Note: Descriptions are shown in the official language in which they were submitted.
WO 2022/246539
PCT/CA2022/050749
Varying a Rate of Eliciting MIMO Transmissions from Wireless Communication
Devices
CROSS-REFERENCE TO RELATED APPLICATIONS
[0001] This application claims priority to U.S. Patent App. No.
17/328,479, filed May 24,
2021, entitled "Varying a Rate of Eliciting MIMO Transmission from Wireless
Communication Devices," the contents of which are hereby incorporated by
reference.
BACKGROUND
[0002] The following description relates to varying a rate at which multiple-
input/multiple-output (MIMO) transmissions are elicited from wireless
communication
devices, for example, for wireless motion detection.
[0003] Motion detection systems have been used to detect movement, for
example, of
objects in a room or an outdoor area. In some example motion detection
systems, infrared
or optical sensors are used to detect movement of objects in the sensor's
field of view.
Motion detection systems have been used in security systems, automated control
systems
and other types of systems.
DESCRIPTION OF DRAWINGS
[0004] FIG. 1 is a diagram showing an example wireless communication system.
[0005] FIGS. 2A-2B are diagrams showing example wireless signals communicated
between wireless communication devices.
[0006] FIG. 2C is a diagram of an example wireless sensing system operating to
detect
motion in a space.
[0007] FIG. 3 is a diagram showing an example PHY frame.
[0008] FIG. 4 is a diagram showing an example PHY frame.
[0009] FIG. 5 is a diagram showing an example multiple-input-multiple-output
(MIMO)
radio configuration.
[0010] FIG. 6 is a diagram showing example frequency spectra of wireless
signals.
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
[0011] FIG. 7 is a diagram showing an example representation of the Open
System
Interconnection (OSI) model.
[0012] FIG. 8 is a diagram showing example message components for three layers
of a
typical OSI model.
[0013] FIG. 9 is a flowchart representing an example process that finds an
upper layer
logical address.
[0014] FIG. 10 is a state machine diagram representing an example process that
elicits
MIMO transmissions from wireless communication devices.
[0015] FIG. 11A shows a flowchart representing an example process to setup an
ICMP
ping.
[0016] FIG. 11B shows a flowchart representing an example process to stop an
ICMP
ping.
[0017] FIG. 11C shows a flowchart representing an example process to conduct
an ICMP
ping.
[0018] FIG. 12A shows a flowchart representing an example process to setup a
TCP
Ping.
[0019] FIG. 12B shows a flowchart representing an example process to conduct a
TCP
Ping.
[0020] FIG. 13 shows a flowchart representing an example process to setup an
ARP
Ping.
[0021] FIG. 14 shows a flowchart representing an example method of eliciting
MIMO
transmissions from wireless communication devices.
[0022] FIG. 15 is a block diagram showing an example wireless communication
device.
[0023] FIG. 16 shows an example exchange of messages in an association process
between a client device and an access point device.
[0024] FIG. 17 shows an example traffic indication map (TIM) element.
[0025] FIG. 18 shows an example MAC header having a frame control field.
2
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
[0026] FIG. 19 shows an example format of a power saving poll message.
[0027] FIG. 20 shows an example control loop that can be used to vary the rate
at which
transmissions are elicited.
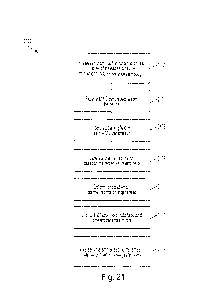
[0028] FIG. 21 shows a flowchart representing an example method of varying a
rate of
eliciting MIMO transmissions from wireless communication devices.
DETAILED DESCRIPTION
[0029] In some aspects of what is described here, a wireless sensing
system can process
wireless signals (e.g., radio frequency signals) transmitted through a space
between
wireless communication devices for wireless sensing applications. Example
wireless
sensing applications include detecting motion, which can include one or more
of the
following: detecting motion of objects in the space, motion tracking,
localization of motion
in a space, breathing detection, breathing monitoring, presence detection,
gesture
detection, gesture recognition, human detection (e.g., moving and stationary
human
detection), human tracking, fall detection, speed estimation, intrusion
detection, walking
detection, step counting, respiration rate detection, sleep pattern detection,
apnea
estimation, posture change detection, activity recognition, gait rate
classification, gesture
decoding sign language recognition, hand tracking heart rate estimation,
breathing rate
estimation, room occupancy detection, human dynamics monitoring, and other
types of
motion detection applications. Other examples of wireless sensing applications
include
object recognition, speaking recognition, keystroke detection and recognition,
tamper
detection, touch detection, attack detection, user authentication, driver
fatigue detection,
traffic monitoring, smoking detection, school violence detection, human
counting, metal
detection, human recognition, bike localization, human queue estimation, Wi-Fi
imaging,
and other types of wireless sensing applications. For instance, the wireless
sensing system
may operate as a motion detection system to detect the existence and location
of motion
based on Wi-Fi signals or other types of wireless signals.
[0030] The examples described herein may be useful for home monitoring. In
some
instances, home monitoring using the wireless sensing systems described herein
may
3
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
provide several advantages, including full home coverage through walls and in
darkness,
discreet detection without cameras, higher accuracy and reduced false alerts
(e.g., in
comparison with sensors that do not use Wi-Fi signals to sense their
environments), and
adjustable sensitivity. By layering Wi-Fi motion detection capabilities into
routers and
gateways, a robust motion detection system may be provided.
[0031] The examples described herein may also be useful for wellness
monitoring.
Caregivers want to know their loved ones are safe, while seniors and people
with special
needs want to maintain their independence at home with dignity. In some
instances,
wellness monitoring using the wireless sensing systems described herein may
provide a
solution that uses wireless signals to detect motion without using cameras or
infringing on
privacy, generates alerts when unusual activity is detected, tracks sleep
patterns, and
generates preventative health data. For example, caregivers can monitor
motion, visits
from health care professionals, and unusual behavior such as staying in bed
longer than
normal. Furthermore, motion is monitored unobtrusively without the need for
wearable
devices, and the wireless sensing systems described herein offer a more
affordable and
convenient alternative to assisted living facilities and other security and
health monitoring
tools.
[0032] The examples described herein may also be useful for setting up a smart
home.
In some examples, the wireless sensing systems described herein use predictive
analytics
and artificial intelligence (AI), to learn motion patterns and trigger smart
home functions
accordingly. Examples of smart home functions that may be triggered included
adjusting
the thermostat when a person walk through the front door, turning other smart
devices on
or off based on preferences, automatically adjusting lighting, adjusting HVAC
systems
based on present occupants, etc.
[0033] In some instances, aspects of the systems and techniques described here
provide
technical improvements and advantages over existing approaches. In some
wireless
network environments, certain wireless communication devices may not
automatically
send MIMO transmissions in response to certain PHY layer or MAC layer
messages. The
PHY layer, also known as the physical layer, can refer to Layer 1 of the Open
System
Interconnection (OS!) model, and the MAC layer, also known as the data link
layer, can
4
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
refer to Layer 2 of the OSI model. In aspects of the systems and techniques
described,
messages initiated by protocols in higher layers (e.g., layers above Layers 1
and 2 of the OSI
model) may be used to elicit MIMO transmissions from wireless communication
devices.
For example, network layer messages (e.g., ICMP Ping, ARP Ping, or modified
versions of
these and other network layer processes) and transport layer messages (e.g.,
TCP Ping, or
modified versions of this and other transport layer processes) may be used to
cause one or
more wireless communication devices to send a wireless transmission that
includes a
MIMO training field.
[0034] The MIMO training field contains signals having a higher frequency
resolution, a
greater number of subcarrier frequencies, and a higher frequency bandwidth
compared to
Legacy training fields in the PHY frame. Use of the MIMO training field for
motion detection
provides more accurate motion detection capabilities. For example, in some
instances,
motion detection can be performed with higher spatial and temporal resolution,
precision,
and accuracy with the use of PHY frames, each having a respective MIMO
training field.
Further, since the MIMO transmissions are elicited using protocols in higher
layers, MIMO
transmissions may be elicited from a broader range of wireless communication
devices, in
a more efficient manner, or both. The ability of a wireless sensing system to
elicit MIMO
transmissions from a broader range of wireless communication devices can allow
the
wireless sensing system to operate in more diverse environments and to cover
greater
spatial areas. In addition, MIMO transmissions may be elicited using existing
resources on
the responding device, for instance, without having to install any additional
hardware,
software, or firmware on the responding device (e.g., reducing or eliminating
a
requirement for specialized motion detection hardware in some cases). Further,
the
systems and techniques described here may be utilized in wireless motion
detection
systems or other types of wireless sensing systems. For instance, eliciting
MIMO
transmissions may be useful in a variety of wireless sensing systems that
utilize channel
state information (CSI) derived from wireless signals (e.g., systems that take
a CSI channel
response and apply digital-signal-processing, machine learning, or other types
of analysis
to the CSI channel response). The technical improvements and advantages
achieved in
examples where the wireless sensing system is used for motion detection may
also be
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
achieved in examples where the wireless sensing system is used for other
wireless sensing
applications.
[0035] In some instances, a wireless sensing system can be implemented using a
wireless communication network. Wireless signals received at one or more
wireless
communication devices in the wireless communication network may be analyzed to
determine channel information for the different communication links (between
respective
pairs of wireless communication devices) in the network. The channel
information may be
representative of a physical medium that applies a transfer function to
wireless signals that
traverse a space. In some instances, the channel information includes a
channel response.
Channel responses can characterize a physical communication path, representing
the
combined effect of, for example, scattering, fading, and power decay within
the space
between the transmitter and receiver. In some instances, the channel
information includes
beamforming state information (e.g., a feedback matrix, a steering matrix,
channel state
information (CSI), etc.) provided by a beamforming system. Beamforming is a
signal
processing technique often used in multi antenna (MIMO) radio systems for
directional
signal transmission or reception. Beamforming can be achieved by operating
elements in
an antenna array in such a way that signals at particular angles experience
constructive
interference while others experience destructive interference.
[0036] The channel information for each of the communication links may be
analyzed
by one or more motion detection algorithms (e.g., running on a hub device, a
client device,
or other device in the wireless communication network, or on a remote device
communicably coupled to the network) to detect, for example, whether motion
has
occurred in the space, to determine a relative location of the detected
motion, or both. In
some aspects, the channel information for each of the communication links may
be
analyzed to detect whether an object is present or absent, e.g., when no
motion is detected
in the space.
[0037] In some instances, a motion detection system returns motion data. In
some
implementations, motion data is a result that is indicative of a degree of
motion in the
space, the location of motion in the space, the direction of motion in the
space, a time at
which the motion occurred, or a combination thereof. In some instances, the
motion data
6
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
can include a motion score, which may include, or may be, one or more of the
following: a
scalar quantity indicative of a level of signal perturbation in the
environment accessed by
the wireless signals; an indication of whether there is motion; an indication
of whether
there is an object present; or an indication or classification of a gesture
performed in the
environment accessed by the wireless signals.
[0038] In some implementations, the motion detection system can be implemented
using one or more motion detection algorithms. Example motion detection
algorithms that
can be used to detect motion based on wireless signals include the techniques
described in
U.S. Patent No. 9,523,760 entitled "Detecting Motion Based on Repeated
Wireless
Transmissions," U.S. Patent No. 9,584,974 entitled "Detecting Motion Based on
Reference
Signal Transmissions," U.S. Patent No. 10,051,414 entitled "Detecting Motion
Based On
Decompositions Of Channel Response Variations," U.S. Patent No. 10,048,350
entitled
"Motion Detection Based on Groupings of Statistical Parameters of Wireless
Signals," U.S.
Patent No. 10,108,903 entitled "Motion Detection Based on Machine Learning of
Wireless
Signal Properties," U.S. Patent No. 10,109,167 entitled "Motion Localization
in a Wireless
Mesh Network Based on Motion Indicator Values," U.S. Patent No. 10,109,168
entitled
"Motion Localization Based on Channel Response Characteristics," U.S. Patent
No.
10,743,143 entitled "Determining a Motion Zone for a Location of Motion
Detected by
Wireless Signals," U.S. Patent No. 10,605,908 entitled "Motion Detection Based
on
Beamforming Dynamic Information from Wireless Standard Client Devices," U.S.
Patent No.
10,605,907 entitled "Motion Detection by a Central Controller Using
Beamforming Dynamic
Information," U.S. Patent No. 10,600,314 entitled "Modifying Sensitivity
Settings in a
Motion Detection System," U.S. Patent No. 10,567,914 entitled "Initializing
Probability
Vectors for Determining a Location of Motion Detected from Wireless Signals,"
U.S. Patent
No. 10,565,860 entitled "Offline Tuning System for Detecting New Motion Zones
in a
Motion Detection System," U.S. Patent No. 10,506,384 entitled "Determining a
Location of
Motion Detected from Wireless Signals Based on Prior Probability," U.S. Patent
No.
10,499,364 entitled "Identifying Static Leaf Nodes in a Motion Detection
System," U.S.
Patent No. 10,498,467 entitled "Classifying Static Leaf Nodes in a Motion
Detection
System," U.S. Patent No. 10,460,581 entitled "Determining a Confidence for a
Motion Zone
7
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
Identified as a Location of Motion for Motion Detected by Wireless Signals,"
U.S. Patent No.
10,459,076 entitled "Motion Detection based on Beamforming Dynamic
Information," U.S.
Patent No. 10,459,074 entitled "Determining a Location of Motion Detected from
Wireless
Signals Based on Wireless Link Counting," U.S. Patent No. 10,438,468 entitled
"Motion
Localization in a Wireless Mesh Network Based on Motion Indicator Values,"
U.S. Patent No.
10,404,387 entitled "Determining Motion Zones in a Space Traversed by Wireless
Signals,"
U.S. Patent No. 10,393,866 entitled "Detecting Presence Based on Wireless
Signal Analysis,"
U.S. Patent No. 10,380,856 entitled "Motion Localization Based on Channel
Response
Characteristics," U.S. Patent No. 10,318,890 entitled "Training Data for a
Motion Detection
System using Data from a Sensor Device," U.S. Patent No. 10,264,405 entitled
"Motion
Detection in Mesh Networks," U.S. Patent No. 10,228,439 entitled "Motion
Detection Based
on Filtered Statistical Parameters of Wireless Signals," U.S. Patent No.
10,129,853 entitled
"Operating a Motion Detection Channel in a Wireless Communication Network,"
U.S. Patent
No. 10,111,228 entitled "Selecting Wireless Communication Channels Based on
Signal
Quality Metrics," and other techniques.
[0039] FIG. 1 illustrates an example wireless communication system 100. The
wireless
communication system 100 may perform one or more operations of a motion
detection
system. The technical improvements and advantages achieved from using the
wireless
communication system 100 to detect motion are also applicable in examples
where the
wireless communication system 100 is used for another wireless sensing
application.
[0040] The example wireless communication system 100 includes three wireless
communication devices 102A, 102B, 102C. The example wireless communication
system
100 may include additional wireless communication devices 102 and/or other
components
(e.g., one or more network servers, network routers, network switches, cables,
or other
communication links, etc.).
[0041] The example wireless communication devices 102A, 102R, 102C can operate
in a
wireless network, for example, according to a wireless network standard or
another type of
wireless communication protocol. For example, the wireless network may be
configured to
operate as a Wireless Local Area Network (WLAN), a Personal Area Network
(PAN), a
metropolitan area network (MAN), or another type of wireless network. Examples
of
8
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
WLANs include networks configured to operate according to one or more of the
802.11
family of standards developed by IEEE (e.g., Wi-Fi networks), and others.
Examples of PANs
include networks that operate according to short-range communication standards
(e.g.,
BLUETOOTHO, Near Field Communication (NFC), ZigBee), millimeter wave
communications, and others.
[0042] In some implementations, the wireless communication devices 102A, 102B,
102C
may be configured to communicate in a cellular network, for example, according
to a
cellular network standard. Examples of cellular networks include networks
configured
according to 2G standards such as Global System for Mobile (GSM) and Enhanced
Data
rates for GSM Evolution (EDGE) or EGPRS; 3G standards such as Code Division
Multiple
Access (CDMA), Wideband Code Division Multiple Access (WCDMA), Universal
Mobile
Telecommunications System (UMTS), and Time Division Synchronous Code Division
Multiple Access (TD-SCDMA); 4G standards such as Long-Term Evolution (LTE) and
LTE-
Advanced (LTE-A); SG standards, and others.
[0043] In some cases, one or more of the wireless communication devices 102 is
a Wi-Fi
access point or another type of wireless access point (WAP). In some cases,
one or more of
the wireless communication devices 102 is an access point of a wireless mesh
network,
such as, for example, a commercially-available mesh network system (e.g.,
GOOGLE Wi-Fi,
EERO mesh, etc.). In some instances, one or more of the wireless communication
devices
102 can be implemented as wireless access points (APs) in a mesh network,
while the other
wireless communication device(s) 102 are implemented as leaf devices (e.g.,
mobile
devices, smart devices, etc.) that access the mesh network through one of the
APs. In some
cases, one or more of the wireless communication devices 102 is a mobile
device (e.g., a
smartphone, a smart watch, a tablet, a laptop computer, etc.), a wireless-
enabled device
(e.g., a smart thermostat, a Wi-Fi enabled camera, a smart TV), or another
type of device
that communicates in a wireless network.
[0044] In the example shown in FIG. 1, the wireless communication devices
transmit
wireless signals to each other over wireless communication links (e.g.,
according to a
wireless network standard or a non-standard wireless communication protocol),
and the
wireless signals communicated between the devices can be used as motion probes
to detect
9
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
motion of objects in the signal paths between the devices. In some
implementations,
standard signals (e.g., channel sounding signals, beacon signals), non-
standard reference
signals, or other types of wireless signals can be used as motion probes.
[0045] In the example shown in FIG. 1, the wireless communication link between
the
wireless communication devices 102A, 102C can be used to probe a first motion
detection
zone 110A, the wireless communication link between the wireless communication
devices
102B, 102C can be used to probe a second motion detection zone 110B, and the
wireless
communication link between the wireless communication device 102A, 102B can be
used
to probe a third motion detection zone 110C. In some instances, the motion
detection zones
110 can include, for example, air, solid materials, liquids, or another medium
through
which wireless electromagnetic signals may propagate.
[0046] In the example shown in FIG. 1, when an object moves in any of the
motion
detection zones 110, the motion detection system may detect the motion based
on signals
transmitted through the relevant motion detection zone 110. Generally, the
object can be
any type of static or moveable object, and can be living or inanimate. For
example, the
object can be a human (e.g., the person 106 shown in FIG. 1), an animal, an
inorganic object,
or another device, apparatus, or assembly, an object that defines all or part
of the boundary
of a space (e.g., a wall, door, window, etc.), or another type of object.
[0047] In some examples, the wireless signals may propagate through a
structure (e.g., a
wall) before or after interacting with a moving object, which may allow the
object's motion
to be detected without an optical line-of-sight between the moving object and
the
transmission or receiving hardware. In some instances, the motion detection
system may
communicate the motion detection event to another device or system, such as a
security
system or a control center.
[0048] In some cases, the wireless communication devices 102 themselves are
configured
to perform one or more operations of the motion detection system, for example,
by
executing computer-readable instructions (e.g., software or firmware) on the
wireless
communication devices. For example, each device may process received wireless
signals to
detect motion based on changes in the communication channel. In some cases,
another
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
device (e.g., a remote server, a cloud-based computer system, a network-
attached device,
etc.) is configured to perform one or more operations of the motion detection
system. For
example, each wireless communication device 102 may send channel information
to a
specified device, system or service that performs operations of the motion
detection
system.
