Note: Descriptions are shown in the official language in which they were submitted.
1 . jEUE ".D OF Tli~ iNV~NTION:
The field of the invention is computer systems employing
hierarchical file systems.
2. ART ~ACIfGROU~ID:
Computer systems available today range in cost and
sophistication from low cost micro-processor personal computers to
sophisticated, high cast mainframe computers. However, the computer
systems can be said to include the same basic components: at least one
central processing unit which controls the performance of computer operations,
input/output units which control the input and output of information within
and
out of the computer system, and memory or storage space which stores
information used by the CPU to perform computer operations.
The CPU is controlled by the operating system which dictates how
2o certain computer operations are to be performed. One portion of the
operating
system is the file system which determines and controls the file structure in
the
computer system.
One type of file structure in use is referred to as a hierarchical file
structure. In a hierarchical file structure files are organized info a tree
structure
having a single root node referred to as the "root". One or more nodes may
then be connected to the root and one or more nodes may be connected to
each node. Every non leaf node (that is, a node which has a Bode connected
to it ) of the tree structure is considered to be a directory of files; and
the files at
the leaf nodes of the tree are either directories, regular files, or special
device
82225.P052 1
~~1~%~~~~
files. The name of any file is identified by a path name which describes how
to
locate the file in the file system hierarchy. Tha path name is a sequence of
component or node names separated by "!" characters. A component name is
a sequence of characters that designates a file name uniquely contained in the
previous component. A full path name starts with the "/" character which
specifies a file that can ba found by starting at the file system root and
traversing the file tree following the branches that lead to successive
component names of the path names. For example, the path name
/usr/srclcmd/one.c represents the portion of a tree structure represented in
Fig.
l0 9 and identified as the path through nodes 10, 15, 20, 25 and 30.
There ace numerous commands which manipulate, refer to, or
access the file structures and files within the file structure. Such commands
include the "mount" and "unmount" commands. The mount command connects
a first file system (the term "file system" will hereinafter be used, as it is
used in
the art, to identify a hierarchical file structure existing in a computer
system) to
a second file system while the unmount system command disconnects the first
file system from the second file system. Once the file system is mounted, the
information in that file system is accessed through the directory of the root
file
2o system it is mounted upon. This is illustrated in Fig. 2. Root file system
40, has
directories or nodes bin 42, src 45 and usr 46. The file system 70 is mounted
on directory usr and the node 72 may be accessed using the path name
/usr/bin/date.
Further information may ba found on the mount command in most
operating systems manuals. More specific information may be found in the
context of the UNlX operating system environment in: Mach, J. Tha Des's
the Unix Operating Svstem, (Prentice-Hall 1966). As can ba seen from the
above-description, file systems era mounted on a directory-by-directory basis;
that is, at least one directory is mounted on a file system comprising at
least one
s2~s.~o52 2
. -. 2~iC~'~f~~~.
directory. In a convention UNIX operating system, once a file system has been
mounted on a specific directory, the inode of that directory may no longer be
accessed by processes.
However, as the sophistication of the users and the applications
executed on the computer system increase, it has become desirable to have
the capability to mount file systems on a per-process basis even though the
processes are located within the same directory. Thus, it is advantageous to
have several mounts performed within one directory such that different mounts
are utilized according to the current process.
82225.~Q52
~~l t: '~~~~.
--.
n is therefore an object of the present invention to provide a
computer system for per-process mounting of fife systems in a hierarchical
fife
system structure.
To provide per-process mounting, a temporary directory is
created off the current root directory. The file system, starting at the root
directory, is then mounted on the temporary directory using an innovative loop-
lo back file system function which results in the file system being virtually
duplicated having the temporary directory as the root directory. A mount of
the
file system containing process specific files can than be performed on the
temporary directory without affecting the original file system. A change root
directory command is then executed to change the root directory to the
temporary directory and execution then continued with respect to the mounted
file system having the temporary directory as its root.
2~~( f~'7~91
The objects, features and advantages of the system of the present
invention will be apparent from the following description in which:
FtG. 1 illustrates a hierarchical file structure employed in
computer systems.
FIG. 2 illustrates the system command mount which ~s employed
to in prior art operating systems.
