Note: Descriptions are shown in the official language in which they were submitted.
CA 02823174 2013-08-07
SYSTEM AND METHOD FOR DISCLOSING UNAUTHORIZED REMOVAL OF
ARTICLES FROM SECURED PREMISES
Field of the Invention
[0001] This invention relates to a method of securing an inventory of
multiple
types of articles which are for sale within retail premises, to retail
premises secured by an
integrated inventory control and security system, and to a method of
documenting events
which disclose attempted unauthorized removal of an article of for-sale
merchandise from
within secured premises.
Background of the Invention
[0002] Theft of merchandise is a common problem for many businesses.
It is
typically considered an added cost of "doing business", a cost which
ultimately is borne by
consumers.
Summary of the Invention
[0003] General aspects of the invention relate to methods of securing
and
accounting for an inventory of multiple types of articles which are for sale
within retail
premises.
[0004] The general aspects include retail premises having an inventory
of for-sale
articles secured by equipment for performing the disclosed methods.
Brief Description of the Drawings
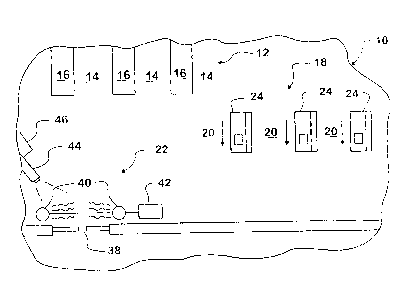
[0005] Figure 1 is a diagram showing a layout of a representative
retail facility
which has check-out counters and is secured by a security system and method
embodying
principles of the present invention.
[0006] Figure 2 is an elevation view, partly broken away to show an
interior, of a
check-out counter.
1
CA 02823174 2013-08-07
[0007] Figure 3 is a perspective view of an article of merchandise for
sale at the
retail facility.
[0008] Figure 4 shows a passive security device securing an article of
merchandise.
[0009] Figure 5 shows several retail facilities each having its own
security system.
Detailed Description
[0010] Figure 1 shows a portion of a building comprising retail
premises 10 which
comprises a merchandise area 12 containing aisles 14 where various articles of
for-sale
merchandise are stocked on shelves 16. Articles which customers wish to
purchase are carried
by the customers to a check-out area 18 where sales are consummated.
[0011] Check-out area 18 comprises check-out lanes 20 which may either
be self-
service or be served by an employee of the retailer. After a sale has been
consummated, a
customer can transport the purchased merchandise to an exit area 22 of the
premises through
which the customer can exit the building with his/her purchased merchandise.
[0012] Figure 2 shows each check-out lane 20 to comprise a check-out
counter 24
on which articles of merchandise to be purchased (designated by the general
reference M) are
placed. Merchandise to be purchased may first be placed on an approach surface
26 which is
ahead of a surface 28 onto or over which the merchandise is moved article-by-
article while
automated equipment causes the sale of each article to be registered, as will
be more fully
explained hereinafter. After the sale of an article has been registered, the
article passes onto a
powered conveyor 29 which conveys the article to an inclined ramp 30 along
which it can
slide, or roll if the ramp has rollers, onto a collection surface 31 where the
customer can
retrieve it after having paid for it.
[0013] Each article of merchandise contains a UPC bar code which
uniquely
identifies the specific article. Surface 28 contains one or more areas 32
which allow a scanner
34 to "read" the UPC bar code on an article of merchandise when the article is
placed on or
moved past an area 32. By making areas 32 optically transparent and using an
optical scanner
34 behind the areas, a visible UPC bar code on an article label, tag, or
packaging, or on an
2
CA 02823174 2013-08-07
article itself, can be read by scanner 34 to identify the article. With the
article having been
electronically identified, the electronic identity is processed by a computer-
based register 36
which has access to a data bank comprising a correlation of sale price to bar
code for each of
various articles of merchandise stocked for sale to determine the article's
sale price from the
data bank, and the sale price is then recorded in one or more appropriate
ways, such as
electronically in a suitable storage medium, or memory. The article is then
placed on conveyor
29 for transport via ramp 30 to collection surface 31.
