Note: Descriptions are shown in the official language in which they were submitted.
CA 03152848 2022-02-28
USER IDENTIFYING METHOD AND DEVICE, AND COMPUTER EQUIPMENT
BACKGROUND OF THE INVENTION
Technical Field
[0001] The present invention relates to the field of computer technology, and
more particularly
to a user identifying method, a user identifying device, and a computer
equipment.
Description of Related Art
[0002] Currently, the detection of scammer gangs usually exists in the fields
of finances and
housing loans, and the specific means is to extract some individual attributes
with
relatively strong symbolism to serve as nodes in the graph theory, to form
connectible
sides by points with identical features, so as to construct a graph structure.
Since the
examination of personal qualifications in the fields of finances and housing
loans usually
requires such information with relatively strong social characteristics as the
ID cards,
mobile phone numbers, and emergency contact persons, etc., the attributes are
utilized in
the above technique to serve as connection points, to realize the objective of
risk detection
in the profession of finance. However, it is impossible in the e-commerce
industry to
collect relevant information of a user merely through one round of purchasing
by the user,
so symbolic attributes of users in the e-commerce industry are usually few and
far
between, while other attributes are usually too broad to be of any use. Taking
the attribute
of ordering ip for example, in the same cell, under the same shopping mall
WiFi, the case
of the same and single ip usually occurs when the user is connected to the
same mobile
base station at a single region, and in this case the mode and method to
extract features
should be changed. In addition, label propagation usually enlarges the
population detected,
since the ordering cost of the user is usually low and examination is scanty
in an e-
commerce scenario, the fraud network in the traditional finance and insurance
professions
1
Date Recue/Date Received 2022-02-28
CA 03152848 2022-02-28
cannot be entirely adapted for use in the e-commerce scenario.
SUMMARY OF THE INVENTION
[0003] In order to overcome the problems pending in the state of the art, the
present invention
proposes a user identifying method, and corresponding device and computer
equipment,
of which the method associates non-subject features to generate a combined
feature,
whereby is overcome the problem in which it is difficult to obtain strongly
associated
features of users or the features are insufficient under an e-commerce
environment, and
makes full use of the non-subject features to construct a precise graph model,
so as to
complete identification of scalper gangs.
[0004] Specific technical solutions provided by the embodiments of the present
invention are as
follows.
[0005] According to the first aspect, the present invention provides a user
identifying method,
and the method comprises:
[0006] integrating order data within a preset time dimension with order-
related identification
data;
[0007] obtaining a subject feature and non-subject features from the
integrated data and
generating a combined feature by combining at least two of the non-subject
features that
satisfy a preset condition, and determining feature values of the subject
feature and the
combined feature, wherein the subject feature is a feature whereby it can be
directly
determined that there is association between orders, and the non-subject
features are
features whereby it cannot be directly determined that there is association
between orders;
[0008] abstracting the orders as order nodes, abstracting the feature values
of the subject feature
and the combined feature as feature nodes, abstracting relations between the
orders and
the corresponding feature values as sides, and creating a bipartite graph
according to the
order nodes, the feature nodes and the sides; and
2
Date Recue/Date Received 2022-02-28
CA 03152848 2022-02-28
[0009] performing cluster analysis on the bipartite graph to obtain a
clustering result, and
identifying suspicious users according to the clustering result.
[0010] Preferably, the method further comprises:
[0011] performing feature extraction and statistics on historical order data,
and obtaining
historical non-subject features through the identification; and
[0012] generating a historical combined feature by combining at least two of
the historical non-
subject features that satisfy a preset condition.
[0013] Preferably, the method further comprises:
[0014] data-processing the integrated data, and generating orders with a
unified data format.
[0015] Preferably, the step of data-processing the integrated data, and
generating orders with a
unified data format specifically includes:
[0016] field-mapping the integrated data, and transforming different types of
data formats into
the same primary key form; and
[0017] aggregating data with the same primary key, and generating orders with
a unified data
format.
[0018] Preferably, the step of creating a bipartite graph according to the
order nodes, the feature
nodes and the sides specifically includes:
[0019] obtaining a unique identification of the orders and the feature values
of the subject feature
and the combined feature;
[0020] merging, duplicate-removing and coding the unique identification and
the feature values;
[0021] correspondingly associating the coded unique identification and feature
values with the
unique identification and the feature values before coding; and
[0022] creating the bipartite graph according to the associated data.
