Note: Descriptions are shown in the official language in which they were submitted.
CA 02897145 2015-07-03
WO 2014/107594 PCMJS2014/010206
SYSTEM AND METHOD FOR PROVIDING A SECURITY CODE
BACKGROUND
[0001] The disclosure generally relates to the use of electronic stored-
value cards in electronic
transactions.
100021 The electronic transaction market is currently filled with many
types of credit cards,
debit cards, stored value cards, and loyalty cards, all of which may be
offered by different issuers,
vendors, and providers. Some of the cards are tailored to be redeemed from a
retailer while others
may be redeemed by financial institutions. Other cards have promotions
attached to them, e.g.,
loyalty cards. However, the increasing quantity and complexity of the cards
makes organization
and redemption increasingly difficult, thus potentially hindering the growth
of the market. For
example, a user may not know or remember that the user has a stored value card
for a specific store
during a purchase at that store because the user has too many stored value
cards. Also, a user may
not understand the various types of promotions available to him using a card
in combination with a
loyalty card, and as such, may not benefit from promotions applicable to the
user's purchase.
Historically, cards have been embodied in a tangible medium such as plastic,
and thus are
susceptible to loss, theft, or simply being left at home when needed. With the
continued growth in
card-based transactional offerings provided to consumers, many consumers are
faced with the
burdensome task of organizing, managing, tracking, transporting, and storing
all of their credit,
debit, stored-value, loyalty, and other types of merchant, vendor, and
provider issued cards. What
today's consumers need is a more efficient, secure, and effective way of
accessing and using their
card-related assets.
SUMMARY
[0003] A computer implemented method may comprise receiving a request for a
security code
of an electronic stored-value card, calculating the security code by a
security code provider,
providing a calculated security code of the electronic-stored value card in
response to the request
for a security code, and eliminating the calculated security code from
databases of the security
code provider.
[0004] A computer-implemented electronic stored-value card security code
providing system may
be configured to receive a request for a security code of the electronic
stored-value card, to
calculate the security code, to provide the calculated security code in
response to the request for a
security code, and to eliminate the calculated security code from the system.
1
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[0001] A computer implemented method may comprise providing an electronic
stored-value
card, wherein the electronic stored-value card requires a security code for
conducting transactions,
receiving a request for the security code of the electronic stored-value card,
calculating the security
code by a security code provider, providing a calculated security code of the
electronic-stored
value card in response to the request for a security code, and eliminating the
calculated security
code from databases of the security code provider.
[0005] A computer-implemented electronic stored-value card security code
providing system
comprising a component configured to receive a request for a security code of
the electronic
stored-value card, calculate the security code, provide the calculated
security code in response to
the request for a security code, and eliminate the calculated security code
from the component.
BRIEF DESCRIPTION OF THE DRAWINGS
[0006] Figure 1 is a flowchart depicting an embodiment of a method for
providing a security
code.
[0007] Figure 2 is a flowchart depicting another embodiment of a method for
providing a
security code.
[0008] Figure 3 is a schematic illustration of an embodiment of a system
for providing a
security code.
[0009] Figures 4A, 5A, 5B, and 5C are schematic representations of an
electronic value token
transaction processing system in accordance with at least one embodiment.
[0010] Figure 4B illustrates an exemplary embodiment of an electronic
wallet.
[0011] Figures 6A, 6B, and 6C are front perspective views of representative
individual proxy
cards in accordance with at least one embodiment.
[0012] Figure 61.) is a front perspective view of a representative user
device in accordance with
at least one embodiment.
[0013] Figure 7A is a flowchart depicting exemplary processes utilized by
an electronic value
token transaction computer for creating an electronic wallet or
adding/redeeming value tokens
to/from the electronic wallet in accordance with at least one embodiment.
[0014] Figure 7B is a flowchart depicting exemplary processes utilized by
an electronic value
token transaction computer for creating an electronic sub-wallet or
adding/redeeming value tokens
to/from the electronic sub-wallet in accordance with at least one embodiment.
2
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[0015] Figure 8 illustrates a particular machine suitable for implementing
the several
embodiments of the disclosure.
[0016] Figures 9A-D illustrates a series of user interface screens and prompts
in accordance with
at least one embodiment.
DETAILED DESCRIPTION
[0017] Disclosed herein are systems and methods for using stored-value
cards, such as
electronic stored-value cards (hereinafter "eSVC" or "eSVCs"). Particularly,
the systems and
methods disclosed herein may provide security codes necessary for payments
transactions
without violating any rules (e.g., laws, regulations, guidelines, or
combinations thereof)
prohibiting the storage of a security code for a card (e.g., an eSVC).
Embodiments for the
provision of a security code as disclosed herein may also be included in
methods and systems for
distributing open loop eSVCs. Additionally, the disclosed systems and methods
may provide
electronic stored-value card users a guided process for registering electronic
stored-value cards
into existing and new electronic wallets, and the use of value tokens in the
electronic wallet(s)
for electronic transactions.
[0018] Acquisition and/or purchase of a stored-value card (e.g., an
electronic stored-value
card) may involve an account vendor, a redeeming merchant, and an account
issuer. In various
embodiments, the account vendor, redeeming merchant and account issuer may be
the same,
different, or related entities. The point of sale where the electronic stored-
value card is
purchased and/or acquired is referred to herein as the account vendor or
simply vendor. An
entity that will accept value contained in the electronic stored-value card
for business
transactions, for example, as tender for a purchase, is referred to as a
redeeming merchant. An
entity that provides the financial backing and/or payment processing accessed
via use of the
electronic stored-value card is referred to as the account issuer, or simply,
issuer. Account issuers
may include direct issuers of electronic stored-value cards such as store-
branded cards (e.g.,
Macy's, Target), and in some embodiments the account vendor may also be the
account issuer
and/or the redeeming merchant. Account issuers also may include banks,
financial institutions,
and processors such as VISA, Mastercard, American Express, etc., and
electronic stored-value
cards issued by such institutions may be readily accepted by a number of
redeeming merchants
to conduct transactions such as purchases. Account issuers may be in various
industries, such as
the entertainment, health, medical, pharmaceutical industries. For example,
the account issuer
3
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
may be a pharmaceutical company utilizing promotional electronic stored-value
cards for
pharmaceutical products. In some instances, an electronic stored-value card
may be sold and/or
issued at the same or different account vendor (e.g., account vendor is Store
X or a different or
unrelated Store Z). In such instances, the Store X branded electronic stored-
value card may be
issued by Store X, by Store Z, or by a third party such as bank or financial
institution.
[0019] Under current rules (e.g., the VISA U.S.A. Cardholder Information
Security Program
Payment Application Best Practices and the Payment Card Industry Payment
Application Data
Security Standard) the needed security code may not be readily available to
certain parties in a
transaction. For example, when a user converts a physical card to an eSVC and
discards the
physical card, or when a user obtains an eSVC via other means described
herein, the security
code may be unavailable to the user, to the merchant, to an electronic wallet
provider, to the
eSVC processor, or combinations thereof when the user makes a transaction. As
such, parties to
a payment transaction, i.e., entities such as the processor of an eSVC, the
merchant, the user, or
any other entity which is prohibited from storing a security code may be
dependent upon the
availability of the security code from the issuer of the eSVC. The disclosed
systems and
methods allow for the calculation and provision of the security code of the
eSVC by entities
prohibited from storing and retaining the security code.
[0020] As used herein, "electronic-stored value card" or "eSVC" refers to
an electronic
embodiment of an account that may be used to transact business with a merchant
willing to
accept a value (e.g., points, miles, dollars, or any other measure of value
such as a value token
described hereinbelow), for example as tender for a purchase or discount for a
purchase. As used
herein, "electronic stored-value card" or "eSVC" may additionally or
alternatively refer to an
electronic embodiment of an account used for promotional and/or marketing
purposes. The
accounts may comprise credit accounts, debit accounts, gift accounts,
telephone accounts, loyalty
accounts, membership accounts, ticket accounts, entertainment accounts, sports
accounts,
prepaid accounts, discount accounts, healthcare accounts, the like, or
combinations thereof.
Such accounts may be associated with corresponding physical cards, including
credit cards, debit
cards, gift cards, telephone cards, loyalty cards, membership cards, ticket
cards, entertainment
cards, sports cards, prepaid cards, discount cards, healthcare cards, the
like, or combinations
thereof. Such accounts may additionally or alternatively comprise electronic
accounts, such as
electronic credit accounts, electronic debit accounts, electronic gift
accounts, electronic
4
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
telephone accounts, electronic loyalty accounts, electronic membership
accounts, electronic
ticket accounts, electronic entertainment accounts, electronic sports
accounts, electronic prepaid
accounts, electronic discount accounts, electronic healthcare accounts, the
like, or combinations
thereof In embodiments, the value of an electronic stored-value card may be
embodied as an
"electronic value token" or "value token," both of which are described in
detail hereinbelow.
[0021] As used herein, "card information" refers to information associated
with an electronic
stored-value card, associated with the account from which the electronic
stored-value card is
based, associated with the physical card with which the account is associated,
or combinations
thereof The card information is used for an electronic transaction with a
merchant using the
electronic stored-value card. In embodiments, card information may comprise a
cardholder
name, card name, an account number (e.g., primary account number), a service
code, a UPS, a
phone number, an identification number (e.g., driver's license number,
passport number, visa
number, social security number, IP address), an expiration date, a billing
address, or
combinations thereof.
[0022] As used herein, a "security code" refers to a security code of a
physical card or eSVC
which is subject to the rules against storage and retention of such codes. In
embodiments a
security code may comprise a series of three or four digits which have been
associated with a
physical card or eSVC by the issuer. In embodiments a security code may
comprise a series
digits, letters, symbols, or combinations thereof. In embodiments, a security
code is in addition
to a card account number which is embossed or printed on the card and is also
in addition to a
personal identification number or password associated with the card. In
embodiments, e.g.,
when the stored-value card (e.g., eSVC) is not present for physical inspection
by a receiving
merchant (e.g., an online or telephonic transaction), a security code serves
to verify that a
requested stored-value card (e.g., eSVC) transaction is a valid and/or
authorized transaction
request by a cardholder (e.g., a person rightfully possessing the card and/or
authorized to request
a transaction). In embodiments, a security code may comprise a card security
code (CSC), a card
verification value (CVV or CVV2), a card verification value code (CVVC), card
verification
code (CVC or CVC2), verification code (V-code or V code), card code
verification (CCV),
credit card ID (CID or CCID), or combinations thereof
[0023] Disclosed herein are embodiments of methods for providing a security
code of an
electronic stored-value card. The various steps of the methods may be omitted,
substituted, and
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
rearranged except where specified hereinbelow. The methods described
hereinbelow are
applicable for open-loop stored-value cards and for closed-loop stored-value
cards.
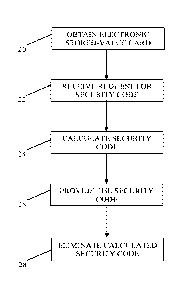
[0024] Figure 1 shows a flow chart of an embodiment of a method disclosed
herein. The
embodiment of the method shown in Figure 1 begins at block 20.
[0025] At block 20, an eSVC (e.g., eSVC 11 of Figure 3) may be obtained,
for example, by a
user or consumer. The user or consumer may comprise a person or an automated
device
configured to make purchases under various conditions. The eSVC may be
obtained by
converting a physical card (e.g., credit cards, debit cards, gift cards,
telephone cards, loyalty
cards, membership cards, ticket cards, entertainment cards, sports cards,
prepaid cards, discount
cards, healthcare cards, the like, or combinations thereof) to a digital
format (e.g., by submission
of card information to an electronic wallet provider). Additionally or
alternatively, the electronic
stored-value card may be obtained (e.g., sent, received, delivered, fetched,
acquired, presented,
or combinations thereof) via various communication means, including SMS,
email, video (e.g.,
YouTube, Vimeo, Skype, video message, or combinations thereof), instant
message, a website,
an online storage medium, a cloud storage system, other means for
electronically obtaining the
electronic stored-value card, or combinations thereof For example, in an
embodiment the eSVC
may be an eGift delivered as a uniform resource locator ("URL") to a user
through email or any
other channel (e.g., SMS, Facebook wall post, and Twitter), the URL refers to
an HTML page
that displays the eGift with appropriate logo, terms and conditions,
redemption instructions, card
number, security code (CVV2) and expiration date. In an embodiment the eSVC
may be an
eCode delivered directly to the user (e.g., via SMS, Instant Message, and
email) and includes a
primary account number, security information, and an expiration date. In an
embodiment, the
eSVC may be directly provisioned to a user's electronic wallet. In
embodiments, a user of the
eSVC may use the obtained eSVC, for example, by clicking on a link to redeem
the eSVC (e.g.,
in the form of a e-gift, discount, credit, promotional offer, or combinations
thereof, etc.) at a
merchant online transaction portal, by accessing the eSVC in an electronic
wallet provided by an
electronic wallet provider and stored by the electronic wallet provider, by
using an eSVC
identifier (e.g., number, promo code, discount code) via a transaction portal
(e.g., of a merchant),
or combinations thereof
[0026] In embodiments, before the user obtains (e.g., receives, activates,
redeems, or
combinations thereof) the eSVC, the eSVC provider, the e-wallet provider, the
eSVC processor,
6
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
the eSVC issuer, the merchant, or combinations thereof may provide fraud
mitigation. In an
embodiment, providing fraud mitigation may comprise blocking access to an eSVC
before a user
views the eSVC, blocking access to an eSVC before a user activates the eSVC,
or both. In an
additional or alternative embodiment, providing fraud mitigation may comprise
determining a
digital fingerprint of a user device (e.g., user device 14), at the time a
user attempts to view an
eSVC to determine the risk associated with the user, the eSVC, or both. In an
additional or
alternative embodiment, providing fraud mitigation may comprise withholding
the providing of
the eSVC (e.g., withholding the delivery of redemption information for the
eSVC). In an
additional or alternative embodiment, providing fraud mitigation may comprise
determining a
geographic location of the eSVC and/or user and pausing the providing of the
eSVC for a period
of time determined by the geographic location. For example, the providing of
the eSVC may be
held for a longer period of time in geographic locations known or determined
to be of high risk
of fraud, and the providing of the eSVC may be held for a short period of time
or for a period of
time comprising zero in geographic locations known or determined to be of low
or no risk of
fraud.
100271 In embodiments, before the user obtains (e.g., receives, activates,
redeems, or
combinations thereof) the eSVC, the eSVC provider, the e-wallet provider, the
eSVC processor,
the eSVC issuer, the merchant, or combinations thereof may not associate an
account and/or
value with the eSVC until the user takes an affirmative step to purchase the
eSVC. For example,
an account and/or value for the eSVC may not be associated with the eSVC until
a user clicks on
a URL, responds to an email, responds to an SMS, a voicemail, other
notification, or
combinations thereof to obtain the eSVC.
100281 Various registration, authentication, allocation, and provisioning
techniques may be
performed prior to use of the eSVC which would be recognized by one skilled in
the art with the
aid of this disclosure. For example, the user may register the eSVC in one or
more electronic
wallets (e.g., electronic wallet 10 of Figure 3). As used herein, an
"electronic wallet" (also
referred to as "e-wallet") may include an electronically maintained data file
(e.g., maintained on
a computer device of a provider of the electronic wallet) which may comprise
an electronic
stored-value card(s), authentication information, rules for use, sub-wallets
(e.g., for separately
maintaining electronic stored-value card-related information), and electronic
value tokens (e.g.,
electronic representations of the monetary and/or other value associated with
the electronic
7
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
stored-value card-related information contained in the e-wallet/sub-wallet).
In certain
embodiments (e.g., as reflected in Figures 9A-D) a user may create an e-
wallet, establish rules
for the e-wallet, provision the e-wallet, and access the e-wallet to
facilitate electronic
transactions. Suitable processes for registering the eSVC are disclosed in
International
Application Serial No. PCT/US13/26501, filed on February 15, 2013, and
entitled "System and
Method of Registering Stored-Value Cards Into Electronic Wallets." Examples of
techniques for
authenticating, allocating, and provisioning an eSVC are described
hereinbelow.
[0029] To
use the obtained eSVC, the user may be required to supply a security code of
the
eSVC. Because the eSVC is a virtual card, the user may not have the security
code (e.g., the
CVV2).
[0030] At
block 22 a request for a security code is received. The security code provider
and/or a computer device of a security code provider may receive the request
for a security code,
e.g., from a user of the eSVC, from a merchant, from an electronic wallet
provider, or
combinations thereof. For example, the user of the eSVC may send a request for
a security code
in order to use the eSVC for a purchase of a good or service from a merchant
(e.g., in an open
loop transaction network). To request the needed security code, the user may
utilize a user
device (e.g., user device 14 of Figure 3) to contact a computer device (e.g.,
computer device 12,
13, 18, or 19 of Figure 3) of the security code provider. In another example,
a merchant (e.g.,
which is not also the eSVC issuer and cannot store the security code) may send
a request for a
security code in order to accept the eSVC for the purchase of a good or
service by the user. To
request the needed security code, the merchant may utilize a computer device
(e.g., merchant
computer device 16 of Figure 3) to contact a computer device (e.g., computer
device 12, 13, 18,
or 19 of Figure 3) of the security code provider. In another example, a
provider of an eSVC
and/or a user's electronic wallet (e.g., which is not also the eSVC issuer and
cannot store the
security code) may send a request for a security code, e.g., as an
intermediary between the user
of the eSVC and the security code provider. To request the needed security
code, the electronic
wallet provider may utilize a computer device (e.g., provider computer device
12 of Figure 3) to
contact a computer device (e.g., computer device 13, 18, or 19 of Figure 3) of
the security code
provider. Before sending a request for the security code, the electronic
wallet provider may
identify the brand of the issuer of the eSVC, contact the issuer of the eSVC
(e.g., via an issuer
computer device 19 of Figure 3), receive a card token from the issuer of the
eSVC, and associate
8
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
the card token with the request for a security code of the eSVC. A "card
token" may comprise a
fraud-prevention identifier, such as a temporary code or access key to the
computer device of the
issuer. In an embodiment, an entity (e.g., merchant, processor of the eSVC,
provider of the
eSVC and/or e-wallet) which needs to request the security is also the security
code provider. In
such an embodiment, the entity would internally request the security code,
e.g., from a security
code unit on the computer device of such an entity.
[0031] In embodiments, the security code provider may comprise an entity
separate from a
processor of the eSVC, the eSVC issuer, the electronic wallet provider, and
the merchant. In
alternative embodiments, the security code provider may comprise a party which
is the provider
of the user's electronic wallet, the merchant, the issuer of the eSVC, the
processor of the eSVC,
or combinations thereof. In embodiments, the security code provider may
comprise a party
which is: the processor of the eSVC; alternatively, the issuer of the eSVC;
alternatively, the
electronic wallet provider; alternatively, the merchant; alternatively, the
electronic wallet
provider and the merchant; alternatively, the electronic wallet provider and
the processor of the
eSVC; alternatively, the electronic wallet provider and the eSVC issuer;
alternatively, eSVC
issuer and the eSVC processor; alternatively, the eSVC issuer and the
merchant; alternatively,
the eSVC processor and the merchant; alternatively, the electronic wallet
provider, the eSVC
issuer, and the eSVC processor; alternatively, the electronic wallet provider,
eSVC processor,
and the merchant; alternatively, the electronic wallet provider, the eSVC
issuer, and the
merchant; alternatively, the merchant, the eSVC issuer, and the eSVC
processor; alternatively,
the electronic wallet provider, the eSVC issuer, the eSVC processor, and the
merchant. In
embodiments where the security code provider is also the eSVC issuer, rules
may allow the
entity to store and/or retain a security code; however, such an entity may
also choose to calculate
the security code according to the present disclosure or delegate such
calculating responsibilities
to an agent of the security code provider. In an embodiment, the security code
provider is an
entity which calculates the security code to provide the security code but
does not store or retain
the security code (or versions thereof, e.g., received-calculated security
code, recalculated
security code, etc.).
[0032] At block 24, the security code is calculated (e.g., by the security
code provider). In an
embodiment where the security code provider comprises the provider of the
electronic wallet, the
electronic wallet provider's computer device (e.g., computer device 12 of
Figure 3) may calculate
9
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
the security code upon receiving a request for the security code (e.g., from
the user device 14 of
Figure 3). In an embodiment where the security code provider comprises the
processor of the
eSVC, the processor's computer device (e.g., computer device 18 of Figure 3)
may calculate the
security code upon receiving a request for the security code (e.g., from the
electronic wallet
provider's computer device 12 or from the user device 14 of Figure 3).
[0033] In embodiments, calculating the security code by the security code
provider may
comprise calculating the security code using the card information of the eSVC,
wherein the card
information comprises a primary account number, an expiration date, and a
security information of
the eSVC. In embodiments where a party (e.g., the electronic wallet service
provider) is allowed
under regulations and laws to store the security code, the provider computer
device 12 may store
the calculated security code, e.g., in an electronic wallet.
[0034] At block 26, the calculated security code is provided. In an
embodiment, the electronic
wallet provider (e.g., via a computer device 12 of Figure 3) may provide
(e.g., send) the calculated
security code to user (e.g., via user device 14 of Figure 3) (e.g., without
communication with an
eSVC processor). That is, in embodiments, the electronic wallet provider
(e.g., via provider
computer device 12 of Figure 3) may receive a calculated security code from
the security code
provider (e.g., via security code provider computer device 13 of Figure 3, for
example, in
embodiments where the electronic wallet provider and security code provider
are different entities)
and provide the calculated security code to the user (e.g., via user device 14
of Figure 3) without
communication with the processor of the eSVC (e.g., via processor computer
device 18 of Figure
3), or the electronic wallet provider may calculate the security code (e.g.,
via provider computer
device 12 of Figure 3, for example, in embodiments where the security code
provider comprises
the electronic wallet provider) and provide the calculated security code to
the user (e.g., via user
device 14 of Figure 3) without communication with the processor of the eSVC
(e.g., via processor
computer device 18 of Figure 3). In additional or alternative embodiments, the
processor of the
eSVC (e.g., via computer device 18 of Figure 3) may provide (e.g., send) the
calculated security
code to the provider of the electronic wallet (e.g., computer device 12 of
Figure 3), to the user (e.g.,
via user device 14 of Figure 3), to the merchant (e.g., via merchant computer
device 16 of Figure
3), or combinations thereof. If the electronic wallet provider receives the
calculated security code
from the processor of the eSVC, the electronic wallet provider may then
provide (e.g., send) the
calculated security code to the user (e.g., via user device 14 of Figure 3),
to the merchant (e.g., via
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
merchant computer device 16 of Figure 3, or both. In embodiments, providing
the security code
may include displaying the security code to the user (e.g., via a display on
the user device 14 of
Figure 3), to the merchant (e.g., via merchant computer device 16 of Figure
3), or both. In
embodiments, sending the security code may include various communication
means, including
SMS, email, video (e.g., YouTube, Vimeo, Skype, video message, or combinations
thereof),
instant message, a website, an online storage medium, a cloud storage system,
other means for
electronically obtaining the electronic stored-value card, or combinations
thereof
[0035] At block 28, the calculated security code is eliminated from
databases of the security
code provider. As used herein, the term "eliminate" includes the lack of
retention and/or storage of
a security code, a calculated security code, a received-calculated security
code, a recalculated
security code, or combinations thereof Additionally or alternatively, the term
"eliminate" include
the erasure of a security code, a calculated security code, a received-
calculated security code, a
recalculated security code, or combinations thereof In an embodiment where the
electronic wallet
provider is the security code provider, the electronic wallet provider may
eliminate the calculated
security code from databases of the electronic wallet provider. In an
additional or alternative
embodiment where the processor of the eSVC is the security code provider, the
processor may
eliminate the calculated security code from databases of the processor. In
embodiments, the step of
eliminating is performed by an entity which is not also the issuer of the
eSVC.
[0036] Once the user or merchant receives the calculated security code, the
user and/or
merchant may then use the calculated security code in a transaction.
[0037] Figure 2 shows a flow chart of another embodiment of a method
disclosed herein.
The embodiment of the method of Figure 2 may be used in addition to or in the
alternative to the
method of Figure 1. Moreover, any of the steps of the method of Figure 2 may
be used in
combination or in the alternative with any of the steps of the method of
Figure 1, and vice versa.
The embodiment of the method shown in Figure 2 begins at block 30.
[0038] At block 30, a calculated security code is received (e.g.,
calculated according to block
24 of the method in Figure 1). In the embodiments disclosed herein, the
calculated security code
which is received may be referred to as a "received-calculated security code."
The calculated
security code may be received by an electronic wallet provider, the issuer of
the eSVC, the
processor of the eSVC, the merchant, or combinations thereof In an embodiment,
the electronic
wallet provider may receive the calculated security code. For example, a
merchant (e.g., via
11
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
merchant computer device 16 of Figure 3), processor of the eSVC (e.g., via
computer device 18),
or both, may contact the electronic wallet provider and/or eSVC provider
(e.g., via the computer
device 12 of Figure 3) to complete a transaction with a consumer or user and
requiring the
calculated security code of the eSVC. In an additional or alternative
embodiment, the processor of
the eSVC (e.g., via the computer device 18) may receive the calculated
security code. For example,
a merchant (e.g., merchant computer device 16 of Figure 3), electronic wallet
provider and/or
eSVC provider (e.g., via computer device 12 of Figure 3), or combinations
thereof, may contact
the processor (e.g., via the computer device 18 of Figure 3) to complete a
transaction with a
consumer or user and requiring the calculated security code of the eSVC.
[0039] In embodiments, a request to process a payment transaction may be
associated with or
comprise the received-calculated security code, and the provider of the e-
wallet and/or provider of
the eSVC (e.g., via computer device 12), the processor of the eSVC (e.g., via
computer device 18)
may receive a request to process a payment transaction associated with the
received-calculated
security code. In embodiments where a party (e.g., an entity which includes
the issuer of the
eSVC) is allowed under rules, regulations and/or laws to store the security
code, the party may
store the received-calculated security code in a database.
[0040] At block 32, the security code is recalculated (e.g., by an entity
which is the security
code provider or by an entity which is not the security code provider). In
embodiments, the
provider of the e-wallet and/or eSVC (e.g., via computer device 12 of Figure
3), the processor
(e.g., via computer device 18), the merchant (e.g., via merchant computer
device 16), or
combinations thereof may recalculate the security code upon receiving a
request to process a
transaction with the eSVC (e.g., from the user, processor, merchant, or
combinations thereof).
[0041] In embodiments, recalculating the security code by the security code
provider may
comprise recalculating the security code using the card information of the
eSVC, wherein the card
information comprises a primary account number, an expiration date, a security
information, a
service code, or combinations thereof, of the eSVC. In embodiments where a
party (e.g., an entity
which is also the issuer of the eSVC) is allowed to store the security code,
the recalculated security
code may be stored.
[0042] At block 34, a determination is made whether the received-calculated
security code
matches the recalculated security code. In embodiments, the provider of the
eSVC and/or e-wallet,
the eSVC processor, the merchant, or combinations thereof, may determine
whether the received-
12
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
calculated security code matches the recalculated security code. If the
received-calculated security
code matches the recalculated security code, then the payment transaction may
be processed, e.g.,
as in block 36; additionally or alternatively, the codes may be eliminated,
e.g., as in block 38, after
transaction processing, before transaction processing, concurrently with
transaction processing, or
combinations thereof. If the received-calculated security code does not match
the recalculated
security code, then a party may be notified, e.g., as in block 39.
[0043] The step at block 34 is an example of a fraud mitigation technique
performed before
the user uses (e.g., redeems) a value on the eSVC for a payment transaction.
In embodiments,
before the user uses the eSVC, the eSVC provider, the e-wallet provider, the
eSVC processor,
the eSVC issuer, the merchant, or combinations thereof may provide fraud
mitigation. In an
additional or alternative embodiment, providing fraud mitigation may comprise
determining a
digital fingerprint of a user device (e.g., user device 14 of Figure 3), at
the time a user attempts to
use a calculated security code to determine the risk associated with the user
and/or user device,
the eSVC, or both. In an additional or alternative embodiment, providing fraud
mitigation may
comprise determining a risk score associated with an eSVC and/or an e-wallet,
wherein the risk
score is based on, for example, metadata of a payment transaction request,
transaction frequency,
transaction type, transaction amount, number of transactions, transaction
location (e.g., via
geocoding techniques), or other risk assessment information known to one
skilled in the art with
the aid of this disclosure. In an additional or alternative embodiment,
providing fraud mitigation
may comprise withholding the processing of the payment transaction (e.g.,
withholding the
redemption for the eSVC). In an additional or alternative embodiment,
providing fraud
mitigation may comprise determining a geographic location of the eSVC and/or
user and pausing
the processing of the payment transaction for a period of time determined by
the geographic
location. For example, the processing of the payment transaction may be held
for a longer period
of time in geographic locations known or determined to be of high risk of
fraud, and the
processing of the payment transaction may be held for a short period of time
or for a period of
time comprising zero in geographic locations known or determined to be of low
or no risk of
fraud.
[0044] At block 36, the payment transaction is processed. In an embodiment,
the payment
transaction may be processed by the provider of the eSVC and/or e-wallet
(e.g., via computer
device 12 of Figure 3), by the merchant (e.g., via computer device 16 of
Figure 3), by the processor
13
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
(e.g., via computer device 18 of Figure 3), or combinations thereof. For
example, the payment
transaction may be processed by applying a value of the eSVC (e.g., currency,
discount,
promotion, points, rewards, a value token or electronic value token as
described for the value token
transaction processing systems described hereinbelow) to complete the
transaction. In an
embodiment, to process the payment transaction, authentication information of
the request to
process a payment transaction may be identified, a value associated with the
eSVC (e.g., embodied
as a value token, described below) may be identified, at least a portion of
the value of the eSVC
(e.g., value token) may be applied to at least a portion of a request to
process a payment
transaction, or combinations thereof In an embodiment, identifying
authentication information
may comprise the method steps discussed for blocks 32, 34, and 38. In
embodiments, processing
the payment transaction may further comprise processing at least a portion of
the request to process
a payment transaction in a primary wallet of an e-wallet (e.g., electronic
wallet 10 of Figure 3),
processing at least a portion of the request to process a payment transaction
in a sub-wallet of an e-
wallet (e.g., of electronic wallet 10 of Figure 3), or both. In embodiment, a
notification may be
sent to the user, merchant, processor, and or provider that the payment has
been processed, the
received-calculated security code has been accepted, or both.
[0045] At block 38, the received-calculated security code and the
recalculated security code
are eliminated from databases of the security code provider. Elimination of
the security codes may
take place before processing of the payment transaction, after processing of
the payment
transaction, concurrent with the processing of the payment transaction, or
combinations thereof In
an embodiment where the provider of the eSVC and/or e-wallet receives the
calculated security
code and/or recalculates the security code, the provider may eliminate the
received-calculated
security code and/or recalculated security code from databases of the provider
(e.g., in computer
device 12 of Figure 3). In an embodiment where the processor receives the
calculated security
code and/or recalculates the security code, the processor may eliminate the
received-calculated
security code and/or recalculated security code from databases of the
processor (e.g., in computer
device 18 of Figure 3). In an embodiment where the merchant receives the
calculated security
code and/or recalculates the security code, the merchant may eliminate the
received-calculated
security code and/or recalculated security code from databases of the
merchant.
[0046] At block 39, a notification is sent. For example, the user (e.g.,
via user device 14 of
Figure 3) and the merchant (e.g., via merchant computer device 16 of Figure 3)
may be notified
14
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
that the received-calculated security code is invalid. In an embodiment where
a determination is
made that the received-calculated security code does not match the
recalculated security code, a
notification may be sent, e.g., as a fraud prevention means.
[0047] Figure 3 is a schematic illustration of an embodiment of a system
according to the
disclosure. As shown in Figure 3, an embodiment of the disclosed system for
providing a
security code may comprise a user device 14 (e.g., of a user), a merchant
computer device 16
(e.g., of a merchant), a provider computer device 12 (e.g., of an electronic-
wallet provider and/or
eSVC provider), a security code provider computer device (e.g., of a security
code provider) a
processor computer device 18 (e.g., of an electronic stored-value card
processor), an issuer
computer device 19 (e.g., of an issuer of the eSVC), or combinations thereof
[0048] While Figure 3 shows one embodiment of a system according to the
disclosure, it
should be understood many system embodiments are disclosed. For example, many
system
embodiments may accomplish the embodiments of the methods for providing a
security code
disclosed hereinabove depending upon whether the security code provider
computer device 13
comprises the same or different computer device as the provider computer
device 12, merchant
computer device 16, processor computer device 18, or issuer computer device
19.
[0049] In embodiments, the security code provider computer device 13 may
comprise a
device separate from the user device 14, the processor computer device 18, the
issuer computer
device 19, the provider computer device 12, and the merchant computer device
16. In alternative
embodiments, the security code provider computer device 13 may comprise a
device which is
same device as merchant computer device 16, the provider computer device 12,
the issuer of the
eSVC computer device 19, the processor of the eSVC computer device 18, or
combinations
thereof. In embodiments, the security code provider computer device 13 may
comprise a device
which is: the processor computer device 18; alternatively, the issuer computer
device 19;
alternatively, the provider computer device 12; alternatively, the merchant
computer device 16;
alternatively, the provider computer device 12 and the merchant computer
device 16;
alternatively, the provider computer device 12 and the processor computer
device 18;
alternatively, the provider computer device 12 and the issuer computer device
19; alternatively,
issuer computer device 19 and the processor computer device 18; alternatively,
the issuer
computer device 19 and the merchant computer device 16; alternatively, the
processor computer
device 18 and the merchant computer device 16; alternatively, the provider
computer device 12,
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
the issuer computer device 19, and the processor computer device 18;
alternatively, the provider
computer device 12, the processor computer device 18, and the merchant
computer device 16;
alternatively, the provider computer device 12, the issuer computer device 19,
and the merchant
computer device 16; alternatively, the merchant computer device 16, the issuer
computer device
19, and the processor computer device 18; alternatively, the provider computer
device 18, the
issuer computer device 19, the processor computer device 18, and the merchant
computer device
16. In embodiments where the security code provider is also the eSVC issuer,
rules may allow
the entity to store and/or retain a security code; however, such an entity may
also choose to
calculate the security code according to the present disclosure or delegate
such calculating
responsibilities to an agent of the security code provider. In an embodiment,
the security code
provider is an entity which calculates the security code to provide the
security code but does not
store or retain the security code (or versions thereof, e.g., received-
calculated security code,
recalculated security code, etc.).
[0050] The components of the system of Figure 3 may be operably connected
via one or
more networks (e.g., broadband, optical, Wi-Fi, Bluetooth, NFC, cellular,
satellite, cloud, card
processing network, banking network, a local area network, the World Wide Web
for Internet,
non-cellular mobile phone network, a land-line network, Public Switched
Telephone Network
(PSTN), a dedicated communication line, other networks for transferring
electronic information,
or combinations thereof). Particularly, the user device 14 may be operably
connected to the
provider computer device 12, the security code provider computer device 13,
the merchant
computer device 16, the processor computer device 18, the issuer computer
device 19, or
combinations thereof, via the network; the merchant computer device 16 may be
operably
connected to the user device 14, the security code provider computer device
13, the processor
computer device 18, the provider computer device 12, the issuer computer
device 19, or
combinations thereof, via the network; the provider computer device 12 may be
operably
connected to the user device 14, the merchant computer device 16, the security
code provider
computer device 13, the processor computer device 18, the issuer computer
device 19, or
combinations thereof, via the network; the processor computer device 18 may be
operably
connected to the user device 14, provider computer device 12, security code
provider computer
device 13, the merchant computer device 16, the issuer computer device 19, or
combinations
thereof, via the network; or combinations thereof. When any of the computer
devices 13, 14, 16,
16
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
18, or 19 of the system is operably connected to the provider computer device
12, said devices
13, 14, 16, 18, or 19 may additionally be operably connected to an e-wallet on
the provider
computer device 12.
[0051] The security code provider computer device 13 may comprise one or
more computer
devices (e.g., a computer, a tablet, a smartphone, a cloud computing system, a
server, or
combinations thereof), which is suitable for performing the functions
described herein.