[0049] In an example aspect of operation, wireless communication devices 102A,
102B
may broadcast wireless signals or address wireless signals to the other
wireless
communication device 102C, and the wireless communication device 102C (and
potentially
other devices) receives the wireless signals transmitted by the wireless
communication
devices 102A, 102B. The wireless communication device 102C (or another system
or
device) then processes the received wireless signals to detect motion of an
object in a space
accessed by the wireless signals (e.g., in the zones 110A, 110B). In some
instances, the
wireless communication device 102C (or another system or device) may perform
one or
more operations of a motion detection system.
[0050] FIGS. 2A and 2B are diagrams showing example wireless signals
communicated
between wireless communication devices 204A, 204B, 204C. The wireless
communication
devices 204A, 20413, 204C may be, for example, the wireless communication
devices 102A,
10213, 102C shown in FIG. 1, or may be other types of wireless communication
devices.
[0051] In some cases, a combination of one or more of the wireless
communication
devices 204A, 204B, 204C can be part of, or may be used by, a motion detection
system. The
example wireless communication devices 204A, 204B, 204C can transmit wireless
signals
through a space 200. The example space 200 may be completely or partially
enclosed or
open at one or more boundaries of the space 200. The space 200 may be or may
include an
interior of a room, multiple rooms, a building, an indoor area, outdoor area,
or the like. A
first wall 202A, a second wall 202B, and a third wall 202C at least partially
enclose the
space 200 in the example shown.
[0052] In the example shown in FIGS. 2A and 2B, the first wireless
communication device
204A transmits wireless motion probe signals repeatedly (e.g., periodically,
intermittently,
at scheduled, unscheduled or random intervals, etc.). The second and third
wireless
11
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
communication devices 204B, 204C receive signals based on the motion probe
signals
transmitted by the wireless communication device 204A.
[0053] As shown, an object is in a first position 214A at an initial time (t0)
in FIG. 2A, and
the object has moved to a second position 214B at subsequent time (t1) in FIG.
2B. In FIGS.
2A and 2B, the moving object in the space 200 is represented as a human, but
the moving
object can be another type of object. For example, the moving object can be an
animal, an
inorganic object (e.g., a system, device, apparatus, or assembly), an object
that defines all or
part of the boundary of the space 200 (e.g., a wall, door, window, etc.), or
another type of
object. In the example shown in FIGS. 2A and 2B, the wireless communication
devices
204A, 204B, 204C are stationary and are, consequently, at the same position at
the initial
time tO and at the subsequent time t1. However, in other examples, one or more
of the
wireless communication devices 204A, 204B, 204C may be mobile and may move
between
initial time tO and subsequent time t1.
[0054] As shown in FIGS. 2A and 2B, multiple example paths of the wireless
signals
transmitted from the first wireless communication device 204A are illustrated
by dashed
lines. Along a first signal path 216, the wireless signal is transmitted from
the first wireless
communication device 204A and reflected off the first wall 202A toward the
second
wireless communication device 20413. Along a second signal path 218, the
wireless signal is
transmitted from the first wireless communication device 204A and reflected
off the
second wall 202B and the first wall 202A toward the third wireless
communication device
204C. Along a third signal path 220, the wireless signal is transmitted from
the first
wireless communication device 204A and reflected off the second wall 202B
toward the
third wireless communication device 204C. Along a fourth signal path 222, the
wireless
signal is transmitted from the first wireless communication device 204A and
reflected off
the third wall 202C toward the second wireless communication device 204B.
[0055] In FIG. 2A, along a fifth signal path 224A, the wireless signal is
transmitted from
the first wireless communication device 204A and reflected off the object at
the first
position 214A toward the third wireless communication device 204C. Between
time tO in
FIG. 2A and time t1 in FIG. 2B, the object moves from the first position 214A
to a second
position 214B in the space 200 (e.g., some distance away from the first
position 214A). In
12
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
FIG. 2B, along a sixth signal path 224B, the wireless signal is transmitted
from the first
wireless communication device 204A and reflected off the object at the second
position
214B toward the third wireless communication device 204C. The sixth signal
path 224B
depicted in FIG. 213 is longer than the fifth signal path 224A depicted in
FIG. 2A due to the
movement of the object from the first position 214A to the second position
214B. In some
examples, a signal path can be added, removed, or otherwise modified due to
movement of
an object in a space.
[0056] The example wireless signals shown in FIGS. 2A and 2B may experience
attenuation, frequency shifts, phase shifts, or other effects through their
respective paths
and may have portions that propagate in another direction, for example,
through the walls
202A, 202B, and 202C. In some examples, the wireless signals are radio
frequency (RF)
signals. The wireless signals may include other types of signals.
[0057] The transmitted signal may have a number of frequency components in a
frequency bandwidth, and the transmitted signal may include one or more bands
within
the frequency bandwidth. The transmitted signal may be transmitted from the
first
wireless communication device 204A in an omnidirectional manner, in a
directional
manner or otherwise. In the example shown, the wireless signals traverse
multiple
respective paths in the space 200, and the signal along each path may become
attenuated
due to path losses, scattering, reflection, or the like and may have a phase
or frequency
offset.
[0058] As shown in FIGS. 2A and 2B, the signals from various paths 216, 218,
220, 222,
224A, and 224B combine at the third wireless communication device 204C and the
second
wireless communication device 204B to form received signals. Because of the
effects of the
multiple paths in the space 200 on the transmitted signal, the space 200 may
be
represented as a transfer function (e.g., a filter) in which the transmitted
signal is input and
the received signal is output. When an object moves in the space 200, the
attenuation or
phase offset applied to a wireless signal along a signal path can change, and
hence, the
transfer function of the space 200 can change. When the same wireless signal
is
transmitted from the first wireless communication device 204A, if the transfer
function of
the space 200 changes, the output of that transfer function, e.g. the received
signal, can also
13
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
change. A change in the received signal can be used to detect motion of an
object
Conversely, in some cases, if the transfer function of the space does not
change, the output
of the transfer function - the received signal - may not change.
[0059] FIG. 2C is a diagram showing an example wireless sensing system
operating to
detect motion in a space 201. The example space 201 shown in FIG. 2C is a home
that
includes multiple distinct spatial regions or zones. In the example shown, the
wireless
motion detection system uses a multi-AP home network topology (e.g., mesh
network or a
Self-Organizing-Network (SON)), which includes three access points (APs): a
central access
point 226 and two extension access points 228A, 228B. In a typical multi-AP
home
network, each AP typically supports multiple bands (2.4G. SG, 6G), and
multiple bands may
be enabled at the same time. Each AP may use a different Wi-Fi channel to
serve its clients,
as this may allow for better spectrum efficiency.
[0060] In the example shown in FIG. 2C, the wireless communication network
includes a
central access point 226. In a multi-AP home Wi-Fi network, one AP may be
denoted as the
central AP. This selection, which is often managed by manufacturer software
running on
each AP, is typically the AP that has a wired Internet connection 236. The
other APs 228A,
22813 connect to the central AP 226 wirelessly, through respective wireless
backhaul
connections 230A, 23013. The central AP 226 may select a wireless channel
different from
the extension APs to serve its connected clients.
[0061] In the example shown in FIG. 2C, the extension APs 228A, 22813 extend
the range
of the central AP 226, by allowing devices to connect to a potentially closer
AP or different
channel. The end user need not be aware of which AP the device has connected
to, as all
services and connectivity would generally be identical. In addition to serving
all connected
clients, the extension APs 228A, 228B connect to the central AP 226 using the
wireless
backhaul connections 230A, 230B to move network traffic between other APs and
provide
a gateway to the Internet. Each extension AP 228A, 22811 may select a
different channel to
serve its connected clients.
[0062] In the example shown in FIG. 2C, client devices (e.g., Wi-Fi
client devices) 232A,
23213, 232C, 232D, 232E, 232F, 232G are associated with either the central AP
226 or one
14
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
of the extension APs 228 using a respective wireless link 234A, 234B, 234C,
234D, 234E,
234F, 234G. The client devices 232 that connect to the multi-AP network may
operate as
leaf nodes in the multi-AP network. In some implementations, the client
devices 232 may
include wireless-enabled devices (e.g., mobile devices, a smartphone, a smart
watch, a
tablet, a laptop computer, a smart thermostat, a wireless-enabled camera, a
smart TV, a
wireless-enabled speaker, a wireless-enabled power socket, etc.).
[0063] When the client devices 232 seek to connect to and associate with their
respective APs 226, 228, the client devices 232 may go through an
authentication and
association phase with their respective APs 226, 228. Among other things, the
association
phase assigns address information (e.g., an association ID or another type of
unique
identifier) to each of the client devices 232. For example, within the IEEE
802.11 family of
standards for Wi-Fl, each of the client devices 232 may identify itself using
a unique
address (e.g., a 48-bit address, an example being the MAC address), although
the client
devices 232 may be identified using other types of identifiers embedded within
one or
more fields of a message. The address information (e.g., MAC address or
another type of
unique identifier) can be either hardcoded and fixed, or randomly generated
according to
the network address rules at the start of the association process. Once the
client devices
232 have associated to their respective APs 226, 228, their respective address
information
may remain fixed. Subsequently, a transmission by the APs 226, 228 or the
client devices
232 typically includes the address information (e.g., MAC address) of the
transmitting
wireless device and the address information (e.g., MAC address) of the
receiving device.
[0064] In the example shown in FIG. 2C, the wireless backhaul connections
230A, 230B
carry data between the APs and may also be used for motion detection. Each of
the wireless
backhaul channels (or frequency bands) may be different than the channels (or
frequency
bands) used for serving the connected Wi-Fl devices.
[0065] In the example shown in FIG. 2C, wireless links 234A, 234B,
234C, 234D, 234E,
234F, 234G may include a frequency channel used by the client devices 232A,
232B, 232C,
232D, 232E, 232F, 232G to communicate with their respective APs 226, 228. Each
AP may
select its own channel independently to serve their respective client devices,
and the
wireless links 234 may be used for data communications as well as motion
detection.
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
[0066] The motion detection system, which may include one or more motion
detection
or localization processes running on the one or more of the client devices 232
or on one or
more of the APs 226, 228, may collect and process data (e.g., channel
information)
corresponding to local links that are participating in the operation of the
wireless sensing
system. The motion detection system may be installed as a software or firmware
application on the client devices 232 or on the APs 226, 228, or may be part
of the
operating systems of the client devices 232 or the APs 226, 228.
[0067] In some implementations, the APs 226, 228 do not contain motion
detection
software and are not otherwise configured to perform motion detection in the
space 201.
Instead, in such implementations, the operations of the motion detection
system are
executed on one or more of the client devices 232. In some implementations,
the channel
information may be obtained by the client devices 232 by receiving wireless
signals from
the APs 226, 228 (or possibly from other client devices 232) and processing
the wireless
signal to obtain the channel information. For example, the motion detection
system
running on the client devices 232 may have access to channel information
provided by the
client device's radio firmware (e.g., Wi-Fi radio firmware) so that channel
information may
be collected and processed.
[0068] In some implementations, the client devices 232 send a request to their
corresponding AP 226, 228 to transmit wireless signals that can be used by the
client
device as motion probes to detect motion of objects in the space 201. The
request sent to
the corresponding AP 226, 228 may be a null data packet frame, a beamforming
request, a
ping, standard data traffic, or a combination thereof. In some
implementations, the client
devices 232 are stationary while performing motion detection in the space 201.
In other
examples, one or more of the client devices 232 may be mobile and may move
within the
space 201 while performing motion detection.
[0069] Mathematically, a signal f (t) transmitted from a wireless
communication device
(e.g., the wireless communication device 204A in FIGS. 2A and 2B or the APs
226, 228 in
FIGS. 2C) may be described according to Equation (1):
16
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
f(t) = cnei'nt
n=-00
where coõ represents the frequency of nth frequency component of the
transmitted signal,
cn represents the complex coefficient of the nth frequency component, and t
represents
time. With the transmitted signal f(t) being transmitted, an output signal
rk(t) from a path
k may be described according to Equation (2):
rk(t) = ,
an kaneiC(Dnt+.1),,,k)
(2)
n=-00
where aõ,k represents an attenuation factor (or channel response; e.g., due to
scattering,
reflection, and path losses) for the nth frequency component along path k, and
cp,,k
represents the phase of the signal for nth frequency component along path k.
Then, the
received signal R at a wireless communication device can be described as the
summation of
all output signals rk(t) from all paths to the wireless communication device,
which is
shown in Equation (3):
R =Irk(t)
(3)
Substituting Equation (2) into Equation (3) renders the following Equation
(4):
R =11 (an,keickn')cnejwnt
(4)
k n=-00
[0070] The received signal R at a wireless communication device (e.g., the
wireless
communication devices 204B, 204C in FIGS. 2A and 2B or the client devices 232
in FIGS.
2C) can then be analyzed (e.g., using one or more motion detection algorithms)
to detect
motion. The received signal R at a wireless communication device can be
transformed to
the frequency domain, for example, using a Fast Fourier Transform (FFT) or
another type
of algorithm. The transformed signal can represent the received signal R as a
series of n
complex values, one for each of the respective frequency components (at the n
frequencies
wõ). For a frequency component at frequency wn, a complex value Yn may be
represented
as follows in Equation (5):
17
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
I = criamkei0mk .
(5)
[0071] The complex value Y for a given frequency component can indicates a
relative
magnitude and phase offset of the received signal at that frequency component
con. The
signal f (t) may be repeatedly transmitted within a time period, and the
complex value
Yr, can be obtained for each transmitted signal f (t). When an object moves in
the space, the
complex value Yi.õ changes over the time period due to the channel response
aõ,k of the
space changing. Accordingly, a change detected in the channel response (and
thus, the
complex value Yri) can be indicative of motion of an object within the
communication
channel. Conversely, a stable channel response may indicate lack of motion.
Thus, in some
implementations, the complex values Yr, for each of multiple devices in a
wireless network
can be processed to detect whether motion has occurred in a space traversed by
the
transmitted signals f (t). The channel response can be expressed in either the
time-domain
or frequency-domain, and the Fourier-Transform or Inverse-Fourier-Transform
can be
used to switch between the time-domain expression of the channel response and
the
frequency-domain expression of the channel response.
[0072] In another aspect of FIGS. 2A, 2B, 2C, beamforming state information
may be used
to detect whether motion has occurred in a space traversed by the transmitted
signals [(t).
For example, beamforming may be performed between devices based on some
knowledge
of the communication channel (e.g., through feedback properties generated by a
receiver),
which can be used to generate one or more steering properties (e.g., a
steering matrix) that
are applied by a transmitter device to shape the transmitted beam/signal in a
particular
direction or directions. In some instances, changes to the steering or
feedback properties
used in the beamforming process indicate changes, which may be caused by
moving objects
in the space accessed by the wireless signals. For example, motion may be
detected by
identifying substantial changes in the communication channel, e.g. as
indicated by a
channel response, or steering or feedback properties, or any combination
thereof, over a
period of time.
[0073] In some implementations, for example, a steering matrix may be
generated at a
transmitter device (beamformer) based on a feedback matrix provided by a
receiver device
18
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
(beamformee) based on channel sounding. Because the steering and feedback
matrices are
related to propagation characteristics of the channel, these beamforming
matrices change
as objects move within the channel. Changes in the channel characteristics are
accordingly
reflected in these matrices, and by analyzing the matrices, motion can be
detected, and
different characteristics of the detected motion can be determined. In some
implementations, a spatial map may be generated based on one or more
beamforming
matrices. The spatial map may indicate a general direction of an object in a
space relative to
a wireless communication device. In some cases, "modes" of a beamforming
matrix (e.g., a
feedback matrix or steering matrix) can be used to generate the spatial map.
The spatial
map may be used to detect the presence of motion in the space or to detect a
location of the
detected motion.
[0074] In some implementations, the output of the motion detection system may
be
provided as a notification for graphical display on a user interface on a user
device. In some
implementations, the user device is the device used to detect motion, a user
device of a
caregiver or emergency contact designated to an individual in the space 200,
201, or any
other user device that is communicatively coupled to the motion detection
system to
receive notifications from the motion detection system.
[0075] In some instances, the graphical display includes a plot of
motion data indicating
a degree of motion detected by the motion detection system for each time point
in a series
of time points. The graphical display can display the relative degree of
motion detected by
each node of the motion detection system. The graphical display can help the
user
determine an appropriate action to take in response to the motion detection
event,
correlate the motion detection event with the user's observation or knowledge,
determine
whether the motion detection event was true or false, etc.
[0076] In some implementations, the output of the motion detection system may
be
provided in real-time (e.g., to an end user). Additionally or alternatively,
the output of the
motion detection system may be stored (e.g., locally on the wireless
communication devices
204, client devices 232, the APs 226, 228, or on a cloud-based storage
service) and
analyzed to reveal statistical information over a time frame (e.g., hours,
days, or months).
An example where the output of the motion detection system may be stored and
analyzed
19
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
to reveal statistical information over a time frame is in health monitoring,
vital sign
monitoring, sleep monitoring, etc. In some implementations, an alert (e.g., a
notification, an
audio alert or a video alert) may be provided based on the output of the
motion detection
system. For example, a motion detection event may be communicated to another
device or
system (e.g., a security system or a control center), a designated caregiver,
or a designated
emergency contact based on the output of the motion detection system.
[0077] In some implementations, a wireless motion detection system can detect
motion
by analyzing components of wireless signals that are specified by a wireless
communication standard. For example, a motion detection system may analyze
standard
headers of wireless signals exchanged in a wireless communication network. One
such
example is the IEEE 802.11ax standard, which is also known as `Wi-Fi 6." A
draft of the
IEEE 802.11ax standard is published in a document entitled "P802.11ax/D4.0,
IEEE Draft
Standard for Information Technology ¨ Telecommunications and Information
Exchange
Between Systems Local and Metropolitan Area Networks ¨ Specific Requirements
Part 11:
Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY)
Specifications
Amendment Enhancements for High Efficiency WLAN," March 2019, which is
accessible at
https://ieeexplore.ieee.org/document/8672643 and hereby incorporated by
reference in
its entirety. Standard headers specified by other types of wireless
communication
standards may be used for motion detection in some cases.
[0078] In some implementations, a motion detection algorithm used by a
wireless
motion detection system utilizes a channel response (an output of a channel
estimation
process) computed by a wireless receiver (e.g., a Wi-Fl receiver). For
example, the channel
responses computed by a channel estimation process according to a Wi-F! 6
standard may
be received as inputs to the motion detection algorithm. The channel
estimation in the Wi-
Fi 6 standard occurs at the PHY layer, using the PHY Frame (the PHY Frame is
also called a
PPDU) of the received wireless signal.
[0079] In some examples, a motion detection algorithm employed by a wireless
motion
detection system uses channel responses computed from orthogonal frequency-
division
multiplexing (OFDM)-based PHY frames (including those produced by the Wi-Fi 6
standard). The OFDM-based PHY frames can, in some instances, be frequency-
domain
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
signals having multiple fields, each having a corresponding frequency-domain
signal. With
this class of OFDM-based PHY frames, there are typically two types of PPDU
fields that
allow the Wi-Fl receiver to estimate the channel. The first is the Legacy-
Training-Field, and
the second are the MIMO-Training-Fields. Either or both fields may be used for
motion
detection. An example of a MIMO-Training-Field that may be used is the so-
called "High-
Efficiency Long Training Field" known as HE-PHY (e.g., in the Wi-Fi 6
standard, according
to the IEEE 802.11ax standard).