[0014] After all articles of merchandise have been processed in this
manner,
register 36 provides a total of the individual sale prices in a dollar or
other currency amount
which the customer then pays by any appropriate means of payment such as cash,
credit, or
debit. A sales receipt which lists articles purchased and the sale price of
each, and the total
amount of the transaction, which may include other charges such as tax, is
printed and issued
to the customer who can then collect the purchased merchandise from collection
surface 31
and leave the building through an exit door 38 of exit area 22.
[0015] For securing "for-sale" merchandise against unauthorized
removal from
premises 10, such as by theft or pilferage, each article of merchandise is
secured by the
presence of a passive security device which, upon attempted unauthorized
removal of the
secured article from the premises, will be detected when the secured article
comes within a
specified range of a detector 40 shown in Figure 1 at exit area 22 inside exit
door 38.
Detection of a passive security device by detector 40 immediately initiates
some form or
forms of security action.
[0016] Such forms of action include issuing an alarm via an alarm
device or
system 42 which may comprise one or more of sounding an audible alarm in the
building,
illuminating a visible alarm in the building, and transmitting a silent alarm
to security or staff
personnel on the premises and/or to a remote location. Exit door 38 may also
be locked
closed.
[0017] Exit area 22 is also continuously monitored by a closed circuit
television
camera 44 and an associated video recording device 46 which records the exit
area scene
either continuously or at a sufficiently fast snap-shot rate, and which may
also have audio
recording capability.
3
CA 02823174 2013-08-07
[0018]
Detector 40 comprises a detection transmitter which continuously transmits
(i.e. wirelessly broadcasts) a detection signal into an approach to exit door
38 which is inside
the building premises. The broadcast range does not extend to merchandise area
12 or to
check-out area 18. Detector 40 also comprises a receiver for detecting receipt
of a wireless
return signal from a passive security device in response to the passive
security device having
received a detection signal from the transmitter.
[0019]
Figure 3 shows an article of merchandise M containing one or more visible
UPC bar codes 48 and one or more passive security devices 50. Figure 3 should
not be
construed to imply the size, shape, or location of passive security device 50,
or the number of
such passive security devices on articles, or where such passive security
devices are placed on
articles, because that is a function of the nature of each article and of the
nature of the
particular passive security device or devices used. The presence of a passive
security device
on any particular article of merchandise should be known only to authorized
personnel, such
as management and security staff of a retailer for example. The size and
placement of a
passive security device on any particular article of merchandise should render
its presence
unnoticeable to anyone, other than perhaps in some instances to authorized
personnel having
knowledge.
[0020] A
passive security device may take any of various specific forms, to be
discussed in more detail later. A passive security device is essentially a
miniature, disposable
electronic circuit having an antenna, or antennas, which render the device
capable of receiving
an incident wireless signal or signals and of transmitting a return signal or
signals in response
to such an incident signal or signals. A passive security device which
receives an incident
signal of sufficient strength will transmit a return signal of sufficient
strength to be detected by
the receiver of detector 40. The signal strengths are strong enough to provide
detection of
unpaid-for merchandise even when the person attempting to remove the
merchandise from the
premises does so in a concealed manner and/or uses some form of protective
shielding.
[0021]
Attempted removal of an unpaid-for article of merchandise through exit
area 22 will result in a signal which is being broadcast by the detection
transmitter of detector
40 causing the passive security device which secures the article to transmit a
return signal
4
CA 02823174 2013-08-07
which, upon detection by the receiver of detector 40, causes some form or
forms of security
action to be initiated.
[0022] So that a paid-for article of merchandise will not cause
detector 40 to
initiate security action when it comes within the broadcast range of the
transmitter of detector
40, each check-out counter 24 comprises a "kill" transmitter 52 shown in
Figure 2. Kill
transmitter 52, which may also be referred to as an unsecuring transmitter
because it unsecures
a secured article to allow the article to be removed from the premises without
giving an alarm,
can transmit a wireless signal, referred to as a kill signal or alternately an
unsecuring signal,
which is capable of rendering a passive security device incapable of
transmitting a return
signal in response to an incident signal from the detection transmitter of
detector 40. In this
way, the state of a passive security device is changed from a first, or
"live", state to a second,
or "killed", state.
