Note: Descriptions are shown in the official language in which they were submitted.
CA 02880904 2015-02-03
WO 2014/(1258(19
PCT/US2013/053835
COMPUTERIZED METHOD AND SYSTEM FOR MANAGING SECURE CONTENT SHARING IN A
NETWORKED SECURE COLLABORATIVE. EXCHANGE ENVIRONMENT
CROSS-REFERENCE TO RELATED APPLICATIONS
100011 This application claims the benefit of the following provisional
applications, each of which are
hereby incorporated by reference in its entirety: U.S. Patent Application No.
61/680,115 filed August 6,2012; U.S. Patent
Application No. 61/702,587 filed September 18, 2012; U.S. Patent Application
No. 61/715,989 filed October 19, 2012; U.S.
Patent Application No. 61/734,890 filed December 7, 2012, and U.S. Patent
Application No. 61/783,868 filed March 14,
2013.
100021 This application is a continuation-in-part of the following non-
provisional application, which is
hereby incorporated by reference in its entirety: 13/871,593 filed April 26,
2013, which claims the benefit of the following
provisional applications, each of which is incorporated by reference in its
entirety: U.S. Patent Application No. 61/639,576
filed April 27, 2012, U.S. Patent Application No. 61/680,115 filed August 6,
2012; U.S. Patent Application No. 61/702,587
tiled September 18, 2012; U.S. Patent Application No. 61/715,989 filed October
19, 2012; U.S. Patent Application No.
61/734,890 filed December 7, 2012, and U.S. Patent Application No. 61/783,868
filed March 14, 2013.
FIELD OF THE INVENTION
100031 The present invention relates to networked secure content sharing
and collaboration.
BACKGROUND
100041 Despite the availability of the Internet, there is still no
entirely satisfactory way for people at
different companies or other entities to have the benefits of private network
security, such as for collaborative work between
enterprises on a daily basis and for ad hoc alliances, i.e., different sets of
entities coming together to function as one mega or
meta entity, for the duration of some particular project. In such cases, the
time and expense of actually wiring a network
between two or more companies or other entities and agreeing on one common
software package or standard presents a
barrier to conventional network solutions. In addition, any new process for
the sharing of content has in the past generally
required the user to adopt new workflow components, applications, and habits
that tend to be disruptive to the user's normal
day-to-day workflow routine, e.g. when working internal to their enterprise
and with personal use. Simply using the Internet
remains imperfectly secure for the sharing of confidential information without
some pre-arranged secure encryption
processes has been cumbersome and unproductive, especially in today's
increasing use of personal devices being
incorporated into the workflow. There is a need for such systems and for users
to utilize the systems in such a way that does
not force them to adopt new infrastructure, software, and business and
personal processes in their daily workflow in order to
achieve a shared and potentially secure extended work environment.
100051 Thus, there are still yet-unsolved problems associated with
different groups of companies or other
entities to sharing securely over an expanding global network environment.
SUMMARY
100061 The present disclosure describes methods and systems for securely
sharing content (e.g., computer
data content, such as documents, presentations, spreadsheets, emails, blog
entries, texts, and the like) that allows for `tui-
sharing' of the content in a managed, secure manner. The facility to un-share
content may be implemented through the
content being shared along with a secure protection feature, such as being
encrypted and wrapped in a unique DRM wrapper,
where the protection feature specifies a user or group of users that are
authorized to access the content for viewing. When
the content is shared with that user, access to the content may be revoked at
any time (e.g. by changing the DRM, removing
access to the key, changing permissions, and the like). Further, if the sender
of the content controls the protection feature,
then the sender has complete lifetime control of any content they distribute
or provide access to. This secure un-sharing
1
CA 02880904 2015-02-03
WO 201-1/025809
PCT/US2013/053835
facility may be used to securely share content beyond the secure protective
facilities of their enterprise (e.g., allowing secure
sharing beyond the firewall of the sender's enterprise), out to users in other
companies, into the public space, to users not
intended to get the content, and the like, where the sender maintains complete
control to access of the content, no matter
where or to who the content has been distributed. In this way, the secure
sharing of content is made to be easy across
corporate boundaries at the user level and at the individual content level
(e.g., at the level of an individual document).
100071 In embodiments, a method for managing a networked secure
collaborative computer data exchange
environment may be provided, comprising establishing, by a secure exchange
server managed by an intermediate business
entity, a user login data authentication procedure that allows a user through
at least one client computing device to access the
secure exchange server, wherein the user is one of a plurality of users of a
plurality of other business entities and
communications between the secure exchange server and the plurality of users
is through a communications networlc;
storing, by the secure exchange server, at least one user login authentication
data far at least one of the plurality of users;
receiving a computer data content from a first of the plurality of users,
wherein the first of the plurality of users permits a
sharing access to the computer data content to at least a second of the
plurality of users, and wherein management for access
to the computer data content is through an exchange content access facility
managed by the intermediate business entity;
granting, by the secure exchange server, sharing access to the computer data
content to the at least second of the plurality of
users when the secure exchange server receives from the second of the
plurality of users its client login authentication data
provided that the second of the plurality of users is one of the subset of the
plurality of users to which sharing access is
permitted; receiving a request from the at least second of the plurality of
users to access a copy of the computer data content;
granting, by the secure exchange server, the copy access request to the at
least second of the plurality of users, wherein a
copy of the computer data content is made; receiving from the first of the
plurality of users a request to revoke sharing access
to the computer data content to the at least second of the plurality of users;
revoking, by the secure exchange server, sharing
access to the computer data content to the at least second of the plurality of
users; and deleting access, by the secure
exchange server, to the copy of the computer data content made by the at least
second of the plurality of users. In
embodiments, additional sharing of the computer data content within the
plurality of users may be made, wherein the
revoking of sharing access to the computer data content revokes access to all
instances of the shared computer data content
and all copies of the computer data content made by the plurality of users.
The copy of the computer data content may be
stored on the secure data server, wherein the copy of the computer data
content may be deleted from the secure data server,
and wherein the deleting access to the computer data content may make the
computer data content inaccessible to the at least
the second of the plurality of users. The copy of the computer data content
may be stored on a client computing device by
the at least second of the plurality of users. The deleting access to the copy
of the computer data content may be revocation
of digital rights management of the computer data content The revocation of
the digital rights management of the computer
data content may be made by the first of the plurality of users. The computer
data content may be a word processor
document, a spreadsheet document, a presentation document, an email, a text, a
blog entry, a multimedia file, and the like.
The computer data content may be a secure encrypted computer data content. The
computer data content may be viewed by
the at least second of the plurality of client users through a secure viewing
facility. The at least second of the plurality of
users may be connected to a public network that is outside of the firewall for
the business entity that manages the first or
second of the plurality of users. The at least second of the plurality of
users may access the computer data content through a
personal computing device that is not owned by the business entity that
manages the at least second of the plurality of users.
The at least second of the plurality of users may access the computer data
content through a mobile computing device. The
exchange content access facility may be interfaced through a dashboard
facility accessible though at least the first of the
plurality of users. The dashboard facility may provide reports showing
activity related the sharing of computer data content
The dashboard facility may be accessible through third-party environments. The
dashboard facility may track the location
and version of the shared computer data content on computing devices
accessible by the at least second of the plurality of
users. The communications network may be a wide area network, such as the
Internet.
2
CA 02880904 2015-02-03
WO 201-1/025809
PCT/US2013/053835
100081 In embodiments, a method for managing a networked secure
collaborative computer data exchange
environment may be provided, comprising establishing, by a secure exchange
server managed by an intermediate business
entity, a user login data authentication procedure that allows a user through
at least one client computing device to access the
secure exchange server, wherein the user is one of a plurality of users of a
plurality of other business entities and
communications between the secure exchange server and the plurality of users
is through a communications network;
storing, by the secure exchange server, at least one user login authentication
data for each of the plurality of users; receiving
a computer data content from a first of the plurality of users, wherein the
first of the plurality of users permits a sharing
access to the computer data content to a subset of the plurality of users, and
wherein management for access to the computer
data content is through an exchange content access facility managed by the
intermediate business entity; granting, by the
secure exchange server, sharing access to the computer data content to
individuals within the subset of the plurality of users
when the secure exchange server receives from the individuals their client
login authentication data; receiving a request from
at least a second of the plurality of users to access a copy of the computer
data content; granting, by the secure exchange
server, the copy access request to the at least second of the plurality of
users, wherein a copy of the computer data content is
made; receiving from the first of the plurality of users a request to revoke
sharing access to the computer data content to the
subset of the plurality of users; and revoking, by the secure exchange server,
sharing access to all instances of the computer
data content to the subset of the plurality of users. In embodiments, the
revoking of shared access to all instances of the
computer data content may be revoking shared access to all instances of the
computer data content on all computer devices
that the subset of the plurality of users have stored the computer data
content. The stored computer data content may be a
copy of the computer data content. The stored computer data content may be an
annotated version of the computer data
content.
100091 These and other systems, methods, objects, features, and
advantages of the present invention will be
apparent to those skilled in the art from the following detailed description
of the preferred embodiment and the drawings. All
documents mentioned herein are hereby incorporated in their entirety by
reference.
BRIEF DESCRIPTION OF THE FRAMES
100101 The invention and the following detailed description of certain
embodiments thereof may be
understood by reference to the following figures:
100111 Fig. 1 depicts a top-level block diagram of the present
invention.
100121 Fig. 2 depicts functions of a host in an embodiment of the
present invention.
100131 Fig. 3 depicts a functional block diagram for the community
facility in an embodiment of the
present invention.
100141 Figs. 3A-3R depict embodiments of the community facility user
interface.
100151 Fig. 4 depicts a functional block diagram for the amendment
voting facility in an embodiment of the
present invention.
100161 Fig. 4A depicts a flow diagram for an embodiment process flow of
the amendment voting facility.
100171 Figs. 4B-4H depict embodiments of the amendment voting facility
user interface.
100181 Fig. 5 depicts a functional block diagram for the secure e-
signing facility in an embodiment of the
present invention.
100191 Figs. 5A-5G depict embodiments of the e-signing process user
interface.
100201 Fig. 6 depicts a functional block diagram for the dashboard
facility in an embodiment of the present
invention.
100211 Figs. 6A-6K depict embodiments of the dashboard facility user
interface.
100221 Fig. 7 depicts a functional block diagram for the email-in
facility in an embodiment of the present
invention.
100231 Figs. 7A-7M depict embodiments of the email-in facility user
interface.
3
CA 02880904 2015-02-03
WO 2014/(1258(19
PCT/US2013/053835
100241 Fig. 8 depicts a functional block diagram for the viewer facility
in an embodiment of the present
invention.
MOM Figs. 8A-8G depict embodiments of the viewer facility.
100261 Fig. 9 depicts a functional block diagram for the mobile device
interface facility in an embodiment
of the present invention.
100271 Figs. 9A-9K depict embodiments of the mobile device viewing
interface.
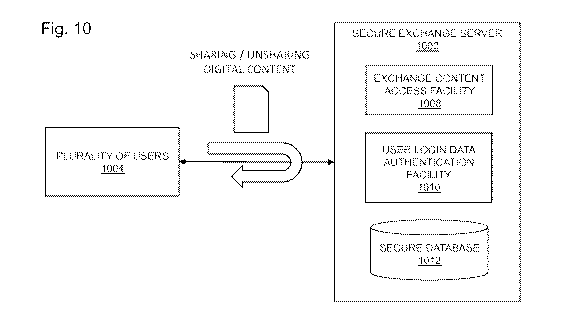
100281 Fig. 10 depicts a functional block diagram for an un-sharing
facility in an embodiment of the
present invention.
100291 Fig. 10A depicts an illustrative process flow diagram that in
part describes an interaction utilizing
the un-sharing facility.
100301 While the invention has been described in connection with certain
preferred embodiments, other
embodiments would be understood by one of ordinary skill in the art and are
encompassed herein.
100311 All documents referenced herein are hereby incorporated by
reference.
DETAILED DESCRIPTION
100321 The present invention may be used for a secure exchange service
(alternatively referred to as an
'exchange' or 'exchange service' throughout this disclosure) where many types
of communications are requited between
different parties that are associating for a temporary transaction or project,
but as competitors or for other reasons are not
suitable for a permanent communication network (such as an intranet or
enterprise network, such as a LAN or WAN) as
might be used fbr a single government agency, single corporation, or other
single enterprise or institution. Transaction
projects involving financial transactions and projects involving complex legal
agreements (such as mergers, acquisitions, and
the like) are situations in the which the methods and systems described herein
are particularly suitable; however, these are
not necessarily the only sort of projects appropriate, as any project in
which parties need to share confidential information
across entities, outside the boundaries of the network of a single entity, may
benefit from the methods and systems described
herein.
100331 In an example, transactions within the banking industry may
provide a situation where a secure
exchange service may be particularly applicable, where ad hoc syndicates are
formed under the leadership of one or more
lead banks to permit a number of agent or associate banks to participate in a
major loan to a borrower. Such loans have
become more common and may involve loans in excess of one billion dollars.
Syndication of such large loans is used since
any one bank is not prepared to lend such a large amount to a single customer.
Conventionally, proposed terms of a loan are
negotiated between the borrower and the lead banks, each in consultation with
its advisors such as legal counsel, public-
relations consultants, accountants and insurance carriers. In some instances,
some advisors may be in-house advisors as
employees of a given entity and thus constitute an internal team. However, the
advisors in many instances may be
independently associated with external entities such as law firms or major
accounting firms and thus constitute either
external teams or combinations of the above. The lead bank(s) negotiates with
the borrower to arrive at terms and conditions
for the loan, such as the interest rate, repayment schedule, security and the
bank's fee for processing and syndicating the
loan. The lead bank may agree to underwrite the entire loan in which case the
lead bank uses syndication to create sub-loans
between it and other banks to raise the funds for the loan. All of these
transactions require management of voluminous
amounts of documentation, most of which is confidential and whose disclosure
could result in huge damages to the borrower
or lenders. Thus, it would be desirable to provide an exchange as described
here which enables secure document
transmission between users over a global communication network without
requiring the users to communicate in advance to
establish an encryption method. In this example, the exchange service may
provide a suitable level of security with respect
to each of the shared transactions, among companies that commonly may be
vigorous competitors, with numerous
confidential documents that the companies do not want uncontrollably shared
among other members of the loan-project
group or accessible by outsiders generally. Substantially secure
communications is particularly of the utmost concern to all
4
CA 02880904 2015-02-03
WO 2014/025809
PCT/US2013/053835
parties to a syndicated loan transaction: the borrower, the lead bank, and the
associate banks. A virtual network system
provided through the exchange may readily provide substantial security to
ensure that information and communications
among all the various parties are secure.
100341 In embodiments, the exchange may enable electronic transmission
and reception of confidential
documents over a global communication network such as the Internet for
distributing electronic documents containing
sensitive information or data to selected entities, for notifying intended
recipients of the availability of such documents, for
tracking access, downloading and uploading of such documents, and the like.
100351 In embodiments, the exchange may only be accessed by authorized
computers using an acceptable
log-in procedure, including user name and password. Communications within the
exchange may establish a communication
session based upon a selected security protocol, and thereafter messages are
transmitted between using such secure
encryption. Communications may be exchanged via a secure encrypted
communication session using a selected encryption
protocol, and may deny access if a secure session cannot be established at a
desired secure level.
100361 In embodiments, the exchange may provide a filly provisioned,
turnkey service for users, where
once the user's enterprise has established an account through the exchange,
documents in electronic form may be uploaded
to the secure site maintained through the exchange host server, where a
variety of secure collaborative communications
options may be chosen including document storage, e-mail, video broadcasting,
video confemneing, white boarding, and the
like, to augment and manage interactive access to the documents, including a
user graphical interface for managing user
interactions with one or more exchanges.
