Note: Descriptions are shown in the official language in which they were submitted.
This application is a division of application
Serial No. 530,937, filed March 2, 1987.
Background of the Invention
-
The present invention relates to electronic
locking systems, and more particularly to electronic
locking systems of a type including a reprogrammable
key which electronically and mechanically interacts
with a reprogrammable lock cylinder.
Electronic security systems have been well
~nown for a number of years, and recent years have
seen the marriaye of electronic technology with
traditional door locking devices such as mortise locks.
Some of the early commercial systems have required a
hard-wired connection between a central processor and
the electronics of the locking systems of ~iven doors.
A disadvantage of such systems is the requirement of
cable connections between the central, controller and
individual loc]c assemblies. This requires expensive
remodelling, and such installations are vulnerable to
tampering.
Other systems integrate hardware elements
;~ for control of functions of locking systems within the
lock assembly itself, typically by housing circuit
~ boards, power supplies, etc. within the door or in a
module attached to the door. This approach also
requires considerable remodelling of the
.
,
~: :
.
`~ ~: : :
~: ,
. ",.,,,.,.. , . . , , . . , , . , . . ., .. ~ ... .. . ... . . .
~6~3~ ~-
-- 2 --
installations to adapt to the ~pecifications of the given
locking systems. There is a need for improved locking systems
which permit retrofitting of locking assemblies of a type
compatible with traditional. installations, thereby
facilitating the conver~ion from traditional ~echanical
locking systems to electronic locks.
The use of innovative techniques for coding locks, such as
for example optical, magnetic, electronic, and other
techniques, offers the possibility of a number of significant
advantages as compared with mechanical bitting. Electronic
coding and the like holds the promise of increased information
content with attendant improvements to system capabilities;
the flexibility of recoding the cylinder or key (or both);
networking with other electronic systems of an installation;
ef~ective new countermeasures against "lock-pic~ing" attempts;
and developments of versatile management systems for hotels
and other institutions. Prior art electronic locking rystems
have just begun to realize some of these advantages, and ~re
hindered by limitations on the loads of infor~at on in chan~e
between key and lock.
U.K. Patent Application GB 2112055A and Australian Patent
Application AU-A-2112588/83 disclose combination
mechanical/electronic lock cylinders includiny a rotorl'
(cylinder plug) and "stator" (cylinder shell)~ The stator
houses a solenoid-actuated locking bolt which is oriented
parallel to the keyway and which has a retainingmember at o~e
end. The retaining member mates with a grooved blocking
member ~ixed to the rotor, the cam groove being pro~iled to
.
~ 2.~3~ ~
-- 3 --
include a "blocking notch" (in 2112055A or "retaining ring"
(in 21588/83) which prevent rotation of the rotor in certain
states of the solenoid.
U.~. Patent Application GB 2155988 A discloses a
mechanical/electronic key in which an electronic ~sembly
(such as a dual-in-line standard package integrated circuit~
is mounted in a casing which serves as the key grip. The
casing is fixed to the key shank and includes a connecting
part for electrical contacts. ~his application does not show
the use of electronically eraseable programmable read-only-
~emory (EEPROM) for strong keying code, nor the mounting of an
IC directly to the key shank.
It is a primary object of the invention to provide an
electronic door locking system type including a self-contained
lock cylinder. A related object is to design a system of this
type which is compatible with pre-existing mechanical lock
installations, facilitating conversion from mechanical to
electronic locks
~ Another object of the invention is to design a reliable
locking system. Such system should avoid failures due to a
variety of physical conditions, such as mechanical stresses,
poor electronic connections, and electrostatic discharges.
Desirably such system should be a purely electronic one,
i.e. not dependent on mechanical bitting or the key to open
the lock cylinder.
~;
......
., ~ , . . . . .
3~3~i
Sti11 another object is to provide the
ability to elec-tronically transfer information from
the key to the cylinder, and from the cylinder to the
key. A related object is to permit recoding of the
cylinder by the key, and vice versa. Such a system
should be versatile in operation, allowing mul~i-
level master keying and a variety of other significant
keying functions.
3~
-- 5
SUMMARY OF THE INVENTION
The invention adapts to an electronic lock
comprising a housing, and a plug supported for rotation
within the housing and having a keyway to receive the
blade of a key which rotates the plug during operation
of the locking apparatus. A locking member is movable
into engagement with the plug to prevent the movement Oc
the plug and the operation of the locking apparatus and
movable out of engagement with the plug to allow the
rotation of the plug and the operation of the lockin~
apparatus. A solenoid having a core coupled to the
locking member moves the locking member into and out of
; engagement with the plug. A permanent magnet is movable
between a first position to receive and hold the
solenoid core to maintain the locking member out of
engagement with the plugr and a second position to
release the solenoid core, and a driving means moves the
magnèt in at least one direction between the first and
second positions.
Consequently, power may be turned off to the
solenoid after retention by the magnet and a battery
source is preserved. According to one feature of the
invention, the driving means comprises a cam which
supports the magnet and is slideabIy movable
transversely to the solenoid core to move the magnet
hetween the first and second positions. The electronic
lock further comprises a second pin slideably supported
and extending into the keyway to intercept the key blade
when the key blade is inserted in the keyway. The cam
includes a bearing surface aligned with the second pin
;~ such that as the key biade is lnserted into the keyway,
- . ~
6 --
the second pin is driven out of the keyway and against
the bearing surface of the cam, and the came is driven
transversely from the second position to the first
position. The magnet is offset radially away from the
~ 5 solenoid core relative to a blocking surface of said cam
,~ to provide a clearance region to permit the movement of
the solenoid core toward the ~agnet and the withdrawal
of the pin from the cylindrical plug when the magnet is
~: in the first position. The blocking surface prevents
the withdrawal of the solenoid core and maintains the
locking pin in engagement with the locking pin when the
maqnet is in the second position.
srief Description of the Drawings
The above and additional aspects of the invention
are illustrated in the following detailed description of the
preferred embodiment~ which should be taken in conjunction
with the drawings in which:
.
