Note: Descriptions are shown in the official language in which they were submitted.
CA 02753670 2011-08-25
WO 2010/097963 PCT/JP2009/054243
- 1 -
DESCRIPTION
HOME SECURITY SURVEILLANCE SYSTEM
TECHNICAL FIELD
The present invention is directed to a home security surveillance system,
and more particularly to such a system in which a service provider implements
a
home security service to individual customer's homes respectively equipped
with
in-house alarm network.
BACKGROUND ART
There has been proposed a hazard alarm system, for example, as
disclosed in WO 2008/088079 that is designed to operate solely in a user's
home
for giving a fire alarm in a multiplicity of rooms or locations when any one
of the
locations is detected to see a fire occurrence. For this purpose, the prior
alarm
system utilizes a master detector and a plurality of slave detectors, which
are
disposed in different locations and are communicated with each other through
an
in-house network. Each of the detectors incorporates a detector for detection
of
a hazard or fire condition as well as an alarm unit which issues an alarm upon
the
detector generating a hazard signal indicative of the occurrence of the hazard
condition. The master detector is specifically designed to receive the hazard
signal from anyone of the slave detectors and to generate a linking hazard
signal
and transmit the same to all the other detectors for simultaneous alarm at
every
detectors or rooms. While on the other hand, the slave terminal is designed to
transmit the hazard signal to the master detector and optionally to the other
slave
detectors, but not to relay the hazard signal to the others. Thus, only the
master
detector acts as a repeater to relay the hazard signal to all the other
detectors in
CA 02753670 2011-08-25
WO 2010/097963 PCT/JP2009/054243
- 2 -
order to successfully issue the alarms from all of the detectors for enhancing
system integrity against possible failure of issuing the alarm in any one of
the
rooms.
In recent years, there is a growing demand of expanding the above
individual in-house alarm networks to an integrated network service or system
with the use of a widely-available computer network, e.g. the Internet, in
order to
add an assistant service of dealing with the hazard condition by a third party
other than the individual users. When implementing such integrated network
service, it is required to employ a computer-based server on the side of a
service
provider, and a gateway in each of the users' homes as an interface between
the
in-house alarm network and the server so as to collect the hazard signal
transmitted within the in-house alarm network. The server can be designed to
communicate through the public computer network with the gateway so as to
acknowledge hazard condition detected in the in-house alarm network for
providing an assistance service upon receiving of the hazard condition
detected
in the in-house alarm network.
Thus, it is required to establish a communication between the gateway to
the in-house alarm network, i.e., at least one of the detectors. Accordingly,
it is
a straightforward solution to use a communication protocol employed in the
in-house alarm network also to the communication between the in-house alarm
network and the gateway, and to make the communication between the gateway
and the master detector by making the use of its repeater function.
However, such straightforward solution is thought not to be sufficient for
reliable and fail-safe service because of a possible communication error in
the
in-house alarm network results in a failure of notifying the server of the
hazard
CA 02753670 2011-08-25
WO 2010/097963 PCT/JP2009/054243
- 3 -
condition, and also because of that a possible defect of the master detector
results in the like failure.
Thus, the implementation of the integrated network system has to take
into the consideration of the above potential insufficiencies and is well
coordinated with the existing in-house alarm network for realizing reliable
and
fail-safe home security surveillance system.
DISCLOSURE OF THE INVENTION
The present invention has been achieved to solve a problem of providing
a reliable and fail-safe home security surveillance system or integrated
service
system in which the server can successfully collect hazard condition detected
in
the in-house alarm network through different signal information paths.
The home security surveillance system in accordance with the present invention
includes a plurality of detection terminals arranged to detect a hazardous
condition in a customer's home and generate a hazard signal, and a
computer-based server having a terminal enrollment table arranged to store an
enrollment record for each of the detection terminals, and a gateway unit
adapted
to be installed in each of said customer homes. The enrollment record is
configured to include a terminal code predetermined to identify each of the
detection terminals. Each detection terminal includes a radio transceiver for
transmitting the hazard signal to the other detection terminal through a first
communication network. The gateway unit includes a communication means
which is arranged to communicate with the server through the public computer
network, and also to communicate with the detection terminals through a second
communication network for receiving an aid-requesting signal from at least one
of
CA 02753670 2011-08-25
WO 2010/097963 PCT/JP2009/054243
- 4 -
the detection terminals and transmitting the aid-requesting signal to the
server.
The server has a processor which is configured to collect the aid requesting
signal from the gateway unit, and an alert means configured to provide an
alert
report in response to receiving the aid-requesting signal.
Each detection terminal includes an alarm unit which provides an alarm
upon such detection terminal generating the hazard signal or receiving a
linking
hazard signal from one of the other detection terminals. Further, each
detection
terminal is arranged to function selectively as a mater and a slave. The
master
is defined to provide the linking hazard signal when receiving the hazard
signal
from any one of the other detection terminal, while the slave is defined to
transmit
the hazard signal to the master through the first communication network. The
gateway unit is arranged to relay the aid-requesting signal to the server upon
receiving the aid-requesting signal.