[0023] Various ways of rendering a passive security device incapable
of
responding to an incident signal from the detection transmitter of detector 40
include causing
an internal circuit change in the passive security device which changes a
response
characteristic of the passive security device, such as changing the frequency
at which it would
respond to a broadcast from the transmitter of detector 40 to a different
frequency to which the
receiver of detector 40 is not tuned, or overwhelming the internal circuit
with enough energy
to "burn out" one or more circuit elements needed for transmission of a return
signal, thereby
simply destroying the passive security device.
[0024] Upon register 36 having registered the sale price of an article
in an
appropriate storage medium or memory, the registration of the sale will cause
kill transmitter
52 to transmit an unsecuring signal which "kills" the passive security device
securing the
article. The kill transmission broadcast is properly targeted to hit the
passive security device
securing an article whose sale has just been registered, but the broadcast
range is not so far as
to kill passive security devices on other articles which may be nearby waiting
to be scanned.
Register 36 keeps a record of each kill by transmitter 52 in an appropriate
storage medium or
memory. Figure 2 shows kill transmitter 52 in a location where it transmits a
wireless
broadcast targeted toward a paid-for article on conveyor 29.
CA 02823174 2013-08-07
[0025]
For assurance that the passive security device securing the article whose
sale has just been registered has in fact been killed by kill transmitter 52
and is therefore no
longer "live", register 36 causes a "kill confirmation" transmitter 54 to
confirm each kill after
sale of the article has been registered and kill transmitter 52 has
transmitted a kill signal
intended to kill the passive security device on the article. Kill confirmation
transmitter 54
performs a kill confirmation by transmitting a wireless signal which would
cause a "live"
passive security device to respond by returning a non-confirmation signal to a
receiver located
either in kill confirmation transmitter 54 or in the immediate vicinity. The
kill confirmation
broadcast is properly targeted to hit the presumptively-killed passive
security device of the
article whose sale has just been registered, but the broadcast range is not so
far as to cause
"live" passive security devices on nearby other articles of merchandise to
return signals.
Figure 2 shows kill confirmation transmitter 54 in a location where it
transmits a broadcast
which is targeted toward a presumptively-killed article on ramp 30. A kill
confirmation may
be recorded in register 36 in a suitable storage medium or memory in
correlation with the
registered paid-for sale price of an article of merchandise.
[0026]
Some of the various forms of passive security device 50 comprise passive
nano-, micro-, or pulse-technology circuits. Such extremely small devices,
whose sizes render
them incapable of being seen by a person's naked eye, lend themselves to
placement in
merchandise in a variety of ways. Placement should be in a place where the
circuit would be
unlikely to be removed before an article leaves the secured premises. Articles
of wearing
apparel can be secured by passive security devices placed in apparel parts
which if removed or
altered would damage the articles. They can be placed in sewn-in labels or
tags which would
be expected to not be removed prior to leaving secured premises. Manufactured
merchandise
can use the manufacturing process to embed a passive security device directly
in an article
during its manufacturing process using processes such as laminating or
pressing. Figure 3
shows a passive security device 50 placed underneath a label L which is
adhered to packaging
of the article.
[0027]
Nano-technology allows nano-type passive security devices to be
dispersed in printing ink or fabric dye which is applied to an article of
merchandise, a label on
an article, or packaging containing an article. Placement of nano-type passive
security devices
6
CA 02823174 2013-08-07
in printing ink which is used to print UPC bar codes on articles allows bar
codes themselves to
function as the passive security devices, thereby avoiding a separate securing
process. One or
more nano-type devices which are dispersed in printing ink will become
embedded in the ink
after the bar code has been printed and the ink has dried.
[0028] A manufacturer of articles who incorporates passive security
devices by
placing them directly on the articles or else in packaging of the articles and
then ships them to
a wholesale or retail customer enables the customer to verify the presence of
passive security
devices upon receipt of shipment and count them by a detector to determine if
the correct
quantity of articles has been shipped.