.
'
:: :
~ ~ ,
:
.
3~ii
- 7 --
Figure 1 is a schematic drawing of the electronic locking
system of the invention;
Figure 2 is a sectional view of a lock cylinder in
accordance with the preferred em~odiment, ~aken along the
plane of'a fully inserted key (section 2-2 of Figure 3~;
Figure 3 is plan view of the lock cylinder of
Figure 2;
Figure 4 is a sectional view of the lock cylinder of
Figure 2,.taken along the section 4-4;
Figure 5 is a sectional view of a preferred
electromagnetic actuator, acting as a primary release
mechanism for the locking ~ystem of Figure l;
' Figure 6~ is a sectional view of a secondary release.
: mechanism employing the actuator of Figure 5, taken along the
plane of a fully inserted key;
Figure 6~ is a sectional view of the secondary release
mechanism of Figure 6A, in a section take~ along the lines 6B-
: ~ 6B;
~ ~ Figure 7 is a sectional view o~ an alternative
electromagnetic release mechanism;
.. Figure 8 is a perspective view of a preferred desig~ of an IC-bearing key Por the locking system of Figure 1, showing an
. IC package insert in phantom;
Figure 9 is an expl,oded view of the IC package insert of
~:25 ~ Figure~8;
Figure 10 is a fragmentary view of the key blade of an
a1ternative key design in accordance with the invention;
: ' .
~ .- . .,, ~,... .
3~
-- 8 --
Figure 11 is a diagrammatic view of the integrated circuit
mounting area of the key blade of Figure 10;
Figure 12 is a block schematic diagram of ~lectronic logic
circuitry for the lock cylinder of Figure 1;
Figure 13 is a flow chart schematic diagram of a basic
operating program for the electronic logic of
Figure 12;
Figure 14 is a flow chart schematic diagram of a ~asic
Zone/One Use Subroutlne for the cylinder logic of Figure 20;
Figure 15 is a perspective view of an advantageous design
of key/cylinder recombination console;
Figure 16 is a schematic view of a preferred management
system configuration for the electronic locking system of
Figure 1, embodying the console of Figure 15;
Figure 17 is a sectional view of a release assembly in
accordance with a further embodiment of the invention, in its
locked configuration; and
Yigure 18 iis a sectional view of the release mechanism of
Figure 17, with key inserted and solenoid enabled.
,0 Detailed Descrlption
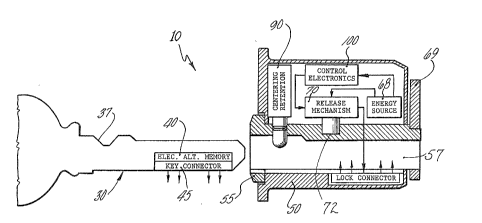
: One should now refer to Figures 1-4 for a general overview
of an electric locking system 10 according to a preferred
embodiment of the invention. Figure 1 shows highly
schematically the principal elements of locking system 10, in
:2~ which a key 30 i5 inserted into mortise lock cylinder 50 to
open the lock. Electronic logic circuitry 100 within cylinder
.
50 recognizes the full Insertion of key 30, and extracts
: ~ .
_"~,, ,. ' .,
6;L~3~;i
g
electronically encoded information from the key memory 40 via
key connectors 45 and cylinder connectors 59. Control
electronics l00 stores and processes keying codes received
from key memory 40 as well as resident cylinder codes. The
logic cir'cuitry l00 can alte{ the codcs i.n key memory 40 based
,~ on data transmitted from cylinder 50, and can alter codes
stored within the cylinder based on data from key memory 400
The processing of access codes from the key and cylinder
by cylinder electronics l00 results in a decision to grant or
deny access. If an "authorized access" decision is made,
release assembly 70 receives a drive signal from control
: electronics l00, causing it to withdraw a radially oriented
locking pin 72 from cylinder plug 55~ A user may then turn
key 30 to rotate cylinder plug 55 as in a mechanical mortise
lock, and rotate a cam (not shown) to release a door locking
mechanism. Although locking system l0 is described in the
- context of a mortlse lock, any compatible mechanical,system
may be employed. Optionally, cylinder 50 also houses a key
~ centering and retention device 90, which interacts with a
2~ single bit 37 or notch in the key to ensure the proper
location of key 30 within keyway 57.
CYLINDER OVERVIEW
Figures 2-4 show in various views a preferred design for
lock cylinder 50, with a fully inserted key 3V. The sectional
~25 view of Figure 2 shows key blade 33 of key 30 inserted in the
keyway 57 of plug 55. Centering/retention pin 92, biased by
spring 94, fits withln a notch 37 along the upper edge of the
:
. . ~ . ,. ~ .. ; ' '
~L~6~3~j;
-- 10 --
key 30. Pin 92 is co~prised of discrete upper and lower
segments 92a, 92b. Pin 92 prevents the withdrawal of key 30
except when in its illustrated, "home" position, at which
point the rear camming surface of notch 37 exerts an upward
force during key withdrawal. When pin 92 is in itC. e~tended
position, the interface 95 between pin segments 92a and 92b is
aligned with the cylinder-plug shear line 55, to permit plug
rotation. With key 30 in its home position, ohmic contacts
45a-45d (Figure 3) abut against cylinder contacts 59a-59d~
which are in thi~ embodiment placed along the lower edge of
key 30 for reasons of spatial economy. (Cf. Fig. 4).