[0052] In embodiments, the security code provider computer device 13 may be
configured to
receive a request for a security code of an eSVC (e.g., from the provider
computer device 12, the
user device 14, the merchant computer device 16, the processor computer device
18, the issuer
computer device 19, or combinations thereof); to calculate the security code
(e.g., using at least a
portion of the card information of the eSVC); to provide (e.g., send, display,
etc.) the calculated
security code in response to the request for a security code (e.g., to the
provider computer device
12, the user device 14, the merchant computer device 16, the processor
computer device 18, the
issuer computer device 19, or combinations thereof); to eliminate the
calculated security code
from the security code provider computer device 13 (e.g., from any
database/datastore of the
security code provider computer device 13); to receive the calculated security
code (e.g., from
the provider computer device 12, the user device 14, the processor computer
device 18, the
merchant computer device 16, the issuer computer device 19, or combinations
thereof), for
example, as part of a request to process a payment transaction; to recalculate
the security code of
the eSVC (e.g., eSVC 11); to determine whether the received-calculated
security code (e.g.,
received from the provider computer device 12, the user device 14, the
merchant computer
device 16, the processor computer device 18, the issuer computer device 19, or
combinations
thereof) matches the recalculated security code; to eliminate the received-
calculated security
code and recalculated security code from the security code provider computer
device 13 (e.g.,
from any database/datastore of the security code provider computer device 13);
to receive (e.g.,
from the provider computer device 12, the user device 14, merchant computer
device 16,
processor computer device 18, issuer computer device 19, or combinations
thereof) a request to
process a payment transaction (e.g., against an eSVC 11, for example, in e-
wallet 10); to identify
authentication information of the request to process a payment transaction; to
identify a value
(e.g., value token, currency, rewards, points, discount, promotion,
combinations thereof, etc.)
associated with the eSVC; to apply at least a portion of the value to at least
a portion of the
17
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
request to process the payment transaction; to provide fraud mitigation; to
block access to an
eSVC before a user views the eSVC; to block access to an eSVC before a user
activates the
eSVC, to determine a digital fingerprint of a user device (e.g., user device
14), at the time a user
attempts to view an eSVC to determine the risk associated with the user, the
eSVC, or both; to
withhold the providing of the eSVC (e.g., withholding the delivery of
redemption information for
the eSVC); to determine a geographic location of the eSVC and/or user; to
pause the providing
of the eSVC for a period of time determined by the geographic location, or
combinations thereof.
[0053] In additional embodiments, in order to calculate and/or recalculate
the security code,
the security code provider computer device 13 may use a primary account
number, an expiration
date, a service code, a security information (e.g., magnetic stripe security
code), or combinations
thereof, of the eSVC (e.g., eSVC 11). In embodiments, the security code
provider computer
device 13 may be configured to process at least a portion of a request to
process a payment
transaction via a primary wallet of an electronic wallet 10, the security code
provider computer
device 13 may be configured to process at least a portion of a request to
process a payment
transaction via a sub-wallet of an electronic wallet 10, or both (primary
wallets and sub-wallets
are discussed hereinbelow).
[0054] The user device 14 may comprise a personal computer, a tablet, a
smartphone, a
cloud computing system, a server, or combinations thereof. The device used by
the user or
consumer to transact business with the merchant computer device 16 may be the
same or
different device from the user device 14. In embodiment, the user or consumer
may transact
business using the user device 14; alternatively, the user or consumer may use
the user device 14
to request and receive a calculated security code and use other means (e.g., a
computer device
separate from the user device 14) to transact business, e.g., with a merchant
via merchant
computer device 16). In an embodiment, the user device 14 may be used to
convey transaction
information to the provider computer device 12, security code provider
computer device 13,
merchant computer device 16, processor computer device 18, issuer computer
device 19, or
combinations thereof. In embodiments, a user or consumer may interact (e.g.,
use the eSVC) via
the user device 14 with the provider computer device 12, for example, to add
or remove eSVCs
(e.g., in an e-wallet 10), add value to an eSVC (e.g., eSVC 11), manage an
eSVC embodied as a
value token (described hereinbelow, register an eSVC, activate an eSVC,
transfer or exchange an
eSVC for another eSVC (e.g., in an embodiment where the provider computer
device 12 is also a
18
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
merchant computer device 16), transfer eSVCs to an e-wallet or a primary
wallet or a sub-wallet,
or combinations thereof. In embodiments, a user or consumer may interact
(e.g., use an obtained
eSVC) via the user device 14 with a transaction portal (i.e., online merchant
portal to redeem a
gift, discount, credit, reward, points, etc.) without interaction with an e-
wallet hosted by an e-
wallet provider. Embodiments of the disclosed system may further comprise an
interface (e.g.,
associated with the user device 14) through which a viewer may access one or
more eSVCs (e.g.,
eSVC 11). In an embodiment, a user may interact via the user device 14 with
the electronic
wallet 10 to obtain a security code of the eSVC 11 in the electronic wallet
10.
100551 In embodiments, the security code provider computer device 13 may
comprise the
user device 14. In such embodiments, the user device 14 may be configured to
receive a request
for a security code of an eSVC (e.g., from the provider computer device 12,
the merchant
computer device 16, the processor computer device 18, the issuer computer
device 19, or
combinations thereof); to calculate the security code (e.g., using at least a
portion of the card
information of the eSVC); to provide (e.g., send, display, etc.) the
calculated security code in
response to the request for a security code (e.g., to the provider computer
device 12, the
merchant computer device 16, the processor computer device 18, the issuer
computer device 19,
or combinations thereof); to eliminate the calculated security code from the
user device 14 (e.g.,
from any database/datastore of the user device 14); to receive the calculated
security code (e.g.,
from the provider computer device 12, the processor computer device 18, the
merchant computer
device 16, the issuer computer device 19, or combinations thereof), for
example, as part of a
request to process a payment transaction; to recalculate the security code of
the eSVC (e.g.,
eSVC 11); to determine whether the received-calculated security code (e.g.,
received from the
provider computer device 12, the merchant computer device 16, the processor
computer device
18, the issuer computer device 19, or combinations thereof) matches the
recalculated security
code; to eliminate the received-calculated security code and recalculated
security code from the
user device 14 (e.g., from any database/datastore of the user device 14); to
receive (e.g., from the
provider computer device 12, merchant computer device 16, processor computer
device 18,
issuer computer device 19, or combinations thereof) a request to process a
payment transaction
(e.g., against an eSVC 11, for example, in e-wallet 10); to identify
authentication information of
the request to process a payment transaction; to identify a value (e.g., value
token, currency,
rewards, points, discount, promotion, combinations thereof, etc.) associated
with the eSVC; to
19
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
apply at least a portion of the value to at least a portion of the request to
process the payment
transaction; to provide fraud mitigation; to block access to an eSVC before a
user views the
eSVC; to block access to an eSVC before a user activates the eSVC; to
determine a digital
fingerprint of a user device (e.g., user device 14), at the time a user
attempts to view an eSVC to
determine the risk associated with the user, the eSVC, or both; to withhold
the providing of the
eSVC (e.g., withholding the delivery of redemption information for the eSVC);
to determine a
geographic location of the eSVC and/or user; to pause the providing of the
eSVC for a period of
time determined by the geographic location; or combinations thereof.
[0056] In additional embodiments, in order to calculate and/or recalculate
the security code,
the user device 14 may use a primary account number, an expiration date, a
service code, a
security information (e.g., magnetic stripe security code), or combinations
thereof, of the eSVC
(e.g., eSVC 11).
[0057] The merchant computer device 16 may comprise a computer device
(e.g., a point-of-
sale device) of a merchant. The merchant computer device 16 may have any
suitable
configuration for performing the functions disclosed herein (e.g., a personal
computer, a tablet, a
smartphone, a cloud computing system, a server, or combinations thereof). In
embodiments, the
merchant computer device 16 may perform transactions with a computer device
(e.g., user device
14) of a consumer, for example, in a transaction (e.g., online,
telephonically, or both) requiring
the security code for an eSVC. The merchant computer device 16 may communicate
with the
processor computer device to complete a transaction with a user or consumer.
[0058] In embodiments, the security code provider computer device 13 may
comprise the
merchant computer device 16. In such embodiments, the merchant computer device
16 may be
configured to receive a request for a security code of an eSVC (e.g., from the
provider computer
device 12, the user device 14, the processor computer device 18, the issuer
computer device 19,
or combinations thereof); to calculate the security code (e.g., using at least
a portion of the card
information of the eSVC); to provide (e.g., send, display, etc.) the
calculated security code in
response to the request for a security code (e.g., to the provider computer
device 12, the user
device 14, the processor computer device 18, the issuer computer device 19, or
combinations
thereof); to eliminate the calculated security code from the merchant computer
device 16 (e.g.,
from any database/datastore of the merchant computer device 16); to receive
the calculated
security code (e.g., from the provider computer device 12, the user device 14,
the processor
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
computer device 18, the issuer computer device 19, or combinations thereof),
for example, as
part of a request to process a payment transaction; to recalculate the
security code of the eSVC
(e.g., eSVC 11); to determine whether the received-calculated security code
(e.g., received from
the provider computer device 12, the user device 14, the processor computer
device 18, the issuer
computer device 19, or combinations thereof) matches the recalculated security
code; to
eliminate the received-calculated security code and recalculated security code
from the merchant
computer device 16 (e.g., from any database/datastore of the merchant computer
device 16); to
receive (e.g., from the provider computer device 12, the user device 14,
processor computer
device 18, issuer computer device 19, or combinations thereof) a request to
process a payment
transaction (e.g., against an eSVC 11, for example, in e-wallet 10); to
identify authentication
information of the request to process a payment transaction; to identify a
value (e.g., value token,
currency, rewards, points, discount, promotion, combinations thereof, etc.)
associated with the
eSVC; to apply at least a portion of the value to at least a portion of the
request to process the
payment transaction; to provide fraud mitigation; to block access to an eSVC
before a user views
the eSVC; to block access to an eSVC before a user activates the eSVC; to
determine a digital
fingerprint of a user device (e.g., user device 14), at the time a user
attempts to view an eSVC to
determine the risk associated with the user, the eSVC, or both; to withhold
the providing of the
eSVC (e.g., withholding the delivery of redemption information for the eSVC);
to determine a
geographic location of the eSVC and/or user; to pause the providing of the
eSVC for a period of
time determined by the geographic location; or combinations thereof.
[0059] In additional embodiments, in order to calculate and/or recalculate
the security code,
the merchant computer device 16 may use a primary account number, an
expiration date, a
service code, a security information (e.g., magnetic stripe security code), or
combinations
thereof, of the eSVC (e.g., eSVC 11). In embodiments, the merchant computer
device 16 may be
configured to process at least a portion of a request to process a payment
transaction via a
primary wallet of an electronic wallet 10, the merchant computer device 16 may
be configured to
process at least a portion of a request to process a payment transaction via a
sub-wallet of an
electronic wallet 10, or both (primary wallets and sub-wallets are discussed
hereinbelow).
[0060] The provider computer device 12 may be a computer device of a
provider of one or
more electronic wallets (e.g., electronic wallet 10), a provider of an eSVC
(e.g., eSVC 11), or
both. The provider computer device 12 may have any suitable configuration for
performing the
21
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
functions disclosed herein (e.g., a personal computer, a tablet, a smartphone,
a cloud computing
system, a server, or combinations thereof). Figure 3 shows the provider
computer device 12 may
comprise an electronic wallet 10. In embodiments, the provider computer device
12 may further
comprise an electronic value token transaction processing system, for example,
of an
embodiment described in Figures 4A-B, and 5A-C hereinbelow. In embodiments,
the provider
computer device 12 may further comprise a database (e.g., database/datastore
180 as described
for the figures hereinbelow) to store one or more eSVCs (e.g., eSVC 11), one
or more electronic
wallets (e.g., electronic wallet 10), at least a portion of the card
information associated with each
eSVC, or combinations thereof.
[0061] Figure 3 shows an embodiment of the system comprising one electronic
wallet 10.
In alternative embodiments, the system may comprise a first electronic wallet
and a second
electronic wallet. In additional or alternative embodiments, the electronic
wallet 10 may
comprise any number of sub-wallets as described herein below. Electronic
wallets (e.g.,
electronic wallet 10) may offer a variety of services, including storing,
managing, and facilitating
the redemption of value (e.g., monetary, discount, promotional, value tokens,
rewards, etc.) of
eSVCs. One or more electronic stored-value cards (hereinafter "eSVC" or
"eSVCs") (e.g., eSVC
11) may be associated (e.g., registered) with the one or more electronic
wallets. For example, a
first eSVC (e.g., eSVC 11 ) and a second eSVC may be registered in electronic
wallet 10.
Alternatively, a first eSVC (e.g., eSVC 11) may be registered in a first
electronic wallet and a
second eSVC may be registered in a second electronic wallet. In additional or
alternative
embodiments, one or more eSVCs may be associated (e.g., registered) in a sub-
wallet of an
electronic wallet (registration techniques, methods, and processes are
discussed hereinbelow).
Embodiments of the electronic wallet 10 are described in detail hereinbelow,
for example, in the
discussion for Figure 4B.
[0062] In embodiments, the security code provider computer device 13 is the
provider computer
device 12. In such embodiments, the provider computer device 12 may be
configured to receive
a request for a security code of an eSVC (e.g., from the user device 14, the
merchant computer
device 16, the processor computer device 18, the issuer computer device 19, or
combinations
thereof); to calculate the security code (e.g., using at least a portion of
the card information of the
eSVC); to provide (e.g., send, display, etc.) the calculated security code in
response to the
request for a security code (e.g., to the user device 14, the merchant
computer device 16, the
22
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
processor computer device 18, the issuer computer device 19, or combinations
thereof); to
eliminate the calculated security code from the provider computer device 12
(e.g., from any
database/datastore of the provider computer device 12); to receive the
calculated security code
(e.g., from the user device 14, the processor computer device 18, the merchant
computer device
16, the issuer computer device 19, or combinations thereof), for example, as
part of a request to
process a payment transaction; to recalculate the security code of the eSVC
(e.g., eSVC 11); to
determine whether the received-calculated security code (e.g., received from
the user device 14,
the merchant computer device 16, the processor computer device 18, the issuer
computer device
19, or combinations thereof) matches the recalculated security code; to
eliminate the received-
calculated security code and recalculated security code from the provider
computer device 12
(e.g., from any database/datastore of the provider computer device 12); to
receive (e.g., from the
user device 14, merchant computer device 16, processor computer device 18,
issuer computer
device 19, or combinations thereof) a request to process a payment transaction
(e.g., against an
eSVC 11, for example, in e-wallet 10); to identify authentication information
of the request to
process a payment transaction; to identify a value (e.g., value token,
currency, rewards, points,
discount, promotion, combinations thereof, etc.) associated with the eSVC; to
apply at least a
portion of the value to at least a portion of the request to process the
payment transaction; to
provide fraud mitigation; to block access to an eSVC before a user views the
eSVC; to block
access to an eSVC before a user activates the eSVC; to determine a digital
fingerprint of a user
device (e.g., user device 14), at the time a user attempts to view an eSVC to
determine the risk
associated with the user, the eSVC, or both; to withhold the providing of the
eSVC (e.g.,
withholding the delivery of redemption information for the eSVC); to determine
a geographic
location of the eSVC and/or user; to pause the providing of the eSVC for a
period of time
determined by the geographic location; or combinations thereof.
100631 In additional embodiments, in order to calculate and/or recalculate
the security code,
the provider computer device 12 may use a primary account number, an
expiration date, a
service code, a security information (e.g., magnetic stripe security code), or
combinations
thereof, of the eSVC (e.g., eSVC 11). In embodiments, the provider computer
device 12 may be
configured to process at least a portion of a request to process a payment
transaction via a
primary wallet of an electronic wallet 10, the provider computer device 12 may
be configured to
23
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
process at least a portion of a request to process a payment transaction via a
sub-wallet of an
electronic wallet 10, or both (primary wallets and sub-wallets are discussed
hereinbelow).
[0064] The processor computer device 18 may comprise a computer device of a
processor of
an electronic stored-value card (e.g., eSVC 11). The processor computer device
18 may have
any suitable configuration for performing the functions disclosed herein
(e.g., a personal
computer, a tablet, a smartphone, a cloud computing system, a server, or
combinations thereof).
[0065] In embodiments, the security code provider computer device 13 is the
processor
computer device 18. In such embodiments, the processor computer device 18 may
be configured
to receive a request for a security code of an eSVC (e.g., from the provider
computer device 12,
the user device 14, the merchant computer device 16, the issuer computer
device 19, or
combinations thereof); to calculate the security code (e.g., using at least a
portion of the card
information of the eSVC); to provide (e.g., send, display, etc.) the
calculated security code in
response to the request for a security code (e.g., to the provider computer
device 12, the user
device 14, the merchant computer device 16, the issuer computer device 19, or
combinations
thereof); to eliminate the calculated security code from the processor
computer device 18 (e.g.,
from any database/datastore of the processor computer device 18); to receive
the calculated
security code (e.g., from the provider computer device 12, the user device 14,
the merchant
computer device 16, the issuer computer device 19, or combinations thereof),
for example, as
part of a request to process a payment transaction; to recalculate the
security code of the eSVC
(e.g., eSVC 11); to determine whether the received-calculated security code
(e.g., received from
the provider computer device 12, the user device 14, the merchant computer
device 16, the issuer
computer device 19, or combinations thereof) matches the recalculated security
code; to
eliminate the received-calculated security code and recalculated security code
from the processor
computer device 18 (e.g., from any database/datastore of the processor
computer device 18); to
receive (e.g., from the provider computer device 12, the user device 14,
merchant computer
device 16, issuer computer device 19, or combinations thereof) a request to
process a payment
transaction (e.g., against an eSVC 11, for example, in e-wallet 10); to
identify authentication
information of the request to process a payment transaction; to identify a
value (e.g., value token,
currency, rewards, points, discount, promotion, combinations thereof, etc.)
associated with the
eSVC; to apply at least a portion of the value to at least a portion of the
request to process the
payment transaction; to provide fraud mitigation; to block access to an eSVC
before a user views
24
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
the eSVC; to block access to an eSVC before a user activates the eSVC; to
determine a digital
fingerprint of a user device (e.g., user device 14), at the time a user
attempts to view an eSVC to
determine the risk associated with the user, the eSVC, or both; to withhold
the providing of the
eSVC (e.g., withholding the delivery of redemption information for the eSVC);
to determine a
geographic location of the eSVC and/or user; to pause the providing of the
eSVC for a period of
time determined by the geographic location; or combinations thereof.
[0066] In additional embodiments, in order to calculate and/or recalculate
the security code,
the processor computer device 18 may use a primary account number, an
expiration date, a
service code, a security information (e.g., magnetic stripe security code), or
combinations
thereof, of the eSVC (e.g., eSVC 11). In embodiments, the processor computer
device 18 may
be configured to process at least a portion of a request to process a payment
transaction via a
primary wallet of an electronic wallet 10, the processor computer device 18
may be configured to
process at least a portion of a request to process a payment transaction via a
sub-wallet of an
electronic wallet 10, or both (primary wallets and sub-wallets are discussed
hereinbelow).
[0067] In embodiments, the processor computer device 18 may comprise a
database (e.g., the
database/datastore 180 described herein below) to store at least a portion of
the card information
associated with each eSVC.
[0068] The issuer computer device 19 may comprise a computer device of an
issuer of an
electronic stored-value card (e.g., eSVC 11). The issuer computer device 19
may have any
suitable configuration for performing the functions disclosed herein (e.g., a
personal computer, a
tablet, a smartphone, a cloud computing system, a server, or combinations
thereof).
[0069] In embodiments, the security code provider computer device 13 is the
issuer
computer device 19. In such embodiments, the issuer computer device 19 may be
configured to
receive a request for a security code of an eSVC (e.g., from the provider
computer device 12, the
user device 14, the merchant computer device 16, the processor computer device
18, or
combinations thereof); to calculate the security code (e.g., using at least a
portion of the card
information of the eSVC); to provide (e.g., send, display, etc.) the
calculated security code in
response to the request for a security code (e.g., to the provider computer
device 12, the user
device 14, the merchant computer device 16, the processor computer device 18,
or combinations
thereof); to eliminate the calculated security code from the issuer computer
device 19 (e.g., from
any database/datastore of the issuer computer device 19); to receive the
calculated security code
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
(e.g., from the provider computer device 12, the user device 14, the processor
computer device
18, the merchant computer device 16, or combinations thereof), for example, as
part of a request
to process a payment transaction; to recalculate the security code of the eSVC
(e.g., eSVC 11); to
determine whether the received-calculated security code (e.g., received from
the provider
computer device 12, the user device 14, the merchant computer device 16, the
processor
computer device 18, or combinations thereof) matches the recalculated security
code; to
eliminate the received-calculated security code and recalculated security code
from the issuer
computer device 19 (e.g., from any database/datastore of the issuer computer
device 19); to
receive (e.g., from the provider computer device 12, the user device 14,
merchant computer
device 16, processor computer device 18, or combinations thereof) a request to
process a
payment transaction (e.g., against an eSVC 11, for example, in e-wallet 10);
to identify
authentication information of the request to process a payment transaction; to
identify a value
(e.g., value token, currency, rewards, points, discount, promotion,
combinations thereof, etc.)
associated with the eSVC; to apply at least a portion of the value to at least
a portion of the
request to process the payment transaction; to provide fraud mitigation; to
block access to an
eSVC before a user views the eSVC; to block access to an eSVC before a user
activates the
eSVC; to determine a digital fingerprint of a user device (e.g., user device
14), at the time a user
attempts to view an eSVC to determine the risk associated with the user, the
eSVC, or both; to
withhold the providing of the eSVC (e.g., withholding the delivery of
redemption information for
the eSVC); to determine a geographic location of the eSVC and/or user; to
pause the providing
of the eSVC for a period of time determined by the geographic location; or
combinations thereof
[0070] In additional embodiments, in order to calculate and/or recalculate
the security code,
the issuer computer device 19 may use a primary account number, an expiration
date, a service
code, a security information (e.g., magnetic stripe security code), or
combinations thereof, of the
eSVC (e.g., eSVC 11). In embodiments, the issuer computer device 19 may be
configured to
process at least a portion of a request to process a payment transaction via a
primary wallet of an
electronic wallet 10, the issuer computer device 19 may be configured to
process at least a
portion of a request to process a payment transaction via a sub-wallet of an
electronic wallet 10,
or both (primary wallets and sub-wallets are discussed hereinbelow).
[0071] An exemplary system for providing a security code for an electronic
stored-value card
is depicted in Figure 3. A user having user device 14 may obtain an eSVC from
the provider
26
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
computer device 12, for example, via an e-wallet of the user stored on the
provider computer
device 12 which is accessible by a device (e.g., the user device 14) of the
user, or via a delivery
of the eSVC to the user device 14 (e.g., by SMS, email, video (e.g., YouTube,
Vimeo, Skype,
video message, or combinations thereof), instant message, a website, an online
storage medium,
a cloud storage system, other means for electronically obtaining the
electronic stored-value card,
or combinations thereof). Before the eSVC is obtained, the provider computer
device 12,
security code provider computer device 13, merchant computer device 16,
processor computer
device 18, issuer computer device 19, or combinations thereof may provide
fraud mitigation. In
embodiments, fraud mitigation may comprise blocking access to an eSVC before a
user views
the eSVC, e.g., on user device 14; blocking access to an eSVC before a user
activates the eSVC;
determining a digital fingerprint of a user device (e.g., user device 14), at
the time a user
attempts to view an eSVC to determine the risk associated with the user, the
eSVC, or both;
withholding the providing of the eSVC (e.g., withholding the delivery of
redemption information
for the eSVC); determining a geographic location of the eSVC and/or user;
pausing the providing
of the eSVC for a period of time determined by the geographic location; or
combinations thereof.
100721 A user or consumer having an eSVC may obtain a security code, e.g.,
a CVV2, for
the eSVC in a number of ways. For example, if the user received the eSVC as a
URL, e.g., in an
email as an eGift, the user may select/activate the URL which opens a webpage
hosted by the
eSVC provider. The URL may contain an identifier of the eSVC for the provider
webpage
which facilitates a display of relevant data, e.g., logo, terms and
conditions, redemption
instructions, card number, security information, and expiration date, etc.,
for the eSVC. The
webpage may then communicate with an API of the eSVC provider to retrieve the
security code,
e.g., CV V2, for the webpage-displayed eSVC. As such, upon receipt of the
eSVC, the user may
initiate a process for acquiring the eSVC's security code necessary for future
transactions.
Similarly, if the eSVC user/consumer received the eSVC as an eCode, e.g.,
delivered directly to
the user (e.g., via SMS, Instant Message, and email) the eCode message may
provide the user
with link or instructions for accessing the eSVC provider's system for
obtaining the eSVC's
security code in a manner similar to the manner described concerning the above-
eGift
embodiment. Further, in an embodiment wherein the eSVC is directly provisioned
to the user's
electronic wallet, the e-wallet provisioning action may induce the e-wallet to
provide the user
with link or instructions for accessing the eSVC provider's system for
obtaining the eSVC's
27
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
security code in a manner similar to the manner described concerning the above-
eGift
embodiment.
[0073] In another example, when a user desires a transaction with a
merchant device 16 (e.g.,
a website, Internet portal, or other transaction point described herein or
known to those skilled in
the art with the aid of this disclosure), and the user has not yet received
the eSVC's security
code, the user may use the user device 14 to request a security code for the
eSVC by contacting
the provider computer device 12 or the security code provider computer device
13 (e.g., in
embodiments where provider computer device 12 is not of the security code
provider). If the
user uses the user device 14 to request the security code for the eSVC by
contacting the provider
computer device 12, the provider computer device 12 may calculate the security
code (e.g., in
embodiments where the provider computer device 12 is of the security code
provider), or the
provider computer device 12 may forward the request or make a request for the
security code of
the eSVC by contacting the security code provider computer device 13 (e.g.,
which can be the
computer device of an independent entity, of the merchant, of the eSVC
processor, of the eSVC
issuer, or combinations thereof). As discussed above, the disclosure
contemplates embodiments
where the merchant computer device 16, processor computer device 18, and/or
issuer computer
device 19 make a request for the security code of the eSVC which the user uses
for the
transaction.
[0074] After the security code request is received, the security code
provider computer
device 13 calculates the security code of the eSVC, for example, using the
primary account
number, expiration date, service code, available security information (e.g.,
from the magnetic
stripe of the physical card of the eSVC), or combinations thereof In an
embodiment, a CVV2
may be calculated by encrypting the primary account number, the expiration
date, and security
code with encryption keys. The security code provider computer device 13 then
sends the
calculated security code to the provider computer device 12 (e.g., in
embodiments where the user
request was forwarded to the security code provider computer device 13 by the
provider
computer device 12) or sends the calculated security code to the user device
14. In embodiments
where the provider computer device 12 receives the calculated security code,
the provider
computer device 12 then sends the calculated security code to the user device
14.
[0075] The security code provider computer device 13 may eliminate the
calculated security
code from some, selected, or all databases of the security code provider
computer device 13.
28
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
The provider computer device 12 may eliminate the calculated security code
from some,
selected, or all databases of the provider computer device 13.
[0076] After
the user device 14 receives the calculated security code the calculated
security
code may be used in the transaction with the merchant computer device 16. The
merchant
computer device 16 may require various inputs to capture eSVC information from
the user
device 14. For example, the merchant computer device 16 may require an account
number,
billing address, expiration date, and the calculated security code of the
eSVC. The merchant
computer device 16 may establish a secure communication with the eSVC
processing system on
processor computer device 18 and request to process the payment transaction.
The
communication between the merchant computer device 1 6 and the processor
computer device 18
may be encrypted for security. The processor computer device 18 may comprise a
transaction
routing service, an internal card processing service, a settlement service, a
product master catalog
service, and an inventory management service. The transaction routing service
of the processor
computer device 18 may communicate with the merchant computer device 16 as
well as third
party card processors. The transaction routing service may receive the
collected eSVC
information (i.e., account number, expiration date, name on the eSVC,
calculated security code)
from the merchant computer device 16 and determine whether to forward the
request to process a
payment transaction to a third party processor (e.g., to forward the request)
or to process the
request to process the payment transaction for the eSVC 11, for example, by
comparing an
information of the eSVC 11 to information in a master catalog service to
determine whether the
eSVC 11 is a product for which the processor computer device 18 acts as the
processor. Thus,
for example, if the eSVC is a stored-value card processed by the processor
computer device 18,
then the transaction routing service may forward the request to process a
payment transaction to
the internal card processing service within the processor computer device 18
or is one processed
by a third party eSVC processor. If the eSVC 11 is processed by a third party
processors, the
transaction routing service routes the activation request to the third party
processor for payment
processing. The transaction routing service of the processor computer device
18 may receive a
payment response from the appropriate third party processors and may transmit
the payment
response back to the merchant computer device 16.
[0077] If
the transaction routing service determines that the eSVC 11 is one that is
processed
by the processor computer device 18 (and not merely a request to process a
payment for which
29
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
the processor computer device 18 serves as a routing service), the processor
computer device 18
may transfer the request to process a payment transaction from the merchant
computer device 16
to the internal card processing service of the processor computer device 18
which uses the
information contained in the request (e.g., account number, name on the eSVC,
expiration date,
the received-calculated security code) to determine whether to process the
eSVC 11. For
example, the processor computer device 18 may recalculate the security code of
the eSVC 11
and determine whether the recalculated security code matches the received-
calculated security
code. If the recalculated security code of the eSVC 11 matches the received-
calculated security
code of the eSVC 11, the internal card processing service of the processor
computer device 18
may contact the issuer computer device 19 to process the payment transaction.
Upon processing
of the payment transaction, the processor computer device 18 may transmit a
successful payment
response to the merchant computer device 16 via the transaction routing
service of the processor
computer device 18. The internal card processing service may also update a
database/datastore
of payment status to indicate that the eSVC 11 has been used for a payment
transaction. The
internal card processing service may also eliminate the received-calculated
security code and
recalculated security code from databases/datastores of the processor computer
device 18. The
internal card processing service of the processor computer device 18 may also
compare the
eSVC type to types of cards issued by the issuer of the eSVC in the product
master catalog
service to help verify that the eSVC is authentic.
[0078] The transaction routing service may also route the request to
process a payment
transaction to the settlement service of the processor computer device 18. The
settlement service
may allocate appropriate portions of value paid for the payment transaction
among the various
entities involved in the transaction (i.e., provider computer device 12,
issuer computer device 19,
etc.). This amount may be a percentage of the amount of the value of the
payment transaction.
The settlement service of the processor computer device 18 may also allocate
amounts received
for the payment transaction to the eSVC issuer (e.g., via issuer computer
device 19), the eSVC
processor (e.g., via processor computer device 18), the provider of the eSVC
(e.g., via provider
computer device 12, combinations thereof, etc.).
[0079] Reference to the calculation of a recalculated security code should
include
embodiments where the security code is calculated by one entity while the
recalculated security
code is calculated by another entity. Reference to the calculation of the
recalculated security code
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
should also include embodiments where the security code is calculated and
recalculated by the
same entity.
[0080] In embodiments disclosed herein, the security code which is
calculated or
recalculated according to the embodiments disclosed herein may comprise a
security code used
for transactions which do not utilize the magnetic stripe security code or
smart chip security code
of a physical card, for example, a security code suitable for a transaction
where a physical card is
not swiped or read (e.g., via NFC, Bluetooth, Wi-Fi, radio, or any other
frequency), such as a
digital (e.g., online) transaction or a telephonic transaction. In additional
or alternative
embodiments, the security code may be embodied as a calculated security code,
a received-
calculated security code, a recalculated security code, or combinations
thereof (discussed
hereinbelow). In embodiments, the security code, calculated security code,
received-calculated
security code, recalculated security code, or combinations thereof, may
comprise a CVV2.
[0081] According to the disclosed systems and methods, the security code
provider has the
ability to provide a security code without storing the security code in order
to comply with rules
governing security codes. As such, the security code provider may observe
rules which prohibit
the storage and/or retention of security codes while serving customers or
users with mechanisms
for making payment transactions when such security codes are needed.
Additionally, the
systems and methods disclosed herein provide redundancy to ensure calculated
security codes
and received-calculated security codes are accurate and/or correct without
storing the security
codes.
[0082] The embodiments described herein also provide fraud mitigation
techniques which
have various advantages. The fraud mitigation techniques help to protect eSVC
providers as
well as eSVC distributers from fraud associating with redeeming eSVCs. It has
been found that
performing a fraud mitigation step before a user obtains the eSVC affects the
ability of a user to
obtain the eSVC by fraudulent means. The fraud mitigation techniques provide
an ability for the
disclosed method and system embodiments to withhold or "soft void" an eSVC
before a user
obtains the eSVC which prevents loss due to fraud. The fraud mitigation
techniques also provide
improved customer service. For example, if a user claims they never received
or lost their eSVC
(e.g., email or text notification was deleted), the embodiments disclosed
herein allow for
withholding the processing of payment transaction, blocking the eSVC from
being obtained,
issuance of a replacement eSVC, or combinations thereof. The fraud mitigation
techniques
31
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
disclosed herein help protect eSVC providers, e-wallet providers, eSVC
processors, eSVC
issuers, merchants, and eSVC distribution partners from fraud before and after
purchase of the
eSVC.
[0083] The embodiments for provision of a security code as described herein
above may be
included in systems and method for distributing open loop eSVCs. For example,
a computer
device (e.g., one or more of the computer devices described herein above) may
receive an open
loop eSVC distribution request, provide the open loop eSVC in response to the
open loop eSVC
request, notify a recipient or user of the open loop eSVC provided in response
to the open loop
eSVC distribution request; allow the open loop eSVC to be associated with an
electronic wallet;
and enable the open loop eSVC for a transaction (e.g., redemption, purchase,
reload, registration,
or combinations thereof) as disclosed herein. The open loop eSVC may be
provided via any
embodiment disclosed herein (e.g., eGift, eCode, directly to an electronic
wallet, or combinations
thereof). Additionally or alternatively, the open loop eSVC may be delivered
as a uniform source
locator ("URL"), for example, via email, short message service ("SMS"), social
media post, other
electronic channel, or combinations thereof. In embodiments, the open loop
eSVC is delivered
directly to the recipient via any mechanism disclosed herein. Any URL may
reference a
HyperText Markup Language ("HTML") page, and in such embodiments, the HTML
page may
provide information concerning the embodiment by which the eSVC is provided
(e.g., eGift,
eCode, electronic wallet, or combinations thereof). The provided information
may include terms
and conditions, redemption instructions, reload instructions, an
identification number of the open
loop eSVC, a security code, an expiration date, or combinations thereof. When
the provided
information includes a security code, the security code may comprise an
embodiment or a
combination of the embodiments disclosed herein. Moreover, the security code
may be obtained
dynamically by a computer device (e.g., of an issuer of the eSVC). The
computer device may not
store the security code and instead the computer device may calculate the
security code (e.g., as
discussed herein above; additionally or alternatively, in a particular
embodiment, a CVV2 is
calculated by encrypting PAN, the expiration date, and the security code with
encryption keys) in
order to provide or facilitate provision of the security code. In embodiments,
the security code
may be calculated in real time.
[0084] Also disclosed herein (e.g., as shown in Figures 4A, 5A-B, and 7A-
B), an electronic
value token transaction processing system provides users, merchants, vendors,
issuers, providers,
32
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
and other interested parties an efficient, secure, and effective system for
facilitating the
organization, management, transportation, storage, and use of the
aforementioned e-wallets and
electronic value tokens in financial transactions. As described hereinbelow,
there are certain basic
concepts and functions employed by e-wallets and e-wallet enabled systems.
These concepts
include the creation of an e-wallet, provisioning the e-wallet (e.g.,
converting tangible cards into
electronic value tokens and associating the electronic value tokens to an e-
wallet or requesting an
electronic value token be associated with the e-wallet), accessing the e-
wallet, and establishing
rules for the e-wallet's use. Moreover, as will be more fully detailed herein,
the e-wallet may be
used in a system wherein the e-wallet provider manages the entirety of the e-
wallet's contents (e.g.,
the primary e-wallet, any sub-wallets or secondary wallets, and associated
electronic value tokens
therein). Alternatively, the e-wallet may be used in a system wherein the e-
wallet provider
manages only a portion of the e-wallet's contents (e.g. the primary e-wallet
and electronic value
tokens therein) and delegates the management of one or more (or all) sub-
wallets or secondary
wallets to a third-party's electronic value token transaction processing
system. As will be further
detailed herein, either of the two described management systems may be
configured to allow the
systems' user to fully manage the functionalities of the user's e-wallet;
participate in value
added/bonus programs offered by issuers, vendors, and/or other electronic
value token-related
parties; participate in card exchange activities (e.g., wherein a user
exchanges an electronic value
token maintained in its e-wallet for an electronic value token not in the e-
wallet); and participate in
savings programs offered by issuers, vendors, and/or other electronic value
token-related parties.
[0085] Figure 4A illustrates an exemplary electronic value token
transaction processing system
100. Specifically, Figure 4A illustrates an electronic value token transaction
computer 150
configured for communication with point of sale devices 111, one or more
authorization systems
160 (e.g., retailer, bank, and credit card), and datastore 180. Moreover,
Figure 4A illustrates that
the point of sale devices 1 l 1 are in communication with a proxy card 200
(which will be shown
below to represent an embodiment of a means for a user to access an e-wallet)
and that the
datastore 180 comprises an e-wallet unit 199, which in turn comprises e-
wallets 10.