The characterizing feature of the present invention resides in that each
detection terminal is arranged to generate and transmit the aid-requesting
signal
to the gateway unit through the second communication network upon generating
the hazard signal, and that the second communication network has a
communication protocol different from the first communication network.
With this feature, the server can receive the aid-requesting signal either
from the master or the slave for fail-safe acknowledgement of the hazard
condition detected in the customer's home, yet avoiding possible interference
between the first communication network and the second communication
network.
Preferably, the gateway unit is configured to transmit a request
acknowledgement signal to the detection terminal sending the aid-requesting
CA 02753670 2013-01-10
- 5 -
signal, and each detection terminal is configured to re-send the aid-
requesting
signal to the gateway unit when the request acknowledgement signal is not
received within a predetermined response time period. Thus, the master and
the slave can successfully transmit the aid-requesting signal to the server
through
the gateway unit, even if it temporarily fails to transmit the aid-requesting
signal.
Further, the detection terminal assigned as the slave may be
programmed to transmit the hazard signal as the aid-requesting signal first to
the
gateway unit upon generating the hazard signal, and subsequently transmit the
hazard signal to the master. Thus, the gateway can promptly transmit the
aid-requesting signal to the server for immediate acknowledgement of the
hazard
condition on the side of the server. Further, the slave is configured to re-
send
the hazard signal to the master when the request acknowledgement signal is not
received from the gateway unit within a predetermined response time period,
whereby the master can be successfully informed of the hazard signal.
In a preferred embodiment, the gateway unit includes an assigning
means which is arranged to assign the master to one of the detection terminals
that is energized to first establish communication with the gateway unit, and
assign said slave to the other detection terminal that is energized to later
establish communication with gateway unit. Thus, the system can be easily
developed in the customer's home without requiring the customer to understand
how to discriminate the master from the slave, and vice versa.
According to an aspect of the present invention there is provided a home
security surveillance system comprising:
a plurality of detection terminals arranged to detect a hazardous condition
in a customer's home and generate a hazard signal, each of said
CA 02753670 2013-01-10
- 5a -
detection terminals including a radio transceiver for transmitting said hazard
signal to the other detection terminals through a first communication network,
a computer-based server having a terminal enrollment table arranged to
store an enrollment record for each of said plurality of detection terminals,
said
enrollment record including a terminal code predetermined to identify each of
said detection terminals;
a gateway unit being adapted to be installed in each of said customer's
homes, and including a communication means which is arranged to
communicate with said server through a public computer network, and also to
communicate with said detection terminals through a second communication
network for receiving an aid-requesting signal from at least one of said
detection
terminals and transmitting said aid-requesting signal to said server;
wherein said server has a processor which is configured to collect said aid
requesting signal from said gateway unit, and an alert means configured to
provide an alert report in response to receiving said aid-requesting signal,
wherein each of said detection terminals includes an alarm unit which
provides an alarm upon the corresponding detection terminal generating said
hazard signal or receiving a linking hazard signal from one of the other
detection
terminals,
wherein each of said detection terminals is arranged to function selectively
as a master and a slave, said master being defined to provide said linking
hazard
signal when receiving said hazard signal from any one of the other detection
terminals, and said slave being defined to transmit said hazard signal to said
master through said first communication network,
wherein said gateway unit is arranged to relay said aid-requesting signal
to said server upon receiving said aid-requesting signal,
CA 02753670 2013-01-10
- 5b -
wherein each of said detection terminals is arranged to generate and
transmit said aid-requesting signal to said gateway unit through said second
communication network upon generating said hazard signal, said second
communication network having a communication protocol different from said
first
communication network, and
wherein
said gateway unit includes an assigning means arranged to assign said
master to one of said detection terminals that is energized to first establish
communication with said gateway unit, and assign said slave to one of the
other
detection terminals that is energized to later establish communication with
said
gateway unit.
These and still other advantageous features of the present invention will
become more apparent from the following detailed description when taken in
conjunction with the attached drawings.
CA 02753670 2011-08-25
WO 2010/097963 PCT/JP2009/054243
- 6 -
BRIEF DESCRIPTION OF DRAWINGS
FIG. 1 is a schematic view of a home security surveillance system in
accordance
with the present invention;
FIG. 2 is a schematic view illustrating terminal registration tables and a
terminal
status table respectively prepared in detection terminals and a gateway unit
constituting the above system, in addition to a terminal enrollment table of a
server;
FIG. 3 is a block diagram of the server;
FIG. 4 is a block diagram of the detection terminal;
FIG. 5 is a block diagram of the gateway unit;
FIG. 6 is a timing chart illustrating how the detection terminals are assigned
as a
master and a slave;
FIG. 7 is a timing chart illustrating how the system is reconfigured in case
when
one of the slave is removed from the system;
FIG. 8 is a timing chart illustrating how the system is reconfigured in case
when
the master is removed from the system;
FIG. 9 is a timing chart illustrating how the system is reconfigured in case
one of
the slaves is replaced with a new detection terminal;
FIG. 10 is a timing chart illustrating how the system is reconfigured in case
the
master is replaced with a new detection terminal; and
FIG. 11 is a timing chart illustrating an operation sequence upon detection of
hazardous condition at one of the detection terminals.