Having reference to both Figures 3 and 4, the
- illustrated, self-contained configuration of lock cylinder 50
includes an upper cavity 52 to house the release assembly 70,
power supply 68r and cylinder electronics lO0. Key
centering/retention assembly 90 is shown housed in a separate
chamber 96. This packaging of components is compatible with
the form factor of a standard U.S. l l/8" mortise cylinder,
thus permitting the retrofitting of electronic cylinders 50 in
conventional lock installations.
As seen in Figure 4, release assembly 70 must fit within a
limited volume. Its pin 72 must have ~equisite size and mass,
and firmly engage cylinder plug 55, to resist the torque of an
attempted forced entry. That portion of cylinder shell 51
2~ housing the locking pin 72 should include adequate bearing
material for the operation of mechanism 70. When release
. " . .. , , . ,, . . , . .. _ .
~3~3~
-- 11 --
A
motor 75 is actuated to allow access, it retract~ pin 72 which
moves clear of the shear line 56 ~Figure 2) to allow plug 55
to rotate.
Power ~upply 68 provides su~fficient peak current and power
, .
to power the release mechanism driver circuitry 130 ~Fig. 12).
lthough a variety of self-generating power sources and
battery technologies may be employed, excellent results have
been obtained using lithium thionyl chloride batteries. In an
alternative embodiment, not illustrated in the drawings, the
cylinder electronics and power supply are packaged externally
to the cylinder in a separate module. This approach allows
more flexibility in packaging the remaining cylinder
components, and facilitates the adaptation of the invention to
a standard l 1/8" mortise cylinder.
RELEASE NECHANISM
:
Figure 5-7 -show various designs for the release mechanism
70, the device which prevents rotation of plug 55 until the
control logic 100 commands it to allow access (permit plug
rotation). Release assembly 70 is designed to translate
~0 limited amounts of electrical energy into the physical force
required to move radially oriented locking pin 72. Figure 5
illustrates an advantageous design 210 for the release
mechanism motor 75 of Figures 2-4. Release actuator 210
includes~a permanent magnet 213 with pole pieces 211, 212,
whose field acts on a bobbinless voice coil 214. Coil 214 is
attached to a two layer disc spring, comprised of a histable
snapover spring 215, and outer, deflection spring 217. 5nap
~ ~3~33~
- 12 _
spring 215 is affixed to the central pole piece 212 at its
center and to voice coil 214 at its perimeter, and locates
voice coil 214 in the center of the gap betwe~n pole pieces
211, 212. Deflection spring 217 is joined to snap ~pring 215
at its periphery, and is firmly a~ixed at its center to
locking pin 218.
In operation, when locking pin 218 is in its outward,
locking position, it is necessary in order to retract the pin
to provide current through coil 214 to generate a field of
opposite polarity to that of permanent magnet 213, of
sufficient strength to overcome the snap action of bistable
spring 215. If pin 218 is free to move, deflection spring 217
~ will pull the pin toward magnet 213. If pin 218 is ja~med,
spring 217 will deflect in order to permit spring 215 to
toggle; when the pin is freed, deflection spring 217 will then
pull pin 218 toward magnet 213.
When current of oppos-ite polarity is applied, coil 214
will move away from magnet 213, and toggle spring 215 will
snap to its outward position. Again, if pin 218 is
constrained, the deflection spring 217 will allow the motion
of coil 214 and apply an outward force on the pin until it is
free to move.
In the preferred application of magnetic actuator 210,
this device is us2d as a "primary release mechanism" -- i.e.
pin 218 serves as the locking pin 72 (Figures 2-4). When key
30 is inserted in keyway 57 and a valid code is recognized by
the lock electronics 100, assembly 210 will apply a retraction
force to pin 72. If the key is applying a torque to the plug
.. . ., , . ~ , .
, . - ,
~2~i3~33~i
55, pin 72 will not move until the torque is removed by
jiggling the key. The pin will then move toward magnet 211
allowing plug 55 to rotate. When the key r.otations have been
completed, key 30 is returned to its home position to be
withdrawn from cylinder 50. A sensor (not shown) detects the
; withdrawal motion of the key, and sends a signal to motor 75
to push the locking pin bark into plug hole 54. Assembly 90
ensures that key 30 can be removed only when pin 72 is aligned
over the plug hole 54.
Xn an alternative embodiment of the invention, illustrated
in Figures 6A and 6B, the magnetic actuator device of Figure 5
is combined with a separate locking pin to achieve ~ release
- mechanism that also provides the key withdrawal alignment
function -- a "secondary" release assembly. Figure 6A shows
release assembly 230 in its unlocked configuration, seen along
the plane of fully inserted key blade 33~. The separate
locking pin assembly 231 includes a blocking pin 234, locking
pin 233 and compression spring 232; pins 233 and 234 meet at
an indented interface 238, while locking pin 233 includes a
circumferential groove 239. As seen in the transverse
sectional view of Figure 69, the release mechanism
incorporates a magnetic motor 237 such as that of Figure 5,
which reciprocates a sear tongue 236.
Before a key 30' is inserted locking pin assembly 231 is
held in an upward position by the insertion of sear tongue 236
into groove 239, as shown in Figure 6B. Upon an nallow
access" decision by the key electronics after the full
insertion o an authorized key ~Fig. 6A), motor 237 is
.. . .
3~
- 14 -
activated pulling sear tongue 236 free of the locking pin 233.