[0086] Figure 4B illustrates an electronic wallet 10 in accordance with one
embodiment, and it
is to be understood that the details of e-wallet 10 may be employed in any of
the various
embodiments disclosed herein (e.g., as e-wallet 10 of Figs. 4A, 5A, and 5B)
and the maintenance
of said e-wallet 10 may be wholly performed by a single e-wallet system (e.g.,
electronic value
33
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
token transaction processing system 100) or may distributed across multiple e-
wallet systems (e.g.,
electronic value token transaction processing systems 1100 and 1200 and E-
Wallet Aggregator
System 1000). Specifically, Figure 4B illustrates an electronic wallet 10
comprising authentication
information 801, rules 802, electronic value tokens 804, sub-wallet 807 for
credit card electronic
value tokens, sub-wallet (with corresponding rules 817 and electronic value
tokens 827), sub-
wallet 808 for debit card electronic value tokens (with corresponding rules
818 and electronic
value tokens 828), and sub-wallet 809 for stored-value card electronic value
tokens (with
corresponding rules 819 and electronic value tokens 829). Figures 4A and 4B
may be further
understood from the below discussion.
[0087] In order to eliminate the increasing complexity in organization,
transport, security, and
redemption, transaction cards are stored electronically as value tokens in
electronic wallets. As
used herein, a value token refers to an electronic identifier that may be used
to transact business
with a party willing to accept the electronic value token, for example as
tender for a purchase.
Examples of such value tokens include electronic representations of, or
associated with, stored
value cards (also referred to as prepaid cards) and other physical
representations of value of a
variety of types such as credit cards, debit cards, gift cards, prepaid
telephone cards, loyalty cards,
membership cards, tickets or ticket cards, entertainment cards, sports cards,
prepaid cards,
coupons, admission passes, prepaid or pre-purchased goods or services, and the
like. In an
embodiment, a value token includes cash or currency. In an embodiment, the
electronic value
token includes a credit or debit card or account. In an embodiment, a value
token includes a
preexisting account such as a merchant account, bank account, etc. In an
embodiment, a value
token includes a merchant-issued and/or accepted credit, points, coupon or
promotional value. In
an embodiment, a value token is associated with a prepaid card or account, and
unless otherwise
indicated it is to be understood that the various embodiments described herein
may be carried out
in the context of a prepaid card or account such as a merchant gift card.
[0088] A physical credit card, debit card, stored-value card, or other
physical representations
of value may be converted into a value token to be added to the electronic
wallet. For example,
physical gift cards or other physical representations of value may be
transformed into value tokens
in a user's electronic wallet via a point-of-sale device, cellular phone, a
computer, short messaging
service ("SMS"), and the like. Once so transformed, the electronic value
tokens may be redeemed
by the user, after authentication, without possession of the physical
representation such as gift
34
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
cards by accessing the user's electronic wallet during purchase. In this way,
the use of the term
value token herein refers to electronic representations and physical
representations that can be
transformed into electronic representations. In at least one embodiment, the
physical gift card is
inoperative after transformation. In an alternative embodiment, the physical
gift card is inoperative
after redemption of the electronic value token using the electronic wallet or
the physical gift card
[0089] Consumer use of value tokens typically involves a vendor, a
redeeming merchant or
retailer, and an issuer. In various embodiments, the vendor, redeeming
merchant, and issuer may
be the same, different, or related entities. The point of sale where value
tokens are purchased or
otherwise made available for inclusion in an electronic wallet may be referred
to as the vendor.
Thus, the vendor sells the electronic value tokens themselves although the
electronic value tokens
may be redeemed at another place of business. An entity that will accept a
value token for
business transactions, for example as tender for a purchase, may be referred
to as a redeeming
merchant or retailer. For example, a grocery store may sell the electronic
value token of an apparel
store. The grocery store is the vendor and the apparel store is the redeeming
merchant or retailer.
An entity that provides the financial backing and/or payment processing for a
given value token
such as a prepaid card or account may be referred to as the issuer. Issuers
include direct issuers of
value tokens such as store-branded value tokens (e.g., store branded prepaid
cards or tokens issued
directly by the merchant, sometimes referred to as closed-loop prepaid cards),
and in some
embodiments the vendor may also be the issuer and/or the redeeming merchant
(e.g., a prepaid
card or token issued, sold, and redeemed by the same merchant). Issuers also
include financial
institutions such as banks, VISA, MasterCard, American Express, etc., and
value tokens issued by
such institutions may be readily accepted by a number of redeeming merchants
to conduct
transactions such as purchases (sometimes referred to as open loop prepaid
cards or tokens since
they may be redeemed at a number of different merchants). Issuers may also be
the providers of
branded electronic wallets such as Google, Facebook, Twitter, and the like,
and in some
embodiments such branded wallet contains value tokens associated with the
issuer (e.g., Google
"cash" or credits, Pay Pal currency, Facebook electronic currency, etc.) and
may contain or be
associated with a sub-wallet containing gift card-related value tokens, a sub-
wallet containing
credit card-related value tokens, a sub-wallet containing debit card-related
value tokens, or a
combination thereof.
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[0090] Generally, an electronic value token transaction computer 150
credits or debits (or takes
other actions of the type described herein) the accounts associated with the
electronic value tokens
contained within an electronic wallet or sub-wallet. The electronic value
token transaction
computer 150 may generate or forward messages to authorization systems 160 so
that the
authorization systems 160 can credit or debit (or take other action of the
type described herein) the
accounts associated with the electronic value tokens. Confirmation messages
are returned to the
electronic value token transaction computer 150 and POS device 111, and the
electronic wallet 10
or a sub-wallet is updated as necessary.
100911 In at least one embodiment, transaction information is separate from
authentication
information. For example, information about a purchase item, purchase price,
purchase location,
etc. is considered transaction information and is separate from authentication
information such as
an authentication token, PIN, account number, etc. Among other things, keeping
the information
separate allows for separate processing and routing, allowing for greater
efficiency and privacy.
For example, in applying the electronic value tokens according to the
configurable rule, the priority
may be based on a transaction information variables such as physical location
of a retailer
originating the electronic wallet request; transaction amount; type of
retailer; time of day; day of
week; week of month; month of year; department of retailer originating the
electronic wallet
request; lane of retailer originating the electronic wallet request;
identification of checker; parent
company of a retailer originating the electronic wallet request; value of
value tokens; and type of
the electronic wallet request in various embodiments. Such transaction and/or
authentication
information may be used by the systems described herein in conjunction with
rules based decision
making (e.g., checking such transaction data to validate and apply a promotion
associated with the
transaction), for security purposes (e.g., checking such transaction data
against pre-determined
profiles to assist with fraud detection), and the like.
[0092] In at least one embodiment, the wallet provider stands in for the
purchaser, and
redemption of the electronic value token occurs after the purchase. However,
this time mismatch
creates a discrepancy in the retailer's records. Specifically, the retailer
records a transaction
between the retailer and the wallet provider. The retailer records a later
redemption via value
token, seemingly for no purchase. In these instances, a third party
administrator is required that
can connect the redemption with the transaction.
36
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[0093] There can be many ways to provision or add value tokens to an
electronic wallet. For
example, a user may pay the vendor for a value token, and the vendor may
insert the electronic
value token into the user's wallet. Alternatively, the user may obtain a
physical representation of
the electronic value token from the vendor (e.2., a card, chit, printed
receipt, etc.) and may
subsequently add the value to the electronic wallet (for example, via a phone
or internet accessed
user interface). The user may have a choice of many different retailers
affiliated with the vendor.
In other words, a given vendor may offer a plurality of tokens associated with
different retailers.
For example, a retailer may offer promotions to compete for the user's
business when purchasing a
value token such as a prepaid account.
[0094] Each retailer may mandate a specific format for value tokens. For
example, one retailer
may require a 16 digit card number plus a 4 digit month/year expiration date.
Other retailers may
require pin numbers, access numbers, card verification value numbers, card
security code numbers,
and the like. Each piece of information for different retailers may have a
different format as well
as a different name. As such, an electronic wallet provider or host (for
example, a primary e-wallet
provider) would benefit by allowing third party administration for electronic
representations of
value tokens have a variety of formats such as stored value cards, credit
cards, debit cards, loyalty
and promotion cards, and other subsets of value tokens for which
administration by the primary e-
wallet provider would be more expensive.
[0095] In an embodiment, value tokens associated with prepaid cards or
accounts may be
associated with a sub-wallet within the electronic wallet (for example, a sub-
wallet of a primary,
branded electronic wallet such as a Google electronic wallet), and a third
party may administer the
sub-wallet on behalf of the primary/principal electronic wallet host or
provider. For example,
during a transaction involving value tokens associated with prepaid cards or
accounts (e.g.,
electronic or virtual stored value cards), the provider of the electronic
wallet allows a sub-wallet
associated with such value tokens to take control of a portion of the
transaction, sometimes referred
to as a sub-transaction. In an embodiment, a sub-transaction comprises a
transaction associated
with an electronic prepaid card or account such as redemption, value addition
(e.g., topping up),
activation, closure, fraud detection, etc. Specifically, the third party
administrator can quickly and
cheaply administer the transaction, including but not limited to determining
and/or providing the
proper formatting for the sub-transaction, and further execute the sub-
transaction independently
and/or in cooperation with the primary electronic wallet host or provider.
Such formatting may
37
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
relate to the particulars of information/data contained upon or associated
with a given value token
(e.g., type of card number, security code, etc.) and/or the formatting of
information or data
associated with a particular transaction (e.g., the characteristics,
organization, packaging, etc. of
data such as card type, transaction type, security code, etc. into messaging
fields or other data
formats for receipt/transmission while processing a transaction). For example,
the third party
administration can pass the proper transaction formatting template to the
primary wallet provider.
In at least one embodiment, the third party administrator determines from the
request, or requests
from the user, the identity of the retailer associated with the transaction.
Preferably, the third party
administrator maintains a database of a plurality of transaction formats
associated with a plurality
of retailers. After determining the identity of the retailer associated with
the transaction, the third
party administrator identifies the associated transaction format for the
identified retailer using the
format database and all subsequent processing is performed using the retailer-
specific transaction
format and vocabulary. In an embodiment, a user may wish to add a value token
to an electronic
wallet using a physical stored value card. The user is requested to identify
the retailer associated
with the stored value card, for example via a user interface located at a
point of sale (including, in
an embodiment, a point of sale associated with a personal computer such as on-
line shopping via
websites). In another embodiment, the user provides information associated
with the stored value
token via a web-based or personal digital assistant interface (e.g., a mobile
phone app).
Accordingly, based upon the user provided data, the appropriate format may be
referenced from
the database and the user may be shown a pictorial representation or other
mockup representation
of the physical stored value card with the specific input information
highlighted on the mockup.
As such, the user knows exactly which inputs are required to add the
electronic value token to the
electronic wallet. I he user inputted information derived from the mockup will
be in the proper
format and/or may be further modified, packaged, etc. by the third party
administrator to meet
further formatting requirements. While the example described is simple, more
complex
transactions are also possible. As will be described more fully herein,
transactions relating to (i)
using value tokens in primary and/or sub-wallets for portions of transactions
is similarly handled as
is (ii) exchanging value tokens in primary and/or sub-wallets for other types
of value tokens or
value tokens associated with other retailers. For example, a user may wish to
exchange a value
token associated with a retailer the user does not frequent for a value token
associated with a
retailer that the user does frequent. Moreover, the third party administrator
may use the transaction
38
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
format associated with the identified retailer for financial reconciliation of
the transaction or sub-
transaction (e.g., debiting and crediting a prepaid account). In this
instance, use of the proper
transaction format is not only convenient but often required.
[0096] As indicated above, an electronic sub-wallet is a specifically
defined portion of an e-
wallet located in or associated with a specific e-wallet (e.g., a primary or
principal wallet). A sub-
wallet may be administered/maintained by the primary or principal e-wallet's
administrator,
processor, and/or provider or may be administered by another party, system,
processor, subroutine,
or server. The separate administration of the electronic sub-wallet allows the
primary e-wallet
provider and user to take advantage of economies of scale. For example, all
electronic value
tokens may be stored in one sub-wallet while credit and debit cards are stored
in the primary e-
wallet or a separate electronic sub-wallet. As such, the provider of the
primary e-wallet may
administrate/perform transactions concerning value tokens associated with
credit and debit cards
residing in the primary e-wallet while allowing a third party to
administrate/perform transactions
concerning value tokens associated with electronic value tokens residing in an
electronic sub-
wallet, freeing the third party from costly banking and credit regulations.
Moreover, the third party
administrator may use the economies of scale to receive payment for its
services via arbitrage,
commission, pay per transaction, or the like.
[0097] Via the separate administration of a sub-wallet, the third party
administrator (e.g.,
administrator of an electronic sub-wallet associated with electronic prepaid
accounts) provides
convenience to both the user and the primary electronic wallet provider.
Often, the third party
administrator is the only entity with the knowledge and expertise (e.g., a
database of required
transaction formats) to process financial reconciliations or other
transactions associated with an
electronic prepaid account associated with a given issuer. For example, a
third party administrator
may be the only entity capable of matching a particular transaction on the
retailer's book to a
particular use of a value token or electronic wallet. As discussed in more
detail herein, in some
embodiments, the third party administrator carries out, implements, and/or is
responsible for all or
a portion of the functionality described in conjunction with the electronic
value token transaction
computer 150, for example in the context of administering one or more
electronic sub-wallets (e.g.,
an electronic sub-wallet associated with electronic prepaid accounts such as
closed loop accounts
issued on behalf of one or more merchants) for the primary host or provider of
an electronic wallet
such as a branded electronic wallet.
39
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[0098] Access to the electronic wallet may be gated or protected by an
authentication token or
other means for securely accessing an electronic wallet, examples of which
include a proxy card or
a personal digital assistant or mobile device such as a smart phone. Other
embodiments for access
to the electronic wallet include cardless access such as a number/password
combination, a number
without a password, and the like. Biometric information may also be used for
authentication and
access purposes, e.g. a fingerprint or iris print. Near field communication
technology may also be
used to implement authentication tokens. Near field communication technology
may be
implemented at a physical point of sale or in association with an online
transaction. In either
context, the near field communication technology may be implemented by a user
via a proxy card
(e.g., 200, 201, or 203), personal computer, personal digital assistant, smart
phone 204, or other
online transaction-related device. Thus, the authentication token may be
tangible, intangible, or a
combination thereof. In an embodiment, the authentication token may be
generated, created,
and/or formed at the initiation of an electronic transaction to uniquely
identify the electronic
transaction. In an embodiment, the uniquely generated authentication token may
comprise
elements of an electronic wallet identifier, a merchant identifier, a point of
sale identifier, an
electronic value token identifier, an electronic value token issuer
identifier, an electronic value
token transaction processor identifier, or combinations thereof. In another
embodiment, the
uniquely generated authentication token may be wholly unique and not comprise
any portion of
any previous identifier.
[0099] Examples of proxy cards are depicted in Figures 6A, 6B, and 6C.
Figure 6A depicts a
proxy card 200 in which the authentication information 211 is encoded on the
card 200 by means
of a bar code capable of being read by an optical scanner. Figure 6B depicts a
proxy card 201 in
which the authentication information 211 is encoded on a magnetic strip
located on the card 201.
Figure 6B depicts a proxy card 203 in which the authentication information 211
is encoded on a
near field communication chip on the card 201. In some embodiments, the proxy
card may have a
magnetic strip and a bar code (or a plurality of magnetic strips and/or bar
codes), and one or more
of such may contain the authentication information 211. The proxy cards 200,
201, and 203 are
fabricated from a suitable first material, such as plastic, paper, a plastic-
coated paper, laminates, or
combinations thereof. The proxy cards 200, 201, and 203 are typically made in
a thickness range
of from about 0.005 to about 0.040 inch. The proxy cards 200, 201, and 203
each bear
authentication information 211, for example an account number, serial number,
authorization code,
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
digital signature, electronic key or key code, RFID chip/data, etc.
corresponding to an e-wallet.
The proxy card authentication information 211 is unique to the proxy card and
associates the proxy
card to an electronic wallet, and in an embodiment such association is stored
in a database
accessible by an administrator of the e-wallet. The authentication information
211 may be encoded
in a bar code as depicted in Figure 6A on proxy card 200, a magnetic strip as
depicted in Figure 6B
on proxy card 201, a near field communication chip as depicted in Figure 6C on
proxy card 203, a
series of numerals, a series of letters, or a combination thereof The proxy
cards 200, 201, and 203
may also be fashioned with personal identification numbers, or PlNs, to be
entered during the
course of the transaction, that correspond to the authentication information
211 and allows access
and/or use of the electronic wallet. In an embodiment, the PIN may be encoded
in a bar code, a
magnetic strip, a series of numeral, a series of letters, or a combination
thereof. In an embodiment,
the PIN may be obscured from view by packaging, by an obscuring material such
as a scratch-off
strip or peel-off label, or combinations thereof. In some embodiments, the
proxy card may
comprise a card security code (CSC), a card verification value (CVV or CV2), a
card verification
value code (CVVC), card verification code (CVC), verification code (V-code or
V code), card
code verification (CCV), credit card ID (CCID), or combinations thereof, and
such codes (along
with any other authentication data or token described herein) may be employed
in an authorization
or authentication transaction, for example initiated at a point of sale in
conjunction with an e-wallet
payment for a purchase transaction.
[00100] Figure 6B depicts a proxy card 201 in which the authentication
information 211 is
encoded on a magnetic strip located on the card 201. The magnetic strip may be
made
conventional construction, such as one deposited from a slurry, positioned on
the card 201 so that it
can be scanned in magnetic strip reading equipment such as a 1 ranz terminal
made by Verifone.
For additional security, the authentication information 211 may also be
subjected to an encryption
algorithm prior to encoding on the magnetic strip.
[00101] In at least one embodiment, the proxy card 200 comprises a bar code,
such as a UPC
code (e.g., a GS1-128 or UCC/EAN-128), positioned on the proxy card 201 so
that it can be
scanned by well-known bar code reading equipment. Encoded in the bar code on
the proxy card is
a representation of the authentication information 211.
[00102] In other embodiments, series of numerals, series of letters, or
combinations thereof,
may be placed on the proxy cards 200 and 201 to be read or interpreted by a
human or a device, i.e.
41
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
optical character recognition device, configured to interpret a series of
shapes corresponding to the
package identifier. Any suitable authentication token as described herein such
as virtual or
cardless authentication tokens, mobile phones, etc. may be employed in the
various embodiments
described herein.
[00103] In
further embodiments, e.g., proxy card 203, near field communication
technology,
radio frequency identification (RFID) tags, microprocessors, and/or microchips
may be placed on
the proxy card to be interpreted by specifically configured devices. The
RFID tags,
microprocessors, and/or microchips may be used in addition to or in place of
the bar code 255 on
proxy card 200 and magnetic strip 256 on proxy card 201, or may be used in
combination with
these or other means of encoding the authentication information on the proxy
card. Alternatively,
such RFID or other means such as near field, Bluetooth, etc. may be employed
by a user operated
device (e.g., a personal digital assistant such as a smart phone) to provide
electronic wallet access
and/or authorization functionality. In an embodiment, the authentication token
is associated with a
personal digital assistant such as a smart phone 204, as depicted in Figure
6D. For example, an
electronic wallet stored in and/or accessed via a phone may include an
authentication token, or the
phone itself may contain hardware and/or unique electronic data (e.g.,
authentication data such as
serial number, MAC address, SIM card, digital signature, electronic key, user
ID, phone number,
passcode, etc.) that serves as the authentication token. Such a phone may use
near field
communication to communicate data associated with the authentication token
with a point of sale
device for authentication and transaction purposes. For example, the phone may
be passed near the
point of sale device and transfer user and/or wallet information and
authentication information to
the point of sale device using near field communication protocol. The phone
may transfer all or a
portion of the wallet and/or authentication information, leaving the point of
sale device to
determine which portions are applicable to the current transaction, or the
phone may transfer only
presently applicable portions of information, i.e. information to be used
during the current
transaction, to the point of sale device. That is, logic as to the transfer of
wallet and/or
authentication information to/from the authentication token (e.g., phone) and
the point of sale
device may reside on the authentication device, on the point of sale device,
or both. In an
embodiment, the phone may provide hardware and/or software for authenticating
a user, for
example a camera or scanner and associated application for confirming
biometric data associated
with the user, and upon authenticating the user, the phone would convey the
successful
42
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
authentication to the point of sale device. The point of sale device may
communicate with the
wallet host or provider (e.g., a primary e-wallet host) and any sub-wallet
hosts or providers, e.g.,
third party administrators. In another example, the point of sale device may
communicate with
only the wallet host or provider (e.g., a primary e-wallet host), and the
wallet host or provider may
communicate with third party administrators, for example a sub-wallet host or
administrator.
Despite multiple configurations to enable communication, the transaction may
still occur in real
time with no delay to the customer because the parties use scalable
architecture.
[00104] In an embodiment, the authentication device is a proxy card.
Although a proxy card is
not a physical card, the proxy card's similar appearance to a credit card,
debit card, and/or stored-
value card will help adoption of and access to electronic wallets because
consumers know how to
use electronic value tokens. As such, consumers may come to think of proxy
cards as multiple
cards rolled into one or simply think of a proxy card as an electronic wallet
itself, despite being a
physical representation. Authentication tokens may take and/or be associated
with tangible or
intangible embodiments such as a mobile device, a personal identification
number, a phone number
plus a personal identification number, a password, a username plus password,
biometric identifier,
and the like. Authentication tokens contain, provide and/or are associated
with authentication
information (e.g., electronic authentication data or information), which
associates a user with an
electronic wallet. As such, multiple value tokens contained in the electronic
wallet (or a sub-wallet
thereof) are associated with the user.
[00105] Returning to Figure 4A, an electronic value token transaction
computer 150 accesses
electronic wallets 10 from datastore 180. The prepaid or stored value card
electronic value tokens
may include electronic representations of gift cards, loyalty cards,
promotions, and the like. The
POS device 111 obtains authentication information from an e-wallet user via an
authentication
token such as a smart phone or the proxy card 200 and sends the authentication
information (and is
some instances, rules for allocating the contents of the e-wallet for the
requested transaction) to the
electronic value token transaction computer 150 along with purchase
information and/or value
token information as part of a transaction request. The electronic value token
transaction computer
150 uses the authentication information to locate the correct electronic
wallet 10 or sub-wallet in
the datastore 180 and acts upon the electronic value token (e.g., adds a value
token to a primary
wallet or sub-wallet, activates a value token, debits a value token, tops-off
a value token, checks
the balance of a value token, etc.) or examines rules (received with the
request, associated with the
43
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
e-wallet by the electronic value token transaction processing system 100,
1100, 1200, or a
combination thereof) in light of the request's information. For example, for a
purchase transaction
the electronic value token transaction computer 150 selects the electronic
value tokens that cover
the purchase based on the rules, for example rules associated with the order
or priority in which to
apply or redeem value tokens to cover the purchase price.
[00106] As shown in Figures 5A and 5B, the electronic value token transaction
computer 150
comprises a rules unit 159. The rules unit 159 provides processing,
management, associating, and
implementing functionalities for e-wallet (and sub-wallet) rules as provided,
selected, and/or
required by e-wallet users, e-wallet providers, e-wallet accepting merchants,
electronic value token
issuers, e-wallet transaction system administrators, and combinations thereof
The rules unit 159
may function to associate provided, selected, and/or required rules with e-
wallets and sub-wallets
maintained in the database 180 and/or e-wallet unit 199. The rules unit 159
may comprise a rules
engine for deriving rules to be applied to a transaction in the absence of (or
in place of) any
particular rule provided or selected by any other rule assigning entity. The
rules unit 159 may
provide for e-wallet/sub-wallet rules data to be populated via (i) e-wallet
user input (e.g., via kiosk,
smart phone, personal digital assistant, and internet accessible user
interface); e-wallet provider
input; (iii) e-wallet system administrator's input; (iv) or any combination
thereof For example, an
e-wallet user may, via kiosk 189 interfacing, provide the electronic value
token transaction
computer 150 with specific, customized rules detailing the manner in which
electronic value
tokens contained in the e-wallet should be prioritized for use in satisfying
transactions.
Alternatively, the same e-wallet user could simply select the types of rules
applicable to the e-
wallet from a list of options provided by the kiosk's 189 display. In
addition, there may be
instances, e.g., in a savings context, wherein certain laws, regulations,
and/or policies require that
an e-wallet be limited to a given number of selected transactions per period
(e.g., transfers from a
savings-dedicated e-wall et).
[00107] In an embodiment, the rules can be created and configured by the user
as a flowchart
for selection of value tokens based on purchase information. For example, a
rule may comprise
selection of a closed loop-related (Store X branded) value token for a Store X
purchase of any
amount, with any remaining purchase balance to result in selection of an open
loop-related (Credit
Card Y) value token to fund such remainder. Alternatively, the user may invoke
a rule that
prescribes that open loop-related electronic value tokens should not be used
to satisfy balances for
44
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
closed loop-related electronic value token purchase, but rather debit card-
related electronic value
tokens residing in the e-wallet should be utilized to satisfy the balance
instead. As such, a user
may access and apply multiple value tokens with the efficiency of using one
authentication token
(e.g., one proxy card or smart phone). For example, the user may use an
electronic gift card, an
electronic coupon, and two electronic credit cards from an electronic wallet
or sub-wallet all in the
time it takes to use only one physical card such as a prepaid, debit, or
credit card. The user, the
retailer, issuers, vendors, merchants, advertisers, and other parties benefit
from the time saved, the
ready access to multiple sources of value (e.g., multiple accounts associated
with the various value
tokens), promotional opportunities, transaction tracking and data mining
regarding customer
purchasing behavior, promotional and advertising efficacy, real-time/point of
product selection or
purchase promotional opportunities, etc.
[00108] In another embodiment, the rules may be established by the e-wallet
system provider
(e.g., a primary and/or secondary e-wallet provider or host). The e-wallet
system provider may
establish a rule concerning e-wallet allocations when there is no user
established rule available (or
if under the terms of a user's e-wallet use agreement the system's rules take
precedent in
designated transaction activities). For example, the e-wallet system may put a
rule in place that
directs the electronic value token transaction computer 150 to first apply an
e-wallet system
provider's own branded electronic value token residing in the user's e-wallet
to satisfy the
requested transaction when the transaction concerns, relates, or involves an
affiliate and/or
contractually-related entity of the e-wallet system provider. As such, this
type of rule could allow
for the e-wallet system provider and its affiliates and/or contractually-
related entities to maximize
revenues or other business objectives based on use of the e-wallet system and
other synergistic
effects.
[00109] In a further embodiment, the e-wallet's rules may be fashioned to
automatically direct
electronic value token exchange activities (electronic value token exchange
will be discussed in
more complete detail herein). For example, the e-wallet user may manage the e-
wallet (as will be
described in more detail herein, e.g., in relation to Figures 9A-D) so that
upon the occasion when
the user presents the e-wallet to satisfy a transaction at retail
establishment, e.g., Retailer Q, and the
e-wallet contains no Retailer Q branded electronic value tokens, the e-wallet
will automatically,
and in real time, initiates an electronic value token exchange process wherein
the e-wallet
communicates a request for electronic value token exchange to the electronic
value token
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
transaction computer 150. Additionally or alternatively, the user may be
presented in real-time
with a promotion to obtain a retailer-specific value token (e.g., a real-time
offer for a store branded
value token such as a credit account). In this example, the e-wallet user may
mange the e-wallet so
that all electronic value tokens associated with prepaid services (gift card-
type electronic value
tokens) are located in a designated sub-wallet and each of said electronic
value tokens may be
placed/ordered/designated in the sub-wallet via a preferential ranking system,
e.g., most preferred
electronic value token or token type (e.g., #1) to least preferred electronic
value token or token type
(e.g., #22, if there are 22 types of electronic value tokens in the sub-
wallet). For example, Retailer
M branded electronic value tokens may be designated as most preferred and
Retailer L branded
electronic value tokens may be designated as least preferred. Further in the
example, the e-wallet
also has been provided with rules by the user that directs the e-wallet, in
circumstances wherein the
e-wallet has been presented to facilitate a transaction at a retailer in which
the e-wallet contains
none of said retailer's electronic value tokens (the e-wallet will recognize
the retailer based on
information exchanged between the e-wallet and the retailer's communication
devices at the onset
of the original transaction), such as the Retailer Q scenario described above,
the e-wallet rules
direct the e-wallet to initiate an electronic value token exchange request and
to include in said
request the exchange of the least preferred electronic value token residing in
the e-wallet, i.e., the
Retailer L branded electronic value token (#22) and if necessary preferred
electronic value token
#21, #20, etc., for a Retailer Q electronic value token in an amount
sufficient to meet the original
transaction's amount. The electronic value token transaction computer 150,
upon receipt of the
electronic value token exchange request, communicates with an electronic value
token exchange
program 2000 (which is part of the overall electronic value token transaction
processing system
100, 1100, or 1200) to effectuate the requested electronic value token
exchange. The requested
electronic value token exchange is performed, the e-wallet receives the
requested Retailer Q
branded electronic value token, which is coincidentally used in conducting the
original transaction,
and the e-wallet surrenders (or makes unavailable for use and only available
for modification) the
Retailer L branded electronic value token to the electronic value token
transaction computer 150,
which in this case was actually valued in excess of the requested Retailer Q
branded electronic
value token. As such, the electronic value token transaction computer 150,
modifies the value of
the Retailer L branded electronic value token (either internally or via
communication with the
Retailer L branded electronic value token's issuing system) to reflect the
value reduction based on
46
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
the provided Retailer Q branded electronic value token, extracts the exchange
rate for the exchange
of the Retailer Q branded electronic value token for the Retailer L branded
electronic value token
(as will be discussed more fully herein), communicates the transactional
information to all
interested parties, and returns (or makes available again) the value-modified
Retailer L branded
value token to the user's e-wallet. In an alternate embodiment, the e-wallet's
electronic value
token exchange rules could have provided that the e-wallet query the
electronic value token
transaction computer 150 regarding the best available exchange rate for the
electronic value tokens
residing in the e-wallet and make the exchange based on the best exchange rate
rather than the
ranking of the electronic value tokens.
[00110] Figure 5A illustrates an exemplary electronic value token
transaction processing system
100 in accordance with one embodiment. As shown, the electronic value token
transaction
processing system comprises: (a) at least one point of sale device 111; (b) an
electronic wallet
processing system, e.g., electronic value token transaction computer 150; (c)
a datastore 180
containing an electronic wallet unit 199 storing electronic value tokens,
e.g., 804, 827, 828, and
829, such as account numbers, electronic wallet account information, value
added award
conditions (herein "value added award" is synonymous with "value added bonus,"
"value added
bonus award," "value added award bonus," and "value differentiation"), and
other information
related to adding, redeeming, and managing the electronic value tokens; (d) at
least one individual
issuers' authorization system 160; and (e) any other unit included in the
system by the electronic
value token transaction computer administrator 151. In one embodiment, the
electronic value
token transaction computer 150 comprises a value added determination unit 153,
a point-of-sale
("PUS") interface 152, a message modification unit 154, a reconciliation unit
155, an issuer system
interface 156, an authorization unit 157, and a sorting unit 198. In an
embodiment, the electronic
value token transaction computer 150 (or a unit thereof such as sorting unit
189) further comprises
token exchange interface, which may communicate with electronic value token
exchange program
2000. The PUS Interface 152 provides a means for the electronic value token
transaction computer
150 to communicate with the point of sale device 111 via, for example, the
Internet, a Public
Switched Telephone Network ("PSTN"), or an independent dedicated network.
Likewise, the
electronic value token transaction computer 150 may communicate via issuer
system interface 156
with the issuers' authorization system 160 via, for example, the Internet, a
Public Switched
Telephone Network (PSTN), or an independent dedicated network. Communications
106, 107
47
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
between the POS interface 152 and the point of sale device 111 and
communications 109, 110
between the issuer system interface 156 and the issuers' authorization systems
160 may be
encrypted for added security and/or may utilize a virtual private network
("VP1\1"). The sorting
unit 198 may sort the communications into various types for routing in various
ways. For
example, the sorting unit 198 may identify and sort electronic wallet and/or
sub-wallet requests
(e.g., upon receipt of authorization information with a transaction request,
the sorting unit 198 can
route the requested transaction to a specific electronic wallet maintained by
the system and/or to a
specific sub-wallet or sub-wallets associated with an electronic wallet),
balance inquiry requests,
registration requests, activation requests, redemption requests, and
management requests for
routing to the various units of Figure 5A. The electronic value token
transaction computer 150 or
sorting unit 198 may also generate messages based on the requests for similar
routing.
[00111] As can be seen in Figure 5A, at the point of sale device 111
(typically located at a
vendor and/or redeeming merchant or retailer, but alternatively located at a
kiosk 189 or at a user's
home or office where a personal computer is configured to act as a point of
sale, for example
during an on-line transaction), the authentication token is interpreted by a
point of sale
interpretation unit 101 (e.g., a card reader). The point of sale
interpretation unit 101 can comprise
a human, a bar code scanner, magnetic strip reader, optical character
recognition device, biometric
device, numerical keyboard (e.g., for entering a token identification number)
or other device
configured to interrogate, interpret, capture, or input the data encoded in or
on the authentication
token.
[00112] About contemporaneously with (or, alternatively, prior or
subsequent to) the
interpretation of the authentication token, a request for an electronic wallet
transaction by a point
of sale transaction unit 104 is made. the point of sale transaction unit 104
can comprise a human,
an electronic input device, a register or terminal, a computer processing unit
("CPU"), a personal
computer, a personal digital assistant (e.g., smart phone) or other means of
requesting or messaging
interpreted by the point of sale interpretation unit 101 and/or point of sale
processing unit 105. In
some embodiments, the actions performed by the point of sale interpretation
unit 101 and the point
of sale transaction unit 104 may be performed by one unit capable of
performing both actions that
would be performed by the individual units, for example a point of sale
register/terminal or a
personal computer during an on-line, web-based transaction.
48
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00113] The point of sale interpretation unit 101 and the point of sale
transaction unit 104
communicate with the point of sale processing unit 105. The point of sale
processing unit 105 can
comprise a CPU or other type of processing device accepted for use in the
industry. The point of
sale interpretation unit 101 communicates authentication information 102 to
the point of sale
processing unit 105. The point of sale transaction unit 104 communicates the
request 103 for an
electronic wallet transaction to the point of sale processing unit 105. The
point of sale processing
unit 105 may combine this information to communicate with the electronic value
token transaction
computer 150 (e.g., transmits a message requesting an electronic wallet
transaction along with the
associated transaction and/or authentication data). In an embodiment, the
point of sale processing
unit 105 stores and/or receives from the electronic value token transaction
computer 150 (or a sub-
administrator or unit associated therewith, such as a sub-wallet
administrator) a transaction format
associated with the POS retailer and/or associated with a given transaction
type and/or value token,
and such transaction format may be used to format the transaction request or
message, to prompt
the user for further information, or for other data gathering or
transmit/receive features at the point
of sale. For example, a user making a purchase at a retailer operates a card
reader. A card reader
may a display with an input device and a barcode reader or magnetic strip
scanner. The card
reader may be touch sensitive and may have various buttons used for input.
Following the card
reader prompts, the user sees the options "Debit," "Credit," and "E-Wallet."
The user selects "E-
Wallet." The user then sees the options "Purchase," "Add Token," and "Delete
Token." The user
selects "Purchase." Following additional prompts (which in an embodiment
relate to a transaction
format specific to the particular retailer of the point of sale), the user
enters a PIN number. In some
embodiments, the actions performed by the point of sale interpretation unit
101, the point of sale
transaction unit 104, and the point of sale processing unit 105 may all be
performed by one unit
(e.g., an integrated POS device such as a computerized register) capable of
performing all the
actions that would be performed by the individual units.
[00114] The point of sale processing unit 105 is connectable to the
electronic value token
transaction computer 150 via a suitable network, such as the Internet, the
public switched
telephone network (PSTN), or an independent dedicated network. Each point of
sale processing
unit 105 has an associated identifier (e.g., a terminal identifier or serial
number) that may be
transmitted to the electronic value token transaction computer 150 during the
course of connecting
the point of sale processing unit 105 to the electronic value token
transaction computer 150. Each
49
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
point of sale processing unit 105 may include multiple point of sale
transaction units corresponding
to individual terminals each with its own terminal identification, for example
present within a
given store location.