BEST MODE FOR CARRYING OUT THE INVENTION
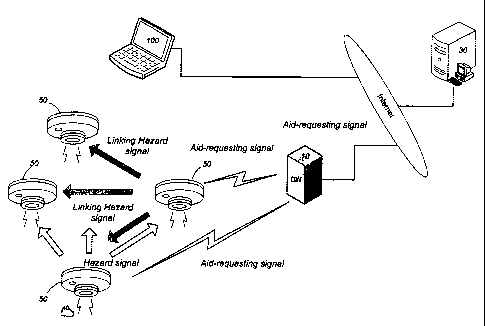
Now referring to FIG. 1, there is shown a home security surveillance
CA 02753670 2011-08-25
WO 2010/097963 PCT/JP2009/054243
- 7 -
system which employs a hazard detection subsystem in accordance with the
present invention. The home security surveillance system is provided by a
service provider and includes a computer-based server 30 installed on the side
of
a service provider for collecting hazard information such as fire occurrence
from
an in-house alarm network in each of customers' homes and providing an
assistance, for instance, dispatching qualified personnel to the customers
home
and/or informing an urgent prompt to a customer out of ones' home. The
in-house network is realized by the subsystem which is developed in each of
the
customers' homes and includes a plurality of detecting terminals 50 such as
smoke detectors, and a gateway unit 10 which acts as an interface between the
detecting terminals and the server 30. The server 30 is equipped or linked
with
an alert device 38 which generates an alert report when receiving the hazard
information in the form of an aid-requesting signal from any one of the
detection
terminals 50 through the gateway unit 10. As will be discussed later in
details,
each of the detection terminals is configured to communicate with each other
through a first communication network, and also communicate with the gateway
unit 10 through a second communication network.
The system further includes an input device 100, for instance, a personal
computer or the like which belongs to each customer and is configured to
communicate with the server 30 through a public computer network, e.g., the
Internet for enrolling the detection terminals 50 in the server 30. For this
purpose, the server 30 is provided with a terminal enrollment table 37, which
is
configured, as shown in FIG. 2, to store a record of terminal code, for
instance,
manufacture's serial number entered by the customer by use of the input device
100. No other entry is required on the side of the customer. The customer is
CA 02753670 2011-08-25
WO 2010/097963 PCT/JP2009/054243
- 8 -
only required to insert the record of the terminal code or delete such record
in
advance of developing the in-house alarm network of the subsystem.
As shown in FIG. 3, the server 30 includes, in addition to a memory
constituting the terminal enrollment table 37, a communication module 32 for
communication with the input device 100 as well as the gateway unit 10 through
the public network, and a processor constituting an enrolling module 34 and a
hazard event module 36. The enrolling module 34 is programmed to insert,
delete, and update the enrollment record in the terminal enrollment table 37
in
response to the customers input at the input device 100. The hazard event
module 36 is programmed to activate an alert device 38 for providing the alert
report in response to the aid-requesting signal transmitted by way of the
gateway
unit 10 and received at the communication module 32. The alert device 38 may
be a display, a speaker, or the like providing information to the personnel of
the
service provide.
The detection terminals 50 employed in the present invention are of the
same configuration which enables each of the detection terminal to function
selectively as a master and a slave. The detection terminal 50 is powered by
an
incorporated battery (not shown), and includes, as shown in FIG. 4, a power
switch 52, a smoke sensor 56, an alarm unit 58, a radio transceiver 68, a
processor, and a memory. The smoke sensor 56 is designed to detect a smoke
density in an atmosphere and output a density signal indicative of the
detected
smoke density to a hazard event module 64 realized in the processor. When
the smoke density exceeds a predetermined threshold, the hazard even module
64 generate a hazard signal indicative of possible fire and output the signal
to the
alarm unit 58, which responds to give an alarm sound. The hazard signal is
CA 02753670 2011-08-25
WO 2010/097963 PCT/JP2009/054243
- 9 -
transmitted by means of the radio transceiver 68 to the other detection
terminals
50 forming the in-house alarm network through the first communication network,
and is also transmitted as the aid-requesting signal to the gateway unit 10
through the second communication network. To this end, the hazard event
module 64 is configured to generate the hazard signal in compliance with a
first
communication protocol specific to the first communication network, and the
aid-requesting signal in compliance with a second communication protocol,
which
is different from the firs communication protocol, specific to the second
communication network.