Drive spring 232 pushes the pins 233, 234 downwardly until the
locking pin 233 seats in cylinder plug 55 against the notch
37~ in key blade 33'. At this position, the interface 238
between pins 233 and 234 lines up with shear line 56 allowing
the plug 55 to rot~ate. While pin assembly 231 i~ extended,
the mating between locking pin 233 and key notch 37' prevents
key 30' from being withdrawn. If plug 55 is properly aligned
with key 30~ in its home position, the key can be re~oved
urging pin assembly 233 upwardly due to the key~s ramp
profile. During key withdrawal, motor 237 is actuated in the
; opposite polarity to push sear tongue 2~6 against pin assembly
~ 231. When key blade 33' pushes pins 233, 234 to the proper
height, sear tongue 236 enters groove 239 preventing further
movement.
he blocking pin 234 abuts against the
cylinder shell to prevent the forcing of pin ~assembly 231
upwardly beyond the shear line. Pin 235 resists t~mpering
with pin assembly 231 using a drill or like device.
Figure 7 illustrates a further electromagnetic release
mechanism 250. This assembly is designed to protect against
manipulation using an external magnetic field, as well as
against forced entry by vibration, using a sharp impact
~ against the lock cylinder housing, etc. Furthermore, assembly
25~ 250 requires very little energy in operation, thereby
prolonging the intervals between battery replacement6.
. ~ . . .
i3(~3~;
- 15 -
As seen in Figure 7, release assembly 250 consists of two
locking pins 251 and 262, solenoids 252 and 255, permanent
magnets 253 and 257, flat spring (clock spring) 258, spring
loaded pin 261 (comprised of parts 261a, 261b), a winding 256
on the lower locking pin 262, and a spring 254. When spring
loaded pin 261b has fully engaged cylinder plug 55, it is
mechanically constrained in its locked position by spring 259,
which is coupled to pin 261b. Clock spring 258 constrains
locking pin 251 in its locked position. Upon insertion of a
properly bitted key, spring loaded pin 261b is ramped up,
thereby aligning the gap 263 between pins 261a, 261b with the
shear line 56. This urges clock spring 258 upwardly and
removes the mechanical restraint on locking pin 251, which is
now free to move up to its unlocked position. If the cylinder
logic recognizes a valid key, solenoid 252 is energized,
pulling locking pin 251 against permanent magnet 253. Plug 55
is thereby unlocked and free to rotate. Upon removal of key
30 from the keyway, spring loaded pin 261 returns to its fully
depressed position, blocking the shear line 56 and unloading
flat spring 258. Spring 258 in turn pushes locking pin 251
into a locked position.
A second, coaxial solenoid-actuated locking pin 262 is
incorporated into release assembly 250 to protect against
unauthorized opening of the lock while using a key blank to
~5 ramp up the spring loaded pin 261. If an external force is
applied to the locking cylinder envelope to attempt to move
~ ,
...
- 16 ~
locking pin 251 up against permanent magnet 253, lower locking
pin 262 will simultaneously move upward uncler the action of
spring 254. Pin 262 will thereby move against permanent
magnet 257 into its locked position and prevent rotation of
plug 55. Upon subsequent insertion of a valid key, a slight
momentary current through solenoid winding 255 induces a
voltage differential in the output terminals in winding 2560
The resulting voltage differential will be processed by the
cylinder electronics 100 to energize solenoid 255, pulling
locking pin 262 back and allowing plug 55 to rotate freely.
Solenoid 255 is thus energized only in the event that locking
pin 262 has been moved upwardly into its locked position,
thereby changing the relative position of windings 255 and
256.
n alternative version of the solenoid release assembly of
Figure 7 omits the lower locking assembly and replaces the
conventional solenoid 252 and permanent magnet 253 with a
bistable solenoid assembly. Such bistable solenoid assembly
will exhibit a toggle characteristic when energized; in either
of its two positions, it will be much less susceptible to
external magnetic fields, sharp impacts to the lock envelope,
etc.
In the release assembly of Figure 7 the flat spring 258
and spring loaded pin 261 serve as a bistate mechanical
assembly which acts in cooperation with the solenoid-locking
pin components. Such assembly mechanically restrains the
locking pi~ in its locked pQSition when the release ~echanism
i~ in its locked configuration; is moved to a second state by
3~3~ii
- 17 -
the key during insertion of the latter, thereby pro-
viding a clearance regio~ for the locking pin so that
the la-tter may be moved to its unlocked position by
the solenoid; and upon removal o~ the key reverts to
its first configuration due to a mechanical bias,
thereby forcing locking pin 251 in-to its locked
position.
Figures 17 and 18 illustrate a further release
assembly 470 incorporating a bistable mechanical
assembly having the functional characteristics dis-
cussed above Release assembly 470 includes a solenoid
485 which is radially aligned relative to the keyway,
the solenoid plunger being coupled to locking pin 485
which when e~tended prevents rotation o~ the cylinder
plug 50. When release assembly 470 is in its locked
; configuration, locking pin 485 is restrained in its
extended position by cam member 475, and a further
pin 471 is also held down by plug 471. Absent a
countervailing force the plug is biased in this
position by compression spring 474. Upon insertion
of a key 43~, the pin 471 is ramped up until it rests
against the key ledge 435, at which point the pin in-
dention 472 is aligned with the shear line 56; ~in
471 displaces plug 475 via ramp surface 476, providing
: 25 a:clearance region 478 for the end 477 of locking pin
: 485. At this point, if solenoid 480 is actuated the
~, locking pin 485 can retract from cylinder plug.50;,
magnet 479 latches the pin 485 in this retracted
position so that the solenoid need not be constantly
powered or pulsed to maintain this configuration~ Upon
~removal of the key, compression spring 475 drives plug
475 to its original position, thereby camming down
locking pin 4~85 and pin 471.
.... , ~ .
