Note: Descriptions are shown in the official language in which they were submitted.
CA 02465650 2004-04-30
IVlethod for Preventing User Identity Spoofing or Impersonation in
!/nice Biometric Authentication Systems
FIELD OF INVENTION
s [0001] The present invention relates to voice biometric authentication. In
particular, the present invention relates to method and system for preventing
user identity spoofing in a voice biometric authentication system.
BACKGROUND OF THE INVENTION
[0002] The biometric characteristics of an individuals voice are as unique to
~o an individual as a fingerprint or retinal pattern. Sound waves generated by
our vocal organs, for practical purposes, have enough repetitions to be
regarded as periodic. In 19t" century, Fourier showed that any non-sinusoidal
wave, no matter how complicated, can be represented as the sum of a
number of sinusoidal waves of different frequencies, amplitudes and phases.
~s The spectrum of the speech wave specifies the amplitudes, frequencies and
phases of the wave's sinusoidal components. The sum of many sinusoidal
waves can result in a wave with a non-sinusoidal shape with the basic pattern
of the non-sinusoidal wave repeating with the sarne periodicity as the lowest
frequency component of all components added. Phase-change can also alter
2o the wave shape of the resulting wave. Therefore, a variety of wave shapes
can be represented by adding sinusoidal components of the same amplitudes
and frequencies, but of different phases. However, our hearing mechanism
cannot always detect the effect of such changes. Non-sinusoidal waves,
consisting of sinusoidal waves with the same amplitudes and frequencies,
2s often sound the same, even if their wave shapes differ because of
differences
in the phase relationship of their components. For this reason, in considering
frequency domain spectrum, only the "°amplitude'° of the non-
sinusoidal wave
considered, and not the °°phase°' spectrum. The amplitude
spectrum specifies
just the frequencies and amplitudes of the sinusoidal components
-1-
CA 02465650 2004-04-30
[0003] By regarding the sound waves as the sum of a number of waves with
simple, sinusoidal shapes, we can derive that each of the sound waves will
have a unique frequency domain spectrum with a unique identifier.
[0004] US Patent 6, 488,800 describes a speaker verification system using
s the voice of a user uttering a continuous, random length digit string is
provided. The speaker verification system includes a random digit generator
for generating a continuous, random length digit string; a user interface for
providing the continuous, random length digit string; a feature extractor for
extracting voice features from the user°s voice uttering the
continuous,
to random length digit string; a digit voice verification unit for comparing
the
voice features with items in a speaker-independent continuous digit voice
model to derive a digit string corresponding to items in the speaker-
independent continuous digifi voice model, which match the voice features,
and for determining whether the derived digit string is identical to the digit
is string provided to the user via the user interface; and a speaker
verification
unit for comparing the voice features with a speaker-dependent model of the
user to measure the similarity between them.
[0005] Extraction of characteristic frequency and intensity features from
frequency domain digital representation has been described in Canadian
2o Patent Application no. 2,364,293, which is filed in the name of the
applicant
as in the present application. Canadian Patent Application no. 2,375,415,
which is also filed in the name of the applicant of the present application,
describes a voice transaction fraud detection method and system which
includes means to assess the emotion of the user based upon analysis of
2s voice characteristics.
[0006] As with all security systems, there will be fraudsters who will attempt
to
breach or fool the system. One such method for attempting this type of
security breach is to fraudulently claim another users identity and then
attempt to gain access through impersonation. This method is called identity
3o spoofing.
-2-
CA 02465650 2004-04-30
[0007] A number of methods have been developed to prevent the identity
spoofing in a voice biometric system. However, there were disadvantages
with the existing method: in the case where a poor quality recording is made,
such as with an analog recording device, the voice verification system can
fail
s to verify the fraudster as the recording will not produce a voice print of
sufficient fidelity to match the original voice print; in the case of text
dependant voice verification systems, manipulating the recorded audio file to
subtly change the audio data can easily fool this 1-to-1-file comparison.
SUMMARY OF THE INVENTION
to [0008] The present invention relates to method and system for preventing
user identity spoofing in a voice biometric authentication system.
[0009] According to one aspect of the present invention there is provided a
method for preventing user identity spoofing in a voice biometric
authentication system comprising the steps of: determining a first unique
is characteristic identifier of a first voice; storing the first identifier in
a database;
determining a second unique characteristic identifier of a second voice; and
comparing the second identifier with the first identifier to determine the
identity of the second voice.
[0010] According to another aspect of the present invention there is provided
2o a voice biometric authentication system comprising: receiver for receiving
voices; means for determining a first unique characteristic identifier of a
first
voice; a database for storing the first identifier; means for determining a
second unique characteristic identifier of a second voice; and means for
comparing the second identifier with the first identifier to determine the
zs identity of the second voice.
[0011 ] According to yet another aspect of the present invention there is
provided a computer program product, comprising: a memory for having
computer-readable code embodied therein for authenticating voice biometric
comprising: code means for determining a first unique characteristic
identifier
_3_
CA 02465650 2004-04-30
of a first voice; code means for storing the first identifier in a database;
code
means for determining a second unique characteristic identifier of a second
voice; and code means for comparing the second identifier with the first
identifier to determine the identity of the second voice.
s [0012] It is an object of the invention to provide a novel method and system
for preventing user identity spoofing or impersonation in voice biometric
authentication systems.