[00115] As depicted in Figure 5A, the electronic value token transaction
computer 150 is
configured to: (a) form a secure connection with the retailer/merchant and/or
vendor (e.g., via the
point of sale device 111, customer internet access, or kiosk 189), the
issuers' authorization systems
160, and any other entities 190 authorized to access the electronic value
token transaction
computer 150 by the electronic value token transaction computer administrator
151; (b) to
communicate with issuers' authorization systems 160 to request and receive
redemption or
addition of value tokens into electronic wallets; (c) to communicate with
issuers' authorization
systems 160 to redeem all or a portion of the electronic value tokens
associated with the electronic
wallet; (d) generate and maintain a transaction log 170 of all activities
performed; (e) generate and
maintain an error log 175 of all activities unsuccessfully completed and
reasons therefore; (f)
communicate to the retailer/merchant and/or vendor (e.g., via the POS unit
111) the redemption or
addition of value tokens into electronic wallets and any information
concomitant with the
redemption or addition of value tokens into electronic wallets; and (g)
communicate to the
retailer/merchant and/or vendor (e.g., via the POS unit 111) any reasons why
transactions cannot
not be completed.
[00116] The electronic value token transaction computer 150 may comprise a
singular
processing unit (e.g., a centralized server), a plurality of processing units
(e.g., a distributed
computing system with various units distributed and in communication with each
other), or
combinations thereof, with concomitant storage capabilities, each capable of
or designated for:
accessing the datastore 180; creating a transaction log 170; creating and
maintaining an error log
175; communicating with retailers/merchants and/or vendors, e.g., at a point
of sale, including via
the internet for on-line transactions; communicating with the individual
issuers' authorization
systems 160; processing individual value token and electronic wallet requests;
processing
redemption requests; processing value added functions to add additional cash
value or add an
electronic redemption coupon for a specific product(s) or service(s);
processing redemption request
for electronic redemption coupons for specific product(s) and/or service(s);
and communicating
with other systems 190 capable of and authorized to communicate with the
electronic value token
transaction computer 150.
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00117] Datastore 180 maintains records of accounts associated with each
electronic wallet
indicating: (a) whether each individual value token has been added or
redeemed, (b) whether the
authentication token has been registered, (c) records and details of each
individual redemption
request, (d) the amount remaining on the electronic value tokens, (e) rules
required for redeeming
the electronic value tokens, (f) identity of the issuers of the electronic
value tokens, (f) value added
bonus awards, (g) rules for redeeming value added bonus awards, and (h) any
combination thereof.
The datastore may also maintain records of rules required for granting a value
added bonus award
to an electronic wallet or value token.
[00118] Datastore 180 also maintains records associated with each
electronic wallet and/or sub-
wallet indicating: (a) timing of, and other information related to,
registration activities; (11) timing
of, and other information related to, management activities; (c) timing of,
and other information
related to, transaction activities; (e) rules applicable; (0 identity of the
issuers electronic value
tokens therein; (0 identity of sub-wallets associated therewith; (h) any other
records requested by
issuers, merchants, vendors, advertisers, users, or other interested parties;
and (i) any combination
thereof. While a single datastore 180 is shown, it should be understood that a
plurality of
datastores may be employed, and relevant data divided among the datastores in
any suitable
manner to meet the various processes and objectives described herein. Also,
the various data may
be associated with one or more datastores closely coupled to and/or located in
proximity to one or
more sub-units, sub-processors, third party processors, and the like
associated with the electronic
value token transaction computer 150, and such datastores preferably have data
used by such sub-
units, sub-processors, and third party processors.
[00119] The electronic value token transaction computer 150 is also
configured to generate and
maintain a transaction log 170 of all activity involving the electronic value
token transaction
computer 150. The transaction log may comprise a detailed summary of
transaction types such as:
(a) requested value token additions; (b) requested value token sales; (c)
requested value token
redemptions; (d) requested value token exchanges; (e) the monetary amount
ascribed to value
token additions; (f) the monetary amount ascribed to value token redemptions;
(g) the monetary
value ascribed to value token exchanges; (h) the value added amounts,
products, or services
additions; (i) the value added amounts, products, or services redemptions; (j)
the time the
electronic value tokens were added; (k) the time the electronic value tokens
were redeemed; (1) the
transaction or communication performed with the issuer for adding value
tokens; (m) the
51
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
transaction or communication performed with the issuer for redeeming value
tokens; (n) the PIN
communicated to the vendor in response to a request to add a value token
requiring the input of a
PIN for use; (o) e-wallet registration; (p) e-wallet set-up activities; (q) e-
wallet transaction
activities; (r) e-wallet savings activities; (s) e-wallet management
activities; (t) any other
information the electronic value token transaction computer administrator 151
directs the
electronic value token transaction computer 150 to maintain as a log entry;
and (u) any
combination thereof
1001201 The information contained in the transaction log 170 may be used
for data mining
purposes, e.g., to generate reconciliation reports, settlement reports,
payment reports, audit reports,
e-wallet registration reports, e-wallet management reports, e-wallet usage
reports, e-wallet savings
reports, electronic value token purchase reports, electronic value token
redemption reports,
electronic value token exchange reports, electronic value token sale reports,
or other forms of
information aggregation for the benefit of, use by, or for provision to, the
electronic value token
transaction administrator 151, the datastore administrator 181, vendors,
issuers, issuers'
authorization systems 160, redeeming merchants, or other interested parties.
For example, the
transaction log 170 contains information about each transaction performed by
electronic value
token transaction computer 150 (and any sub-components thereof) and may be
utilized by the
reconciliation unit 155 when reconciling accounts belonging to various
vendors, merchants, issuers
and the electronic value token transaction processing system administrator(s).
Additional data
mining considerations that may be recorded, analyzed, and/or provided
interested parties (e.g.,
vendors, merchants, issuers, advertisers, etc.) include data about: (i) the
purchase habits of e-wallet
users; (ii) electronic value token purchases, sales, redemptions, and
exchanges; (iii), special offer
and/or value added activities; (iv) loyalty-related activities; and (v)
savings-related activities, all of
which can be used for marketing, inventory, and other purposes.
1001211 Oversight and maintenance of the electronic value token transaction
computer is
performed by the electronic value token transaction computer administrator
151. Although not
required, in an alternative embodiment, the electronic value token transaction
computer
administrator 151 may also function as the datastore administrator 181. The
electronic value token
transaction computer 150 is configured to generate and maintain an error log
of all transactions that
were not completed and reasons therefore. In some embodiments, the error log
is administered by
the electronic value token transaction computer administrator 151.
52
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00122] The electronic value token transaction computer 150 is also
configured to communicate
with other entities 190 authorized to access the electronic value token
transaction processing
system and specifically authorized to access the electronic value token
transaction computer 150.
These other entities may comprise third party payment management systems,
third party audit
systems, issuer affiliated entities, vendor affiliated entities, redeeming
merchants or redeeming
merchant affiliated entities, financial institutions such as banks, credit
card agencies, or credit
unions, or any other entity provided access by the electronic value token
transaction computer
administrator 151 or other entity having authority to grant access.
[00123] The transaction request from the point of sale device 111, or other
access point,
associated with an e-wallet may contain one or more of the following pieces of
information: (a)
authentication information, (b) point of sale terminal identification, (c)
amount to be credited or
debited, (d) the time of the request, (e) the date of the request, (f)
identification of the issuer, (g)
identification of the vendor, (h) location of vendor, (i) identification of
the product(s) and/or
service(s) being purchased, (j) an activation or deactivation request, (k) a
wallet management
function such as addition of a value token, deletion of a value token,
exchange of a value token,
changing management or processing rules associated with one or more value
tokens, partitioning a
wallet into sub-wallets or vice-versa, etc., (1) and any combination thereof.
However, the
information contained within the request is not limited to the enumerated list
but may comprise
other items in addition to the items enumerated or in place of the items
enumerated above.
[00124] Upon receipt of the electronic wallet transaction request from the
point of sale, and
identification and sorting as such by the sorting unit 198, the electronic
value token transaction
computer 150 accesses the electronic wallet unit of datastore 180. The
electronic value token
transaction computer 150 processes the information contained in the datastore
180 and
communicates 109, 110 with the individual issuers' authorization systems 160
to effectuate
management of the electronic value tokens and corresponding accounts. The
message
modification unit may adjust the messages and requests so that multiple units,
sub-
components/processors, or third-party administrators can recognize and
correctly interpret the
messages. For example, after the electronic value token transaction computer
150 determines the
individual issuers' authorization systems 160 associated with the request, the
message modification
unit 154 accesses the database 180 to determine the appropriate transaction
messaging formats for
each individual issuers' authorization systems 160 and then formats the
subsequent
53
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
communications to said individual issuers' authorization systems 160 using the
individual issuers'
authorization systems 160 specified/preferred transaction format and
vocabulary. The electronic
value token transaction computer's 150 communication with the individual
issuers' authorization
systems 160 may occur simultaneously or independently. The electronic value
token transaction
computer 150 is connectable to the individual issuers' authorization systems
as via a suitable
network, such as the PSTN, the Internet, or an independent dedicated network.
The electronic
value token transaction computer 150 is configured to send and/or receive
communication 110
from the issuers' authorization systems 160 concerning the status of the
electronic value tokens.
[00125] The reconciliation unit 155 reconciles the accounts of various
issuers, selling vendors,
and/or redeeming merchants, to credit and debit appropriate merchants,
vendors, the electronic
value token transaction processing system administrator, and issuers with the
value of various
transactions to reflect which entities received value from which other
entities. For example, if a
vendor A sells a value token issued by issuer B for a specified amount and
receives payment from
a user who adds the electronic value token to the user's electronic wallet,
the selling vendor
receives a percentage (e.g., retains a percentage) of the purchase amount
and/or a predetermined
amount, the electronic value token system administrator receives a percentage
of the purchase
amount and/or predetermined amount for processing the transaction, and the
issuer receives the
remainder. If a value token issued by issuer Y is redeemed at merchant X to
purchase items, then
the amount redeemed is debited to the issuer Y and credited to the merchant X,
sometimes minus a
transaction fee collected by the issuer and/or a transaction or processing fee
collected by the
electronic value token transaction processing system administrator.
[00126] Authorization unit 157 is utilized when the electronic value token
transaction computer
150 is also the authorizing system such that the electronic value token
transaction computer 150
authorizes electronic wallet requests rather than transmitting the request to
the issuers'
authorization systems 160 for authorization. The authorization unit 157 may
perform the same
and/or different functions as described for authorization systems 160 and vice-
versa.
[00127] The authorization unit 157 will validate the formatting of the e-
wallet transaction
request (e.g., primary or sub-wallet) received from the PUS processor 105 (or
other transaction
originating device/component/processor). In other words, the authorization
unit 157 will check the
data fields in the request to confirm that the fields are populated with data
and that the data is in the
correct format (e.g., length, alphanumeric format). If the request is
improperly formatted, the
54
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
authorization unit 157 will reject the request, or in some embodiments may
retrieve the proper
format (e.g., from a format database) and modify the transaction request to
comply with the proper
format. The authorization unit 157 also performs various validation checks on
the request. The
authorization unit 157 verifies card-related transaction information based on
an analysis of several
criteria, such as: 1) determining that the UPC code for the product is present
in the datastore 180
(or other database such as an issuer's database) for the electronic value
token transaction
processing system 100; 2) determining that the value amount of the requested
transaction
corresponds to the customer's payment for the subject transaction request,
e.g., whether the UPC
information identifies the card as a $25.00 card and that the corresponding
transaction request
includes a $25.00 payment by the customer; 3) determining that the UPC
information identifies the
card as being a type of card available for processing by the requesting
merchant; and 4)
determining that the Bank Identification Number ("BIN") of the card (i.e., the
first six digits of the
card's identification number), which identifies the card issuer, corresponds
to the UPC information
identifying the card issuer.
[00128] The authorization unit 157 may also verify transactions based on
other criteria such as
transaction velocity (number/amount per unit time). For example, if a card
processor is concerned
that multiple void transactions are indicative of fraudulent activity, the
card processor could ask
that the electronic value token transaction processing system 100 monitor the
number of void
transactions requested and reject transactions from terminals that exceed a
pre-selected amount of
void transactions per unit time. Lastly, the authorization unit 157 may be
configured to reject
transaction requests in the event that the information received by the
authorization unit 157 is
unintelligible.
[00129] If the request is properly formatted and is validated as described
above, the electronic
value token transaction computer 150 may transmit details of transactions to
the issuers'
authorization systems rather than authorization requests. Also, in some
embodiments, the issuer,
the authorizing system (e.g., authorization unit 157) , and the transaction
computer are part of the
same entity and, in such an embodiment, there would be no issuers'
authorization systems 160 or
the issuers' authorization systems 160 would be under common control with the
other units of the
electronic value token transaction computer 150 (for example, a commonly owned
and operated
computing system, that may be centralized (e.g., part of a centralized data
center) and/or
distributed within a commonly owned or controlled system or network).
Furthermore, it should be
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
noted that although units associated with the electronic value token
transaction computer 150 (e.g.,
units 152-157) are depicted as various units within a single data processing
system for illustration
and conceptual purposes, one or more of units 152-157 could be implemented on
separate
computers, systems, or servers in a distributed data processing environment.
[00130] An exemplary process utilized by an electronic value token transaction
computer 150
for facilitating a purchase using an electronic wallet in accordance with a
primary e-wallet
transaction processing embodiment is depicted in Figure 7A. Such an embodiment
may be
exemplified by the e-wallet transaction processing request being both
initially received by and
subsequently performed by the electronic value token transaction processing
system 100. The
actions depicted can be performed in the order shown or in a different order,
and two or more of
the actions can be performed in parallel.
[00131] In block 302, the electronic value token transaction computer 150
receives a request or
multiple requests from a point of sale terminal. In at least one embodiment
the requests may
comprise an electronic wallet transaction request, a balance inquiry request,
a registration request,
an activation request, or a redemption request, a wallet management request,
and contains one or
more of the following: (a) identity of the terminal, (b) authentication
information, (c) the amount of
the purchase, (d) the identity of the electronic value token issuer, (e) the
identity of the vendor, (f)
the identity of the location, (g) the time of the request, (h) the date of the
request, (i) information
expressly identifying the request as an e-wallet transaction request (e.g.,
transaction type data); (j)
information identifying a primary e-wallet, sub-wallet(s), or a combination
thereof; (k) any other
transaction and/or authentication data described herein; and (1) any
combination thereof. The
request at block 302 may comprise other information, requests or functions,
for example of the
types described herein, in addition to or in place of the above enumerated
items. In at least one
embodiment, the authentication information is based on an authentication token
selected from the
group consisting of proxy card and cellular phone. Using the identity of the
electronic value token
issuer, transactions may be correctly formatted for communication with the
electronic value token
issuer.
[00132] Using information contained within the electronic wallet
transaction received from the
point of sale device 111 and/or from information obtained from datastore 180,
in block 304, the
electronic value token transaction computer 150 determines whether the request
is an electronic
wallet request containing valid authentication information and whether the
request is for
56
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
redemption of a value token(s), addition of a value token(s), deletion of a
value token(s), or
management of the electronic wallet. The electronic wallet request may
comprise a bank
identification number ("BIN") located on the proxy card as part of the
authentication information.
The sorting unit may decode the BIN number or otherwise verify that the
request is an electronic
wallet request.
[00133] Using information contained within the electronic wallet
transaction received from the
point of sale device 111 and/or from information obtained from datastore 180,
in block 324, the
electronic value token transaction computer 150 identifies/determines the
primary e-wallet, sub-
wallet(s), and/or locations of said e-wallet or sub-wallet(s)
indicated/necessary to effectuate the
received e-wallet transaction request. If the authorization information
received indicates the
requested e-wallet transaction involves a primary e-wallet, sub-wallet, or
combinations thereof
maintained by the electronic value token transaction computer 150, the
electronic value token
transaction computer 150 may (i) apply its own logic to the request; (ii)
apply rules stored in a
primary wallet (e.g., rules established by the electronic value token
transaction processing system
administrator, the primary e-wallet user, or a combination thereof); (iii)
apply rules stored in a sub-
wallet (e.g., rules established by the electronic value token transaction
processing system
administrator, the sub-wallet user, or a combination thereof) (iv) apply rules
received with the
request from the point of sale 111 (e.g., contemporaneous rules submitted with
the request by the
user of the primary e-wallet/sub-wallet); (v) or any combination thereof
[00134] For example, an embodiment may include the electronic value token
transaction
computer 150 determining that the entire request is related to value tokens
contained in a primary
e-wallet. Upon receipt of the request, the electronic value token transaction
computer 150 will
query its authorization unit 157 (as described more fully herein), its
datastore 180, the E-Wallet
unit 199, and any other necessary unit to determine whether the primary e-
wallet comprises value
tokens capable of meeting the subject request (e.g., whether the primary e-
wallet contains value
tokens associated with vendors, merchants, and/or issuers related to the
requested transaction).
Such determination may be performed by comparing electronic value token
identifications, user
IDs, requested transaction types. The electronic value token transaction
computer 150 will
subsequently evaluate the manner in which the electronic value tokens
available in the primary e-
wallet corresponding to the request will be applied under the primary e-
wallet's rules and/or rules
57
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
received with the request, and perform or refuse to perform the requested
transaction and/or
transactions.
[00135] Another embodiment may include the electronic value token transaction
computer 150
determining that the entire request is related to value tokens contained in a
sub-wallet. Upon
receipt of the request, the electronic value token transaction computer 150
will query its
authorization unit 157 (as described more fully herein), its datastore 180,
the E-Wallet unit 199,
and any other necessary unit to determine whether the sub-wallet comprises
value tokens capable
of meeting the subject request (e.g., whether the sub-wallet contains value
tokens associated with
vendors, merchants, and/or issuers related to the requested transaction). Such
determination may
be performed by comparing electronic value token identifications, user IDs,
requested transaction
types. The electronic value token transaction computer 150 will subsequently
evaluate the manner
in which the electronic value tokens available in the sub-wallet corresponding
to the request will be
applied under the sub-wallet's rules and/or rules received with the request,
and perform or refuse to
perform the requested transaction and/or transactions.
[00136] In
another example, an embodiment may include the electronic value token
transaction computer 150 determining that a portion of the entire transaction
request is related to
electronic value tokens residing in a primary e-wallet while a portion of the
transaction request is
related to electronic value tokens residing in a sub-wallet(s). Such
determination may be made by
evaluating the requested transaction type, the electronic value token
identification, or any other
methods for determining transaction allocation. The electronic value token
transaction computer
150 will evaluate the manner in which the electronic value tokens available in
the primary e-wallet
corresponding to the request will be applied under the primary e-wallet's
rules (as those rule may
affect payment methods to be employed which are located in the primary e-
wallet), the electronic
value token transaction computer 150 will evaluate the manner in which the
electronic value
tokens available in any applicable sub-wallet corresponding to the request
will be applied under
such sub-wallet's rules and/or rules received with the request, and perform or
refuse to perform the
requested transaction and/or transactions.
[00137] In an
exemplary embodiment, at block 324, the electronic value token transaction
computer 150 may identify, in response to a received transaction request, one
or more value tokens
in a primary e-wallet and one or more electronic value tokens in a sub-wallet
that, when used
together, will cover the entirety of the requested e-wallet transaction.
Moreover, one of the
58
CA 02897145 2015-07-03
WO 2014/107594 PCT[US2014/010206
electronic value tokens located in the primary e-wallet or sub-wallet may be
an electronic
representation of a loyalty card and another electronic value token located in
either the same or
different location of said loyalty card value token may be an electronic
representation of a retailer's
gift card. In such an example, the electronic value token transaction computer
150 can effectuate
the coincidental use of the "loyalty card" token and the "retailer's gift
card" token, regardless of
the tokens' locations in the primary e-wallet and/or sub-wallet(s) to allow
for an enhanced user
benefit as opposed to not coincidentally applying the value of the "retailer's
gift card" token and
the "loyalty card" token for the transaction, e.g., a 5% increase in the value
of the "retailer's gift
card" token or loyalty point bonus applied to the "loyalty card" token for the
use of the "retailer's
gift card" token.
[00138] A value token may be associated with a closed loop account or open
loop account. A
closed loop account typically expires after the funds in the account have been
depleted, e.g. a gift
card account. An open loop account does not typically expire. Rather, there is
typically an
ongoing obligation for various entities to credit and debit the account, e.g.
a branded credit card
account or debit card account such as Visa or Mastercard. Closed loop accounts
are often
associated directly with retailers while open loop accounts are often
associated with financial
institutions (e.g., Chase or Citi issued Visa). In at least one embodiment,
the electronic value
tokens comprise closed loop account numbers and open loop account numbers. The
closed loop
account numbers are associated with retailers able to debit or credit closed
loop accounts
associated with the closed loop account number. The open loop account numbers
are associated
with financial institutions able to debit or credit open loop accounts
associated with the open loop
account numbers. The electronic value token may have an expiration date or
specified dates of use
that are different from any other value tokens. Furthermore, the electronic
value tokens may
identify specific merchants, locations, and/or products with which the
electronic value tokens may
be utilized.
[00139] If the request is for value token addition, then in block 306, the
electronic wallet is
created (if not already created) and the electronic value token is added to
the electronic wallet. The
following Tables include elements, parameters, and information included in e-
wallet transaction
communications and used by the electronic value token transaction processing
system 100 to
facilitate and effectuate e-wallet transactions.
59
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00140] Table 1A illustrates request parameters requested to create a
wallet in at least one
embodiment. Table 1B illustrates response parameters requested to create a
wallet in at least one
embodiment.
Table 1A
Request Parameters
Element Data Suggested Description
Type Length
accounttype String 200 Account Type
loadamt decimal N/A Amount to be loaded
into the wallet
account
loadamtcurrency string 3 Denomination Type.
txn-uniqueidentifier string 12 Unique transaction
id.
Table 1B
Response Parameters
Element Data Type Description
accountid string Unique identifier for a account
accounttype string Type of the account.
currency string Denomination Type.
balance decimal Balance available in the account
uniqueidentifier string (numeric) The unique identifier
identifies a
transaction.
code string The Status of the requested transaction.
description string The Status description of the requested
transaction.
[00141] The electronic value token transaction computer 150 preferably
allocates memory for
the electronic wallet and value token(s) and associates the account number
with the electronic
wallet and/or authentication information stored in the electronic wallet unit
199 by storing the
pieces of information in a data structure on the datastore 180. Table 2
illustrates the parameters for
a gift card value token in at least one embodiment.
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
Table 2
Element and Description Data Type Suggested
Length
statusinfo.status.code String 7
statusinfo.status.description String 500
card.retailer.id Integer 11
String
card.retailer.name String 100
card.number String 50
card.securitycode String 50
card.expirydate Integer String 6
card.activationdate Date String 20
card.initialbalance Decimal String 10
card.currentbalance Decimal String 10
card.currentbalanceasof Date String 20
card.customerservice. String 20
phone
card.customerservice. String 256
web site
card.currency String 3
[00142] Table 3 illustrates more detailed parameters for a gift card
electronic value token in an
alternative embodiment, including the designation of associated wallet(s)
and/or sub-wallet(s).
Table 3
Element and Description Data Type Suggested
Length
card.retailer.id Integer 11
String
card.retailer.name String 100
card.number String 50
card.securitycode String 50
card.expirydate Integer String 6
card.registeredto String 10
card.activationdate Date String 20
card.initialbalance Decimal 10
String
card.islookedupinitialbalance String 1
card.currentbalance Decimal 10
String
card.islookedupcurrentbalance String 1
card.customerservice. String 20
61
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
Element and Description Data Type Suggested
Length
phone
card.customerservice. String 256
website
card .notes String 500
card.nickname String 100
card.currency String 3
card.user.firstname String 50
card.user.lastname String 50
card.user. address .linel String 50
card.user.address.line2 String 50
card.user.address.city String 50
card.user.address.state String 50
card.user.address.zip String 5
card.user.phone.number String 10
card.user.email.address String 128
card.additionalinfol String 300
card.additionalinfo2 String 300
card.additionalinfo3 String 300
wallet.id Integer String 10
Collection offolders
wallet.folder.l.id Integer String 10
wallet.folder.l.name String 100
wallet.folder.2.id Integer String 10
wallet.folder.2.name String 100
[... More folders]
[00143] The request, however, may be modified for other reasons unrelated
to the add token
decision and forwarded to the appropriate one of the issuers' authorization
systems 160 as part of
the reconciliation process, for example the request could concern redemption,
deletion, reloading
value, added value, balance inquiry, or a combination thereof, each of which
would be
communicated to the issuers' authorization systems 160 for reconciliation.
62
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00144] Table 4 illustrates formatting for authentication communication.
Table 4
Element and Description Data Type
client_ref id String
signature String
timestamp String(in the format
yyMMddI1-immssSSSz)
nonce String
encryption_type String
usertoken String
uuid String
user_ip String
channel String
[00145] Each request is authenticated using the signature, a user is
authenticated with
username/password or open id, the session is validated using the user token. A
client may send
client_ref id, timestamp, nonce, encryption_type, channel, user_ip, signature,
optionally usertoken
with each request to be able to validate each message.
[00146] Table 5 illustrates the parameters used to retrieve a user's
wallet.
Table 5
Element Data Type Description
accountid string Unique identifier for a account
accounttype string Type of the account.
currency string Denomination Type.
balance decimal Balance available in the account
code string The Status of the requested transaction.
description string The Status description of the requested
transaction.
63
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
1001471 Table 6A illustrates the request parameters used to redeem value
from a token in the
wallet.
Table 6A
Request Parameters
Element Data Suggested Description
Type Length
accountid String 100 Unique identifier for the account
redamt decimal N/A Amount to redeem from the account
redamtcurrency string 3 Amount type.
txn-uniqueidentifier string 12 Unique transaction id.
txn- bool N/A 0, if it is not a reversal of any
istimeoutreversal transaction type 1, if it is a reversal
transaction.
1001481 Table 6B illustrates the response parameters used to redeem value
from a token in the
wallet.
Table 6B
Response Parameters
Suggested
Element Data Type Length Description
accountid string. 100 Unique identifier for a account
accounttype string 50 Type of the account.
currency string. 3 Denomination Type.
balance decimal N/A Balance available in the account
uniqueidentifier string 12 Unique identifier for the
transaction.
code string 7 The Status of the requested
transaction.
description string 500 The Status description of the
requested
transaction.
64
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00149] Table 7A illustrates the request parameters used to load a value
token into the wallet.
Table 7A
Request Parameters
Data Suggested
Element Description
Type Length
accountid string 100 Unique identifier for a account
amount decimal N/A Amount to load on the account
amountcurrency string 3 Amount Type.
txn- bool N/A 0, if it is not a reversal of any
istimeoutreversal transaction type 1, if it is a reversal
transaction.
txn-uniqueidentifier string 12 Unique transaction id.
[00150] Table 7B illustrates the response parameters used to load a value
token into the wallet.
Table 7B
Response Parameters
Element Data Type Suggested Description
Length
accountid string 100 Unique identifier for a account
accounttype string 50 Type of the account.
balance decimal N/A Balance available in the account
uniqueidentifier string (numeric 12 Unique identifier for
the transaction.
values [0-9] only)
code string 7 The Status of the requested
transaction.
description string 500 The Status description of the
requested transaction.
currency string 3 Denomination Type.
[00151] If the request is for value token redemption, then in block 308,
the electronic value
token transaction computer 150 accesses the electronic wallet previously
determined to be
associated with the authentication information and examines the rules
associated with the
electronic wallet. In at least one embodiment, examining the rules comprises
examining priorities
of value tokens configurable by the user. For example, the user may prefer to
use any closed loop
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
value tokens corresponding to the retailer originating the purchase request.
If none is found or if
the token will not cover the purchase, then the user may prefer to use an open
loop value token for
the remainder. As a result of these preferences, the closed loop value tokens
may all have higher
priority than the open loop value tokens. Among the open loop value tokens,
one may have
priority over another. For example, the user prefers to pay for any remainder
with a credit card
rather than a debit card. In at least one embodiment, the user may configure
these rules via the
Internet or mobile application and save the priorities as default preferences.
In an alternative
embodiment, the user selects the electronic value tokens to apply to the
electronic wallet request at
the POS device, for example at a vendor or retailer location such as a check-
out lane, customer
service counter, or kiosk. As such, selecting the electronic value tokens
comprises selecting value
tokens with the highest priority that, when used together, will cover the
purchase amount. As can
be seen in the example, one purchase transaction has been split into two
redemptions without
compromising efficiency of the purchase. Similarly, one or more electronic
wallet transactions can
be split into two or more transactions without compromising efficiency. In an
embodiment, at least
one of the electronic value tokens is associated with a closed loop prepaid
account (e.g., an
electronic prepaid, gift, or stored value card) and the rules associated with
a primary wallet invoke
a sub-transaction processed by a third party administrator associated with a
sub-wallet.
[00152] In at least one embodiment, examining the rules comprises examining
percentages of
the electronic wallet request to which different value tokens should be
applied and wherein
applying the electronic value tokens comprises applying the electronic value
tokens to the
electronic wallet request in according to the percentages. In block 310, the
electronic value token
transaction computer 150 then selects, based on the rules, value tokens in the
electronic wallet that,
when used together, will cover the electronic wallet request. For example, the
user may configure
the rules such that each purchase is split evenly between two credit cards. As
such, selecting the
electronic value tokens comprises selecting two open loop tokens between which
to split the
purchase amount. Similar to the above example, efficiency is preserved because
where a single
authorization token (e.g., only the proxy card or a mobile device) was used at
the point of sale, not
the two credit cards corresponding to the electronic value tokens. Other rules
can be implemented,
and the rules can be used in various combinations and permutations with each
other. The
electronic value token transaction processing system can also implement "if-
then" rules based on
the information transmitted in the electronic wallet request. For example, a
purchase at a gas
66
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
station can result in a gas credit card value token selection, and the like.
In such am embodiment,
the electronic value token computer 150 may query the rule(s) 802, 817, 818,
and 819 of the
subject e-wallet 10 and/or sub-wallets 807 (e.g., for credit card-type
electronic value tokens), 808
(e.g., for debit card-type electronic value tokens), and 809 (e.g., for stored
value-type electronic
value tokens) and determine, based on transaction request information which
includes a transaction
type, e.g., purchase at a gas station, that rule(s) established for the
subject e-wallet 10 and/or sub-
wallets 807, 808, and 809 require that the transaction type request be first
satisfied with a first
electronic value token type, e.g. a gas card-related electronic value token
829, and upon the
occasion that the subject e-wallet 10 and/or sub-wallet(s) 807, 808, and 809
do not comprise a
sufficient amount of the first value token type to satisfy the entire
transaction request, the electronic
value token computer 150 may satisfy the remainder of the transaction request
with a second
electronic value token type, e.g., a debit card-related electronic value token
828.
[00153] The electronic value token transaction computer 150 also applies
the electronic value
tokens to the electronic wallet request. In applying the electronic value
tokens to the request, the
electronic value token transaction computer 150 can generate and send debit
and credit messages
to be performed on the accounts administered by the retailers and financial
institutions using the
appropriate account numbers, or the electronic value token transaction
computer 150 can credit or
debit the accounts directly if the electronic value token transaction computer
has such
administrative authority.
[00154] In at least one embodiment, the electronic value token transaction
computer 150
modifies the request (e.g., applies a required format) and forwards the
modified request to the
appropriate one of the issuers' authorization systems 160, which receives the
modified request and
acts upon same, for example authorizing and/or processing the request to
redeem the electronic
value token and updating a datastore accordingly. rl he authorization system
160 is not at the same
location from where the electronic wallet request was received in at least one
embodiment. For
example, if the electronic wallet request was received from a retail store,
the authorization system
may be owned and operated by the retailer, but will not be at the retail
store. Rather, the
authorization system may be located at a data center for example. As such,
neither the retail store
nor the retailer in general need be aware of some or all the contents of the
wallet. In at least one
embodiment, the retail store is unaware of even the presence of the electronic
wallet, as it merely
recognizes that some transaction authorizing action has been communicated to
its point of sale
67
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
(e.g., swipe of a proxy card, digital personal assistant interaction with
point of sale device, entry of
a PIN at a keypad at point of sale, or other authorizing activity). In other
words, access and use of
the e-wallet at the point of sale is seamless and does not require any special
or custom actions in
order to process the transaction in comparison to traditional physical tender.
The issuers'
authorization systems 160 sends a response message back to the electronic
value token transaction
computer 150. In an alternative embodiment where the electronic value token
transaction
computer 150 performs the functions of the issuers' authorization systems 160,
the method may
proceed directly from block 306 or 310 to block 314.
[00155] The electronic value token transaction computer 150 receives the
confirmation message
from the appropriate one of the issuers' authorization systems 160 in block
312. At block 314, the
electronic value token transaction computer 150 updates electronic wallet in
the electronic wallet
unit 199 and datastore 180 to reflect that the electronic wallet is activated
and to reflect any debit,
credit, addition, or deletion to/of the electronic value token(s). Figures 9A-
D illustrate a series of
user interface screens and prompts in at least one embodiment. For example,
the user may see the
illustrated prompts when managing the user's electronic wallet via a computer
connected to the
Internet, and/or kiosk 189.
[00156] A transaction log 170 may be updated by the electronic value token
transaction
computer 150 in block 316 to record the details about the transaction. The
details recorded in the
transaction log may include (a) the type, time and date of the transaction,
(b) whether the electronic
wallet was activated, (c) the reason electronic wallet was not activated if
the request was denied,
(d) the credit, debit, addition, or deletion to/of the electronic value
token(s), (e) a change in rules
associated with the electronic value token(s), (f) the identity of the vendor,
(g) the identity of the
issuer, (h) the location of the vendor, (i) the identity of the terminal
adding the electronic value
token, (j) the identity of the entity granting the electronic value token, and
(k) any combination
thereof. The transaction log may include other information (e.g., transaction
and/or authentication
data) in addition to or in place of the items enumerated above.
[00157] The electronic value token transaction computer 150, in block 318,
then forwards the
confirmation message to the point of sale device 111. The electronic value
token transaction
computer 150, prior to forwarding the confirmation message to the point of
sale device 111, may
modify the confirmation message, for example as necessary to include
information that may be
printed on a receipt for the customer and/or presented on a display to the
store clerk operating the
68
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
point of sale device 111. At block 320, the electronic value token transaction
computer 150
reconciles the accounts of the various vendors, merchants, issuers, the
electronic value token
transaction processing system administrator, and other entities involved with
issuing, selling,
redeeming, and marketing the electronic value tokens to debit and credit
appropriate accounts and,
in some embodiments, initiates funds transfers between appropriate bank
accounts belonging to the
various entities. Alternatively, reconciliation of accounts may be performed
periodically (e.g.,
daily, weekly, monthly, etc.) rather than after each transaction. In such an
embodiment, the
information from the transaction log 170 may be utilized to reconcile the
various entities involved
with the sale or redemption of various value tokens thus requiring fewer funds
transfers to be
initiated. In an embodiment, information in transaction log 170 is used to
match transactions and
the like. For example, grouping all transactions from a given location or a
given merchant, or
grouping transaction types (e.g., credit, debit, etc.). In various
embodiments, the sequence of
events depicted in may be varied, and thus may be carried out in any desired
order, sequentially or
simultaneously.