[0023] Preferably, obtaining order data within a preset time dimension
specifically includes:
3
Date Recue/Date Received 2022-02-28
CA 03152848 2022-02-28
[0024] obtaining first data produced in generating the orders;
[0025] judging states of the orders within the preset time dimension, and
obtaining second data
produced when the states of the orders change; and
[0026] integrating the first data and the second data, and generating the
order data.
[0027] Preferably, the step of performing cluster analysis on the bipartite
graph to obtain a
clustering result, and identifying suspicious users according to the
clustering result
specifically includes:
[0028] employing an LPA algorithm to cluster the order nodes and the feature
nodes, and
obtaining a clustering result; and
[0029] obtaining a risk judging result according to the clustering result.
[0030] Preferably, the order-related identification data includes login and/or
registration
information.
[0031] According to the second aspect, the present invention provides a user
identifying device,
and the device comprises:
[0032] a data processing module, for integrating order data within a preset
time dimension with
order-related identification data;
[0033] a feature extracting module, for obtaining a subject feature and non-
subject features from
the integrated data and generating a combined feature by combining at least
two of the
non-subject features that satisfy a preset condition, and determining feature
values of the
subject feature and the combined feature, wherein the subject feature is a
feature whereby
it can be directly determined that there is association between orders, and
the non-subject
features are features whereby it cannot be directly determined that there is
association
between orders;
[0034] a relation model creating module, for abstracting the orders as order
nodes, abstracting
the feature values of the subject feature and the combined feature as feature
nodes,
abstracting relations between the orders and the corresponding feature values
as sides,
4
Date Recue/Date Received 2022-02-28
CA 03152848 2022-02-28
and creating a bipartite graph according to the order nodes, the feature nodes
and the sides;
and
[0035] an identifying module, for performing cluster analysis on the bipartite
graph to obtain a
clustering result, and identifying suspicious users according to the
clustering result.
[0036] Preferably, the feature extracting module is further employed for:
[0037] performing feature extraction and statistics on historical order data,
and obtaining
historical non-subject features through the identification; and
[0038] generating a historical combined feature by combining at least two of
the historical non-
subject features that satisfy a preset condition.
[0039] Preferably, the device further comprises:
[0040] a transforming module, for data-processing the integrated data, and
generating orders
with a unified data format.
[0041] Preferably, the transforming module is specifically employed for:
[0042] field-mapping the integrated data, and transforming different types of
data formats into
the same primary key form; and
[0043] aggregating data with the same primary key, and generating orders with
a unified data
format.
[0044] Preferably, the relation model creating module is specifically employed
for:
[0045] obtaining a unique identification of the orders and the feature values
of the subject feature
and the combined feature;
[0046] merging, duplicate-removing and coding the unique identification and
the feature values;
[0047] correspondingly associating the coded unique identification and feature
values with the
unique identification and the feature values before coding; and
[0048] creating the bipartite graph according to the associated data.
Date Recue/Date Received 2022-02-28
CA 03152848 2022-02-28
[0049] Preferably, the device further comprises:
[0050] a data obtaining module, for obtaining first data produced in
generating the orders,
judging states of the orders within the preset time dimension, and obtaining
second data
produced when the states of the orders change; and
[0051] a data integrating module, for integrating the first data and the
second data, and generating
the order data.
[0052] Preferably, the identifying module specifically includes:
[0053] a clustering module, for employing an LPA algorithm to cluster the
order nodes and the
feature nodes, and obtaining a clustering result; and
[0054] a judging module, for obtaining a risk judging result according to the
clustering result.
[0055] Preferably, the order-related identification data includes login and/or
registration
information.