" ,
In the embodiment of Figures 17 and 18,
; centering/retention assembly 90 has like structures and
functions to that of Figures 2-4.
KEY WIT~ IC
. .
Figures 8-11 illustrate various constructions of the key
30. A suitable design for k~y 30, shown in Figure 9, is quite
similar to that of a conventional mechanical key. The lower
edge 34 of the key has no bitting, and has a rectangular slot
or cavity 35, which houses integrated circuit package 42
(shown in phantom) and key contacts 45. Contacts 45 are
located flush with the lower key edge 34.
The embodiment of Figures 8 and 9 utilizes a surface
mounting technique, wherein the integrated circuit 41 is
mounting in a compact surface mount package 42 having adequate
size and pin outs for the electrically alterable ICs 41 within
each package. Surface mount package 42 is retained within a
rectangular insert 141, shown in phantom in Figure 8, which is
closely fitted within a complementary cavity in the bottom
edge 34 of key 30. The IC package 42 electrically
J communicates with a set of ~our contacts 45a-45d which are
mounted~flush with the outer wall of insert 141 as well as
within key edge 34. Figure 9 shows in an expladed view the
various elements of the IC package insert 141 (only two
contacts 45 are shown). The surface mount package 42
3~35
-- 19 -- ,
comprises a standa{d S08 dual in-line package, including 8
pin-outs 96. Appropriately shaped contacts 45 are embedded in
insert 141 and include flange portions 45a-f, 45b-f, etc.
which fit within apertures 145 in rectangular insert 141, to
provide flush contacts. In an operative embodiment of
surface-mounted IC package 42, mounting insert 141 was a
filled nylon substrate in accordance with Figure 9, with four
imbedded noble metal alloy contacts 45a-45d. Insert 141 was
press fitted into a rectangular slot cut in the bottom edge 34
lO of key 30.
he alternative IC mounting embodiment of Figure 10 and 11
uses a "chip and wire" mounting technïque. The integrated
circuit die 41 is inserted into a cavity 161 which was milled
or coined into one face of key 160. Cavity 161 has previously
15 had a layer of insulating ceramic fired on to create a
dielectric layer over the metal body of the key. The
integrated circuit's pads 41p were electrically coupled by
,conductors 163 to key contacts 165 using well known porcelain-
aver-metal thick film hybrid techniques. Contacts 165a-d
20 comprised noble metal alloy clips which were clipped or bonded
to conductors 163, and anchored at an indented region af the
opposite face of key 160. Contacts 165 were electrically
isolated from the metallic body of key 160 by plate or potting
164, and all required components were encapsulated with a
25 conventional potting material to hermetically seal the
integrated circuit 41.
. ..
~3~3~
-
-- 20
OHMIC CONTACTS
In all of the embodiments of Figures 8-11 ICs 41 are
electrically connected to a set of ohmic key contacts 45.
Advantageously, contacts 45 are composed of a hard noble metal
alloy which allo~ adequate contact pressure to force contact
through dirt or film by a wiping action, and which withstands
corrosion under typical environmental conditions. Excellent
; results have observed with Paliney noble metal alloys (Paliney
is a registered trademark of J.M. NEY Company). In a
~o particular embodiment of the invention, key contacts 45 were
formulated of Paliney 8 alloy (comprising palladium, silver,
and copper) and cylinder contacts S9 of Paliney 7 alloy
(comprising the above elements plus gold and platinum).
With furthe~ reference to Figures 2-4, cylinder contacts
S9a-59d provide firm, reliable ohmic contact with the
respective contacts 45a-45d of a fully inserted key 30. As
best seen in Figure 4, contacts S9 are cantilevered members
mounted to a contact holder 61 at one side of cylinder plug
55, with dished tips pressed firmly against the contacts 45 in
key 30.
Advantageously, locking system 10 relies on a suitable
protocol for data communication between key memory 40 and
cylinder logic 100, to ensure accurate data transmission over
noisy paths (ohmic contacts 45, 59). Such protocol includes
redundant, error-detectio~ data bits in all transmissions.
The data receiver, whether key or cylinder, compares the
~; transmitted access code bits and the error-detecting bits to
see that these match. A number of well known encoding methods
, ~ , .. .
~63~3~
- 21 -
allow the detection of errors as well as the correction of
simpler errors. Such technique enables error-free data
transmission in the face of intermittent contact problems due
to dirt, films, premature key withdrawal, and the like.
Defective transmissions can be recognized and often re
attempted. Significantly, such encoding techniques allow the
key or cylinder to avoid writing erroneous data, or writing
data to the incorrect location. Preferably, this protocol is
implemented both in the cylinder control logic 100 and in I/O
circuitry within the electronically alterable memory 40 in key
30.
ELECTRONICALLY ALTERABLE KEY MEMORY
Electronically alterable key memory 40 has the ability to
store a substantial number of access codes, each of which will
have a much larger range of possible values then found in
traditional mechanical locks. This non-volatile integrated
circuit technology involves memory which may be ~ead like
traditional read-only-memory (ROM), and may ~e written to
after being electronically erased. Such memory devices are
commonly known as EEPROM integrated circuits~ EEPROM i$ a
medium density memory, which retains adequate key memory
within devices on the order o-f 2-3mm micron geometry. To
store data in such devices, the word must be erased and then
written. Typical erase/write cycles ~E/W) are on the order of
20 milliseconds, and require less than 15 milliamperes.