[0080] FIG. 3 shows an example PHY Frame 300 that includes an HE-LTF. The
example
PHY Frame 300 shown in FIG. 3 is from the IEEE 802.11ax standard. These and
other types
of PHY frames that include an HE-LTF may be used for motion detection in some
cases. As
shown in FIG. 3, the example PHY Frame 300 includes a number of fields that
are defined in
the 802.11 standard: L-STF (Legacy Short Training Field), L-LTF (Legacy Long
Training
Field), L-SIG (Legacy Signal), RL-SIG (Repeated Legacy Signal), HE-SIG-A (High-
Efficiency
Signal), HE-STF (High-Efficiency Short Training Field), multiple HE-LTFs,
Data, PE (Packet
Extension). In some instances, the L-LTF field can be used to estimate channel
responses
that can be provided as input to a motion detection algorithm. The HE-LTF
fields, which are
provided as MIMO Training Fields, can also be used to estimate channel
responses that can
be provided as input to a motion detection algorithm.
[0081] In the example shown in FIG. 3, the HE-LTFs can have variable duration
and
bandwidths, and in some examples the PHY Frame 300 breaks a 20 MHz channel
into 256
frequency points (instead of 64 used by previous PHY Frame versions). As such,
the
example HE-LTFs in the PHY Frame 300 may provide four times better frequency
resolution (e.g., compared to earlier PHY frame versions), as each point
represents a
frequency bandwidth of 78.125 kHz instead of 312.5 kHz. Also, the HE-LTF
provides more
continuous subcarriers than other fields, and hence a wider continuous
bandwidth can be
used for motion detection. For instance, Table I (below) shows the continuous
bandwidths
and frequency resolution for the HE-LTF field (labeled "HE" in the table)
compared to
Legacy PHY fields (L-STF and L-LTF) and other MIMO Training Fields (e.g., High-
Throughput (HT) Long Training Field and Very-High-Throughput (VHT) Long
Training
Field).
21
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
Continuous Continuous
Continuous
Continuous HE
Bandwidth HE Legacy
HT/VHT
Bandwidth
Subcarriers Bandwidth
Bandwidth
9.453 MHz 8.125 MHz 8.750
MHz
20MHz 121
(121*78.125kHz) (26 Subcarriers) (28
Subcarriers)
18.91 MHz 8.125 MHz
17.8125 MHz
40MHz 242
(242*78.125kHz) (26 Subcarriers) (56
Subcarriers)
38.91 MHz 8.125 MHz
17.8125 MHz
80MHz 498
(498*78.125kHz) (26 Subcarriers) (56
Subcarriers)
38.91 MHz 8.125 MHz
17.8125 MHz
160MHz 498
(498*78.125kHz) (26 Subcarriers) (56
Subcarriers)
TABLE I
[0082] In some IEEE 802.11 standards, the PHY layer is broken into 2 sub-
layers: the
PLCP Sublayer (Physical Layer Convergence Procedure), and the PMD Sublayer
(PHY
Medium Dependant). The PLCP Sublayer (Physical Layer Convergence Procedure)
takes
data from the MAC layer and translates it into a PHY frame format. The format
of the PHY
frame is also referred to as a PPDU (PLCP Protocol Data Unit). A PPDU may
include fields
that are used for channel estimation. The PMD Sublayer (PHY Medium Dependant)
provides a modulation scheme for the PHY layer. There are many different IEEE
802.11
based PHY frame formats defined. In some examples, a wireless motion detection
system
uses information derived from OFDM based PHY frames, such as, for example,
those
described in the following standard documents: IEEE 802.11a-1999: Legacy OFDM
PHY;
IEEE 802.11n-2009: HT PHY (High-Throughput); IEEE 802.11ac-2013: VHT PHY (Very-
High-Throughput); IEEE 802.11ax (Draft 4.0, March 2019): HE PHY (High-
Efficiency).
[0083] Other types of PHY layer data may be used, and each PHY layer
specification may
provide its own PPDU format. For instance, the PPDU format for a PHY layer
specification
may be found in some IEEE 802.11 standards under the section heading "<XXX>
PHY
Specification" ==> "<XXX> PHY" ==> "<XXX> PPDU Format". The example PHY frame
300
shown in FIG. 3 is an HE PHY frame provided by an ODFM PHY layer of an example
802.11
standard.
22
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
[0084] In some IEEE 802.11 standards (e.g., IEEE 802.11a-1999), the OFDM PHY
divides
a 20 MHz channel into 64 frequency bins. Modulation and Demodulation is done
using 64-
point complex inverse Fast Fourier Transform (IFFT) and Fast Fourier Transform
(FFT). In
an example modulation process: data bits grouped (e.g., depending on QAM
constellation),
each group of bits is assigned to one of the subcarriers (or frequency bins);
depending on
QAM constellation, group of bits mapped to a complex number for each
subcarrier; and a
64-point IFFT is performed to generate complex-time-domain I and Q waveforms
for
transmission. In an example demodulation process: complex I and Q time domain
signals
are received; a 64-point FFT is performed to compute complex number for each
subcarrier;
depending on QAM constellation, each subcarrier complex number is mapped to
bits; and
bits from each subcarrier are re-assembled into data. In a typical modulation
or
demodulation process, not all 64 subcarriers are used; for example, only 52 of
the
subcarriers may be considered valid for data and pilot, and the rest of the
subcarriers may
be considered NULLED. The PHY layer specifications in more recently-developed
IEEE
802.11 standards utilize larger channel bandwidths (e.g., 40 MHz, 80 MHz, and
160 MHz).
[0085] FIG. 4 shows an example PHY Frame 400 that includes a Very High
Throughput
Long Training Field (also referred to as "VHT-LTF"). The example PHY Frame 400
shown in
FIG. 4 is from the IEEE 802.11ac standard. A draft of the IEEE 802.11ac
standard is
published in a document entitled "802.11ac-2013 - IEEE Standard for
Information
technology--Telecommunications and information exchange between systems¨Local
and
metropolitan area networks¨Specific requirements¨Part 11: Wireless LAN Medium
Access
Control (MAC) and Physical Layer (PHY) Specifications--Amendment 4:
Enhancements for
Very High Throughput for Operation in Bands below 6 GHz," Dec. 2018, which is
accessible
at https://ieeexplore.ieee.org/document/7797535 and hereby incorporated by
reference
in its entirety. These and other types of PHY frames that include a VHT-LTF
may be used for
motion detection in some cases.
[0086] As shown in FIG. 4, the example PHY Frame 400 includes a number of
components that are defined in the 802.11 standard: L-STF, L-LTF, L-SIG, VHT-
SIG-A (Very-
High-Throughput Signal A), VHT-STF (Very-High-Throughput Short Training
Field), VHT-
LTF (Very-High-Throughput Long Training Field), VHT-SIG-B (Very-High-
Throughput
23
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
Signal B), Data. The PPDU for Legacy, HT, VHT, and HE PHYs begin with a Legacy
Preamble
which includes the L-STF and the L-LTF, as shown in the example PHY frame 400
in FIG. 4.
The L-LTF can be used for channel estimation in some cases. The VHT-LTF, which
has a
wider bandwidth compared to the L-LTF and contains similar information, can be
used for
MIMO channel estimation. The HT-LTF and VHT-LTF are very similar, except that
the VHT-
LTF allows higher order MIMO and allows 80 MHz and 160 MHz channels. These
fields are
beneficial to use for motion detection because they can provide wider
continuous
bandwidth and MIMO channel information. With MIMO channel estimation, there
are
generally Nr x Nc channel responses computed. This provides more information
with
benefit to motion detection. FIG. 5 shows an example MIMO device configuration
500
including a transmitter having Nr antennas and a receiver having Nc antennas.
In the
example of FIG. 5, Nr x Nc channel responses may be computed based on the HE-
LTF or the
VHT-LTF or another MIMO training component of a PHY frame.
[0087] In some implementations, a wireless communication device computes a
channel
response, for example, by performing a channel estimation process based on a
PHY frame.
For instance, a wireless communication device may perform channel estimation
based on
the example PHY frame 300 shown in FIG. 3, the example PHY frame 400 shown in
FIG. 4,
or another type of PHY frame from a wireless signal.
[0088] In some instances, the channel information used for motion detection
may
include a channel response generated by channel estimation based on the L-LTF
in the PHY
frame. The L-LTF in the 802-11ax standard can be equivalent to the LTF in the
IEEE
802.11a - 1999 standard. The L-LTF may be provided in the frequency domain as
an input
to a 64-point IFFT. Typically, only 52 of the 64 points are considered valid
points for
channel estimation; and the remaining points (points [-32, -26) and (26, 311)
are zero. As
described in the IEEE 802.11a - 1999 standard, the L-LTF may be a long OFDM
training
symbol including 53 subcarriers (including a zero value at DC), which are
modulated by the
elements of a sequence L given by the following:
L-26,26 = 1, -1, -1, 1, 1, -1, - 1, 1, 1, 1, 1, 1, -1, -1, 1, - 1, -
1, 1, 1, 1, 1, 0,
- -1, 1, 1, -1, 1, -1, 1, - -1, -1, -1, -1, 1, 1, -
- -1, 1, 1, 1, 1)
24
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
[0089] The example "L" vector shown above represents the complex frequency-
domain
representation of the field at baseband (centered around DC) and is described
in page 13 of
a draft of the IEEE 802.11a - 1999 standard. The draft of the IEEE 802.11a -
1999 standard
is published in a document entitled "802.11a-1999 - IEEE Standard for
Telecommunications and Information Exchange Between Systems - LAN/MAN Specific
Requirements - Part 11: Wireless Medium Access Control (MAC) and physical
layer (PHY)
specifications: High Speed Physical Layer in the 5 GHz band" and accessible at
https://ieeexploredeee.org/document/815305. The example "L" vector is
considered
"Legacy", as it was part of the original OFDM PHY specification, and is
considered part of
the legacy preamble. Hence in later specification versions, it is referred to
as the L-LTF (for
Legacy-Long Training Field).
[0090] In some instances, the channel information used for motion detection
may
include a channel response generated by channel estimation based on one or
more of the
MIMO training fields in the PHY frame (e.g., the HE-LTF, HT-LTF, or VHT-LTF
fields). The
HE-LTF may be provided in the frequency domain as an input to a 256-point
IFFT. With a
typical HE-LTF, there are 241 valid points (e.g., instead of 52 as in the
legacy case). Each
point in the HE-LTF represents a frequency range of 78.125 kHz, whereas each
Legacy
point represents a larger frequency range of 312.5 kHz. Therefore, the HE-LTF
may provide
higher frequency resolution, more frequency domain data points, and a larger
frequency
bandwidth, which can provide more accurate and higher-resolution (e.g., higher
temporal
and spatial resolution) motion detection. An example HE-LTF is described on
page 561 of
the draft of the IEEE 802.11ax standard as follows:
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
In a 20 MHz trainninsion, the 4x HE-LIT requenee transmitted on subcarriers [-
122: 122] ir2 given by
Equation (27-42).
HELTF_322.22,=
{-1, ¨1, +1 ¨1 +1, ¨1 +1 ¨1, +1, ¨1 ¨1, +1. +1 ¨1 ¨1. +1 ¨1, ¨1, ¨1. ¨1
+1
-F1,-1 -1 -1 -1 +1 -1 -1, -4 -1,-1,-F1,-1 -F1,-1 -1,-1,-1 -t, +1 ¨f, +1 ¨1
+1. +1_ ¨1,-1.-1
- ¨1, ¨1, ¨1, ¨1, ¨1, ¨1, +1. ¨1. ¨1, ¨1. ¨1. ¨1, ¨1, ¨1, ¨1, +1. +1. ¨1.
¨1. ¨1. ¨1. ¨
1, ¨I, ¨1, ¨1, +1_ +I, +1_ ¨1_ +1_ +1_ +1_ ¨1_ +1_ ¨1_ +1_ ¨1. ¨1. ¨1. ¨1. ¨1_
+1_ ¨1_ +1_
¨1_ ¨1,-1, ¨1,-1_ +1_ +1, +1, 0, 0, 0_ ¨1, +1, ¨1, +1_ (27-
42) ¨1 +1, +1_ ¨1, +1_ ¨1, +1_ ¨1, ¨1_
+1, ¨1,-1, +1.¨I, +1. ¨1. +1. +1.¨I. ¨1.¨i. +1, +1. ¨1. ¨1. --1, ¨1. ¨/, ¨1.
¨1,-1, +1.
+1, ¨1, ¨1, ¨1, ¨1,¨i, +1. ¨1. +1, ¨1, ¨1, ¨1,¨I, ¨1, ¨1,4-1. +1. ¨1. ¨1.
+1, ¨1. ¨
1: ¨1: ¨1: +1: +1. ¨1 +1. +1. +1. ¨1. ¨1. ¨1. ¨1. ¨1. ¨1. ¨1. ¨1. ¨1. ¨1. ¨1.
¨1. ¨1. ¨1.
+1_ +1_ ¨1_ ¨1, ¨1, ¨1, +1, ¨1_ ¨1_
¨1, +1. ¨1, +1,-1_ ¨1,+1_ ¨1, +1_ +1_
¨1, ¨1, ¨1_ ¨1_ ¨1, ¨1_ ¨1_ ¨1 ¨1, ¨1, ¨1 -h1 ¨1_ ¨1, ¨1. ¨1)
[0091] In some instances, a channel response can be estimated on a receiver
device by
performing an FFT of the received time-domain sequence (e.g., the example L-
LTF and HE-
LTF sequences shown above), and dividing by the expected result [
CH(N)=RX(N)/L(N) ].
The 64-Point FFT Bin 600 in the top portion of FIG. 6 shows the resulting
spectrum that can
be measured (20 MHz and 40 MHz channels) from the L-LTF in an example PHY
frame. The
128-Point FFT Bin 650 in the bottom portion of FIG. 6 shows the resulting
spectrum that
can be measured for the same 20 MHz channels from the HE-LTF in an example PHY
frame.
As shown in FIG. 6, the HE-LTF may provide higher frequency resolution (more
points in
the same frequency bandwidth), a higher number of frequency domain data points
(more
bins), and a larger frequency bandwidth.
[0092] In some aspects of what is described here, messages initiated
by protocols in
higher layers (e.g., layers above Layers 1 and 2 of the OSI model) may be used
to elicit
MIMO transmissions from wireless communication devices. The MIMO wireless
signal can
be used for motion detection or another type of wireless sensing application.
In some
implementations, the MIMO wireless signal includes a MIMO training field that
can be used
for motion detection. In some aspects, the HT-LTF, VHT-LTF or HE-LTF field in
a PHY frame
of a wireless transmission according to an IEEE Wi-Fi standard may be used for
motion
detection. Such wireless signals may be transmitted through a space over a
time period, for
example, from one wireless communication device to another. A MIMO training
field (e.g.,
the HT-LTF, VHT-LTF or HE-LTF field) may be identified in the PHY frame of
each wireless
26
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
signal, and channel information may be generated based on the respective MIMO
training
fields. The channel information may then be used for wireless sensing (e.g.,
to detect
motion of an object, to detect breathing, to detect gestures, etc.) of the
space during the
time period.
[0093] FIG. 7 is a diagram showing a typical representation of the Open System
Interconnection (OSI) model 700. As shown in FIG. 7, the typical OSI
networking model
defines seven layers: (Layer 1) the physical layer, (Layer 2) the data link
layer, (Layer 3)
the network layer, (Layer 4) the transport layer, (Layer 5) the session layer,
(Layer 6) the
presentation layer, (Layer 7) the application layer. A networking model may
define
additional or different layers in some cases.
[0094]
As shown in FIG. 7, each of the OSI layers provides specified
functionality and
defines specified data objects. A user application (e.g., operating in Layer 6
and/or Layer 7)
operating on a device can communicate using the standard network features
represented
in the OSI model 700; the user application may initiate such communication by
interacting
with the operating system (OS) socket library in the session layer. As shown
in FIG. 7, the
OS socket library exists in Layer 5, and due to standardization has virtually
the same API on
all modern operating systems (e.g., Linux, Windows, Android, OSX, etc). Each
session may
be identified by a "socket handle" that is returned to the user application by
the operating
system, and the user application may use the socket handle when interacting
with the
Socket API.
[0095] In the example OSI model 700 shown in FIG. 7, the transport layer
(Layer 4)
defines a way for multiple applications to talk to each other. There are many
transport
layer protocols used; the most common are: TCP (Transmission Control
Protocol), and UDP
(User Datagram Protocol). Applications can select, via the socket API, which
protocol to use
for communication. Transport layer messages and the corresponding contents are
identified by a "port number," which is typically is a 16-bit value. Many
standardized
applications have dedicated port numbers; for example, a web server typically
communicates on port 80, and the OS Socket Library knows to pass data received
on port
80 to the socket handle belonging to the web server.
27
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
[0096] In the example OSI model 700 shown in FIG. 7, below the transport layer
(Layer
4) is the network layer (Layer 3). The network layer provides Internet
Protocol (IP)
resources, which primarily allow grouping of multiple devices into a logical
network.
Network layer services generally allow for identification of both logical
network and
physical device, as well as providing mechanisms for different networks to
communicate
with each other (typically referred to as routing). For example, the network
layer may
include Internet Protocol version 4 (IPv4), Internet Protocol version 6 (IPv6)
or another IP
version. The Internet Protocol (IP) may serve as the communications protocol
for
relaying data between devices and across network boundaries (e.g., over the
Internet). In
some examples, each device is identified by a logical 32-bit address (e.g., in
IPv4), or a 128-
bit address (e.g., IPv6) in the network layer. Both an IPv4 and IPv6 address
contain a
network portion, and a device portion, which is determined based on
standardized criteria.
[0097] In the example OSI model 700 shown in FIG. 7, below the network layer
(Layer
3) is the data link layer (Layer 2) and the physical layer (Layer 1). The data
link layer (also
known as the MAC layer) handles coordinating how multiple devices communicate
using a
shared media (e.g., a shared wireless channel for Wi-Fi, or another form of
shared media).
In the MAC layer, each device is identified by a 48-bit MAC address. In Wi-Fi
networks, the
network layer and the data link layer are defined by the IEEE 802.11
standards. The
physical layer generates PHY frames for communication between devices.
[0098] In some systems, a motion detection algorithm employed by a wireless
motion
detection system uses channel responses computed from orthogonal frequency-
division
multiplexing (OFDM)-based PHY frames (including those defined by IEEE 802.11
standards
for Wi-Fi networks). For OFDM modulation, Wi-Fi signals contain multiple
fields that can
be used to compute a channel estimation or response. First, there is the
Legacy-LTF (Long
Training Field), which is generally present on every Wi-Fi message. Second,
there are the
MIMO LTF's (HT-LTF, VHT-LTF, HE-LTF). For devices which support HE/VHT/HE
modes,
the MIMO fields are typically present for longer transmissions, and they
consume airtime
and can decrease the efficiency for short transmissions.
