Note: Descriptions are shown in the official language in which they were submitted.
CA 03151313 2022-02-15
WO 2021/033069
PCT/IB2020/057486
1
SECURE ARMING AND FIRING IN AN ELECTRONIC BLASTING SYSTEM
Field of the invention
The invention relates to an electronic blasting system and to a method of
facilitating secure
arming and firing in an electronic blasting system. The invention also relates
to an apparatus
for use in such a system and/or method.
Background to the invention
Detonators are employed in the blasting of rock for the extraction of minerals
or other
valuable components, the quarrying of rock and in civil engineering projects
that require rock
blasting. Blasting is generally done by drilling a pattern of boreholes,
priming each borehole
with a detonator and a booster and filling the hole, in accordance with the
design, with
commercial explosives. Types of detonators used include those attached to a
pyrotechnic
fuse (fuse head), electric detonators, shock-tube initiated detonators and, in
the last 20 years
or so, electronic detonators.
Wired electronic blasting depends on electrical leads from a blaster unit
(usually near the
blast) to every hole that has been supplied with an electronic detonator. The
surface wiring
system may comprise a lead-in line which connects to lines running along each
row of holes.
Connectors, usually insulation displacement connectors (IDCs), are used to
connect the
lead-in line or trunk line electrically to the row lines. Similar connectors
may be used to
connect the detonator leg wires to the row lines.
Each detonator typically comprises a metal tube containing a sealing plug, a
crimp, an
electronic module, a fuse head connected to the electronic module and an
explosive charge.
The electronic module of modern detonators typically comprises a
microprocessor, a power
supply to supply regulated power to the microprocessor, a firing capacitor and
a bleed
resistor which acts as a shunt and drains the firing capacitor to safe voltage
levels after a
period of time.
CA 03151313 2022-02-15
WO 2021/033069
PCT/IB2020/057486
2
During preparations for a blast, one or more detonators is/are placed in each
hole. The
detonators are then logged, during which the operator applies a hand-held
logging device,
commonly referred to as a "logger" to the detonator to generate an association
between the
detonator's unique electronic identity and the borehole into which it is
deployed. Logging
commonly also includes programming the detonator by writing a firing time for
the hole in
question into the detonator's memory, testing the detonator for its readiness
to fire, and
recording all relevant details of the detonator in the memory of the logger.
As explained above, multiple detonators are typically connected to each other
in an
electronic blasting system. These form so-called multiple detonator circuits
or bound
networks. Blasts are usually divided into sub-circuits of, for example, about
200 to 1000
detonators. A number of these sub-circuits can comprise a single, large blast.
For these
large blasts, multiple loggers are generally used. Appropriate logistics and
control
procedures must be carried out in large blasts to make sure that every sub-
circuit is
energised, that all detonators are tested and ready to fire, and that every
detonator receives
the fire command. At some point in this process, disconnected subsets of data
from the
various loggers are combined into a list or data set essentially describing
the entire blast.
Some systems do not require this activity in order to execute the blast, but
it will be
appreciated that it is at least required for record keeping and/or planning
purposes.
A need has been identified for an apparatus, system and/or method to
facilitate or ensure
secure arming and firing of a large blast.
Summary of the invention
In accordance with a first aspect of the invention, there is provided a method
of facilitating
secure arming and firing in an electronic blasting system, the electronic
blasting system
comprising multiple detonators connected or connectable to at least one
blasting box, and
the method comprising:
providing a plurality of logging devices for interrogating and programming
each
detonator; and
initialising one of the logging devices as a key logger such that the key
logger is the
only device in or associated with the electronic blasting system that is
capable of carrying
out one or both of:
CA 03151313 2022-02-15
WO 2021/033069
PCT/IB2020/057486
3
initialising each blasting box as a control unit or as a blaster unit, or as a
combination control unit and blaster unit, and
authorising arming and firing of a blast in the electronic blasting system;
and
using the key logger to initialise each blasting box and/or to authorise
arming and
firing of a blast in the electronic blasting system.
The key logger may thus be initialised as the only device that has final
authority over a blast
process.
