. The electronic user will engage with
communication
with the authentication system 100 through the authentication interface 104.
The
electronic user must have been previously configured with some unique
identifier
CA 02647684 2008-09-29
WO 2007/128134 PCT/CA2007/000821
17
associated with a personal characteristic such as cellular telephone number or
the
email address of a sponsor in the corporation network 201. The electronic user
will
obtain a digital certificate as previously disclosed and will exchange
authentication
messages 700 in order to secure the wireless link 704.
Referring to FIGs. 1 and 2, in other preferred embodiments, the authentication
interface 104 is not a web interface but can consist of one or more software
processes
running on local or remote servers such as a SMS server, a fax server, a chat
server,
an email server or others. In those cases the user 101 communicates with the
authentication interface 104 through SMS, facsimile, chat or email
communication. In
yet other embodiments (not illustrated), the authentication interface can
consist in a
physical security access unit that the user 101 can access through a plurality
of
components such as a security access card that is inserted into the physical
security
access unit, or a radio frequency (RF) enabled security access tag that
communicates
through radio waves with said access unit, or an infrared (IR) enabled
security access
tag that communicates through infrared waves with said access unit. The
components
should be capable of storing user credential information such as a password,
email
addresses and so on; the components should further be capable of communicating
the credentials to said access unit. Those skilled in the art will recognize
that other
forms of interfaces capable of transferring information between the user 101
and the
validation entity 105 can also be used.
Referring to FIGs. 1 and 2, in other preferred embodiments the validation
entity 105
does not consist of servers but can be of another nature such as one or more
human
operators that are enabled to receive the unique identifier from the user 101,
validate
the user's identity and issue him a personal digital certificate.
Referring to FIGs. 1, 2, 4 and 6, IT staff within the corporation network 201
may elect
to be involved in one or more of the steps in FIGs. 4 and 6 by specifying that
all user
provisioning requests receive their approval before the system 100 grants the
user
101 a digital certificate at step 413. The authentication interface 104 may
also (not
illustrated) ask the user to specify his affiliation with the corporation
network 201. This
CA 02647684 2008-09-29
WO 2007/128134 PCT/CA2007/000821
18
way IT staff can be notified only in the case of users claiming to belong to a
certain
group such as interns. This may be because interns for example may have more
access privileges to the internal network 210 (while regular users have none)
which
necessitate further validation of their identity.
Referring to FIGs. 1, 2, 4 and 6, in another preferred embodiment, step 413
can
involve the installation of the user's certificate on a USB key or smart card
device
instead of a laptop 213, PDA 214 or IP telephone 218. Those skilled in the art
should
recognize that other media extemal to the user's electronic terminal 103 may
also be
used to store the certfficate and corresponding private key. Such a setup will
enable
enhanced security protection.
Referring collectively to FIGs. 1, 2, 4, 5, 6, and 7 when the user 101
initially connects
to the temporary unsecured network to obtain a personal digital certificate,
the
authentication interface 104 may install a client application on the
electronic terminal
103. This client application enables the corporation network 201 to control
the
certificate provisioning steps as well as force the disconnection of the
temporary
unsecured connection and re-authentication using secure network communication
technologies to establish a secure link 704.