100371 In embodiments, the exchange may provide a secure site for
placing documents and messages to be
transmitted over a secure virtual network and allows authorized users to read
or edit messages according to their level of
authorization. Any documents that are edited may be immediately available on
the system so that other persons involved in
the exchange has access to the edited or modified documents immediately. In
addition, the exchange may provide tracking of
each document to allow selected users to see who has had access to the
messages and documents and who has modified or
edited any of the documents.
100381 In embodiments, the exchange may provide a centralized firewall
that may be employed to protect
confidential information so that no unauthorized access to such information
occurs. A firewall, such as may be effectively
used for corporate intranets, may be applied in each exchange. Groups of
users, such as on a virtual network, may be treated
like a remote comorate office and restricted by firewall protocols from
uncontrollable access to the information from other
users. In addition, if needed, respective inter-user ftrewalls may be
established to prevent one user from accessing
information in the host site of another user. The exchange may be particularly
suitable lbr communication among multiple
unrelated groups of users, since a centralized firewall simplifies the
logistics of each user having to separately provide access
through their own respective local firewalls. In such a centralized
architecture, the host server, as opposed to being processed
at each respective user, may conveniently process server access security data.
Similarly, system backup and recovery may be
better handled by a centralized backup and recovery system, as opposed to such
recovery tasks being separately handled at a
multiplicity of local sites.
100391 As depicted in Fig. 1, a plurality of exchange service users 110
of the exchange service may
exchange data, such as documents, messages, data, and the like, between a
secure host server 102 and a plurality of user
computers 104, 104A, 104B across a network 108 (e.g. the Internet) in a secure
manner such as only accessed by authorized
user computers using an acceptable log-in procedure. In embodiments, the user
computers may interface with the network
through a network server, a mail server, and the like, and in association with
an enterprise intranet, where a firewall is
present between the user computer and the network, and where the exchange is
conducted between the user computers and
the host computer through a secure exchange across the network and through the
network server, mail server, and the like.
In another embodiment, the user computers may interact in the exchange with
the host server across the network while away
from or in the absence of the enterprise intranet and enterprise firewall. For
instance, the user may be able to access the
CA 02880904 2015-02-03
WO 2014/(1258(19
PCT/US2013/053835
exchange while at home, such as using a mobile enterprise computer, a
personally owned computer, a mobile device, and the
like.
100401 In embodiments, the exchange host server 102 may be distributed
over a plurality of server
computers, and therefore host server 102 should be viewed as an illustrative
example of one of such multiple servers. In this
way, the server computers may work together to provide essentially seamless
access to a large number of users on various
plattirms with varying communications speeds. The server computers may run
under server management software which in
turn may be responsible for coordination of services, maintaining state and
system status, monitoring, security, and other
administrative functions. In embodiments, a user computer having a suitable
Web browser may directly access the host
server, where the exchange may not need to provide each user with subscriber
application software, such as including
software modules for access, activation, viewing, communications, and the
like, relative to the exchange service.
100411 In embodiments, whenever an exchange of data is initiated, such
as by a document being received
at the host server 102 connected to a host database 112, the host server may
extract the address of the intended recipient and
create a notification to the recipient(s) of the existence of the data at the
host server. The notification may contain the URL.
for the host server. However, the recipient may not be able to access the
message unless the recipient is authorized to use the
system, such as the recipient needing to be a registered user and have an
assigned password to access the data, or other
repository at the host server where data is stored, such as on a user database
108, 108A, or 108B. If the intended recipient is
granted access to the host server, the recipient may then locate the message
intended for them by browsing through all
messages to which the recipient has been granted access.
100421 While the notification sent to the intended recipient may be sent
using standard Internet protocol
without encryption, once the user computer contacts the host server, the
server may establish a secure encrypted
communication session using a selected encryption protocol. The host server
may deny access if a secure session cannot be
established at a desired secure level, such as 128-bit encryption.
100431 In embodiments, exchange services for different users may utilize
separate software structured
server databases 108, 108A, 108B. For example, company 'A' and company 'B' may
use the same secure host server 102,
but each company's data may be maintained in separate databases 108A and
10813, although perhaps in the same physical
data storage facility. This feature offers the advantage of allowing the host
server to be customized for each company. For
example, when the external user accesses the host server, the host server may
recognize the user and associate the user with a
particular one of the companies A and B. Using this recognition, the host
server may present a customized browser interface
which makes the host server look like the selected company. To the external
user, it may appear that they have been
connected directly to the company server rather than the host server. Thus,
the present invention may allow a user to
securely send data such that the network connection is substantially
transparent to the user. Further, the system may provide
customization of the remote host server for each of a plurality of different
users such that an external user accessing the
remote server may appear to be connected to an internal client server.
100441 Fig. 2 shows fluffier details in connection with the server
software that may be readily incorporated
in the host server 102, including a community facility 202, amendment voting
facility 204, e-signing facility 208, dashboard
facility 210, email-in facility 212, viewer facility 214, mobile device
interface facility 218, network service facility 220,
distribution facility 222, interface facility 224, format conversion facility
228, sign-on facility 230, encryption facility 232,
usage facility 234, syndication facility 238, transaction identification
facility 240, link facility 242, user authorization facility
244, authorized reader facility 248, authorized editor facility 250,
notorization facility 252, multimedia facility 254,
comment facility 258, and email facility 260.
100451 For example, the distribution facility 222 may allow the host
server to electronically distribute data
using secure communications among the plurality of users. The usage facility
234 may allow the host server to monitor the
usage of the network to permit the users to be billed for the network service.
The host server may be set up to manage a
plurality of separate virtual networks concurrently, with each such virtual
network representing a different client, such as
company A and company B. Further, a community facility 202 may provide for
users of different companies to be exposed
6
CA 02880904 2015-02-03
WO 2014/025809
PCT/US2013/053835
to one other even if the different companies have not had any previous
contacts (e.g. through a shared exchange), and a
dashboard facility 210 may provide companies to manage exchanges, documents,
contacts, communications, preferences,
and the like.
100461 The host server may offer a high level of security for all data
by employing substantially secure
network connections, and by means of security and encryption technologies
developed for networks such as may be readily
incorporated in the encryption facility 232. Additionally, the host server may
provide highly secure access control by way of
the user authorization liscility 244 that may allow only authorized personnel
to access individual messages and related
documents and communications. The viewer facility 214 may be able to protect
documents from unauthorized viewing,
printing, saving, and the like, and a mobile device interface facility 218 may
enable secure viewing on a mobile device, such
as a personal tablet being used away from an enterprise network. The Email-in
facility 212 may provide for the ability to add
content to an exchange using regular email, such as that is sent to a
designated secure email address.
100471 The host server may give each user the ability to electronically
link or be interconnected via a link
facility 242 with any number of other users. Although data may be preferably
formatted in a particular form, such as may be
readily implemented with a commercially available document exchange program,
other fermis could be optionally
accommodated using a suitable format conversion facility 228. The multimedia
facility 254 may also be used to process data
into a format suitable for presentation to the user in forms other than text,
such as audio, still or moving images, and the like.
100481 The virtual-network viewer may also include a multimedia viewer
facility configured to, for
example, provide: viewing of interactive multimedia or mixed media memoranda
through suitable decoders, such as audio
decoders, Joint Photographic Experts Group (JPEG) still image decoders, and
Moving Pictures Experts Group (MPEG)
moving image decoders. The virtual-network viewer may also support various
collaborative communications options such as
e-mail, video conferencing and white boarding which are enabled for a given
transaction pursuant to instructions from the
appropriate user. Of course, the range of multimedia capability and the
collaborative communications options may vary
depending on the various groupware facilities available to the user.
100491 The notarization facility 252 may be provided to electronically
certify any electronic data forwarded
to users, such as incorporating electronic signature technology, and the like.
The network service facility 220 may
conveniently be used to display various data in connection with the network
service such as additional services that may be
available by the network service to the users. The above facilities may work
jointly with the email facility 260, the interface
facility 224, and the like, to send notices of data for exchange and interface
with to securely pass data.
100501 A virtual-network viewer or browser may conveniently provide the
end user with an easy-to-use
graphical interface to data and other particularly confidential information on
the network service's virtual-network service.
The virtual-network service may provide identification of services available
over the virtual network as well as a variety of
options for accessing and retrieving data. The virtual-network viewer may
include the transaction identification facility 240
that, fbr example, may enable a user to quickly find and access information.
The virtual-network viewer may automatically
provide a suitable connection to the user to the virtual-network service
through the sign-on facility 230. The viewer may also
prompt the user to input one or more passwords or identifications which should
be recognized by either the authorized editor
facility 250 or the authorized reader facility 248 in order to access
information on a database.
100511 For the convenience of the users, some data offered through the
virtual-network service may be
designed as interactive multimedia documents that will include video,
graphics, audio, and other multimedia elements.
Multimedia communications may provide the user with a wide variety of
information in addition to that provided by more
standard text data.
100521 By way of an example, a syndication desk, i.e., one or more
individuals authorized to be responsible
for the management of a syndicated transaction, of a lead user may be able to
broadcast and/or selectively send e-mail
messages processed by the syndication facility 238 to associate users and vice-
versa. For example, amendment data
processed by the amendment voting facility 204 may be used to vote on changes
to a transaction document amongst
authorized users. The amended document may be conveniently distributed via
email using the e-mail facility 260 for
7
CA 02880904 2015-02-03
WO 201-1/025809
PCT/US2013/053835
providing associate users with up-to-the-minute information about the
transaction. Amendments or messages may be
appended to the documental the host site of the network service where they may
be ordinarily viewed by accessing the
virtual-network service that is authorized to access the document. E-mail
messages or amendments may also be downloaded
for printing or for attachment to local documents. Similarly, comment data in
connection with a transaction may be
processed through the comment facility 258 for appropriate distribution to
authorized users. Transaction documents may
also be signed by authorized users through the e-signing facility 208.
100531 Referring to Fig. 3, the community facility 202 may provide
community, social, and the like
facilities, as part of the system, such as to be able to expand a user's
contacts list through exposure to other users who use or
are otherwise associated with the facilities and more generally to make it
easier for users to find and connect with other users
who may have mutual interests. The community facility 202 may allow community
users 302, such as the plurality of
exchange service users 110 and plurality of other community users 304, to find
one another using industry-specific profiles,
such as provided by a profile manager 308, to find other community users,
invite users to communicate by sending
invitations through a communications manager 310, see status of invitation
that have been sent or received, and the like.
Through a community user interface 312 and associated profile manager 308,
communications manager 310, and profile
search facility 314, the community facility 202 may provide the user with a
larger visibility to the plurality of users in the
system, allow them to declare how they want to be viewed, control whether they
want to be viewed, determine whether they
can participate or not, enable them to be anonymous (e.g. profile only), allow
them to be fully visible to other users, allow
them to be available to users within just a particular industry, and the like.
If a user is in a particular industry, they may be
able to view a basic description of that community, as well as to other
industries that the user determines to be beneficial.
The system may be provided a profile window in the community user interfat:e
312 that is set up based on industry or
technical specifications, such as for private equity, lvf&A, finance, legal,
and the like. There may be a variety of different
types of user profiles available, such as, in connection with transactions, a
buyer side, an investor side, an advisor side, an
expert side, a seller side, and the like. The community user interface 312 may
provide a user set up through a step-through
process wizard, where the user selects industries, subsets of industries, and
the like. Users may be as specific or as general
as they wish, and position themselves in the community as seeking
opportunities, presenting opportunities, presenting
themselves as an expert to be called on to facilitate, and the like. The
system may provide for location information, specify a
deal type, specify a deal size, and the like, to help people who are searching
for these profiles. The user may be able to
upload attachments, examples, and the like. A visibility setting may be
provided, such as available to community members,
where the user is optionally able to remain anonymous. If the user chooses to
not be anonymous then they may be visible to
users immediately, but still protected in the system. In an example, a user
may be a "buyer" and an "advisor", where they
can see their own profile or sub-profile, edit the sub-profile, add another
profile, and the like.
100541 In embodiments, the community facility 202 may provide for search
capabilities through the profile
search facility 314, such as starting a new search, saving searches, saving
the history of a search, and the like, to begin
interacting with the profiles of users. The watcher may be able to search by a
particular industry, investors, deal size, deal
type, geography, type of profile and the like. The user may begin a search and
generate results including the sub-profiles in
the system that matched the search criteria. In addition, there may be a
variety of visibility levels associated with the
searches. For example, a search may return three matches but where one match
is a user that is an anonymous user. In this
instance, information may be withheld as to specifics, but with the ability to
see more general profile attributes, such as a
user's title. Them may also be search indicators associated with previous
searches, matches, contacts, and the like, such as
with an icon to indicate past communication, and the like. In embodiments, the
user may use a filter set to find a group the
user wants to multi-select, grab, and move into another list.
100551 Another feature of the community facility may be an 'activity
index', or similar measure, such as
for judging how active a user is on the system. For instance, a user
performing M&A activities on the system may provide a
qualified view indicating whether they are a current M&A buyer or not, such as
showing how active they are. The system
may also find information that indicates activity from other sources, and
import that information to the system, thus
8
CA 02880904 2015-02-03
WO 2014/(1258(19
PCT/US2013/053835
providing a fuller indication of the user's activity level within the system,
such as how many deals they might be working
on.
100561 Another feature of the community facility may enable a user to
entice other users who are
anonymous to be visible in order to initiate an interaction with them. For
instance, a user may contact an anonymous user
and add them to an exchange after the invitation to connect has been accepted.
The user may 'click on' an anonymous user
and send an invitation to them. In this instance, the sending user may become
more visible to the anonymous user who is
being invited. A subject line and a note regarding why the user is interested
in contact them may be provided. An
'invitations list' may show what invitations have been sent, and the system
may provide for a historical thread for the user's
activity.
100571 In embodiments, the system may keep a user's information
anonymous until the user accepts an
invitation from the inviting user, but where the anonymous user can still
interact with the inviting user while still staying
anonymous. The system may therefore provide a robust interaction facility at
the profile level (email, etc.) without requiring
actual acceptance of the invitation, and enable a continued dialog without
revealing who they were (e.g., to get additional
information, clarification, etc.). As the interaction goes back and foith, the
goal may be to wind up in an acceptance state,
but the system may also provide a means of blocking communications, such as
after the user 'accepts' or 'declines'. The
system may support an interaction until the user provides an acceptance, at
which time the user's contact information may
become visible, be provided a download of profile information, include the
user in a contacts list, be recommended to an
exchange, and the like. Once the user accepts, both parties may become visible
to one another, including providing a history
of the interaction.
100581 Referring to Fig. 3A, the community facility may provide a user
interface for user interaction with
the community facility, such as a with a profile tab for a user. In
embodiments, a new profile may be added through the user
interface. Referring to Fig. 3B, the user interface may provide for
identification of a sub-file, selection of an industry,
selection of a geography, setting profile details, setting visibility,
adjusting a privacy policy, and the like. in embodiments, a
view for setting visibility may be provided, where the user may specify
visibility to community members, such as being
visible to community members, visible but anonymous to community members (e.g.
contact information and attachment(s)
are hidden), visible only the user, and the like. Referring to Fig. 3C, an
example profile is provided for an lvf&A seller
seeking investors, the profile including an industry focus (materials), deal
sizes (<$25 Million), geography (Asia/Pacific),
deal type (full entity sale/merger), visibility (anonymous), and the like.
100591 The community facility user interface may provide for a plurality
of tabs, such as a hub, exchanges,
tasks, documents, people, approvals, maintenance, forms, calendar, dashboards,
fund data, collaboration, and the like.