[0056] According to the third aspect, the present invention provides a
computer equipment that
comprises:
[0057] one or more processor(s); and
[0058] a memory, associated with the one or more processor(s), wherein the
memory is employed
to store a program instruction, and the program instruction performs the
following
operations when it is read and executed by the one or more processor(s):
[0059] integrating order data within a preset time dimension with order-
related identification
data;
[0060] obtaining a subject feature and non-subject features from the
integrated data and
generating a combined feature by combining at least two of the non-subject
features that
satisfy a preset condition, and determining feature values of the subject
feature and the
combined feature, wherein the subject feature is a feature whereby it can be
directly
determined that there is association between orders, and the non-subject
features are
features whereby it cannot be directly determined that there is association
between orders;
6
Date Recue/Date Received 2022-02-28
CA 03152848 2022-02-28
[0061] abstracting the orders as order nodes, abstracting the feature values
of the subject feature
and the combined feature as feature nodes, abstracting relations between the
orders and
the corresponding feature values as sides, and creating a bipartite graph
according to the
order nodes, the feature nodes and the sides; and
[0062] performing cluster analysis on the bipartite graph to obtain a
clustering result, and
identifying suspicious users according to the clustering result.
[0063] The embodiments of the present invention achieve the following
advantageous effects.
[0064] The present invention integrates data within life cycles of orders, and
associates the data
within life cycles of orders with identification data, so that the problem is
solved in which
the shopping link flow is complicated and data cannot be unified, and it is
made possible
to better identify the subject feature and non-subject features, and to
provide the
construction of the graph model with ample information and a highly effective
mode of
use.
[0065] The present invention associates non-subject features that satisfy a
preset condition to
generate a combined feature, whereby is overcome the problem in which it is
difficult to
obtain strongly associated features of users or the features are insufficient
under an e-
commerce environment, and the non-subject features are made full use of to
construct a
precise graph model.
[0066] The present invention obtains historical non-subject features from
historical order data,
and associates and combines the historical non-subject features, thus
remedying the
factual defect of features missing in the e-commerce environment, and
providing a new
method for mining deeper network relations.
[0067] The present invention rectifies the combined feature through the LPA
algorithm, thus
effectively avoiding excessive propagation, and enhancing the precision in
finding out
7
Date Recue/Date Received 2022-02-28
CA 03152848 2022-02-28
scalper gangs.
[0068] Of course, it is not necessarily prerequisite for the present invention
to simultaneously
achieve all of the aforementioned effects, as it suffices to satisfy one of
them.
BRIEF DESCRIPTION OF THE DRAWINGS
[0069] To more clearly describe the technical solutions in the embodiments of
the present
invention, drawings required to illustrate the embodiments are briefly
introduced below.
Apparently, the drawings introduced below are merely directed to some
embodiments of
the present invention, while persons ordinarily skilled in the art may further
acquire other
drawings on the basis of these drawings without spending creative effort in
the process.
[0070] Fig. 1 is a view illustrating the application environment of a user
identifying method
provided by an embodiment of the present application;
[0071] Fig. 2 is a flowchart illustrating a user identifying method provided
by Embodiment 1 of
the present application; and
[0072] Fig. 3 is a view schematically illustrating the structure of a user
identifying device
provided by Embodiment 2 of the present application.
DETAILED DESCRIPTION OF THE INVENTION
[0073] To make more lucid and clear the objectives, technical solutions and
advantages of the
present invention, the technical solutions in the embodiments of the present
invention will
be clearly and comprehensively described below with reference to the
accompanying
drawings in the embodiments of the present invention. Apparently, the
embodiments as
described are merely partial, rather than the entire, embodiments of the
present invention.
Any other embodiments makeable by persons ordinarily skilled in the art on the
basis of
8
Date Recue/Date Received 2022-02-28
CA 03152848 2022-02-28
the embodiments in the present invention without creative effort shall all
fall within the
protection scope of the present invention.
[0074] The user identifying method provided by the present application is
applicable to the
application environment as shown in Fig. 1, in which server 12 communicates
with
database 11 and terminal 13 via network. Database 11 is employed to store
order data and
identification data, server 12 is employed to operate on and calculate the
order data and
the identification data to identify scalper gangs, terminal 13 can be, but is
not limited to
be, any of various personal computers, notebook computers, smart mobile
phones, panel
computers and portable wearable devices, and server 12 can be embodied as an
independent server or a server cluster consisting of a plurality of servers.
[0075] Embodiment 1
[0076] As shown in Fig. 2, the present application provides a user identifying
method, and the
method comprises the following steps.
