Note: Descriptions are shown in the official language in which they were submitted.
~1 26~L3~
POSTAGE AND MAI~ING r~FoRMA~Io-N APPLYING SYSTE~
Backaround of the Invention
Since the issuance of ~.S. Patent No. 1,530,852 to
Arthur ~. Pitney, March 24, 1925, the postage meter has had
a steady evolution. Po~tage meters are mass produced
devices for printing a defined unit value for governmental
or private carrier delivery of parcel~ and envelopes. The
term postage meter also includes other like devices which
provide unit value printing such as a tax stamp meter.
lo Postage meters include internal accounting devices which
account for postage value, which postage value is stored
~;~6~34~
2--
within the meter. The accounting device accounts for both
the recharging of the meter with additional postage value
and the printing of postage by the meter printing mechanism.
No external independent accounting system is available for
accounting for the postage printed by the meter.
Accordingly, postage meters must possess high reliability to
avoid the loss of user or governmental funds.
Throughout the years, two general types of postage
meters have been used: one that uses a r~tatable print drum
and is referred to as a rotary postage meter, and the other
that uses a stationary print head and a reciprocating platen
and is referred to as a flat bed postage meter. Most
recently, there has been a change from a completely
mechanical device to meters that incorporate electronic
components extensively. Although there have been a number
of changes, there are certain elements that remain constant.
For example, the need for security is absolute. In prior
postage meters, such security is applied both to the
printing portion of the meter and to the accounting portion.
The reason for the absolute security requirement is because
a postage meter is printing value, and unless security
measures are taken, one would be able to print unauthorized
postage, thereby defrauding the U.S. Postal Service. Most
security measures taken are of a physical nature, but
recently there have been suggestions for the use of
encryption to ensure that a postage indicia is valid.
Nevertheless, such encryption merely supplements the
physical security systems that have been used and suggested
by the prior art. Furthermore, the known prior encryption
systems attest to the validity of the indicia but provide no
means for determining whether the printed indicia is just a
copy of a valid indicia. Additionally, prior systems relied
upon the post office accounting for postage by monitoring
the number and value of mail pieces sent by a particular
meter user.
Another common factor in prior postage systems is the
inclusion of a postage indicia normally placed in the upper
right hand corner of one surface of an envelope or package.
This indicia has taken a specific form. The postage amount
~2643~1
is contained in a rectangular border and the date of the
postage impression appears in a circular border. This form
has evolved from the original appearance of a canceled stamp
wherein the stamp is of a rectangular configuration and the
cancellation mark included the date within a circle. Also
included in this indicia is the postage meter number and the
city and state from which the enve~ope was mailed.
Although postage meters have performed satisfactorily
in the past and continue to perform satisfactorily, with the
advance of electronics, postage systems are needed that are
less expensive and more flexible while still providing the
serviceability and security required. Additionally, it
would be desirable to have a postage system that is more
compatible with contemporary mail processing systems.
Summary of the Invention
Encryption is utilized to prevent fraudulent postage
taking. An encryption message is derived from postage
information and/or recipient address information and applied
to a mail piece. With the inclusion of recipient address
information in the encryption message, there is a
relationship between authentication and the mail piece that
is unique for each mail piece. In accordance with one
aspect of the instant invention, the postage information and
encryption are placed in the address field of the mail piece
along with address information. With the encryption in the
address field, authentication can be made on the fly by an
automatic mail scanning/sorting machine quickly and
efficiently.
~264341
3A
various aspects of this invention are as
follows:
A system for providing self authentication of
a mail piece, comprising:
encryption means operative to derive an
encryption message based upon postage information and
address information,
means for communicating recipient address
information to said encryption means,
means for communicating postage information to
said encryption means, and
means for placing onto a mail piece an
encryption message generated by said encryption means.
A system for providing self authentication on
mail piece, comprising:
encryption means operative to derive an
encrypted message based upon address information,
means for communicating recipient address
information to said encryption means, and
means for placing onto a mail piece an
encrypted message derived from said address information
by~said encryption means.