The master is defined to provide a linking hazard signal when receiving
the hazard signal from any one of the other detection terminals, while the
slave is
defined to transmit the hazard signal to the master through the first
communication network, and to give the alarm upon receiving the hazard linking
signal from the master. The linking hazard signal is prepared in accordance
with the first communication protocol and is transmitted from the master to
all of
the slaves forming the in-house alarm network for providing the alarm at every
detection terminals simultaneously. The master is also configured to generate
and transmit the aid-requesting signal to the gateway unit 10 when receiving
the
hazard signal from any one of the slaves or when generating the hazard signal
by
its own. In this sense, the master acts as a repeater to transmit the
aid-requesting signal to the gateway unit in parallel with the aid requesting
signal
transmitted from the slave directly to the gateway unit 10. In addition, the
slave
is configured to transmit the hazard signal also to the other slave or slaves,
when
detecting the hazard configuration or fire occurrence. In order to make
interrelated operations between the master and the slaves, the detection
terminal
CA 02753670 2011-08-25
WO 2010/097963 PCT/JP2009/054243
- 10 -
has a terminal registration table 67 which is realized in the memory to store,
as
shown in FIG. 2, a record of a master/slave index indicative of the master or
slave, and a node number discriminating each one of the detection terminals
from the other within the in-house alarm network. Further, the record of the
terminal registration table 67 includes the terminal code. When the detection
terminal is assigned as the master, as will be discussed later, it is made to
store
the master/slave index and the node numbers for all of the detection
terminals.
When, on the other hand, the detection terminal is assigned as the slave, it
is
made to store the master/slave index and the node number of itself and the
master.
The processor also realizes a configuration/registration module 62 which
is programmed to interact with the gateway unit 10 to complete a terminal
configuration of assigning the maser and slave, and a terminal registration of
determining the node number in association with the master/slave index.
As shown in FIG. 5, the gate unit 10 includes a radio transceiver 11 for
communication with the server 30 as well as with the detection terminals 50
through the second communication network, which is distinguished from the
first
communication network of interconnecting the detection terminals 50 due to the
use of a specific communication protocol different from that of the first
communication network. The gateway unit 10 also includes a memory
constituting a terminal status table 17 which has a configuration identical to
the
terminal enrollment table 37 and is updated to reflect a change in the
enrollment
record of the terminal enrollment table 37. Further, the gateway unit 10 has a
processor constituting a hazard event module 12, an authentication module 14,
and an assigning module 16. The hazard event module 12 is programmed to
CA 02753670 2011-08-25
WO 2010/097963 PCT/JP2009/054243
- 11 -
relay the aid-requesting signal to the server 30, in response to receiving it
from
any one of the detection terminals 50. The authentication module 14 is
programmed to authenticate the detection module, i.e., check whether or not
the
detection terminal 50 making a configuration demand is recorded in the
terminal
status table 17, and permits.the entry of such detection terminal 50 into the
in-house alarm network when it is so recorded in the terminal status table 17.
The assigning module 16 is programmed to assign the master to one of the
authenticated detection terminals 50 and the slave to the other authenticated
detection terminals 50. The result of such assignment is recorded in the
terminal status table 17, as well as in the terminal registration table 67 of
each
detection terminals.
Now referring to FIG. 6, the terminal configuration and the terminal
registration are explained in details. After the customer enters the terminal
code
for each of the detection terminals 50 to be installed in one's home in the
terminal
enrollment table 37 of the server, the gateway unit 10 responds to record the
terminal code in the terminal status table 17 when communicating first with
the
server. Thus, the gateway unit 10 becomes ready for making the terminal
configuration. When one of the first detection terminals is energized with its
power switch turned on, it transmits to the gateway unit 10 the configuration
demand including the terminal code. When the gateway unit authenticates the
detection terminal transmitting the configuration demand as being recorded in
the
terminal status table 17, the gateway unit 10, i.e., the assigning module 16
acknowledges that the detection terminal is the first one that establishes the
communication with the gateway unit 10, and returns a configuration request to
the detection terminal, requesting the detection terminal to transmit a
CA 02753670 2011-08-25
WO 2010/097963 PCT/JP2009/054243
- 12 -
configuration response of a specific encryption key to the gateway unit 10.
When the gateway unit 10 verifies the configuration response as valid, it
transmits a configuration instruction a configuration instruction to the
detection
terminal in order to assign the master thereto, and at the same time, updates
the
record of the terminal status table 17 with respect to the detection terminal
by
setting the master/slave index of "1" and the node number of "00", both
indicating
the master. The configuration request and the configuration response are
provided only for exchanging the encryption key between the detection terminal
and the gateway unit for an encrypted communication, and may be optional.
That is, the gateway unit 10 may be configured to transmit the configuration
instruction in direct response to the configuration demand from the detection
terminal of which terminal code is authenticated.