FIG. 3 is a block diagram of the kernel in the UNIX operating
system employed in the preferred embodiment of the system of the present
invention.
FIG. 4 is a flow chart describing the preferred embodiment of the
process of the present invention.
FIG. 5 is a block diagram illustrative of the preferred embodiment
of the system of the present invention.
82225.P052
Through the system of the present invention per-process
mounting may be achieved on a computer system employing a hierarchical file
structure thereby adding increased flexibility and capabilities to the
computer
syste m.
~Dne operating system which uses a hierarchical file structure is
the UNIX~ (UNIX is a registered trademark of AT&T) operating system.
io Although the preferred embodiment is described in a UNIX operating system
environment, it is evident to one skilled in the art that the system of the
present
invention may be applied to other computer systems employing an operating
system which utilizes a hierarchical file structure.
i5 In a UNIX-based computer system, the operating system interacts
directly with the hardware providing common services to programs and
isolating the software and users from the hardware idiosyncrasies of a
particular computer system. Viewing the system as a set of layers, the
operating system is commonly called the "system kernel" or just "kernel",
2o emphasizing its isolation from the user programs. because the programs are
independent of the underlying hardware, it is easy to move the programs
between UNIX systems running on different hardware. The UNIX file system,
located within the kernel, organizes and controls access to the file
structures.
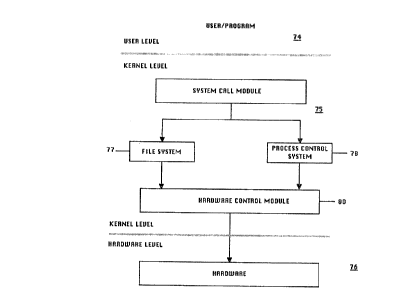
25 The kernel is depicted generally in dig. 3. dig. 3 shows ~ levels:
user/programs 74, kernel 75 and hardware 76. The system call module
represents the border or interface between the user or user programs and the
kernel. The system calls are divided into those system calls that interface
with
the file system 77 and those that interact with the process control system 76.
3o The process control system is responsible for process synchronization,
82225.P052 6
~(jCt'7fi~~.
interprocess communication, memory management and process scheduling.
The file system communicates with the hardware control module &0 which
interfaces to the computer system hardware and manages files, allocates fifes
space, administers free space, controls access to files and retrieves data for
users and programs.
The system will herein be described in reference to Figs. 4 and 5.
At block 100, Fig. 4, a temporary directory is created. This directory is
preferably created off the root directory so as to eliminate any subsequent
2o confusion with the following process steps and to clearly distinguish the
temporary sub-directory from other sub-directories of the same root. The
directory identification as temporary is used because it is preferred that
after
the process, for which the file system was created, has completed execution,
the temporary directory and nodes connected to it are removed such that the
25 file system is restored to its previous structure. However, the temporary
directory does not have to be removed and can remain indefinitely in the file
system structure. The first step described in Fig. 4 block 100 is illustrated
by
Figs. 5a and 5b. Fig. 5a shows the root directory 200, sub-directory usr 205
and sub-directory of usr identified as src 210. Fig. 5b illustrates the file
system
2o after the step 100 of Fig. 4. The temporary directory tmp 215, has been
created
having a sub-directory off of tmp identified as too 220.
At block 105, Fig. 4, the file system comprising directories 200,
205, 210, 215 and 220 are mounted on the directory too 220, whereby the
25 directory too 220 reflects the contents of the original root directory "/"
200. This
is illustrated in Fig. 5c, wherein the file system shown in Fig. 5b is
duplicated
by mounting the system an directory too 220, resulting in the structure,
illustrated by the rectangular shaped nodes, foo 220 having sub-directories
tmp 225, foo 230, usr 235 and src 240. This process is achieved using an
3o innovative technique referred to as loop-back mounting in which the file
82225.P052
~~0.6'~~:91.
structure or file system is duplicated off a different directory or different
file
system by adding a second pointer which dictates the location of the directory
in the file system. This process, results in the "virtual" placement of the
directory in two locations. ft should be noted that the apparent duplication
of
the directories does not result in the actual duplication of the directaries;
only
one set of directories exist but the directories appear to be concurrently
connected to two different nodes.