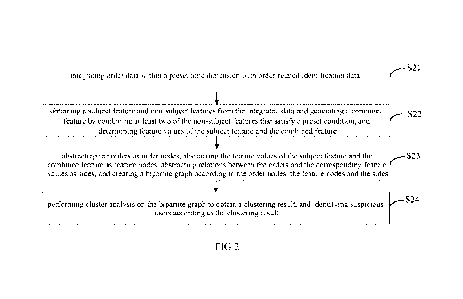
[0077] S21 - integrating order data within a preset time dimension with order-
related
identification data.
[0078] In this embodiment, the order-related identification data includes
login and/or registration
information; the order data within a preset time dimension includes data
generated from
orders generated within the preset time dimension, amended orders, and paid
orders, etc.
[0079] Obtaining order data within a preset time dimension can include the
following steps:
[0080] obtaining first data produced in generating the orders;
[0081] judging states of the orders within the preset time dimension, and
obtaining second data
produced when the states of the orders change; and
[0082] integrating the first data and the second data, and generating the
order data.
9
Date Recue/Date Received 2022-02-28
CA 03152848 2022-02-28
[0083] The first data produced in generating the orders includes data produced
from orders
generated within the preset time dimension, such as order address information,
etc.; the
second data produced when the states of the orders change includes one order
being
submitted for a number of times, different information being used at each
submission,
and information change during order payment, etc.
[0084] In this solution, the integration of the data produced in generating
the orders with the data
produced when states of the orders change makes it possible to obtain all data
within the
life cycle.
[0085] Step S21 is further explained and described by setting the preset time
dimension as one
hour.
[0086] Orders within one hour are obtained with the current timing as the end,
and order data is
obtained; the order data is integrated with the identification data (for
example, such
information as ip information associated ip home, operator, etc., and such
information as
membership associated registered mobile phone, registered ip, registered
equipment
model, registered mobile phone home, and operator etc.), and orders of a
preset data
format are generated.
[0087] The data format of the integrated orders can be of the following form:
{
messageFlag: "cart sync",
cart2No: "64325242342",
submitTime: "2017-10-01 13:04:09",
address: {
province: "Anhui Province",
city: "Huaibei City",
Date Recue/Date Received 2022-02-28
CA 03152848 2022-02-28
detail: "No. 1 Middle School of Huaibei, No. 2 Gucheng Street xx"
1
receiver: "Yangzhi",
receivePhone: {
number: "1861163)00(X",
province: "Beijing",
city: "Beijing",
smsPlatform: true/false
isVirtual: true/false
}
[0088] In this solution, the order data is integrated with the identification
data, whereby the order
data is more enriched, and ample information is provided for the subsequent
construction
of the graph model; moreover, the integrated data forms into a specified data
format, so
that the problem is solved in which the shopping link flow is complicated and
data cannot
be unified, and a highly effective mode of use is provided to the construction
of the graph
model.
[0089] S22 - obtaining a subject feature and non-subject features from the
integrated data and
generating a combined feature by combining at least two of the non-subject
features that
satisfy a preset condition, and determining feature values of the subject
feature and the
combined feature.
[0090] The subject feature indicates a feature whereby it can be directly
determined that there is
association between orders, such as goods receiving information, mobile phone
number,
etc.; the non-subject features indicate features whereby it cannot be directly
determined
that there is association between orders, such as order IP, etc.
[0091] Prior to obtaining the subject feature and the non-subject features,
the following step can
11
Date Recue/Date Received 2022-02-28
CA 03152848 2022-02-28
be further included:
[0092] data-processing the integrated data, and generating orders with a
unified data format.
[0093] In this solution, when life cycles of the orders are at different
phases, the data formats
produced are also different, so it is required to perform unified format
transformation on
the integrated data, and the process can specifically include:
[0094] field-mapping the integrated data, and transforming different types of
data formats into
the same primary key form; and
[0095] aggregating data with the same primary key, and generating orders with
a unified data
format.
[0096] By performing a transformation process on the primary keys of the data,
integration of
data produced by different life cycles of the orders is facilitated, and a
highly effective
mode of use is provided to the construction of the graph model.
[0097] After the orders with a unified data format have been obtained, the
subject feature and
non-subject features can be extracted therefrom, at least two non-subject
features that
satisfy a preset condition are combined to generate a combined feature, and
feature values
of the subject feature and the combined feature are determined.