[0099] In some instances, for the motion detection system to measure the
channel
response, a client/leaf device needs to transmit a wireless message (e.g., a
message
28
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
addressed to an access point or another device in the Wi-Fl network). The IEEE
802.11
MAC layer standard contains a defined mechanism that states: if a device
receives a data
message, the device acknowledges that it was received correctly. This
mechanism may
provide a form of "sounding"/"illumination", as it allows for a 0 payload
length MAC frame
(a Null Data Frame) to be sent to any Wi-Fi enabled device, knowing that it
will return with
an ACK message. In some systems, a limitation of the Null-Data/ACK mechanism
is that the
standard defines that the ACK must be transmitted using "legacy" mode, as
switching to the
MIMO mode for a short transmission is not efficient. In such systems, the
wireless
messages sent according to IEEE 802.11 standards do not provide a MIMO
estimation
unless the client/leaf device generates a large enough transmission to cause
the radio to
make use of the MIMO transmission mode.
[00100] Although some systems can use the Legacy training fields for motion
detection,
other systems may not support capturing the Legacy estimation due to hardware
or other
constraints, and hence only provide the ability to extract the MIMO
estimations. Therefore,
some systems are limited, in the sense that a higher layer in the OSI model
may be required
to elicit a MIMO channel estimation, for example, when there is no
standardized
mechanism in the MAC/PHY layers and the client/leaf does not necessarily
support non-
standard components. In some instances, utilizing a higher layer in the OSI
model may
reduce efficiency, for example, if larger data transmission overhead is
required to generate
a channel estimation.
[00101] A motion detection algorithm may also benefit from a MIMO estimation
(e.g.,
relative to a Legacy estimation), as multiple antenna on both transmit and
receive side
introduce an element of spatial diversity, each illuminating or sensing a
slightly different
view or perspective of the environment due to the antenna's physical
separation. To obtain
these and other benefits offered by having a MIMO estimation, a mechanism
using standard
components within higher layers in the OSI model may be utilized to elicit a
MIMO channel
estimation in some cases.
[00102] In some aspects, the systems and techniques described here provide
solutions
for using a higher layer in the OSI model to elicit a MIMO channel estimation,
for example,
using components in the MAC/PHY layer specifications to elicit a client/leaf
node to
29
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
generate a message containing a MIMO training field. The solutions may exploit
the fact
that the higher layers encapsulate their messages into the payload of MAC/PHY
"Data-
Frames", which can be transmitted containing the MIMO fields. Hence by
eliciting a
client/leaf node using existing standard components or protocols within the
Network/Transport layers, a MIMO training field can be obtained from that
device.
[00103] FIG. 8 is a diagram showing example frame formats for three layers of
a typical
OS! model. In particular, the diagram in FIG. 8 shows frame formats for TCP
messages
generated by a transport layer, IPv4 messages generated by a network layer,
and 802.11
messages generated by a MAC layer. As represented in FIG. 8, the OS! Model
works on the
concept of "encapsulation" for transmission of messages, in which data
provided from the
layer above is "encapsulated" into the payload field of the message. For
reception, the
opposite occurs. In the example of FIG. 8, data provided in the Network layer
is included in
the payload field of the message in the MAC layer, and the data provided in
the Transport
layer is included in the payload field of the message in the Network layer.
[00104] In some cases, a wireless communication device can use one or more
layers
above the MAC layer (e.g., transport layer, network layer, or another layer
above the data
link layer) to elicit a MIMO transmission from another wireless communication
device. For
example, an access point (AP) in a wireless network (e.g., a mesh node or
another type of
AP) may generate and send a network layer message or a transport layer message
that
causes a client device to send a response using MIMO transmission. The
following
discussion and the processes shown in FIGS. 9, 10, 11A, 11B, 11C, 12A, 12B,
and 13 provide
examples of systems and techniques that may be used to initiate or otherwise
elicit client
data transmission (e.g. MIMO transmission) for motion detection; other systems
and
techniques may be used in some instances.
[00105] In some examples, software-implemented processes can utilize
components (in
some cases, existing components) in layers above the MAC layer to cause a
client/leaf
device transmit data. Such process may be used to enable motion detection
functionality
using the MIMO fields without the need to add or modify or add any software on
the
client/leaf device.
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
[00106] In some implementations, an address discovery process is used to
obtain an
address for communication with layers above the MAC layer. For example,
channel
estimation may be defined at the MAC/PHY layers, and the identification of a
client/leaf
device may be given by its MAC address (e.g., a 48-bit MAC address). In some
instances, for
higher layer transmission to a device, knowledge of the device's upper layer
logical address
(e.g., IP address) may be needed, and an address discovery process can be used
to obtain
the device's upper layer logical address (e.g., IP address) from its lower
layer physical
address (e.g., MAC address). At least in some contexts, the operation of
obtaining the
device's upper layer logical address (e.g., IP address) from its lower layer
physical address
(e.g., MAC address) requires a different (often more difficult) process than
common
procedures that obtain the lower layer physical address (e.g., MAC address)
given an upper
layer logical address (e.g., IP address).
[00107] FIG. 9 is a flow chart representing an example process 900 that finds
an upper
layer logical address (e.g., an IPv4 address or IPv6 address) from a lower
layer physical
address (e.g., a MAC address). The process 900 may include additional or
different
operations, and the operations shown in FIG. 9 may be performed in the order
shown or in
another order. In some cases, one or more of the operations shown in FIG. 9
are
implemented as processes that include multiple operations, sub-processes for
other types
of routines. In some cases, operations can be combined, performed in another
order,
performed in parallel, iterated or otherwise repeated or performed in another
manner. The
process 900 may be performed by the example wireless communication devices
102A,
102B, 102C shown in FIG. 1, by the example wireless communication devices
204A, 204B,
204C shown in FIGS. 2A and 2B, by any of the example devices (e.g., client
devices 232 or
AP devices 226, 228) shown in FIG. 2C, or by another type of device.
[00108] In some instances, the upper layer logical address that is obtained
from process
900 may be encapsulated in a payload field of a lower layer message. For
example, in
implementations where the process 900 is used to obtain a network address, the
network
address may be encapsulated in the payload field of a MAC layer message (e.g.,
as seen in
FIG. 8). As another example, in implementations where the process 900 is used
to obtain a
transport layer address, the transport layer address may be encapsulated in
the payload
31
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
field of a network layer message (e.g., as seen in FIG. 8). In some instances,
a wireless
communication device can create a cache of address mappings. The cache is
stored on the
wireless communication device and shows the mapping between the lower layer
physical
address (e.g., MAC address) and the upper layer logical address (e.g., network
address).
Either the IPv4 protocol or the IPv6 protocols may operate at the network
layer, and the
process 900 queries the cache (which may contain an IPv4 neighbor table or an
IPv6
neighbor table depending on which protocol operates at the network layer) to
determine
the network address from the lower layer physical address (e.g., the MAC
address).
[00109] At 902, the cache is queried to determine if it contains an IPv4
neighbor table. In
some implementations, the IPv4 neighbor table may also be referred to as the
IPv4 Address
Resolution Protocol (ARP) table. At 904, the process 900 determines whether
the IPv4
neighbor table is stored in the cache. At 906, in response to a determination
that the IPv4
neighbor table is stored in the cache, the network address (e.g., the IPv4
address) is
obtained from the cache and the internet protocol (IP) variables for the IPv4
address are
setup and initialized. As an example, the fields for the network layer packet
shown in FIG. 8
are setup and initialized at 906.
[00110] At 908, in response to a determination that the IPv4 neighbor table is
not stored
in the cache, the cache is once again queried to determine if it contains an
IPv6 neighbor
table. At 910, the process 900 determines whether the IPv6 neighbor table is
stored in the
cache. At 912, in response to a determination that the IPv6 neighbor table is
stored in the
cache, the network address (e.g., the IPv6 address) is obtained from the cache
and the IP
variables for the IPv6 address are setup and initialized.
[00111] At 914, in response to a determination that the IPv6 neighbor table is
not stored
in the cache, the network is scanned. As an example, at 914, the process 900
iterates
through the IPv4 and IPv6 link-local addresses to determine if one or more of
the IPv4 and
IPv6 link-local addresses elicits a response. At 916, the process 900
determines whether an
error has occurred. In some instances, an error occurs when the scanning
performed at 914
does not elicit any response. At 918, in response to a determination that an
error has
occurred, a delay for a predetermined time (e.g., in a range from about 5
seconds to about
15 seconds) occurs before the process 900 is iterated from 902. In the example
shown in
32
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
FIG. 9, 10 seconds is depicted as the delay, but another delay may be used in
other
examples. At 920, in response to a determination that an error has not
occurred (e.g., the
scanning performed at 914 elicits a response), the cache is updated at 920 to
reflect the
mapping between the lower layer physical address (e.g., MAC address) and the
IPv4 or IPv6
link-local address that provided the response. From 920, the process 900 is
iterated from
902.
[00112] One example technique that can be used to elicit a MIMO transmission
from a
wireless communication device is commonly referred to as an "ICMP Ping". In
some cases,
an ICMP Ping process is defined in the network layer, and off-the-shelf
applications exist to
generate such messages (e.g., ping, ping6, fping). The ICMP Ping process may
be explicitly
defined to provide a response given a request, and may be used for network
connectivity
troubleshooting or other purposes. The ICMP Ping process may be natively built
into the
network stack, and may provide a mechanism for causing a client/leaf device
produce a
data transmission in certain instances. The ICMP Ping may utilize an IPv4,
IPv6, or another
similar network layer protocol. However, some devices (for security, privacy,
or other
reasons) disable ICMP. With ICMP disabled, a device which has received a ping
message
may not generate a response, and hence may not elicit a wireless transmission
that can
produce a channel response measurement. In some cases, existing ICMP Ping and
related
processes can be modified to provide advantages for wireless motion detection
systems.
For example, the ICMP Ping processes shown in FIGS. 11A, 11B, and 11C are
tailored for
sending periodic requests, may provide a feedback mechanism to ensure received
responses, and may provide better data efficiency (e.g., by eliminating
padding and
unnecessary data inserted by off-the-shelf applications). Another type of ICMP
Ping process
may be used.
[00113] Another example technique that can be used to elicit a MIMO
transmission from
a wireless communication device is referred to here as "ARP Ping", which in
some
implementations may utilize aspects of the standardized ARP Exchange
mechanism.
Address Resolution Protocol (ARP) is a protocol typically defined in the
network layer; off-
the-shelf applications for generating repeated standardized ARP Exchanges
exist (e.g.,
arping). In many network contexts, communication is not possible without ARP,
and APR is
33
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
considered mandatory for every device. For example, ARP may be required for
all IP
networked devices. Devices may use ARP to obtain the data-link layer address
of another
device (which may be required for communication). The standardized ARP
Exchange
process is typically used to find the MAC address of the device that holds a
given network
layer (IP) address. In some systems, there are four addresses utilized: (1)
the sender
Network-Layer address, (2) the sender MAC-Layer address, (3) the target
Network-Layer
address, (4) the target MAC-Layer address. Both sender addresses (1 and 2) are
known to
the requester because they are the local addresses of the device making the
request. The
standardized ARP Exchange may be used when the target Network-Layer address
(3) is
known, but the target MAC-Layer address (4) is not known. The standardized ARP
Exchange sends a broadcast MAC frame (Destination MAC Address =
ff:ff:ff:ff:ff:ff), which
means every device on the network receives the message. However, only the
device that
holds the given Target network layer (IP) Address can respond, and from that
response, the
Source MAC Address can be extracted. This exchange can create a request /
response that
is encapsulated into a MAC/PHY MIMO data transmission from the responding
device in
some instances. however, in other instances the standardized ARP Exchange does
not elicit
a MIMO transmission from the responding device. For example, some modern
wireless
communication devices may respond to the standardized ARP Exchange request
using a
legacy MAC/PHY data transmission, or can be cached and not actually
transmitted.
[00114] As noted, a standardized ARP request is a broadcast layer-2
transmission
(identified with the destination MAC address field set to if:if:if:if:if:ft),
which generally
requires all devices belonging to the same logical network to receive the
message. This
means all layer-2 network devices (such as switches, bridges, wireless access
points) are
required to transmit the ARP request to all clients and can result in flooding
the entire
network with the single request. For the purpose of eliciting a single device
to transmit a
response for the purpose of motion sensing, flooding an entire network is not
desirable and
may introduce negative effects (e.g., power consumption, air-efficiency, or
wired network
resources). These negative effects may impact the network globally, whether or
not specific
clients are participating in the motion detection system. In some cases, the
ARP Ping
processes described here can be implemented in a manner that is more efficient
and avoids
34
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
the negative effects mentioned above. For example, the ARP Ping process shown
in FIG. 13
may send an ARP request with a known destination MAC address (and without a
broadcast
MAC) to eliminate the broadcast nature of the request. For example, the ARP
request may
be addressed to the device from which MIMO transmissions are sought. Another
type of
ARP Ping process may be used.
[00115] Another example technique that can be used to elicit a MIMO
transmission from
a wireless communication device is referred to here as "TCP Ping", which in
some
implementations may utilize aspects of the standardized TCP Handshake
mechanism. In
some cases, a TCP Ping can be used for sounding wireless communication devices
to obtain
wireless signals that can be used by a motion detection system. The TCP Ping
process can
be used to elicit MIMO transmissions from client/leaf devices in a variety of
contexts,
including scenarios where the client/leaf device is configured to not respond
to ICMP
requests (e.g., devices that do not have 1CMP enabled), and scenarios where
ARP responses
from the client/leaf device result in a Legacy Wi-Fi transmission or a cached
response. The
Transmission Control Protocol (TCP) is typically defined in the transport
layer; TCP
generally operates as a connection-oriented protocol, meaning that data
exchanges
generally occur in both directions, which can be leveraged for eliciting MIMO
transmissions
from a device. Example TCP Ping processes are shown in FIGS. 12A, 12B. Another
type of
TCP Ping process may be used.
[00116] In some contexts, a typical execution of the standardized TCP
Handshake starts
by a client "requesting" to start a connection with a host. To start this
transaction, the client
populates the SRC and DST port fields, and sets the SYN flag. A host can do
one of three
actions: (1) It can accept the request, by responding with the ACK flag set;
(2) It can reject
the request, by responding with the RST flag set; or (3) It can do nothing and
just drop the
frame. The response from action (1) is received if there is an application
listening to the
given port on the host, and the connection has been accepted. The response
from action (2)
is typically received if either there is no application on the host listening
to the given port,
or potentially the port is blocked. And action (3) generally occurs if there
is a firewall which
has explicit instructions to drop any transmissions received by the specific
host/port.
Technically, a result of either action (1) or action (2) may create the ping
request/response
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
action that can produce a MIMO transmission. However, in some instances,
action (1) is
less desirable response because an additional message exchange is then
required by the
client to properly close the connection (and hence consume more air-time and
reduce
efficiency).
[00117] In some implementations, the TCP Ping process shown in FIGS. 12A, 12B
performs a "port-scan" that identifies a set of ports which responds with a
result of action
(23. The "port-scan" may be executed, for example, in the same manner as the
initial step in
the standardized TCP Handshake, or in another manner. After a list of ideal
ports have been
obtained, one or more of them can be targeted for the TCP Ping process. In
some
implementations, during the scan phase, a delay may be added between requests
(with no
delay, requests may eventually be dropped); the scan phase of destination
ports does not
need to be linear (ports 1 to 65535) (e.g., a 16-bit maximum length PR
sequence may be
used to pick the destination ports); and the TCP Source Port may be randomized
(e.g., a 16-
bit maximum length PR sequence may be used for this). In some cases, scanning
for and
looping through 16 ports which respond to a SYN with an RST may be sufficient.
This may
be true in cases where the Source Port is randomized in a manner that is
difficult to detect.
It is also possible to periodically scan for a new set of 16 ports, however
this may not be
needed in all cases, for example, when pinging at a period of 100 ms.
[00118] FIG. 10 is a state machine diagram representing an example process
1000 that
elicits MIMO transmissions from wireless communication devices. The process
1000 may
include additional or different operations, and the operations shown in FIG.
10 may be
performed in the order shown or in another order. For example, in the example
of FIG. 10,
an ICMP Ping process is followed by a TCP Ping process, which in turn is
followed by an
ARP Ping process. However, in other implementations, any sequence or order of
Ping
processes may be used. In some cases, one or more of the operations shown in
FIG. 10 are
implemented as processes that include multiple operations, sub-processes for
other types
of routines. In some cases, operations can be combined, performed in another
order,
performed in parallel, iterated or otherwise repeated or performed in another
manner. The
process 1000 may be performed by the example wireless communication devices
102A,
102B, 102C shown in FIG. 1, by the example wireless communication devices
204A, 204B,
36
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
204C shown in FIGS. 2A and 2B, by any of the example devices (e.g., client
devices 232 and
AP devices 226, 228) shown in FIG. 2C, or by another type of device.
[00119] Implementations of the example process 1000 shown in FIG. 10 may
utilize ICMP
Ping processes, TCP Ping processes, IPv4 ARP Ping processes, IPv6 neighbor
discovery
protocol, or a combination of multiple types of ping processes. The process
1000 may be
modified to utilize additional or different types of ping processes.
[00120] The example process 1000 shown in FIG. 10 combines multiple different
ping
mechanisms into a single protocol that can be controlled by a state machine.
In some cases,
by having each mechanism provide feedback to the state machine, as represented
in FIG.
10, the process 1000 may select the best ping mechanism available to produce
channel
information to be used for motion detection. In some cases, feedback within
each sub-
process is used to help the state machine determine which mechanism is the
best to use
and may ensure that a reliable mechanism is selected. In the example shown in
FIG. 10,
each of the three ping mechanisms provides feedback to the motion detection
system, so
that the motion detection system can select one of the mechanisms based on the
feedback
(e.g., the mechanism that provides the best data for motion detection may be
selected), and
the motion detection system may select a different mechanism for each
client/leaf node
used by the motion detection system.
[00121] At 1002, a network layer address of a device is determined. For
example, the
process 900 shown in FIG. 9 or another type of process may be used to obtain
an IP address
of a device.
[00122] At 1010, 1012 and 1014, an ICMP Ping process is performed. As shown in
FIG.
10, the ICMP Ping process includes a Setup ICMP Ping operation at 1010, an
ICMP Ping
operation at 1012 and a Stop ICMP Ping operation at 1014. The ICMP Ping
process may
include additional or different operations. In some instances, the ICMP Ping
process elicits
a MIMO transmission from the device (e.g., the device corresponding to the IP
address
found at 1002). In some cases, the ICMP Ping process does not elicit a MIMO
transmission
from the device, and the process 1000 proceeds to the TCP Ping process. In
some
implementations, two types of feedback may be used to make this decision of
whether to
37
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
proceed to the TCP Ping process: (1) the response received delay, and (2) the
channel state
information (CSI) generation rate. Either or both of these criteria can be
used to evaluate
the ICMP Ping process, and optionally switch to the TCP Ping process if
results are not
sufficient.
[00123] At 1020, 1022 and 1024, a TCP Ping process is performed. As shown in
FIG. 10,
the TCP Ping process includes a Setup TCP Ping operation at 1020, a TCP Ping
operation at
1022 and a Stop TCP Ping operation at 1024. The TCP Ping process may include
additional
or different operations. In some instances, the TCP Ping process elicits a
MIMO
transmission from the device (e.g., the device corresponding to the IP address
found at
1002). In some cases, the TCP Ping process does not elicit a MIMO transmission
from the
device, and the process 1000 proceeds to the ARP Ping process. In some
implementations,
two types of feedback may be used to make this decision of whether to proceed
to the ARP
Ping process: (1) the response received delay, and (2) the channel state
information (CSI)
generation rate. Either or both of these criteria can be used to evaluate the
TCP Ping
process, and optionally switch to the ARP Ping process if results are not
sufficient.