[00158] Figure 5B illustrates an exemplary electronic value token
transaction processing system
1100 in accordance with an embodiment wherein the electronic wallet processing
system
comprises the electronic value token transaction computer 150, functioning as
an electronic sub-
wallet transaction processor, integrated with a primary electronic wallet
transaction processor such
as depicted by E-Wallet Aggregator System 1000. E-Wallet Aggregator System
1000 may be
further understood to have the same functionalities, capabilities, database
access, networked
connections, and operative components as the herein described electronic value
token transaction
computer 150, and in some embodiments an electronic value token transaction
computer 150 and
its associated components (e.g., electronic value token transaction processing
system 100) may
serve as, or be substituted for, the E-Wallet Aggregator System 1000. In an
embodiment, the E-
Wallet Aggregator System 1000 may be controlled, maintained, operated, owned,
and/or otherwise
managed by a common entity or entities which control, maintain, operate, own,
and/or otherwise
manage the electronic value token transaction computer 150. i.e., the primary
electronic wallet
transaction processor and the electronic sub-wallet transaction processor
share a common
controller, maintainer, operator, owner, and/or manager. In an embodiment, the
E-Wallet
Aggregator System 1000 may be controlled, maintained, operated, owned, and/or
otherwise
managed by an entity or entities that are separate, distinct, and/or unrelated
to the entity and/or
69
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
entities which control, maintain, operate, own, and/or otherwise manage the
electronic value token
transaction computer 150, i.e., the primary electronic transaction processor
and the electronic sub-
wallet transaction processor do not share a common controller, maintainer,
operator, owner, and/or
manager. As shown, when functioning in an electronic sub-wallet transaction
processing capacity,
the electronic value token transaction processing system 1100 comprises: (a)
an electronic value
token transaction computer 150; (b) an E-Wallet Aggregator System interface
1052; (c) a datastore
180 containing an electronic wallet unit 199 storing electronic value tokens,
e.g., 804, 827, 828,
and 829, such as account numbers, electronic wallet account information, value
added award
conditions (herein "value added award" is synonymous with "value added bonus,"
"value added
bonus award," "value added award bonus," and "value differentiation"), and
other information
related to adding, redeeming, and managing the electronic value tokens, as
described in detail
herein; (d) at least one individual issuers' authorization system 160; and (e)
any other unit included
in the system by the electronic value token transaction computer administrator
151. In one
embodiment, the electronic value token transaction computer 150 comprises a
value added
determination unit 153, an E-Wallet Aggregator System interface 1052, a
message modification
unit 154, a reconciliation unit 155, an issuer system interface 156, an
authorization unit 157, and a
sorting unit 198. The E-Wallet Aggregator System interface 1052 provides a
means for the
electronic value token transaction computer 150 to communicate with the E-
Wallet Aggregator
System 1000 via, for example, the Internet, a Public Switched Telephone
Network ('PSTN"), or an
independent dedicated network. Likewise, the electronic value token
transaction computer 150
may communicate via issuer system interface 156 with the issuers'
authorization system 160 via,
for example, the Internet, a Public Switched Telephone Network (PSTN), or an
independent
dedicated network. Communications 116, 117 between the E-Wallet Aggregator
System interface
1052 and the E-Wallet Aggregator System 1000 and communications 109, 110
between the issuer
system interface 156 and the issuers' authorization systems 160 may be
encrypted for added
security and/or may utilize a virtual private network ("VPN"). The sorting
unit 198 may sort the
communications into various types for routing in various ways. For example,
the sorting unit 198
may identify and sort sub-wallet requests (e.g., upon receipt of authorization
information with a
transaction request, the sorting unit 198 can route the requested transaction
to a specific electronic
sub-wallet maintained by the system and/or to a specific section or sections
maintained within the
electronic sub-wallet), balance inquiry requests, registration requests,
activation requests,
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
redemption requests, and management requests for routing to the various units
of Figure 5B. The
electronic value token transaction computer 150 or sorting unit 198 may also
generate messages
based on the requests for similar routing.
[00159] As can be seen in Figure 5B, at the point of sale device 111
(typically located at a
vendor and/or redeeming merchant or retailer, but alternatively located at a
kiosk 189 or at a user's
home or office where a personal computer is configured to act as a point of
sale, for example
during an on-line transaction), the authentication token is interpreted by a
point of sale
interpretation unit 101 (e.g., a card reader). The point of sale
interpretation unit 101 can comprise
a human, a bar code scanner, magnetic strip reader, optical character
recognition device, biometric
device, numerical keyboard (e.g., for entering a token identification number)
or other device
configured to interrogate, interpret, capture, or input the data encoded in or
on the authentication
token.
[00160] About contemporaneously with (or, alternatively, prior or subsequent
to) the
interpretation of the authentication token, a request for an electronic wallet
transaction by a point
of sale transaction unit 104 is made. The point of sale transaction unit 104
can comprise a human,
an electronic input device, a register or terminal, a computer processing unit
("CPU"), a personal
computer, a personal digital assistant, smart phone, or other means of
requesting or messaging
interpreted by the point of sale interpretation unit 101 and/or point of sale
processing unit 105. In
some embodiments, the actions performed by the point of sale interpretation
unit 101 and the point
of sale transaction unit 104 may be performed by one unit capable of
performing both actions that
would be performed by the individual units, for example a point of sale
register/terminal or a
personal computer during an on-line, web-based transaction.
[00161] The point of sale interpretation unit 101 and the point of sale
transaction unit 104
communicate with the point of sale processing unit 105. The point of sale
processing unit 105 can
comprise a CPU or other type of processing device accepted for use in the
industry. The point of
sale interpretation unit 101 communicates authentication information 102 to
the point of sale
processing unit 105. The point of sale transaction unit 104 communicates the
request 103 for an
electronic wallet transaction to the point of sale processing unit 105. The
point of sale processing
unit 105 may combine this information to communicate with the E-Wallet
Aggregator System
1000 (e.g., transmits a message requesting an electronic wallet transaction
along with the
associated transaction and/or authentication data). In an embodiment, the
point of sale processing
71
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
unit 105 stores and/or receives from the E-Wallet Aggregator System 1000 (or a
sub-administrator
or unit associated therewith, such as a sub-wallet administrator, e.g.,
electronic value token
transaction computer 150) a transaction format associated with the POS
retailer and/or associated
with a given transaction type and/or value token, and such transaction format
may be used to
format the transaction request or message, to prompt the user for further
information, or for other
data gathering or transmit/receive features at the point of sale. For example,
a user making a
purchase at a retailer operates a card reader. A card reader may a display
with an input device and
a barcode reader or magnetic strip scanner. The card reader may be touch
sensitive and may have
various buttons used for input. Following the card reader prompts, the user
sees the options
"Debit," "Credit," and "E-Wallet." The user selects "E-Wallet." The user then
sees the options
"Purchase," "Add Token," and "Delete Token." The user selects "Purchase."
Following
additional prompts (which in an embodiment relate to a transaction format
specific to the particular
retailer of the point of sale), the user enters a PIN number. In some
embodiments, the actions
performed by the point of sale interpretation unit 101, the point of sale
transaction unit 104, and the
point of sale processing unit 105 may all be performed by one unit (e.g., an
integrated POS device
such as a computerized register) capable of performing all the actions that
would be performed by
the individual units.
[00162] The point of sale processing unit 105 is connectable to the E-
Wallet Aggregator System
1000 via a suitable network, such as the Internet, the public switched
telephone network (PSTN),
or an independent dedicated network. Each point of sale processing unit 105
has an associated
identifier (e.g., a terminal identifier or serial number) that may be
transmitted to the E-Wallet
Aggregator System 1000 during the course of connecting the point of sale
processing unit 105 to
the E-Wallet Aggregator System 1000. Each point of sale processing unit 105
may include
multiple point of sale transaction units corresponding to individual terminals
each with its own
terminal identification, for example present within a given store location.
[00163] As depicted in Figure 5B, the E-Wallet Aggregator System 1000 is
configured to: (a)
form a secure connection with the retailer/merchant and/or vendor (e.g., via
the point of sale device
111), the electronic value token transaction computer 150, and the issuers'
authorization systems
160; (b) to communicate with issuers' authorization systems 160 to request and
receive redemption
or addition of value tokens into electronic wallets; (c) to communicate with
issuers' authorization
systems 160 to redeem all or a portion of the electronic value tokens
associated with the electronic
72
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
wallet; (d) communicate with the electronic value token transaction computer
150 to facilitate
transactions concerning value tokens residing in an electronic sub-wallet
maintained by the
electronic value token transaction processing system 1100;(e) communicate to
the
retailer/merchant and/or vendor (e.g., via the POS unit 111) the redemption or
addition of value
tokens into electronic wallets and any information concomitant with the
redemption or addition of
value tokens into electronic wallets and/or sub-wallets; and (f) communicate
to the
retailer/merchant and/or vendor (e.g., via the POS unit 111) any reasons why
transactions cannot
not be completed.
[00164] The electronic value token transaction computer 150 may comprise a
singular
processing unit (e.g., a centralized server), a plurality of processing units
(e.g., a distributed
computing system with various units distributed and in communication with each
other), or
combinations thereof, with concomitant storage capabilities, each capable of
or designated for:
accessing the datastore 180; creating a transaction log 170; creating and
maintaining an error log
175; communicating with the E-Wallet Aggregator System 1000; communicating
with the
individual issuers' authorization systems 160; processing individual value
token and electronic
wallet requests; processing redemption requests, processing value added
functions to add
additional cash value or add an electronic redemption coupon for a specific
product(s) or
service(s), processing redemption request for electronic redemption coupons
for specific product(s)
and/or service(s), and communicating with other systems 190 capable of and
authorized to
communicate with the electronic value token transaction computer 150.
[00165] Datastore 180 maintains records of accounts associated with each
electronic sub-wallet
indicating: (a) whether each individual value token has been added or
redeemed, (b) whether an
authentication token for an individual value token has been registered, (c)
records and details of
each individual redemption request, (d) the amount remaining on the electronic
value tokens, (e)
rules required for redeeming the electronic value tokens, (f) identity of the
issuers of the electronic
value tokens, (g) value added bonus awards, (h) rules for redeeming value
added bonus awards,
and (i) any combination thereof. The datastore may also maintain records of
rules required for
granting a value added bonus award to an electronic wallet or value token.
[00166] Datastore 180 also maintains records associated with each
electronic wallet and/or sub-
wallet indicating: (a) timing of, and other information related to,
registration activities; (b) timing
of, and other information related to, management activities; (c) timing of,
and other information
73
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
related to, transaction activities; (d) rules applicable; (e) identity of the
issuers electronic value
tokens therein; (f) identity of sub-wallets associated therewith; (g) any
other records requested by
issuers, merchants, vendors, advertisers, users, or other interested parties;
and (h) any combination
thereof. While a single datastore 180 is shown, it should be understood that a
plurality of
datastores may be employed, and relevant data divided among the datastores in
any suitable
manner to meet the various processes and objectives described herein. Also,
the various data may
be associated with one or more datastores closely coupled to and/or located in
proximity to one or
more sub-units, sub-processors, third party processors, and the like
associated with the electronic
value token transaction computer 150, and such datastores preferably have data
used by such sub-
units, sub-processors, and third party processors.
[00167] The electronic value token transaction computer 150 is also
configured to generate and
maintain a transaction log 170 of all activity involving the electronic value
token transaction
computer 150. The transaction log may comprise a detailed summary of
transaction types such as:
(a) requested value token additions; (b) requested value token sales; (c)
requested value token
redemptions; (d) requested value token exchanges; (e) the monetary amount
ascribed to value
token additions; (f) the monetary amount ascribed to value token redemptions;
(g) the monetary
value ascribed to value token exchanges; (h) the value added amounts,
products, or services
additions; (i) the value added amounts, products, or services redemptions; (j)
the time the
electronic value tokens were added; (k) the time the electronic value tokens
were redeemed; (1) the
transaction or communication performed with the issuer for adding value
tokens; (m) the
transaction or communication performed with the issuer for redeeming value
tokens; (n) the PIN
communicated to the vendor in response to a request to add a value token
requiring the input of a
PIN for use; (o) e-wallet registration; (p) e-wallet set-up activities; (q) e-
wallet transaction
activities; (r) e-wallet savings activities; (s) e-wallet management
activities; (t) any other
information the electronic value token transaction computer administrator 151
directs the
electronic value token transaction computer 150 to maintain as a log entry;
and (u) any
combination thereof.
[00168] The information contained in the transaction log 170 may be used
for data mining
purposes, e.g., to generate reconciliation reports, settlement reports,
payment reports, audit reports,
e-wallet registration reports, e-wallet management reports, e-wallet usage
reports, e-wallet savings
reports, electronic value token purchase reports, electronic value token
redemption reports,
74
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
electronic value token exchange reports, electronic value token sale reports,
or other forms of
information aggregation for the benefit of, use by, or for provision to, the
electronic value token
transaction administrator 151, the datastore administrator 181, the E-Wallet
Aggregator System
1000 (e.g., for communication to vendors or other purposes), vendors, issuers,
issuers'
authorization systems 160, redeeming merchants, or other interested parties.
For example, the
transaction log 170 contains information about each transaction performed by
electronic value
token transaction computer 150 (and any sub-components thereof) and may be
utilized by the
reconciliation unit 155 when reconciling accounts belonging to various E-
Wallet Aggregator
System 1000 associated vendors, merchants, issuers, as well as vendors,
merchants, and issuers not
associated with the E-Wallet Aggregator System 1000, and also the electronic
value token
transaction processing system administrator 151. Additional data mining
considerations that may
be recorded, analyzed, and/or provided interested parties (e.g., vendors,
merchants, issuers,
advertisers, etc.) include data about: (i) the purchase habits of e-wallet
users; (ii) electronic value
token purchases, sales, redemptions, and exchanges; (iii), special offer
and/or value added
activities; (iv) loyalty-related activities; and (v) savings-related
activities, all of which can be used
for marketing, inventory, and other purposes.
[00169] Oversight and maintenance of the electronic value token transaction
computer is
performed by the electronic value token transaction computer administrator
151. Although not
required, in an alternative embodiment, the electronic value token transaction
computer
administrator 151 may also function as the datastore administrator 181. The
electronic value token
transaction computer 150 is configured to generate and maintain an error log
of all transactions that
were not completed and reasons therefore. In some embodiments, the error log
is administered by
the electronic value token transaction computer administrator 151.
[00170] The electronic value token transaction computer 150 is also
configured to communicate
with other entities 190 authorized to access the electronic value token
transaction processing
system and specifically authorized to access the electronic value token
transaction computer 150.
These other entities may comprise E-Wallet Aggregator System 1000, third party
payment
management systems, third party audit systems, issuer affiliated entities,
vendor affiliated entities,
redeeming merchants or redeeming merchant affiliated entities, financial
institutions such as banks,
credit card agencies, or credit unions, or any other entity provided access by
the electronic value
token transaction computer administrator 151 or other entity having authority
to grant access.
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00171] In an embodiment, the transaction request from the E-Wallet Aggregator
System 1000
may contain one or more of the following pieces of information: (a)
authentication information, (b)
point of sale terminal identification, (c) amount to be credited or debited,
(d) the time of the
request, (e) the date of the request, (f) identification of the issuer, (0
identification of the vendor,
(h) location of vendor, (i) identification of the product(s) and/or service(s)
being purchased, (j) an
activation or deactivation request, (k) a wallet management function such as
addition of a value
token, deletion of a value token, exchange of a value token, changing
management or processing
rules associated with one or more value tokens, partitioning a wallet into sub-
wallets or vice-versa,
etc., (1) and any combination thereof However, the information contained
within the request is not
limited to the enumerated list but may comprise other items in addition to the
items enumerated or
in place of the items enumerated above.
[00172] Upon receipt of the electronic wallet transaction request from the
E-Wallet Aggregator
System 1000, and identification and sorting as such by the sorting unit 198,
the electronic value
token transaction computer 150 accesses the electronic wallet unit of
datastore 180. The electronic
value token transaction computer 150 processes the information contained in
the datastore 180 and
communicates 109, 110 with the individual issuers' authorization systems 160
to effectuate
management of the electronic value tokens and corresponding accounts. The
message
modification unit may adjust the messages and requests so that multiple units,
sub-
components/processors, or third party administrators can recognize and
correctly interpret the
messages. For example, after the electronic value token transaction computer
150 determines the
individual issuers' authorization systems 160 associated with the request, the
message modification
unit 154 accesses the database 180 to determine the appropriate transaction
messaging formats for
each individual issuers' authorization systems 160 and then formats the
subsequent
communications to said individual issuers' authorization systems 160 using the
individual issuers'
authorization systems 160 specified/preferred transaction format and
vocabulary. The electronic
value token transaction computer 150 can also provide the appropriate
messaging formatting
information, e.g., a template, to the E-Wallet Aggregator System 1000 to
facilitate that system's
processing of information related to the request. The electronic value token
transaction computer's
150 communication with the individual issuers' authorization systems 160 may
occur
simultaneously or independently. The electronic value token transaction
computer 150 is
connectable to the individual issuers' authorization systems as via a suitable
network, such as the
76
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
PSTN, the Internet, or an independent dedicated network. The electronic value
token transaction
computer 150 is configured to send and/or receive communication 110 from the
issuers'
authorization systems 160 concerning the status of the electronic value
tokens.
[00173] The reconciliation unit 155 reconciles the accounts of various
issuers, selling vendors,
and/or redeeming merchants, to credit and debit appropriate merchants,
vendors, the electronic
value token transaction processing system administrator, and issuers with the
value of various
transactions to reflect which entities received value from which other
entities. For example, if a
vendor A sells a value token issued by issuer B for a specified amount and
receives payment from
a user who adds the electronic value token to the user's electronic wallet,
the selling vendor
receives a percentage (e.g., retains a percentage) of the purchase amount
and/or a predetermined
amount, the E-Wallet Aggregator System 1000 and/or the electronic value token
system
administrator receives a percentage of the purchase amount and/or
predetermined amount for
processing the transaction, and the issuer receives the remainder. If a value
token issued by issuer
Y is redeemed at merchant X to purchase items, then the amount redeemed is
debited to the issuer
Y and credited to the merchant X, sometimes minus a transaction fee collected
by the issuer and/or
a transaction or processing fee collected by the electronic value token
transaction processing
system administrator.
[00174] Authorization unit 157 is utilized when the electronic value token
transaction computer
150 is also the authorizing system such that the electronic value token
transaction computer 150
authorizes electronic sub-wallet requests rather than transmitting the request
to the issuers'
authorization systems 160 for authorization. The authorization unit157 may
perform the same
and/or different functions as described for authorization systems 160 and vice-
versa.
[00175] The authorization unit 157 will validate the formatting of the
wallet (e.g., primary or
sub-wallet) transaction request received from the E-Wallet Aggregator System
1000. In other
words, the authorization unit 157 will check the data fields in the request to
confirm that the fields
are populated with data and that the data is in the correct format (e.g.,
length, alphanumeric
format). If the request is improperly formatted, the authorization unit 157
will reject the request, or
in some embodiments may retrieve the proper format (e.g., from a format
database) and modify the
transaction request to comply with the proper format. The authorization unit
157 also performs
various validation checks on the transaction request. The authorization unit
157 verifies card-
related transaction information based on an analysis of several criteria, such
as: 1) determining
77
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
that the UPC code for the product is present in the datastore 180 (or other
datastore such as an
issuer's database) for the electronic value token transaction processing
system 1100; 2)
determining that the value amount of the requested transaction corresponds to
the customer's
payment for the subject transaction request, e.g., whether the UPC information
identifies the card
as a $25.00 card and that the corresponding transaction request includes a
$25.00 payment by the
customer; 3) determining that the UPC information identifies the card as being
a type of card
available for processing by the requesting merchant; and 4) determining that
the Bank
Identification Number ("BIN") of the card (i.e., the first six digits of the
card's identification
number), which identifies the card issuer, corresponds to the UPC information
identifying the card
issuer.
[00176] The authorization unit 157 may also verify transactions based on
other criteria such as
transaction velocity (number/amount per unit time). For example, if a card
processor is concerned
that multiple void transactions are indicative of fraudulent activity, the
card processor could ask
that the electronic value token transaction processing system 1100 monitor the
number of void
transactions requested and reject transactions from terminals that exceed a
pre-selected amount of
void transactions per unit time. Lastly, the authorization unit 157 may be
configured to reject
transaction requests in the event that the information received by the
authorization unit 157 is
unintelligible.
[00177] If the request is properly formatted and is validated as described
above, the electronic
value token transaction computer 150 may transmit details of transactions to
the issuers'
authorization systems rather than authorization requests. Also, in some
embodiments, the issuer,
the authorizing system 9e.g., authorization unit 157), and the transaction
computer are part of the
same entity and, in such an embodiment, there would be no issuers'
authorization systems 160 or
the issuers' authorization systems 160 would be under common control with the
other units of the
electronic value token transaction computer 150 (for example, a commonly owned
and operated
computing system, that may be centralized (e.g., part of a centralized data
center) and/or
distributed within a commonly owned or controlled system or network).
Furthermore, it should be
noted that although units associated with the electronic value token
transaction computer 150 (e.g.,
units 152-157) are depicted as various units within a single data processing
system for illustration
and conceptual purposes, one or more of units 152-157 could be implemented on
separate
computers, systems, or servers in a distributed data processing environment.
78
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00178] An exemplary process utilized by an electronic value token transaction
computer 150
for facilitating a purchase using an electronic wallet in accordance with an e-
wallet transaction
comprising an electronic sub-wallet maintained by a third party electronic
value token transaction
computer which maintains the sub-wallet as part of a relationship with a
primary e-wallet system
provider, e.g., the E-Wallet Aggregator System 1000, embodiment is depicted in
Figure 7B. Such
an embodiment may be exemplified by the e-wallet transaction processing
request being initially
received by the E-Wallet Aggregator System 1000 and performed in part by the
electronic value
token computer 150. The actions depicted can be performed in the order shown
or in a different
order, and two or more of the actions can be performed in parallel.
[00179] In block 301, the E-Wallet Aggregator System 1000 receives a
request or multiple
requests from the point of sale 111. In at least one embodiment the requests
may comprise an
electronic wallet transaction request, a balance inquiry request, a
registration request, an activation
request, or a redemption request, a wallet management request, and contains
one or more of the
following: (a) identity of the terminal, (b) authentication information, (c)
the amount of the
purchase, (d) the identity of the electronic value token issuer, (e) the
identity of the vendor, (f) the
identity of the location, (g) the time of the request, (h) the date of the
request, (i) information
expressly identifying the request as an e-wallet transaction request (e.g.,
transaction type data); (j)
information identifying a primary e-wallet, sub-wallet(s), or a combination
thereof; (k) any other
transaction and/or authentication data described herein; and (1) any
combination thereof The
request at block 301 may comprise other information, requests or functions,
for example of the
types described herein, in addition to or in place of the above enumerated
items. In at least one
embodiment, the authentication information is based on an authentication token
selected from the
group consisting of proxy card and cellular phone.
[00180] Continuing with the process of block 301, the E-Wallet Aggregator
System 1000 may
determine that a portion of the requested e-wallet transaction may be
processed via the E-Wallet
Aggregator System 1000 while another portion of the requested e-wallet
transaction implicates a
sub-wallet which is maintained by a third party administrator, e.g.,
electronic value token
transaction computer 150. If the electronic wallet transaction request
information received by the
E-Wallet Aggregator System 1000 indicates that the transaction request will
require/involve a sub-
wallet maintained by a third party administrator's system to fully effectuate
a response to the
transaction request, and the rules applicable to the associated primary e-
wallet maintained by the
79
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
E-Wallet Aggregator System 1000 so dictate, the E-Wallet Aggregator System
1000 processes the
original request, generates a new request, generates a sub-request, or
modifies the original request,
to send to the sub-wallet which is maintained in association with the primary
electronic wallet, e.g.,
the primary electronic wallet sends the original request, the new request, the
sub-request, or the
modified original request to the electronic value token transaction computer
150, which maintains
the indicated sub-wallet. In processing the original request, generating the
new request, generating
the sub-request, or modifying the original request to send to the sub-wallet,
the E-Wallet
Aggregator System 1000 may (i) apply its own logic to the e-wallet transaction
request; (ii) apply
rules stored in the primary wallet (e.g., rules formulated by the primary e-
wallet provider, the
primary e-wallet user, or a combination thereof); (iii) apply rules received
with the transaction
request from the point of sale 111 (e.g., contemporaneous rules submitted with
the request by the
user of the primary electronic wallet and/or electronic sub-wallet); (iv) or
any combination thereof
[00181] In block 303, the electronic value token transaction computer 150
receives a request or
multiple requests from the E-Wallet Aggregator System 1000. In at least one
embodiment the
requests may comprise an electronic sub-wallet request, a balance inquiry
request, a registration
request, an activation request, or a redemption request, a sub-wallet
management request, and
contains one or more of the following: (a) identity of the terminal, (b)
authentication information,
(c) the amount of the purchase, (d) the identity of the electronic value token
issuer, (e) the identity
of the vendor, (f) the identity of the location, (2) the time of the request,
(h) the date of the request,
(i) information expressly identifying the request as an e-wallet transaction
request (e.g., transaction
type data); (j) information identifying a primary e-wallet, sub-wallet(s), or
a combination thereof
(k) any other transaction and/or authentication data described herein; and (1)
any combination
thereof. The request at block 303 may comprise other information, requests or
functions, for
example of the types described herein, in addition to or in place of the above
enumerated items. In
at least one embodiment, the authentication information is based on an
authentication token
selected from the group consisting of proxy card and cellular phone. Using the
identity of the
proxy card and/or cellular phone, embedded transactions may be correctly
formatted for
communication with the pertinent electronic value token issuers of the subject
transaction request.
[00182] Using information received from the E-Wallet Aggregator System 1000
pursuant to the
transaction request and from information obtained from datastore 180, in block
304, the electronic
value token transaction computer 150 determines whether the request is an
electronic sub-wallet
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
request containing valid authentication information and whether the request is
for redemption of a
value token(s), addition of a value token(s), deletion of a value token(s), or
other management of
the electronic sub-wallet. The electronic sub-wallet request may comprise a
bank identification
number ("BIN") as part of the authentication information. The sorting unit may
decode the BIN
number or otherwise verify that the request is an electronic sub-wallet
request concerning an
electronic value token residing in the indicated sub-wallet.
[00183] Using information contained within the electronic wallet
transaction received from the
E-wallet Aggregator System 1000, and/or from information obtained from
datastore 180, in block
324, the electronic value token transaction computer 150 identities/determines
the sub-wallet(s),
and/or locations of said sub-wallet(s) indicated/necessary to effectuate the
received e-wallet
transaction request. If the authorization information received indicates the
requested e-wallet
transaction involves a sub-wallet maintained by the electronic value token
transaction computer
150, the electronic value token transaction computer 150 may (i) apply its own
logic to the request;
(ii) apply rules stored in a sub-wallet (e.g., rules established by the
electronic value token
transaction processing system administrator, the sub-wallet user, or a
combination thereof); (iii)
apply rules stored in a sub-sub-wallet (e.g., rules established by the
electronic value token
transaction processing system administrator, the sub-sub-wallet user, or a
combination thereof)
(iv) apply rules received with the request from the point of sale 111 (e.g.,
contemporaneous rules
submitted with the request by the user of the primary e-wallet/sub-wallet);
(v) or any combination
thereof.
[00184] For example, an embodiment may include the electronic value token
transaction
computer 150 determining that the entire request received from the E-Wallet
Aggregator System
1000 is related to value tokens contained in a singular sub-wallet. Upon
receipt of the request, the
electronic value token transaction computer 150 will query its authorization
unit 157 (as described
more fully herein), its datastore 180, the E-Wallet unit 199, and any other
necessary unit to
determine whether the sub-wallet comprises value tokens capable of meeting the
subject request
(e.g., whether the sub-wallet contains value tokens associated with vendors,
merchants, and/or
issuers related to the requested transaction). Such determination may be
performed by comparing
electronic value token identifications, user IDs, requested transaction types.
The electronic value
token transaction computer 150 will subsequently evaluate the manner in which
the electronic
value tokens available in the sub-wallet corresponding to the request will be
applied under the sub-
81
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
wallet's rules and/or rules received with the request, and perform or refuse
to perform the
requested transaction and/or transactions.
[00185] Another embodiment may include the electronic value token transaction
computer 150
determining that the entire request received from the E-Wallet Aggregator
System 1000 is related
to value tokens contained in a sub-sub-wallet. Upon receipt of the request,
the electronic value
token transaction computer 150 will query its authorization unit 157 (as
described more fully
herein), its datastore 180, the E-Wallet unit 199, and any other necessary
unit to determine whether
the sub-sub-wallet comprises value tokens capable of meeting the subject
request (e.g., whether the
sub-sub-wallet contains value tokens associated with vendors, merchants,
and/or issuers related to
the requested transaction). Such determination may be performed by comparing
electronic value
token identifications, user IDs, requested transaction types. The electronic
value token transaction
computer 150 will subsequently evaluate the manner in which the electronic
value tokens available
in the sub-sub-wallet corresponding to the request will be applied under the
sub-sub-wallet's rules
and/or rules received with the request, and perform or refuse to perform the
requested transaction
and/or transactions.
[00186] In
another example, an embodiment may include the electronic value token
transaction computer 150 determining that a portion of the request received
from the E-Wallet
Aggregator System 1000 is related to electronic value tokens residing in a sub-
wallet while another
portion of the request is related to electronic value tokens residing in a sub-
sub-wallet. Such
determination may be made by evaluating the requested transaction type, the
electronic value token
identification, or any other methods for determining transaction allocation.
The electronic value
token transaction computer 150 will evaluate the manner in which the
electronic value tokens
available in the sub-wallet corresponding to the request will be applied under
the sub-wallet's rules
(as those rule may affect payment methods to be employed which are located in
the sub-wallet),
the electronic value token transaction computer 150 will evaluate the manner
in which the
electronic value tokens available in any applicable sub-sub-wallet
corresponding to the request will
be applied under such sub-sub-wallet's rules and/or rules received with the
request, and perform or
refuse to perform the requested transaction and/or transactions.
[00187] In an
exemplary embodiment, at block 324, the electronic value token transaction
computer 150 may identify, in response to a received transaction request, one
or more value tokens
in a sub-wallet and one or more electronic value tokens in a sub-sub-wallet
that, when used
82
CA 02897145 2015-07-03
WO 2014/107594 PCT[US2014/010206
together, will cover the entirety of the requested e-wallet transaction.
Moreover, one of the
electronic value tokens located in the sub-wallet or sub-wallet may be an
electronic representation
of a loyalty card and another electronic value token located in either the
same or different location
of said loyalty card value token may be an electronic representation of a
retailer's gift card. In
such an example, the electronic value token transaction computer 150 can
effectuate the
coincidental use of the "loyalty card" token and the "retailer's gift card"
token, regardless of the
tokens' locations in the sub-wallet and/or sub-sub-wallet(s) to allow for an
enhanced user benefit
as opposed to not coincidentally applying the value of the "retailer's gift
card" token and the
"loyalty card" token for the transaction, e.g., a 5% increase in the value of
the "retailer's gift card"
token or loyalty point bonus applied to the "loyalty card" token for the use
of the "retailer's gift
card" token.
[00188] An electronic value token may be associated with a closed loop account
or open loop
account. A closed loop account typically expires after the funds in the
account have been depleted,
e.g. a gift card account. An open loop account does not typically expire.
Rather, there is may be
an ongoing obligation for various entities to credit and debit the account,
e.g. a branded credit card
account or debit card account such as Visa or Mastercard. Closed loop accounts
are often
associated directly with retailers while open loop accounts are often
associated with financial
institutions (e.g., Chase or Citi issued Visa). In at least one embodiment,
the electronic value
tokens comprise closed loop account numbers and open loop account numbers. The
closed loop
account numbers are associated with retailers able to debit or credit closed
loop accounts
associated with the closed loop account number. The open loop account numbers
are associated
with financial institutions able to debit or credit open loop accounts
associated with the open loop
account numbers. The electronic value token may have an expiration date or
specified dates of use
that are different from any other value tokens. Furthermore, the electronic
value tokens may
identify specific merchants, locations, and/or products with which the
electronic value tokens may
be utilized.
[00189] If the request is for electronic value token addition, then in
block 306, the electronic
sub-wallet is created (if not already created) and the electronic value token
is added to the
electronic sub-wallet. The following Tables include elements, parameters, and
information
included in e-wallet transaction communications and used by the electronic
value token transaction
computer 150 to facilitate and effectuate electronic sub-wallet transactions
as part of an
83
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
coincidental primary e-wallet transaction being processed by a primary e-
wallet transaction
processing system, e.g. the E-Wallet Aggregator System 1000.
[00190] Table 8A illustrates request parameters requested to create a sub-
wallet in at least one
embodiment. Table 8B illustrates response parameters requested to create a sub-
wallet in at least
one embodiment.
Table 8A
Request Parameters
Element Data Suggested Description
Type Length
primaryewalletauth string variable Authorization/ID of
primary e-wallet
provider (e.g.,
Google or PayPal)
accounttype String 200 Account Type
loadamt decimal N/A Amount to be loaded
into the wallet
account
loadamtcurrency string 3 Denomination Type.
txn-uniqueidentifier string 12 Unique transaction
id.
Table 8B
Response Parameters
Element Data Type Description
accountid string Unique identifier for a account
accounttype string Type of the account.
currency string Denomination Type.
balance decimal Balance available in the account
uniqueidentifier string (numeric) The unique identifier
identifies a
transaction.
code string The Status of the requested transaction.
description string The Status description of the requested
transaction.
[00191] The electronic value token transaction computer 150 preferably
allocates memory for
the electronic sub-wallet and value token(s) and associates the account number
with the electronic
sub-wallet and/or authentication information stored in the electronic wallet
unit 199 by storing the
84
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
pieces of information in a data structure on the datastore 180. Table 9
illustrates the parameters for
a gift card value token in at least one embodiment.
Table 9
Element and Description Data Type Suggested
Length
statusinfo.status.code String 7
statusinfo.status.description String 500
card.retailer.id Integer 11
String
card.retailer.name String 100
card.number String 50
card.securitycode String 50
card.expirydate Integer String 6
card.activationdate Date String 20
card.initialbalance Decimal String 10
card.currentbalance Decimal String 10
card.currentbalanceasof Date String 20
card.customerservice. String 20
phone
card.customerservice. String 256
website
card.currency String 3
[00192] Table 10 illustrates more detailed parameters for a gift card
electronic value token in an
alternative embodiment, including the designation of associated sub-wallet(s)
and/or sub-sub-
wallet(s).
CA 02897145 2015-07-03
WO 2014/107594
PCT/US2014/010206
Table 10
Element and Description Data Type Suggested
Length
card.retailer.id Integer 11
String
card.retailer.name String 100
card.number String 50
card.securitycode String 50
card .expirydate Integer String 6
card .registeredto String 10
card.activationdate Date String 20
card.initialbalance Decimal 10
String
card.islookedupinitialbalance String 1
card.currentbalance Decimal 10
String
card.islookedupcurrentbalance String 1
card.customerservice. String 20
phone
card.customerservice. String 256
website
card.notes String 500
card.nickname String 100
card.currency String 3
card.user.firstname String 50
card.user.lastname String 50
card.user.address.linel String 50
card.user.address.1ine2 String 50
card.user.address.city String 50
card.user.address.state String 50
card.user.address.zip String 5
card.user.phone.number String 10
card.user.email.address String 128
card.additionalinfol String 300
card.additionalinfo2 String 300
card.additionalinfo3 String 300
wallet.id Integer String 10
Collection offolders
wallet.folder.l.id Integer String 10
wallet.folder.1 .name String 100
wallet.folder.2.id Integer String 10
wallet.folder.2.name String 100
[... More folders]
86
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00193] The request, however, may be modified for other reasons unrelated
to the add token
decision and forwarded to the appropriate one of the issuers' authorization
systems 160 as part of
the reconciliation process, for example the request could concern redemption,
deletion, reloading
value, added value, balance inquiry, or a combination thereof, each of which
would be
communicated to the issuers' authorization systems 160 for reconciliation.
[00194] Table 11 illustrates formatting for authentication communication.
Table 11
Element and Description Data Type
client ref id String
signature String
timestamp String(in the format
yyMMddHHmmssSSSz)
nonce String
encryption_type String
usertoken String
uuid String
user_ip String
channel String
[00195] Each request is authenticated using the signature, a user is
authenticated with
username/password or open id, the session is validated using the user token. A
client may send
client_ref id, timestamp, nonce, encryption_type, channel, user_ip, signature,
optionally usertoken
with each request to be able to validate each message.
[00196] Table 12 illustrates the parameters used to retrieve a user's
wallet.
Table 12
Element Data Type Description
accountid string Unique identifier for a account
accounttype string Type of the account.
currency string Denomination Type.
balance decimal Balance available in the account
code string The Status of the requested transaction.
description string The Status description of the requested
transaction.
87
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
1001971 Table 13A illustrates the request parameters used to redeem value
from a token in the
sub-wallet.
Table 13A
Request Parameters
Element Data Suggested Description
Type Length
accountid String 100 Unique identifier for the account
redamt decimal N/A Amount to redeem from the account
redamtcurrency string 3 Amount Type.
txn-uniqueidentifier string 12 Unique transaction id.
txn- bool N/A 0, if it is not a reversal of any
istimeoutreversal transaction type 1, if it is a reversal
transaction.
1001981 Table 13B illustrates the response parameters used to redeem value
from a token in the
sub-wallet.
Table 13B
Response Parameters
Suggested
Element Data Type Length Description
accountid string 100 Unique identifier for a account
accounttype string 50 Type of the account.
currency string 3 Denomination Type.
balance decimal N/A Balance available in the account
uniqueidentifier string 12 Unique identifier for the
transaction.
code string 7 The Status of the requested
transaction.
description string 500 The Status description of the
requested
transaction.
88
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
1001991 Table 14A illustrates the request parameters used to load a value
token into the sub-
wallet.
Table 14A
Request Parameters
Data Suggested
Element Description
Type Length
accountid string 100 Unique identifier for a account
amount decimal N/A Amount to load on the account
amountcurrency string 3 Amount Type.
txn- bool N/A 0, if it is not a reversal of any
istimeoutreversal transaction type 1, if it is a reversal
transaction.
txn-uniqueidentifier string 12 Unique transaction id.
1002001 Table 14B illustrates the response parameters used to load a value
token into the sub-
wallet.