Upon receiving the configuration instruction at the detection terminal 50,
the configuration/registration module 62 responds to write the master/slave
index
of "1' and the node number of "00" in association with the terminal code of
its
own in the terminal registration table 67. Thus, the detection terminal 50
(hereinafter also referred to as "DT-master") becomes ready for registration
of
the other detection terminals (hereinafter also referred to as "DT-slave")
which
constitute the in-house alarm network with the DT-master.
Subsequently, when one of the other detection terminals 50 (DT-slave) is
energized by manipulation of the power switch 52, the detection terminal 50
(DT-slave) goes into a stage 1 sequence ( i.e., a slave configuration
sequence) of
transmitting the configuration demand with its terminal code, and optionally
receiving the configuration request from the gateway unit 10, and transmitting
back the configuration response to the gateway unit 10. When the terminal
CA 02753670 2011-08-25
WO 2010/097963 PCT/JP2009/054243
- 13 -
code is recorded in the terminal status table 17, the gateway unit 10 assigns
the
slave to the detection terminal 50 (DT-slave) by transmitting to the DT-slave
the
configuration instruction by which the configuration/registration module 62 of
the
DT-slave responds to write the master/slave index of "0" as associated with
its
own terminal code in the terminal registration table 67. When sending the
configuration instruction to the DT-slave which establishes the communication
with the gateway unit 10 later than the preceding one of the detection
terminals,
i.e., the DT-master, the gateway unit 10 includes a registration instruction
in the
configuration instruction. That is, the assigning module 16 generates the
registration instruction to be added with the configuration instruction. When
receiving such configuration instruction, the DT-slave goes into a stage 2
sequence (i.e., a slave registration sequence) starting from waking up the
DT-master by sending a registration demand to the DT-master.
Upon receiving the registration demand, the DT-master responds to
return a demand acknowledgement to the DT-slave, and a registration inquiry to
the gateway unit 10. Subsequently, the gateway unit 10 returns a slave
registration permission which is prepared by the assigning module 16 to
include
the node number of "01" to be given to the DT-slave. Then, the DT-master
responds to transmit a registration order to the DT-slave with the node number
of
1101" indicative of that the DT-terminal is the first slave recognized by the
DT-master, in addition to the master/slave index, and the node number of about
the DT-master so that the configuration/registration module 62 of the DT-slave
updates the record of its own to have the node number of "01", and adds the
record of the DT-master in the terminal registration table 67, as shown in
FIG. 2.
After completion of updating the terminal registration table 67, the DT-slave
CA 02753670 2011-08-25
WO 2010/097963 PCT/JP2009/054243
- 14 -
returns a registration response to the DT-master which responds to add the
record of the DT-slave in its terminal registration table 67. Upon receiving
the
registration response from the DT-slave, the DT-master sends a slave
registration request to the gateway unit 10 so that the gateway unit updates
the
record of the DT-master and the newly added DT-slave in the terminal status
table 17 with regard to the master/slave index and the node number in relation
to -
the terminal code. After updating the terminal status table 17, the gateway
unit
issues a registration completion response to the DT-slave, completing the
slave registration sequence, i.e., the stage 2 sequence.
If the registration completion response is not received within 2500 ms
from the configuration demand, the above slave configuration sequence followed
by the slave registration sequence is repeated. With the completion of the
above registration for all of the other DT-terminals, the DT-master
acknowledges
each of the DT-slaves and the vice versa as constituting the in-house alarm
network such that the each DT-slave can transmit the hazard signal to the
DT-master and the other DT-slave through the first communication network,
i.e.,
the in-house alarm network, and the DT-master can transmit the aid-requesting
signal to the gateway unit 10 through the second communication network upon
receiving the hazard signal from any one of the DT-slaves, in addition to that
each of the DT-slave can transmit the aid-requesting signal directly to the
gateway unit 10 through the second communication network.
Referring to FIG. 7, there is shown a time chart illustrating how the
system works when one of the DT-slaves is removed from the system. When
the DT-slave, for instance, one having the node number of "01" becomes
defective and is powered off, the customer utilizes the input device 100 to
delete
CA 02753670 2011-08-25
WO 2010/097963 PCT/JP2009/054243
- 15 -
the record of the defective DT-slave from the terminal enrollment table 37 in
the
server 30. The change of the record is reflected in the terminal status table
17
of the gateway unit 100 when it communicates with the server 30. That is, the
terminal status table 17 is updated to give a delete flag to the record of the
defective DT-slave, indicating that such recorded is to be deleted. In this
situation, the DT-master functions to make a status check sequence whether or
not the registered DT-slaves are currently available in the system. The status
check sequence is initiated by manipulation of a set button 54 on the side of
the
DT-master. Upon manipulation of the set button 54, the
configuration/registration module 62 responds to generate a status check
request
for all of the existing or registered DT-slaves, interrogating whether or not
each of
the DT-slaves registered in the terminal registration table 67 is recorded as
a
valid one in the terminal status table 17 of the gateway unit 10. When
returning
a status request acknowledgement to the DT-master, the gateway unit 10
provides a slave remove instruction for deleting the defective DT-slave from
the
terminal registration table 67, i.e., the record of the defective DT-slave
which is
marked with the delete flag in the terminals status table. In response to the
slave remove instruction, the DT-master deletes such record from its terminal
registration table 67, and returns a slave remove confirmation to the gateway
unit,
such that the gateway unit updates its terminal status table 17 by actually
deleting the record with the delete flag. When the other non-defective DT-
slave,
for example, having the node number of 102" has its set button 54 pressed, the
DT-slave transmits a like status check request whether or not the DT-slave
nO2n
is recorded in the terminal status table 17 of the gateway unit and receives
therefrom the status request acknowledgement, which necessitates no change in
CA 02753670 2011-08-25
WO 2010/097963 PCT/JP2009/054243
- 16 -
the terminal registration table 67 of the DT-slave "02g.