[0098] For the same equipment, it may be possible for a normal person to
circulate it by sale to
the black industry after use, and unbounded network might be engendered if no
limitation
of time is made, so it is required at this time to perform time effect
analysis on the subject
feature according to historical order data so as to avoid misjudgment of
normal users.
[0099] The process of generating a combined feature is as follows.
[0100] Exemplarily, an order has non-subject features (F1, F2, F3), and
another order has non-
subject features (F1, F2, F3, F4), if feature Fl cannot identify that there is
relation
12
Date Recue/Date Received 2022-02-28
CA 03152848 2022-02-28
between two subjects, then features greater than thresholds are associated and
combined
according to a preset condition (for instance, to set a threshold for each
feature) to obtain
a combined feature F1+F2+F3, at this time, there is association between
identical subjects
(orders) of Fl+F2+F3.
[0101] In this solution, the association of non-subject features that satisfy
a preset condition to
generate a combined feature can overcome the problem in which it is difficult
to obtain
strongly associated features of users or the features are insufficient under
an e-commerce
environment, and make full use of the non-subject features to construct a
precise graph
model.
[0102] As should be noted, since combined features are variegated in one
order, so there may be
plural feature values to which one order corresponds. Specifically, refer to
the following
data structure:
{
featureVertex:[{
featureName: "feature x 1 + feature x 2 = feature x n",
featureCode: ",
featureGroup: ",
featureValue: "Huaibei City 0001xx",
hashCode: 12343235,
associateOrderNum: 10
},{
featureName: "feature 1 + feature 2 + feature x",
featureCode: ",
featureGroup: ",
featureValue: "Huaibei City 0002xx",
hashCode: 123431234,
13
Date Recue/Date Received 2022-02-28
CA 03152848 2022-02-28
associateOrderNum: 1
ll,
1
where featureVertex is a feature array formed by feature values of different
orders, and
featureValue is the feature value of an order.
[0103] Besides, in order to obtain more combined features to define the
relation between orders,
to compensate for the factual defect of features missing in the e-commerce
environment,
and to realize the mining of deeper network relations, it is further possible
to perform
statistics and feature extraction on historical order data so as to obtain
combined features,
specifically, performing statistics and feature extraction on historical order
data to
generate combined features can include:
[0104] performing feature extraction and statistics on historical order data,
and obtaining
historical non-subject features through the identification;
[0105] Specifically, the distribution circumstance of historical order data is
acquired through
statistics of the historical order data, and the distribution circumstance is
based on to
identify and obtain abnormal features, namely historical non-subject features.
[0106] generating a historical combined feature by combining at least two
historical non-subject
features that satisfy a preset condition.
[0107] Exemplarily, the statistical indicator can be set as a threshold,
historical non-subject
features that are higher than the threshold are associated and combined
according to the
threshold as set, so as to generate the historical combined feature.
[0108] S23 - abstracting the orders as order nodes, abstracting the feature
values of the subject
feature and the combined feature as feature nodes, abstracting relations
between the
orders and the corresponding feature values as sides, and creating a bipartite
graph
according to the order nodes, the feature nodes and the sides.
14
Date Recue/Date Received 2022-02-28
CA 03152848 2022-02-28
[0109] The feature nodes and the order nodes in this solution combine to
constitute node
collections. Each side (i, j) is formed by an order node and a feature node,
the two nodes
of each side belong to different node collections (for example, i belongs to
the feature
node collection, and j belongs to the order node collection), and a bipartite
graph can be
thusly constructed and obtained. In the bipartite graph, the order nodes
retain the entire
information of the feature nodes to which the order corresponds.
[0110] The step of creating a bipartite graph according to the order nodes,
the feature nodes and
the sides can include the following steps:
[0111] obtaining a unique identification of the orders and the feature values
of the subject feature
and the combined feature;
[0112] merging, duplicate-removing and coding the unique identification and
the feature values;
[0113] correspondingly associating the coded unique identification and feature
values with the
unique identification and the feature values before coding; and
[0114] creating the bipartite graph according to the associated data.