[00124] At 1030, 1032 and 1034, an ARP Ping process is performed. As shown in
FIG. 10,
in instances where the IP address is an IPv4 address, the ARP Ping process
includes a Setup
IPv4 ARP Ping operation at 1030, an IPv4 ARP Ping operation at 1032 and a Stop
IPv4 ARP
Ping operation at 1034. In instances where the IP address is an IPv6 address,
the ARP Ping
process includes a Setup IPv6 neighbor discovery protocol operation at 1030,
an IPv6
neighbor discovery protocol operation at 1032 and a Stop IPv6 neighbor
discovery
protocol operation at 1034. The ARP Ping process may include additional or
different
operations. In some instances, the ARP Ping process elicits a MIMO
transmission from the
device (i.e., the device corresponding to the IP address found at 1002). In
some cases, the
ARP Ping process does not elicit a MIMO transmission from the device, and the
process
1000 proceeds to 1040. In some implementations, two types of feedback may be
used to
make this decision of whether to proceed to operation 1040: (1) the response
received
delay, and (2) the channel state information (CSI) generation rate. Either or
both of these
criteria can be used to evaluate the ARP Ping process, and optionally
reiterate to another
38
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
mechanism if results are not sufficient At 1040, a neighbor cache is flushed,
and the
process 1000 proceeds to another iteration beginning at 1002.
[00125] FIG. 11A shows a flowchart representing an example process 1100 to
setup an
ICMP ping. FIG. 11B shows a flowchart of an example process 1110 to stop an
ICMP ping.
FIG. 11C shows a flowchart representing an example process 1120 to conduct an
ICMP
ping. The respective processes 1100, 1110, 1120 may include additional or
different
operations, and the operations shown in FIGS. 11A, 11B, and 11C may be
performed in the
order shown or in another order. In some cases, one or more of the operations
shown in
FIGS. 11A, 11B, and 11C are implemented as processes that include multiple
operations,
sub-processes for other types of routines. In some cases, operations can be
combined,
performed in another order, performed in parallel, iterated or otherwise
repeated or
performed in another manner. The processes 1100, 1110, 1120 may be performed
by the
example wireless communication devices 102A, 102B, 102C shown in FIG. 1, by
the
example wireless communication devices 204A, 204B, 204C shown in FIGS. 2A and
2B, by
any of the example devices (e.g., client devices 232 and AP devices 226, 228)
shown in FIG.
2C, or by another type of device.
[00126] The example processes 1100, 1110, 1120 shown in FIGS. 11A, 1113, and
11C may
be used, for example, to perform operations 1010, 1014, 1012, respectively in
the example
process 1000 shown in FIG. 10. In some implementations, the example processes
1100,
1110, 1120 shown in FIGS. 11A, 11B, and 11C may be used in another context. In
some
implementations, for applications with wireless motion detection systems, the
ICMP Ping
processes represented in FIGS. 11A, 11B, and 11C can provide advantages, for
example, as
noted above.
[00127] The example process 1100 in FIG. 11A illustrates initialization logic
for an ICMP
ping process. In some implementations, the process 1100 initializes computing
resources
and message fields that are needed for the ICMP ping process 1110. The example
process
1100 includes determining whether a timer has been set up successfully (at
1101). In some
implementations, setting up the timer includes initiating an operating system
(0S)-level
call requesting the OS to set up a timer handle. In some instances, there may
not be
computing resources to set up the timer handle, and the OS may return an error
message
39
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
indicating the absence of such resources, thus indicating that the timer has
not been set up
successfully. Conversely, when there are sufficient computing resources to set
up the timer
handle, the OS may return a message indicating successful set up of the timer
handle.
[00128] In response to a determination that the timer has not been
successfully setup,
the ICMP Ping mechanism may be terminated (e.g., by performing the process
1110 shown
in FIG. 11B). Conversely, in response to a determination that the timer has
been set up
successfully, a determination is made at 1103) as to whether a socket has been
opened
successfully. In some implementations, setting up the socket includes
initiating an OS-level
call requesting the OS to set up a socket handle. In some instances, there may
not be
computing resources to set up the socket handle, and the OS may return an
error message
indicating the absence of such resources, thus indicating that the socket has
not been set up
successfully. Conversely, when there are sufficient computing resources to set
up the
socket handle, the OS may return a message indicating successful set up of the
socket
handle.
[00129] In response to a determination that the socket has not been opened
successfully,
the ICMP Ping mechanism may be terminated (e.g., by performing the process
1110 shown
in FIG. 1113). Conversely, in response to a determination that the socket has
been opened
successfully, the process 1100 proceeds to initialize a raw ICMP echo request
frame (e.g., at
1105). At 1105, fields that are required for the ICMP ping messages are
initialized and
placed in the payload of the IPv4 or IPv6 frame.
[00130] At 1107, a sequence counter is initialized to zero. The sequence
counter tracks
the number of ICMP ping messages that are sent, and each ICMP ping message is
matched
to a respective sequence number (e.g., described in the example of FIG. 11C).
At 1109, CSI
rate feedback is initialized. In some implementations, the device from which
MIMO
transmissions are elicited can provide CS1 to the device transmitting the 1CMP
ping
messages. By initializing CSI rate feedback at 1109, CST can he obtained from
the MIMO
transmissions that are elicited by the ICMP ping messages, and the rate at
which the CSI is
being received can be determined to ascertain whether CSI is being received at
a rate that
is fast enough to accurately or reliably detect motion in the space 200, 201.
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
[00131] The example process 1110 in FIG. 11B illustrates termination logic for
an ICMP
ping process. In some implementations, the process 1110 releases the computing
resources
that were requested in the initialization process 1100. At 1111, the timer
(e.g., requested
at 1101) is disabled and at 1113, the socket (e.g., requested at 1103) is
closed. In some
implementations, the timer is disabled and the socket is closed by an OS-level
call that
indicates, to the OS, that these resources are no longer needed.
[00132] The example process 1120 in FIG. 11C illustrates a process of
conducting the
ICMP ping. In some implementations, the ICMP ping includes sending a
predetermined
number of consecutive ICMP ping messages (e.g., using the operations at 1121,
1123, 1125,
1127, 1129, 1131). In some instances, the predetermined number of consecutive
ICMP ping
messages may be referred to as a block of ICMP ping messages. The number of
consecutive
ICMP ping messages within the block (referred to as "BLOCKSIZE") can be an
application-
specific tuned parameter, for example 64 ICMP ping messages. The "BLOCKSIZE"
can also
be set based on the period at which the space 200, 201 is sampled for motion.
In some
implementations, the space 200, 201 is sampled every 100 milliseconds, and a
reasonable
"BLOCKSIZE" is equal to 64 ICMP ping messages. After a block of ICMP ping
messages has
been sent, the process 1120 analyzes the received responses (e.g., using the
operations at
1133, 1135, 1137, 1139) to determine whether MIMO transmissions have been
successfully elicited by the block of ICMP ping messages or whether a further
block of ICMP
ping messages needs to be transmitted.
[00133] At 1121, an ICMP ping message is updated. In some instances, an ICMP
ping
message may be referred to as an echo request frame, and updating the ICMP
ping message
may include updating fields (e.g., the checksum field) of the ICMP ping
message. At 1123, a
timer tick is awaited. The timer tick allows for a predetermined period of
time (e.g., about
100 milliseconds) to elapse so that a wireless signal (e.g., a MIMO
transmission) can be
received in response to a previously transmitted ICMP ping message. In some
instances,
the predetermined period of time may be equal to the period at which the space
200, 201 is
sampled for motion. After the timer tick occurs, at 1125, the timestamp of the
ICMP ping
message that was updated at 1121 is determined. In some instances, the
timestamp of the
ICMP ping message is matched to the current sequence number. At 1127, the ICMP
ping
41
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
message that was updated at 1121 is sent. In some implementations, the ICMP
ping
message may be referred to as an ICMP echo request.
[00134] At 1129, a determination is made as to whether the predetermined
number of
consecutive ICMP ping messages (e.g., "BLOCKSIZE") has been sent. In response
to a
determination that the predetermined number of consecutive ICMP ping messages
has not
been sent, the sequence counter is incremented (at 1131) and process 1120 is
iterated
from 1121.1n response to a determination that the predetermined number of
consecutive
ICMP ping messages has been sent, a feedback or check mechanism is executed.
[00135] In the example process 1120, the feedback or check mechanism (e.g.,
including
operations 1133, 1135, 1137, 1139) is executed after the block of ICMP ping
messages has
been sent. At 1133, the timestamps of the received responses are processed to
determine a
difference between the time a respective ICMP ping message was transmitted
(e.g.,
obtained from the timestamp associated with the ICMP ping message) and the
time its
corresponding response was received. If the time difference associated with
any ICMP ping
message within the block of ICMP ping messages is greater than a threshold,
then the entire
block of ICMP ping messages is deemed to be a failed block. This failure logic
may be
implemented inside operation 1133 that processes timestamps of received
responses.
[00136] At 1135, a determination is made as to whether the number of
consecutive failed
blocks is greater than a threshold number of failures. In the example shown in
FIG. 11C, the
threshold number of failures is depicted as being 10, but another integer
threshold number
may be used in other examples. A determination that the number of consecutive
failed
blocks is greater than the threshold number of failures may indicate that
repeated blocks of
ICMP ping messages have failed to elicit successful MIMO transmissions from a
wireless
communication device. Therefore, in response to a determination that the
number of
consecutive failed blocks is greater than the threshold number of failures,
the ICMP Ping
mechanism maybe terminated in favor of attempting another type of mechanism.
[00137] In response to a determination that the number of consecutive failed
blocks is
not greater than the threshold number of failures, a secondary feedback check
is
performed. The secondary feedback check is referred to in FIG. 11C as CSI rate
feedback
42
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
(CSI Rate FB) (e.g., in operations 1137 and 1139). The checks performed at
1137 and 1139
determine the rate at which MIMO transmissions (including CSI) are being
received in
response to the block of ICMP ping messages. If the ICMP Ping response is
encapsulated by
the client/leaf device in a MAC data frame that does not contain a MIMO
training field, the
response times may pass the check at 1135, but without a MIMO training field,
there may
be no CS1 output from the radio. Accordingly, the secondary check at 1137 and
1139 may
be used to ensure the block of ICMP ping messages elicits responses containing
a MIMO
training field.
[00138] At 1137, a determination is made as to whether CSI rate feedback is
enabled, and
if so, a determination is made (at 1139) as to whether the average CSI rate is
greater than
or equal to twice the period at which the space 200, 201 is sampled for
motion. A
determination that the average CSI rate is greater than or equal to twice the
period at
which the space 200, 201 is sampled may indicate that MIMO transmissions
(including CSI)
are not being received at a rate that is fast enough to accurately or reliably
detect motion in
the space 200, 201. Consequently, in response to a determination that the
average CSI rate
is greater than or equal to twice the period at which the space 200, 201 is
sampled, the
ICMP Ping mechanism may be terminated in favor of attempting another type of
mechanism. Conversely, if CSI rate feedback is not enabled or if the average
CSI rate is less
than twice the period at which the space 200, 201, the sequence counter is
incremented (at
1131) and process 1120 is iterated from 1121.
[00139] FIG. 12A shows a flow chart representing an example process 1200 to
setup a
TCP Ping. FIG. 12B shows a flow chart representing an example process 1210 to
conduct a
TCP Ping. The respective processes 1200, 1210 may include additional or
different
operations, and the operations shown in FIGS. 12A and 12B may be performed in
the order
shown or in another order. In some cases, one or more of the operations shown
in FIGS.
12A and 12B are implemented as processes that include multiple operations, sub-
processes for other types of routines. In some cases, operations can be
combined,
performed in another order, performed in parallel, iterated or otherwise
repeated or
performed in another manner. The processes 1200 and 1210 may be performed by
the
example wireless communication devices 102A, 102B, 102C shown in FIG. 1, by
the
43
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
example wireless communication devices 204A, 204B, 204C shown in FIGS. 2A and
2B, by
any of the example devices (e.g., client devices 232 and AP devices 226, 228)
shown in FIG.
2C, or by another type of device.
[00140] The example processes 1200, 1210 shown in FIGS. 12A, 12B may be used,
for
example, to perform operations 1020, 1022 in the example process 1000 shown in
FIG. 10.
In some implementations, the example processes 1200, 1210 shown in FIGS. 12A,
12B may
be used in another context.
[00141] The example processes 1200 determines the number of valid TCP ports in
the
network, obtains a valid local interface IP address, and initializes computing
resources and
message fields that are needed for the TCP ping process 1210. The example
process 1200
includes scanning the network for TCP ports (at 1201). In some
implementations, the
network is scanned for TCP ports by sending a TCP packet with a set
synchronize (SYN)
flag to each port identifier. For example, FIG. 8 shows a TCP packet having
various fields,
including a field for various flags. The SYN flag depicted in the example of
FIG. 8 may be set
in the TCP packet that is sent to each port identifier. In some instances, a
port identifier is a
16-bit identifier, and the TCP packet with the set SYN flag is sent to each
unique 16-bit
identifier. A valid TCP port may respond to the TCP packet having the set SYN
flag with a
TCP packet having a set reset (RST) flag. For example, the RST flag depicted
in the example
of FIG. 8 may be set in the TCP packet that is sent as a response. At 1203, a
determination is
made as to whether there is more than one valid TCP port. In some
implementations, the
number of valid TCP ports is determined by counting the number of received TCP
packets
having a set RST flag.
[00142] In response to a determination that there is less than or equal to one
valid TCP
port, the TCP ping setup is terminated (e.g., in favor of attempting another
type of
mechanism). Conversely, in response to a determination that there is more than
one valid
TCP port, a determination is made (at 120S) as to whether a timer has been set
up
successfully. In some implementations, an OS-level call similar to the OS-
level call
described for operation 1101 may be used to determine whether the timer has
been set up
successfully.
44
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
[00143] In response to a determination that the timer has not been set up
successfully,
the TCP ping setup is terminated (e.g., in favor of attempting another type of
mechanism).
Conversely, in response to a determination that the timer has been set up
successfully, a
determination is made (at 1207) as to whether a socket has been opened
successfully. An
OS-level call similar to the OS-level call described for operation 1103 may be
used to
determine whether the socket has been set up successfully.
[00144] In response to a determination that the socket has not been opened
successfully,
the TCP ping setup is terminated (e.g., in favor of attempting another type of
mechanism).
However, in response to a determination that the socket has been opened
successfully, a
local interface IP address is requested (at 1209). In some implementations,
requesting a
local interface IP address includes initiating an OS-level call requesting a
local interface IP
address from the OS. At 1211, a determination is made as to whether a valid
local interface
IP address has been obtained. A valid local interface IP address is obtained
when there are
sufficient computing resources available for the OS to provide the local
interface IP
address. In some instances, there may not be computing resources to provide a
local
interface IP address, and the OS may return an error message indicating this.
Therefore, a
valid local interface IP address is not obtained when there are insufficient
computing
resources available to provide the local interface IP address.
[00145] In response to a determination that a valid local interface IP address
is not
obtained, the TCP ping setup is terminated (e.g., in favor of attempting
another type of
mechanism). Conversely, in response to a determination that a valid local
interface IP
address has been obtained, variables of a TCP ping message are set up (at
1213). For
example, the various fields of the example TCP packet shown in FIG. 8 are set
up at 1213. In
some instances, a TCP ping message may be referred to as a datagram (indicated
in FIG.
12A as "dgram"), and the acknowledgement variable (indicated in FIG. 12A as
"ack" and
shown in FIG. 8 as the flag "ACK"), the address variables (indicated in FIG.
12A as "addr"
and shown in FIG. 8 as "Source Port" and "Destination Port"), or both, of the
datagram may
be set up at 1213. The combination of variables that are set up may depend, at
least in part
on whether the IPv4 of the IPv6 protocol is used at the network layer.
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
[00146] At 1215, TCP fields and the contents of the datagram are initialized.
For example,
the various fields of the TCP packet shown in FIG. 8 are initialized at 1215.
At 1217, file
descriptors (indicated in FIG. 12A as "FD") for a select function (indicated
in FIG. 12A as
"select()") are set up. In some instances, the select function is configured
to inform the OS
to generate an alert when an event included in the file descriptors has
occurred. In some
implementations, the file descriptors can include the reception of a TCP
packet having a set
RST flag, a timer expiration, or both. Therefore, in such implementations, the
OS generates
an alert when the timer has expired or when a TCP packet having a set RST flag
is received.
In some instances, the timer is set to expire after a predetermined period of
time, which
may be equal to the period at which the space 200, 201 is sampled for motion
(e.g., 100
milliseconds in some instances).
[00147] At 1219, CSI rate feedback is initialized. In some implementations,
the device
from which MIMO transmissions are elicited can provide CSI to the device
transmitting the
ICMP ping messages. By initializing CSI rate feedback at 1219, CSI can be
obtained from the
MIMO transmissions that are elicited by the TCP ping messages, and the rate at
which the
CSI is being received can be determined to ascertain whether CSI is being
received at a rate
that is fast enough to accurately or reliably detect motion in the space 200,
201.
[00148] The example process 1210 in FIG. 1213 illustrates a process of
conducting the
TCP ping. In some implementations, the TCP ping includes sending a
predetermined
number of consecutive TCP ping messages (e.g., using the operations at 1221,
1223, 1225,
1227, 1229, 1231, 1233, 1235, 1237). In some instances, the predetermined
number of
consecutive TCP ping messages may be referred to as a block of datagrams. The
number of
consecutive datagrams within the block (referred to as "BLOCKSIZE") can be an
application-specific tuned parameter, for example 64 datagrams. The
"BLOCKSIZE" can
depend on the period at which the space 200, 201 is sampled for motion. In
some
implementations, the space 200, 201 is sampled every 100 milliseconds, and a
reasonable
"BLOCKSIZE" is equal to 64 datagrams. After a block of datagrams has been
sent, the
process 1210 analyzes the received responses (e.g., using the operations at
1239, 1241,
1243, 1245) to determine whether MIMO transmissions have been successfully
elicited by
the block of datagrams or whether a further block of datagrams needs to be
transmitted.
46
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
[00149] At 1221, the select function is executed. The select function waits
for an event
included in the file descriptors to occur. In some implementations, the file
descriptors can
include the reception of a TCP packet having a set RST flag, expiration of the
timer, or both.
In essence, at 1221, a period of time is allowed to elapse so that a wireless
signal (e.g., a
MIMO transmission) can be received in response to a previously transmitted TCP
ping
message.
[00150] After the alert has been generated by the OS, a determination is made
(at 1223)
as to whether the timer has expired. The determination at 1223 ascertains
whether the
alert at 1221 can be attributed to the expiration of the timer. In response to
a
determination that the timer has not expired, a determination is made (at
1225) as to
whether a TCP packet having a set RST flag was received. The determination at
1225
ascertains whether the alert at 1221 can be attributed to the reception of a
TCP packet
having a set RST flag. In response to a determination that a TCP packet having
a set RST flag
was not received, process 1210 is iterated starting at 1221. Conversely, in
response to a
determination that a TCP packet having a set RST flag was received, the
timestamp of the
received datagram is obtained and the timestamp is used to indicate the time
at which the
datagram is received (at 1227). The process 1210 is subsequently iterated
starting at 1221.