Brief Description of the Drawinqs
Fig. 1 shows a block diagram of a system that
utilizes the instant invention:
Fig. 2 is a plan view of an envelope having
postage information printed thereon in the address field
in accordance with the instant invention;
Fig. 3a is a view similar to Fig. 2 but with
bar codes instead of alpha-numerics in a portion of the
address field;
~6A3~11
--4--
Fig. 3b is a view similar to Fig. 3a but showing a
different format;
Fig. ~ is a block diagram of a mail scanning/sorting
machine that would have application in the instant
invention; and
Fig. 5 is a flow chart showing cooperation between two
components shown in Fig. 2.
Detailed Description of the Preferred Embodiment
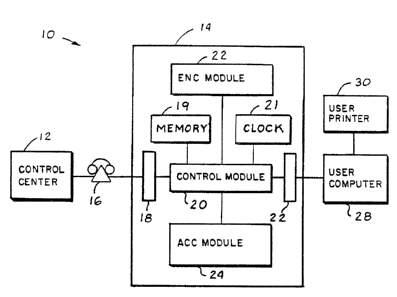
Referring initially to Fig. 1, a postage and mailing
information applying system is shown generally at 10 and
includes a control center 12 and an accounting unit 14 that
are in communication with one another through a
communicating device such as a telephone 16, facsimile
machine, telex machine, and the like.
Located within the accounting unit 14 is a modem or
converter 18 which provides communication between the
telephone 16 and a control module 20 of the accounting unit,
which control module may be a CPU such as an Intel 8085
microprocessor available from Intel Corporation, Santa
Clara, California. The control module 20 has a memory 19
and a clock 21 either integral or in connection therewith.
The memory 19 would store the transaction number, i.e., a
number assigned to the accounting unit of the occasion of
clarifying postage to the system 10, the customer number and
the like. In communication with the control module 20 is an
encryption module 22 as well as an accounting module 24.
The encryption module would be any of a readily available
encryption device which may, for example, encrypt in
accordance with the NBS Data Encryption Standard (DES)
pursuant to a preset secure key. An example of a suitable
encryption module 22 would be an Intel 8294 encryptor. The
accounting module 24 may be a battery augmented RAM that
incorporates the ascending and descending registers. As is
known from previous postage metering devices, the ascending
register is the register that records the amount of postage
that is dispensed or printed on each transaction and the
descending register is the register that records the value,
or amount, of postage that may be dispensed and decreases
~Z~434~
--5--
from an original or charged amount as postage is printed.
Another modem 26 within the accounting unit 14 provides
communication between the control module 20 and a user
computer 28. The user computer may be any typical computer
that has input, logic and output for example, a personal
computer such as the IsM AT available from I8M Corp.,
Armonk, N.Y. Connected to the user computer 28 is a user
printer 30. Although the user printer may be of any type
that is capable of printing individual alpha-numerics, a dot
matrix printer is preferable since a dot matrix printer is
capable of printing any configuration including bar codes.
In the block diagram shown in Fig. 1, the control
center 12 may be a Post Office which serves as a source of
postage value. Systems are known whereby a postage meter
may be charged remotely upon a user providing his assigned
customer number to the Post Office, see for example U.S.
Pat. No. 4,097,923. The Post Office, in turn, will provide
postage value that is automatically inpu~ to the customer's
postage meter, in this case the accounting unit 14. The
postage value will be received within the descending
register portion of the accounting module 24 to increase the
amount to a figure that is the sum of that amount being
charged and the unused amount from previous charging. In
the system of Fig. 1, the secure portion of the postage
meter is replaced by the accounting unit 14 that is a secure
unit such that tampering by physical, electronic or magnetic
means is inhibited. Security features such as shields,
break away bolts and the like are well known and the means
for securing the accounting unit 14 will not be further
described. In a preferred embodiment, the accounting unit
14 would have no display and would only be accessible by the
user computer 28 upon an assigned code word being received
by the control module 20 of this accounting unit 14 from the
user computer. It will be understood that the user printer
30 is not a secure printer nor are the links between the
user computer 28 and the accounting unit 14 and the user
computer and the user printer. The postage information to
be printed by the user printer 30 would include an
encryption number that is generated by the encryption module
6434
--6--
22. Encryption may be based upon any recognized code such
as DES, supra, National Security Agency (NSA) cipher or
Rivest, Shamir and Adleman (RSA) cipher. Upon the
appropriate information being supplied to the accounting
unit 14 from the user computer 28, the encryption module 22
would generate an encryption number which would then be
communicated through the user computer 28 and printed by the
user printer 30. This supplied information could include,
the customer number, the value of postage and the like. In
a particular embodiment of this invention, the street
address, zip code and the like of the recipient is included
in the encryption for the purposes of authentication. As
used in this disclosure, authentication is defined as the
determining of the genuineness of postage printed upon a
mail piece.