Referring to Fig. 3D, a people tab may include contacts, groups, community,
and the like, and a community tab may show
community invitations. When the community tab is displayed, there may be
search results displayed, no search results
displayed, a button for starting a new search, and the like. Fig. 3E shows an
example search result, including two visible
users, an anonymous user, and the like.
100601 There may be actions the user may take with regard to a search
result, such as to make contact, open
an invitation, view detail, download a vCard, request to add a user to an
exchange, manage a user exchange access, and the
like. When a user is anonymous, an indication of such may be provided in place
of their name, such as `User is
Anonymous', blanks in place of location, phone number, email contact
information, company, and the like. Fig. 3F provides
an example for an interface for composing an invitation. Users that receive an
invitation may be asked to accept or decline
the invitation, and the sending user may receive replies as email alerts
(e.g., such as available under the community
invitations section of the user interface). The invitation may include a
subject, note, number of users the invitation is being
sent to, information about the sending user (e.g. name, email ID, phone
number), a cc function, and the like. An invitation
may be provide to a visible user, an anonymous user, logged-in users, logged-
out users, and the like. Successfully sending
an invitation may result in an acknowledgement, such as an invitation alert, a
text alert, and the like. Fig. 30 shows an
example of an 'alert sent' indication. An indication of a successful alert
sent may also include a dialog indication, a title of
9
CA 02880904 2015-02-03
WO 20141025809
PCT/US2013/053835
the invitation, the body of the invitation, and the like. Users that receive a
note may be able to reply directly to the sending
user's email address, as shown in an example in Fig. 31-I. Figure 31, shows an
example of what user information may be left
blank when the user is an anonymous user, such as email contact information,
organization, position, industry, functional
area, address infermation, phone number(s), fax number, and the like. Fig. 3J
shows at least a portion of the information that
may be hidden, such as in this example that the user is an M&A advisor/expert,
area of expertise is investment banking,
industry focus areas (e.g. industrials, financials, utilities,
telecommunication services, health care, information technology,
energy, consumer discretionary, materials, consumer staples), deal sizes,
geography, and the like. Fig. 3K shows an example
of a user rabox showing the invitation alert. Fig. 3L shows an example of
options available to the recipient of an invitation,
such as to accept or decline the invitation, where Fig. 3M shows an embodiment
'decline invitation' screen, and Figs. 3N
and 30 shows an embodiment overview for invitations sent, received, accepted,
declined, and the like. Fig. 3P shows a
running communications thread between two users in association with an
invitation, where as shown, the accept-decline
options may continue to be presented to the recipient of the invitation until
they accept or decline the invitation. Fig. 3Q
shows an embodiment contacts search.
100611 Fig. 3R depicts an example contact flow between two users. As
shown, user I has set up a sub-
profile that includes setting their visibility to anonymous. User 2 conducts a
community search and finds user 1, where user
2 opens a user details page(s). User 2 then sends an inquiry to the anonymous
user I, where user 1 receives the inquiry (such
as in their email inbox) and views the invitation in the community user
interface. User I then has the option to accept or
decline the invitation, where user I then closes the reply window. User 2 is
able to see the inquiry status, such as through
searching, where user 2 sees the inquiry, sees the status of accept or
decline. User 1 is able to view the thread of the
accepted/declined notes.
100621 In embodiments, a method for managing a networked secure
collaborative computer data exchange
environment may be provided, the method including establishing, by a secure
exchange server controlled by an intermediate
business entity, a client login data authentication procedure that allows at
least one client computing device of a plurality of
client computing devices operated by users of a plurality of business entities
to access the secure exchange server, wherein
communications between the secure exchange server and the plurality of client
computing devices is through a
communications network; storing, by the secure exchange server, at least one
client login authentication data for each of the
plurality of client computing devices; receiving content from a first of the
plurality of client computing devices; by the
secure exchange server, permitting access to the content for a subset of the
plurality of computing devices through an
exchange content access facility, wherein the exchange content access facility
is managed by at least one business entity of
the plurality of business entities; granting, by the exchange server, access
to the content to a second of the plurality of client
computing devices when the secure exchange server receives from the second of
the plurality of client computing devices its
client login authentication data provided that the second of the plurality of
client computing devices is one of the subset of
the plurality of computing devices; and providing an exchange community
facility where the users of the plurality of client
computing devices establish an informational profile that is made accessible
to other users of the plurality of client
computers and are enabled to interact with one another based on the content of
the informational profile.
100631 In embodiments, access to the exchange server by client
processors may be through a host server
controlled by the business entity that controls the client processor. The
client computing devices may be at least one of
owned and managed by at least one of the plurality of business entities. The
client computing devices may be owned by
individual users. The secure exchange server may be at least one of a
plurality of exchange servers. The content may be at
least one of a document, a spreadsheet, a message, data, an image, audio
content, video content, multimedia content, and the
like. The content may be transferred to the secure exchange server via
encrypted data transmission.
100641 In embodiments, the content of the informational profile may
include contact information, business
association, and the like. The exchange community facility may provide users
with facilities for sending an invitation to
another user for communication. After the invitation is sent the exchange
community facility may provide a status of the
invitation Mated to the invitation being at least one of being sent, received,
and read. The informational profile for the
CA 02880904 2015-02-03
WO 201-1/025809
PCT/US2013/053835
sending user may be restricted as anonymous until the receiving user accepts
the invitation for communication. The
exchange community facility may provide for informational profile viewing
control, where the viewing control allows the
informational profile to be viewed by other users, by a selected group of
users, and the like. The exchange community
facility may provide a graphical user interface through which a user manages
their informational profile and interactions
with other users, where the graphical user interface includes a search engine
interface, provides an activity index measure of
how active a user is on the exchange community facility, and the like. An
informational profile may be categorized by
professional activity, such as including a buyer, seller, investor, expert,
and the like. The informational profile may include
credentials for an individual, an indication of an area of interest (e.g. a
type of project in which an individual is interested in
participating), and the like.
100651 In embodiments, a method for managing a networked secure
collaborative computer data exchange
environment may be provided, establishing, by a secure exchange server
controlled by an intermediate business entity, an
authentication procedure for a client login authentication data that allows at
least one of a plurality of user client computing
devices operated by users of at least two business entities to access the at
least one secure exchange server, wherein
communications between the secure exchange server and the plurality of user
client computing devices is through a
communications network; storing, by the secure exchange server, the at least
one client login authentication data for each of
the plurality of client computing devices; receiving, from a first of the
plurality of user client computing devices, content;
associating access, by the secure exchange server, to the content to a subset
of the plurality of user computing devices
through an exchange content access facility, the exchange content access
facility managed by at least one of the plurality of
business entities; granting, by the exchange server, access to the content of
the secure exchange server to a second of the
plurality of user client computing devices when the secure exchange server
receives a client login authentication data from
the second of the plurality of user client computing devices and dependent
upon the second of the plurality of user client
computing devices being one of the subset of the plurality of user client
computing devices; and providing an exchange
community facility where the users of the plurality of client computing
devices establish an informational profile that is
made accessible to other users of the plurality of client computers and are
enabled to interact with one another based on the
content of the informational profile, wherein the interaction is executed as
an anonymous interaction, where the anonymous
interaction provides a subset of content from the informational profile.
100661 Referring to Fig. 4, the amendment voting facility 204 may
provide for managing, integrating, and
facilitating a process where agency clients executing a transaction (e.g. a
syndicated loan) may vote on modifications or
amendments to a transaction or transaction content, including an auditable
process 402, aggregated vote metrics 404,
centralized vote processing 408, and the like. The auditing process 402 may
utilize vote documentation, consent forms,
signature page tracking, digital distribution, vote collection, and signature
page submission, and the like, where the these
documents may be fully traceable. The distribution, vote collection and
signature page submission may all occur online,
speeding the process and better ensuring transparency. Aggregating vote
metrics 404 may utilize weighted voting
calculations for consent percentage, visualization of responses (e.g. which
lenders have done what), and the like, where vote
calculations may be weighted by commitment percentage, and where a visual
display of user responces may make it easy to
see which users have taken action, and what those actions are. Centralized
vote processing 408 may include sending
reminder alerts, completion of approval tasks, completion of a vote, and the
like. Features of the amendment voting facility
404 may include amendment templates for quick configuration and launch, lender
voting that includes signature pate
collection (e.g. with electronic submission of signature pages), task lists
for consent, an amendment voting user interface 410
to track progress and statistics (e.g. group tracking, simplified reminders,
export for vote tally and reporting), amendments
within existing exchanges, and the like.
100671 Referring to Fig. 4A depicts an embodiment flow process diagram
fur the amendment voting
facility, where an agency team initiates a vote response inquiry 420, such as
including documents, amendments, signature
pages, due dates, automatic alerts, and the like. I.enders may then receive an
alert 422, including task assignments, such as
for external counsel, the agency team, participants (e.g. lenders), and the
like. Documents (e.g., memos, signature pages)
11
CA 02880904 2015-02-03
WO 2014/(1258(19
PCT/US2013/053835
may be downloaded and tracked 424. Signature pages, such as a memo 428 with a
signature page 430, may be signed 432
and submitted 434 as a response. Participants (e.g., administrator agency,
external counsel) may receive the vote response
438. In an external process votes may be weighted 440, such as based on
committed dollar amounts on an agent's records.
The process may be finalized 442, such as with posting totals (e.g., for an
agent back team), where members of the process
(e.g. lenders and borrowers in a loan process) are notified. In embodiments,
the amendment voting facility may reduce or
eliminate the manual process surrounding a vote collection and consent
process, such as associated with a load process, and
helps the user efficiently prioritize a vote collection strategy.
100681 in an example, on a syndicated loan, one agency bank may be in
charge and have a number of
lenders supporting that loan, often hundreds or even in excess of a thousand
such lenders. As proposed modifications or
amendments are made, each may need to be disseminated, have users react to it
(such as providing information, making
selections, and the like), be returned with appropriate documentation to the
agency bank, and the like. A typical process is
conventionally performed offline, when banks are required to have signing
authorities pen-ink sign and re-submit to the
agency bank. Further to the example, when a new amendment comes up, the agency
bank may create a new transaction
exchange environment for the amendment process. Through a data link the lender
groups of members of those groups may
be pushed into the new exchange environment, such that each of them appears as
a participant in the exchange. Data relating
to all current positions of the lenders (the amounts of their financial
positions with respect to the particular loan or loans)
may also be pushed into the exchange, so that it is available for further
processing. In embodiments, the current position of a
user with respect to the transaction structure may have a bearing on the
voting, such as the weight given to a user's vote,
minimum amounts related to the amendment, and the like. Such amounts may be
stored and retrieved for processing by the
exchange. For instance, an agency bank may ask lenders to confirm their
understanding of their positions in the process,
some or all of the data with respect to positions may be pre-populated into
the system and carried through into the
transaction, and the like.
100691 In embodiments, the amendment voting facility may allow for the
naming of an amendment vote, a
date fur the vote, a vote distribution, inclusion of associated documents,
facility fur signature providing page submissions,
inclusion of instructions to voters, a process of approval, a step for outside
counsel to review, and the like. Once the
announcement for the vote is sent out, an administrator agent may be able to
view the tasks that have gone out, to what
individuals and groups, and the status of the voting. Features of the
amendment voting facility may include import and
export of commitment data, support of amendment vote collection workflow,
creation of vote template configurations,
configuration of election forms, display of an amendment voting graphical user
interface dashboard, configuration of
signature pages, access for an administrator to complete tasks, facility for
client-specific amendment vote definition, and the
like. Import and export may include users ability to populate a deal structure
automatically (e.g., from a source file), create a
list of lenders groups and tranches commitment information on a new deal
exchange, reconcile an existing deal structure,
generate reports (e.g. listing commitment amounts for each participant,
updating commitments, and the like. Support of
amendment vote collection workflow may include support of a plurality of
different amendment types and allow users to
create process definitions available for run-time execution, and the like,
when the different amendment types may include a
simple yes-no, a yes-no with signature, consent-no consent, amend and extend,
and the like. Amendment vote collection
workflow may include specification of due dates and time, collection of
election options, distribution of documentation, the
ability to edit voting parameters, and the like. Creation of vote template
configurations may include support of vote template
configuration creation, such as to encapsulate the amendment vote process for
document control management, including
users setting up owners, monitors, and vote elements once, and reusing for
subsequent votes; providing consistent language
and instructions and documentation across transactions and votes; setting up
vote types that may be adjusted as-needed, and
the like. The election form may be configured to allow users to dynamically
generate election forms based on group
participant relationships (e.g. lenders only having visibility to cases they
have access to). Display of an amendment voting
dashboard may include view of a list of multiple amendments initiated for a
particular transaction, view of details of the
process (e.g., list of lenders and their related status such s progress
against a task), view of participant contact and additional
12
CA 02880904 2015-02-03
WO 201-1/025809
PCT/US2013/053835
inlimmation, and the like. Configuration of the signature page may include
custom text, a logo, and the like, where users
may update and maintain their own custom signature pages, such as for all
transactions, per transaction, per vote, and the
like.
100701 Continuing with the syndicated loan example, a lender may receive
an email alert that they are
invited into a new amendment task process. They may then be asked to login,
where they are brought into the task flow that
came from the alert. Tasks may include instructions, document review, election
options, and the like. Pre-populated
information may also be provided in association with the task. The user may
record their vote and save any amendments
associated with their elections. Their election and amendments may be
printable, where the user may then take that
document to the signatory to have it signed. In this instance, all of the
infbrmation, including instructions may be included
in the hard copy for the lender, and where the signing indicates legal
consent. In this way, there may be one single entry
point of information, where the lender receives the document to be signed, has
it signed, and is provided a facility for
loading the document back into the system. In embodiments, an e-signature and
described herein may also be utilized for
signing the document and entry into the system.
100711 In embodiments, a user may be provided the user interface 410 to
view the exchanges that are
running amendments, to see tasks generated and what state they are in, to view
individual tasks for a particular lender, to
view signature pages (e.g., where all of the election option information is
carried), and the like. Custom fields may also be
provided, such as to allow users to change commitments. In embodiments, users
may see information as the data is
populated, even before signatures are applied. A user may need to perform a
calculation, such as to weight each vote to see
how close they are to carrying the amendment. The system may enable the user
to export data to a document (e.g., a
spreadsheet) for performing the calculation separate from the system, and to
monitor the amendment process and changes
thereto. For instance, and continuing with the loan syndication example, an
administrator agent may be most interested in
monitoring response levels and challenges to the current commitment levels.
For instance, if only three users are seen to
have any challenge on their commitment amounts, then the administrator may
need to handle those first, which may be a
priority if there is a discrepancy. The user may also be interested in those
who are planning to take action (e.g., increase
their commitment, reduce their commitment, by how much their commitment may
change, and the like). Ultimately, the
agency bank may have the final say, and so the system may provide them with
priority, and so enable them to decide on
whether to allow the changes or not
100721 Figs. 4B-4H depict embodiments of the amendment voting facility
user interface. Fig. 4B
illustrates an embodiment dashboard listing and graphic showing the status of
a user's amendment voting, where the graphic
shown displays a pie graph of ' no consent', 'consent', and `no response', as
well as a listing of specific amendment voting
statuses. Fig. 4C shows a user notification of being assigned an amendment
vote task. Fig. 4D shows a user interface for
distribution of an amendment vote. Fig. 4E shows options available to the user
for making the amendment vote, including to
'agree' or to 'disagree' with the '30,000,000 USD' commitment Fig. 4F shows a
listing of an amendment voting task status
for a user. Fig. 4G shows a signature page being submitted by a user,
including a note stating, "Please find my signature
page attached, for review". Fig. 4H shows an updated listing and status for
the user's amendment voting tasks.