[0115] Exemplarily,
[0116] The unique identification and feature value data of the orders are
extracted, and a
dataframe table is constructed, whose format is as shown in the following
Table 1:
Table 1
Order Identification Featurevalue
Order-1 Feature-1
Order-1 Feature-2
Order-2 Feature-2
Order-n Feature-k
[0117] The order identifications and feature values are merged and duplicate-
removed, to form
a dataframe of a single column, as shown in the following Table 2:
Table 2
Date Recue/Date Received 2022-02-28
CA 03152848 2022-02-28
Order Identification
Order-1
Order-n
Feature-1
Feature-K
[0118] IDs are assigned to the order identifications and feature values, as
shown in the following
Table 3:
Table 3
Order Identification ID
Order-1 1
Order-n n
Feature-1 n+1
Feature-K n+k
[0119] Table 1 is associated with Table 3, and the correspondence relation of
the character string
type is transformed into a mapping relation of long digits, as shown in the
following Table
4:
Table 4
Order Identification Featurevalue ID1 ID2
Order-1 Feature-1 1 n+1
Order-1 Feature-2 1 n+2
Order-2 Feature-2 2 n+2
Order-n Feature-k n n+k
[0120] A bipartite graph is created according to Table 4.
[0121] S24 - performing cluster analysis on the bipartite graph to obtain a
clustering result, and
identifying suspicious users according to the clustering result.
16
Date Recue/Date Received 2022-02-28
CA 03152848 2022-02-28
[0122] The nodes and the sides in the bipartite graph are clustered through a
connectivity related
algorithm of the graph, and groups having identical association are output, so
as to
identify suspicious users. This step can specifically include:
[0123] employing an LPA algorithm to cluster the order nodes and the feature
nodes, and
obtaining a clustering result;
[0124] The LPA algorithm can rectify the combined feature, effectively avoid
excessive
propagation, and enhance the precision in finding out scalper gangs.
[0125] This step specifically includes:
[0126] setting unique labels for all nodes; and
[0127] refurbishing the labels of the nodes till convergence, and generating a
community
structure.
[0128] Specifically, each node transmits messages to its neighboring nodes,
while each node
receives messages sent from its neighboring nodes and accumulatively adds
group
weights as received, and updates its own label according to the label with the
greatest
accumulated weight until the label is stabilized, and a community structure is
generated,
in which the weight of a message is a product of a node weight, a side weight
and a
partition coefficient.
[0129] obtaining a risk judging result according to the clustering result.
[0130] Specifically, the clustering result is performed with risk
transformation according to
business requirements, and suspicious users are identified and obtained.
[0131] Exemplarily, when a gang purchased a certain category of commodities
over a number of
times, a gang risk is established, and a scalper gang is thus identified and
obtained.
[0132] In addition, after the clustering result has been performed with risk
transformation, two
data outputs are obtained. One is order information, including gang unique
code, etc., that
facilitates quick retrieval and statistics, the other is gang information,
including the
number of the gang member, equipment information involved, and ip information
etc.,
that facilitates quick perception of gang characteristics for quick decision.
17
Date Recue/Date Received 2022-02-28
CA 03152848 2022-02-28
[0133] Embodiment 2
[0134] As shown in Fig. 3, the present application provides a user identifying
device, and the
device comprises:
[0135] a data processing module 31, for integrating order data within a preset
time dimension
with order-related identification data;
[0136] a feature extracting module 32, for obtaining a subject feature and non-
subject features
from the integrated data and generating a combined feature by combining at
least two of
the non-subject features that satisfy a preset condition, and determining
feature values of
the subject feature and the combined feature, wherein the subject feature is a
feature
whereby it can be directly determined that there is association between
orders, and the
non-subject features are features whereby it cannot be directly determined
that there is
association between orders;
[0137] a relation model creating module 33, for abstracting the orders as
order nodes, abstracting
the feature values of the subject feature and the combined feature as feature
nodes,
abstracting relations between the orders and the corresponding feature values
as sides,
and creating a bipartite graph according to the order nodes, the feature nodes
and the sides;
and
[0138] an identifying module 34, for performing cluster analysis on the
bipartite graph to obtain
a clustering result, and identifying suspicious users according to the
clustering result.
[0139] Preferably, the feature extracting module 34 is further employed for:
[0140] performing feature extraction and statistics on historical order data,
and obtaining
historical non-subject features through the identification; and
[0141] generating a historical combined feature by combining at least two of
the historical non-
subject features that satisfy a preset condition.