Referring now to Fig. 2, a format is shown for applying
postage information and mailing information to the address
field of a mail piece such as an envelope 34. By postage
information is meant postage amountr date of mailing, meter
or customer number, transaction number, class of mail and
the like. By address information is meant the house number,
name, city, state, zip code and the like of the mail
recipient. In this particular configuration, an envelope 34
is shown with a label 36 attached in the address field
portion of the envelope. As used in this specification and
claims, the term address field has the meaning as defined in
U.S. Postal Service regulations. Such definition may be
found in the U.S. Postal Service's pamphlet "Guide to
Business Mail Properties", page 20, September, 1984.
Although this embodiment is described with the combination
of a label 36 and envelope 34, it will be appreciated that
the characters may be printed directly upon the envelope or
upon an insert that would be placed within a window type
envelope. It will be understood that this label 36 replaces
and eliminates the need for the normal indicia that is
applied to the upper right hand corner of a mailpiece. One
of the features of the instant invention is that a standard
indicia is no longer required because the security features
126434~
--7--
provided by such standard indicia are replaced by the
security offered by encryption.
In a preferred embodiment, the first line 38 of the
label would have information relative to the amount of
postage and the customer number. The second line 40
contains the date of the mailing, the time the postage is
imprinted and the class of mail. The third line 42 contains
an encryption message in the form of numbers and letters
that may be derived from the information on the first two
lines as well as information from the address of the
recipient of the mail piece that follows this third line.
As shown, the printed lines are parallel to one another to
facilitate automatic reading. It will be appreciated that
other conventional machine readable configurations may be
used rather than parallel lines.
The postage amount, customer number, date and class of
mail are input through the keyboard of the user computer 28
to the control module 20. The encrypting module 22 then
generates an encryption number or message and upon the print
command being given by the computer operator, the time is
determined and an encrypted message is obtained. This
encryption message 42, is then printed by the user printer
30 on line 3 of the label 36. With this information, a
Postal Service representative would be able to input the
encryption message into a suitable computer and determine
whether the postage is genuine by decrypting the
information.
Although the system has been shown using alpha-numerics
in the address field, it will be appreciated that bar code
may be used to print the first three lines as shown in Fig.
3. This bar code may be of any form including the bar-half
bar configuration used presently by the Postal Service. The
bar codes could be combined in an indicia for aesthetic
purposes and placed within the address field as shown in
Fig. 3b or in the upper right hand corner of the envelope
34. Although the bar code is shown extending parallel to
the alpha-numerics, it will be appreciated that the bar
codes could extend parallel thereto. The bar code also
~Z64~41
--8--
appear on the bottom edge of the envelope as shown at 44 so
as to be read by present Postal Service equipment.
The advantage of the system shown and described is that
one is able to eliminate the standard postage indicia that
has been in practice for decades and still provide the
assurance associated therewith. In addition, by having all
the information in the address field, authentication may be
obtained quickly from information appearing on the envelope.
secause of the presence o~ the recipient's zip code, the
encryption message 42 that appears on the label 36 is unique
for that mail piece. More specifically, there is a
connection between the mail piece and the encryption
message. In prior systems, there was no relationship
between the code or encryption and the mail piece, but
rather a seed number or the like was used in conjunction
with sender information such as the sender's zip code, meter
number, and the like. Present high speed automatic
scanning/sorting machines incorporate OCR readers capable of
reading the information in the address field of an envelope
34 and sorting in accordance therewith. An example of such
an automatic scanning/sorting machine is the Pitney Bowes
Optical Character Reader described in publication 150 of the
United States Postal Service entitled "Automatic
Mechanization for Mail Processing Systems", page 14, May,
1985. A decryption module could be added to such an
automatic sorting machine by which the encrypted line 42
would be read as well as the address line by the OC~ reader.
