Note: Descriptions are shown in the official language in which they were submitted.
CA 02207876 1997-06-17
CUSTOMER AU 1 ~;~TICATION APPARATUS
This invention relates to Customer Allthentication Apparatus, and more particularly to
such app~dlus for use over a telephone network.
In modern society, the telephone is being increasingly used as a means for a customer to
obtain services without the need to travel. An impe iiment of the spread of such remote
services is the risk of fraud due to inadequate customer authentication.
Credit card companies have long kept a file on personal data, such as a person's mother's
maiden name, that is unlikely to be known by fraudulent users. If a customer wishes to
obtain information about his or her account, the operator will ask questions drawn from
the customer file. This system requires operator intervention and can be defeated by a
determined fraudulent user who could obtain the limited number of items of information
by carrying out the necessary research in advance. Such a system has not yet been applied
to automated telephone services.
An object of the invention is to provide a secure customer allth~ntication system suitable
remote access of automated services.
Accordingly the present invention provides a method of authenticating a customerwishing to access a service, compri~ing the steps of storing digital data in a memory, the
digital data representing information associated with each customer, randomly generating
a stimulus related to the stored data and pre3~ g said stimulus to a customer wishing to
access the service, accepting customer input in response to the stimulus and generating
customer response data the~er~ , co.,.p~ g the customer response data with the stored
data, l~ealillg such steps on an iterative basis, and validating the customer when the
customer response data match the stored data within predefined limits.
In a p~ef~lled embodiment, customer a~lthentication is performed in two steps based on:
I) Customer voice print ~llthentication, and
2) Customer personal knowledge verification.
Depending on the level of security required, one or both steps may be used.
In one embodiment, the customer is first asked to repeat a series of spoken words and
these are m~tehed with previous digitally stored recordings made by the customer to
CA 02207876 1997-06-17
perform voice ~ign~ re verification. The customer is then asked a series of questions,
and his or her responses are first recognized using a voice recognition unit. They are then
matched with knowledge items stored in the data base. Both the spoken words and the
knowledge items are randomly selected as a subset of the set of records in the data base.
The total number of records can be quite large so as to reduce the chances of a fraudulent
user being able to obtain all the answers. Voice recognition can be performed on the
responses or not at all.
The two checks can be combined in that, if desired, voice print alltllentication can be
carried on the customer's responses to knowledge-based queries.
If desired, a timer can be arranged to time out if the user does not respond to a question
within the predet~rmined period of time. An ~lthentic customer will generally be able to
respond to the questions immediately whereas the fraudulent user, given the large number
of questions, might have to refer to a rerele.lce source, and the timer can limit the
oppo~ ily to do so by timing out if the response has not been given within a certain time
period.
The invention is particularly adapted for telephone systems with a remote telephone
providing the stimuli and accepting the customer input, and the rem~ining part of the
eqllipment being at the service provider's premises.
One particular application of the invention is bank account manipulation. Once a person
has been ~llth~nticated as a valid customer, he or she can then carry out bank transactions
from any remote location (e.g. home) using the telephone key pad. The latter, if desired,
can be used as a medns of accepting customer input, although voice comm~n~l~ arefe~ed because they are faster.
The invention also provides customer ~lthentication a~a~dlus compri~ing a memory for
storing digital data represçntin~ information items associated with each customer, a
selection unit for randomly selecting digital data associated with an information item on
an iterative basis, tr~n~d~lcer means for pres~nting a stimulus related to the stored data to a
customer wishing to access the service, input means for accepting customer input in
response to the stimulus and generating customer response data theleLvlll, a coll~dlor
for co...p~ g the customer response data with the stored data and validation means for
CA 02207876 1997-06-17
v~lid~ting the customer when the customer response data match the stored data within
predefined limits.
The tr~n~ cer means and input means can conveniently be provided by a remote
telephone.
The invention can require a perfect match to all responses, although this may beunrealistic. For example, people do not always pronounce words in exactly the same way
and a legili,llale customer might inadve.lelllly give the wrong response to a question. The
invention makes a decision on the basis of the number of correct and wrong answers.
Criteria for ~lele~ ...ining validity can be set in advance. Furthermore, the number of
iterations is flexible, and if the customer gives wrong answers or the equipment fails to
recognize a voice response, the number of iterations can be increased so that the
probability of error is small.
This invention thus allows a service provider to recognize and validate the identity of a
caller by using two fl~lth~ntication mech~llisms, either alone or in combination:
a) voice sign~hlre verification
b) caller personal knowledge verification
Task b is done by requesting verbal feedback from the caller using a randomly selected
subset of stimuli based on a set of pre-recorded knowledge items. In summary, the
allmentis~tion system can perform voice si n~hlre verification as well as user personal
knowledge verification either co~ .llly or separately.
Voice si~hlre may be pel~u~ ed on one or more pre-defined set of sounds (e.g., words).