In some embodiments, sets of information collected from the detonators in the
electronic
blasting system by a plurality of the logging devices are combined or
consolidated into a
single file in one of the logging devices, thereby initialising that one
logging device as the
key logger.
In some embodiments, the key logger is the only device that has the authority
to initialise a
blasting box as a control unit, or as a blaster unit, or as a combination
control unit and blaster
unit.
The key logger may be the only logging device which is configured to authorise
the control
unit to arm the electronic blasting system, interrogate the detonators and
signal the blaster
units to charge the detonators and initiate the blast.
The key logger may be configured to generate a pin, preferably a One Time Pin
(OTP) or
some other unique code or identifier, when or in response to it being
initialised as the key
logger, wherein the pin is required at critical events in the blasting
process.
Critical events may be predefined and may include at least arming and firing
of the blast. In
some embodiments, the pin is required for: initialising a blasting box as
either a control unit
or as a blaster unit or as a combination control unit and blaster unit,
binding a number of
blaster units to a control unit, authorising the control unit to arm the
system, and signalling
the blaster units to charge the detonators and initiate the blast. The pin may
be required to
confirm each critical event. The pin is referred to as the "OTP" in the
remainder of this
specification.
CA 03151313 2022-02-15
WO 2021/033069
PCT/IB2020/057486
4
In a typical implementation, each blaster unit has a unique
identity/identifier (ID), and
multiple blaster units are bound to a single control unit by the key logger,
wherein the key
logger associates each blaster unit's unique ID with the key logger's OTP, for
the purposes
of security and control.
Preferably, the key logger carries a summary of all of the detonators and
blaster units, bound
to a control unit, in a single blast file which may be transferred to the
control unit for purposes
of identifying those blaster units that the control unit may communicate with.
During
communications with the control unit, any blaster unit which is activated, but
whose unique
ID has not been associated with the OTP, will not respond.
The key logger's OTP survives for the duration of the blast process and once
the control unit
has issued a blast command, the OTP loses validity.
The logging device may be a portable logging device, also known as a logger,
for use in a
suitable blasting system.
In accordance with a second aspect of the invention, there is provided a
logging device for
use in an electronic blasting system, the electronic blasting system
comprising multiple
detonators connected or connectable to at least one blasting box, the logging
device being
configured to be initialised as a key logger, thereby configuring the logging
device as the
only device in or associated with the electronic blasting system that is
capable of initialising
each blasting box as a control unit or as a blaster unit or as a combination
control unit and
blaster unit and/or the only device in or associated with the electronic
blasting system that
is capable of authorising arming and firing of a blast in the electronic
blasting system.
The logging device may be configured to receive sets of information collected
from the
detonators in the electronic blasting system by a plurality of logging
devices, the information
being combined or consolidated into a single file in the logging device,
thereby initialising it
as the key logger.
The logging device may include any of the further features already mentioned
above and
may be configured to carry out any of the method steps already described
above.
CA 03151313 2022-02-15
WO 2021/033069
PCT/IB2020/057486
The logging device may be a logging device for interrogating and programming
detonators
in the blasting system.
The key logger may carry a summary of (or other data indicative of) all of the
detonators and
5 blaster units, bound to a particular control unit, in a single blast
file. The key logger may be
configured to transfer this summary to the control unit for purposes of
identifying those
blaster units that the control unit may communicate with.
In accordance with a third aspect of the invention, there is provided an
electronic blasting
system comprising:
a plurality of detonators;
at least one blasting box to which the detonators are connected or
connectable; and
a plurality of logging devices for interrogating and programming detonators in
the
blasting system, wherein on of the logging device is a logging device as
described above
for initialisation as a key logger.
The electronic blasting system may be a system for mining and/or quarrying
operations.