~ 22 -
Although a variety of EEPROM process technologies are
available, it is desirable to utili~e a type which achieves
high reliability over an extended service life. Various SNOS
(Silicon Nitride Oxide Silicon) and CMOS (Complementary Metal
Oxide Semiconductors) process technologies have been developed
for the design and production of EEPROM devices of suitable
characteristics for key memory 40 and cylinder memory 180
(Figure 1). EEPROM cells have a normal life expectancy of
10,000 E/W cycles, after which there will be an increased risk
of catastrophic failure. For SNOS process technologies, these
failure parameters are related in that data written to a given
memory cell on the 10,000th erase/write cycle will be retained
for at least ten years, and subsequent erase/write cycles to
the same cell will be retained for a somewhat shorter period.
It is important to include in key memory 40 on-board
input/output protection against electrostatic discharge (ESD)
attac~. I/O protection circuits for integrated circuits are
well known to persons of ordinary skill in the art. Such
; protection is critical to the reliability of locking systems
~20~ according to the present lnvention.
3,~CI~ONICS
Figure l2 is a block schematic diagram of cylinder control
; ~ ~ loglc 100, which supervises the various electronic functions
~; o~ lock cylinder 50. Control logic 100 is a microprocessor
based system including central processing unit (CPU) 105 as
its central element. Other major components of cylinder loglc
, :
. . ~ . , , .~ .
, .~ . .
3~3
- 23 -
100 are key serial interface 110, which provide~ ~ynchronous
~erial communications of access code data to and from the key
EEPROM 40; timing circuitry 120, which provider various timing
signals for cylinder logic 100; Rey Sensing circuitry as~embly
150, which produces signals indicative of the full insertion
of key 30 in keyway 57, and of the withdrawal of the key;
Po~er Control circuitry 140, which regulates the delivery of
power from battery 68 to the various elements of cylinder
logic 100; and.Release Driver 130, which outputs actuating
signals to the release assembly 70 in response to an
appropriate command from CPU 105. Optionally, timing
circuitry 120 incorporates a real time clock (not shown) to
provide real time control over the keying system, as further
di~cussed below. Key serial interface 110 includes
appropriate input protection circuitry, which together with
control of the capacitive coupling of the logic elements to
the cylinder body 50, protects the cylinder electronics 100
; ` from catastrophic high voltage attack due to electrostatic
discharge f ESD). Although a variety of key sensors may be
suitabl~ employed in combination with sensing logic 150, it is
preferred to sense the change in resistance between two
normally open cylinder contacts 59. This arrangement draws
very little current from power source 68 should key 30 be left
in keyway 57 over an extended period.
2~ Cyli~nder logic 100 also encompasses various types of
: ~ ~ memory, including random access memory ~RAM) 160, read only
memory (ROM) 170, and electronically alterable memory (EEPROM)
: 180. RAM 160 receives data from key interface 110 and permits
~6~3~
- ~4 -
high speed processing of this data by CPU 105. ROM 170 ~tores
the firmware for the cylinder control logic; certain routines
are explained below in the discussion of the lock'~ keying
system. EEPROM 180 comprises nonvolatile memory for the
access codes resident in cylinder 50, and may take the form of
any of a number of energy-efficient commercially-available
devices.
A significant design characteristic of control logic 100
is its low power consumption. Under the supervision of Power
Control assembly 140, the control logic 100 undergoes various
states of power distribution to the various subassemblies.
Until ~ey Sensing logic 150 signals the full insertion of key
30, this assembly 150 is the only one which receives pawer.
When a key is recognized as present, sensing logic 150 directs
power to CPU 105 and other components involved in the decision
to permit or deny access. When this decision has been made,
Power Control assembly 190 turns off all but the Release
Driver 130 (if required) and the Key Sensing logic 150 (which
is on at all times). Low Battery assembly 145 detects a low
power state of battery 68 and may provide an external
indication (as by lighting an LED) as well as a signal to CPU
105.
In one embodiment of the invention, timin~ assembly 120
includes a real time clock to provide a time-of-day signal --
i.e., a resolution of some number of minutes. Illustratively,
;~ this clock takes the form of a dedicated clock IC. The energy
source 68 (Fig. 1) is designed to provide continuous input
power to this clock IC. The inclusion of a time of day clock
,,~, , - , . . . j .
3~
- 25 -
significantly affects the access code memory ~tructure, and
keying system firmware, as discussed below.
The preferred construction of cylinder electronics 100
utilizes thick film hybrid technology, including a single
board cylinder controller which houses the CPU 105~ ~AM 160r
RQM 170, and various other elements largely expressed in
"standard cell logic". This circuit comprises a miniature
ceramics substrate, with either small surface mount IC
packages, or chip-in wire mountings. Certain high voltage or
higher powered components are preferably built of discrete
components, such as discrete transistors which switch the high
current pulses produced by the Release Driver 130.
Figure 13 is a high-level flowchart schematic diagram of
the basic operating program 850 for cylinder logic 100, which
is resident in ROM 170 (Figure 12). At 851 the ~ey Sensing
assembly 150 detects the valid insertion of a key, causing
Power control 140 to provide power to CPU 105 and key 30, at
853. At 854, the logic selects a suitable communication
protocol for Key Serial I/O 110 (Figure 12); different
protocols would typically be required for normal key 30 and
for the cylinder recombinating device 355 (shown in Figure 15,
and discussed below at "Management System"). At 856 the ~ey
Serial I/O reads data from the key memory 40 into RAM 160.
s further explained below under "Keying System", the key
2~ and cylinder memories are structured in the preferred
embodiment in a pl~rality of keying functions Fl, F2. . .FN.