[00151] Conversely, in response to a determination that the timer has expired,
the
datagram is updated (at 1229). In some instances, the port identifiers (e.g.,
16-bit port
identifiers) for a valid source port (indicated in FIG. 12B as "sport" and
shown in FIG. 8 as
"Source Port") and a valid destination port (indicated in FIG. 12B as "dport"
and shown in
FIG. 8 as "Destination Port") are updated at 1229. The port identifiers for
valid source and
destination ports may be obtained, as an example, at 1201 and 1203 when the
network is
scanned for valid TCP ports.
[00152] At 1231, the timestamp of the datagram that was updated at 1229 is
determined.
In some instances, the timestamp of the datagram is matched to the current
sequence
number. At 1233, the datagram that was updated at 1229 is sent (e.g., from the
valid source
port to the valid destination port). In some implementations, the datagram is
sent as a TCP
packet having a set SYN flag.
47
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
[00153] At 1235, a determination is made as to whether the predetermined
number of
consecutive datagrams (e.g., "BLOCKSIZE") has been sent. In response to a
determination
that the predetermined number of consecutive datagrams has not been sent, the
sequence
counter is incremented, a valid source port is pseudo-randomly chosen, and the
next valid
destination port is selected (at 1237), and process 1210 is iterated from
1221. In response
to a determination that the predetermined number of consecutive datagrams has
been
sent, a feedback or check mechanism is executed.
[00154] In the example process 1210, the feedback or check mechanism (e.g.,
including
operations 1239, 1241, 1243, 1245) is executed after the block of datagrams
has been sent.
At 1239, the timestamps of the received responses are processed to determine a
difference
between the time a respective datagram was transmitted (e.g., obtained from
the
timestamp associated with the datagram) and the time its corresponding
response was
received. If the time difference associated with any datagram within the block
of
datagrams is greater than a threshold, then the entire block of datagrams is
deemed to be a
failed block. This failure logic may be implemented inside operation 1239 that
processes
timestamps of received responses.
[00155] At 1241, a determination is made as to whether the number of
consecutive failed
blocks is greater than a threshold number of failures. In the example shown in
FIG. 1213, the
threshold number of failures is depicted as being 10, but another integer
threshold number
may be used in other examples. A determination that the number of consecutive
failed
blocks is greater than the threshold number of failures may indicate that
repeated blocks of
datagrams (or TCP ping messages) have failed to elicit successful MIMO
transmissions from
a wireless communication device. Therefore, in response to a determination
that the
number of consecutive failed blocks is greater than the threshold number of
failures, the
TCP Ping mechanism may be terminated in favor of attempting another type of
mechanism.
[00156] In response to a determination that the numher of consecutive failed
blocks is
not greater than the threshold number of failures, a secondary feedback check
is
performed. The secondary feedback check is referred to in FIG. 12B as CSI rate
feedback
(CSI Rate FB) (e.g., in operations 1243 and 1245). The checks performed at
1243 and 1245
determine the rate at which MIMO transmissions (including CSI) are being
received in
48
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
response to the block of datagrams. If the TCP packet having a set SYN flag is
encapsulated
by the client/leaf device in a MAC data frame that does not contain a MIMO
training field,
the response times may pass the check at 1241, but without a MIMO training
field, there
may be no CSI output from the radio. Accordingly, the secondary check at 1243
and 1245
may be used to ensure the block of datagrams elicits responses containing a
MIMO training
field.
[00157] At 1243, a determination is made as to whether CSI rate feedback is
enabled, and
if so, a determination is made (at 1245) as to whether the average CSI rate is
greater than
or equal to twice the period at which the space 200, 201 is sampled for
motion. A
determination that the average CSI rate is greater than or equal to twice the
period at
which the space 200, 201 is sampled may indicate that MIMO transmissions
(including CSI)
are not being received at a rate that is fast enough to accurately or reliably
detect motion in
the space 200, 201. Consequently, in response to a determination that the
average CSI rate
is greater than or equal to twice the period at which the space 200, 201 is
sampled, the TCP
Ping mechanism may be terminated in favor of attempting another type of
mechanism.
Conversely, if CSI rate feedback is not enabled or if the average CSI rate is
less than twice
the period at which the space 200, 201, the sequence counter is incremented, a
valid source
port is pseudo-randomly chosen, and the next valid destination port is
selected (at 1237),
and process 1210 is iterated from 1221.
[00158] FIG. 13 shows a flow chart representing an example process 1300 to
setup an
ARP ping. The process 1300 may include additional or different operations, and
the
operations shown in FIG. 13 may be performed in the order shown or in another
order. In
some cases, one or more of the operations shown in FIG. 13 are implemented as
processes
that include multiple operations, sub-processes for other types of routines.
In some cases,
operations can be combined, performed in another order, performed in parallel,
iterated or
otherwise repeated or performed in another manner. The process 1400 may be
performed
by the example wireless communication devices 102A, 102B, 102C shown in FIG.
1, by the
example wireless communication devices 204A, 204B, 204C shown in FIGS. 2A and
2B, by
any of the example devices (e.g., client devices 232 and AP devices 226, 228)
shown in FIG.
2C, or by another type of device.
49
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
[00159] The example process 1300 shown in FIG. 13 may be used, for example, to
perform operation 1030 in the example process 1000 shown in FIG. 10. In some
implementations, the example process 1300 shown in FIG. 13 may be used in
another
context. In some implementations, for applications with wireless motion
detection systems,
the ARP Ping processes represented in FIG. 13 can provide advantages, for
example,
compared to using standard tools (e.g., arping). For instance, the ARP Ping
process
represented in FIG. 13 may provide an ARP request without a broadcast MAC, but
instead
with the desired destination MAC address (which is already known), which can
eliminate
the broadcast nature of the ARP request.
[00160] The example process 1300 is used when the IPv4 protocol operates at
the
network layer, and at 1301, a determination is made as to whether the IPv4
protocol is
used. The cache that is queried at 902 in FIG. 9 contains an IPv4 neighbor
table when the
IPv4 protocol is used, and thus the determination made at 1301 can be made
based
whether an IPv4 neighbor table exists in the cache queried at 902. In response
to a
determination that the IPv4 protocol is not used, the ARP Ping setup may be
terminated
(e.g., in favor of attempting another type of mechanism).
[00161] Conversely, in response to a determination that the IPv4 protocol is
used, a
determination is made (at 1303) as to whether a timer has been set up
successfully. In
some implementations, an OS-level call similar to the OS-level call described
for operation
1101 may be used to determine whether the timer has been set up successfully.
[00162] In response to a determination that the timer has not been set up
successfully,
the ARP ping setup is terminated (e.g., in favor of attempting another type of
mechanism).
Conversely, in response to a determination that the timer has been set up
successfully, a
determination is made (at 1305) as to whether a socket has been opened
successfully. An
OS-level call similar to the OS-level call described for operation 1103 may be
used to
determine whether the socket has been set up successfully.
[00163] In response to a determination that the socket has not been opened
successfully,
the ARP ping setup is terminated (e.g., in favor of attempting another type of
mechanism).
However, in response to a determination that the socket has been opened
successfully, a
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
local interface IP address and a MAC address are requested (at 1307). In some
implementations, requesting a local interface IP address and a MAC address
includes
initiating an OS-level call requesting a local interface IP address and a MAC
address from
the OS. At 1309, a determination is made as to whether a valid local interface
IP address
has been obtained. A valid local interface IP address is obtained when there
are sufficient
computing resources available for the OS to provide the local interface IP
address. In some
instances, there may not be computing resources to provide a local interface
IP address,
and the OS may return an error message indicating this. Therefore, a valid
local interface IP
address is not obtained when there are insufficient computing resources
available to
provide the local interface IP address.
[00164] In response to a determination that a valid local interface IP address
is not
obtained, the ARP ping setup is terminated (e.g., in favor of attempting
another type of
mechanism). Conversely, in response to a determination that a valid local
interface IP
address has been obtained, the process 1300 proceeds to initialize a raw ARP
request
frame (e.g., at 1311). At 1311, fields that are required for the ARP ping
messages are
initialized and placed in the payload of the IPv4 frame.
[00165] At 1313, CSI rate feedback is initialized. In some implementations,
the device
from which MIMO transmissions are elicited can provide CSI to the device
transmitting the
ARP ping messages. By initializing CSI rate feedback at 1313, CSI can be
obtained from the
MIMO transmissions that are elicited by the ARP ping messages, and the rate at
which the
CSI is being received can be determined to ascertain whether CSI is being
received at a rate
that is fast enough to accurately or reliably detect motion in the space 200,
201.
[00166] FIG. 14 shows a flowchart representing an example process 1400 of
eliciting
MIMO transmissions from wireless communication devices. The process 1400 may
include
additional or different operations, and the operations shown in FIG. 14 may be
performed
in the order shown or in another order. In some cases, one or more of the
operations
shown in FIG. 14 are implemented as processes that include multiple
operations, sub-
processes for other types of routines. In some cases, operations can be
combined,
performed in another order, performed in parallel, iterated or otherwise
repeated or
performed in another manner. The process 1400 may be performed by the example
51
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
wireless communication devices 102A, 102B, 102C shown in FIG. 1, by the
example
wireless communication devices 204A, 204B, 204C shown in FIGS. 2A and 213, by
any of the
example devices (e.g., client devices 232 and AP devices 226, 228) shown in
FIG. 2C, or by
another type of device.
[00167] The process 1400 may be performed by a wireless communication device
that
seeks to elicit MIMO transmissions from another wireless communication device.
At 1402,
network or transport layer messages are generated. Network layer messages may
be
generated when an ICMP ping process (e.g., described in FIGS. 11A, 11B, 11C)
or an ARP
ping process (e.g., described in FIG. 13) is used to elicit the MIMO
transmissions. As
described in FIG. 8, the network layer messages may be encapsulated into the
payload field
of respective Media Access Control (MAC) layer messages. Transport layer
messages may
be generated when a TCP ping process (e.g., described in FIGS. 12A, 12B) is
used to elicit
the MIMO transmissions. As described in FIG. 8, transport layer messages that
may be
generated may be encapsulated into the payload field of respective network
layer
messages. In some implementations, the network or transport layer messages may
be
addressed to the device from which MIMO transmissions are sought. The address
of the
device from which MIMO transmissions are sought may be an upper layer logical
address
(e.g., network address) of the device and may be obtained using the process
described in
FIG. 10.
[00168] At 1404 the network or transport layer messages are wirelessly
transmitted to
the device from which MIMO transmissions are sought. The network layer
messages may
be wirelessly transmitted according to the ICMP Ping process (e.g., described
in FIGS. 11A,
11B, 11C), the ARP Ping process (e.g., described in FIG. 13), or a combination
thereof. The
transport layer messages may be wirelessly transmitted according to the TCP
Ping process
(e.g., described in FIGS. 12A, 12B).
[00169] In some examples, the device that transmits the network or transport
layer
messages may detect a failure of the network or transport layer messages to
elicit
successful MIMO transmissions from the device to which the network or
transport layer
messages are addressed. For example, the failure of the network or transport
layer
messages to elicit successful MIMO transmissions may manifest itself as the
number of
consecutive failed blocks being greater than a threshold number of failures
(e.g., at 1135 in
52
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
FIG. 11C or at 1241 in FIG. 12B) or the MIMO transmissions (including CSI) are
not being
received at a rate that is fast enough to accurately or reliably detect motion
in the space
(e.g., at 1139 in FIG. 11C or at 1245 in FIG. 12B). When such a failure
occurs, the device that
transmits the network or transport layer messages may terminate the mechanism
used to
transmit the network or transport layer messages in favor of attempting
another type of
mechanism to transmit the network or transport layer messages. For example, as
seen in
FIG. 10, an ICMP ping process that transmits network layer messages may fail
to elicit
successful MIMO transmissions, and the device may instead transmit transport
layer
messages using a TCP ping process to elicit successful MIMO transmissions. As
another
example, a TCP ping process that transmits transport layer messages may fail
to elicit
successful MIMO transmissions, and the device may instead transmit network
layer
messages using an ARP ping process to elicit successful MIMO transmissions.
[00170] At 1406, MIMO transmissions are received from the device to which the
network
or transport layer messages are addressed. The MIMO transmissions can include
MIMO
training fields. The MIMO training fields contain signals (e.g., CSI) having a
higher
frequency resolution, a greater number of subcarrier frequencies, and a higher
frequency
bandwidth compared to Legacy training fields in the PHY frame. Use of the MIMO
training
field for motion detection provides more accurate motion detection
capabilities. Therefore,
at 1408, a training field is identified in each MIMO transmission, and channel
information is
generated based on the training field (at 1410). At 1412, the channel
information is used to
detect motion that occurred in a space (e.g., the space 200, 201).
[00171] FIG. 15 is a block diagram showing an example wireless communication
device
1500. As shown in FIG. 15, the example wireless communication device 1500
includes an
interface 1530, a processor 1510, a memory 1520, and a power unit 1540. A
wireless
communication device (e.g., any of the wireless communication devices 102A,
102B, 102C
in FIG. 1, wireless communication devices 204A, 204B, 204C shown in FIGS. 2A
and 2B,
client devices 232 and AP devices 226, 228 shown in FIG. 2C) may include
additional or
different components, and the wireless communication device 1500 may be
configured to
operate as described with respect to the examples above. In some
implementations, the
interface 1530, processor 1510, memory 1520, and power unit 1540 of a wireless
communication device are housed together in a common housing or other
assembly. In
53
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
some implementations, one or more of the components of a wireless
communication device
can be housed separately, for example, in a separate housing or other
assembly.
[00172] The example interface 1530 can communicate (receive, transmit, or
both)
wireless signals. For example, the interface 1530 may be configured to
communicate radio
frequency (RF) signals formatted according to a wireless communication
standard (e.g., Wi-
Fi, 4G, SG, Bluetooth, etc.). In some implementations, the example interface
1530 includes a
radio subsystem and a baseband subsystem. The radio subsystem may include, for
example, one or more antennas and radio frequency circuitry. The radio
subsystem can be
configured to communicate radio frequency wireless signals on the wireless
communication channels. As an example, the radio subsystem may include a radio
chip, an
RF front end, and one or more antennas. The baseband subsystem may include,
for
example, digital electronics configured to process digital baseband data. In
some cases, the
baseband subsystem may include a digital signal processor (DSP) device or
another type of
processor device. In some cases, the baseband system includes digital
processing logic to
operate the radio subsystem, to communicate wireless network traffic through
the radio
subsystem or to perform other types of processes.
[00173] The example processor 1510 can execute instructions, for example, to
generate
output data based on data inputs. The instructions can include programs,
codes, scripts,
modules, or other types of data stored in memory 1520. Additionally or
alternatively, the
instructions can be encoded as pre-programmed or re-programmable logic
circuits, logic
gates, or other types of hardware or firmware components or modules. The
processor 1510
may be or include a general-purpose microprocessor, as a specialized co-
processor or
another type of data processing apparatus. In some cases, the processor 1510
performs
high level operation of the wireless communication device 1500. For example,
the
processor 1510 may be configured to execute or interpret software, scripts,
programs,
functions, executables, or other instructions stored in the memory 1520. In
some
implementations, the processor 1510 be included in the interface 1530 or
another
component of the wireless communication device 1500.
[00174] The example memory 1520 may include computer-readable storage media,
for
example, a volatile memory device, a non-volatile memory device, or both. The
memory
54
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
1520 may include one or more read-only memory devices, random-access memory
devices,
buffer memory devices, or a combination of these and other types of memory
devices. In
some instances, one or more components of the memory can be integrated or
otherwise
associated with another component of the wireless communication device 1500.
The
memory 1520 may store instructions that are executable by the processor 1510.
For
example, the instructions may include instructions to perform one or more of
the
operations described above.
[00175] The example power unit 1540 provides power to the other components of
the
wireless communication device 1500. For example, the other components may
operate
based on electrical power provided by the power unit 1540 through a voltage
bus or other
connection. In some implementations, the power unit 1540 includes a battery or
a battery
system, for example, a rechargeable battery. In some implementations, the
power unit
1540 includes an adapter (e.g., an AC adapter) that receives an external power
signal (from
an external source) and coverts the external power signal to an internal power
signal
conditioned for a component of the wireless communication device 1500. The
power unit
1540 may include other components or operate in another manner.
[00176] Wireless signals may be communicated (e.g., transmitted and received)
among
the respective wireless communication devices shown in the example wireless
communication systems of FIGS. 1, 2A, 2B, and 2C. For example, data may be
communicated on one or more wireless links of the example wireless
communication
systems of FIGS. 1, 2A, 2B, and 2C. The data that is communicated can be
unicast data,
multicast data, or broadcast data, depending on the wireless communication
devices the
data is addressed or expected to be delivered to. For example, unicast data is
addressed
and intended to have a single destination or recipient. As an illustration, in
the wireless
communication system of FIG. 2C, AP 228A may transmit unicast data addressed
to and
intended for client device 232B. In this example, the other client devices
232A, 232C, 232D,
and 232E are not intended recipients of the unicast data from AP 228A.
Multicast data, by
comparison, is addressed and intended to have one or more destinations or
recipients. As
an illustration, in the wireless communication system of FIG. 2C, AP 228A may
transmit
multicast data addressed to and intended for client devices 232A, 232B, 232C.
In this
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
example, the other client devices 232D, 232E are not intended recipients of
the multicast
data from AP 228A. Broadcast data is intended to be delivered to all devices
within a
broadcast footprint. In an IP network (e.g., an IPv4 or IPv6 protocol), the
broadcast
footprint can be determined by the network portion of the IP address, which
can be defined
by an IP subnet mask. As an illustration, in the wireless communication system
of FIG. 2C,
the client devices 232A, 232B, 232C, 232D, 232E may be within the broadcast
footprint of
the AP 228A, and the AP 228A may transmit broadcast data intended for all the
client
devices 232A, 232B, 232C, 232D, 232E.
[00177] In some instances, the example wireless communication systems of FIGS.
1, 2A,
2B, and 2C may be configured to operate according to one or more of the IEEE
802.11
family of standards. For example, the example wireless communication systems
may
operate as a Wi-Fi network, which can have a built-in power saving feature
that allows a
wireless communication device (e.g., an AP device or a client device) to power
off
transmission and reception components for a negotiated amount of time, without
any loss
of data. Stated differently, a Wi-Fi network can have a built-in power saving
feature that
allows a wireless communication device to enter a sleep mode for a
predetermined
duration (e.g., to reduce or conserve power consumption). For example, the Wi-
Fi network
can have a built-in power saving feature that causes the power unit 1540 shown
in FIG. 15
to cause the wireless communication device 1500 to enter a sleep mode for a
predetermined duration (e.g., to reduce power consumption of the wireless
communication
device 1500). Example wireless communication devices that can use the built-in
power
saving feature of a Wi-Fi network include the example wireless communication
devices
102A, 102B, 102C shown in FIG. 1, the example wireless communication devices
204A,
204B, 204C shown in FIGS. 2A and 2B, or the example devices (e.g., client
devices 232 or AP
devices 226, 228) shown in FIG. 2C, or any other wireless communication
device.