Brief description of the drawings
An embodiment of the invention is described below, by way of example only, and
with
reference to the following drawings, in which:
Figure 1 is a schematic diagram of an electronic blasting system according to
the invention;
Figure 2 is a schematic drawing of a detonator of the electronic blasting
system;
Figure 3 is a schematic drawing of a logger connected a detonator of the
electronic blasting
system;
Figure 4 is a schematic drawing of a logger connected to a number of
detonators of the
electronic blasting system;
Figure 5 is a flow diagram depicting exemplary steps in a method/process of
initialising one
logger out of a plurality of loggers as a key logger and initialising blaster
units; and
Figure 6 is a flow diagram depicting exemplary steps in a method/process of
using the
initialised key logger to initialise a control unit and to authorise a blast.
CA 03151313 2022-02-15
WO 2021/033069
PCT/IB2020/057486
6
Detailed description with reference to the drawings
The following description is provided as an enabling teaching of the
invention, is illustrative
of principles associated with the invention and is not intended to limit the
scope of the
invention. Changes may be made to the embodiment/s depicted and described,
while still
attaining results of the present invention and/or without departing from the
scope of the
invention. Furthermore, it will be understood that some results or advantages
of the present
invention may be attained by selecting some of the features of the present
invention without
utilising other features. Accordingly, those skilled in the art will recognise
that modifications
and adaptations to the present invention may be possible and may even be
desirable in
certain circumstances and may form part of the present invention.
Referring to Figure 1, an example embodiment of an electronic blasting system
(10) is
shown. The system (10) comprises multiple detonators (12) connected via
connectors (14)
to a surface harness wire network (16) and to a blasting machine, also known
as a blaster
unit (18) or (19). Multiple blaster units (18, 19) are connected wirelessly,
via suitably
configured modems and antennas (21), to a control unit (20) that controls the
detonators
(12) through their powering, programming, calibration, arming and firing
processes. In some
cases, blaster units (18, 19) may be connected to each other via a two-wire
cable (22) as
shown in Figure 1, e.g. for signal integrity and synchronization between
units.
The blaster units (18, 19) and the control unit (20) can both be referred to
as "blaster boxes",
but they have been configured to perform different functions, as is described
in more detail
below.
In use, at a blast site, a pattern of boreholes is drilled according to a
blast design, where the
parameters of each hole, including its position and firing time, are pre-
assigned. Each
borehole is then primed with one or more detonators (12). The detonator (12)
may be
inserted into a booster (not shown) to create a primer that initiates the
explosive charge,
alternatively the detonator (12) may directly initiate certain explosives
itself. The detonator
(12) is then lowered into the borehole and the hole is filled with a
predetermined quantity of
explosives. The hole is then charged.
CA 03151313 2022-02-15
WO 2021/033069
PCT/IB2020/057486
7
Each detonator (12) in the network is connected to the surface harness wire
(16) via a two-
core cable (24) and a connector (14).
Referring to Figure 2, each detonator (12) comprises a sealing plug (26), a
crimp (28), an
electronic module (30), a fuse head (32) and an explosives charge (34) which
are contained
inside a metal shell (36).
In this example embodiment, each electronic module (30) comprises
electrostatic discharge
and over-voltage barriers (38), a low-voltage power supply (40) to supply
regulated power
to an application specific integrated circuit (ASIC) (42) (containing non-
volatile memory and
a firing switch). The electronic module (30) further includes a bleed resistor
(44) and a firing
capacitor (46). The bleed resistor (44) acts as a shunt to drain the firing
capacitor to safe
voltage levels after a period of time.
The ASIC (42) has non-volatile memory that allows data to be written to and
read from it
during manufacturing, during programming, during testing and during the
initiation of the
detonator.
Referring to Figure 3, the detonators (12) are each programmed by writing a
firing time and
relative position into the detonator's non-volatile memory by means of a
portable logging
device, referred to herein as a portable logger (60) (or simply "logger"),
connected to the
detonator, either via the connector (14) which connects to the logger's
connector port (62)
or directly from the cable (24) to the cable ports (64) (not depicted).
The logger (60) registers each detonator's unique identity/identifier (UID),
and other details
already stored in the detonator's ASIC (42), and programs a firing time into
the detonator
(12), based on the detonator's position in the blast design. Additional
information, including
the fact that the detonator has been positively tested, detonator position,
date and time and
logger ID may also be recorded on the detonator's (12) non-volatile memory.