100731 In embodiments, a method for managing a networked secure
collaborative computer data exchange
environment, the method including establishing, by a secure exchange server
controlled by an intermediate business entity, a
client login data authentication procedure that allows at least one client
computing device of a plurality of client computing
devices operated by users of a plurality of business entities to access the
secure exchange server, wherein communications
between the secure exchange server and the plurality of client computing
devices is through a communications network;
storing, by the secure exchange server, at least one client login
authentication data for each of the plurality of client
computing devices; receiving content from a first of the plurality of client
computing devices; by the secure exchange server,
permitting access to the content for a subset of the plurality of computing
devices through an exchange content access
facility, wherein the exchange content access facility is managed by at least
one business entity of the plurality of business
entities; granting, by the exchange server, access to the content to a second
of the plurality of client computing devices when
13
CA 02880904 2015-02-03
WO 2014/025809
PCT/US2013/053835
the secure exchange server receives from the second of the plurality of client
computing devices its client login
authentication data provided that the second of the plurality of client
computing devices is one of the subset of the plurality
of computing devices; and providing an amendment voting facility for
conducting a process of voting when the content
relates to a proposed amendment to an agreement wherein the amendment voting
facility enables users of the subset of the
plurality of computing devices to vote on the proposed amendment.
100741 In embodiments, access to the exchange server by client
processors may be through a host server
controlled by the business entity that controls the client processor. The
client computing devices may be at least one of
owned and managed by at least one of the plurality of business entities. The
client computing devices may be owned by
individual users. the secure exchange server may be at least one of a
plurality of exchange servers. The content may be at
least one of a document, a spreadsheet, a message, data, an image, audio
content, video content, multimedia content, and the
like. The content may be transferred to the secure exchange server via
encrypted data transmission.
100751 In embodiments, the process of voting on the proposed amendment
may be traceable, such as
traceability including tracing vote documentation, consent forms, signature
pages, digital distribution, vote collection,
signature page submission, and the like. The amendment voting facility may
provide for the aggregating of vote metrics for
tracking the process of voting amongst the users of the subset of the
plurality of computing devices, such as aggregating vote
metrics utilizing weighted voting calculations for consent percentage and
visualization of responses. The amendment voting
facility may provide for a vote graphical user interface dashboard to track
progress and statistics, such as where the tracking
of progress and statistics includes group tracking, reminders, export for vote
tally and reporting, and the like. The
amendment voting facility may provide for relative weighting of votes amongst
the voting users. The amendment voting
facility may provide for management of the voting process including a date for
the vote, a vote distribution list, inclusion of
associated documents, facility for signature-providing page submissions,
inclusion of instructions to voters, a process of
approval, a step for outside counsel to review, and the like. A vote may be
cast as a yes-no vote, a yes-no vote with
signature, a consent, and the like. A voting form may be provided, where the
voting form is configured to allow users to
dynamically generate voting forms, such as where the dynamically generated
voting forms are based on user participant
relationships. The voting form may include a user customizable text or logo.
100761 Referring to Fig. 5, the secure electronic signature facility 208
(also referred to herein as
signature facility' or 'e-signing' herein) may support the process of
providing documents for signature and for a user e-
signing and sending the e-signed documents back to the sender. In embodiments,
the electronic signature facility 208 may
provide for secure viewing of the document signing, such as through face
recognition 504 to determine the number of people
viewing the monitor on which the signing is being executed andlor utilizing a
digital photo of a user to verify the user is who
they say they are, utilizing biometric authentication 508, utilizing screen
obfuscation 510 to ensure only authorized users are
viewing the document for signing, and the like. For instance, a computing
device being used for e-signature may have a
camera that views and detects the surrounding environment to determine how
many people are cuirently viewing the screen,
and if a condition exists where there is not only one person viewing the
screen, the screen may obfuscate the document being
e-signed, such as blurring, blanking, screening, and the like. For example, if
the computer device detects that no one is
viewing or multiple people are viewing the semen, the screen may blank out the
document In another instance, the
computing device may utilize a cam= to match the face of the person viewing
the screen with a stored image of the person
that is authorized toe-sign, and if the match is made, permitting the process
of e-signing to proceed. In another instance, a
biometric match may be required to permit the process of e-signing to proceed,
such as through the use of a match to an iris
as viewed through a camera, an e-fingerprint through a fingerprint pad for
input to the computing device, or any other
biometric verification method known to the art. In embodiments, conditions for
enabling an e-signature process to proceed
may be stored in a user profile 512, where if the conditions (e.g. number of
people viewing, authorization matching though
images and/or biometrics) are not met, the document may be obfuscated.
100771 Fig. 5A shows a user interface embodiment for turning on an e-
signature process for an exchange.
Note that a user may only be able to view the document, or portion of the
document, for which the e-signature applies. For
14
CA 02880904 2015-02-03
WO 201-1/025809
PCT/US2013/053835
instance, through the viewer facility, non-applicable portions of the document
may be blocked out in some way as described
herein. Fig. 5B shows a toolbar for e-signature, where the user may click on
an e-signature icon to initiate (or terminate) an
e-signature process. Fig. 5C shows an embodiment of how a user may move around
an e-signature by dragging thee-
signature with the mouse. The user may be able to perform a number of
docinnent functions, such as find, zoom, rotate,
page up-down, and the like. In embodiments, if any portion of the e-signature
is moved by the user to a position that places
it off the page, the signature unction may be disabled (e.g. e-signature
disappears) to avoid placement of the e-signature in a
position that won't show the entire e-signature on the document once the
process is complete. Once the user has placed the
e-signature, they may apply the signature and complete the process. Fig. 5D
shows an example confirmation dialog box for
completion of the e-signature process, including a confirmation note to the
user about the final placement of the e-signature,
where the user may be allowed to return to placement of the e-signature if
they are not satisfied. The user, once satisfied,
may save the e-signature application and placement, such as illustrated in
Fig. 5E. As shown in Fig. 5F, if there are unsaved
changes at a time when the user attempt to close the application a prompt may
appear notifying the user that there are
unsaved changes and asking them if they want to save or close without saving.
Fig. 5G shows an embodiment dialog box for
cancelling an e-signature, showing control buttons for confirming whether to
cancel or to continue.
100781 In embodiments, a method for managing a networked secure
collaborative computer data exchange
environment may be provided, the method including establishing, by a secure
exchange server controlled by an intermediate
business entity, a client login data authentication procedure that allows at
least one client computing device of a plurality of
client computing devices operated by users of a plurality of business entities
to access the secure exchange server, wherein
communications between the secure exchange server and the plurality of client
computing devices is through a
communications network; storing, by the secure exchange server, at least one
client login authentication data for each of the
plurality of client computing devices; receiving content from a first of the
plurality of client computing devices; by the
secure exchange server, permitting access to the content for a subset of the
plurality of computing devices through an
exchange content access facility, wherein the exchange content access facility
is managed by at least one business entity of
the plurality of business entities; granting, by the exchange server, access
to the content to a second of the plurality of client
computing devices when the secure exchange server receives from the second of
the plurality of client computing devices its
client login authentication data provided that the second of the plurality of
client computing devices is one of the subset of
the plurality of computing devices; and providing an electronic signature
facility for managing a process of signing the
received content by at least one of the subset of the plurality of computing
devices, wherein the electronic signature facility
includes a signature viewer interface that restricts viewing of the content
for signing.
100791 In embodiments, access to the exchange server by client
processors may be through a host server
controlled by the business entity that controls the client processor. The
client computing devices may be at least one of
owned and managed by at least one of the plurality of business entities. The
client computing devices may be owned by
individual users. The secure exchange server may be at least one of a
plurality of exchange servers. The content may be at
least one of a document, a spreadsheet, a message, data, an image, audio
content, video content, multimedia content, and the
like. The content may be transferred to the secure exchange server via
encrypted data transmission.
ROM in embodiments, the electronic signature facility may include an
electronic signature graphical user
interface for presenting the content for signing. The restricted viewing may
be a signing user being restricted to only those
portions of the content that the signing user is authorized to view. The
restricted viewing may be a signing user being
restricted to only those portions of the content for which the signing
applies.
100811 In embodiments, a method for managing a networked secure
collaborative computer data exchange
environment may be provided, establishing, by a secure exchange server
controlled by an intermediate business entity, an
authentication procedure for a client login authentication data that allows at
least one of a plurality of user client computing
devices operated by users of at least two business entities to access the at
least one secure exchange server, wherein
communications between the secure exchange server and the plurality of user
client computing devices is through a
communications network; storing, by the secure exchange server, the at least
one client login authentication data for each of
CA 02880904 2015-02-03
WO 2014/(1258(19
PCT/US2013/053835
the plurality of client computing devices; receiving, from a first of the
plurality of user client computing devices, content;
associating access, by the secure exchange server, to the content to a subset
of the plurality of user computing devices
through an exchange content access facility, the exchange content access
facility managed by at least one of the plurality of
business entities; granting, by the exchange server, access to the content of
the secure exchange server to a second of the
plurality of user client computing devices when the secure exchange server
receives a client login authentication data from
the second of the plurality of user client computing devices and dependent
upon the second of the plurality of user client
computing devices being one of the subset of the plurality of user client
computing devices; and providing an electronic
signature facility for managing a process of signing the received content by
at least one of the subset of the plurality of
computing devices, wherein the electronic signature facility verifies the
identity of the signing user through biometric
profiling utilizing previously stored biometric data from the signing user.
100821 In embodiments, a method for managing a networked secure
collaborative computer data exchange
environment may be provided, establishing, by a secure exchange server
controlled by an intermediate business entity, an
authentication procedure for a client login authentication data that allows at
least one of a plurality of user client computing
devices operated by users of at least two business entities to access the at
least one secure exchange server, wherein
communications between the secure exchange server and the plurality of user
client computing devices is through a
communications network; storing, by the secure exchange server, the at least
one client login authentication data for each of
the plurality of client computing devices; receiving, from a first of the
plurality of user client computing devices, content;
associating access, by the secure exchange server, to the content to a subset
of the plurality of user computing devices
through an exchange content access facility, the exchange content access
facility managed by at least one of the plurality of
business entities; granting, by the exchange server, access to the content of
the secure exchange server to a second of the
plurality of user client computing devices when the secure exchange server
receives a client login authentication data from
the second of the plurality of user client computing devices and dependent
upon the second of the plurality of user client
computing devices being one of the subset of the plurality of user client
computing devices; and providing an electronic
signature facility for managing a process of signing the received content by
at least one of the subset of the plurality of
computing devices, the electronic signature facility assembling an
electronically signed document including signatures from
a plurality of users, each of which has had access to only a subset of the
content for which they were the signatory.
100831 In embodiments, a method for managing a networked secure
collaborative computer data exchange
environment may be provided, establishing, by a secure exchange server
controlled by an intermediate business entity, an
authentication procedure for a client login authentication data that allows at
least one of a plurality of user client computing
devices operated by users of at least two business entities to access the at
least one secure exchange server, wherein
communications between the secure exchange server and the plurality of user
client computing devices is through a
communications network; storing, by the secure exchange server, the at least
one client login authentication data for each of
the plurality of client computing devices; receiving, from a first of the
plurality of user client computing devices, content;
associating access, by the secure exchange server, to the content to a subset
of the plurality of user computing devices
through an exchange content access facility, the exchange content access
facility managed by at least one of the plurality of
business entities; granting, by the exchange server, access to the content of
the secure exchange server to a second of the
plurality of user client computing devices when the secure exchange server
receives a client login authentication data from
the second of the plurality of user client computing devices and dependent
upon the second of the plurality of user client
computing devices being one of the subset of the plurality of user client
computing devices; and providing an electronic
signature facility for managing a process of signing the received content by
at least one of the subset of the plurality of
computing devices, wherein the electronic signature facility provides for
secure viewing of the content as presented to a
signing user through a computer display of the signing user's client computing
device, wherein the user's client computing
device includes an integrated camera for viewing the environment around the
signing user and a face detection facility fin-
recognizing the signing user, detecting if the signing user is the only
individual present in the viewed environment, and if
not, obfuscates the viewing of the content. The obfuscation may be blanking
the screen, distorting the viewing of the
16
CA 02880904 2015-02-03
WO 201-1/025809
PCT/US2013/053835
content, and the like. The detection of the signing user by the face detection
facility may be accomplished by comparing an
image of a previously stored facial image of the signing user to the face
detected in the viewed environment.
100841 Referring to Fig. 6, the dashboard facility 210 may provide
organized facilities for managing
exchanges amongst the plurality of exchange service users 110, disseminate to
users of multiple groups of users, separating
exchange environments, and the like. For example, for a corporate M&A or
private equity group, the dashboard may
provide users with the ability to take their information, create a profile and
expose the information to other parties (e.g., to
private equity investors showing perlbrmance of their individual funds). The
dashboard may present information in an
organized manner, allow for loading of information through an information
importer 602, provide permissions 604 to view
information, allow for the exporting of information through an information
exporter 608, and the like. The dashboard
facility may provide for user access and display of both structured and
unstructured data, access to views that provide a
custom format or familiar terms to a particular category of transaction client
(e.g., fund, investment documents, capital
account statement, investment team), and the like, which also may restrict a
user's view to content applicable to them or to
the targeted category of transaction. In a private equity example, the user
may configure the dashboard to their specific
needs, such as including useful widgets 610 to display, infbrmation relating
to the market (e.g. available funds). A lands
widget may provide for selection of a fund, providing overview and performance
information, and the like. There may also
be sub-widgets that provide further functionality to a widget. The user may
also have multiple dashboards, such as for
different exchanges, different markets, different deals, and the like. One
dashboard may handle information that is available
to other users, and another dashboard may handle all personal files that are
both available and unavailable to other users.
The dashboard facility may also provide a compliance feature, such as to track
changes made in each dashboard.
100851 In an example of setting up a file exchange, an administrator 612
user may place files within an
input file directory, where the files may have a nomenclature that tells what
widget they will populate. The system may
create a configuration, run a process to populate it, ensure it is correct
before allowing access, and the like. In this way, data
may be considered 'stage data' prior to allowing access, and 'production data'
once approved. Once the user is comfortable
with a view, they can proceed and publish the staged data into 'production'.
The system may be able to upload data as CSV
file, create permissions files, and the like. In embodiments, a specific user
might be provided a view within a dashboard but
be given only access to one or more records within the dashboard. For example,
the user might only see a particular fund,
rather than all funds. If they select that fund, they may be able to see child
data associated with that fund. But without
permission, the other funds (or child data) would not be displayed. A
permissions model may give users access to specific
records within the dashboard. In an IvI&A example, a user may be able to see
all the live deals an organization is managing,
a certain human resources team might be allowed to see the dashboard, and the
like, where specific entities are provided
permissions.
100861 The dashboard may have both optional and standard functionality,
such as standard filtering
options, converting documents to a PDF: format, and the like. 'There may be a
widget catalog provided, such as for textual
displays, graphs and charts, document tracking, and the like.
100871 The dashboard may enable management of files at a document level,
at a record level, and the like,
such as to allow a user to add records and manage information. A user may be
able to add new content, put in the required
information, refresh the screen (e.g., on a per-deal basis), and the like. The
user may be able to edit and delete existing
records, show a parent-child relationship, and the like. The user might want
to choose the parent and find the document
within the exchange and link it up to the parent document. The system may have
the ability to manage individual records,
such as for dashboard data, but also to permissions. The user may be able to
take a parent record and provide permission to
one of the many users to enable access to those parents. In embodiments, the
system may provide for an auditing facility,
such as for tracking who is adding records and permissions.