Table 14B
Response Parameters
Element Data Type Suggested Description
Length
accountid string 100 Unique identifier for a account
accounttype string 50 Type of the account.
balance decimal N/A Balance available in the account
uniqueidentifier string (numeric 12 Unique identifier for
the transaction.
values [0-9] only)
code string 7 The Status of the requested
transaction.
description string 500 The Status description of the
requested transaction.
currency string 3 Denomination Type.
89
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00201] If the request is for electronic value token redemption, then in
block 308, the electronic
value token transaction computer 150 accesses the electronic sub-wallet
previously associated with
the authentication information and examines the rules associated with the
electronic sub-wallet. In
at least one embodiment, examining the rules comprises examining priorities of
value tokens
configurable by the user. For example, the user may prefer to use any closed
loop value tokens
corresponding to the retailer originating the purchase request. If none is
found or if the token will
not cover the purchase, then the user may prefer to use an open loop value
token for the remainder.
As a result of these preferences, the closed loop value tokens may all have
higher priority than the
open loop value tokens. Among the open loop value tokens, one may have
priority over another.
For example, the user prefers to pay for any remainder with a credit card
rather than a debit card.
In at least one embodiment, the user may configure these rules via the
Internet or mobile
application and save the priorities as default preferences. In an alternative
embodiment, the user
selects the electronic value tokens to apply to the electronic wallet request
in at the POS device, for
example at a vendor or retailer location such as a check-out lane, customer
service counter, or
kiosk. As such, selecting the electronic value tokens comprises selecting
value tokens with the
highest priority that, when used together, will cover the purchase amount. As
can be seen in the
example, one purchase transaction has been split into two redemptions without
compromising
efficiency of the purchase. Similarly, one or more electronic wallet
transactions can be split into
two or more transactions without compromising efficiency.
[00202] In at least one embodiment, examining the rules comprises examining
percentages of
the electronic sub-wallet request to which different electronic value tokens
should be applied and
wherein applying the electronic value tokens comprises applying the electronic
value tokens to the
electronic sub-wallet request in according to the percentages. In block 310,
the electronic value
token transaction computer 150 then selects, based on the rules, value tokens
in the electronic sub-
wallet that, when used together, will cover the electronic sub-wallet request.
For example, the user
may configure the rules such that each purchase is split evenly between two
credit cards. As such,
selecting the electronic value tokens comprises selecting two open loop tokens
between which to
split the purchase amount. Similar to the above example, efficiency is
preserved because where a
single authorization token (e.g., only the proxy card or a mobile device) was
used at the point of
sale, not the two credit cards corresponding to the electronic value tokens.
Other rules can be
implemented, and the rules can be used in various combinations and
permutations with each other.
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
The electronic value token computer 150 can also implement "if-then" rules
based on the
information transmitted in the electronic sub-wallet request. For example, a
purchase at a gas
station can result in a gas credit card value token selection, and the like.
In such am embodiment,
the electronic value token computer 150 may query the rule(s) 802, 817, 818,
and 819 of the
subject e-wallet 10 and/or sub-wallets 807 (e.g., for credit card-type
electronic value tokens), 808
(e.g., for debit card-type electronic value tokens), and 809 (e.g., for stored
value-type electronic
value tokens) and determine, based on transaction request information which
includes a transaction
type, e.g., purchase at a gas station, that rule(s) established for the
subject e-wallet 10 and/or sub-
wallets 807, 808, and 809 require that the transaction type request be first
satisfied with a first
electronic value token type, e.g. a gas card-related electronic value token
829, and upon the
occasion that the subject e-wallet 10 and/or sub-wallet(s) 807, 808, and 809
do not comprise a
sufficient amount of the first value token type to satisfy the entire
transaction request, the electronic
value token computer 150 may satisfy the remainder of the transaction request
with a second
electronic value token type, e.g., a debit card-related electronic value token
828.
[00203] The electronic value token transaction computer 150 also applies
the electronic value
tokens to the electronic sub-wallet request. In applying the electronic value
tokens to the request,
the electronic value token transaction computer 150 can generate and send
debit and credit
messages to be performed on the accounts administered by the retailers and
financial institutions
using the appropriate account numbers, or the electronic value token
transaction computer 150 can
credit or debit the accounts directly if the electronic value token
transaction computer has such
administrative authority.
[00204] In at least one embodiment, the electronic value token transaction
computer 150
modifies the request and forwards the modified request to the appropriate one
of the issuers'
authorization systems 160, which receives the modified request and acts upon
same, for example
authorizing and/or processing the request to redeem the electronic value token
and updating a
datastore accordingly. The authorization system 160 is not at the same
location from where the
electronic sub-wallet request was received in at least one embodiment. For
example, if the
electronic sub-wallet request was received from a retail store, the
authorization system may be
owned and operated by the retailer, but will not be at the retail store.
Rather, the authorization
system may be located at a data center for example. As such, neither the
retail store nor the retailer
in general need be aware of some or all the contents of the sub-wallet. In at
least one embodiment,
91
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
the retail store is unaware of even the presence of the electronic wallet, as
it merely recognizes that
some transaction authorizing action has been communicated to its point of sale
(e.g., swipe of a
proxy card, digital personal assistant interaction with point of sale device,
entry of a PIN at a
keypad at point of sale, or other authorizing activity). The issuers'
authorization systems 160
sends a response message back to the electronic value token transaction
computer 150. In an
alternative embodiment where the electronic value token transaction computer
150 performs the
functions of the issuers' authorization systems 160, the method may proceed
directly from block
306 or 310 to block 314.
[00205] The electronic value token transaction computer 150 receives the
confirmation message
from the appropriate one of the issuers' authorization systems 160 in block
312. At block 314, the
electronic value token transaction computer 150 updates electronic sub-wallet
in the electronic
wallet unit 199 and datastore 180 to reflect that the electronic sub-wallet is
activated and to reflect
any debit, credit, addition, or deletion to/of the electronic value token(s).
Figures 9A-D illustrate a
series of user interface screens and prompts in at least one embodiment. For
example, the user
may see the illustrated prompts when managing the user's electronic wallet via
a computer
connected to the Internet, and/or kiosk 189.
[00206] A transaction log 170 may be updated by the electronic value token
transaction
computer 150 in block 316 to record the details about the transaction. The
details recorded in the
transaction log may include (a) the time and date of the transaction, (b)
whether the electronic sub-
wallet was activated, (c) the reason electronic sub-wallet was not activated
if the request was
denied, (d) the credit, debit, addition, or deletion to/of the electronic
value token(s), (e) a change in
rules associated with the electronic value token(s), (f) the identity of the
vendor, (g) the identity of
the issuer, (h) the location of the vendor, (i) the identity of the terminal
adding the electronic value
token, (j) the identity of the entity granting the electronic value token, (k)
identity of the E-Wallet
Aggregator System 1000 from which the sub-wallet request was received, (I)
communications
between the electronic value token transaction computer 150 and the E-Wallet
Aggregator System
1000, and (m) any combination thereof. The transaction log may include other
information in
addition to or in place of the items enumerated above.
[00207] The electronic value token transaction computer 150, in block 319,
then forwards the
sub-wallet transaction results and associated information in the form of a
confirmation message to
the E-Wallet Aggregator System 1000. The electronic value token transaction
computer 150, prior
92
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
to forwarding the confirmation message to the E-Wallet Aggregator System 1000,
may modify the
confirmation message as necessary to include information that may be printed
on a receipt for the
customer and/or presented on a display to the store clerk operating the point
of sale device 111. At
block 320, the electronic value token transaction computer 150 reconciles the
accounts of the
various vendors, merchants, issuers, the electronic value token transaction
processing system
administrator, and other entities involved with issuing, selling, and
marketing the electronic value
tokens involved in the sub-wallet request to debit and credit appropriate
accounts and, in some
embodiments, initiates funds transfers between appropriate bank accounts
belonging to the various
entities. Alternatively, reconciliation of accounts may be performed
periodically (e.g., daily,
weekly, monthly, etc.) rather than after each transaction. In such an
embodiment, the information
from the transaction log 170 may be utilized to reconcile the various entities
involved with the sale
or redemption of various value tokens thus requiring fewer funds transfers to
be initiated. In
various embodiments, the sequence of events depicted in may be varied, and
thus may be carried
out in any desired order, sequentially or simultaneously.
[00208] Figure SC illustrates an embodiment of the electronic value token
transaction
processing system 1200 wherein the electronic value token transaction computer
150
communicates with both the point of sale 111 and the E-Wallet Aggregator
System 1000. Thus,
the electronic value token transaction computer 150 may function as both a
primary electronic
wallet transaction processor and an electronic sub-wallet transaction
processor as described in
detail above with respect to Figures SA and 5B.
[00209] Electronic wallet management may be carried out via a variety of user
interfaces such
as smart phone application, personal computer applications, website based
applications, point of
sale terminals, dedicated terminals at stores or other locations, such as
kiosks.
[00210] In at least one embodiment, a user can perform numerous functions via
the World Wide
Web from a computer or mobile phone such as electronic wallet management
functions (e.g.,
balance inquiry, managing loyalty and/or other bonus-type programs); exchange
of value tokens
such as (i) replace value token in e-wallet with value token not currently
present in e-wallet, (ii)
exchange between different wallets (such as placing an electronic value token
from a sub-wallet
configured to allow redemption activities into a sub-wallet configured for
savings activities with
limited redemption possibilities), and (iii) exchange with another user;
purchase electronic value
tokens to be placed in e-wallet; opt in or opt out of receiving targeted
promotional offers and
93
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
materials; and payment functions such as splitting the tender of payment
between available
electronic value tokens in the e-wallet.
[00211] Regarding possible exchange possibilities, a user may exchange a
value token
associated with a retailer that the user is unlikely to frequent with a value
token associated with a
retailer that the user is likely to frequent. Similarly, users may swap, sell,
gift, or re-gift value
tokens or bundles of value tokens to each other.
[00212] Via e-wallet management functionalities, a user can: (i) determine
the amount of value
associated with each value token such as reward points, dollar amounts, etc.;
(ii) check expiration
dates on value tokens, purchase value tokens for others as gifts, and receive
notifications from
specific retailers; (iii) create, register, and delete their electronic wallet
or specific value tokens in
their electronic wallet; (iv) request that the e-wallet provide or make
available a physical
representation of an electronic value token in the user's electronic wallet
(e.g., in an embodiment,
a print-on-demand service is provided to allow the user to print out a chit,
coupon, check, or other
physical representation of an electronic value token at a kiosk 189 or other
accessible printer); and
(v) allow the e-wallet to send the user specific value tokens, e.g., by using
a GPS service in the
user's mobile phone, or via integration with the user's SMS services.
[00213] In at least one embodiment, the user's electronic wallet is
integrated with the user's
social network services such as Facebook and Twitter. Accordingly, the user
can perform
management functions via social network platforms or receive value tokens via
social network
platforms. Full or partial information about the user's electronic wallet can
be made available to
the user's social network contacts as well.
[00214] As depicted in Figure 9A, a user may access the e-wallet system,
e.g., electronic value
token transaction processing system 100 or E-Wallet Aggregator System 1000,
via such systems'
interactive display pages/screens (wherein the interactive display
pages/screens are accessed via a
user's computer, a user's personal digital assistant or smart phone, point of
sale terminal, kiosk
189, or other device. As Figure 9A depicts, a user may create and/or register
an e-wallet or sub-
wallet by providing certain requested information and agreeing to certain
terms and conditions.
[00215] As depicted in Figure 9B, a user may manage its e-wallet by inputting
certain card
specific information into the e-wallet systems interactive display
page/screen. In an embodiment, a
user may register a gift card by inputting the gift card's brand, card number,
expiration date, CVV2
code, and card nickname and selecting the "Add Gift Card to My Wallet" button
on the screen.
94
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00216] As shown in Figure 9C, a user is provided many options for managing an
e-wallet and
its contents. For example, as shown, a user may review the specific details
associated with the
electronic value tokens (depicted as gift cards in Figure 9C) present in the e-
wallet and/or sub-
wallet. Moreover, the user could request that the electronic value tokens be
presented as: (i) "Last
added" (as shown in Figure 9C); (ii) as contained in various "Sub-wallets"
(sub-wallets could be
categorized or nicknamed, such as "Dining," "Home Improvement," "Debit,"
"Credit," "Loyalty,"
etc.); (iii) as in highest to lowest remaining value; or (iv) as ranked in
regards to preference for use.
[00217] As is also shown in Figure 9C, the user has the ability to "Add a Gift
Card," "Add
Value," "Redeem Card," and "Sell Card."
[00218] The "Add a Gift Card" functionality enables a user to place an
electronic value token
into the e-wallet. The "Add a Gift Card" selection provides at least two
different methods for the
user to add an electronic value token to the e-wallet. First, an electronic
value token representing a
physical card possessed by the user may be added to the e-wallet. As described
in reference to
Figure 9B, by selecting "Add a Gift Card" and the subsequent manner of such
addition, the screen
display of Figure 9B may be presented to the user. Accordingly, the user may
add a "gift card" to
the e-wallet by inputting the gift card's brand, card number, expiration date,
CVV2 code, and card
nickname and selecting the "Add Gift Card to My Wallet" button on the screen.
Alternatively, the
user may have access to a card reader (e.g., mag stripe reader and/or bar code
reader), such as a
device attached to a user's computer, personal digital assistant or smart
phone, and utilize such
device to read information from a physical card, in conjunction with the
user's computer, personal
digital assistant or smart phone, to enter the card's information into the e-
wallet system for
conversion into an electronic value token. Second, an electronic value token
representing a
physical card not already possessed by the user may be added to the e-wallet.
In such an
embodiment, when the user selects this option, the user may be presented a
display screen
informing the user of all the different types and value amounts of electronic
value tokens that are
available for purchase. The availability of electronic value tokens for
purchase can be ascribed to
the e-wallet system's (e.g., the electronic value token transaction processing
system's 100)
relationships with card issuers, merchants, vendors, and/or processors (e.g.,
a GiftCard Mall web-
based application as provided by BlackHawk Network which provides users with
the ability to
select from a variety of different types of gift cards (and varying
denominations) and have the
cards selected delivered to the user (or to a user's identified recipient) in
either tangible form (via
mail or other courier) or delivered electronically (e.g., via the electronic
value token transaction
processing system)) or may be ascribed to the e-wallet system's (e.g., the
electronic value token
transaction processing system's 100) ability to access an electronic value
token exchange
program 2000, as will be described more fully below.
[00219] The "Add Value" functionality enables a user to select an
electronic value token and
increase the value of said token. Such "reloading," "topping off," or
"recharging" of an electronic
value token may be performed as is described in International Application
Serial No.
PCT/US11/40055. For example, when the e- wallet user desires to
reload/recharge/top off a
telecom-related electronic value token residing in the e-wallet, the user can
select "Add Value" on
the display screen which will prompt the system to transmit the
reload/recharge/top-up request to
the electronic value token computer 150.
[00220] In a first embodiment of the reload/recharge/top-up scenario, the
electronic value
token computer 150 approves the request if the telecom-related electronic
value token is activated
and associated with a phone number. The electronic value token computer 150
determines the
telecom account associated with the phone number and adds the requested
reload/recharge/top-
up amount to the account. The electronic value token computer 150 sends a
response to the
request (e.g., indicating that the reload/recharge/top-up amount has been
added to the associated
account). The electronic value token computer 150 transmits a
reload/recharge/top-up transaction
request to the phone number's associated telecom carrier. Upon receiving
approval of the
reload/recharge/top-up transaction request from the telecom carrier, the
electronic value token
computer 150 modifies the value of the telecom-related electronic value token
to reflect the
reload/recharge/top-up amount. The electronic value token computer 150 will
cause the display
accessed by the user to reflect the modification of the electronic value
token's value, or if the
reload/recharge/top-up transaction request was not approved, the electronic
value token
computer 150 will cause the display to inform the user as to that result.
While the "Add Value"
functionality has been described in relation to telecom-related electronic
value tokens, the "Add
Value" functionality is equally applicable and functionable for
reloading/recharging/topping-up
electronic value tokens associated with debit cards, prepaid services cards,
gift cards, etc.
[00221] The "Redeem Card" functionality enables a user to select an
electronic value token
and use that token to satisfy a purchase, or other transaction. In the "Redeem
Card" scenario, if
the whole value of the electronic value token is not used in the redemption
transaction, the system
will
96
CA 2897145 2020-01-22
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
modify/reduce the remaining value of the token and cause the display to inform
the user of the
"new" reduced value of the token, while also informing all interested parties
as to the redemption
transaction and recording and adjusting any pertinent logs accordingly.
Alternatively, when an e-
wallet is used in a point of sale-type of transaction context, rather than the
above described e-wallet
management context, the "Redeem Card" functionality may be automatically
invoked via
transactional information conveyed from a point of sale and thus, the can be
based on
predetermined rules.
[00222] The "Sell Card" functionality enables a user to select an
electronic value token to
monetize via offering the card for sale to (i) another e-wallet user, (ii) the
e-wallet (or sub-wallet)
system provider, or (iii) an electronic value token exchange program 2000 (as
more fully described
herein). In the "Sell Card" scenario, a user will inform the e-wallet system
as to the electronic
value token it desires to sell, select the forum for such sale from a list of
available forums, instruct
the system as to how the proceeds from the sale should be remitted to the e-
wallet (e.g., in the form
of e-wallet system branded electronic value token, value added to other
selected electronic value
token(s), and/or delivery of a hard/tangible form of receipt that the user may
present for tender,
(e.g., chit, coupon, check, or combination thereof)) and, if applicable,
instruct the system as to a
threshold value for the sale of the electronic value token that the user is
not willing to go below
e.g., set a reserve price. The system will execute the desired sale
transaction, and cause the display
to inform the user of the results of the sale of the electronic value token,
while also informing all
interested parties as to the sale transaction and recording and adjusting any
pertinent logs
accordingly.
[00223] As is further shown in Figure 9C, a user may choose to manage "My
Rewards" which
would bring up a screen showing the user options available due to the user's
receipt of loyalty or
other types of rewards for using the e-wallet and/or electronic value tokens.
The user may also
select "Special Offers" which would bring up a screen showing the user any
promotional-type
offerings available to the user via the e-wallet. The user may also select
"Exchange" which would
bring up a screen showing the user options available for electronic value
token exchange via the e-
wallet.
[00224] In similar fashion as described in reference to the above available
e-wallet management
abilities and functionalities, a kiosk 189 may be coupled to the electronic
value token transaction
97
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
computer 150 in at least one embodiment and function as a user's interface
with an e-wallet
transaction system to allow the user to access e-wallet management
functionalities.
[00225] The kiosk 189 may be placed in a high-traffic area such as a shopping
mall, and may
perform any electronic wallet management function. For example, users may
create, delete, and
alter their electronic wallets or sub-wallets. Users may also check the
balances of electronic value
tokens residing in the e-wallet, add, remove, reload, recharge, print, and
exchange value tokens in
their electronic wallets or sub-wallets. The kiosk 189 may mirror transactions
available through an
electronic wallet management website in at least one embodiment, or the
functionality of an e-
wallet enabled personal digital assistant and/or smart phone. Users may employ
a print-on-demand
function with their value tokens if a particular retailer does not accept
electronic wallet
transactions. For example, a user may select a value token to print, and a
printer connected to the
kiosk 189 will print a physical representation of the selected value token,
for example a receipt
having a scannable bar code linked to the electronic value token. The physical
representation may
be a gift card with a magnetic stripe, a paper receipt or coupon with a
barcode or matrix code (e.g.,
QR code), and the like. In an embodiment, kiosk 189 may print a physical card,
for example for an
additional printing fee. The user may also provision and/or partition (e.g.,
create sub-wallets) an
electronic wallet using the kiosk 189. For example, after authentication of
the user and
identification of the electronic wallet associated with the user, the user may
insert the user's
physical stored value cards into the kiosk 189, for example a machine operated
kiosk similar to an
automatic teller machine or alternatively a manned kiosk having appropriate
card readers and the
like. The kiosk 189 may convert the physical stored value cards into
electronic value tokens in the
user's electronic wallet. Afterwards, the physical stored value card may be
retained or destroyed
by the kiosk 189 or returned to the user. In one embodiment, the physical
stored value card is not
usable by the user after the conversion. In another embodiment, the user may
have the option to
use the electronic value token or the physical stored value card. In other
words, both will be
"active" and available for use. The user may also purchase value tokens to
provision a wallet
directly from the kiosk 189.
[00226] In at least one embodiment, a user is associated with multiple
electronic wallets. In
order to identify one wallet out of multiple wallets associated with a user,
each of the multiple
wallets is associated with a unique wallet identification ("ID"). A database
or lookup table, for
98
example, may be used to access wallet identifications. In at least one
embodiment, the wallet ID
is customizable by the user.
[00227] As referenced with respect to both the primary e-wallet and sub-
wallet embodiments
described above, the disclosed e-wallet and sub-wallet methods and systems
provide users with
the ability to add value to electronic value tokens residing in an e-wallet
and/or sub-wallet. In an
embodiment, similar value-added capabilities and functionalities of the
instantly described
electronic value token transaction processing system 100 are detailed and
described in
International Application Serial No. PCT/US11/20570, such similar value-added
capabilities and
functionalities may be adapted from the context described in International
Application Serial No.
PCT/US11/20570 to be applied in the instant e- wallet/electronic value token
context.
[00228] Customers may be offered incentives to purchase and/or redeem a
value token(s) via
value differentiation between the purchase and redemption values of said value
token(s).
[00229] In an embodiment, a value token with a face value of $25 may be
purchased by a
customer for $25, but the electronic value token may be added to the
electronic wallet in the
amount of $30 -the $25 purchase price plus an additional $5 added as an
incentive to purchase
the electronic value token. Alternatively, rather than adding cash value to
the electronic value
token, the electronic value token may be encoded with a redemption coupon code
for a specific
product or service. For example, a $15 value token to a coffee house may have
an electronic
redemption coupon code for a free shot of the customer's syrup of choice to be
added to any
coffee purchased at the coffee house. The free shot of syrup may be redeemed
in connection
with redeeming a portion, or all, of the electronic value token amount or the
free shot of syrup
may be redeemed separately.
[00230] In another embodiment, a value token vendor is able to offer
customers incentives to
redeem a value token by adding value in addition to the value of the
electronic value token at the
time the customer redeems the electronic value token. For example, a merchant
could run a
promotion in which it offers customers an additional $5 credit when the
customer uses a value
token for a purchase at one of the merchant's retail stores during a specified
period of time.
[00231] As noted above, the electronic value token transaction computer 150
communicates
with the datastore 180 and/or the issuers' authorization systems 160. The
electronic value token
transaction computer 150 may compare one or more of the card identification,
the terminal
99
CA 2897145 2020-01-22
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
identification, vendor identification, and the time and date of the activation
request contained
within the transaction request to data contained in the datastore 180 to
determine whether the
electronic value token to be added/redeemed is eligible for a value added
award. For example, a
vendor may run a promotion to encourage customers to purchase a value token,
wherein value
tokens purchased within a specified period of time may be purchased for a
price less than the value
designated by the electronic value tokens description or metadata. Thus, a
customer could
purchase a $25 value token for some amount less than $25, e.g., $20. In either
of the above
examples, the value differentiators, e.g., bonus added to a redemption value
of a value token and
reduction of purchase price for a designated value of a value token, may be
applicable to bundled
value token packages and the value differentiators distributed amongst and/or
across the electronic
value tokens, either equally or disproportionately. Similarly, retailers can
collaborate for cross-
promotions by honoring other retailer's value tokens in full, in part, or for
specific products or
promotions. By selecting to use an electronic wallet at the point of sale, the
user may even receive
the benefits of promotions of which the user was unaware. Furthermore, by
configuring the rules,
the user can be assured of getting the best promotions at various retailers
without comparison
shopping. As such, retailers can implement and change promotions at a rapid
pace and cross-
promote with other retailers on a daily or even hourly basis without spending
advertising resources
to make sure that the user is aware of the promotion and without requiring the
user to perform the
legwork involved in traditional redemption models such as cutting coupons,
inputting various
promotional codes, and the like. Moreover, retailers can finely tune
promotions to various market
segments in order to strengthen relationships by providing for the segment's
particular needs.
[00232] The message modification unit 154 modifies the messages 106 and 110
to add value
added information into the messages. For example, if it is determined by the
value added
determination unit 153 that a value token to be added is eligible for a value
added bonus, the
message 106 received from the point of sale device 111 is modified by the
message modification
unit 154 to include the determined value added bonus and is then forwarded as
message 109 to the
appropriate issuers' authorization system 160 for authorizing the request for
the amount specified
in the activation request plus the value added bonus. As another example, if
it is determined that
the electronic value token is eligible to be purchased at a discount, the
message 106 received from
the point of sale device 111 is modified by the message modification unit 154
(and forwarded as
message 109) to indicate to the appropriate issuers' authorization system 160
that the electronic
100
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
value token will be added to the electronic wallet for one amount, but that
the customer will be
charged a lesser amount reflecting the discount associated with the electronic
value token.
[00233] In an embodiment, the message modification unit 154 also modifies
messages 110 from
the issuers' authorization systems 160 intended for the point of sale device
111 to include any
information regarding value added to the electronic value token that may be
printed on the receipt
generated for the customer as well as information that may be presented to a
cashier on a terminal
101 or 104 that the cashier may communicate to the customer, and such modified
messages are
forwarded as messages 107 to the point of sale device 111.
[00234] As referenced with respect to both the primary e-wallet and sub-wallet
embodiments
described above, the disclosed e-wallet and sub-wallet methods and systems
provide users with the
ability to exchange an electronic value token residing in the user's e-wallet
or sub-wallet with/for
an electronic value token not presently residing in the user's e-wallet or sub-
wallet, but made
available via the e-wallet's or sub-wallet's transaction system(s).
[00235] The electronic value token computer's 150 owner and/or operator may
earn revenue via
arbitrage-type activities. That is, electronic value token computer's 150
owner and/or operator
may keep the difference in going rates between two electronic value tokens,
e.g., a first electronic
value token being traded/exchanged and a second electronic value token being
desired/obtained.
In at least one embodiment, the electronic value token transaction computer
150 may charge the
user transaction fee for the exchange instead. The transaction fee may be flat
or based on the size
of the exchange.
[00236] The electronic value token transaction computer 150 may also charge
either or both of
the issuers and/or retailers associated with the exchange a flat transaction
fee or one based on the
amount of the exchange. these fees may be minimal but generated in high
volume. All parties
may benefit because the user is receiving value tokens the user will use in
exchange for value
tokens the user would not use. Moreover, one issuer and/or retailer is
eliminating the debt or
inventory liability associated with the exchanged value token, thus freeing up
capital for other uses.
Also, the other issuer and/or retailer may be gaining a customer, retaining a
loyal customer, or
increasing revenue if the customer spends more than the amount of the
electronic value token.
[00237] As referenced with respect to both the primary e-wallet and sub-wallet
embodiments
described above, the disclosed e-wallet and sub-wallet methods and systems
provide users with the
ability to exchange electronic value tokens located in e-wallets and/or sub-
wallets for other
101
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
electronic value tokens not located in said e-wallets or sub-wallets. Such
value token exchange
may be initiated (1) by an e-wallet user (i) at a point of sale, (ii) at a
kiosk,(iii) via a user's personal
digital assistant or smart phone, (iv) via web access to the user's e-wallet,
(v) or any other method
of accessing the user's e-wallet; or (2) by an application of an e-wallet rule
by an e-wallet
processing system, wherein the rule is established by (i) the e-wallet user,
(ii) the e-wallet provider,
(iii) or a combination thereof
[00238] In at least one embodiment, exchanging a first value token
associated with a first
retailer located in the e-wallet for a second value token associated with a
second retailer not located
in the e-wallet requires an exchange rate be applied. This exchange rate may
be applied against the
value of the second value token being sought in the exchange, thus reducing
the face value of the
second value token is relation to the value of the first value token for which
it is exchanged or the
exchange rate may be applied against some other valued asset located in the e-
wallet (as prescribed
by any pertinent rules or directives). The exchange rate may be realized by
the e-wallet processing
system and/or shared with designated vendors, merchants, and issuers.
[00239] The exchange rate may established via an ongoing valuation program
operated by the
e-wallet processing system or affiliated entity comprising the tracking of the
use of and interest in
electronic value tokens, gift cards (or other similar instruments), the
acquisition of such electronic
value tokens, gift cards (or other similar instruments) from other e-wallet
users or other sources,
and the establishment of dynamically varying values for all such electronic
value tokens and gift
card-type instruments available to the e-wallet processing system for
incorporation into an
electronic value token exchange program.
[00240] The above-described electronic value token exchange program may be
exemplified by
the following discussion. An e-wallet user can approach an e-wallet associated
kiosk 189 at
Retailer A's establishment. The e-wallet user interfaces with the kiosk 189
and provides the kiosk
with e-wallet identifying information (e.g., as described in Table 1 herein
"accountid"). The
provision of identifying information may be made via manual input by the
kiosk's user or may be
made automatically via communication between the e-wallet user's personal
digital assistant (or
proxy card 200) and the kiosk 189. The e-wallet user may then use the kiosk
189 to access the e-
wallet' s electronic value token exchange program and the kiosk 189 may be
further used to
facilitate and complete any requested electronic value token exchange. In an
embodiment, the e-
wallet user may wish to exchange an electronic value token issued and/or
accepted by Retailer B
102
contained in the user's e-wallet (or a sub-wallet thereof) for an electronic
value token issued
and/or accepted by Retailer A. The e-wallet user interfacing with kiosk 189
can result in the e-
wallet user being presented with a screen display such as is depicted in
Figure 9C. Besides
providing the e- wallet user with the ability to review the contents of the e-
wallet, the display allows
the e-wallet user to select an "Exchange" tab from the available
functionalities. The "Exchange"
tab will then present the e-wallet user with the options available for
electronic value token
exchange. As depicted in Figure 9D, such options can comprise: (1) view a
selection of electronic
value token(s) available for acquisition; (2) view the selection of electronic
value token(s)
presently residing in e- wallet; (3) view the various exchange rates for the
identified electronic
value token(s) for acquisition as calculated in view of the electronic value
tokens selected for
removal (exchange) from the e-wallet (exchange rates may vary based on
types/retailers of
electronic value tokens selected for exchange); (4) view options for
satisfying exchange rate (e.g.,
(i) reduction in value of electronic value token selected for acquisition to
meet the exchange rate
or (ii) application of the amount of the exchange rate to some other asset
residing in the e-wallet
such as a credit card value token or a debit card value token); (5) view a
selection of options for
delivery of the electronic value token selected for acquisition such as (i)
delivery into the e-wallet
(or sub-wallet), (ii) delivery via email, SMS, social media, or other
electronic method to a personal
digital assistant or computer, (iii) print out of a tangible version of the
electronic value token (e.g.,
via print on receipt-type capability as described in U.S. Patent Application
Serial No. 12/719,741)
at the kiosk or other user-selected print device. The user may make its
desired selections in
response to the information provided in each of the above- describe screens,
as each of the
described screen view options include functionality allowing for selection of
the displayed options.
In this example, the user selects that the Retailer B $25.00 electronic value
token residing in the
e-wallet is to be exchanged for a Retailer A electronic value token. As a
result, the electronic value
token exchange program prompts the kiosk 189 to display that the requested
exchange will result
in the user acquiring a Retailer A electronic value token in the amount of
$24.75 if the user selects
that the exchange rate be applied against the value of the Retailer A
electronic value token (the
exchange rate will vary from transaction to transaction, the exchange rate
could be any value,
e.g., $0.001 to $10.00, or any values below, within, or above this range). The
user makes such
selection. The electronic value token exchange program prompts the kiosk 189
to display the
available delivery methods and the user selects delivery into the e-wallet.
103
CA 2897145 2020-01-22
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
The electronic value token exchange program prompts the kiosk 189 to display
another screen
similar to Figure 9C, but indicating that the e-wallet now contains a Retailer
A electronic value
token in the amount of $24.75.
[00241] As a result of the above "Exchange" transaction, the e-wallet user
received its desired
Retailer A electronic value token and the electronic value token exchange
program received a
Retailer B $25.00 electronic value token. As part of the above-described
transaction, the electronic
value token exchange program contacted the electronic value token issuing
entity of Retailer A
electronic value tokens (e.g., in an embodiment issuing entity of Retailer A
electronic value tokens
could be the electronic value token exchange program 2000) and requested a
Retailer A $24.75
electronic value token be provided to meet the e-wallet user's request;
alternatively, the electronic
value token exchange program modified a Retailer A electronic value token it
already controlled,
e.g., modified a Retailer A $25.00 electronic value token to only be worth
$24.75 and informed the
issuing entity of Retailer A electronic value tokens that it could reduce its
liability associated with
said card by $0.25. Further, the electronic value token exchange program 2000
will contact the
Retailer B electronic value token issuer and provide the issuer with the
appropriate Retailer B
$25.00 electronic value token identification so that the issuer can remove
that Retailer B $25.00
electronic value token from its list of liabilities. Thus, as an end result,
the electronic value token
exchange program's activities have resulted in a $0.25 value (the exchange
rate, i.e., difference in
value of electronic value token acquired by requesting user and electronic
value token surrendered
by requesting user as part of the exchange) that may be allocated to
interested parties per
established contractual obligations.
[00242] In an alternative scenario, if the e-wallet requesting user selects
the exchange rate to be
satisfied by another asset residing in the e-wallet or sub-wallet, such as a
credit card electronic
value token or a debit card electronic value token, the e-wallet user would be
provided with a
$25.00 Retailer A electronic value token matching the $25.00 Retailer A
electronic value token
surrendered in the transaction and the exchange rate of $0.25 would be
realized from charging
against the credit card electronic value token or debiting against the debit
card electronic value
token. Such actions would be transacted with communications between the
electronic value token
exchange program and the credit card electronic value token or the debit card
electronic value
token requesting that the $0.25 exchange rate value be paid to the electronic
value token exchange
program. Thus, again as an end result, the electronic value token exchange
program's activities
104
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
would have resulted in a $0.25 value (the exchange rate) that may be allocated
to interested parties
per established contractual obligations.
[00243] The above-described electronic value token exchange transaction (or
any described
variation thereof), although described in the kiosk 189 context, could also be
performed at point of
sale, via a personal digital assistant with e-wallet functionality, or via a
computer with access the
user's e-wallet.
[00244] In an alternative electronic value token exchange embodiment, as
discussed previously,
the e-wallet may automatically direct electronic value token exchange
activities. For example, the
e-wallet user may manage the e-wallet so that upon the occasion when the user
presents the e-
wallet to satisfy a transaction at retail establishment, e.g., Retailer Q, and
the e-wallet contains no
Retailer Q branded electronic value tokens, the e-wallet will automatically,
and in real time, initiate
an electronic value token exchange process wherein the e-wallet communicates a
request for
electronic value token exchange to the electronic value token transaction
computer 150. In this
example, the e-wallet user has managed the e-wallet so that all electronic
value tokens associated
with prepaid services (gift card-type electronic value tokens) are located in
a designated sub-wallet
and each of said electronic value tokens were placed/ordered/designated in the
sub-wallet via a
preferential ranking system, e.g., most preferred electronic value token or
token type (e.g., #1) to
least preferred electronic value token or token type (e.g., #22, if there are
22 types of electronic
value tokens in the sub-wallet. For example, Retailer M branded electronic
value tokens may be
designated as most preferred and Retailer L branded electronic value tokens
may be designated as
least preferred. Further in the example, the e-wallet also has been provided
with rules by the user
that directs the e-wallet, in circumstances wherein the e-wallet has been
presented to facilitate a
transaction at a retailer in which the e-wallet contains none of said
retailer's electronic value tokens
(the e-wallet will recognize the retailer based on information exchanged
between the e-wallet and
the retailer's communication devices at the onset of the original
transaction), such as the Retailer Q
scenario described above, the e-wallet rules direct the e-wallet to initiate
an electronic value token
exchange request and to include in said request the exchange of the least
preferred electronic value
token residing in the e-wallet, i.e., the Retailer L branded electronic value
token (#22) and if
necessary preferred electronic value token #21, #20, etc., for a Retailer Q
electronic value token in
an amount sufficient to meet the original transaction's amount. The electronic
value token
transaction computer 150, upon receipt of the electronic value token exchange
request,
105
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
communicates with an electronic value token exchange program 2000, e.g., an
electronic value
token distributor, (which is part of the overall electronic value token
transaction processing system
100) to effectuate the requested electronic value token exchange. The
requested electronic value
token exchange is performed, the e-wallet receives the requested Retailer Q
branded electronic
value token, which is coincidentally used in conducting the original
transaction, and the e-wallet
surrenders (or makes unavailable for use and only available for modification)
the Retailer L
branded electronic value token to the electronic value token transaction
computer 150, which in
this case was actually valued in excess of the requested Retailer Q branded
electronic value token.