It is noted in this connection that the status check sequence is initiated by
pressing the set button 54 for a short period, for example, less than 4
seconds.
When, on the other hand, the set button 54 is pressed for a long period more
than 4 seconds, the DT-master or DT-slave makes the above status check
followed by a manual test routine which generates a pseudo hazard signal for
checking whether the in-house alarm system reacts to issue the alarm from the
individual detection terminal. In this case, after sending the status check
request and receiving the status request acknowledgement, the DT-master or the
DT-slave issues a test request to the gateway unit which responds to return a
test request acknowledgement. Upon receiving the test request
acknowledgement, the DT-master or the DT-slave is allowed to enter a manual
test mode of giving the pseudo hazard signal to generate the alarm within the
in-house alarm network, while the gateway unit can acknowledge that the
resulting alarm is false one and simply as a result of the test.
In addition, as will be discussed later with reference to FIG. 11, the set
button, when long-pressed, issues a stop alarm signal provided that that there
is
the hazardous condition detected in the in-house alarm network.
Further, it is also noted in this connection that the each of the DT-master
and the DT-slaves is activated intermittently or comes into an intermittent
operation mode of checking whether or not the hazardous condition is detected,
and wakes-up to transmit the hazard signal as well as the aid-requesting
signal
immediately upon detection of the hazardous condition. In the figures, such
intermittent operation mode of the terminal is denoted by the term
"intermittent
operation". Also, each of the DT-master and the DT-slave is configured to
issue
CA 02753670 2011-08-25
WO 2010/097963 PCT/JP2009/054243
- 17 -
the status check request to the gateway unit at regular intervals for checking
whether or not the second communication network operates successfully.
FIG. 8 illustrates a time chart how the system works when the DT-master
is removed. As a result of that the DT-master becomes defective and is
removed from the system, the customer is required to delete the record of the
defective DT-master from the terminal enrollment table 37 in the server 30
such
that the gateway unit 10 updates its terminal status table 17 to reflect the
deletion.
In this situation, when one of the DT-slaves, in this instance, DT-slave
having the
node number of "01" has its set button 54 pressed for the short period, this
DT-slave makes the status check sequence by transmitting the status check
request to the gateway unit 10. However, the gateway unit 10 fails to
successfully return the status request acknowledgement to the DT-slave,
because of that the gateway unit acknowledges no DT-master in its terminal
status table 17. After repeating to transmit the status check request for a
predetermined number within a predetermined period after the short-pressing of
the set button 54, the DT-slave is allowed to make the configuration sequence
to
the gateway unit 10. Upon receiving the configuration demand from the
DT-slave, the gateway unit 10 makes a reconfiguration routine for
reestablishing
the in-house alarm network. The reconfiguration routine continues by the
gateway unit 10 returning the configuration instruction by which the receiving
DT-slave is assigned as a new master and rewrites its terminal registration
table
67 to have the master/slave index of "1". That is, upon receiving the
configuration demand, as explained with reference to FIG. 6, from the
detection
terminal establishing the communication with the gateway unit, the gateway
unit
refers to its terminal status table and permits the assigning module 16 to
assign
CA 02753670 2011-08-25
WO 2010/097963 PCT/JP2009/054243
- 18 -
the master to the detection terminal transmitting the configuration demand,
only
when the terminal status table shows a record of the detection terminal
transmitting the configuration demand, and shows no record of any detection
terminal already assigned as the master.