100881 Referring to Fig. 6A, an example layout for listing available
funds and fund information is shown,
providing a plurality of columns for content. Figs. 6B-6D illustrate editing
the example fund, such as editing specific
column content. Fig. 6E shows an alert for a condition under which the user
cannot save edits, such because the user no
17
CA 02880904 2015-02-03
WO 201-1/025809
PCT/US2013/053835
longer has the latest version of the data (e.g. with new data was uploaded or
another user edited the content since the time the
dashboard was opened). In this instance, a control button may be provided to
update the dashboard data. Fig. 6F shows an
example dialog box for creating a new fund in the example layout. Figs. 6G-6H
shows dialog boxes for attaching a
document. Figs. 61-6K show a user interface for providing permissions in
association with the example fund, including
providing an H) of the user wanting to change permissions.
100891 Referring to Fig. 7, the Email-in facility 212 may provide for
the ability to add content to an
exchange using regular email, such as sent to a designated email address. This
facility may be especially important with
respect to users that circulate critical information and documents via email,
and where there is a tendency to lose track of it
at some point. Users may use the system's email-in facility to store email in
a secure repository 702, and to be able to tell
people to send email to this repository as part of a regular business process.
The exchange manager 712 may then review
and process the information further. This may simplify the learning curve of
using any web application. Lithe manager is
very knowledgeable, he may not need all of the counter-parties to spend time
learning the application. They simply send the
content into an exchange. Other features may include an email address being
associated with a folder in an exchange, a
maximum number of allowed emails in an exchange (e.g. a user may define a
cap), an email conversion facility 704, a white-
list and black-list 708 of users, notifications 710 of success and/or error,
and the like. In embodiments, email-in may be
limited to authorized users only, such as already in the exchange, listed on a
white list, and the like.
100901 Use cases for email-in may include submission of analysis
documents for review, a method for
having a third party review applications (e.g. in order to create accounts
while ensuring the third party does not gain control
over attachments that contain private information), and the like. In addition,
the system may provide for folder permissions
in the email Iblder that can be used to prevent misuse. For compliance, the
user may be able to store communications in an
archive 714 and track what was done in association with the communications.
100911 In embodiments, any exchange may be set up with email-in as a
feature. An administrator or client
may go through the process, such as defining where the sender's email address
is stored in the system, using custom fields
for the 'from' field, storing the message as an email, cap the maximum emails
it can accept, choosing the folder it will be
associated with, and the like. A folder location may thus be mapped to an
email address (e.g., with the domain pre-defined
but the pm-fix available for end user definition). The user may select users
to be included for the feature, set alert settings
and notification settings (e.g. problem alerts, that something was added), and
the like. A white list may be included, such as
for who should be able to send emails into the exchange (e.g. could be domains
or even addresses). If a user is not on the
white list, they may not be able to send emails to the exchange. A black list
may be included, where a user may choose
users to refuse acceptance onto the exchange.
100921 The email-in facility may create a folder structure within a pre-
defined mapped folder, and create a
sub-folder for each email that is sent into the exchange, such as with the
subject as the title of that folder. Contents of the
folders may then include any attached documents. The email-in content may be
organized like any exchange, where new
emails are added as they come in. The system may be configured to send to a
group, or to only one. For instance, a user
may send the folder to one person to review but not give the recipient the
right to do resend, print, or save the document.
Permission may be applied to the documents like any other document as
described herein, such as who can review the
correspondence, who can modify it, save it, print it, and the like. In
embodiments, an event trigger facility 718 may be
provided where received email may trigger an event, such as a task, a process,
and the like. For instance, if a contract comes
in it may trigger a renewal process. In another instance, an amendment process
may be triggered with the reception of an
email.
100931 In embodiments, the email-in facility may include the collection
of mails from various parties into
a structured database for later management and processing by a critical
information exchange manager, eliminate the
learning curve of using a web application to upload document to the cloud,
allow specific internal-external parties to post
documents into a web folder that may be shared with predefined individuals at
various control levels, and the like.
Components may include an email address associated with a folder in an
exchange, a maximum number of allowed emails in
18
CA 02880904 2015-02-03
WO 201-1/025809
PCT/US2013/053835
an exchange, a definition of email conversion options, a white list, a black
list, notifications on success and/or error, and the
like. In an example, client or prospect requests may be processed, such as for
an investment fimi with a need to submit
documents for analysis, a bank looking for a way to have a third pail review
applications to create new accounts while
ensuring that the third party does not gain control over the attachments that
contain private information, a bank having
compliance needs such as needing to archive all communications they have (e.g.
cc'ing and replying to the system on all
correspondences), and the like. Fig. 7A shows an introduction to email-in to
the user, and a control button to begin the
process. In embodiments, there may be a number of steps/options in the
execution of email-in, such as choosing basic
options, mapping folders, selecting alert recipients, creation of a white
list, creation of a black list, enabling-disabling of the
system, and the like. Fig. 7B shows an example dialog box for selection of
basic options, including a custom field selection
for the 'limn' of an email, how incoming email body content be stored,
definitions for the maximum number of emails that
should be accepted into the exchange, and the like. Figs. 7C-7F shows a dialog
boxes for selection of a fblder in association
with mapping folders, with Fig. 7E showing an alert for when a duplicate email
address is used. Fig. 7G illustrates the
selection of users and their alert settings. Fig. 7H shows an embodiment
warning for a duplicate domain or email address
associated with the creation of a blacklist. Fig. 71 shows a possible
checklist in association with the enabling of the system,
such as shown in the figure for selection of a custom field, mapping to two
folders, folders for mapping email into, no
maximum specified for number of emails, two domains listed on a white list,
and one domain listed on a black list. Fig. 7J
shows a user interface presented to the user once email-in is enabled, showing
tabs for listing options, mapped folders, alert
recipients, white lists, black lists, and the like, and showing specifically
the email-in options. Figs. 7K-7M show examples
of the content and dialog boxes provided in association with the mapped
folders tab.
100941 In embodiments, a method for managing a networked secure
collaborative computer data exchange
environment may be provided, the method including establishing, by a secure
exchange server controlled by an intermediate
business entity, a client login data authentication procedure that allows at
least one client computing device of a plurality of
client computing devices operated by users of a plurality of business entities
to access the secure exchange server, wherein
communications between the secure exchange server and the plurality of client
computing devices is through a
communications network; storing, by the secure exchange server, at least one
client login authentication data for each of the
plurality of client computing devices; receiving content from a first of the
plurality of client computing devices; by the
secure exchange server, permitting access to the content for a subset of the
plurality of computing devices through an
exchange content access facility, wherein the exchange content access facility
is managed by at least one business entity of
the plurality of business entities; granting, by the exchange server, access
to the content to a second of the plurality of client
computing devices when the secure exchange server receives from the second of
the plurality of client computing devices its
client login authentication data provided that the second of the plurality of
client computing devices is one of the subset of
the plurality of computing devices; and providing a secure email input
facility for accepting non-secure email from outside
the exchange into the secure collaborative computer data exchange environment,
wherein the non-secure email is received
and stored as secure email in the secure exchange server.
100951 In embodiments, access to the exchange server by client
processors may be through a host server
controlled by the business entity that controls the client processor. The
client computing devices may be at least one of
owned and managed by at least one of the plurality of business entities. The
client computing devices may be owned by
individual users. The secure exchange server may be at least one of a
plurality of exchange servers. The content may be at
least one of a document, a spreadsheet, a message, data, an image, audio
content, video content, multimedia content, and the
like. The content may be transferred to the secure exchange server via
encrypted data transmission.
100961 in embodiments, the acceptance of the non-secure email may be
dependent upon a controlled listing
stored in the secure exchange server, where the listing is a white listing
specifying emails that are allowed, a black listing
specifying email that are not allowed, and the like. The reception of a non-
secure email may trigger an event, where the
triggered event is the initiation of a content amendment process, the
initiation of a new exchange, the distribution of the
email within the exchange, storage of the email in a secure archive facility,
and the like. The email may be automatically
19
CA 02880904 2015-02-03
WO 201-1/025809
PCT/US2013/053835
associated with an area of content on the exchange based on the sender of the
email, the subject line of the email, the
destination address of the email within the exchange and the content of the
email, and the like.
100971 Referring to Fig. 8, the viewer facility 214 may provide for a
secure viewing 802 protection of
documents from unauthorized viewing, printing, saving, and the like, such as
without having to install custom client software
(e.g. without installing anything beyond Adobe Flash). Documents in certain
formats, such as Microsoft Office products,
PDF documents, and the like, may be supported for protection. For example, for
a PDF document a security warning may
appear that a user is only allowed to view the document However, if the user
tries to print the screen, the screen may
distort, such as transitioning to a fuzzy state. In embodiments, the user may
need to hold the enter key down to make the
document viewable. The user may be able to page up and down, rotate, zoom, and
the like. The system may provide for
watermarking the document so that if a user is permitted to print screen, the
document will print with the watermarking. The
viewer facility may also include functions such as viewing annotations 804 in
the viewer, connectivity with the e-signing
facility 208 (e.g. with a 'stamping' tool), document visibility based on face
detection, document protection from
eavesdroppers (e.g. automatic limitation of document viewing, also referred
herein as spotlighting, based on detection of a
second face), granular / page level document access reports 808, document
protection 810 using facial recognition based
encryption, text to voice feature 812 (e.g. such as in Apple* Sid), hand
gesture based controls 814 (e.g. scrolling control
based on hand-list movement), real-time white-boarding 818, secure video chat
820 (e.g. one-on-one, group), and the like.
In embodiments, the viewer facility may include an audio comment component,
such as to allow a user to input comments
into the document through audio dictation, to have the viewer facility play
back the comments in audio, to provide audio
output for various aspects of the document, and the like.
100981 In embodiments, the viewer may be able to detect faces and
enhance security based on face
detection, such as through utilization of a camera connected to or integrated
with the computing device being used to view
content. The viewer may also utilize a 'secure view', such as where only a
portion of a document is made viewable by the
person viewing the document. Secure view may implement security measures (e.g.
blanking the screen, distorting the
screen, putting up a screen) based on eye motion, movement of the face, the
presence of a second face, and the like.
Viewing time may be monitored and reported, audited, and the like, based on
how long the user's face has looked at the
document, where the monitoring, reporting, auditing, and the like may be
provided automatically. Document encryption and
decryption may be provided based on document permissions. For instance, if the
document can only be opened by a specific
number of people, face detection may use the author, or any other permissioned
user's face to encrypt the document and
require the same face to be detected to allow 'un-locking' of the document
Encryption of the face may then be 'recorded'
and used as an electronic signature, thereby tying the face to the user's
profile. Recording of viewing time may be on a
document level, on a per page basis, and the like. Viewing statistics may be
mined for business intelligence by sellers in a
strategic transaction, such as through a CIO with an enterprise, a marketing
analyst, or any such user who may benefit from
knowing with content is being read and what content is not being read.
100991 In embodiments, the viewer may provide a search facility to
search within a document. The system
may allow for highlighting a search result, highlighting a selected portion of
the document, and the like. The system may
provide facilities for annotating, marking, commenting, and the like, to a
document, such as a private annotation for the user,
a shared annotation fbr other users, and the like. The system may provide for
a secure document view, where only some
portions of the document are viewable. For instance, a user may only want to
show another user a selected portion of a
document The secure document view may also allow a user to increase the size
of the document view window, which may
better ensure that people proximate to you only see the relevant portions of
the document. Another feature of the secure
document view may include distorting those portions of the document that are
not selected for viewing, such as making
those sections fuzzy. The secure document view may react to the eye movement
of the user, such as scrolling the document
as the user's eye gaze direction shills, distorting or blocking the document
from view if the user looks away from the viewer,
and the like.
CA 02880904 2015-02-03
WO 2014/(1258(19
PCT/US2013/053835
1001001 The viewing facility may have capabilities for dealing with
certain document formats in a standard
way. For instance, the system may automatically convert Microsoft Word and
PowerPoint documents to a PDF format, open
spreadsheets (e.g. Microsoft Excel) in a spreadsheet viewer, and the like. For
instance, when an Excel document is opened,
it may be rendered on the fly, decrypted on the fly as a user scrolls down,
retrieved from the server and encrypted on the fly,
and the like.
1001011 Figs. 8A-8G depict embodiments of the viewing facility, such as
for use in a spreadsheet, word
processor, and the like, where Figs. 813-8D depict embodiments of the viewing
facility as applied to a spreadsheet, and Figs.
8E-8G depict embodiments of the viewing facility as applied to word
processors. Fig. RA illustrates functions of the viewing
facility with respect to a sample spreadsheet document, where (I) shows a
toolbar, (2) shows a page/sheet count, (3) shows a
document search box, (4) shows the spotlight interface, and (6) shows a
scrollbar. Fig. 8B shows a search ftinction and
sample results, where (1) shows the search window, (2) shows a search results
window, (3) shows how the results may be
grouped by page/worksheet name, (4) shows a search term highlighted, and (5)
shows a message displayed, such as if some
search results are displayed before the entire document search is complete.
Fig. 8C illustrates an embodiment of the
spotlight function, where only a portion of the document is viewable. Fig. 8D
shows a dialog box responding to a user
clicking on the print icon. Note that printing may be restricted as described
herein, where the dialog box may send an alert
to the user identifying the restrictions. Fig. RE illustrates functions of the
viewing facility with respect to a sample word
processing document, where (I) shows a toolbar, (2) shows a page/sheet count,
(3) shows a document search box, (4) shows
the spotlight interface, and (6) shows a scrollbar. Fig. BE shows a sample
search results set. Fig. 8G illustrates a number of
viewer facility functions related to a print command, including ( I) a print
icon, (2) a document window grayed out, (3) a
print window, (4) printer options, (5) range of pages for print, (6) a cancel
control button where if the user cancels the print
the gray-out function may be turned off and again revel the document, (7) a
'next' control button to close the pre-print
window and open an operating system print dialog.
1001021 in embodiments, a method for managing a networked secure
collaborative computer data exchange
environment may be provided, the method including establishing, by a secure
exchange server controlled by an intermediate
business entity, a client login data authentication procedure that allows at
least one client computing device of a plurality of
client computing devices operated by users of a plurality of business entities
to access the secure exchange server, wherein
communications between the secure exchange server and the plurality of client
computing devices is through a
communications network; storing, by the secure exchange server, at least one
client login authentication data for each of the
plurality of client computing devices; receiving content from a first of the
plurality of client computing devices; by the
secure exchange server, permitting access to the content for a subset of the
plurality of computing devices through an
exchange content access facility, wherein the exchange content access facility
is managed by at least one business entity of
the plurality of business entities; granting, by the exchange server, access
to the content to a second of the plurality of client
computing devices when the secure exchange server receives from the second of
the plurality of client computing devices its
client login authentication data provided that the second of the plurality of
client computing devices is one of the subset of
the plurality of computing devices; and providing a secure content viewer
facility for the user to securely view the content on
the user's client computing device, wherein the secure view is provided
through a viewing restriction based on a user action.
1001031 In embodiments, access to the exchange server by client
processors may be through a host server
controlled by the business entity that controls the client processor. The
client computing devices may be at least one of
owned and managed by at least one of the plurality of business entities. The
client computing devices may be owned by
individual users. The secure exchange server may be at least one of a
plurality of exchange servers. The content may be at
least one of a document, a spreadsheet, a message, data, an image, audio
content, video content, multimedia content, and the
like. The content may be transferred to the secure exchange server via
encrypted data transmission.
1001041 In embodiments, the viewing restriction may be obfuscating the
content view when the user action
is an attempt to print screen, a security warning when the user action is an
attempt to view the document, a water mark being
inserted on the content when the action is a user printing the content, and
the like. The client computing device may be a
21
CA 02880904 2015-02-03
WO 2014/025809
PCT/US2013/053835
mobile client computing device, such as personally owned by the user, and
configured for secure content viewing through
the business entity.