As such, the electronic value token transaction computer 150, modifies the
value of the Retailer L
branded electronic value token (either internally or via communication with
the Retailer L branded
electronic value token's issuing system) to reflect the value reduction based
on the provided
Retailer Q branded electronic value token, extracts the exchange rate for the
exchange of the
Retailer Q branded electronic value token for the Retailer L branded
electronic value token (as will
be discussed more fully herein), communicates the transactional information to
all interested
parties, and returns (or makes available again) the value-modified Retailer L
branded value token
to the user's e-wallet.
[00245] In an alternate embodiment, the e-wallet's electronic value token
exchange rules could
have provided that the e-wallet query the electronic value token transaction
computer 150
regarding the best available exchange rate for the electronic value tokens
residing in the e-wallet
and make the exchange based on the best exchange rate rather than the ranking
of the electronic
value tokens. Further the e-wallet user may subjectively determine which
electronic token(s)
should be exchanged to satisfy a transaction.
[00246] In an embodiment, the electronic token exchange program 2000 may
survey a user's e-
wallets and sub-wallets maintained by the electronic value token transaction
computer 150 and
make the e-wallet user an offer(s) for electronic value token exchange(s). For
example, the
electronic token exchange program 2000, as part of the survey may determine,
based on (i) the
history of the e-wallet's use; (ii) the length of time an unused electronic
value token has resided in
an e-wallet; (iii) the demand for certain electronic value tokens in the
marketplace; (iv) dates for
spoilage of electronic value tokens; (v) promotional offers for acquiring
electronic value tokens;
and (vi) combinations thereof, to offer an e-wallet user to exchange an
electronic value token(s)
presently residing in the user's e-wallet/sub-wallet for an electronic value
token(s) not presently
106
residing in the user's e-wallet/sub-wallet. In an embodiment, the electronic
token exchange
program 2000 may supplement the offer for exchange with a value added/bonus
incentive as
described previously herein. In another embodiment, the offer may include an
option for the user
to place a portion of the exchange value amount into a savings wallet, as will
be more fully below.
[00247] As referenced with respect to both the primary e-wallet and sub-
wallet embodiments
described above, the disclosed e-wallet and sub-wallet methods and systems
provide users with
the ability to designate the locations of value tokens residing in an e-wallet
or sub-wallet, as well
as rules prescribing the use and/or availability of said e-wallet and/or sub-
wallet. As also
described herein, electronic value token(s) may be removed from a sub-wallet
configured to allow
redemption activities (hereinafter "fully-redeemable" designated e-wallet or
sub-wallet) and
placed into a sub-wallet configured for savings activities with limited
redemption possibilities
(hereinafter "savings" designated e-wallet or sub-wallet). In fact, the
instant system provides for
electronic value token(s) to be placed into a "savings" designated e-wallet or
sub-wallet at the
time the electronic value token is made available to the e-wallet or sub-
wallet.
[00248] In an embodiment, electronic value tokens may be designated for
and/or placed in
certain e-wallets and/or sub-wallets which have rules providing that the e-
wallets or sub-wallets
are to be used for savings activities and thus are not readily available for
general access or for
redemption/exchange activities. In an embodiment, similar savings
capabilities, functionalities,
requirements, and limitations of the instantly described electronic value
token transaction
processing system 100 are detailed and described in International Application
Serial No.
PCT/US11/49338, such similar savings capabilities, functionalities,
requirements, and limitations
may be adapted from the context described in International Application Serial
No.
PCT/US11/49338 to be applied in the instant e- wallet/electronic value token
context.
[00249] At least in some embodiments, allows a user to easily redistribute
electronic value
tokens (e.g., debit card-related electronic value tokens) from a "fully-
redeemable" designated e-
wallet or sub-wallet to a "savings" designated e-wallet or sub-wallet, and
vice versa. The user
may be limited by law to a given number of, e.g., six, transfers out of the
"savings" designated e-
wallet or sub-wallet to the "fully-redeemable" designated e-wallet or sub-
wallet per calendar
month. The user may designate one-time transfers through the e-wallet system's
website, IVR,
personal digital assistant or smart phone, or with a customer service
representative. The user
may also establish
107
CA 2897145 2020-01-22
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
and automated transfers between the "fully-redeemable" designated e-wallet or
sub-wallet and the
"savings" designated e-wallet or sub-wallet. To encourage savings, users may
be presented with
option to automatically fund the "savings" designated e-wallet or sub-wallet
from the "fully-
redeemable" designated e-wallet or sub-wallet that may be triggered by various
transaction events,
including: (a) upon receiving a direct deposit, (b) when a
reload/recharge/topping up transaction
occurs, and/or (c) at a designated time interval (e.g., recurring weekly or
monthly). The user can
elect all, some, or none of the options available. Moreover, the above events
may be transacted
regardless of the "fully-redeemable" designated or "savings" designated e-
wallet or sub-wallet's
current balance. The user may have the ability to select an amount or percent
of electronic value
tokens loaded onto "fully-redeemable" designated e-wallet or sub-wallet. Where
the user chooses
a time interval for automatic transfers, the user may be able to select a
preferred date. The user
would have the flexibility to update, edit, or otherwise change the automatic
funding option at any
time. Any negative "fully-redeemable" designated e-wallet or sub-wallet may
need to be cured
prior to initiating any automatic or one-time transfers to "savings"
designated e-wallet or sub-
wallet. If an automatic transfer cannot be fully funded or cannot be funded at
all, any amounts
available will be taken from the "fully-redeemable" designated e-wallet or sub-
wallet to the
"savings" designated e-wallet or sub-wallet and a notification will be
provided to the e-wallet user
describing the transaction. Automatic transfers will continue thereafter for
the designated transfer
option and amount.
[00250] The electronic value token transaction computer 150 above may be
implemented on
any particular machine with sufficient processing power, memory resources, and
network
throughput capability to handle the necessary workload placed upon it.
[00251] All of, or a portion of, the system described above may be implemented
on any
particular machine (or machines), e.g., any particular electronic component
(or electronic
components), with sufficient processing power, memory resources, and
throughput capability to
handle the necessary workload placed upon the computer, or computers. Figure 8
illustrates a
computer system 580 suitable for implementing all, or a portion of, one or
more embodiments
disclosed herein. The computer system 580 includes a processor 582 (which may
be referred to as
a central processor unit or CPU) that is in communication with memory devices
including
secondary storage 584, read only memory (ROM) 586, random access memory (RAM)
588,
108
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
input/output (I/O) devices 590, and network connectivity devices 592. The
processor 582 may be
implemented as one or more CPU chips.
[00252] It is understood that by programming and/or loading executable
instructions onto the
computer system 580, at least one of the CPU 582, the RAM 588, and the ROM 586
are changed,
transforming the computer system 580 in part into a particular machine or
apparatus having the
novel functionality taught by the present disclosure. It is fundamental to the
electrical engineering
and software engineering arts that functionality that can be implemented by
loading executable
software into a computer can be converted to a hardware implementation by well
known design
rules. Decisions between implementing a concept in software versus hardware
typically hinge on
considerations of stability of the design and numbers of units to be produced
rather than any issues
involved in translating from the software domain to the hardware domain.
Generally, a design that
is still subject to frequent change may be preferred to be implemented in
software, because re-
spinning a hardware implementation is more expensive than re-spinning a
software design.
Generally, a design that is stable that will be produced in large volume may
be preferred to be
implemented in hardware, for example in an application specific integrated
circuit (ASIC), because
for large production runs the hardware implementation may be less expensive
than the software
implementation. Often a design may be developed and tested in a software form
and later
transformed, by well known design rules, to an equivalent hardware
implementation in an
application specific integrated circuit that hardwires the instructions of the
software. In the same
manner as a machine controlled by a new ASIC is a particular machine or
apparatus, likewise a
computer that has been programmed and/or loaded with executable instructions
may be viewed as
a particular machine or apparatus.
[00253] The secondary storage 584 is typically comprised of one or more
disk drives or tape
drives and is used for non-volatile storage of data and as an over-flow data
storage device if RAM
588 is not large enough to hold all working data. Secondary storage 584 may be
used to store
programs which are loaded into RAM 588 when such programs are selected for
execution. The
ROM 586 is used to store instructions and perhaps data which are read during
program execution.
ROM 586 is a non-volatile memory device which typically has a small memory
capacity relative to
the larger memory capacity of secondary storage 584. The RAM 588 is used to
store volatile data
and perhaps to store instructions. Access to both ROM 586 and RAM 588 is
typically faster than
to secondary storage 584. The secondary storage 584, the RAM 588, and/or the
ROM 586 may be
109
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
referred to in some contexts as computer readable storage media and/or non-
transitory computer
readable media.
[00254] I/O devices 590 may include printers, video monitors, liquid
crystal displays (LCDs),
touch screen displays, keyboards, keypads, switches, dials, mice, track balls,
voice recognizers,
card readers, paper tape readers, or other well-known input devices.
[00255] The network connectivity devices 592 may take the form of modems,
modem banks,
Ethernet cards, universal serial bus (USB) interface cards, serial interfaces,
token ring cards, fiber
distributed data interface (FDDI) cards, wireless local area network (WLAN)
cards, radio
transceiver cards such as code division multiple access (CDMA), global system
for mobile
communications (GSM), long-term evolution (I,TE), worldwide interoperability
for microwave
access (WiMAX), and/or other air interface protocol radio transceiver cards,
and other well-known
network devices. These network connectivity devices 592 may enable the
processor 582 to
communicate with the Internet or one or more intranets. With such a network
connection, it is
contemplated that the processor 582 might receive information from the
network, or might output
information to the network in the course of performing the above-described
method steps. Such
information, which is often represented as a sequence of instructions to be
executed using
processor 582, may be received from and outputted to the network, for example,
in the form of a
computer data signal embodied in a carrier wave.
[00256] Such information, which may include data or instructions to be
executed using
processor 582 for example, may be received from and outputted to the network,
for example, in the
form of a computer data baseband signal or signal embodied in a carrier wave.
The baseband
signal or signal embedded in the carrier wave, or other types of signals
currently used or hereafter
developed, may be generated according to several methods well known to one
skilled in the art.
The baseband signal and/or signal embedded in the carrier wave may be referred
to in some
contexts as a transitory signal.
[00257] The processor 582 executes instructions, codes, computer programs,
scripts which it
accesses from hard disk, floppy disk, optical disk (these various disk based
systems may all be
considered secondary storage 584), ROM 586, RAM 588, or the network
connectivity devices 592.
While only one processor 582 is shown, multiple processors may be present.
Thus, while
instructions may be discussed as executed by a processor, the instructions may
be executed
simultaneously, serially, or otherwise executed by one or multiple processors.
Instructions, codes,
110
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
computer programs, scripts, and/or data that may be accessed from the
secondary storage 584, for
example, hard drives, floppy disks, optical disks, and/or other device, the
ROM 586, and/or the
RAM 588 may be referred to in some contexts as non-transitory instructions
and/or non-transitory
information.
[00258] In an embodiment, the computer system 580 may comprise two or more
computers in
communication with each other that collaborate to perform a task. For example,
but not by way of
limitation, an application may be partitioned in such a way as to permit
concurrent and/or parallel
processing of the instructions of the application. Alternatively, the data
processed by the
application may be partitioned in such a way as to permit concurrent and/or
parallel processing of
different portions of a data set by the two or more computers. In an
embodiment, virtualization
software may be employed by the computer system 580 to provide the
functionality of a number of
servers that is not directly bound to the number of computers in the computer
system 580. For
example, virtualization software may provide twenty virtual servers on four
physical computers.
In an embodiment, the functionality disclosed above may be provided by
executing the application
and/or applications in a cloud computing environment. Cloud computing may
comprise providing
computing services via a network connection using dynamically scalable
computing resources.
Cloud computing may be supported, at least in part, by virtualization
software. A cloud computing
environment may be established by an enterprise and/or may be hired on an as-
needed basis from a
third party provider. Some cloud computing environments may comprise cloud
computing
resources owned and operated by the enterprise as well as cloud computing
resources hired and/or
leased from a third party provider.
[00259] In an embodiment, some or all of the functionality disclosed above may
be provided as
a computer program product. 1 he computer program product may comprise one or
more computer
readable storage medium having computer usable program code embodied therein
to implement
the functionality disclosed above. The computer program product may comprise
data structures,
executable instructions, and other computer usable program code. The computer
program product
may be embodied in removable computer storage media and/or non-removable
computer storage
media. The removable computer readable storage medium may comprise, without
limitation, a
paper tape, a magnetic tape, magnetic disk, an optical disk, a solid state
memory chip, for example
analog magnetic tape, compact disk read only memory (CD-ROM) disks, floppy
disks, jump
drives, digital cards, multimedia cards, and others. The computer program
product may be suitable
111
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
for loading, by the computer system 580, at least portions of the contents of
the computer program
product to the secondary storage 584, to the ROM 586, to the RAM 588, and/or
to other non-
volatile memory and volatile memory of the computer system 580. The processor
582 may
process the executable instructions and/or data structures in part by directly
accessing the computer
program product, for example by reading from a CD-ROM disk inserted into a
disk drive
peripheral of the computer system 580. Alternatively, the processor 582 may
process the
executable instructions and/or data structures by remotely accessing the
computer program
product, for example by downloading the executable instructions and/or data
structures from a
remote server through the network connectivity devices 592. Ihe computer
program product may
comprise instructions that promote the loading and/or copying of data, data
structures, files, and/or
executable instructions to the secondary storage 584, to the ROM 586, to the
RAM 588, and/or to
other non-volatile memory and volatile memory of the computer system 580.
[00260] In some contexts, the secondary storage 584, the ROM 586, and the RAM
588 may be
referred to as a non-transitory computer readable medium or a computer
readable storage media.
A dynamic RAM embodiment of the RAM 588, likewise, may be referred to as a non-
transitory
computer readable medium in that while the dynamic RAM receives electrical
power and is
operated in accordance with its design, for example during a period of time
during which the
computer 580 is turned on and operational, the dynamic RAM stores information
that is written to
it. Similarly, the processor 582 may comprise an internal RAM, an internal
ROM, a cache
memory, and/or other internal non-transitory storage blocks, sections, or
components that may be
referred to in some contexts as non-transitory computer readable media or
computer readable
storage media.
[00261] The ordering of steps in the various processes, data flows, and
flowcharts presented are
for illustration purposes and do not necessarily reflect the order that
various steps must be
performed. The steps may be rearranged in different orders in different
embodiments to reflect the
needs, desires and preferences of the entity implementing the systems.
Furthermore, many steps
may be performed simultaneously with other steps in some embodiments.
[00262] Also, techniques, systems, subsystems and methods described and
illustrated in the
various embodiments as discrete or separate may be combined or integrated with
other systems,
modules, techniques, or methods without departing from the scope of the
present disclosure. Other
items shown or discussed as directly coupled or communicating with each other
may be coupled
112
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
through some interface or device, such that the items may no longer be
considered directly coupled
to each other but may still be indirectly coupled and in communication,
whether electrically,
mechanically, or otherwise with one another. Other examples of changes,
substitutions, and
alterations are ascertainable by one skilled in the art and could be made
without departing from the
spirit and scope disclosed. The following numbered entries represent a non-
exhaustive collection
of exemplary embodiments of the instantly disclosed subject matter:
[00263] 1. A computer implemented method, comprising:
receiving a request to process a payment transaction against an electronic
wallet;
identifying authentication information of the request;
identifying a value token in the electronic wallet; and
applying at least a portion of the value token to at least a portion of the
request.
[00264] 2. The method of 1, further comprising:
accepting an authentication token to access the electronic wallet.
[00265] 3. The method of 2, wherein the authentication information is based
on the
authentication token, wherein the authentication token comprises a proxy card,
a mobile device, a
password, a biometric identifier, or combinations thereof
[00266] 4. The method of 1, wherein the electronic wallet comprises a
primary wallet and a
sub-wallet.
[00267] 5. The method of 4, further comprising:
processing at least a portion of the request via the primary wallet.
[00268] 6. The method of 4, further comprising:
processing at least a portion of the request via the sub-wallet.
[00269] 7. the method of 4, wherein the primary wallet comprises the value
token, the method
further comprising:
determining the request is related to the primary wallet; and
determining the value token is capable of meeting the request.
[00270] 8. The method of 7, wherein applying at least a portion of the
value token comprises
applying at least a portion of the value token of the primary wallet to the
request.
113
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00271] 9. The method of 4, wherein the sub-wallet comprises the value
token, the method
further comprising:
determining the request is related to the sub-wallet; and
determining the value token is capable of meeting the request.
[00272] 10. The method of 9, wherein applying at least a portion of the
value token comprises
applying at least a portion of the value token of the sub-wallet to the
request.
[00273] 11. The method of 4, wherein the electronic wallet comprises two or
more value
tokens, wherein the primary wallet comprises at least one of the two or more
value tokens, wherein
the sub-wallet comprises at least another of the two or more value tokens.
[00274] 12. The method of 11, further comprising:
determining a portion of the request is related to the primary wallet; and
determining another portion of the request is related to the sub-wallet.
[00275] 13. The method of 12, further comprising:
applying at least a portion of the primary wallet's value token to the
request; and
applying at least a portion of the sub-wallet's value token to the request.
[00276] 14. The method of 8 or 13, wherein the value token of the primary
wallet is applied to
the request under a rule of the primary wallet or the request.
[00277] 15. The method of 10 or 13, wherein the value token of the sub-
wallet is applied to the
request under a rule of the sub-wallet or the request.
[00278] 16. The method of 4, wherein an aggregator system receives the
request, the method
further comprising:
determining at least a portion of the request may be processed in the sub-
wallet; and
sending the portion of the request from the aggregator system to a third
party.
[00279] 17. The method of 1, wherein the request includes an identity of a
point of sale
terminal; authentication information; an amount of a purchase; an identity of
the value token
issuer; an identity of a vendor; an identity of a location; a time of the
request; a date of the request;
information identifying a primary wallet, sub-wallet, or a combination
thereof; transaction data;
authentication data; or combinations thereof.
[00280] 18. The method of 1, wherein the value token comprises an
electronic representation of
value, wherein the electronic representation of value comprises a credit card,
debit card, gift card,
prepaid telephone card, loyalty card, membership card, ticket or ticket card,
entertainment card,
114
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
sports card, prepaid card, coupon, admission pass, prepaid or pre-purchases of
goods or services,
cash, currency, credit card account, debit card account, merchant account,
bank account, merchant-
issued credit, merchant-issued point, merchant-issued promotional value,
merchant-accepted
credit, merchant-accepted point, merchant-accepted promotional value, or
combinations thereof.
[00281] 19. The method of 18, wherein the value token further comprises at
least two
electronic representations of value of different types.
[00282] 20. The method of 1, wherein the value token comprises a closed loop
account
number, wherein applying at least a portion of the value token comprises
crediting or debiting a
closed loop account associated with the closed loop account number.
[00283] 21. The method of 1, wherein the value token comprises an open loop
account number,
wherein applying at least a portion of the value token comprises crediting or
debiting an open loop
account associated with the open loop account number.
[00284] 22. The method of 1, wherein applying at least a portion of the
value token comprises
using the value token according to a set of configurable rules specifying
priority of the value
tokens.
[00285] 23. The method of 22, wherein the priority is based on a
transaction information
variable comprising physical location of a retailer originating the electronic
wallet request;
transaction amount; type of retailer; time of day; day of week; week of month;
month of year;
department of retailer originating the electronic wallet request; lane of
retailer originating the
electronic wallet request; identification of checker; parent company of a
retailer originating the
electronic wallet request; value of value tokens; type of the electronic
wallet request; or
combinations thereof.
[00286] 24. The method of 1, wherein applying at least a portion of the
value token comprises
using the value token according to a set of configurable rules specifying
percentages of the
electronic wallet request to which value tokens may be applied.
[00287] 25. The method of 1, further comprising:
examining a rule associated with the electronic wallet.
[00288] 26. The method of 25, wherein examining a rule comprises:
examining a priority of the value token.
[00289] 27. The method of 25, wherein examining a rule comprises:
examining a percentage of the request;
115
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
wherein applying at least a portion of the value token comprises applying at
least a portion
of the value token to the request according to the percentage.
[00290] 28. The method of 1, wherein the electronic wallet comprises a
closed loop-related
value token and an open loop-related value token, the method further
comprising:
selecting the closed loop-related value token; and
then selecting the open loop-related value token.
[00291] 29. The method of 1, wherein the electronic wallet comprises an
open loop-related
value token, the method further comprising:
withholding the open loop-related value token from being applied to the
request.
[00292] 30. The method of 1, further comprising:
exchanging at least a portion of the value token of the electronic wallet for
at least a portion
of a second value token not located in the electronic wallet.
[00293] 31. The method of 30, further comprising:
applying an exchange rate against the second value token or an asset located
in the
electronic wallet.
[00294] 32. The method of 30, wherein exchanging at least a portion of the
value token
comprises:
contacting a second value token distributor; and
requesting the second value token distributor to provide the second value
token.
[00295] 33. The method of 1, wherein the electronic wallet comprises a
first sub-wallet and a
second sub-wallet, wherein the first sub-wallet comprises the value token, the
method further
comprising:
placing the value token of the first sub-wallet into the second sub-wallet.
[00296] 34. The method of 1, further comprising:
provisioning the electronic wallet with the value token.
[00297] 35. The method of 34, wherein the value token is provisioned in an
amount different
than the purchase price.
[00298] 36. The method of 34, wherein provisioning the electronic wallet
comprises encoding
the value token with a coupon code.
[00299] 37. The method of 34, wherein provisioning the electronic wallet
comprises adding the
value token to the electronic wallet.
116
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00300] 38. The method of 1, wherein the electronic wallet comprises a
savings-designated
sub-wallet, the method further comprising:
placing at least a portion of the value token in the savings-designated sub-
wallet.
[00301] 39. A computer implemented method, comprising:
receiving a request to process a payment transaction against an electronic
wallet;
determining the request contains valid authentication information;
determining a value token, or a combination of value tokens, associated with
the electronic
wallet is capable of meeting the request; and
applying at least a portion of the value token to at least a portion of the
request.
[00302] 40. The method of 39, further comprising:
accepting an authentication token to access the electronic wallet.
[00303] 41. The method of 40, wherein the authentication information is
based on the
authentication token, wherein the authentication token comprises a proxy card,
a mobile device, a
password, a biometric identifier, or combinations thereof.
[00304] 42. The method of 39, wherein the electronic wallet comprises a
primary wallet and a
sub-wallet.
[00305] 43. The method of 42, further comprising:
processing at least a portion of the request via the primary wallet.
[00306] 44. The method of 43, further comprising:
processing at least another portion of the request via the sub-wallet.
[00307] 45. The method of 42, wherein the primary wallet comprises the value
token, the
method further comprising:
determining the request is related to the primary wallet;
wherein applying at least a portion of the value token comprises applying at
least a portion
of the value token of the primary wallet to the request.
[00308] 46. The method of 42, wherein the sub-wallet comprises the value
token, the method
further comprising:
determining the request is related to the sub-wallet;
wherein applying at least a portion of the value token comprises applying at
least a portion
of the value token of the sub-wallet to the request.
117
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00309] 47. The method of 42, wherein the electronic wallet comprises two or
more value
tokens, wherein the primary wallet comprises at least one of the two or more
value tokens, wherein
the sub-wallet comprises at least another of the two or more value tokens.
[00310] 48. The method of 47, further comprising:
determining a portion of the request is related to the primary wallet; and
determining another portion of the request is related to the sub-wallet.
[00311] 49. The method of 48, further comprising:
applying at least a portion of the primary wallet's value token to the
request; and
applying at least a portion of the sub-wallet's value token to the request.
[00312] 50. The method of 45 or 49, wherein the value token of the primary
wallet is applied to
the request under a rule of the primary wallet or the request.
[00313] 51. The method of 46 or 49, wherein the value token of the sub-
wallet is applied to the
request under a rule of the sub-wallet or the request.
[00314] 52. The method of 42, wherein an aggregator system receives the
request, the method
further comprising:
determining at least a portion of the request may be processed in the sub-
wallet; and
sending the portion of the request from the aggregator system to a third
party.
[00315] 53. A method for a sub-wallet in an electronic wallet system, the
method comprising:
receiving a request to process a payment transaction against an electronic
wallet from a
provider of a primary wallet
determining a value token is capable of meeting the request; and
applying at least a portion of the value token to at least a portion of the
request.
[00316] 54. The method of 53, further comprising:
determining the request is related to the sub-wallet;
wherein applying at least a portion of the value token comprises applying at
least a portion
of the value token of the sub-wallet to the request.
[00317] 55. The method of 53, wherein the sub-wallet comprises a sub-sub-
wallet.
[00318] 56. The method of 55, further comprising:
determining the request is related to the sub-sub-wallet;
wherein applying at least a portion of the value token comprises applying the
value token
of the sub-sub-wallet to the request.
118
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00319] 57. The method of 55, further comprising:
determining a portion of the request is related to the sub-wallet; and
determining another portion of the request is related to the sub-sub-wallet.
[00320] 58. The method of 55, wherein the sub-wallet comprises two or more
value tokens,
wherein the sub-wallet comprises at least one of the two or more value tokens,
wherein the sub-
sub-wallet comprises at least another of the two or more value tokens.
[00321] 59. The method of 58, further comprising:
applying at least a portion of the sub-wallet's value token to the request;
and
applying at least a portion of the sub-sub-wallet's value token to the
request.
[00322] 60. The method of 54 or 59, wherein the value token of the sub-
wallet is applied to the
request under a rule of the sub-wallet or the request.
[00323] 61. The method of 56 or 59, wherein the value token of the sub-sub-
wallet is applied to
the request under a rule of the sub-sub-wallet or the request.
[00324] 62. A method for managing the contents of an electronic wallet,
comprising:
receiving a request related to an electronic wallet, wherein the request
comprises an
electronic wallet request, a balance inquiry request, a registration request,
an activation request, a
redemption request, or combinations thereof; and
managing the contents of the electronic wallet according to the request.
[00325] 63. The method of 62, wherein managing the contents comprises:
exchanging at least a portion of a value token of the electronic wallet for at
least a portion
of a second value token not located in the electronic wallet.
[00326] 64. The method of 63, further comprising:
applying an exchange rate against the second value token or an asset located
in the
electronic wallet.
[00327] 65. The method of 63, wherein exchanging at least a portion of the
value token
comprises:
contacting a second value token distributor of the second value token; and
requesting the second value token distributor to provide the second value
token.
119
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00328] 66. The method of 62, wherein the electronic wallet comprises a
first sub-wallet and a
second sub-wallet, wherein the first sub-wallet comprises a value token, the
method further
comprising:
placing the value token of the first sub-wallet into the second sub-wallet.
[00329] 67. The method of 62, further comprising:
provisioning the electronic wallet with a value token.
[00330] 68. The method of 67, wherein provisioning the electronic wallet
comprises adding the
value token to the electronic wallet.
[00331] 69. The method of 67, wherein the value token is provisioned in an
amount different
than the purchase price.
[00332] 70. The method of 67, wherein provisioning the electronic wallet
comprises encoding
the value token with a coupon code.
[00333] 71. The method of 62, wherein the electronic wallet comprises a
savings-designated
sub-wallet, the method further comprising:
placing at least a portion of a value token in the savings-designated sub-
wallet.
[00334] 72. A non-transitory machine-readable storage medium comprising
executable
instructions that, when executed, cause one or more processors to:
receive a request to process a payment transaction against an electronic
wallet;
identify authentication information of the request;
identify a value token in the electronic wallet; and
apply at least a portion of the value token to at least a portion of the
request.
[00335] 73. A non-transitory machine-readable storage medium comprising
executable
instructions that, when executed, cause one or more processors to:
receive a request to process a payment transaction against an electronic
wallet;
determine the request contains valid authentication information;
determine a value token, or a combination of value tokens, associated with the
electronic
wallet is capable of meeting the request; and
apply at least a portion of the value token to at least a portion of the
request.
[00336] 74. A non-transitory machine-readable storage medium comprising
executable
instructions that, when executed, cause one or more processors to:
120
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
receive a request to process a payment transaction against an electronic
wallet from a
provider of a primary wallet;
determine a value token is capable of meeting the request; and
apply at least a portion of the value token to at least a portion of the
request.
[00337] 75. A non-transitory machine-readable storage medium comprising
executable
instructions that, when executed, cause one or more processors to:
receive a request related to an electronic wallet, wherein the request
comprises an
electronic wallet request, a balance inquiry request, a registration request,
an activation request, a
redemption request, or combinations thereof; and
manage the contents of the electronic wallet according to the request.
[00338] 76. A system comprising:
one or more processors;
a memory coupled to at least one of the one or more processors;
the memory comprising executable instructions that, when executed, cause the
one or more
processors to:
receive a request to process a payment transaction against an electronic
wallet;
identify authentication information of the request;
identify a value token in the electronic wallet; and
apply at least a portion of the value token to at least a portion of the
request.
[00339] 77. The system of 76, wherein the one or more processors are
further caused to accept
an authentication token to access the electronic wallet.
[00340] 78. The system of 77, wherein the authentication information is
based on the
authentication token, wherein the authentication token comprises a proxy card,
a mobile device, a
password, a biometric identifier, or combinations thereof.
[00341] 79. The system of 76, wherein the electronic wallet comprises a
primary wallet and a
sub-wallet.
[00342] 80. The system of 79, wherein the one or more processors are
further caused to process
at least a portion of the request via the primary wallet.
[00343] 81. The system of 79, wherein the one or more processors are
further caused to process
at least a portion of the request via the sub-wallet.
121
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00344] 82. The system of 79, wherein the primary wallet comprises the
value token, wherein
the one or more processors are further caused to:
determine the request is related to the primary wallet; and
determine the value token is capable of meeting the request.
[00345] 83. The system of 82, wherein apply at least a portion of the value
token comprises
apply at least a portion of the value token of the primary wallet to the
request.
[00346] 84. The system of 79, wherein the sub-wallet comprises the value
token, wherein the
one or more processors are further caused to:
determine the request is related to the sub-wallet; and
determine the value token is capable of meeting the request.
[00347] 85. The system of 84, wherein apply at least a portion of the value
token comprises
apply at least a portion of the value token of the sub-wallet to the request.
[00348] 86. The system of 79, wherein the electronic wallet comprises two
or more value
tokens, wherein the primary wallet comprises at least one of the two or more
value tokens, wherein
the sub-wallet comprises at least another of the two or more value tokens.
[00349] 87. The system of 86, wherein the one or more processors are
further caused to:
determine a portion of the request is related to the primary wallet; and
determine another portion of the request is related to the sub-wallet.
[00350] 88. The system of 87, further comprising:
apply at least a portion of the primary wallet's value token to the request;
and
apply at least a portion of the sub-wallet's value token to the request.
[00351] 89. The system of 83 or 88, wherein the value token of the primary
wallet is applied to
the request under a rule of the primary wallet or the request.
[00352] 90. The system of 85 or 88, wherein the value token of the sub-
wallet is applied to the
request under a rule of the sub-wallet or the request.
[00353] 91. The system of 79, wherein an aggregator system receives the
request, wherein the
one or more processors are further caused to:
determine at least a portion of the request may be processed in the sub-
wallet; and
send the portion of the request from the aggregator system to a third party.
[00354] 92. The system of 76, wherein the request includes an identity of a
point of sale
terminal; authentication information; an amount of a purchase; an identity of
the value token
122
CA 02897145 2015-07-03
WO 2014/107594 PCT[US2014/010206
issuer; an identity of a vendor; an identity of a location; a time of the
request; a date of the request;
information identifying a primary wallet, sub-wallet, or a combination
thereof; transaction data;
authentication data; or combinations thereof.
[00355] 93. The system of 76, wherein the value token comprises an
electronic representation
of value, wherein the electronic representation of value comprises a credit
card, debit card, gift
card, prepaid telephone card, loyalty card, membership card, ticket or ticket
card, entertainment
card, sports card, prepaid card, coupon, admission pass, prepaid or pre-
purchases of goods or
services, cash, currency, credit card account, debit card account, merchant
account, bank account,
merchant-issued credit, merchant-issued point, merchant-issued promotional
value, merchant-
accepted credit, merchant-accepted point, merchant-accepted promotional value,
or combinations
thereof.
[00356] 94. The system of 93, wherein the value token further comprises at
least two electronic
representations of value of different types.
[00357] 95. The system of 76, wherein the value token comprises a closed
loop account
number, wherein apply at least a portion of the value token comprises credit
or debit a closed loop
account associated with the closed loop account number.
[00358] 96. The system of 76, wherein the value token comprises an open loop
account
number, wherein apply at least a portion of the value token comprises credit
or debit an open loop
account associated with the open loop account number.
[00359] 97. The system of 76, wherein apply at least a portion of the value
token comprises
using the value token according to a set of configurable rules specifying
priority of the value
tokens.
[00360] 98. The system of 97, wherein the priority is based on a
transaction information
variable comprising physical location of a retailer originating the electronic
wallet request;
transaction amount; type of retailer; time of day; day of week; week of month;
month of year;
department of retailer originating the electronic wallet request; lane of
retailer originating the
electronic wallet request; identification of checker; parent company of a
retailer originating the
electronic wallet request; value of value tokens; type of the electronic
wallet request; or
combinations thereof.
123
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00361] 99. The system of 76, wherein apply at least a portion of the value
token comprises use
the value token according to a set of configurable rules specifying
percentages of the electronic
wallet request to which value tokens may be applied.
[00362] 100. The system of 76, wherein the one or more processors are
further caused to:
examine a rule associated with the electronic wallet.
[00363] 101. The system of 100, wherein examine a rule comprises:
examine a priority of the value token.
[00364] 102. The system of 100, wherein examine a rule comprises:
examine a percentage of the request;
wherein apply at least a portion of the value token comprises apply at least a
portion of the
value token to the request according to the percentage.
[00365] 103. The system of 76, wherein the electronic wallet comprises a
closed loop-related
value token and an open loop-related value token, wherein the one or more
processors are further
caused to:
select the closed loop-related value token; and
then select the open loop-related value token.
[00366] 104. The system of 76, wherein the electronic wallet comprises an
open loop-related
value token, wherein the one or more processors are further caused to:
withhold the open loop-related value token from being applied to the request.
[00367] 105. The system of 76, wherein the one or more processors are
further caused to:
exchange at least a portion of the value token of the electronic wallet for at
least a portion
of a second value token not located in the electronic wallet.
[00368] 106. The system of 105, wherein the one or more processors are
further caused to:
apply an exchange rate against the second value token or an asset located in
the electronic
wallet.
[00369] 107. The system of 105, wherein exchange at least a portion of the
value token
comprises:
contact a second value token distributor; and
request the second value token distributor to provide the second value token.
124
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00370] 108. The system of 76, wherein the electronic wallet comprises a
first sub-wallet and a
second sub-wallet, wherein the first sub-wallet comprises the value token,
wherein the one or more
processors are further caused to:
place the value token of the first sub-wallet into the second sub-wallet.
[00371] 109. The system of 76, wherein the one or more processors are
further caused to:
provision the electronic wallet with the value token.
[00372] 110. The system of 109, wherein the value token is provisioned in
an amount different
than the purchase price.
[00373] 111. The system of 109, wherein provision the electronic wallet
comprises encode the
value token with a coupon code.
[00374] 112. The system of 109, wherein provision the electronic wallet
comprises add the
value token to the electronic wallet.
[00375] 113. The system of 76, wherein the electronic wallet comprises a
savings-designated
sub-wallet, wherein the one or more processors are further caused to:
place at least a portion of the value token in the savings-designated sub-
wallet.
[00376] 114. A system comprising:
one or more processors;
a memory coupled to at least one of the one or more processors;
the memory comprising executable instructions that, when executed, cause the
one or more
processors to:
receive a request to process a payment transaction against an electronic
wallet;
determine the request contains valid authentication information;
determine a value token, or a combination of value tokens, associated with the
electronic
wallet is capable of meeting the request; and
apply at least a portion of the value token to at least a portion of the
request.
[00377] 115. The system of 114, wherein the one or more processors are
further caused to:
accept an authentication token to access the electronic wallet.
[00378] 116. The system of 115, wherein the authentication information is
based on the
authentication token, wherein the authentication token comprises a proxy card,
a mobile device, a
password, a biometric identifier, or combinations thereof.
125
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00379] 117. The system of 114, wherein the electronic wallet comprises a
primary wallet and
a sub-wallet.
[00380] 118. The system of 117, wherein the one or more processors are
further caused to:
process at least a portion of the request via the primary wallet.
[00381] 119. The system of 118, wherein the one or more processors are
further caused to:
process at least another portion of the request via the sub-wallet.
[00382] 120. The system of 117, wherein the primary wallet comprises the
value token,
wherein the one or more processors are further caused to:
determine the request is related to the primary wallet;
wherein apply at least a portion of the value token comprises apply at least a
portion of the
value token of the primary wallet to the request.