The logger
(60) also tests each detonator for current consumption, and confirmation that
it has been
successfully programmed, and may request further information from the
detonator, including
environmental measurements.
CA 03151313 2022-02-15
WO 2021/033069
PCT/IB2020/057486
8
In this example, the logger (60) is a handheld portable unit. It includes a
touch-screen
interface that is part of a robust portable microcomputer device and a
separate numeric
keypad for entering detonator firing time values. However, it will be
appreciated that other
user interfaces and designs may be employed without departing from the scope
of the
invention.
During logging of the detonators (12), a file is created in the logger (60),
known as a blast
file. This blast file typically contains a list of all detonators (12) on a
blast (that have been
logged by the logger (60)), with information related to each detonator (12).
The information
includes at least the detonator's unique identification (UID), the detonator's
position ID (PID)
and the detonator's firing time.
Referring Figure 4, once all of the required detonators (12) have been
programmed and
logged, the harness wire (16) is connected to a logger (60) that contains the
blast file, via
the terminal points (64). The logger (60) then tests the harness (16) for
power consumption
and tests the detonators (60), verifying that all logged detonators (12) are
present and
functioning.
Testing is done either for individual detonators (12) when a logger (60) is
connected to a
single detonator via the connector port (62) (see Figure 3), or groups of
detonators on the
surface harness wires (16) when a logger is connected via the terminal points
(64) (see
Figure 4).
As alluded to above, the blaster units (18, 19) and control unit (20) are all
"blast boxes". In
this example embodiment, all blast boxes (18, 19 and 20) are identical in
structure, possible
functionality, software and electronics. However, individual boxes are
configurable based on
their required application and must be initialised as either a control unit or
a blaster unit or
combination thereof during preparation for undertaking a blast.
A blaster unit (18,19) requires wireless communication with a control unit
(20) to allow firing
of detonators (12).
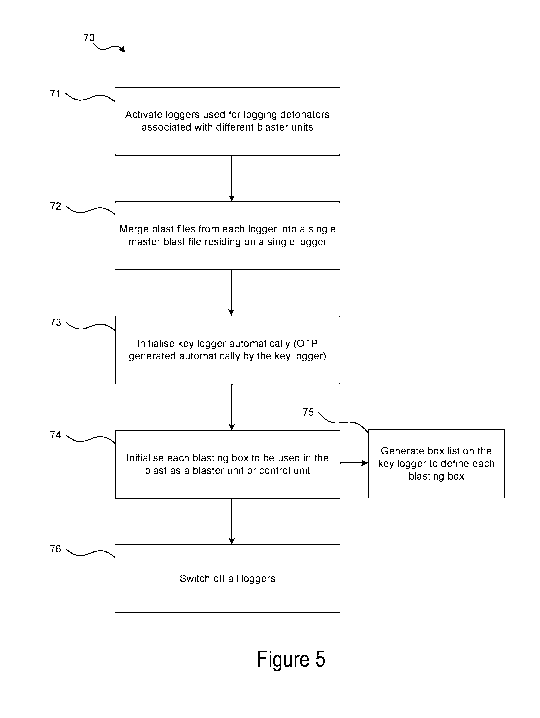
Referring to the flow diagram (70) in Figure 5, where a number of loggers (60)
are used in
the blasting system (10), the loggers (60) are activated and each used for
logging and testing
CA 03151313 2022-02-15
WO 2021/033069
PCT/IB2020/057486
9
of detonators (12) associated (or to be associated) with different blaster
units (18, 19), at
stage (71).
At stage (72), once logging and testing of detonators (12) has been completed,
all the blast
files from the different loggers (60) are combined or consolidated into one
file on one of the
loggers (60). This file may be referred to as a key blast file. This process
initialises that one
logger as the key logger, at stage (73). The key logger is configured such
that, once it has
received/generated the key blast file and is initialised as the key logger, it
generates a One
Time Pin (OTP) which is valid for the duration of the blast. The term "OTP"
should be broadly
interpreted and may be any suitable pin, passcode, password, or the like.
