Note: Descriptions are shown in the official language in which they were submitted.
206566~i
B~CI~;GE~T,~D OF ~E IN~rION
ven~io:~ relat~ to a met:hod of valid~t~ng ~ ~redit c~d. I
C:red~ e com~no~ly se~7t throu~h the post to their i te:~ded ~ecipien~s. i
On receipt of the credit ca~d, th~ hol~er signs the ca~d ~d can then use it to iconduct ~ ~o~ Le c~rd is i~te~epted, ~ the po~t or othexwise, ~ ¦
t~ird par~ ~ sig~ the card~ a~d ca~ ~he~ procee~ to use the c~d
~duleIItly. l~;~en in the ~e ~ l~ge ~s~ctio~s where all ~u~:Lo~ation I
must be obt~ined ~om ~;hë ~nancial i~stitu~o:n is~g the c~rd, a~ ¦
ut~orised pa~r ~y be ~le to use the c~edit c~d for some ~me, ~pi~l~y
weeks o~ e~en mon~hs befo~e it is real~sed th~ the ~e~it ca~d has b~en
~terce.Rted a~d rt ~s recorded on a li~t o~ "hot" c~rds.
the~:mo~e, welI ma~e cou~te~f~it c;~lds are appeaDng i~ cre~i~
umbers~ E these ~re prope~ly encoded, ~ vendor will no~ be able to
dis~uish gemlme a;~d ~u~er~eit c~ds.
As a res~lt o the above two p~ob~ems, ~redit card issu~g houses and b~nks
~;re ~ei~g de~rauded of vas~ of ~[o~
i
F I~ IN~P~I10
I
A~cord~ to t:he icL~ention a me~od of ~ida~ a ~ed~t ca~ compr~ses the ~
steps o~. ¦
iss~m~ ~ ~edit ~rd to a holder, the ~edit c~d ~ a
identifi~io~ ~ode,
~ ~ina ~ second identi~ on code to the holder;
., , ,;
,..
,. . . .
: ~ ,
~0656B~
conducti:~ a v~lidatioIl tr~saç~on u~ the credit card wherein the
~t aIId seco:~d ideIl~fication codes ~e input to ~ termina~; I
determin;ng whether th0 i~rst ~d second iden~ification codes b~ I
correspo~d to the sa~e h~Ide~, ¦
, ,eIlera~j, a valid~ tiorl record con~ g the validity of the ~d if the
~ 1 L ~LU ;i~V U ;U~ LV ~V U~i~ ~V.L I ~;1~V ~L, U~U
stori~ the ~ra~d~on reco~d i~ a database which ~ be accessed by
a ~eI}dor7 so that use of the ~edit c:ard :may ~e authorised by re~erence
tn *lt~ v~ hnn r~ nr~'
The ~st i~el:r~ic~tion code may be encoded o~ a Inagnetic s~ipe on ~e
c:redit ca~d.
I~ addition to the ~t ~e~ fic~tio3:l code, ~urther inforn:lation su~h as the I
period of Yalidity o~ ~e card m~y be encoded o~ l:he ma~e~c stripe.
The second iden~fic~tion code may be a personal ide~ umber OE~
~ssigned to ~e ~older,
I
T~e ~sa~ion is prefe~bly condllcted o~ a termi~ n auto~a~
teLler ma~ e ~AI~ whi~h ~e~ds *le fi~st iden~ficatio~ cude and a~ry further
i~o~matio~:L from t he m~e~ s~ipe o~ tke ~ rd, allows the holder to
~p~t l~he secoIId ide~ ode :maIlu~ly~ and transmi~s the ~odes to a j
cenP:~l da~a prosessra statio~ for Ye~ tio~
A prImed record of the tr~sa~ion ~Aay be generate~ ~nd n~y be ~ine~ 11
by the term~ for rec~d purposes~ or may be issaed to the holder ~o~ u~e i
with t:he ~redit ~cL
Illstead of a~ tbe te~nal m~ly be a po~t-osale ~1?0$) de~ice, a
: . . ,
2~6~6~1
¢o~pute~ with a modem, or e~rel:l a telephone. 1~ t;he l~tte~ ~se, the codes
can be ~mitted verb~ly or by us~ the dialler or keypad of the telepholle.