100105f in embodiments, a method for managing a networked secure
collaborative computer data exchange
environment may be provided, establishing, by a secure exchange server
controlled by an intermediate business entity, an
authentication procedure for a client login authentication data that allows at
least one of a plurality of user client computing
devices operated by users of at least two business entities to access the at
least one secure exchange server, wherein
communications between the secure exchange server and the plurality of user
client computing devices is through a
communications network; storing, by the secure exchange server, the at least
one client login authentication data for each of
the plurality of client computing devices; receiving, from a first of the
plurality of user client computing devices, content;
associating access, by the secure exchange server, to the content to a subset
of the plurality of user computing devices
through an exchange content access facility, the exchange content access
facility managed by at least one of the plurality of
business entities; granting, by the exchange server, access to the content of
the secure exchange server to a second of the
plurality of user client computing devices when the secure exchange server
receives a client login authentication data from
the second of the plurality of user client computing devices and dependent
upon the second of the plurality of user client
computing devices being one of the subset of the plurality of user client
computing devices; and providing a secure content
viewer facility for the user to securely view the content on the user's client
computing device, wherein a secure view is
provided through a viewing restriction based on a user action, the user action
detected through an integrated camera
operating in conjunction with face recognition facility on the client
computing device and the viewing restriction being an
obfuscation of the content view when the user is observed such that viewing of
the content by others is at risk. The user may
be observed with other people in view of the camera, with an eye-gaze that is
away from the client computing device, and
the like.
1001061 In embodiments, a method for managing a networked secure
collaborative computer data exchange
environment may be provided, establishing, by a secure exchange server
controlled by an intermediate business entity, an
authentication procedure for a client login authentication data that allows at
least one of a plurality of user client computing
devices operated by users of at least two business entities to access the at
least one secure exchange server, wherein
communications between the secure exchange server and the plurality of user
client computing devices is through a
communications network; storing, by the secure exchange server, the at least
one client login authentication data for each of
the plurality of client computing devices; receiving, from a first of the
plurality of user client computing devices, content;
associating access, by the secure exchange server, to the content to a subset
of the plurality of user computing devices
through an exchange content access facility, the exchange content access
facility managed by at least one of the plurality of
business entities; granting, by the exchange server, access to the content of
the secure exchange server to a second of the
plurality of user client computing devices when the secure exchange server
receives a client login authentication data from
the second of the plurality of user client computing devices and dependent
upon the second of the plurality of user client
computing devices being one of the subset of the plurality of user client
computing devices; and providing a content viewer
monitoring facility for monitoring the user viewing the content on their
client computing device, wherein the monitoring is
provided through an integrated camera operating in conjunction with a face
recognition facility on the client computing
device.
1001071 In embodiments, a method for managing a networked secure
collaborative computer data exchange
environment may be provided, establishing, by a secure exchange server
controlled by an intermediate business entity, an
authentication procedure for a client login authentication data that allows at
least one of a plurality of user client computing
devices operated by users of at least two business entities to access the at
least one secure exchange server, wherein
communications between the secure exchange server and the plurality of user
client computing devices is through a
communications network; storing, by the secure exchange server, the at least
one client login authentication data for each of
the plurality of client computing devices; receiving, from a first of the
plurality of user client computing devices, content;
associating access, by the secure exchange server, to the content to a subset
of the plurality of user computing devices
22
CA 02880904 2015-02-03
WO 201-1/025809
PCT/US2013/053835
through an exchange content access facility, the exchange content access
facility managed by at least one of the plurality of
business entities; granting, by the exchange server, access to the content of
the secure exchange server to a second of the
plurality of user client computing devices when the secure exchange server
receives a client login authentication data from
the second of the plurality of user client computing devices and dependent
upon the second of the plurality of user client
computing devices being one of the subset of the plurality of user client
computing devices; and providing a content viewer
monitoring facility for monitoring the user viewing the content on their
client computing device, wherein a content viewing
access report is generated that provides statistics related to the time the
user spends viewing portions of the content. The
portion of the content may be at a granular level of a page of the content, at
a granular level of the entire document, and the
like. The content viewing access report may provide for tracking and audit
reporting for the user viewing the content. The
statistics may be used to develop business intelligence.
1001081 In embodiments, a method for managing a networked secure
collaborative computer data exchange
environment may be provided, establishing, by a secure exchange server
controlled by an intermediate business entity, an
authentication procedure for a client login authentication data that allows at
least one of a plurality of user client computing
devices operated by users of at least two business entities to access the at
least one secure exchange server, wherein
communications between the secure exchange server and the plurality of user
client computing devices is through a
communications network; storing, by the secure exchange server, the at least
one client login authentication data for each of
the plurality of client computing devices; receiving, from a first of the
plurality of user client computing devices, content;
associating access, by the secure exchange server, to the content to a subset
of the plurality of user computing devices
through an exchange content access facility, the exchange content access
facility managed by at least one of the plurality of
business entities; granting, by the exchange server, access to the content of
the secure exchange server to a second of the
plurality of user client computing devices when the secure exchange server
receives a client login authentication data from
the second of the plurality of user client computing devices and dependent
upon the second of the plurality of user client
computing devices being one of the subset of the plurality of user client
computing devices; and providing a content viewer
control facility for user-controlled viewing of the content on their client
computing device, wherein the control is at least in
part enabled through an integrated camera operating in conjunction with a
motion recognition facility on the client
computing device. The control may be actualized through monitoring user hand
gestures, monitoring user eye movements,
through monitoring user head movements, and the like. The control may be
enabling the viewing of the content, tuning a
page in viewing the content, inserting a signature into the content, closing a
viewing session for the content, and the like.
1001091 Referring to Fig. 9, the mobile device interface facility 218 may
provide for facilities such that a
mobile device 902 can be used while maintaining the secure exchange
environment provided by the host server 102 as
described herein, such as for a tablet (e.g. an iPad), a smart phone, and the
like, where for instance the mobile device is
provided iiinctionality provided through the e-signing facility 208, the
viewer facility 214, and the like. Facilities normally
provided through the host server 102 as shown in Fig. 2 may be provided in
part or whole on the mobile device, such that the
mobile device may be utilized when the mobile device does not have
connectivity with the host server 102. For instance, the
user may be able to login to the same interface as when they are working
through a non-mobile computer, such as on their
personal computer, and see their list of exchanges, all of their documents,
all of their contacts, and the like. Using an iPad as
an example, all of the user's documents may be encrypted when sent to the iPad
and decrypted for viewing, such that none
of the information is decrypted and stored on the iPad. A user may not be able
to print or save from the mobile device, and
be provided with a secure document viewer, as described herein, such as
partial viewing, eye gaze motion control,
watemiarking, and the like.
1001101 Figs. 9A-9K depict embodiments of the mobile device viewing
interface. Fig. 9A shows public vs.
private exchange views, where 3 exchanges are visible as restricted by public-
private declarations, 31 exchanges are viewed
when all exchanges are able to be viewed, and 15 exchanges are viewable with
viewing only mobile exchanges. Fig.9B
shows functions for accessing exchanges, folders, tiles, and the like. Note
that a message may be displayed if a user attempts
to access an exchange or entity without the required declaration. Fig. 9C
shows examples of public vs. private document
23
CA 02880904 2015-02-03
WO 2014/(1258(19
PCT/US2013/053835
views. Fig. 9D shows examples of adding a document classification, where a
document control button may be provided for
uploading, an appropriation may be specified, and the like. Fig. 9E shows
examples of public and private users and groups.
Figs. 9F-9G show examples of document access reports. Fig. 9H shows public vs.
private views of documents. Figs. 9I-9K
show examples of file uploads to exchanges.
100111j In embodiments, the present invention may provide for technology
aspects related to wohitecture,
structural components, facilities, data, communications, arialytics,
reporting, materials, inbound components, processes,
algorithms, and the like. Architecture, structural components, and facility
may include multi-language support, metadata
association, document content processing, document content distribution,
distributed geo-storage, and the like.
Relationships among components may include CItM integration, sales force
connector, HCM integration, ERP integration,
ECM integration, e-Learning integration, and the like. Data, communications,
analytics, and reporting may include user
history reporting, activity reporting, permission reporting access reporting,
audit and compliance reporting, configurable
dashboards, self-service reporting (e.g. custom, scheduled, ad-hoc), IMAP
folder management, exadata integration, and the
like.
1001121 In embodiments, the present invention may provide for product
aspects related to features,
attributes, benefits, outputs, finictional benefits, security, and the like.
Products may include integration from a secure data
room, public-private bifurcation in the loan market, secure mobile devices,
and the like. Features, attributes, and benefits
may include iPad protected documents, bounce-back reporting, branding,
channels, alerts, task management, multi-task
process management, automatic indexing, migration, automation (e.g. ILIA
automation), specialization (e.g. custom fields,
custom workflow), very large file support, document management (e.g. review
and approve, check-in and out, version
control), customizable user interface, unified inbox, and the like. Product
features may include custom alerts, buyer utilities,
bulk addition of files and folders, dynamically indexing information, advanced
and federated search and filtering, custom
fields and tags, integration with third-party document formats (e.g. Microsoft
Office products), add and management of users
and groups, multi-file uploads, commenting, compliant archiving, native-format
file viewing, business intelligence based on
activity reporting, question and answer components, link mapping, secure
viewing without plug-ins, unified communication
and collaboration (e.g. presence notification, IM-chat-discussion threads,
forums and wikis), administration capability, e-
forms, and the like. Security may include on-demand rights management, access
and authentication (e.g. document and
content level access, multi-factor authentication, single sign-on), data
encryption, tracking and audit, intra-structure security
(e.g. systems protection, security audits), personnel security, process
security, encryption, watermarking, and the like.
1001131 In embodiments, the present invention may provide for market
aspects related uses, applications,
environments of deployment, use scenarios, ecosystems, value chains, system
integration, and the like. Applications may
include corporate repository, extended team collaboration, managed file
transfer, secure extranet, project lifecycle
management, board reporting, legal extranct, legal repository, legal
collaboration, managed file transfer, regulatory audit and
reporting, secure extranet, financial audit management, fundraising, investor
communication, contract management,
regulatory filings, board of directors' communication, Compliance fi,sed
integration, access gatekeeper, project capital
finance, project collaboration, supply chain management, contract
manufacturing, and the like. Markets may include
finance, loan syndication, M&A (e.g. relationship management and marketing
activities, client interactions, sending legal
documents and contacts for comment, edit, and signature), alternative
investments, commercial banking, investment
banking, bankruptcy and restructuring, corporate development, construction,
life sciences, pharmaceutical, biotechnology,
energy and utilities, utility rate case management, insurance,
telecommunications, project life cycle management,
information technology, legal services, government, manufacturing, real
estate, media and entertainment, and the like.
Environments of deployment may include corporate development, corporate
repository, corporate finance, corporate legal,
engineering, human resources, marketing, general services, research and
development, compliance and security, line of
business, and the like. Use scenarios may include, bankruptcy & restructuring,
board reporting, business development and
licensing, clinical site activation, extended team collaboration,
fiindraising, initial public offerings (IP0s), investor portals,
investor reporting, legal extranet, managed file transfer, mergers and
acquisitions, private placements, project lifecycle
24
CA 02880904 2015-02-03
WO 201-1/025809
PCT/US2013/053835
management, regulatory audit and reporting, regulatory case management, safety
document distribution, secure extranet,
structured finances, syndicated lending, virtual data room, and the like.
1001141 Current methods for sharing computer files are not adequately
secure in that a user may make errors
in sending information, such as with a single, errant click, and send
sensitive information into the wrong hands with no way
to recover the sent materials. Alternately, sensitive information may be
provided to a trusted associate that subsequently
leaves a company or department, to a vendor where the user's company
subsequently switches vendors, to someone outside
the company that is subsequently identified as a risk to the spread of
sensitive information, and the like, where the sender
would like to revoke access to the shared content The present invention may
provide for methods and systems for securely
sharing content (e.g., computer data content, such as documents,
presentations, spreadsheets, emails, blog entries, texts, and
the like) that allows for 'un-sharing' of content that has been previously
shared. The facility to un-share content may be
implemented through the content being associated with a secure protection
feature, such as through digital rights
management (DRM), encryption, permissions, and the like. In embodiments, each
content item may shared with the
protection feature, where the protection feature specifies a user or group of
users that are authorized to access the content for
viewing. Then when the content is shared with that user, access to the content
may be revoked at any time (e.g. by changing
the DRM, removing access to the key, changing permissions, and the like).
Further, if the sender of the content controls the
protection feature, then the sender has complete lifetime control of any
content they distribute or provide access to.
1001151 The secure un-sharing facility may be used to securely share
content beyond the secure protective
facilities of their enterprise (e.g., allowing secure sharing beyond the
firewall of the sender's enterprise), out to users in other
companies, into the public space, to users not intended to get the content,
and the like, where the sender maintains complete
control to access of the content, no matter where or to who the content has
been distributed. In this way, the secure sharing
of content is made to be easy amiss corporate boundaries at the user level and
at the individual content level (e.g., at the
level of an individual document). Further, the process allows a user wishing
to unshared a content to be discrete in its
execution, allowing the sender to revoke access without having to contact or
to track down the recipients, who may not have
any indication sent to them that access has been revoked. With the unsharing
facility, the content simple stops being
accessible. And the revoking of access may be for not only the original
content, but for all instances of the content, such as
copies stored on various devices and computer environments (e.g., stored on
desktop, tablet, mobile smart phone, in an
application, through a web browser, and the like), copies sent to third
parties, and the like. And since the protection feature
may apply to all versions that have been modified (e.g., edited versions,
redline versions, commented versions, signed
versions, and the like), access to modified versions of the content may also
be revoked when the access to the original
content is revoked.
100116] In embodiments, access to a shared content may require an access
authentication to a secure facility,
such as the secure exchange server. That is, even if content has been shared
with a user, the user may only be able to view
the content if their access is authenticated. Authentication may be a manual
login to verify that the user attempting access to
the document is a user that is listed to have access to the content.
Alternately, a user that has access may establish a
computer device that is tied to their personal authentication, such as through
the secure facility. For instance, an authorized
user may associate their personal authorization to their portable computing
device (e.g., tablet, smart phone), such as where
the portable computing device has a password to access the device, thus
ensuring that the person requesting the access anti
the mobile device is the authorized user.
1001171 In embodiments, the security process that protects the content,
such as a document to be uploaded
and shared, may incorporate a plurality of protective steps. For example, when
a document is uploaded a virus scan may be
run, permissions may be established, a search index may be created, digital
protection may be applied, the document may be
converted (e.g. formatted), the document may be encrypted, and the like, where
encryption may be applied individually to
each new content, such as through a randomly generated encryption key. When a
download of the document is requested,
such as when an authorized user is downloading as part of the document being
shared, a random key with a key ID may be
generated for that particular document when the document is encrypted with the
random key. A. master key may be split
CA 02880904 2015-02-03
WO 201-1/025809
PCT/US2013/053835
between a database and a file system, where the encrypted random key and
random key ID are stored in the database, and the
random key may be encrypted with the master key, and the like. Permissions,
virus scan, watermark, digital protection, and
the like may then be applied before delivery of the document.
1001181 In embodiments, the un-sharing facility may enable the control of
access down to the individual
content level, such as with the creation of a new document, which may be part
of or be the start of a collaborative social
work stream, allowing users to share content, and then initiate and perpetuate
conversations and interactions around those
contents. Social work streams may support discussion threads, activity
streams, and other common social interaction
facilities, which may utilize the content as the organizing basis. The process
of un-sharing a content may result from
removal of the content from the work stream, retiring the work stream,
removing the individual content entirely, and the like.