3~i
26
In the illustrated program data is read from the key at 8~6 on
a function by-function basis. At the case ~lock co~pri~ed of
step 858 and steps 859. . .861, 862, and 864 the program
selects the appropriate function subprogram stored in ROM 170
and interprets the just-read key codes. Depending on the
nature of the particular subprogram, this interpretation
process may result in an "authorize access" decision; may
yield data which is intended to be delivered to the key or
key-like device (such as for reco~binating a key 30 or for
providing information about cylinder 50 to a clerk console
350); and may result in commands to recode the cylinder memory
180. Cylinder recoding, if required, advantageously takes
place at this stage. At 86~, the CPU tests the key data in
RAM 160 to determine whether an "end of data" flag is present,
while at 864 the redundant check codes in the key data are
analyzed to confirm that valid key data had been received. A
failure of the latter test causes the re-reading of the
invalid key data.
At 865 any output codes resulting from the prior
~20 processing of the key codes are written to the key or key-like
device (e.g., to change one or more function codes of a key
30). At 866 the CPU determines whether the function
processing had resulted in an "authorize access" state, and if
such state is present actuates the Release Drlver 130 to open
~25 the lock. In the ab6ence of an "authoriæe access" flag the
system enters a "time out" state at 867, wherein the timing
logic 120 cloc~s a predetermined time interval during whioh
the ~ey Sen6ing logic 150 is not permitted to output a valid
~3~3~;i
- 27 -
TABLE 1
DOOR UNIT MEMORY MAP
. ..... _ .
DOOR UNIT ID
PROGRAMMING CODE
FIXED FORMAT -~1ESSAGE STORAGE
STATUS
_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _
FUNCTION
YARIABLE
- FORMAT
. STORAGE
. . .. _ .. _ . _
: : '
lABLE 2
` I ZONE FUNCTION
MEMORY MAP
. . .
~ .... . _ l
NUMBER OF RECORDS ~ r---- _
: C03E COMBINATION Sl S2 S3 S4 S5
CODE COHBINATION _ Sl S2 S3 S4 S5
: : CODE COMBINATION Sl S2 S3 S4 S5
::: : : ____ _.____ _ .__ _ ___
: CODE COMBINATION Sl S2 ! S3 54 S5
~ _ _ _ ....... .
:: ~ :
: :
F679
93~
- 28 -
key insertion signal. Time out step 867 limits the frequency
with which an unauthorized u~er can feed a large number of
random codes to the logic 100 using a key-like device. The
time out state may be effected after a prescribed number of
key insertions. At ~69 the Power Control assembly 140 turns
off the supply of power to CPU 105 and Release Driver 130.
P.CCESS CODE MEMORY STRUCTURE
Table 1 shows an advantageous memory map for access codes
contained within the cylinder or door unit EEPROM 180 (Figure
12). This memory map schematically illustrates the logical
addressing scheme of the lock's control program to
sequentially retrieve data from memory cells within EEPROM
180, but does not necessarily depict the physical layout of
such memory cells. Memory 180 includes various fixed format
fields -- fields with a predetermined number of assigned data
bits, and a variable format portion for function storage.
Fixed format fields includes a "door unit identificationn -- a
serial number that identifies the particular cylinder 50, but
has no security function; and the "programming code", a
securlty code which must be transmitted to cylinder logic
100 in order to allow modificatlon of memory 180, as dis-
cussed below under MANAGEMENT SYSTEM; Other fixed format
fields not shown in Table l may be included depending on
the requirements of the door unit firmware. The function
storage flelds contain the data associated with the
particular keying system functions
~L~$303~
- 29 -
programmed into Cylinder Access Code Memory 180; this is
illustrated above in Tables 2 and 3.
Illustratively, key memory 40 is structured similarly to
the cylinder code map of Table 1, but omits the Programming
Code field.
Table 2 illustrates the record structure of a particular
keying system feature -- i.e. the zone function. In its basic
embodiment, the Zone function implements a comparison of each
of a set of key zone codes with each of a set of cylinder zone
codes, and permîts access if any match occurs. The header
byte of this memory map gives the number of zone function
records (here four). Together with preknowledge of the memory
gccu~ied by the records of each function, the header byte
.. . . .
enables the addressing routine to scan through logical memory
l~ to locate the next function within Function Storage
(Table 1). In each record, the code combination represents
the code which must be ~atched to initiate the corresponding
function. The status bits S1-S5 are associated with
specialized Zone features, so that the setting of a particular
use bit (at most one is set) identifies the code combination
with that feature. For example, S1 might be associated with
"one use" - which allows keys to be issued for one time use
only; and S2 might be identified with "electronic lockout" -
pèrmits a ~pecial lockout key to prevent access by normal
keys, until the lockout key is reused. If no status bit S1-S5
is set, the code combination will be a Basic ~one code,
discussed above.
.. . . . . . . .. . .
.. ,~ .............. .. .
. .
3~
- 3~ -
; In the key memory 40 and cylinder memory 180, access codes
~:~ are assigned a given code width ~number of binary digits per
code) which determines by inverse relationship the total
number of available codes in EEPROM. ~ighler code widths will
decrease processing speed, but increase the resistance of the
: system to fraudulent access attempts by means of random codes
electrically fed to the lock; in addition higher-width codes
are less likely to be inadvertently duplicated in system
management. sy decreasing the total number of available
codes, however, the one of higher width codes decreases the
number of available keying system features for a given amount
of memory. In the preferred design of cylinder logic 100
(Figure 20), Power Control 140 is controlled by Central
Processor 105 and Timing Assembly 120 to provide a "time out"
period after the sequential presentation of a certain number
of unauthorized key codes, as discussed above with reference
to Figure 13.
KEYING SYSTEM
.
Tables 3 and 4 give simplified record structures for
: 20 cylinder and key memory function storage fields for Basic Zone
and One Use functlons, and should be referenced together with
: the flow chart schematic diagram of Fiyure 14 to illustrate
the relationship between the access code memory structures and
the associated keying system software routines in RO~ 170.