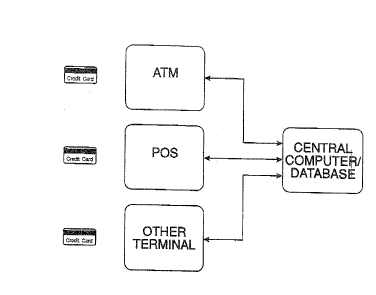
Figure 1 is a s~mplified block dia~am sho~ing apparatus for so~du~g t~emeth~3d of t~e ilIve~o~ Ld
F~ e 2 is a simpli~ed ~ow ~art ~ a~ng ~e metho~ ¦
A com~erl~r~LI Gre~it card i~ ly a pla~ ect~ lar pIece of pl~
materi~l on urhich ~e emboss~d a ~ique iden~fication numher, the ~me o~
the c~rd holder an~ ~he exp~ date of the c~ Other in~orm~on m~y a~so
appea~ T~e cred~t ~ard usually has 2 m~ e~ic ~tnpe on its ba~, on w~i~h
the credit card m~mber is recorded. C~ther rele~t in~o~mation~ such as t~e
per~od of ~ y of thB t~d, C~l ~lso ~e recorded cn ~he In~gnehc s~ipe.
Tn o~de:r to use c~ed~t cards (or other cards) for w~th~ l of ~d~ fror1 le
a~o~nt of a holder, a pe~oD~l ide:~ num~er (PI~j is iss~d w~
kQown only to thc card holder~ When t~e ~d is llsed in an ~ltom~;~c teller
e ~ATM:) ~or a ~sh withdra~ or a 5Im;l~r transac~o~ the card is i~rs~
~se~ted ~nto t~e termin~l~ which reads the ~rd nu~ber, Y~ d~tes ar~d/or
related I~fo~at~o~ on the r~e~ st~ipe. The te~ l the~ ~lows the ~d
holde~ to input the PIN code ma:~ually. A veIi~tcation pro~edPle is then
ca~ied out to ensure that the c~d nllmher and th2 PIN ~ode b~th coIrespsn~
to ~e s~me h~lder. T~e ~eriE~on p:~ocedure m~y require the ~d ~ber
a~d the P~ code to ~e ~tted to 3. central da~ba~e for venficatio~, or
t:he data m~y be stored ~t the term~nal itse~ ~ any 2verlt~ if the ve~ific~tio~proce~ure is not ~ed Q~t s~i~a~or~y, ~e tr~sac~o~ is abo~ed.
Repeated unsuc~1 ~o~s ~allyre~ n ~e ~ard bei~ co~scated
l~y ~he macL~ e.
.... . ....
... . : ,; ,
~6~65
Il co~rzs~ to rhe a~o~e procedule, no PIN code ~ req~led ~o use the credit
card L~ a normal cred~t tra~sac~on. ~ long a5 the si~atule o~ ~he back of
the card co~responds to the ~ature on the ~redit car~ slip pro~ided by a
vendo~, and the card ~ ~ot ~s~ed as a stole~ or lost card~ the ~a~sac~on
app~ovedi Xnthe c~se o~ t~n~c~ons ~lvol~ng relatively large sllm~(~ypica~y
greater ~ha~ 00,00) ~he ve~dor ma~ ~ontact the credit caLd iss~er for an
"authoIisatiorl"7 to co~ ~hat ~e c~rd holder's accou~t h~s suffl~ie~t credit
for the l~ ion. ~owever~ if t;he card has been intercepted in the post, the
issuer a~d ~he intended re~ipie~t D1ay be completely ~ aware ofthe the~ of
the ca~d, ~d it Inay be some weeks or months before the ~redit card issuer
is ~oforrned of ~he ~act that the c~ld ~ ~ sLn~ a~d it is placed ~n the "hot"
~s~ Sin~larl~ it ~ght be some weeks ~efo~e theissuer and the card holder
realise ~ a counterfei~ copy of a ~d is being ~e~
To prevent this, ~he in~entio:~ proposes that 1:he ~edit card issu&r requi~e a
va~idation lla;~a~tion to be ca~ied out usi~ a newly issued ~edit c~d ~d
l:he PII~ code of the i~ended c~d holder ~e~ore the credit c~rd is, conside~ed
t~ be v31id or "~llthonsedn. The c~d a~ld PIN code ca:L be sent to the
~nteIIded holder i::L the usual way, by pos~ or ~an be colle~ted per~o~lly.