1001191 The present disclosure describes a secure content sharing and
productivity solution for
organizations to share confidential and non-confidential content between and
amongst enterprises over a global
communication network such as the Internet, including outside enterprise
firewalls. The present disclosure may provide a
secure content sharing and collaboration environment that goes beyond the
enterprise firewall; establishing a seamless dual-
use user woikflow environment that accommodates both secure and personal
exchange of content without the need for the
user to adopt substantially new workflow process and applications; providing
secure interlaces for viewing documents using
mobile computing devices, such as touch-interface tablets (e.g. including the
incorporation of personal user devices); and the
like.
1001201 The need for beyond-the-firewall content sharing space has been
created by the confluence of
technology evolution (e.g. cloud computing and virtualization, portable form
factor innovation, 'big data' 81 tools),
organizational shills (e.g. rapidly growing cross-enterprise collaboration,
global fragmentation of enterprise, cross-functional
teams, demographics shifts), changes in the role of integration technology
(e.g. cost and complexity reduction, pressure lbr
measureable business value, 'computerization' of enterprise IT and 'bring your
own device'), government and regulatory
issues (e.g. increasing regulations, cyber security threats), and the like
that collectively increase the importance of easy and
secure collaboration of documents and content beyond the enterprise firewall.
Other solutions have taken a variety of
approaches to address fragments of these requirements, but important unmet
needs remain for information technology
directors, business leaders, and users remain, including in the areas of
integration of security/control, ease of use, seamless
operation across different ways of sharing, and the like.
1001211 In embodiments, the system may include methods and systems for
providing a single fabric to
enhance the most common forms of beyond-the-firewall content sharing,
improving individual and team productivity across
the extended enterprise while providing unified security and compliance for IT
and business leaders; allow users to continue
beyond-the-firewall sharing however they prefer with a single user interface
enhancing the security and productivity of e-
mail, sync-and-share folders, externalized enterprise content management, and
enterprise social collaboration tools; integrate
with consumer-focused sync-and-share services where possible to enable their
secure and compliant use within the
enterprise; enhance forms of collaboration to which users are already
accustomed, and not require adoption of a new way of
working or collaboration destination; target the unique collaboration and
sharing requirements of the extended enterprise and
complement other enterprise systems; and the like.
1001221 In embodiments, a need for a comprehensive sharing system may
include an ease of use and
intuitive user interface; with granular security pennissions, to help ensure
that unauthorized individuals can't open
documents; ability to control content post-sharing (e.g. the ability to pull
back a document), enabling a user to recover and
destroy data remotely, such as in using a virtual data room; productivity
tools integrated with content sharing, consolidating
a plurality of user log-ins and passwords; the ability to integrate with
existing infrastructure, to eliminate the need for a
plurality of sharing tools; providing multiple channels for collaboration in
order to integrate the methods and systems into as
many productivity platforms as possible; and the like.
1001231 Referring to Fig. 10, the present disclosure describes an
exchange content access facility 1008 in
association with the secure exchange server 1002 that improves the security
with which a plurality of users 1004 collaborate
26
CA 02880904 2015-02-03
WO 2014/(1258(19
PCT/US2013/053835
freely, including through a plurality of different content sharing devices and
facilities, while providing lifetime control of
their content For example, suppose a user sent quarterly sales data to an old
accounting firrn, employee records to someone
outside of HR, the wrong contract to the wrong vendor. When a user `un-
shares', content access may be instantly revoked,
including any content that may have been from copies of the original content.
In embodiments, the user may have total
lifetime control of each and every content item, such as documents, emails,
communications, and the like. In embodiments,
the content may be stored and tracked in a secure database 1012. Users may
share and revoke access to content all the way
down to the document level, providing a secure place to upload files and sham
them across devices. In this way, users may
be provided a secure storage facility for company sensitive information, where
users are able to work more securely, such as
with their existing infrastructure (e.g. seamless integration with
applications like Microsoft Outlook, SharePoint, and the
like). The un-share facility may allow a user to create a new work stream,
securely upload the documents, and work with
teams that are enabled to securely collaborate. In addition, the un-sharing
facility may provide for reports, audits,
summaries, and the like through a dashboard facility, such as a summary view
of all work streams, customized security
settings, ability to add new participants, provide automated reporting, and
the like. The exchange content access facility
1008 may utilize a user login data authentication facility 1010 to
authenticate users' access to content, where there may be
the option of having a single sign-on in association with other user logins.
In embodiments, the login may utilize security
hashing in a redirect IJRI., such as to secure the login against Phishing
attacks. The single sign-in may extend to mobile
devices, including personal mobile devices, were a lookup table may be used to
verify that the user has single sign-on
capabilities or not.
100124] In embodiments, a method for managing a networked secure
collaborative computer data exchange
environment may be provided. The secure exchange server 1002, such as managed
by an intermediate business entity, may
establish a user login data authentication procedure that allows a user to
access the seem exchange server, where the secure
exchange server may store user login authentication data for each of the
plurality of users, such as in a secure database.
Users may access the secure exchange server through a plurality of different
computer devices, applications,
communications channels, and the like. The user may be one of a plurality of
users 1004 that work for a plurality of other
business entities (e.g., users may be employees of the same business entity or
users may be working for different business
entities), where the users of the other business entities communicate with the
secure exchange server through a
communications network, such as a wide area network (e.g., the Internet). To
share a computer content item, a first of the
plurality of users may request a sharing access from the secure exchange
server to a content item to at least a second of the
plurality of users. Management for access to the content may be through an
exchange content access facility 1008 managed
by the intermediate business entity. After the exchange server receives the
content from the first of the plurality of users, it
may grant sharing access to the content when the secure exchange server
receives from the second of the plurality of users its
client login authentication data (provided that the second of the plurality of
users is one of the subset of the plurality of users
to which sharing access is permitted). The second of the plurality of users
may then request a copy of the content from the
secure exchange server, wherein a copy of the content is made. Further, the
second of the plurality of users may further copy
the content onto a plurality of different computing devices, make changes,
revisions, annotations, and the like to a new
version of the content, send the content to other users, send the content to
people and computing devices beyond the
boundaries of the business entities, and the like. To un-share the content,
the first of the plurality of users may then make a
request to the secure exchange server to revoke sharing access to the content
to the second of the plurality of users. As a
result, the secure exchange server revokes access by the second user to the
content, such as through encryption and DRM
facilities described herein. Further, this revocation of the second user's
access to the content may similarly be applied to all
instances of the content within the plurality of users, wherein the revoking
of sharing access to the content revokes access to
all instances of the shared content and all copies of the content made by the
plurality of users. In a similar fashion, any
individual that does not have authority to access the content may not have the
ability to access any instance of the content.
In embodiments, copies of the content may be deleted from the secure data
server, wherein the deleting access to the copy of
the content is revocation of digital rights management of the content. The
digital rights management of the content may be
27
CA 02880904 2015-02-03
WO 201-1/025809
PCT/US2013/053835
controlled in part by the first of the plurality of users, including revoking
access to the content through changes in the digital
rights management associated with the content. The content may be a secure
encrypted content. Users may securely view
the content through a secure viewing facility. Users may be connected to a
public network that is outside of the firewall for
the business entity that manages them. Users may access the content through a
personal computing device that is not owned
by the business entity that manages them, such as through a personal computer,
personal mobile device, and the like. Users
through a dashboard facility may interface the exchange content access
facility, where the dashboard facility may provide
reports showing activity related the sharing of content. The dashboard
facility may be accessible through third-party
environments. The dashboard facility may track the location and version of the
shared content on computing devices
accessible by the at least second of the plurality of users.
1001251 Fig. 10A provides a non-limiting example of how the present
invention may provide an improved
workflow between collaborating individuals. In this workflow scenario, an
enterprise knowledge worker 'Fred' (e.g. internal
counsel) is collaborating with a chief information officer 'George' who works
at the same company as Fred, and an external
partner 'Pam' (e.g. external counsel). As shown, in a first step 1021, Fred
may sync files from his personal computer, such
as with resources in the cloud. These resources may include syncing with
virtual secure data room facilities, third-party
computer sync facilities that are compatible with the present invention, and
the like, and may be made available through the
dashboard facility. In a second step 1022, Fred may also access his files and
have the ability to sync to devices that George
has approved, such as through a virtual secure data room, an enterprise or
shared enterprise policy facility, and the like. In a
step three 1023, Fred may view status of a project he and Pain are working on,
such as through the dashboard facility. As
part of a process template, he may be reminded to send a file to Pam for
review. In a step four 1024, Pam may receive the
file on her iPad, where she opens it to review, such as through the mobile
device viewing facility. In a step five 1025, Fred
may now want to share some confidential files with Pam, such as though a
virtual secure data room facility, with the ability
to 'pull-back' the document from Pam at anytime through the un-sharing
facility. In addition, Fred may task Pam to
annotate, review, markup, revise, and the like, the file he's sharing, such as
through a content creation application (e.g., word
processor, spreadsheet application, presentation application, media tool), the
amendment voting facility, the e-signing
facility, via the secure viewer facility, and the like. In a step six 1026,
based on content inspection and destination, Fred may
see his actions are risky and decides to remediate, such as by un-sharing the
document from Pam's access, as implemented
through the dashboard facility, and the like. He may then, for instance,
choose to share the files as mad-only. In a step
seven 1027, Pam receives system notification on her Macintosh computer, such
as through the dashboard facility. In a step
eight 1028, Pam annotates the read-only file in the Mac application, and
competes the task, such as through an application
that Pam is familiar with and integrated for ease of use in the familiar
workflow environment cm:fled by the present
invention. In a step nine 1029, Fred sees that Pam has finished her task, such
as though the dashboard facility, opens the
annotated file and syncs (e.g. via SharePoint). In a step ten 1030, Fred
manages teamwork items against a schedule, and
with all tasks competed, closes the project. For instance, the project may
have been a loan syndication project, and once
complete, Fred may completely eliminate accessibility to documents and
communications that were transmitted during the
transaction, such as removing access to any documents that were transmitted
during execution of the project In a step
eleven 1031, Pam may also revoke files when the project is completed, and
files are wiped from her devices, such as the
system pulling back the files as tracked by the system in a secure database
created for the project (which in itself may be
deleted once the project is complete). In a step twelve 1032, George may see
risky sharing activity in his security event
management system, and in a step thirteen 1033, see compliance reports and
audit information in a governance, risk
management, and compliance (GRC) system, such as through monitoring via the
dashboard facility. In embodiments, a
workflow thread may be initiated within an exchange amongst other business
entities, with selected individuals in a micro-
transaction, from an email thread, and the like. In embodiments, a user may be
enabled to create a concept of a big project
and use micro-transaction capabilities to break the big project down into
smaller projects that can link back up to the big
project A user may be able to create tasks out of their email inbox, turn an
email thread into a task, clear a task by
converting the email into a work-stream, make an exchange an extension of an
email, and the like.
28
CA 02880904 2015-02-03
WO 2014/(1258(19
PCT/US2013/053835
1001261 In embodiments, the system may provide for the ability to
remotely delete content from a device
while the device is off-line or not connected to a network. This capability
may be implemented by providing a lease to a
desktop application when it starts up and has a successful logon, such as
configured by a policy through an administer
console. When a device is powered up and a lease period is expired without a
successful logon during the lease period, the
system may initiate a deletion of files, such as would be the case if the
device had been lost or stolen. This application may
be a separate desktop service running on the device in the background (e.g.,
sleep and awake in pre-defined time intervals).
When a device is powered up, the application may record the values of a lease
expiration date/time of a previous successful
login. In another instance, the service may try to connect to a server, and if
it detects connection failures continuously past
the lease expiration date and time, it may assume that either the device no
longer needs to run the application, or it could be
lost or stolen. In the case of the device that is subsequently found or re-
used, the content may be re-synced for the user once
they login to the application successfully. There may be hard or soft leases
implemented in the system. In the instance of a
hard lease, files may be deleted permanently on the local machine when the
lease is expired. In a soft lease, rather than
deleting data, the system may move the data to a random location on the disk
where a user cannot find it. For example, the
system may modify the folder attribute for the data, such as to "+S +H".
Setting those attributes will mark it as an important
operating system file so that the operating system won't display the data even
if settings allow the display of hidden files and
folders. In embodiments, the system may provide for automatically deleting
documents, whether the de-vice is online or not,
based on a date/time range. For instance, setting a range of dates for the
life of documents to be between on date/time and
another, at which time all related documents and folders are deleted. The
system may also delete documents, folders,
desktop, and the like, after a predetermined number of login failure attempts,
where the system may provide access again
upon restoration of access privileges.
1001271 In embodiments, the system may provide for remotely deleting
documents through a limited local
access facility, where the user may have access to a document, folder, and the
like, only through an encrypted local
application. In this way, files stay encrypted on a user machine and the only
way to access them is to use the application that
will decrypt the documents. The local application may also be embedded, as
described herein, such as through a browser,
where a user may only be able to access documents with credentials that tie to
the encryption key. The local application may
be a viewer application, where documents are distributed through a
distribution engine, but where the user can only view the
documents using the viewer that would decrypt the document for viewing.
1001281 in embodiments, the system may integrate the sharing capability
with other third-party
environments, such as including existing file sharing solutions (e.g. Drop
Box, Cioogle Drive, Skydrive, Box.com,
MediaFire, SugarSync, TitanFile, YouSendft, SparldeShare, 'Munro One)
providing cloud storage, file synchronization,
client software, and the like. In addition to sharing resources, the present
invention may also provide a 'share' option within
other thud-party day-to-day workflow solutions, such as desktop tools (e.g.
Microsoft Office, Mork, Cioogle Does,
OpenOffice, and the like) and enterprise tools (enterprise DBs, CIIM. tools,
analytical tools), and the like, where without
departing the interface of the third-party tool or application, the present
invention may allow content to be shared outside the
enterprise with another party, but with the secure data room and secure
viewing features as described herein (e.g. the ability
to track access and viewing, ability to have 'road only' viewing and
annotation, secure viewing on a mobile device, ability to
pull back a document), and the like. Further, the present invention may be
able to interface with templated secure sharing
processes, such as by having input events and output actions consist with
those (e.g., Outlook receives an email from a
secure process and signals an action; LinkedIn lets a user view and approve a
corporate voting item).
1001291 In embodiments, the system may enable an organization to maximize
the value of content by
balancing the freedom to share with the necessary control and monitoring
provided by the system, which extends the way an
organization works, such as by allowing them to share and access content
wherever it is needed, controlling and monitoring
content wherever it goes, coordinate work across people, organizations and
devices as a natural extension of familiar tools
and experiences. The system may provide for a full-service, global facility as
a 'partner' wherever the user may go,
providing visibility and control of work-centric content, freedom to
collaborate, and the like. The system may provide a
29
CA 02880904 2015-02-03
WO 201-1/025809
PCT/US2013/053835
trusted standard for information security 'beyond the firesvalF, providing
automation and monitoring of corporate
information policy, extending a familiar user experience and existing
infrastructure, and the like. Collectively, the methods
and systems of the present invention may provide for an intent-based sharing
'fabric' for enabling comprehensive
collaboration.
1001301 In embodiments, the system may provide fin- improved
connectivity, security, productivity, and the
like, as related to a shared collaborative work environment. Productivity may
include the ability to assign and manage
document-centric business actions (e.g. e-signature), project task management,
and the like, such as to provide more
structured document sharing platforms (e.g. more than just email, which may be
an ad-hoc communication). Security may
include role and file-based permissions, outside the firewall pullback of
document permissions, automatic document content
and security classification, and the like. Connectivity may include single
secure connection to document sharing tools across
devices, secure access to internal ECM platform for external parties,
integration of enterprise-class security into existing
sync-and-share tools, and the like, such as to enable access anywhere the
client needs it and the ability to make updates to
documents easily, mgamlless of where the user is located. The system may
provide advanced analytical features to improve
productivity, such as audit compliance, document versioning and tracking,
document contextualization, historical
performance analysis, predictive analytics, task productivity optimization,
and the like. The system may also include social
collaborative features to improve interactions within projects, such as
improved communications within the workflow,
secure project management, tablet-based collaboration, synchronous co-editing,
social collaboration, a social layer around
business applications, and the like.