[0029] If a retailer of articles wishes to apply passive security
devices, a hand tool
applicator, like the one 56 shown in Figure 4, can apply them at locations on
articles of
merchandise which the retailer chooses and are known only to the retailer.
Such an applicator
can dispense ink containing nano-type passive security devices, labels
containing passive
security devices, or apply passive security devices directly by adhesive
mounting or other
similar techniques.
[0030] Figure 2 also shows a removable medium, such as a cassette 58,
associated
with register 36. Cassette 58 has a protocol known to a supplier, or licensor,
of the check-out
lane apparatus (i.e., scanner 34, register 36, kill transmitter 52, and
associated electronic data
processing equipment), but not to the user of the apparatus, for limiting the
total dollar or
other currency sales volume of articles of merchandise whose passive security
devices are
allowed to be killed by the apparatus. The intent is to provide an accounting
control on the
extent of use of the apparatus which will assure that a user prepays the
supplier, or a licensor
of the supplier, for use of the apparatus. Once the sales volume of
merchandise processed by
the apparatus nears the prepaid limit, an alert can be given to enable the
supplier or licensor to
replenish the cassette, or exchange the cassette for a fresh one, upon user
prepayment for
continued use. Instead of a cassette, use can be monitored remotely by the
supplier or licensor
who can allow continued use after user prepayment. If a user is creditworthy,
the supplier or
licensor can monitor use and invoice the user accordingly after the fact.
[0031] By using this accounting procedure, it becomes unnecessary to
involve a
supplier of merchandise or a supplier of passive security devices in an
accounting procedure.
7
CA 02823174 2013-08-07
A supplier of merchandise who applies passive security devices to them could
however be a
secondary or alternate point of accounting.
[0032] If the total sales volume were to near the prepaid limit,
certain controls in
the apparatus become effective to shut down scanner 34, register 36, kill
transmitter 52, and
kill confirmation transmitter 54, thereby rendering the corresponding check-
out lane 20
inoperative until a fresh cassette containing a fresh prepayment currency
amount is installed or
the existing one is reloaded with a fresh prepayment currency amount. By
preventing the
registration of the sale of an article in this way, its passive security
device remains "live",
preventing the secured article from being removed from the premises without
triggering an
alarm at the exit, or alternatively its removal can be authorized by the
purchaser paying for it
at another check-out lane which will kill the live passive security device.
[0033] Cassette 58 thereby provides a removable medium containing
value which
is progressively depleted in the amount of the sale price of each secured
article as the sale
price of each secured article is registered in the register. Upon the amount
of depletion of the
value approaching some limit, such as the prepaid limit initially loaded into
the cassette, the
kill transmitter is prevented from transmitting a kill signal. To continue use
of the kill
transmitter, the cassette is removed from the system, and its value
replenished only by a
supplier or licensor of the system, such as by returning the cassette to such
supplier or
licensor. By requiring such removal before a cassette can be replenished with
value, and by
uniquely identifying each cassette, a supplier or licensor of the system can
monitor system
usage to assure user compliance with conditions of use specified by the
supplier or licensor.
[0034] The point at which the remaining value in cassette 58 will
prevent kill
transmitter 54 from transmitting a kill signal can be set in different ways.
One way is by using
historical sales data to set a value which is greater than the remaining value
in the cassette and
which is likely to be exceeded by the total sales price of merchandise
purchased by the next
customer. Another way is to cause register to perform a "pre-kill" calculation
by comparing
the sale price of an article which has just been scanned to value remaining in
the cassette. If
the sale price of an article which has just been scanned exceeds the value
remaining in the
cassette, the register is prevented from registering the sale and the check-
out lane is shut
down.
8
CA 02823174 2013-08-07
[0035] The ability to manufacture electronic passive security devices
with
different frequency response characteristics allows each of different secured
premises to be
assigned their own unique frequency, much as commercial radios stations are.
By reserving
frequencies in this way, only passive security devices associated with a
particular secured
premises are useful at those premises. Figure 5 shows several retail stores
60, 62, each of
which has its own security system like the one shown in Figure 1, with only
the detectors 40
being shown in Figure 5.