At this time, the gateway unit 10 updates the terminal status table 17 to
rewrite the master/slave index of the new DT-master. Thereafter, the DT-master
transmits the status check request to the gateway unit 10 which returns the
status request acknowledgement to the DT-master. Whereby, the DT-master
responds to clear the records of the remaining DT-slaves with regard to the
node
number, and the gateway unit 10 clears the records of the remaining DT-slaves
with regard to the node number. Then, the gateway unit 10 becomes ready for
completing the reconfiguration routine in combination with the DT-master. That
is, upon receiving the configuration demand from each of the remaining
DT-slaves, in this instance, DT-slave having the node number of "02% the
gateway unit 10 generates the configuration instruction designating a new node
number of 1101" and the master/slave index of "0", and transmits the same to
the
DT-slave, which responds to update its own terminal registration table 67
correspondingly, thereby completing the stage 1 sequence (slave configuration
sequence). At this time, the gateway unit 10 has its terminal status table 17
updated to reflect the change made to the DT-slave. The configuration
instruction generated in the gateway unit 10 includes the registration
instruction
by which the DT-slave comes into the stage 2 sequence (i.e., the slave
registration sequence), which starts from waking up the new DT-master by
sensing the registration demand and complete by receiving the registration
completion response from the gateway unit 10, as explained in details with
CA 02753670 2011-08-25
WO 2010/097963 PCT/JP2009/054243
- 19 -
reference to FIG. 6. Similarly, any of the remaining DT-slaves completes the
above reconfiguration routine simply by pressing the set button 54 for the
short
time period. Upon completion of the reconfiguration of the all the existing
DT-slaves, the new DT-master has its terminal registration table 67 updated to
acknowledge the DT-slaves by their node numbers for communication within the
in-house alarm network, in addition to that the DT-master as well as the
DT-slaves can communicate with the gateway unit 10 with the use of individual
node numbers.
Referring to FIG. 9, there is shown another time chart illustrating how the
system works when replacing the DT-slave with a new one. As a result of that
one registered DT-slave (one having the node number "Olu, in this instance)
becomes defective and has to be replaced with the new detection terminal, the
customer uses the input device 100 to remove the record of the defective
DT-slave from the terminal enrollment table 37 in the server 30 and insert a
record of the newly added detection terminal in the terminal enrollment table
37.
The change of the record is reflected in the terminal status table 17 of the
gateway unit 100 when it communicates with the server 30. In this situation,
upon being energized to communicate with the gateway unit 10, the new
DT-slave interacts with the gateway unit 10 to complete the stage 1 sequence
and the stage 2 sequence as explained herein above so as to be given the
master/slave index of "0" and a new node number, whereby the new DT-slave is
recognized by the gateway unit 10 and also by the DT-master for successful
communication therebetween. Subsequently, in response to the short-pressing
of the set button 54, the DT-master makes the status check sequence whether or
CA 02753670 2011-08-25
WO 2010/097963 PCT/JP2009/054243
- 20 -
not the DT-slaves recorded in its terminal registration table are currently
available
in the system. That is, the DT-master generates and transmits the status check
request to the gateway unit 10, interrogating whether or not each of the
DT-slaves recorded in the terminal registration table 67 is also recorded as
valid
one in the terminal status table 17 of the gateway unit 10. When returning a
status request acknowledgement to the DT-master, the gateway unit 10 provides
the slave remove instruction for deleting from the terminal registration table
67
the record of the terminal which is marked with the delete flag in the
terminal
status table 17. In response to the slave remove instruction, the DT-master
deletes such record from its terminal registration table 67, and returns the
slave
remove confirmation to the gateway unit for completely deleting such record
also
from the terminal status table. Thereafter, when the DT-slave has its set
button
short-pressed, it transmits the status check request to the gateway unit 10
which
returns the status request acknowledgement indicative of that no change is
necessary for the terminal registration table 67 of the requesting DT-slave.
When the DT-master becomes defective and is replaced with a new one,
the system operates as shown in FIG. 10. In this situation, the user updates
the
terminal enrollment table 37 of the server 30 by deleting the record of the
defective DT-master and inserting the terminal code of a new detection
terminal.
The resulting change is reflected in the terminal status table 17 of the
gateway
unit 10. In response to the new detection terminal being energized to
establish
the communication with the gateway unit 10 by sending the configuration
demand, the gateway unit 10 checks whether or not there is the record of the
detection terminal assigned as the master in the terminal status table 17, and
complete the stage 1 sequence by sending the configuration instruction, which
CA 02753670 2011-08-25
WO 2010/097963 PCT/JP2009/054243
- 21 -
assigns the master to the new detection terminal when the terminal status
table
shows no record of the detection terminal assigned as the master. Thus, the
newly added detection terminal is acknowledged as the new DT-master.
Thereafter, the new DT master transmits the status check request to the
gateway
unit 1.0 and receives therefrom the status request acknowledgement for
confirmation of that the DT-master is recorded in the terminal status table.
At
this time, the DT-master does not acknowledge the associated DT-slaves, since
no record of the DT-slaves are entered in its terminal registration table 67.
Also,
the gateway unit 10 clears the node number of each DT-slave from its terminal
status table, such that it fails to return the status acknowledgement to each
DT-slave, even when each DT-slave has its set button short-pressed in an
attempt to interact with the gateway unit.