[0013] One of the advantages of the present invention is that it prevents
users
from spoofing or impersonating other users..
to [0014] The invention can operate with text dependent and independent voice
biometric systems; and with voice biometric verification and identification
systems; and automatically detects attempts of identity spoofing of voice
biometric systems.
[0015] The invention further operates in real-time to detect user identity
Is spoofing attempts to prevent fraudulent access. The invention can identify
attempts to conduct identity spoofing with copied digital audio files, even
when the audio data has been partially manipulated to inject noise or other
spurious data.
[0016] This summary of the invention does not necessarily describe all
2o features of the invention.
BRIEF DESCRIPTION OF THE DRAWINGS
[0017] These and other features of the invention will become more apparent
from the following description in which reference is made to the appended
drawings wherein:
2s [0018] FIGURE 1 shows a flow chart of steps to acquire a unique identifier
in
accordance with an embodiment of the present invention; and
[0019] FIGURE 2 shows a flow chart of a method and system for preventing
user identity spoofing in a voice biometric authentication system.
-4-
CA 02465650 2004-04-30
DETAILED DESCRIPT14N
[0020] Voice biometric authentication systems usually operate in the following
manner:
~ The user enrols in the system by providing voice responses to several
s queries. The user utterances are used to form a unique voice print for
the user;
~ Successively, a user accesses the system and provides a voice sample
for verification of identity; and
~ The system compares the new voice sample print against the original
to stored from the enrolment process in order to determine if the user is
indeed who they claim to be.
[0021 ] This invention relates to a method and a system for preventing a
fraudster to attempt to spoof, or to impersonate other legitimate users, in
voice biometric based voice verification and identification systems. These
is systems are typically used in government, financial, and security
applications
in order to control user access to computer networks, telephony applications,
and/or buildings/restricted access areas. Automated, computer based
systems have been developed and used, to allow authentication of an
individuals identity based upon a sample of speech.
20 [0022] There are several classifications of the systems used to
authenticate
identity based upon voice biometrics: First, systems can either perform
speaker verification or speaker identification. in speaker verification the
user
claims an identity that must be verified as true or false. In speaker
identification the user provides a speech sample and then one must choose
2s which speaker within a closed set matches the user sample. Each of the two
systems, speaker verification and speaker identification, can also be either
text dependant or text independent. Text dependent systems use a known
utterance, for example a password or combination digit sequence, which is
predefined for each speaker. Text independent systems use a different
-s-
CA 02465650 2004-04-30
response for each identification attempt. In this case, the input could be a
random response to a question.
[0023) Fraudster attempts to impersonate a valid user through identity
spoofiing, for example, by attempting to surreptitiously record a valid user
s speaking their utterances and then attempt to access the system by using the
recorded utterances. The fraudster attempts to spoof the system by claiming
the identity of a valid user and then playing the recorded utterances for the
valid user when prompted by the voice biometric system.
[0024] As shown in Figure 1 and 2, this invention solves this problem of
to identity spoofing for voice verification and identification based biometric
systems. The invention allows the voice verification and identification based
biometric system to identify user utterances that are recordings of previous
utterances and are therefore being employed to spoof the voice biometric
access system.
is [0025) The invention involves the employment of methods to derive a unique
signature or representation of a recorded voice utterance from a user,
preferably a digital signal processing method.
[0026) Referring to Figure 1, each time a user interacts with the voice
biometric system and provides an utterance either for enrollment or for
2o verification, a unique characteristic identifier for the utterance is
derived
through signal processing methods by analyzing the frequency domain
spectrum. This unique characteristic identifier is then stored with the
utterance in the voice biometric system database.
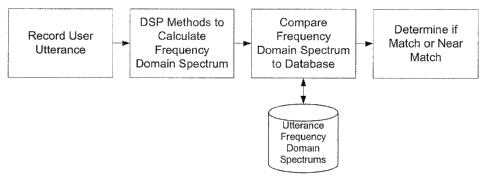
[0027] Referring to Figure 2, a user provides an audio sample, which is
2s received by the voice authentication system. A second unique identifier is
generated for this audio sample by analyzing the frequency domain spectrum.
This second identifier is compared to the first identifier which is stored in
a
database to determine whether there is a match or not.
-6-
CA 02465650 2004-04-30
[0028] It should be apparent to a person skilled in the art that the method
and
system described in Figure 2 can be used both for the user verification or
user identification, and can be either text dependant or text independent.
[0029] The analysis of the frequency domain spectrum and the calculation of
s the unique identifier can be performed, for example by a microprocessor, a
digital signal processor or any other means known to those skilled in the art.
[0030] The invention can operate with text dependent and independent voice
biometric systems; and with voice biometric verification and identification
systems; and automatically detects attempts of identity spoofing of voice
to biometric systems.
[0031 ] The invention further operates in real-time to detect user identity
spoofing attempts to prevent fraudulent access. The invention can identify
attempts to conduct identity spoofing with copied digital audio files, even
when the audio data has been partially manipulated to inject noise or other
~ s spurious data.
[0032] The present invention has been described with regard to one or more
embodiments. However, it will be apparent to persons skilled in the art that a
number of variations and modifications can be made without departing from
the scope of the invention as defined in the claims.
_7_