[0036] The security system of store 60 operates at a different
frequency than the
one of store 62. The supplier of the security system, or the licensor of the
supplier, can assign
a unique frequency to each user which can forestall or prevent unauthorized
use of the
apparatus and which can also avoid interference with other wireless
communication functions,
such as inventory control for example. A chain of stores having different
geographical
locations can be assigned a common frequency for use at all stores.
[0037] Attempts to defeat a security system can be made more difficult
by using
passive security devices which respond to coded wireless detection signals
rather than just one
particular frequency alone and/or which respond to multiple frequencies. These
features may
be incorporated into a single passive security device or may be provided by
using several
different passive security devices to secure a single article of merchandise.
A person trying to
defeat a system would therefore have to have knowledge not merely of a single
frequency, but
also knowledge of multiple frequencies and/or codes in order to kill whatever
passive security
devices are on an article.
[0038] A passive security device may also have the capability to
respond to a
detection signal by a return signal which identifies the specific article in
some way such as by
its bar code information. This would require a unique passive security device
for the specific
article of merchandise stocked for sale.
[0039] There may be instances where management or staff needs to
remove from
secured premises one or more secured articles which have not been sold. A
separate kill
transmitter under the control of management may be used to kill the passive
security devices
on such articles so that they can be removed without triggering an alarm.
9
CA 02823174 2013-08-07
[0040] The security system shown in and described with reference to
Figure I can
provide conclusive proof of attempted theft. Upon detector 40 issuing an alarm
indicating that
a person is carrying an unpaid-for article of merchandise into exit area 22,
the person can be
stopped by store and/or security personnel and asked for a cash register
receipt to prove the
article has been paid for. In the absence of such proof, the article is then
first transported out
of range of the detection signal from detector 40 and then brought back into
range, causing an
alarm to once again be issued. These events are recorded on recorder 46 with
witnesses
present. This proves that the passive security device was live when the person
first attempted
to remove it from the premises.
[0041] With witnesses still present, the article is then brought to an
idle check-out
counter 24 and processed as if it were being paid for. Register 36 will cause
kill transmitter 52
to unsecure the article by killing the passive security device. The article is
then brought back
to exit area 22 where it will not trigger an alarm. This scene is also
recorded with witnesses
present and proves a second time that the article was not paid for.
[0042] Certain prospective users of the system and method disclosed
herein may
already have an inventory control system in place using individual R.F.I.D.
tags (radio
frequency identification tags) applied to each article of merchandise to
identify the particular
article. An R.F.I.D. tag is a form of passive security device. Those R.F.I.D.
tags may also be
used as passive security devices in the system and method disclosed herein to
provide a
combined inventory control and security system.
[0043] The combined system registers entry of secured articles of
merchandise for
sale into inventory within the premises and distinguishes between authorized
and attempted
unauthorized removal of secured articles from the premises.
[0044] The combined system comprises an inventory control sub-system
for
registering entry of articles for sale into the premises by scanning inventory
control R.F.I.D.
tags on the articles and causing each article whose R.F.I.D. tag has been
scanned to be
registered in an inventory data base, and a security sub-system for
distinguishing between
authorized and attempted unauthorized removal of articles registered in the
inventory data
base from the premises.
CA 02823174 2013-08-07
[0045] The security sub-system comprises i) a detector for wirelessly
detecting
attempted unauthorized removal of articles from the premises by detecting
R.F.I.D. tags on the
articles when their unauthorized removal is attempted, ii) a register for
registering an article
for authorized removal from the premises by scanning its R.F.I.D. tag and for
subtracting the
article which has been registered for authorized removal from inventory in the
inventory data
base; and iii) an unsecuring transmitter controlled by the register for
wirelessly transmitting to
the R.F.I.D. tag on the article which has been registered for authorized
removal, an unsecuring
signal which unsecures the secured article by changing the R.F.I.D. tag from
an article-
securing state which renders the R.F.I.D. tag wirelessly detectable by the
detector to a non-
securing state which renders the R.F.I.D. tag wirelessly undetectable by the
detector.
100461 While a presently preferred embodiment has been illustrated and
described,
it is to be appreciated that the invention may be practiced in various forms
within the scope of
the following claims.
11