At step 910 Fig. 4 the file system, for example the file system that
io is desired to be process-specific, is mounted on the temporary file system
created. Referring to Figs. 5d and 5e the fife system shown in Fig. 5d
comprising directories bin and etc are mounted on the file system,
specifically
the src sub-directory 240. The resulting structure is represented by the
trapezoidal shaped nodes shown in Fig. 5e. At step 115, Fig. 4, the root
Zs directory is changed to be ltmp/foo node 220 of Fig. 5e. (ln the tJNlX
operating
system the change root directory command is CHROOT). As a result, the file
system visible to the user or process is as shown in Fig. 5f; since it is
visible
only to the process, it is termed "per-process. The stnrcture comprises the
root
node, which in Fig. 5e was directory foo 220 which now appears as the root
20 260, having sub-directories tmp 265, and fao 270 as well as sub directories
usr
2$0, 75 src 280, bin 290 and etc 300.
Thus, the process may be executed within the file structure of Fig.
5f without affecting the ability of other processes executed in the original
file
25 system (depicted in Fig. 5a).
it can be seen that the steps set forth in the flowchart of Fig. 4 may
be repeated, for example by creating a temporary directory tmpl having a sub-
directory foo, and mounting the directories containing the files to be
executed
3o with respect to another process. Furthermore the process described may
again
82225.PO52 $
be repeated for a second process, third process or more processes such that
each process is mounted on a separate file system thereby emulating or
providing per-process mounting.
The loopback mounting technique may be easily accomplished in
one implementation of the UNIX operating sytem. This implementation includes
a virtual file system in the kernel by which it is able to support multiple
file
. system types such as multiple versions of UNIX and non-UNIX systems such as
~SDOS. Such a virtual file system is described in y ode ~ ~, Architecture for
to ~ Iti i~i~ SX~Qm Tyroes in Sun U~ix, S. R. Kieiman, published by Sun
~llicrosystems, inc., fufountain Viaw, California.
As described in that paper, the conventional file system
independent inode of the UNIX is renamed vnode (virtuaP node). All file
m manipulation is done with a vnode object. File systems are manipulated
through the virtual file system. Each virtual file system~includes an analog
to
the mount table entry of the conventional UNiX system; this specifies the file
system type, the directory which is the mount point, generic flags (e.g., read
only), and a pointer to file system type specific data. This is linked to a
list of
2o mounted file systems so that file system dependent data may be provided.
This
virtual file system allows loopback mounts to be made.
To make a loopback mount, the user executes the IUfOUNT ()
system call. fn the command, the user specifies (1 ) that this call is to be a
2s ioopback mount, (2) the directory which is to be mounted, and (3) the
directory
it is to be mounted on. As pointed out, the vnode structure in the kernel
contains a pointer to the virtual file system specific data. This data
inciud~s for
a loopback file, among other things, a pointer to the "real vnode" for
the.file.
Thus, if directory A is loopback mounted onto directory ~, then in the kernel,
3o the vnode for directory ~ is a loopback vnode whose real vnode is the vnode
s222s.POS2
2~1t:' o ~~''~,
for directory A. For example, in Fig. 5(e)-(f), where the root directory "/"
is
mounted ~o the directory foo 220, the vnode for foo 220 has a pointer to the
root
"/" directory as its real directory.
When the kernel receives a filesystem request for directory
foo220, then the kernel executes the file system independent lookup code
before invoking the file system dependent lookup code for the virtual file
system
that the vnode is in. Since directory foo's vnode is in the loopback file
system,
the loopback lookup operation is performed. This operation calls the lookup
to operation for the real vnode, the vnode of root directory "/". in this way,
the
contents of directory foo are the same as the contents of the root directory
"/"
since the same files are found in either directory. Thus, the additional
pointer
which causes directory foo to point to the root directory "/" is the real
vnode
pointer in directory foo's loopback vnode.
While the invention has been described in conjunction with a
preferred embodiment, it is evident that numerous alternatives modifications,
variations and uses will be apparent to those skilled in the art in light of
the
foregoing description.
82225.P052 ~ d