:
"'`'"' ' .,
3~3~;
-
31
TABLE 3
,
SIMPLIFIED MEMORY MAPDOOR ZONE FUNCTION
. .. I
NU BER OF RECORDS I
CODE COMBINATION S1
. ..._ ...
CODE COMBINATION_ S1_
CODE COM31NATION _ S1
TABLE 4
SIMPEIFIED:MEMORY MAP
KEY ZONE FUNCTION
NUMBER OF RECORDS ¦
CODE COMBINATION
. . . .. _
CODE COMBINATION
_
: CODE COMBINATION
.~_ _
CODE COMBINATION
CODE COMBINATION
: ::
;
~:
F679
- . ~ .
26;~335
- 32 -
The door unit or cylinder record structure includes three Zone
records with associated "one use" ~tatus bits S1 ~Table 3),
while the key memory structure contains five Zone records but
no associated status or use bits ~Table 4).
In the basic system program of Figure 13, as part of the
"select functions" case block, the control Eirmware would
include various subroutines associated with particular keying
system features, including the "Basic Zone/One Use Subroutine"
of Figure 14. This routine includes nested loops wherein key
pointer I ~e.g. pointing to a particular record or row of
Table 4) and cylinder pointer J (e.g. pointing to a given
cylinder zone record - cf. Table 3) are each incremented from
1 to the respective "Number of Records" value. For each pair
of values I, J, this routine compares the "code combination't
for the relevant cylinder and key zone records at step 335.
If a match is found the program determines at 33~ whether the
CYL.S1 flag for the rele~ant record J is set. If this "one
use" flag is not set, the routine simply returns a "grant
accessi' decision at 341. If the flag i5 set, however, the
routine first updates CYLCODE (J) with a pseudorandom number
generated by the management system; this prevents a repeated
use of the key to open the same lock cylinder.
Were the Zone Function data structure to take the mare
complicated form shown in Table 2, the subroutine of Figure 14
would be modified to determine whether any of the other status
or use bits 52-S5 were set, and to include appropriate
algorithms to implement these additional keying system
~eatures.
. . .
_ 33 -
~he locking system of the invention can achieve all of the
traditional keying system features found i~ mechanical mortice
cylinders (e.g., great grand master keying, cro~s keying,
etc.), as well as additional, useful functions. Furthermore,
the cylinder access code memory 180 can include updating key
codes, which may be written to the key memory 41 in
implementing certain keying system functions. Specialized
keying system functions may be designed to control
unauthorized copying of key codes, and in general to
selectively update the key memory 40 for enhanced flexibility
together with security.
In the embodiment in which the cylinder electronics 100
includes a real time clock, the keying system can be extended
to inclu~e time-of-day control. Time-of-day can be associated
with each keying function. For Basic Zone/Single Use, a time
can be associated with each door unit zone ~i.e., set of lock
cylinders containing a common zone code). The key system
functions could be modified to include one or more time access
windows, to include automatic cylindsr recording at a given
time of day, and other features. The cylinder memory
structure must be supplemented with time-of-day codes, i.e.
one byte for each significant time-of-day. With reference to
the Management System discussion below, the key/initialization
console 350, and central controller 360~ must have the ability
to keep time-of-day in such a system.
.
~L~f.3~5
- 3'~ -
~ y including a calendar timing device on the Timing
Assembly 120 (Figure 13), the principles disoussed above can
be applied to keying system features tied to particular days,
weeks, etc.
MANAGEMENT SYSTEM
The electronic locking systems of the invention may be
incorporated in "hard-wired" electronic lock installations,
which utiliæe a communication network linking the various lock
cylinders, and a central management system processor. In the
preferred embodiment of the invention, however, the lock
cylinder 50 comprises a stand-alone system, with no hard-wired
communication. The EEPROM elements 41 within each key 30
serve as a substitute for a direct communication link with a
central controller, inasmuch as the key can be encoded at a
remote station to transmit codes to lock cylinder 50. Xey 30
~ can be encoded with special codes which are recognized by
cylinder access code memory 18C. As shown in Figure 16, the
management system advantageously includes one or more
key/cylinder consoles 350, which may take the form for example
; 20 of a portable microcomputer with specialized input/output
devices. Key receptacle 352 accepts insertion of a key 30,
and links the inserted key to internal loqic circuity for
initializing or recoding a key. Cylinder recombinating device
355 includes a key blade 356 similar to a normal key blade 33
~Figure 8), and a plug 357 which mates with an outlet (not
shown) at the rear of console 350. The cylinder recombinating
device 355 contains EEPROM memory essentially identical to the
3;~
35 -
key memory 40, and may be used by authorized operators to
carry a new program from the console 350 to a given cylinder
as required by the management system.
The management system is advantageously adapted to the
requirements of institutional users such as hotels and
universities. The system might
include a plurality of "clerk consoles'` 350a-d in accordance
with the device of Figure 16, which communicate with a central
controller 360. Controller 360 acts as the central repository
o~ the management system data base for the entire
installation, and downloads data into the various consoles
350a-d. Consol'es 350a-d encode keys as required by the keying
system data base, and records to whom they are issued. A
given console 350 can interrogate the central controller 360
to inspect the central database; sensitive information can be
protected by features such as passwords. This preferred
management system may be characterized as a distributed
processing system, with all real time processing effected at
individual lock cylinders 50.
Whlle reference has been made above to specific
embodiments, it will be apparent to those skilled in the art
that various modifications and alterations may be made thereto
without departing from the spirit of the present invention.
Therefore, it is intended that the scope of this invent1on be
~scer~ained by reference to the following claims.