[00383] 121. The system of 117, wherein the sub-wallet comprises the value
token, wherein the
one or more processors are further caused to:
determine the request is related to the sub-wallet;
wherein apply at least a portion of the value token comprises apply at least a
portion of the
value token of the sub-wallet to the request.
[00384] 122. The system of 117, wherein the electronic wallet comprises two
or more value
tokens, wherein the primary wallet comprises at least one of the two or more
value tokens, wherein
the sub-wallet comprises at least another of the two or more value tokens.
[00385] 123. The system of 122, wherein the one or more processors are
further caused to:
determine a portion of the request is related to the primary wallet; and
determine another portion of the request is related to the sub-wallet
[00386] 124. The system of 123, further comprising:
apply at least a portion of the primary wallet's value token to the request;
and
apply at least a portion of the sub-wallet's value token to the request.
[00387] 125. The system of 120 or 124, wherein the value token of the
primary wallet is
applied to the request under a rule of the primary wallet or the request.
[00388] 126. The system of 121 or 124, wherein the value token of the sub-
wallet is applied to
the request under a rule of the sub-wallet or the request.
[00389] 127. The system of 117, wherein an aggregator system receives the
request, wherein
the one or more processors are further caused to:
126
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
determine at least a portion of the request may be processed in the sub-
wallet; and
send the portion of the request from the aggregator system to a third party.
[00390] 128. A system comprising:
one or more processors;
a memory coupled to at least one of the one or more processors;
the memory comprising executable instructions that, when executed, cause the
one
or more processors to:
receive a request to process a payment transaction against an electronic
wallet from
a provider of a primary wallet;
determine a value token is capable of meeting the request; and
apply at least a portion of the value token to at least a portion of the
request.
[00391] 129. The system of 128, wherein the one or more processors are
further caused to:
determine the request is related to the sub-wallet;
wherein apply at least a portion of the value token comprises apply at least a
portion
of the value token of the sub-wallet to the request.
[00392] 130. The system of 128, wherein the sub-wallet comprises a sub-sub-
wallet.
[00393] 131. The system of 130, wherein the one or more processors are
further caused to:
determine the request is related to the sub-sub-wallet;
wherein apply at least a portion of the value token comprises apply the value
token
of the sub-sub-wallet to the request.
[00394] 132. The system of 130, wherein the one or more processors are
further caused to:
determine a portion of the request is related to the sub-wallet; and
determine another portion of the request is related to the sub-sub-wallet.
[00395] 133. The system of 130, wherein the electronic wallet comprises two
or more value
tokens, wherein the sub-wallet comprises at least one of the two or more value
tokens, wherein the
sub-sub-wallet comprises at least another of the two or more value tokens.
[00396] 134. The system of 133, further comprising:
apply at least a portion of the sub wallet's value token to the request; and
apply at least a portion of the sub-sub-wallet's value token to the request.
[00397] 135. The system of 129 or 134, wherein the value token of the sub-
wallet is applied to
the request under a rule of the sub-wallet or the request.
127
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00398] 136. The system of 131 or 134, wherein the value token of the sub-
sub-wallet is
applied to the request under a rule of the sub-sub-wallet or the request.
[00399] 137. A system, comprising:
one or more processors;
a memory coupled to at least one of the one or more processors;
the memory comprising executable instructions that, when executed, cause the
one
or more processors to:
receive a request related to an electronic wallet, wherein the request
comprises an
electronic wallet request, a balance inquiry request, a registration request,
an activation request, a
redemption request, or combinations thereof; and
manage the contents of the electronic wallet according to the request.
[00400] 138. The system of 137, wherein manage the content comprises:
exchange at least a portion of a value token of the electronic wallet for at
least a
portion of a second value token not located in the electronic wallet.
[00401] 139. The system of 138, wherein the one or more processors are
further caused to:
apply an exchange rate against the second value token or an asset located in
the
electronic wallet.
[00402] 140. The system of 138, wherein exchange at least a portion of the
value token
comprises:
contact a second value token distributor of the second value token; and
request the second value token distributor to provide the second value token.
[00403] 141. The system of 137, wherein the electronic wallet comprises a
first sub-wallet and
a second sub-wallet, wherein the first sub-wallet comprises a value token,
wherein the one or more
processors are further caused to:
place the value token of the first sub-wallet into the second sub-wallet.
[00404] 142. The system of 137, wherein the one or more processors are
further caused to:
provision the electronic wallet with a value token.
[00405] 143. The system of 142, wherein the value token is provisioned in
an amount different
than the purchase price.
[00406] 144. The system of 142, wherein provision the electronic wallet
comprises encode the
value token with a coupon code.
128
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00407] 145. The system of 142, wherein provision the electronic wallet
comprises add the
value token to the electronic wallet.
[00408] 146. The system of 137, wherein the electronic wallet comprises a
savings-designated
sub-wallet, wherein the one or more processors are further caused to:
place at least a portion of a value token in the savings-designated sub-
wallet.
[00409] 147. A system comprising:
one or more processors;
a memory coupled to at least one of the one or more processors;
the memory comprising executable instructions that, when executed, cause the
one or more
processors to:
receive a request to process a payment transaction against an electronic
wallet;
identify authentication information of the request;
identify a value token in the electronic wallet; and
apply at least a portion of the value token to at least a portion of the
request.
[00410] 148. The system of 147, wherein the one or more processors are
further caused to
accept an authentication token to access the electronic wallet.
[00411] 149. The system of 148, wherein the authentication information is
based on the
authentication token, wherein the authentication token comprises a proxy card,
a mobile device, a
password, a biometric identifier, or combinations thereof.
[00412] 150. The system of 149, wherein the electronic wallet comprises a
primary wallet and
a sub-wallet.
[00413] 151. The system of 150, wherein the one or more processors are
further caused to
process at least a portion of the request via the primary wallet.
[00414] 152. The system of 151, wherein the one or more processors are
further caused to
process at least a portion of the request via the sub-wallet.
[00415] 153. The system of 152, wherein the primary wallet comprises the
value token,
wherein the one or more processors are further caused to:
determine the request is related to the primary wallet; and
determine the value token is capable of meeting the request.
[00416] 154. The system of 153, wherein apply at least a portion of the
value token comprises
apply at least a portion of the value token of the primary wallet to the
request.
129
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00417] 155. The system of 154, wherein the sub-wallet comprises the value
token, wherein
the one or more processors are further caused to:
determine the request is related to the sub-wallet; and
determine the value token is capable of meeting the request.
[00418] 156. The system of 155, wherein apply at least a portion of the
value token comprises
apply at least a portion of the value token of the sub-wallet to the request.
[00419] 157. The system of 156, wherein the electronic wallet comprises two
or more value
tokens, wherein the primary wallet comprises at least one of the two or more
value tokens, wherein
the sub-wallet comprises at least another of the two or more value tokens.
[00420] 158. The system of 157, wherein the one or more processors are
further caused to:
determine a portion of the request is related to the primary wallet; and
determine another portion of the request is related to the sub-wallet.
[00421] 159. The system of 158, wherein the one or more processors are
further caused to:
apply at least a portion of the primary wallet's value token to the request;
and
apply at least a portion of the sub-wallet's value token to the request.
[00422] 160. The system of 159, wherein the value token of the primary
wallet is applied to the
request under a rule of the primary wallet.
[00423] 161. The system of 159, wherein the value token of the primary
wallet is applied to the
request under a rule of the request.
[00424] 162. The system of 159, wherein the value token of the sub-wallet
is applied to the
request under a rule of the sub-wallet.
[00425] 163. The system of 159, wherein the value token of the sub-wallet
is applied to the
request under a rule of the request.
[00426] 164. The system of 159, wherein an aggregator system receives the
request, wherein
the one or more processors are further caused to:
determine at least a portion of the request may be processed in the sub-
wallet; and
send the portion of the request from the aggregator system to a third party.
[00427] 165. The system of 164, wherein the request includes an identity of
a point of sale
terminal; authentication information; an amount of a purchase; an identity of
the value token
issuer; an identity of a vendor; an identity of a location; a time of the
request; a date of the request;
130
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
information identifying a primary wallet, sub-wallet, or a combination
thereof; transaction data;
authentication data; or combinations thereof.
[00428] 166. The system of 165, wherein the value token comprises an
electronic
representation of value, wherein the electronic representation of value
comprises a credit card,
debit card, gift card, prepaid telephone card, loyalty card, membership card,
ticket or ticket card,
entertainment card, sports card, prepaid card, coupon, admission pass, prepaid
or pre-purchases of
goods or services, cash, currency, credit card account, debit card account,
merchant account, bank
account, merchant-issued credit, merchant-issued point, merchant-issued
promotional value,
merchant-accepted credit, merchant-accepted point, merchant-accepted
promotional value, or
combinations thereof.
[00429] 167. The system of 166, wherein the value token further comprises
at least two
electronic representations of value of different types.
[00430] 168. The system of 167, wherein the value token comprises a closed
loop account
number, wherein apply at least a portion of the value token comprises credit
or debit a closed loop
account associated with the closed loop account number.
[00431] 169. The system of 168, wherein the value token comprises an open
loop account
number, wherein apply at least a portion of the value token comprises credit
or debit an open loop
account associated with the open loop account number.
[00432] 170. The system of 169, wherein apply at least a portion of the
value token comprises
using the value token according to a set of configurable rules specifying
priority of the value
tokens.
[00433] 171. The system of 170, wherein the priority is based on a
transaction information
variable comprising physical location of a retailer originating the electronic
wallet request;
transaction amount; type of retailer; time of day; day of week; week of month;
month of year;
department of retailer originating the electronic wallet request; lane of
retailer originating the
electronic wallet request; identification of checker; parent company of a
retailer originating the
electronic wallet request; value of value tokens; type of the electronic
wallet request; or
combinations thereof.
[00434] 172. The system of 171, wherein apply at least a portion of the
value token comprises
use the value token according to a set of configurable rules specifying
percentages of the electronic
wallet request to which value tokens may be applied.
131
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00435] 173. The system of 172, wherein the one or more processors are
further caused to:
examine a rule associated with the electronic wallet.
[00436] 174. The system of 173, wherein examine a rule comprises:
examine a priority of the value token.
[00437] 175. The system of 174, wherein examine a rule comprises:
examine a percentage of the request;
wherein apply at least a portion of the value token comprises apply at least a
portion of the
value token to the request according to the percentage.
[00438] 176. The system of 175, wherein the electronic wallet comprises a
closed loop-related
value token and an open loop-related value token, wherein the one or more
processors are further
caused to:
select the closed loop-related value token; and
then select the open loop-related value token.
[00439] 177. The system of 176, wherein the electronic wallet comprises an
open loop-related
value token, wherein the one or more processors are further caused to:
withhold the open loop-related value token from being applied to the request.
[00440] 178. The system of 177, wherein the one or more processors are
further caused to:
exchange at least a portion of the value token of the electronic wallet for at
least a portion
of a second value token not located in the electronic wallet.
[00441] 179. The system of 178, wherein the one or more processors are
further caused to:
apply an exchange rate against the second value token or an asset located in
the electronic
wallet.
[00442] 180. 1 he system of 179, wherein exchange at least a portion of the
value token
comprises:
contact a second value token distributor; and
request the second value token distributor to provide the second value token.
[00443] 181. The system of 180, wherein the electronic wallet comprises a
first sub-wallet and
a second sub-wallet, wherein the first sub-wallet comprises the value token,
wherein the one or
more processors are further caused to:
place the value token of the first sub-wallet into the second sub-wallet.
132
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00444] 182. The system of 181, wherein the one or more processors are
further caused to:
provision the electronic wallet with the value token.
[00445] 183. The system of 182, wherein the value token is provisioned in
an amount different
than the purchase price.
[00446] 184. The system of 183, wherein provision the electronic wallet
comprises encode the
value token with a coupon code.
[00447] 185. The system of 184, wherein provision the electronic wallet
comprises add the
value token to the electronic wallet.
[00448] 186. The system of 185, wherein the electronic wallet comprises a
savings-designated
sub-wallet, wherein the one or more processors are further caused to:
place at least a portion of the value token in the savings-designated sub-
wallet.
[00449] 187. A computer implemented method comprising:
receiving a request for a security code of an electronic stored-value card;
calculating the security code by a security code provider;
providing a calculated security code of the electronic-stored value card in
response to the
request for a security code; and
eliminating the calculated security code from databases of the security code
provider.
[00450] 188. The method of 187, wherein the security code provider
comprises a issuer of the
electronic stored-value card, a processor of the electronic stored-value card,
a merchant, or
combinations thereof.
[00451] 189. The method of any of 187 to 188, wherein the step of providing
the calculated
security code comprises:
sending the calculated security code to an electronic wallet;
sending the calculated security code to a user device; or both.
[00452] 190. The method of any of 187 to 189, wherein a card token is
associated with the
request.
[00453] 191. The method of any of 187 to 190, wherein the step of
calculating the security
code comprises:
calculating the security code using a primary account number, an expiration
date, a service
code, a security information, or combinations thereof, of the electronic
stored-value card.
133
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00454] 192. The method of any of 187 to 191, wherein the security code is
a CVV2.
[00455] 193. The method of any of 187 to 191, further comprising:
receiving the calculated security code;
obtaining the security code;
determining whether the received-calculated security code matches the obtained
security
code.
[00456] 194. The method of 193, wherein the step of obtaining the security
code comprises:
recalculating the security code by the security code provider, wherein the
obtained security
code comprises a recalculated security code.
[00457] 195. The method of 194, wherein the step of determining whether the
received-
calculated security code matches the obtained security code comprises:
determining whether the received-calculated security code matches the
recalculated
security code.
[00458] 196. The method of 195, further comprising:
eliminating the received calculated security code and the recalculated
security code from
databases of the security code provider.
[00459] 197. The method of any of 187 to 193, further comprising:
receiving a request to process a payment transaction;
identifying authentication information of the request to process a payment
transaction;
identifying a value of the electronic stored-value card; and
applying at least a portion of the value to at least a portion of the request
to process the
payment transaction.
[00460] 198. The method of 197, wherein the electronic stored-value card is
stored in an
electronic wallet.
[00461] 199. The method of 198, wherein the electronic wallet comprises a
primary wallet and
a sub-wallet.
134
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00462] 200. The method of 199, further comprising:
processing at least a portion of the request to process a payment transaction
via the primary
wallet;
processing at least a portion of the request to process a payment transaction
via the sub-
wallet;
or both.
[00463] 201. The method of any of 187 to 200, wherein the electronic stored-
value card
comprises an electronic open loop stored-value card, the method further
comprising:
receiving an electronic open loop stored-value distribution request;
providing the electronic open loop stored-value card in response to the
electronic open loop
stored-value distribution request;
notifying a recipient of the electronic open loop stored-value card provided
in response to
the electronic open loop stored-value distribution request;
allowing the electronic open loop stored-value card to be associated with an
electronic
wallet; and
enabling the electronic open loop stored-value card for a redemption
transaction, a reload
transaction, or combinations thereof.
[00464] 202. The method of 201, wherein the electronic open loop stored-
value card is
provided as an eGift, an eCode, or directly to the electronic wallet.
[00465] 203. The method of 202, wherein the eGift is delivered as a uniform
source locator
("URL").
[00466] 204. The method of 203, wherein the URL is delivered through email,
short message
service ("SMS"), social media post, or other electronic channel.
[00467] 205. The method of any of 203 to 204, wherein the URL references a
HyperText
Markup Language ("HTML") page and wherein the HTML page provides information
concerning
the eGift. 206. The method of any of 202 to 205, wherein the information
concerning the eGift is
selected from the group consisting of terms and conditions, redemption
instructions, reload
instructions, an identification number of the electronic open loop stored-
value card, a security
code, an expiration date, and combinations thereof.
[00468] 207. The method of any of 202 to 206, wherein the eCode is delivered
directly to the
recipient.
135
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00469] 208. The method of any of 202 to 207, wherein the eCode comprises an
identification
number of the electronic open loop stored-value card, a security code, and an
expiration date.
[00470] 209. The method of any of 206 to 208, wherein the security code is
a card verification
value ("CVV2").
[00471] 210. The method of 209, wherein the CVV2 is obtained dynamically by an
electronic
stored-value card issuer.
[00472] 211. The method of any of 209 to 210, wherein the electronic stored-
value card issuer
does not store the CVV2, rather the CVV2 is calculated for provision to the
recipient.
[00473] 212. The method of any of 209 to 211, wherein the CV V2 is
calculated in real time.
[00474] 213. The method of any of 209 to 212, wherein the CVV2 is
calculated by encrypting
PAN, the expiration date and security code with encryption keys.
[00475] 214. A computer-implemented electronic stored-value card security
code providing
system configured to:
receive a request for a security code of the electronic stored-value card;
calculate the security code;
provide the calculated security code in response to the request for a security
code; and
to eliminate the calculated security code from the system.
[00476] 215. The system of 214, wherein the electronic stored-value card
comprises card
information, the system further configured to calculate the security code
using the card
information.
[00477] 216. The system of any of 214 to 215, wherein the security code
comprises a CVV2.
[00478] 217. The system of any of 214 to 216, wherein the system is of an
electronic stored-
value card provider.
[00479] 218. The system of any of 214 to 217, wherein the security code
provider comprises a
provider of the electronic stored-value card, a processor of the electronic
stored-value card, an
issuer of the electronic stored-value card, a merchant, a user device, or
combinations thereof.
[00480] 219. The system of any of 214 to 218, wherein an electronic
component sends the
security code to an electronic wallet.
[00481] 220. The system of any of 214 to 219, wherein an electronic component
of the system
sends the security code to a user device.
136
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00482] 221. The system of any of 214 to 220, further configured to
calculate the security code
using a primary account number, an expiration date, and a security information
of the electronic
stored-value card.
[00483] 222. The system of any of 214 to 221, further configured to:
receive a calculated security code;
obtain the security code of the electronic stored-value card; and
determine whether a received-calculated security code matches the obtained
security code.
[00484] 223. The system of 222, wherein obtain the security code comprises:
recalculate the security code, wherein the obtained security code comprises a
recalculated
security code, wherein the system is of a security code provider.
[00485] 224. The system of any of 222 to 223, wherein determine whether the
received-
calculated security code matches the obtained security code comprises
determine whether the
received-calculated security code matches the recalculated security code.
[00486] 225. The system of any of 222 to 224, wherein an electronic component
of the system
eliminates the received-calculated security code and/or the recalculated
security code from
databases of the security code provider.
[00487] 226. The system of any of 214 to 225, further configured to:
receive a request to process a payment transaction;
identify authentication information of the request to process a payment
transaction;
identify a value of the electronic stored-value card; and
apply at least a portion of the value to at least a portion of the request to
process a payment
transaction.
[00488] 227. The system of any of 214 to 226 comprising a database to store
the electronic
stored-value card in an electronic wallet.
[00489] 228. The system of 227, wherein the electronic wallet comprises a
primary wallet and
a sub-wallet.
[00490] 229. The system of 228, further configured to process at least a
portion of the request
to process a payment transaction via the primary wallet, to process at least a
portion of the request
to process a payment transaction via the sub-wallet, or both.
[00491] 230. A computer-implemented open loop stored-value card
distribution system
configured to:
137
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
receive an electronic open loop stored-value card distribution request;
provide the electronic open loop stored-value card in response to the
electronic open loop
stored-value distribution request;
notify a recipient of the electronic open loop stored-value card provided in
response to the
electronic open loop stored-value distribution request;
allow the electronic open loop stored-value card to be associated with an
electronic wallet;
and
enable the electronic open loop stored-value card for a redemption
transaction, a reload
transaction, or combinations thereof
[00492] 231. The system of 230, wherein the electronic open loop stored-
value card is provided
as an eGift, an eCode, or directly to the electronic wallet.
[00493] 232. The system of 231, wherein the eGift is delivered as a uniform
source locator
("URL").
[00494] 233. The system of 232, wherein the URL is delivered through email,
short message
service ("SMS"), social media post, or other electronic channel.
[00495] 234. The system of any of 232 to 233, wherein the URL references a
HyperText
Markup Language ("HTML") page and wherein the HTML page provides information
concerning
the eGift.
[00496] 235. The system of any of 231 to 234, wherein the information
concerning the eGift is
selected from the group consisting of terms and conditions, redemption
instructions, reload
instructions, an identification number of the electronic open loop stored-
value card, a security
code, an expiration date, and combinations thereof.
[00497] 236. The system of any of 231 to 235, wherein the eCode is
delivered directly to the
recipient.
[00498] 237. The system of any of 231 to 236, wherein the eCode comprises
an identification
number of the electronic open loop stored-value card, a security code, and an
expiration date.
[00499] 238. The system of any of 235 to 237, wherein the security code is
a card verification
value ("CVV2").
[00500] 239. The system of 238, wherein the CVV2 is obtained dynamically by an
electronic
stored-value card issuer.
138
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00501] 240. The system of any of 238 to 239, wherein the electronic stored-
value card issuer
does not store the CVV2, rather the CVV2 is calculated for provision to the
recipient.
[00502] 241. The system of any of 238 to 240, wherein the CVV2 is
calculated in real time.
[00503] 242. The system of any of 238 to 241, wherein the CVV2 is calculated
by encrypting
PAN, the expiration date and security code with encryption keys.
[00504] 243. A computer implemented method comprising:
providing an electronic stored-value card, wherein the electronic stored-value
card requires
a security code for conducting transactions;
receiving a request for the security code of the electronic stored-value card;
calculating the security code by a security code provider;
providing a calculated security code of the electronic-stored value card in
response to the
request for a security code; and
eliminating the calculated security code from databases of the security code
provider.
[00505] 244. The method of 243, wherein the security code provider
comprises a issuer of the
electronic stored-value card, a processor of the electronic stored-value card,
a merchant, or
combinations thereof
[00506] 245. The method of any of 243 to 244, wherein the step of providing
the calculated
security code comprises:
sending the calculated security code to an electronic wallet;
sending the calculated security code to a user device; or both.
[00507] 246. The method of any of 243 to 245, wherein a card token is
associated with the
request.
[00508] 247. The method of any of 243 to 246, wherein the step of calculating
the security
code comprises:
calculating the security code using a primary account number, an expiration
date, a service
code, a security information, or combinations thereof, of the electronic
stored-value card.
[00509] 248. The method of any of 243 to 247, wherein the security code is a
CVV2.
[00510] 249. The method of any of 243 to 248, further comprising:
receiving the calculated security code;
obtaining the security code; and
139
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
determining whether the received-calculated security code matches the obtained
security
code.
[00511] 250. The method of 249, wherein the step of obtaining the security
code comprises:
recalculating the security code by the security code provider, wherein the
obtained security
code comprises a recalculated security code.
[00512] 251. The method of any of 249 to 250, wherein the step of determining
whether the
received-calculated security code matches the obtained security code
comprises:
determining whether the received-calculated security code matches the
recalculated
security code.
[00513] 252. The method of any of 249 to 251, further comprising:
eliminating the received calculated security code and the recalculated
security code from
databases of the security code provider.
[00514] 253. The method of any of 243 to 252, further comprising:
receiving a request to process a payment transaction;
identifying authentication information of the request to process a payment
transaction;
identifying a value of the electronic stored-value card; and
applying at least a portion of the value to at least a portion of the request
to process the
payment transaction.
[00515] 254. The method of any of 243 to 253, wherein the electronic stored-
value card is
stored in an electronic wallet.
[00516] 255. The method of 254, wherein the electronic wallet comprises a
primary wallet and
a sub-wallet.
[00517] 256. The method of any of 254 to 255, further comprising:
processing at least a portion of the request to process a payment transaction
via the primary
wallet;
processing at least a portion of the request to process a payment transaction
via the sub-
wallet;
or both.
[00518] 257. The method of any of 243 to 256, wherein the electronic stored-
value card
comprises electronic open loop stored-value card, the method further
comprising:
receiving an electronic open loop stored-value distribution request;
140
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
providing the electronic open loop stored-value card in response to the
electronic open loop
stored-value distribution request;
notifying a recipient of the electronic open loop stored-value card provided
in response to
the electronic open loop stored-value distribution request;
allowing the electronic open loop stored-value card to be associated with an
electronic
wallet; and
enabling the electronic open loop stored-value card for a redemption
transaction, a reload
transaction, or combinations thereof
[00519] 258. The method of 257, wherein the electronic open loop stored-
value card is
provided as an eGift, an eCode, or directly to the electronic wallet.
[00520] 259. The method of 258, wherein the eGift is delivered as a uniform
source locator
("URL").
[00521] 260. The method of 259, wherein the URL is delivered through email,
short message
service ("SMS"), social media post, or other electronic channel.
[00522] 261. The method of any of 259 to 260, wherein the URL references a
HyperText
Markup Language ("HTML") page and wherein the HTML page provides information
concerning
the eGift.
[00523] 262. The method of any of 258 to 261, wherein the information
concerning the eGift is
selected from the group consisting of terms and conditions, redemption
instructions, reload
instructions, an identification number of the electronic open loop stored-
value card, a security
code, an expiration date, and combinations thereof.
[00524] 263. The method of any of 258 to 262, wherein the eCode is
delivered directly to the
recipient.
[00525] 264. r1 he method of any of 258 to 263, wherein the eCode comprises
an identification
number of the electronic open loop stored-value card, a security code, and an
expiration date.
[00526] 265. The method of any of 262 to 264, wherein the security code is
a card verification
value ("CVV2").
[00527] 266. The method of 265, wherein the CVV2 is obtained dynamically by an
electronic
stored-value card issuer.
[00528] 267. The method of any of 265 to 266, wherein the electronic stored-
value card issuer
does not store the CVV2, rather the CVV2 is calculated for provision to the
recipient.
141
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00529] 268. The method of any of 265 to 267, wherein the CVV2 is calculated
in real time.
[00530] 269. The method of any of 265 to 268, wherein the CVV2 is calculated
by encrypting
PAN, the expiration date and security code with encryption keys.
[00531] 270. A computer-implemented electronic stored-value card security
code providing
system configured to:
receive a request for a security code of the electronic stored-value card;
calculate the security code;
provide the calculated security code in response to the request for a security
code; and
eliminate the calculated security code from the system.
[00532] 271. The system of 270, wherein the electronic stored-value card
comprises card
information, the system further configured to calculate the security code
using the card
information.
[00533] 272. The system of any of 270 to 271, wherein the security code
comprises a CVV2.
[00534] 273. The system of any of 244 to 246, wherein the system is of an
electronic stored-
value card provider.
[00535] 274. The system of any of 270 to 273, wherein the security code
provider comprises a
provider of the electronic stored-value card, a processor of the electronic
stored-value card, an
issuer of the electronic stored-value card, a merchant, a user device, or
combinations thereof.
[00536] 275. The system of any of 270 to 274, wherein an electronic component
of the system
sends the security code to an electronic wallet.
[00537] 276. The system of 270 to 275, wherein an electronic component of the
system sends
the security code to a user device.
[00538] 277. The system of any of 270 to 276, further configured to
calculate the security code
using a primary account number, an expiration date, and a security information
of the electronic
stored-value card.
[00539] 278. The system of 270 to 277, further configured to:
receive a calculated security code;
obtain the security code of the electronic stored-value card; and
determine whether a received-calculated security code matches the obtained
security code.
142
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00540] 279. The system of 278, wherein obtain the security code comprises:
recalculate the security code, wherein the obtained security code comprises a
recalculated
security code, wherein the system is of a security code provider.
[00541] 280. The system of any of 278 to 279, wherein determine whether the
received-
calculated security code matches the obtained security code comprises
determine whether the
received-calculated security code matches the recalculated security code.
[00542] 281. The system of any of 278 to 280, wherein an electronic component
of the system
eliminates the received-calculated security code and the recalculated security
code from databases
of the security code provider.
[00543] 282. The system of any of 270 to 281, further configured to:
receive a request to process a payment transaction;
identify authentication information of the request to process a payment
transaction;
identify a value of the electronic stored-value card; and
apply at least a portion of the value to at least a portion of the request to
process a payment
transaction.
[00544] 283. The system of any of 270 to 282 comprising a database to store
the electronic
stored-value card in an electronic wallet.
[00545] 284. The system of 283, wherein the electronic wallet comprises a
primary wallet and
a sub-wallet.
[00546] 285. The system of any of 270 to 284, further configured to process
at least a portion
of the request to process a payment transaction via the primary wallet, to
process at least a portion
of the request to process a payment transaction via the sub-wallet, or both.
[00547] 286. A computer-implemented open loop stored-value card
distribution system
configured to:
receive an electronic open loop stored-value distribution request;
provide the electronic open loop stored-value card in response to the
electronic open loop
stored-value distribution request;
notify a recipient of the electronic open loop stored-value card provided in
response to the
electronic open loop stored-value distribution request;
allow the electronic open loop stored-value card to be associated with an
electronic wallet;
143
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
enable the electronic open loop stored-value card for a redemption
transaction, a reload
transaction;
or combinations thereof
[00548] 287. The system of 286, wherein the electronic open loop stored-
value card is provided
as an eGift, an eCode, or directly to the electronic wallet.
[00549] 288. The system of 287, wherein the eGift is delivered as a uniform
source locator
("URL").
[00550] 289. The system of 288, wherein the URL is delivered through email,
short message
service ("SMS"), social media post, or other electronic channel.
[00551] 290. The system of any of 288 to 289, wherein the URI, references a
HyperText
Markup Language ("HTML") page and wherein the HTML page provides information
concerning
the eGift.
[00552] 291. The system of any of 287 to 290, wherein the information
concerning the eGift is
selected from the group consisting of terms and conditions, redemption
instructions, reload
instructions, an identification number of the electronic open loop stored-
value card, a security
code, an expiration date, and combinations thereof.
[00553] 292. The system of any of 287 to 291, wherein the eCode is
delivered directly to the
recipient.
[00554] 293. The system of any of 287 to 292, wherein the eCode comprises an
identification
number of the electronic open loop stored-value card, a security code, and an
expiration date.
[00555] 294. The system of any of 291 to 293, wherein the security code is
a card verification
value ("CVV2").
[00556] 295. The system of 294, wherein the CVV2 is obtained dynamically by an
electronic
stored-value card issuer.
[00557] 296. The system of any of 294 to 295, wherein the electronic stored-
value card issuer
does not store the CVV2, rather the CVV2 is calculated for provision to the
recipient.
[00558] 297. The system of any of 294 to 296, wherein the CVV2 is
calculated in real time.
[00559] 298. The system of any of 294 to 297, wherein the CVV2 is calculated
by encrypting
PAN, the expiration date and security code with encryption keys.
[00560] 299. The method of any of 187 to 213 or any of 243 to 269, wherein the
electronic
stored-value card is provided as a uniform resource locator.
144
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00561] 300. The method of any of 187 to 213 or any of 243 to 269, or 299,
wherein the
electronic stored-value card is provided in a communication via short message
service, instant
message, or email.
[00562] 301. The method of any of 187 to 213 or any of 243 to 269 or any of
299 to 300,
wherein the electronic stored-value card comprises a primary account number,
security
information, and an expiration date.
[00563] 302. The method of any of 187 to 213 or any of 243 to 269 or any of
299 to 301,
wherein the electronic stored-value card is provided directly to an electronic
wallet.
[00564] 303. The method of any of 187 to 213 or any of 243 to 269 or any of
299 to 302,
wherein the request for the security code of the electronic stored-value card
is automatically
generated by selection/activation of the uniform resource locator.
[00565] 304. The method of any of 187 to 213 or any of 243 to 269 or any of
299 to 303,
wherein the request for the security code of the electronic stored-value card
is automatically
generated by accepting, reading, viewing, opening, or otherwise engaging the
communication
received via short message service, instant message, or email.
[00566] 305. The method of any of any of 187 to 213 or any of 243 to 269 or
any of 299 to
304, wherein the request for the security code of the electronic stored-value
card is automatically
generated by accepting, reading, viewing, opening, or otherwise engaging the
communication
received via short message service, instant message, or email.
[00567] 306. The method of any of any of 187 to 213 or any of 243 to 269 or
any of 299 to
305, wherein the request for the security code of the electronic stored-value
card is automatically
generated by accepting, reading, viewing, opening, or otherwise engaging an
indication of the
electronic stored-value card in the electronic wallet.
[00568] 307. The method of any of 187 to 213 or any of 243 to 269 or any of
299 to 306,
wherein the request for the security code of the electronic stored-value card
is generated by an
action separate and apart from a selection/activation of the uniform resource
locator.
[00569] 308. The method of any of 187 to 213 or any of 243 to 269 or any of
299 to 307,
wherein the request for the security code of the electronic stored-value card
is generated by an
action separate and apart from accepting, reading, viewing, opening, or
otherwise engaging the
communication received via short message service, instant message, or email.
145
CA 02897145 2015-07-03
WO 2014/107594 PCT/US2014/010206
[00570] 309. The method of any of 187 to 213 or any of 243 to 269 or any of
299 to 308,
wherein the request for the security code of the electronic stored-value card
is generated by an
action separate and apart from accepting, reading, viewing, opening, or
otherwise engaging the
communication received via short message service, instant message, or email.
[00571] 310. The method of any of 187 to 213 or any of 243 to 269 or any of
299 to 309,
wherein the request for the security code of the electronic stored-value card
is generated by an
action separate and apart from accepting, reading, viewing, opening, or
otherwise engaging an
indication of the electronic stored-value card in the electronic wallet.
[00572] 311. The system of any of 214 to 242 or any of 270 to 298, wherein
the electronic
stored-value card is provided as a uniform resource locator.
[00573] 312. The system of any of 214 to 242 or any of 270 to 298 or of
311, wherein the
electronic stored-value card is provided in a communication via short message
service, instant
message, or email.
[00574] 313. The system of any of 214 to 242 or any of 270 to 298 or any of
311 to 312,
wherein the electronic stored-value card comprises a primary account number,
security
information, and an expiration date.
[00575] 314. The system of any of 214 to 242 or any of 270 to 298 or any of
311 to 313,
wherein the electronic stored-value card is provided directly to an electronic
wallet.
[00576] 315. The system of any of 214 to 242 or any of 270 to 298 or any of
311 to 314,
wherein the request for the security code of the electronic stored-value card
is automatically
generated by selection/activation of the uniform resource locator.
[00577] 316. The method of any of 187 to 213 or any of 243 to 269 or any of
299 to 310,
wherein the request for the security code of the electronic stored-value card
is automatically
generated by accepting, reading, viewing, opening, or otherwise engaging the
communication
received via short message service, instant message, or email.
[00578] 317. The method of any of 187 to 213 or any of 243 to 269 or any of
299 to 309 or of
316, wherein the request for the security code of the electronic stored-value
card is automatically
generated by accepting, reading, viewing, opening, or otherwise engaging the
communication
received via short message service, instant message, or email.
[00579] 318. The method of any of 187 to 213 or any of 243 to 269 or any of
299 to 309 or any
of 316 to 317, wherein the request for the security code of the electronic
stored-value card is
146
automatically generated by accepting, reading, viewing, opening, or otherwise
engaging an
indication of the electronic stored-value card in the electronic wallet.
[00580] 319. The method of any of 187 to 213 or any of 243 to 269 or any of
299 to 309 or
any of 316 to 318, wherein the request for the security code of the electronic
stored-value card is
generated by an action separate and apart from a selection/activation of the
uniform resource
locator.
[00581] 320. The method of any of 187 to 213 or any of 243 to 269 or any of
299 to 309 or
any of 316 to 319, wherein the request for the security code of the electronic
stored-value card is
generated by an action separate and apart from accepting, reading, viewing,
opening, or
otherwise engaging the communication received via short message service,
instant message, or
email.
[00582] 321. The method of any of 187 to 213 or any of 243 to 269 or any of
299 to 309 or
any of 316 to 320, wherein the request for the security code of the electronic
stored-value card is
generated by an action separate and apart from accepting, reading, viewing,
opening, or
otherwise engaging the communication received via short message service,
instant message, or
email.
[00583] 322. The method of any of 187 to 213 or any of 243 to 269 or any of
299 to 309 or
any of 316 to 321, wherein the request for the security code of the electronic
stored-value card is
generated by an action separate and apart from accepting, reading, viewing,
opening, or
otherwise engaging an indication of the electronic stored-value card in the
electronic wallet.
[00584] There has been described herein an systems and methods for
providing a security
code of an electronic stored-value card such that users may purchase, redeem,
and/or exchange
value associated with the electronic stored-value card (e.g., electronic value
tokens residing in an
electronic wallet). It will be apparent to those skilled in the art that
modifications may be made
without departing from the scope of the disclosure. The embodiments described
are
representative only, and are not intended to be limiting. Many variations,
combinations, and
modifications of the applications disclosed herein are possible and are within
the scope of the
disclosure.
147
CA 2897145 2020-01-22