If technology permits a wide choice of words for sign~hlre verification, then, the request
for the ~ign~hlre word(s) should consist of a subset of responses to a randomly selected
set of stimuli. Voice recognition can be performed by an system that performs voice
processing on sounds or phonemes. A suitable is VPRO by Voice Processing Corporation
of Cambridge, M~s~chlleett~
The service provider needs a ~l~t~b~e for each identity it needs to validate. This is done
by recoldillg a set of responses corresponding to a set of stimuli. During validation, only
a subset of the stimuli will be picked randomly for validating the person's identity. The
- 3 -
CA 02207876 1997-06-17
stimuli would typically (but not neces~rily) be presented in the form of a question. The
response should involve a limited set of syllables so as to facilitate the processing of the
voice prmt.
The stimuli must call, not only on the person's knowledge but also on the language
ability of the person. If a person is fluent, or has certain competence in more than one
language, the stimuli should use the person's ability to understand stimuli in the languages
he or she understands, and to provide the responses in these languages as well.
The personal stimuli ~l~t~b~ee have to be created by deciding on a set of stimuli for which
the person can easily remember the response. Ideal stimuli should appeal to knowledge
acquired during user's childhood. For safety reasons, the stimuli should be spoken by a
person other than the person which will use the validation system. Then the
answers/responses must be recorded as spoken by the target person. Obviously, all
stimuli and responses have to be tested thoroughly.
The invention will now be described in more detail, by way of example only, withreference to the accolllp~lyil1g drawings in which:-
Figure 1 is a block diagram of customer ~lthentication apparatus in accordance with the
invenhon;
Figure 2 illushrates a sample validation hand-~h~king session;
Figure 3 illustrates a typical end-to-end operating environment;
Figure 4 shows the customer ~llth~ntication a~alus as adjunct to a service provider;
Figure 5 shows a customer ~lthentication a~palalus as a front end to a service provider
system;
Figure 6 shows a physical embodiment of a customer ~lthentication apparatus; and
Figure 7 shows a ~l~t~b~e shucture suitable for use in the customer ~lthentication
app~lus.
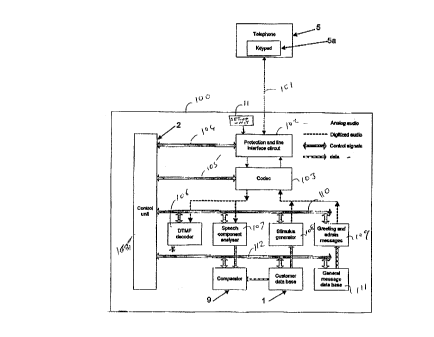
Referring now to Figure 1, an ~llthentication a~pal~lus 100 is connected to a telephone 5
with a keypad Sa over a telephone line 101, which is connected in the app~lus 100 to a
protection and line int~rf~ce circuit 102. This is in turn connected to a codec 103 for
CA 02207876 1997-06-17
digitally encoding or decoding analogue signals arriving from or going to the telephone
line 101. The codec 103 is also conn~cteci to the int~rf~(~e circuit 102 and control unit 2.
Control signals pass between the control unit 2 and the circuits 102, 103 over lines 104,
104.
The codec 103 is connected to a DTMF decoder 106, a speech component analyzer 107, a
stimulus generator 108, and a greeting and admin message generator 109. These units are
all connected to the control unit 2 via line 1 10.
The speech component analyzer 107, stimulus generator 108, and greeting and admin
message unit 109 are respectively connected to a comparator 9, customer ~latab~ee 1, and
general message ~l~t~b~e 111. The latter units are connecte~l to the control unit by line
112.
Database I stores in digital form a large number of groups of data items, each group being
associated with a particular customer. Some of the data items comprise ~ iti7ed
representations of the customer speaking selected words, and some represent responses to
questions within the personal knowledge of the customer. The knowledge items could,
for example, include the maiden name of the customer's mother, the names of any close
relatives of the customer or any general knowledge of the customer, perhaps pe~ g to
the place where the customer was brought up or went to school. If the customer is
f~mili~r with more than one language, knowledge items can be stored in any language
f~mili~r to the customer.
On initiation of a call, control unit 2 sends a message, which is the same for all customers,
requesting the customer to enter his or her account number through the keypad. This is
converted into an audio message in the codec 103. The customer keys in his or her
account number through the telephone keypad 5a, and the response signals are decoded by
DTMF decoder 106, which passes the results to the control unit 2.
The control unit 2 then randomly selects data items from the database 1 corresponding to
the received account number, and passes these data items to the telephone 5 through the
codec 103. The customer normally responds verbally although except in the case of
mi~m~tçhing data, the customer can also respond through the keypad using DTMF tones.
CA 02207876 1997-06-17
~.~sllming the customer responds verbally, the response data is passed through codec 103
to the comparator 9, which colllpales the response data with the corresponding stored data
in the ~l~t~b~e 1. The control unit 2 then allocates a score to the correct ~e ,~onses and
makes a decision according to predefined criteria. The control unit 10 can be designed to
require all responses to be correct, although it can allow for some errors depending on the
design of the system and the level of security required.