[0142] Preferably, the device further comprises:
18
Date Recue/Date Received 2022-02-28
CA 03152848 2022-02-28
[0143] a transforming module 35, for data-processing the integrated data, and
generating orders
with a unified data format.
[0144] Preferably, the transforming module is specifically employed for:
[0145] field-mapping the integrated data, and transforming different types of
data formats into
the same primary key form; and
[0146] aggregating data with the same primary key, and generating orders with
a unified data
format.
[0147] Preferably, the relation model creating module 33 is specifically
employed for:
[0148] obtaining a unique identification of the orders and the feature values
of the subject feature
and the combined feature;
[0149] merging, duplicate-removing and coding the unique identification and
the feature values;
[0150] correspondingly associating the coded unique identification and feature
values with the
unique identification and the feature values before coding; and
[0151] creating the bipartite graph according to the associated data.
[0152] Preferably, the device further comprises:
[0153] a data obtaining module 36, for obtaining first data produced in
generating the orders,
judging states of the orders within the preset time dimension, and obtaining
second data
produced when the states of the orders change; and
[0154] a data integrating module 37, for integrating the first data and the
second data, and
generating the order data.
[0155] Preferably, the identifying module 34 specifically includes:
[0156] a clustering module 341, for employing an LPA algorithm to cluster the
order nodes and
the feature nodes, and obtaining a clustering result; and
[0157] a judging module 342, for obtaining a risk judging result according to
the clustering result.
19
Date Recue/Date Received 2022-02-28
CA 03152848 2022-02-28
[0158] Preferably, the order-related identification data includes login and/or
registration
information.
[0159] As should be noted, when the user identifying device provided by the
aforementioned
embodiment performs user identification, the division into the aforementioned
various
functional modules is merely by way of example, while it is possible, in
actual application,
to base on requirements to assign the functions to different functional
modules for
completion, that is to say, to divide the internal structure of the device
into different
functional modules to complete the entire or partial functions described
above. In addition,
the user identifying device provided by this embodiment pertains to the same
conception
as the user identifying method provided by the method embodiment ¨ see the
corresponding method embodiment for its specific realization process, while no
repetition
will be made in this context.
[0160] Embodiment 3
[0161] Corresponding to the aforementioned method and device, Embodiment 3 of
the present
application provides a computer equipment that comprises:
[0162] one or more processor(s); and
[0163] a memory, associated with the one or more processor(s), wherein the
memory is employed
to store a program instruction, and the program instruction performs the
following
operations when it is read and executed by the one or more processor(s):
[0164] integrating order data within a preset time dimension with order-
related identification
data;
[0165] obtaining a subject feature and non-subject features from the
integrated data and
generating a combined feature by combining at least two of the non-subject
features that
satisfy a preset condition, and determining feature values of the subject
feature and the
combined feature, wherein the subject feature is a feature whereby it can be
directly
determined that there is association between orders, and the non-subject
features are
Date Recue/Date Received 2022-02-28
CA 03152848 2022-02-28
features whereby it cannot be directly determined that there is association
between orders;
[0166] abstracting the orders as order nodes, abstracting the feature values
of the subject feature
and the combined feature as feature nodes, abstracting relations between the
orders and
the corresponding feature values as sides, and creating a bipartite graph
according to the
order nodes, the feature nodes and the sides; and
[0167] performing cluster analysis on the bipartite graph to obtain a
clustering result, and
identifying suspicious users according to the clustering result.
[0168] Although preferred embodiments in the embodiments of the present
invention have been
described, it is still possible for persons skilled in the art to make
additional modifications
and amendments to these embodiments upon learning the basic inventive concept.
Accordingly, the attached Claims are meant to subsume the preferred
embodiments and
all modifications and amendments that fall within the scope of the embodiments
of the
present invention.
[0169] Apparently, it is possible for persons skilled in the art to make
various modifications and
variations to the present invention without departing from the spirit and
scope of the
present invention. Thusly, should such modifications and variations to the
present
invention fall within the range of the Claims and equivalent technology of the
present
invention, the present invention is also meant to cover such modifications and
variations.
21
Date Recue/Date Received 2022-02-28