1001311 In embodiments, the system may provide for synchronization and
sharing for the individual
business professional, including a plurality of channels (e.g. Windows desktop
client, web browser, Microsoft Outlook for
Windows, iOS support [such as a native app for the iPhone and iPad]), features
(e.g. desktop file and folder synchronization:
secure file sharing from desktop, browser, and i0S; push notifications,
collaborative discussion threads and commenting;
user self sign-up), for work with business intent (e.g. sending a copy fbr
download, sharing access to a centrally located file
for review), administration (e.g. canned activity audit reports, such as for
compliance; canned accounting reports, such as for
billing); centralized group policy, such as for security defaults), security
(e.g. with strong, per-file encryption and
permissions; browser-based, read-only file access; integrated file information
rights management (IRM) and digital rights
management (DRM); file access revocation; mobile device security; full
compliance audit), and the like. The term 'work
with business intent may include the ability of users to share files 'with
intent'. For instance, the intent may come in the
form of document tasks that may be assigned to recipients, where the system
may let users send files for review, send for
signature, send for annotation, comment, and the like. For instance, the
system may want to give users the ability to
combine document tasks (verbs) into ad-hoc workflows and save as a template,
which may also be referred to as a verb
cluster. In an example, if a manager has to get slides ready for a board of
directors (BOD) meeting, they may start up a
"BOD" workflow that included several document tasks and individuals
responsible. One employee may get a task to
comment on the slide deck, another gets a task to review and approve the
material, and the manager gets a task to sign the
document for auditors after the first two tasks are completed.
1001.321 in embodiments, the system may provide for document collaboration
and intent-based 'work',
including a plurality of channels (e.g. native Android, iPhone, and the like
support; plugins for Microsoft Office apps;
SharePoint Connector integration; Mac Client [such as file/folder sync]),
features (e.g. desktop file and folder
synchronization for Mac; file sharing with intent, such as for document-
centric work assignment and task management;
calendaring; in-document task completion: collaborative editing and
annotation; 'in-app' publishing and collaboration, such
as check in/out), for work with business intent (e.g. work items such as send
for review and approval, send for feedback and
annotation, request edits to a document, send for electronic signature,
request form completion), administration (e.g. bulk
user administration through active directory. Ili customization and branding,
report creation and scheduling), security (e.g.
device registration, data loss prevention filters, such as reminders to users
when they share tiles in a risky way; remote
device wipe), and the like.
CA 02880904 2015-02-03
WO 201-1/025809
PCT/US2013/053835
1001331 In embodiments, the system may provide for enterprise integration
and business process
management, including a plurality of channels (e.g. published integration API,
third-party app integration, Outlook for Mac),
features (e.g. work template creation, team collaboration spaces, milestone
and project management, in-browser document
editing), for work with business intent (e.g. work item customization, such as
combining document tasks to create
lightweight ad-hoc business processes), administration (e.g. user and
administrator-authored business process), security (e.g.
data loss prevention, such as blocking unsafe actions; security information
manager (SIM) and security event manager
(SEM) integration; customer managed encryption keys; governance, risk
management, and compliance (GRC) system
integration), and the like. For instance, disclosed features (e.g. an un-
sharing feature to pull back documents as described
herein) may be embedded into daily use tools, such as into communications
software (e.g. Microsoft Outlook, Gmail),
browsers (e.g. Windows Explorer, Firefox, Safari), Enterprise Resource
Planning (ERP) applications, legal systems,
collaboration systems, and the like, and to make it easily available and easy
to use. All these systems have a need to
distribute documents outside the enterprise firewall to users who are not
logging into these systems on a daily basis, and by
embedding these capabilities enables users for secure sharing, auditing,
compliance, and the like for documents within user
applications. In an example, suppose sales personnel are building a quote for
a customer in a third-party application, such as
Salesforce.com for instance. Typically, users would have the ability to email
the quote directly, or to download the document
and email it, where there is no audit or compliance within the third-party
application for these quotes. With the use of an
embedded capability, the document would be sent directly from the third-party
application with the system's secure sharing
audit and compliance capabilities, ability to pull back (un-sharing)
documents, and would be available from within the third-
party application. The embedded service may have the standard components to
make this service possible, such as SSO
authentication, file viewer, policy definition, auditing, device provisioning,
user profiles and compliance, and the like, where
these would be built like a service and may be integrated directly into the
standard enterprise applications. Security rules
may also be implemented in the embedded system, such as with a range of
security (e.g., ranging from public to highly
secure), screen capture and viewing protection, device control, auditing
enforced, and the like.
1001341 While the invention has been described in connection with certain
preferred embodiments, other
embodiments would be understood by one of ordinary skill in the art and are
encompassed herein.
1001351 The methods and systems described herein may be deployed in part
or in whole through a machine
that executes computer software, program codes, and/or instructions on a
processor. The present invention may be
implemented as a method on the machine, as a system or apparatus as part of or
in relation to the machine, or as a computer
program product embodied in a computer readable medium executing on one or
more of the machines. The processor may
be part of a server, client, network infrastructure, mobile computing
platform, stationary computing platform, or other
computing platform. A processor may be any kind of computational or processing
device capable of executing program
instructions, codes, binary instructions and the like. The processor may be or
include a signal processor, digital processor,
embedded processor, microprocessor or any variant such as a co-processor (math
co-processor, graphic co-processor,
communication co-processor and the like) and the like that may directly or
indirectly facilitate execution of program code or
program instructions stored thereon. In addition, the processor may enable
execution of multiple programs, threads, and
codes. The threads may be executed simultaneously to enhance the performance
of the processor and to facilitate
simultaneous operations of the application. By way of implementation, methods,
program codes, program instructions and
the like described herein may be implemented in one or more thread. The thread
may spawn other threads that may have
assigned priorities associated with them; the processor may execute these
threads based on priority or any other order based
on instructions provided in the program code. The processor may include memory
that stores methods, codes, instructions
and programs as described herein and elsewhere. The processor may access a
storage medium through an interface that may
store methods, codes, and instructions as described herein and elsewhere. The
storage medium associated with the processor
for storing methods, programs, codes, program instructions or other type of
instructions capable of being executed by the
computing or processing device may include but may not be limited to one or
more of a CD-ROM, DVD, memory, hard
disk, flash drive, RAM, ROM, cache and the like.
31
CA 02880904 2015-02-03
WO 201-1/025809
PCT/US2013/053835
1001361 A processor may include one or more cores that may enhance speed
and performance of a
multiprocessor. In embodiments, the process may be a dual core processor, quad
core processors, other chip-level
multiprocessor and the like that combine two or more independent cores (called
a die).
1001371 The methods and systems described herein may be deployed in part
or in whole through a machine
that executes computer software on a server, client, firewall, gateway, hub,
router, or other such computer and/or networking
hardware. The software program may be associated with a server that may
include a file server, print server, domain server,
internet server, intranet server and other variants such as secondary server,
host server, distributed server and the like. The
server may include one or more of memories, processors, computer readable
media, storage media, ports (physical and
virtual), communication devices, and interfaces capable of accessing other
servers, clients, machines, and devices through a
wired or a wireless medium, and the like. The methods, programs or codes as
described herein and elsewhere may be
executed by the server. In addition, other devices required for execution of
methods as described in this application may be
considered as a part of the infrastructure associated with the server.
1001381 The server may provide an interface to other devices including,
without limitation, clients, other
servers, printers, database servers, print servers, file servers,
communication servers, distributed servers and the like.
Additionally, this coupling and/or connection may facilitate remote execution
of program across the network. The
networking of some or all of these devices may facilitate parallel processing
of a program or method at one or more location
without deviating from the scope of the invention. in addition, any of the
devices attached to the server through an interface
may include at least one storage medium capable of storing methods, programs,
code and/or instructions. A central
repository may provide program instructions to be executed on different
devices. In this implementation, the remote
repository may act as a storage medium for program code, instructions, and
programs.
1001391 The software program may be associated with a client that may
include a file client, print client,
domain client, internet client, intranet client and other variants such as
secondary client, host client, distributed client and the
like. The client may include one or more of memories, processors, computer
readable media, storage media, ports (physical
and virtual), communication devices, and interfaces capable of accessing other
clients, servers, machines, and devices
through a wired or a wireless medium, and the like. The methods, programs or
codes its described herein and elsewhere may
be executed by the client. In addition, other devices required for execution
of methods as described in this application may
be considered as a part of the infrastructure associated with the client.
1001401 The client may provide an interface to other devices including,
without limitation, servers, other
clients, printers, database servers, print servers, file servers,
communication servers, distributed servers and the like.
Additionally, this coupling and/or connection may facilitate remote execution
of program across the network. The
networking of some or all of these devices may facilitate parallel processing
of a program or method at one or more location
without deviating from the scope of the invention. in addition, any of the
devices attached to the client through an interface
may include at least one storage medium capable of storing methods, programs,
applications, code and/or instructions. A
central repository may provide program instructions to be executed on
different devices. In this implementation, the remote
repository may act as a storage medium for program code, instructions, and
programs.
1001411 The methods and systems described herein may be deployed in part
or in whole through network
infrastructures. The network infrastructure may include elements such as
computing devices, servers, routers, hubs,
firewalls, clients, personal computers, communication devices, routing devices
and other active and passive devices, facilitys
and/or components as known in the art. The computing and/or non-computing
device(s) associated with the network
infrastructure may include, apart from other components, a storage medium such
as flash memory, buffer, stack, RAM,
ROM and the like. The processes, methods, program codes, instructions
described herein and elsewhere may be executed by
one or more of the network infrastructural elements.
1001421 The methods, program codes, and instructions described herein and
elsewhere may be implemented
on a cellular network having multiple cells. The cellular network may either
be frequency division multiple access (FDMA)
network or code division multiple access (COMA.) network. The cellular network
may include mobile devices, cell sites,
32
CA 02880904 2015-02-03
WO 201-1/025809
PCT/US2013/053835
base stations, repeaters, antennas, towers, and the like. The cell network may
be a GSM, GPRS, 3t1, E'VDO, mesh, or other
networks types.
1001431 The methods, programs codes, and instructions described herein
and elsewhere may be
implemented on or through mobile devices. The mobile devices may include
navigation devices, cell phones, mobile
phones, mobile personal digital assistants, laptops, palmtops, netbooks,
pagers, electronic books readers, music players and
the like. These devices may include, apart from other components, a storage
medium such as a flash memory, buffer, RAM,
ROM and one or more computing devices. The computing devices associated with
mobile devices may be enabled to
execute program codes, methods, and instructions stored thereon.
Alternatively, the mobile devices may be configured to
execute instructions in collaboration with other devices. The mobile devices
may communicate with base stations interfaced
with servers and configured to execute program codes. The mobile devices may
communicate on a peer to peer network,
mesh network, or other communications network. The program code may be stored
on the storage medium associated with
the server and executed by a computing device embedded within the server. The
base station may include a computing
device and a storage medium. The storage device may store program codes and
instructions executed by the computing
devices associated with the base station.
1001441 The computer software, program codes, and/or instructions may be
stored and/or accessed on
machine readable media that may include: computer components, devices, and
recording media that retain digital data used
for computing for some interval of time; semiconductor storage known as random
access memory (RAM); mass storage
typically for more permanent storage, such as optical discs, forms of magnetic
storage like hard disks, tapes, drums, cards
and other types; processor registers, cache memory, volatile memory, non-
volatile memory; optical storage such as CD,
DVD; removable media such as flash memory (e.g. USB sticks or keys), floppy
disks, magnetic tape, paper tape, punch
cards, standalone RAM disks, Zip drives, removable mass storage, off-line, and
the like; other computer memory such as
dynamic memory, static memory, read/write storage, mutable storage, read only,
random access, sequential access, location
addressable, file addressable, content addressable, network attached storage,
storage area network, bar codes, magnetic ink,
and the like.
1001451 The methods and systems described herein may transform physical
and/or or intangible items from
one state to another. The methods and systems described herein may also
transform data representing physical and/or
intangible items from one state to another.
1001461 The elements described and depicted herein, including in flow
charts and block diagrams
throughout the figures, imply logical boundaries between the elements.
However, according to software or hardware
engineering practices, the depicted elements and the functions thereof may be
implemented on machines through computer
executable media having a processor capable of executing program instructions
stored thereon as a monolithic software
structure, as standalone software facilities, or as facilities that employ
external routines, code, services, and so forth, or any
combination of these, and all such implementations may be within the scope of
the present disclosure. Examples of such
machines may include, but may not be limited to, personal digital assistants,
laptops, personal computers, mobile phones,
other handheld computing devices, medical equipment, wired or wireless
communication devices, transducers, chips,
calculators, satellites, tablet PCs, electronic books, gadgets, electronic
devices, devices having artificial intelligence,
computing devices, networking equipments, servers, routers and the like.
Furthermore, the elements depicted in the flow
chart and block diagrams or any other logical component may be implemented on
a machine capable of executing program
instructions. Thus, while the foregoing drawings and descriptions set forth
functional aspects of the disclosed systems, no
particular arrangement of software for implementing these functional aspects
should be inferred from these descriptions
unless explicitly stated or otherwise clear from the context. Similarly, it
will be appreciated that the various steps identified
and described above may be varied, and that the order of steps may be adapted
to particular applications of the techniques
disclosed herein. All such variations and modifications are intended to fall
within the scope of this disclosure. As such, the
depiction and/or description of an order for various steps should not be
understood to require a particular order of execution
for those steps, unless required by a particular application, or explicitly
stated or otherwise clear from the context.
33
CA 02880904 2015-02-03
WO 2014/025809
PCT/US2013/053835
1001471 The methods and/or processes described above, and steps thereof,
may be realized in hardware,
software or any combination of hardware and software suitable for a particular
application. The hardware may include a
general purpose computer and/or dedicated computing device or specific
computing device or particular aspect or
component of a specific computing device. The processes may be realized in one
or more microprocessors,
microcontrollers, embedded naicrocontrollers, programmable digital signal
processors or other programmable device, along
with internal and/or external memory. The processes may also, or instead, be
embodied in an application specific integrated
circuit, a programmable gate array, programmable array logic, or any other
device or combination of devices that may be
configured to process electronic signals. It will further be appreciated that
one or more of the processes may be realized as a
computer executable code capable of being executed on a machine-readable
medium.
1001481 The computer executable code may be created using a structured
programming language such as C.
an object oriented programming language such as C+4", or any other high-level
or low-level programming language
(including assembly languages, hardware description languages, and database
programming languages and technologies)
that may be stored, compiled or interpreted to run on one of the above
devices, as well as heterogeneous combinations of
processors, processor architectures, or combinations of different hardware and
software, or any other machine capable of
executing program instructions.
1001491 Thus, in one aspect, each method described above and combinations
thereof may be embodied in
computer executable code that, when executing on one or more computing
devices, performs the steps thereof. In another
aspect, the methods may be embodied in systems that perform the steps thereof;
and may be distributed across devices in a
number of ways, or all of the functionality may be integrated into a
dedicated, standalone device or other hardware. In
another aspect, the means for performing the steps associated with the
processes described above may include any of the
hardware and/or software described above. All such permutations and
combinations are intended to fall within the scope of
the present disclosure.
1001501 While the invention has been disclosed in connection with the
preferred embodiments shown and
described in detail, various modifications and improvements thereon will
become readily apparent to those skilled in the art.
Accordingly, the spirit and scope of the present invention is not to be
limited by the foregoing examples, but is to be
understood in the broadest sense allowable by law.
1001511 All documents referenced herein are hereby incorporated by
reference.
34