[00178] As described above in the example shown in FIG. 2C, client devices
(e.g., Wi-Fi
client devices) 232A, 232B, 232C, 232D, 232E, 232F, 232G can be associated
with either the
central AP 226 or one of the extension APs 228 using a respective wireless
link 234A, 234B,
234C, 234D, 234E, 234F, 234G. FIG. 16 shows an example exchange of messages in
an
association process 1600 between a client device 1602 and an AP device 1604.
In some
56
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
instances, the client device 1602 can be identified with any of example client
device 102A,
102B, 102C, 204A, 204B, 204C, 232 shown in FIGS. 1, 2A, 2B, and 2C, or any
other client
device. The AP device 1604 can be identified with any example AP device shown
in FIGS. 1,
2A, 213, and 2C, or any other AP device.
[00179] In the association process 1600, the client device 1602 and the AP
device 1604
are co-located in a space 1606, and after the association process 1600, the
devices 1602,
1604 can be nodes in a Wi-Fi network. In some instances, the client device
1602, the AP
device 1604, or both can carry out a search within their respective ranges
(e.g., about 10
meters) to find other wireless communication devices that have registered
themselves as
being visible or discoverable to other wireless communication devices. In some
instances
(e.g., in one or more of the IEEE 802.11 family of standards), the AP device
1604
periodically transmits a beacon signal, which can be used by the client device
1602 to
discover the AP device 1604. Each beacon signal can be a broadcast message
(e.g., for
associated and non-associated client devices). The rate at which the beacon
signals are
transmitted can be programmable by a network operator, and in some instances,
a beacon
signal is transmitted about every 100 ms (e.g., about every 102.4 ms). Each
beacon signal
transmitted by the AP device 1604 can contain information about the wireless
network.
For example, each beacon signal can be used by the AP device 1604 to announce
or
broadcast the presence of the wireless network, identify the wireless network
and its
supported capabilities, synchronize the times on all associated client
devices, and
broadcast a traffic indication map (TIM) element (e.g., discussed in further
detail below).
Each beacon signal can used by the AP device 1604 for other purposes, in some
implementations.
[00180] In some implementations, once the client device 1602 has discovered
the AP
device 1604, the client device 1602 can transmit an association request
message 1608 to
the AP device 1604. In some implementations, the association request message
1608
includes multiple fields 1610 related to the capabilities of the client device
1602. With
regards to the built-in power saving feature in a Wi-Fi network, the multiple
fields 1610 of
the association request message 1608 includes a Listen Interval field 1612,
which the client
device 1602 can use to indicate, to the AP device 1604, the maximum amount of
time the
57
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
client device 1602 may be in sleep mode before retrieving, for example, any
buffered data
(e.g., unicast, broadcast, or multicast data) from the AP device 1604. In some
implementations, the value in the Listen Interval field 1612 can be an integer
value
expressed in 2 octets (e.g., 16 bits). The integer value can indicate the
maximum number of
beacon signals (and hence the maximum amount of time) that the client device
1602 can be
in sleep mode. As an example, a value of 20 in the Listen Interval field 1612
indicates to the
AP device 1604 that the client device 1602 can be in sleep mode for as many as
20 beacon
signals before requesting buffered unicast data to be communicated from the AP
device
1604 to the client device 1602. As another example, a value of 0 in the Listen
Interval field
1612 can indicate to the AP device 1604 that the client device 1602 will not
enter sleep
mode and is available to receive all beacon signals transmitted by the AP
device 1604.
[00181] After receiving the association request message 1608, the AP device
1604 can
determine whether the client device 1602 is permitted to associate with the AP
device
1604. In some instances, the AP device 1604 transmits an association response
message
1614 to the client device 1602 in response to receiving the association
request message
1608. In instances where the client device 1602 is permitted to associate with
the AP
device 1604, the association response message 1614 includes an association
identifier
(AID) field, which is used by the AP device 1604 to assign a unique identifier
to the now
associated client device 1602. The value in the AID field of the association
response
message 1614 is unique for each associated client device and can be an integer
value in the
range of 1 to 2007 (both 1 and 2007 being included in the range). With regards
to the
built-in power saving feature in a Wi-Fi network, the value in the AID field
of the
association response message 1614 can be used as an index into the TIM element
of a
beacon signal that is transmitted from the AP device 1604 to the client device
1602 after
the client device 1602 is associated with the AP device 1604.
[00182] As discussed above, each beacon signal can include a TIM element. FIG.
17
shows an example TIM element 1700. In some instances, the TIM element 1700 can
be
used by the AP device 1604 to identify the presence of buffered unicast,
broadcast, or
multicast data for the client device 1602. For example, the TIM element 1700
can be used
by the AP device 1604 to indicate to each associated client device that the AP
device 1604
58
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
has buffered unicast data for the respective client devices, and a beacon
signal including a
TIM element indicating the presence of buffered unicast data can be referred
to as a TIM
beacon signal. As another example, the TIM element 1700 can be used by the AP
device
1604 to indicate to each associated client device that the AP device 1604 has
buffered
broadcast or multicast data for the respective client devices. A TIM element
1700 that
indicates the presence of buffered broadcast or multicast data at the AP
device 1604 can be
referred to as a delivery traffic indication (DTIM) element, and a beacon
signal including a
DTIM element can be referred to as a DTIM beacon signal.
[00183] The example TIM element 1700 includes multiple fields 1702, 1704,
1706, 1708,
1710, 1712. The TIM element 1700 includes an element identification (ID) field
1702. For a
TIM element, the element ID field 1702 is equal to 5. The length field 1704
indicates the
number of bytes in the TIM element 1700. In some implementations, the DTIM
count field
1706 is a countdown counter value that indicates the count until a DTIM beacon
signal is
scheduled to be sent. The DTIM count field 1706 is decremented with each
successive
beacon signal transmitted by the AP device 1604. If the DTIM count field 1706
is zero, the
beacon signal is a DTIM beacon signal, and broadcast or multicast data may be
scheduled to
be transmitted by the AP device 1604 following (e.g., immediately following)
the DTIM
beacon signal. The DTIM period field 1708 indicates the quantity of beacon
signals to be
transmitted by the AP device 1604 for each DTIM interval of time. In some
instances, the
partial virtual bitmap field 1712 is a variable length bit mask array (having
a maximum of
251 bytes) indicating the presence of buffered data available from the AP
device 1604. For
example, if the AP device 1604 has buffered data for the client device 1602,
the AP device
1604 may indicate the presence of the buffered data by setting to 1 the bit
within the bit
mask corresponding to the client device 1602.1n some implementations, this bit
within the
bit mask may be described as a TIM value. To reduce the size of the partial
virtual bitmap
field 1712, a bitmap control field 1710 can used to indicate which portion of
the full traffic
indication map (251 bytes) is sent via the partial virtual bitmap field 1712.
In some
instances, the bitmap control field 1710 can provide an indication of whether
broadcast or
multicast data is available for the client device 1602.
59
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
[00184] In instances where the AP device 1604 transmit a DTIM beacon signal,
the AP
device 1604 can transmit the broadcast or multicast data after (e.g.,
immediately after)
transmitting the DTIM beacon signal. Consequently, one difference between a
TIM beacon
signal (e.g., indicating the presence of buffered unicast data for the
respective client
devices) and a DTIM beacon signal (e.g., indicating the presence of buffered
broadcast or
multicast data for the respective client devices) is that the AP device 1604
transmits
buffered broadcast or multicast data to the respective client devices after
(e.g., immediately
after) the DTIM beacon signal. Consequently, a DTIM beacon signal can indicate
to the
client device 1602 that it needs to remain awake to receive the buffered
broadcast or
multi cast data from the AP device 1604.
[00185] Legacy power save is a power save mechanism defined for use in one or
more of
the IEEE 802.11 family of standards that allows the client device 1602 to
inform the AP
device 1604 that it expects to enter a sleep mode and may, consequently, be
unavailable to
receive a given number of subsequent beacon signals from the AP device 1604.
As
described above, the maximum number of beacon signals that the client device
1602
expects to be asleep through can be indicated by the Listen Interval field
1612 negotiated
during association process (e.g., the example process 1600 shown in FIG. 16).
During this
time, the client device 1602 may power down, but may be required to maintain a
precise
clock to ensure it powers up in time to receive a beacon signal from the AP
device 1604.
[00186] The legacy power save mechanism makes use of a power management bit in
a
frame control field of a MAC header. FIG. 18 shows an example MAC header 1800
having a
frame control field 1802. The frame control field 1802 includes a power
management bit
1804. The client device 1602 can indicate to the AP device 1604 that it
expects to enter a
sleep mode by transmitting a MAC layer message to the AP device 1604. The MAC
layer
message can be a 0 payload length MAC frame (a Null Data Frame) where the
power
management bit 1804 is set to a first value (e.g., 1). While the client device
1602 is in sleep
mode, the AP device 1604 can buffer any unicast data for the client device
1602 and set the
bit corresponding to the given AID in the TIM element 1700 indicating unicast
data is
queued. With regards to broadcast or multicast data, although the client
device 1602 may
sleep through the number of TIM beacon signals indicated in the Listen
Interval field 1612,
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
the client device 1602 may need to wake up for all DTIM beacon signals so that
it can
receive the broadcast or multicast data. Once the client device 1602 has woken
up to
receive the TIM beacon signals and any buffered data, the client device 1602
can transmit a
MAC layer message to the AP device 1604 with the power management bit 1804 set
to a
second, different value (e.g., 0), which indicates to the AP device 1604 that
it may transmit
any buffered data to the client device 1602.
[00187] In order to begin fetching buffered data from the AP device 1604, the
client
device 1602 may transmit a power save polling (PS-POLL) message to the AP
device 1604.
FIG. 19 shows an example format of a PS-POLL message 1900. The PS-POLL message
1900
includes a frame control field 1902, a duration or AID field 1904, a basic
service set
identifier (BSSID) field 1906, a transmitter address (TA) field 1908, and a
frame control
sequence (FCS) field 1910. The PS-POLL message that is transmitted from the
client device
1602 to the AP device 1604 is acknowledged by the AP device 1604, which
subsequently
sends a single data frame to the client device 1602. If more than a single
data frame is
buffered at the AP device 1604, the more data field 1806 of the MAC header
1800 may be
set to 1. Subsequent data frames are then provided by the AP device 1604 to
the client
device 1602 one by one in the legacy power save mechanism.
[00188] In some instances, an unscheduled automatic power save delivery (U-
APSD)
mechanism may be used as an enhancement to the legacy power save mechanism.
The U-
APSD mechanism introduces the notion of Quality of Service (QoS), allowing an
application
to group messages into different categories depending on quality. As part of
the U-APSD
feature, mechanisms may be added to allow the client device 1602 to wake up
from sleep
mode and request more than one message to be delivered (depending on the QoS
indication) by the AP device 1604. Longer time windows may be allocated for
higher
priority data. In general, the U-APSD mechanism may be similar to the legacy
power save
mechanism, except that efficiency gains are made by the client device 1602 to
retrieve
buffered data from the AP device 1604.
[00189] As described above, wireless sensing (e.g., wireless motion detection)
may be
based on a wireless communication device transmitting a set of wireless
signals, which can
be used to detect changes in the communication channel. In many wireless
sending
61
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
applications, periodic measurements of the communication channel may be
required for
many sensing applications to detect changes in the communication channel. To
enable such
periodic measurements, a central coordinator (e.g., residing on an AP device
in some
implementations) may be used to elicit transmissions (e.g., MIMO
transmissions) from
wireless communication devices (e.g., client devices that are associated with
the AP
device). As described above in relation to FIGS. 9, 10, 11A to 11C, 12A, 12B,
and 13, various
protocols within all layers of the OSI model 700 (e.g., shown in FIG. 7),
including the MAC
layer Network Layer, Transport Layer, even including up to the Application
Layer, can be
used to elicit periodic transmissions.
[00190] The power save functionality present in one or more of the IEEE 802.11
family
(e.g., the legacy power save or U-APSD mechanisms) allow for power reduction
for all types
of wireless communication devices. However, for the purpose leveraging
existing off-the-
shelf wireless communication devices for wireless sensing without additional
software or
firmware modifications, the power save functionality poses a challenge since
wireless
communication devices may suspend or power down wireless communication for an
interval of time (typically under control of the device). Referring to FIG.
16. since the client
device 1602 may not request data to be delivered for a duration defined by
value in the
Listen Interval field 1612, different client devices may sleep for different
periods of time
that is out of the control of the wireless network or AP device 1604. While
the client device
1602 is in sleep mode, it may not be aware that there is queued data (e.g.,
unicast queued
data) at the AP device 1604 until the client device 1602 wakes up to receive a
TIM beacon
signal. This occurs for both the legacy power save or U-APSD mechanisms.
[00191] Broadcast or multicast messages from the AP device 1604 can be used to
elicit a
transmission from the client device 1602. In some instances, use of broadcast
or multicast
messages for eliciting transmissions from the client device 1602 may be
appealing since
the client device 1602 may need to wake up to receive DTIM beacon signals,
which is a
network-controlled parameter. From an elicitation viewpoint it may also be
more efficient
if a single broadcast or multicast message could be used to generate multiple
transmissions
for the client device 1602. In addition, the DTIM Period setting (e.g., in
field 1708 in FIG.
17) is universal across all associated client devices, requiring them all to
wake up at a time
62
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
determined by the DTIM period. However, the DTIM period may be typically set
such that a
DTIM beacon signal is transmitted every 2 or 3 beacons (e.g., every 204.8 ms
or 307.2 ms,
respectively), which may not be suitable for wireless sensing applications
(which in some
cases require periodic measurements with a rate of around 100 ms).
[00192] The ARP broadcast protocol may be leveraged to elicit periodic
transmissions
from the client device 1602 at a rate that would be suitable for wireless
sensing
applications. However, some intelligent AP devices can implement a caching ARP
service
which can respond on behalf of a client device without the need for sending a
broadcast
transmission. For other multicast protocols, not all client devices subscribe
to multicast
services without explicit user action or the install of extra software.
Together, these
constraints post a challenge for schemes that make use of a deterministic
wakeup to
receive the DTIM beacon signal and broadcast or multicast messages. There are
services
such as multicast Domain Name System (mDNS) or DNS service discovery (DNS-SD),
which
operate using broadcast or multicast messaging, however their usage is just
beginning to
become more common among common IoT devices. Therefore, a mechanism may be
needed to prevent specific client devices from entering sleep mode.
[00193] A decision for a client device to enter power save mode may be made at
one or
more layers in an OS! model (e.g., shown in FIG. 7). In some instances, a
network
implementer can make the decision as to which of the layer(s) in the OSI model
may be
used to decide whether a client device enters a power save mode. Typically,
the main
criteria used is based on whether the client device has data (e.g., at the
given layer) to
transmit or the frequency or type of data that is being received by the client
device. The
processes described above in relation to FIGS. 9, 10, 11A to 11C, 12A, 12B,
and 13 can be
used to generate signals at one or more layers in the OS! model (and to cause
a
corresponding response to be transmitted); therefore, the processes described
above in
relation to FIGS. 9, 10, 11A to 11C, 12A, 12B, and 13 can be used to prevent
client devices
from entering a power save mode.
[00194] In particular, the processes described above in relation to FIGS. 9,
10, 11A to
11C, 12A, 12B, and 13 can utilize existing protocols which are present on off-
the-shelf
client devices and can operate without any user configuration or the install
of extra
63
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
software. Furthermore, the messages that are communicated in an efficient
manner using
the existing protocols and have small overhead (e.g., as shown in FIG. 8) in
the elicitation of
a transmission.
[00195] As described above, the processes shown in FIGS. 9, 10, 11A to 11C,
12A, 12B,
and 13 can be used to elicit MIMO transmissions to that PHY preamble training
fields in the
MIMO transmissions can be used to detect changes in the communication channel.
Additionally or alternatively, the processes shown in FIGS. 9, 10, 11A to 11C,
12A, 12B, and
13 can be used to prevent a wireless communication device (e.g., a client
device) from
entering a sleep mode. Specifically, the rate at which elicitations are
requested can be
programmable such that a minimum is achieved. A programmable elicitation rate
can
prevent a wireless communication device from entering a sleep mode and can
reduce the
load added to the network and device.
[00196] The programmable elicitation rate can be provided as an input to one
or more of
the processes shown in FIGS. 11A to 11C, 12A, 12B, and 13. For example, the
programmable elicitation rate can be used by the timer of the wireless
communication
device during timer setup in operations 1101, 1205, 1303 in FIGS. 11A, 12A,
and 13,
respectively (e.g., the timer can be setup so that transmissions are elicited
at the
programmed elicitation rate). As another example, the programmable elicitation
rate can
be used by the timer of the wireless communication device during the timer
tick operation
1123 shown in FIG. 11B (e.g., each timer tick can be asserted at a rate that
is substantially
equal to the programmed elicitation rate). As a further example, the
programmable
elicitation rate can be used in operations 1221 and 1223 shown in FIG. 12B.
[00197] FIG. 20 shows an example control loop 2000 that can be used to vary
the rate at
which transmissions are elicited. The example control loop 2000 can be used to
ensure
that the rate at which transmissions are elicited is greater than a minimum
value, which in
turn can prevent a wireless communication device from entering a sleep mode
and can
reduce the load added to the network and device.
[00198] The example control loop 2000 includes a first wireless communication
device
2002 and a second wireless communication device 2004. The first wireless
communication
64
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
device 2002 transmits a message 2003 (e.g. a network or transport layer
message) that is
addressed to the second wireless communication device 2004. The message 2003
may be
transmitted in response to one or more of elicitation processes 2006A, 2006B.
In some
implementations, the elicitation process 2006A may be one or more of the
processes
described above in relation to FIGS. 9, 10, 11A to 11C, 12A, 12B, and 13. In
such
implementations, the message 2003 may be higher layer data traffic. In some
implementations, the elicitation process 2006B can be an optional or
additional elicitation
process. As an example, the elicitation process 2006B can be an asynchronous
subsystem
or a state machine that is implemented separately from the process 2006A. For
example,
the elicitation process 2006B may be configured to independently generate
messages 2003
(e.g., leveraging a MAC protocol) for transmission to the second wireless
communication
device 2004. The response from the second wireless communication device 2004
can be
used by the first wireless communication device 2002 to generate channel
information
(e.g., channel state information), which in turn can be used to detect changes
in the
communication channel. An example of the elicitation process 2006B is a state
machine
implemented within the MAC and/or PIIY layers, which does not require the use
of higher
layer protocols. This state machine could even include components or
subsystems defined
by the IEEE 802.11 family of standards.
[00199] As discussed above, the elicitation process 2006B can be an optional
or
additional elicitation process. In implementations where the elicitation
process 2006B is an
additional process, the elicitation process 2006B operates independently from
the
elicitation process 2006A. In some instances, the elicitation process 2006B
generates
elicitation messages 2003 at a rate that is suitable for wireless sensing
applications and
that prevents the first wireless communication device 2002 from entering sleep
mode. For
example, in instances where the wireless sensing application operates on
channel
information that is generated every 100 ms, the elicitation process 200613 can
generate the
message 2003 every 100 ms. One feature of using the elicitation process 200613
is that the
messages 2003 generated by the elicitation process 2006B causes the second
wireless
communication device 2004 to generate respective responses 2005, which can be
used to
generate channel information, while the responses to messages generated by the
elicitation
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
process 2006A are not used to generate channel information, but rather to
prevent the
device from entering a power savings mode. As discussed above, the elicitation
process
2006B can be an optional or additional elicitation process. In implementations
where the
elicitation process 200613 is optionally left out of the control loop 2000,
the elicitation
process 2006A can be used to generate messages 2003 that can be used for both
preventing the first wireless communication device 2002 from entering sleep
mode and
generating channel information (e.g., channel state information) that can be
used to detect
changes in the communication channel.