The speech component analyzer 107 checks the voice-print of the customer. This can be
in response to a request for the customer to pronounce certain words stored in the
customer ~l~taba~e, and/or the answers supplied to the knowledge-based queries. For
example, if the system asks for the customer's mother's maiden name, the control unit can
verify both that the answer is factually correct and that the answer m~tches the customer's
voice-print. This can be done either by using voice-print analysis techniques or by storing
a digital l~res~ ion of the customer actually responding to the question.
Figure 2 illustrates a typical banking transaction using app~lus in accordance with the
invention. The caller is identified on the left hand side of the figure and the automatic
b~nking service on the right. First the caller places a call to the automatic banking
service, which in turn responds by requesting the account number, which the caller enters
by using the telephone keypad. The account number is transmitted as DTMF tones
(although dial pulses can be used) to the automatic banking service which then initi~tes
operation of the customer authentication cycle.
A random stimulus is selecte~l from the ~lat~b~e 1, and the customer's response validated.
If the response is valid, the cycle is repeated with a different randomly selected stimulus.
If his response is incol,~ , the system can either repeat the stimulus or note the response
as incorrect and move onto the next stimulus. In either case, the validation unit 10 notes
the incorrect response.
After a certain number of iterations, the customer is deemed authentic, and the system
notifies the customer that he has been authenticated and that he can request a transaction.
The customer then requests the transaction, which is carried out by the automatic balLking
service. After the transaction has been carried out, the automatic banking service sends an
acknowle~lgment to the customer who can then hang up or request another transaction.
CA 02207876 1997-06-17
Figure 3 shows a more generic illustration of the invention. In Figure 3 a service provider
20 includes an aumentication app~alus in accordance with the invention. The service
provider co~l~n,u~icates over any voice transport system 21, for example a telephone
network, to a voice input device 22, which could be a telephone.
Figure 4 shows a customer ~ thentication appa,~lus in accordance with the invention as
an adjunct to a service provider. Service provider 30 includes an authentication unit 31
connected to customer dat~b~e 1. The service provider dat~b~e 32 con~ills information
that customers desire to access and manipulate. For instance, d~t~h~ce 32 may contain
bank accounts and the like. Interaction with the service provider 30 is through the
privileged user's unit 33 which is connected to the allth~ntication unit 31. The privileged
user's unit co"l",unicates with a call tçrmin~tion and ~ patch unit 34 connected to the
telephone line 31. The latter is also connected to a general service provider unit 35,
which does not require security.
Figure 5 shows another configuration of the invention where the a~lthentication unit is
provided as a front end to a multiple service provider system. Telephone line 21 is
connected to call t~ ion and user idçntification and allthPntication unit 40 connected
to user's personal knowledge dat~ba~e 1. A calling customer is ~l~thenticaled in the
manner described with reference to Figure 2. Once allth~nticated, the customer can be
connected to any one ofthe desired service providers 41 each connected to associated
d~t~b~e units 40 co.~ -g information desired to be accessed or manipulated by the
customer.
Figure 6 shows the physical embodiment of an a~1thçntication unit in accordance with the
invention. Telephone line 21 is connected to digital or analog in1Prf~ce and switching unit
50 through switch 56. The latter allows the unit 50 to be ~ltçrn~tively connected to a local
input 55 for set-up mode or control purposes. Unit 50 is connected over bus, for example
an MVIP or SCSA bus to a digital signal processing unit 51. Interface unit 50 and DSP
unit 51 are connected to another bus, which could be an ISA bus, or an EISA bus, for
example 52. Central processing unit 53 and user's personal knowledge storage (l~t~h~e
54 are connected to the bus 52. The implçmentation shown in Figure 6 is a more practical
CA 02207876 1997-06-17
implementation than the one shown in Figure 1, which helps understand the principles of
the invention, since it uses modern digital signal proceeeing and bus technology.
In Figure 6, the interface for the voice media connects the voice circuit to the DSP unit
when required for voice eign~ re analysis and stimulus-response h~n~leh~ke. A high
speed connection is provided between these two resources, and this can be implemente~l
using the disclosed MVIP or SCSA bus.
Figure 7 shows the functional org~ni7~ti~n ofthe personal knowledge database 1. Each
stimulus SN is associated with a corresponding response RN. The stimulus could be for
example a request to speak a word in which case the stored response is a ~iigiti7~cl
representation of the customer previously speaking the word. If the stimulus is a question,
then the response is the expected answer.
For each new customer, the personal ~l~t~b~ee must of course be established. This can
achieved by the customer visiting the service provider premises and providing a series of
responses through set-up unit 11, which can, for example, include a telephone h~n-leet
The control unit 2 simply requests the new customer to provide answers to a wide range
of question and repeat certain selected words. The responses are digitized and stored in
the new customer's personal information (1~t~b~ee within the database 1.
It will be observed that the invention thus provides an flllthentication method and
appa~alus that offers secure customer validation in a telephone environment. It will be
obvious that the skilled person in the art will be able to devise many di~e~ means of
implementing the invention without departing from the scope of the invention as defined
in the claims.