In this example embodiment, when a blasting box is switched on, it defaults to
an
"unconfigured state" and must be initialised as a blaster unit by the key
logger at stage (74).
A blaster unit (18,19) cannot fire a blast, test detonators, re-program
detonators, or power
up the line unless it is in a bound network of units with an initialised
control unit (20). The
key logger binds the units by creating a blast file, or box list, which
defines each blaster unit
to be used on the blast by the blaster unit's unique ID and the OTP number
(stage (75)).
In this example, once stages (71)-(75) have been carried out, the loggers (60)
are switched
off / deactivated (stage (76)).
The key logger is the only logger (60) that will carry the key blast file
containing information
about the detonators (12) and the blaster units (18,19) associated with and/or
bound to a
single control unit (20).
Referring now to the flow diagram (80) in Figure 6, the key logger is the only
logger (60) that
is configured to (and thus able to) authorise a blasting box as a control unit
and the key
logger initialises one control unit in a bound network of blasting boxes (see
for example the
control unit (20) in Figure 1). The key logger and relevant blasting box are
activated (stage
(81) and (82)) and once the control unit (20) has been initialised, the blast
file and OTP is
transferred from the key logger to the control unit (20). The blast file
contains a list of blaster
unit IDs to be used and controlled by the control unit (20) in the blast (see
stages (83) and
(84)).
CA 03151313 2022-02-15
WO 2021/033069
PCT/IB2020/057486
The OTP survives for the duration of the blast process. Once the control unit
(20) has issued
a blast command, the OTP loses its validity.
Once the control unit (20) has been initialised, it is switched to standby
mode at stage (85)
5 and communication channels to all of the relevant blaster units (as
defined by the blast file)
are opened at stage (86).
The system (10) is armed with authorisation from the key logger on manual
entry of the OTP
(stage (87)). The control unit then instructs the blaster units to power the
detonators (12) up
10 via the surface harness wires (16), charge firing capacitors and start
test sequences (stage
(88)).
Once the detonators firing capacitors have been charged by the blaster units
(18,19), the
blaster units (18, 19) issue repeating test sequences to the detonators (12).
In some
embodiments, testing is done by exception. In other words, detonators (12)
will only respond
to a test if something is wrong.
During the execution of a blast, a system status is continuously or
periodically uploaded to
the key logger from the control unit (20) and at least the following
information can be
displayed on the key logger's screen: current activity, fault reporting, armed
or safe condition
and countdown to blast.
As each blaster unit (18, 19) runs through the testing routines, it reports
the test results to
the control unit (20), which then relays this information to the key logger.
The key logger
will report if a blast must be aborted and will report on any detonator
failures. Specific test
requests can be made from the key logger. In this example embodiment, although
the key
logger cannot issue a "charge capacitors" command or a "fire" command, it is
configured to
authorise the control unit (20) to carry out these commands though the manual
entry of the
OTP in the key logger.
All powering-up of detonators (12) at firing voltage, calibrating, charging of
firing capacitors
and issuing of the blast command is done from the control unit (20) with
authority from the
key logger. It can thus be said that the key logger has final authority over
at least the
abovementioned aspects of the blasting process.
CA 03151313 2022-02-15
WO 2021/033069
PCT/IB2020/057486
11
All commands are issued to the detonators (12) from the control unit (20) via
the blaster
units (18,19) in the bound network.
Once the "fire command" has been authorised by the manual entry of the OTP on
the key
logger (stage (89)), the operator has a limited window of time in which to
fire the blast from
the control unit (20) at stage (90). Once the blast is fired, the OTP loses
its validity. The
operator will then deactivate the key logger and blasting boxes at stage (91).
Embodiments of the invention thus provide an apparatus, system and method to
facilitate or
ensure secure arming and firing of a blast, and particularly a large blast
with multiple sub-
circuits.
This is achieved by launching or initialising one logger amongst a group of
loggers in an
electronic blasting system as a key logger, in such a manner that the key
logger is (i) the
only logger configured to initialise blasting boxes as control units or
blaster units and/or (ii)
the only logger that can be used to authorise arming and firing of the system
via the control
unit.