Subsequently, upon short-pressing of the set button, the DT-master
sends the status check request, requesting the gateway unit 10 to accept the
configuration demand followed by the status check request from each DT-slave.
After that, the DT-slave is allowed to make the configuration sequence to the
gateway unit and receives the configuration instruction to complete the stage
1
sequence and the stage 2 sequence in a manner as described in the above,
whereby the DT-slave is redefined as the slave with the node number given from
the gateway unit, and is recorded in the terminal registration table of the
DT-master. In this manner, all of the existing DT-slaves are redefined and
acknowledged by the DT-master and the gateway unit.
FIG. 11 illustrates how the system works upon detection of the
hazardous condition at one of the DT-slaves. In this instance, DT-slave having
the node number of '101" (herein after referred to as detecting DT-slave)
detects
CA 02753670 2011-08-25
WO 2010/097963 PCT/JP2009/054243
- 22 -
the hazardous condition and is caused to wake-up to issue the alarm and to
transmit the aid-requesting signal to the gateway unit 10. Then, the gateway
unit responds to relay the aid-requesting signal to the server 30 to notify
the
hazardous condition, and return an aid-request acknowledgement to the
detecting DT-slave. Immediately subsequently, the detecting DT-slave
transmits the hazard signal, waking up the DT-master as well as the other
DT-slave (hereinafter referred to as non-detecting DT-slave). In response to
the
hazard signal, the non-detecting DT-slave issues the alarm, while the DT-
master
generates and transmits the linking hazard signal to the detecting and
non-detecting DT-slaves such that each DT-slave issues the alarm. If the
non-detecting DT-slave should have failed to wake-up due to some temporary
communication error, it is caused to wake-up by the interconnecting hazard
signal and issue the alarm. The detective DT-slave and the non-detective
DT-slave, when waking-up, return a linking alarm response back to the
DT-master, which in turn comes into an interlocked mode of transmitting the
aid-requesting signal repeatedly to the gateway unit, and at the same time
transmitting the linking hazard signal repeatedly to the detective and
non-detective DT-slaves.
Upon the set button being pressed in this situation where the linking
hazard signal is repeatedly transmitted, the DT-master transmits an alarm stop
order to the detecting and non-detecting DT-slaves, and at the same time
transmits an alarm status signal to the gateway unit, indicating that the
DT-master is requesting the DT-slaves to stop the alarm. The alarm stop order
and the alarm status signal are transmitted repeatedly within a predetermined
time period of 90 seconds, for example. After the elapse of the time period,
the
CA 02753670 2011-08-25
WO 2010/097963 PCT/JP2009/054243
- 23 -
DT-master transmits an alarm stop confirmation, requesting the detective and
non-detective DT-slaves to return an alarm stop response indicative of that
the
alarm stop order is accepted at the DT-slave. However, while the detecting
DT-slave is still detecting the hazardous condition, the detecting DT-slave
returns
the alarm stop response indicative of the hazardous condition such that the
DT-master responds to continue transmitting the linking hazard signal until
the
hazardous condition is cleared, and continues transmitting to the gateway unit
the aid-request signal including information that the hazardous condition is
still
being detected at the detecting DT-slave after the DT-master transmits the
alarm
stop order.
When the hazardous condition is cleared, the detecting DT-slave
transmits a stop alarm demand to the DT-master, while stopping its own alarm.
Then, the DT-master responds to transmit a stop alarm confirmation order to
all
the DT-slaves, requesting them to return a stop alarm response including
information whether or not the DT-slave is ready for stopping the alarm. Upon
acknowledgement of the stop alarm response, the DT-master transmits a stop
alarm order to the DT-slaves for stopping the alarm at the individual DT-
slaves.
When the alarm is stopped, each DT-slave returns the stop alarm response
indicative of the alarm status to the DT-master, and comes into the
intermittent
reception mode. Likewise, the DT-master comes into the intermittent reception
mode upon receiving the stop alarm response from the DT-slaves. Further,
after receiving the stop alarm demand and until receiving the stop alarm
response, the DT-master functions to transmit the alarm status signal to the
gateway unit with information that the DT-master receives the stop alarm
demand
from the detecting DT-slave.
CA 02753670 2011-08-25
WO 2010/097963 PCT/JP2009/054243
- 24 -
It is noted that the detection terminal is designed to issue the alarm as a
sound-voice "whiz whiz warning smoke alarm" when the hazardous condition is
detected by its own, and to issue the alarm as a sound-voice 'whiz whiz
warning
smoke in another room "when the hazardous condition is detected by the other
detection terminal.
While the detection terminal is in the intermittent operation mode, it
transmits the status check request at regular intervals of 33 hours, for
instance,
to the gateway unit with information about a battery condition or some
parameters indicative whether or not the detection terminal is in good order.
Although the present invention has been described with reference to the
illustrated embodiment, the individual features as described in the above may
be
suitably combined to constitute an improved invention or inventions other than
the claimed invention.