This encryption module would determine the authenticity of
the postage not only on the basis of the visual tests,
postage, date, meter number and the like, but on the basis
of the recipient address. In this manner, not only is a
check made for authenticity of the postage but also for the
fact that the encrypted line belongs to that particular
piece of mail and only that piece because of the recipient
address. More specifically, what is contemplated is a two
way encryption scheme where the decryptor has a "key" to
determine authenticity based upon information on the face of
the envelope 34. This is in contrast to a two way scheme
~Z64341
g
where seed numbers are used and encryption is performed
twice and compared.
Referring now to Fig. 4, such an automatic
scanning/sortins machine with deciphering capability is
shown. The machine includes a mechanical transport unit 48
that singulates batches of mail into a stream of mail pieces
that are conveyed with a predetermined separation past the
various stations of the machine including a scanner 50, a
line finder 54, a segmentation block 56, a normalizer 58, a
simularity measurer 60 and a contextual analysis block 62.
Each envelope 34 is conveyed past the scanner 50 which
produces digitized binary images of the address field
consisting of black and white pixels. The line finder 54
finds the lines in the address field which are to be read.
The segmentation module 56 separates the lines into
characters. The normalization block 58 transforms the
segmented characters into a predetermined size. The
standardized character images are then transferred to a
similarity measurement block 60 where they are compared
~o against stored known character templats to obtain character
recognition. The results of these comparisons are sent to
the contextual analysis unit 62 where the final decision is
made for the address portion of the information while the
encryption portion passes through. An ASCIl code
representation of the recognized characters is then sent to
both a buffer 64 that simply stores the address information
and to a decipher 66 that decrypts the encryption line 42.
The information from the buffer 64 and decipher 66 is then
sent to a computer 68 where the information from each is
compared. The results of the comparison are sent to a
censor 70 where a determination is made as to the
authenticity of the postage on the mail piece. If it is
found to be authentic~ the envelope 34 is routed to a
sorting stack module 72, but if it is deemed to be
fraudulent, this envelope is sent to a rejection bin 74. In
this way, genuineness of the postage on an envelope can be
determined on the fly. Obviously, this process is enhanced
because the printed information on the envelope 32 is
applied in a parallel fashion thereby facilitating fast,
lZ64341
10--
automatic processing. If authentication is made, the
encryption message may be printed in bar code form at the
bottom edge of the envelope 32 as is now done with the
address information by a bar code printer 76 of an automatic
mail sorter. It will be understood that this bottom edge
bar printing of the encrypted message may be performed
alternatively by the user's printer 30 upon it's being
programmed to do so.
Referring now to Fig. 5, a flow chart is shown wherein
the cooperation between the accounting unit 14 and the user
computer 28 is shown. The system is initialized 76 and a
request is made 78 by the accounting unit 14 as to whether
the user is properly identified. If the user is identified,
a request is made by the accounting unit 14 for address and
lS postage information B0 for the purpose of generating the
encryption message. The information is received 82 and a
check for funds is requested 84. A determination is made if
funds are available 86 and if sufficient funds are availabe,
the information is combined 88 with the internal time, date,
ascending registers and the other information in the
accounting unit 14. The encryption message is generated 90
and the plain text and encrypted text are sent 92 to the
user computer 28. As the plain text and encrypted text are
sent, the transaction is accounted for 94 and the system is
returned to its starting point. On the other hand, if funds
are not available 86, then a message is sent to the user
computer 28 that there are insufficient funds.
The user computer 28 initially receives the request
from the accounting module 14 for the address and postage
information 10. With this request, the user would enter the
appropriate address and postage information 102 and this
would be sent 104 to the accounting unit 14. After the
address and postage information are conveyed, the question
is asked whether sufficient funds were received 106. If
sufficient funds were received, then the plain text and
encrypted text are received 108 from the accounting unit 14
and the command is given 110 to print the information on a
mail piece 34.