[00200] A transmitter of the first wireless communication device 2002
communicates the
message 2003 to the second wireless communication device 2004. In some
implementations, the second wireless communication device 2004 is a Wi-Fi
client device
having a Wi-Fi subsystem 2008 (which includes a radio subsystem and a baseband
subsystem). In such implementations, the transmitter of the first wireless
communication
device 2002 may have IEEE 802.11 compliant features. The second wireless
communication device 2004 may further include device higher layer logic
circuits 2010.
Along with the Wi-Fi subsystem 2008, the device higher layer logic circuits
2010 execute
decision logic to determine whether the second wireless communication device
2004 enter
sleep mode. The criteria for entering sleep mode may be implementation
specific, and in
some instances could be based on the rate of data exchange between the Wi-Fi
subsystem
2008 and the device higher layer logic circuits 2010. As an example, the
second wireless
communication device 2004 may not enter sleep mode when there is a high rate
of data
exchange between the Wi-Fi subsystem 2008 and the device higher layer logic
circuits
2010.
[00201] In response to receiving the message 2003 (e.g., network or transport
layer
message), the second wireless communication device 2004 sends a response
transmission
(e.g., a MIMO transmission) that traverses a space between the first and
second wireless
communication devices 2002, 2004. The response transmission is received by a
receiver of
the first wireless communication device 2002. In some instances, the receiver
of the first
wireless communication device 2002 generates channel information (e.g.,
channel state
information) for each response transmission that is received from the second
wireless
66
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
communication device 2004. As described above, the channel information can be
generated based on one or more training fields in each of the response
transmissions
received from the second wireless communication device 2004.
[00202] Since the channel information is generated for each response
transmission that
is received from the second wireless communication device 2004, the channel
information
is generated at some rate, which can be measured using rate measurement
circuitry 2012.
In some instances, the rate measurement circuitry 2012 determines an average
number of
times channel information is generated over a programmable time interval
(indicated in
FIG. 20 as an integration interval). In some instances, the integration
interval is about 10
seconds.
[00203] The rate at which the channel information is generated is compared
against an
expected rate (e.g., in difference block 2014). In some instances, the
expected rate can be
the minimum rate at which response transmissions need to be elicited to
prevent a
wireless communication device from entering a sleep mode. The difference block
2014
performs a subtraction between the measured rate (e.g., output of rate
measurement
circuitry 2012) and the expected rate, and the difference is provided to a
rate selection
block 2016 that initially selects and subsequently varies the rate at which
elicitation
messages 2003 are transmitted from the first wireless communication device
2002 to the
second wireless communication device 2004 (e.g., based on the difference
provided to the
rate selection block 2016 by the difference block 2014).
[00204] In some instances, the initial rate at which elicitation messages 2003
are
transmitted from the first wireless communication device 2002 to the second
wireless
communication device 2004 may be based on an initial value 2018. In some
implementations, the initial value 2018 may be a system-defined value or a
user-defined
value. In some instances, the initial value 2018 may be substantially equal to
the expected
rate (e.g., shown in difference block 2014). If the output produced by the
difference block
2014 indicates that channel information is being generated at a rate that is
less than the
expected rate, the rate selection block increases the rate at which the
elicitation messages
2003 are transmitted from the first wireless communication device 2002 to the
second
wireless communication device 2004, up to a maximum rate 2020. The maximum
rate
67
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
2020 may be selected based on external factors, such as network load, or
device load. In
some instances, the maximum rate 2020 is set to around 40 ms. The output of
the rate
selection block 2016 (representing the updated rate at which the elicitation
messages 2003
are transmitted) may then be provided as an input to one or more of the
processes shown
in FIGS. 11A to 11C, 12A, 12B, and 13.
[00205] FIG. 21 shows a flowchart representing an example method 2100 of
varying a
rate of eliciting MIMO transmissions from wireless communication devices. In
some
instances, the method 2100 illustrates a general operation of the control loop
2000 shown
in FIG. 20. The process 2100 may include additional or different operations,
and the
operations shown in FIG. 21 may be performed in the order shown or in another
order. In
some cases, one or more of the operations shown in FIG. 21 are implemented as
processes
that include multiple operations, sub-processes for other types of routines.
In some cases,
operations can be combined, performed in another order, performed in parallel,
iterated or
otherwise repeated or performed in another manner. The process 2100 may be
performed
by the example wireless communication devices 102A, 102B, 102C shown in FIG.
1, by the
example wireless communication devices 204A, 204B, 204C shown in FIGS. 2A and
2B, by
any of the example devices (e.g., client devices 232 and AP devices 226, 228)
shown in FIG.
2C, or by another type of device.
[00206] The process 2100 may be performed by a wireless communication device
that
seeks to elicit MIMO transmissions from another wireless communication device.
At 2102,
a first set of messages is wirelessly transmitted at a first transmission rate
to the device
from which MIMO transmissions are sought. The first set of messages can be
first network
layer messages, which may be generated and transmitted according to the ICMP
ping
process (e.g., described in FIGS. 11A, 11B, 11C), the ARP ping process (e.g.,
described in FIG.
13), or a combination thereof. As described in FIG. 8, the first network layer
messages may
be encapsulated into the payload field of respective Media Access Control
(MAC) layer
messages. The first set of messages can, additionally or alternatively, be
first transport
layer messages, which may be generated and transmitted according to the TCP
ping
process (e.g., described in FIGS. 12A, 1213). As described in FIG. 8, the
first transport layer
messages that may be generated may be encapsulated into the payload field of
respective
68
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
network layer messages. In some implementations, the network or transport
layer
messages may be addressed to the device from which MIMO transmissions are
sought. The
address of the device from which MIMO transmissions are sought may be an upper
layer
logical address (e.g., network address) of the device and may be obtained
using the process
described in FIG. 10.
[00207] At 2104, MIMO transmissions are received from the device. The MIMO
transmissions can include MIMO training fields. The MIMO training fields
contain signals
(e.g., CSI) having a higher frequency resolution, a greater number of
subcarrier frequencies,
and a higher frequency bandwidth compared to Legacy training fields in the PHY
frame.
Use of the MIMO training field for motion detection provides more accurate
motion
detection capabilities. Therefore, at 2106, a training field is identified in
each MIMO
transmission, and channel information is generated based on the training field
(at 2108). At
2110, the rate at which the channel information is generated is determined
(e.g., using rate
measurement circuitry 2012 shown in FIG. 20). At 2112, the first transmission
rate is
changed to a second, different transmission rate based on the rate at which
the channel
information is generated (e.g., using difference block 2014 and rate selection
block 2016
shown in FIG. 20). At 2114, a second set of messages (e.g., a second set of
network or
transport layer messages) is wirelessly transmitted at the second transmission
rate to the
device from which MIMO transmissions are sought.
[00208] Some of the subject matter and operations described in this
specification can be
implemented in digital electronic circuitry, or in computer software,
firmware, or
hardware, including the structures disclosed in this specification and their
structural
equivalents, or in combinations of one or more of them. Some of the subject
matter
described in this specification can be implemented as one or more computer
programs, i.e.,
one or more modules of computer program instructions, encoded on a computer
storage
medium for execution by, or to control the operation of, data-processing
apparatus. A
computer storage medium can be, or can be included in, a computer-readable
storage
device, a computer-readable storage substrate, a random or serial access
memory array or
device, or a combination of one or more of them. Moreover, while a computer
storage
medium is not a propagated signal, a computer storage medium can be a source
or
69
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
destination of computer program instructions encoded in an artificially
generated
propagated signal. The computer storage medium can also be, or be included in,
one or
more separate physical components or media (e.g., multiple CDs, disks, or
other storage
devices).
[00209] Some of the operations described in this specification can be
implemented as
operations performed by a data processing apparatus on data stored on one or
more
computer-readable storage devices or received from other sources.
[00210] The term "data-processing apparatus" encompasses all kinds of
apparatus,
devices, and machines for processing data, including by way of example a
programmable
processor, a computer, a system on a chip, or multiple ones, or combinations,
of the
foregoing. The apparatus can include special purpose logic circuitry, e.g., an
FPGA (field
programmable gate array) or an ASIC (application specific integrated circuit).
The
apparatus can also include, in addition to hardware, code that creates an
execution
environment for the computer program in question, e.g., code that constitutes
processor
firmware, a protocol stack, a database management system, an operating system,
a cross-
platform runtime environment a virtual machine, or a combination of one or
more of them.
[00211] A computer program (also known as a program, software, software
application,
script, or code) can be written in any form of programming language, including
compiled or
interpreted languages, declarative or procedural languages, and it can be
deployed in any
form, including as a stand-alone program or as a module, component,
subroutine, object or
other unit suitable for use in a computing environment.. A computer program
may, but
need not, correspond to a file in a file system. A program can be stored in a
portion of a file
that holds other programs or data (e.g., one or more scripts stored in a
markup language
document), in a single file dedicated to the program, or in multiple
coordinated files (e.g.,
files that store one or more modules, sub programs, or portions of code). A
computer
program can he deployed to he executed on one computer or on multiple
computers that
are located at one site or distributed across multiple sites and
interconnected by a
communication network.
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
[00212] Some of the processes and logic flows described in this specification
can be
performed by one or more programmable processors executing one or more
computer
programs to perform actions by operating on input data and generating output.
The
processes and logic flows can also be performed by, and apparatus can also be
implemented as, special purpose logic circuitry, e.g., an FPGA (field
programmable gate
array) or an ASIC (application specific integrated circuit).
[00213] To provide for interaction with a user, operations can be implemented
on a
computer having a display device (e.g., a monitor, or another type of display
device) for
displaying information to the user and a keyboard and a pointing device (e.g.,
a mouse, a
trackball, a tablet, a touch sensitive screen, or another type of pointing
device) by which the
user can provide input to the computer. Other kinds of devices can be used to
provide for
interaction with a user as well; for example, feedback provided to the user
can be any form
of sensory feedback, e.g., visual feedback, auditory feedback, or tactile
feedback; and input
from the user can be received in any form, including acoustic, speech, or
tactile input. In
addition, a computer can interact with a user by sending documents to and
receiving
documents from a device that is used by the user; for example, by sending web
pages to a
web browser on a user's client device in response to requests received from
the web
browser.
[00214] In a general aspect MIMO transmissions are elicited from wireless
communication devices and for wireless sensing.
[00215] In some aspects, a wireless sensing system (e.g., a motion detection
system)
initiates a message through a communication protocol defined in a layer above
the physical
(PHY) layer and the data link (MAC) layer in a first wireless communication
device (e.g., in
a transport layer or a network layer). The message is addressed to, and
wirelessly
transmitted to, a second wireless communication device. In response to the
message, the
second wireless communication device sends a MIMO transmission that traverses
a space
between the first and second wireless communication devices. The first
wireless
communication device senses the space (e.g., detects motion of an object in
the space)
based on the MIMO transmissions.
71
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
[00216] In a first example, a first wireless communication device: obtains a
network
layer address of a second wireless communication device; addresses network
layer
messages to the network layer address of the second wireless communication
device;
initiates wireless transmission of the network layer messages; in response to
the network
layer messages, receives MIMO transmissions from the second wireless
communication
device, where the MIMO transmissions traverse a space between the first and
second
wireless communication devices; generates a series of channel responses based
on a
training field in the MIMO transmissions; and detects motion of an object in
the space
based on the series of channel responses.
[00217] Implementations of the first example may include one or more of the
following
features. The network layer messages can be sent according to an ICMP Ping
process, an
ARP ping process, or another type of process. The MIMO training field can be
an HE-LTF,
VHT-LTF or an HT-LTF. The wireless sensing may include detecting motion of an
object in
the space.
[00218] In a second example, a first wireless communication device: generates
a
transport layer message addressed to a second wireless communication device;
initiates
wireless transmission of the transport layer messages; in response to the
transport layer
messages, receives MIMO transmissions from the second wireless communication
device,
where the MIMO transmissions traverse a space between the first and second
wireless
communication devices; generates a series of channel responses based on a
training field in
the MIMO transmissions; and performs wireless sensing of the space based on
the series of
channel responses.
[00219] Implementations of the second example may include one or more of the
following features. The transport layer messages can be sent according to a
TCP Ping
process, or another type of process. The MIMO training field can be an HE-LTF,
VHT-LTF or
an HT-I.TF. The wireless sensing may include detecting motion of an object in
the space.
[00220] In a third example, a first wireless communication device: initiates a
first
mechanism to elicit a MIMO transmission from a second wireless communication
device,
and detects a failure of the first mechanism; initiates a second, different
mechanism to elicit
72
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
a MIMO transmission from the second wireless communication device, and detects
a
success of the second mechanism; generates a series of channel responses based
on MIMO
transmissions elicited from the second device using the second mechanism; and
performs
wireless sensing based on the series of channel responses.
[00221] Implementations of the third example may include one or more of the
following
features. The first mechanism and the second mechanism may include an ICMP
Ping, a TCP
Ping, an ARP Ping, or another type of request/response process. The fist
wireless
communication device may initiate the first mechanism and the second mechanism
(and
possibly additional mechanisms) based on a state of a state machine. The
wireless sensing
may include detecting motion of an object in a space traversed by the MIMO
transmissions.
[00222] In a fourth example, a first wireless communication device in a
wireless
communication network may: generate network or transport layer messages
addressed to
a second wireless communication device in the wireless communication network;
wirelessly transmit the network or transport layer messages to the second
wireless
communication device to elicit multiple-input-multiple-output (MIMO)
transmissions from
the second wireless communication device; and receive MIMO transmissions from
the
second wireless communication device. The MIMO transmissions may traverse a
space
between the first wireless communication device and the second wireless
communication
device. The first wireless communication device may also identify a training
field in each
MIMO transmission; generate channel information based on the respective
training fields;
and detect motion that occurred in the space based on the channel information.
[00223] Implementations of the fourth example may include one or more of the
following
features. The network or transport layer messages includes network layer
messages
encapsulated into a payload field of respective Media Access Control (MAC)
layer messages.
The network layer messages are wirelessly transmitted according to an Internet
Control
Message Protocol (ICMP) Ping process. The first wireless communication device
may
further obtain a network layer address of the second wireless communication
device; and
encapsulate the network layer address of the second wireless communication
device into
the payload field of the respective MAC layer messages. The network or
transport layer
messages include transport layer messages encapsulated into a payload field of
respective
73
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
network layer messages, and the transport layer messages are wirelessly
transmitted
according to a Transmission Control Protocol (TCP) Ping process, an Address
Resolution
Protocol (ARP) Ping addressed to the second wireless communication device, or
a
combination thereof. The first wireless communication device may further
detect a failure
of the network or transport layer messages to elicit MIMO transmissions from
the second
wireless communication device; in response to detecting the failure, generate
second
network or transport layer messages addressed to the second wireless
communication
device; and wirelessly transmit the second network or transport layer messages
to the
second wireless communication device to elicit MIMO transmissions from the
second
wireless communication device. The network or transport layer messages are
wirelessly
transmitted according to a first type of communication process, and the second
network or
transport layer messages are wirelessly transmitted according to a second,
different type of
communication process. The first type of communication process and the second
type of
communication process are selected from the group consisting of an ICMP Ping,
an ARP
Ping addressed to the second wireless communication device, and a TCP Ping.
Identifying
the training field in each MIMO transmission includes identifying the training
field in a PIIY
frame of each MIMO transmission.
[00224] In a fifth example, a non-transitory computer-readable medium stores
instructions that are operable when executed by data processing apparatus to
perform one
or more operations of the first example, the second example, the third
example, or the
fourth example. In a sixth example, a system includes a plurality of wireless
communication
devices, and a device configured to perform one or more operations of the
first example,
the second example, the third example, or the fourth example.
[00225] Implementations of the sixth example may include one or more of the
following
features. One of the wireless communication devices can be or include the
device. The
device can be located remote from the wireless communication devices.
[00226] In another general aspect, a rate at which multiple-input/multiple-
output
(MIMO) transmissions are elicited from wireless communication devices is
varied (e.g., to
prevent the wireless communication devices from entering a sleep / power-
saving mode).
74
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
[00227] In a seventh example, a first wireless communication device:
wirelessly
transmits a first set of messages at a first transmission rate to a second
wireless
communication device to elicit first multiple-input-multiple-output (MIMO)
transmissions
from the second wireless communication device. The first wireless
communication device
also receives the first MIMO transmissions from the second wireless
communication
device, where the first MIMO transmissions traverse a space between the first
wireless
communication device and the second wireless communication device. The first
wireless
communication device further generates first channel information based on
respective
training fields identified in each of the first MIMO transmissions; determines
a rate at
which the first channel information is generated; and varies the first
transmission rate to a
second, different transmission rate based on the rate at which the first
channel information
is generated. The first wireless communication device additionally wirelessly
transmits a
second set of messages at the second transmission rate to the second wireless
communication device to elicit second MIMO transmissions from the second
wireless
communication device.
[00228] Implementations of the seventh example may include one or more of the
following features. Varying the first transmission rate to the second
transmission rate
includes: comparing the rate at which the first channel information is
generated to a
threshold, the threshold being a minimum transmission rate to prevent the
second wireless
communication device from entering a power saving mode; and increasing the
first
transmission rate to the second transmission rate in response to the rate at
which the first
channel information is generated being less than the threshold. The first set
of messages
includes a first set of network or transport layer messages, and the second
set of messages
includes a second set of network or transport layer messages. At least one of
the first set of
network or transport layer messages or the second set of network or transport
layer
messages includes network layer messages encapsulated into a payload field of
respective
Media Access Control (MAC) layer messages. The network layer messages are
wirelessly
transmitted according to an Internet Control Message Protocol (ICMP) Ping
process. At
least one of the first set of network or transport layer messages or the
second set of
network or transport layer messages includes transport layer messages
encapsulated into
CA 03219662 2023- 11- 20
WO 2022/246539
PCT/CA2022/050749
a payload field of respective network layer messages. The transport layer
messages are
wirelessly transmitted according to a Transmission Control Protocol (TCP) Ping
process, an
Address Resolution Protocol (ARP) Ping addressed to the second wireless
communication
device, or a combination thereof.
[00229] While this specification contains many details, these should not be
understood
as limitations on the scope of what may be claimed, but rather as descriptions
of features
specific to particular examples. Certain features that are described in this
specification or
shown in the drawings in the context of separate implementations can also be
combined.
Conversely, various features that are described or shown in the context of a
single
implementation can also be implemented in multiple embodiments separately or
in any
suitable subcombination.
[00230] Similarly, while operations are depicted in the drawings in a
particular order,
this should not be understood as requiring that such operations be performed
in the
particular order shown or in sequential order, or that all illustrated
operations be
performed, to achieve desirable results. In certain circumstances,
multitasking and parallel
processing may be advantageous. Moreover, the separation of various system
components
in the implementations described above should not be understood as requiring
such
separation in all implementations, and it should be understood that the
described program
components and systems can generally be integrated together in a single
product or
packaged into multiple products.
[00231] A number of embodiments have been described. Nevertheless, it will be
understood that various modifications can be made. Accordingly, other
embodiments are
within the scope of the description above.
76
CA 03219662 2023- 11- 20