Pa~cularly when a ~lew credit c~d is issued, a:lld when ~ PIN code s assi~ed
to the card holdert it is pre~erable that the c~d holder collect at least o~e of~e c~rd a~d the ~ code persoIIally, show~~ itable ~den~ïcatio~.
However, once a PIN code has ~een assig:~ed tv t~e card holder, the method
of t~e imre~tion redu~es the rleed for replaceme~t ~ds to be ~ollected
person~lly, or posted by re~stered maiL
To Yalidate the ~redit card, the c~d holder may Ise ~e new ~d for ~ ~sh
wit~drau~al or deposi:t, or n~y simply condu~ a nomm~1 ~¢tioD, such ~s
a "depos~t" or 'withdrawal" o~ zero value, or a~other valida~ion ~a~ac~on
speci~ed by the c~e~ît card ~s~er~ at a~ ATM or other ~emIinal lillke~ to a
host coInputer ~d ~L~Lb~e ~:t the fi~ s~ o:~ in ques~on. Instea~
the terminal ~ have i~s own mte~l computer ~d d~ se. ~be valida~
tr~sa~on ~L also be caIIied ou~ at the same time as a conYen~on~l sa~es
. ~
2~6~6~
~ansactian LS ~e~ out, -for e~ample~ v~a a pa.i~ of s~le (POS) term~nal.
Only once ~i5 has been done, a~d t~e t~ at which ~e ~ransaction is
~onducted and/or ~he host ~ uter of the ~Lrd issller has v~ Eed that the
c~rd ll~mber~ validi~y date~ and ~:he PI~ code correspond to t:t:e d~ base
records, is ~ ~lida~oll reco~d generated whic31 e~ect~vely places the c~rd o~
a ~t ~ vaLid ~d~, so that ~;a~iorL~ greater than any m~mum
unauthorised limit ~ be ~uIthorised. The valîdation record is ~eld 1n a
da~abase, at the fin~nc~ tu~on ooncerned or elsewhere~ which ~ e
accessed ~y vendor~. Tn the e~ent that ~he car~ presellte~ to the Yeudor has
not been s~¢ess~ly validated, it ca:~ be conf~ Lted~ or a~ ala~m ~an be
~enerated.
~he flo~ ~h~ of Figure 2 illns~ates the basic steps carried out by ~he card
issuer, ~e ~xd holder ~d a ve:cldor to whom the card is presented. IE the
~d i~s~ed by the fin;ln~ is reeeIved b~ ~he inten~d re~ipie
he or she ~en ~r~es o~t ~e above des~n~ed v~lida~on Fro~e~ure at a~
ATM or other terTnin~l. As~ that the c~rd holder enters the corre~t P~l
code dunn~ t~e v~da~ol:~ tr~ction, ~e credit ~d w~l be validated, ~d
record to t:h~t ef~ wlll be stored in a database. If the ~d holder e3:1ters
an irLcorrect PIN c~de more t~ prede~term~ed number of times (typi~ly
three ~imes), Jl;he ten~ co~c~ he ~r~
A~ proof t~at t~he validatiQn pr~cedure h2s been co:lld~cted7 the card holder
a deposit slip or ot:her record ~ne~ated by ~:he A~i, whi~h is the~
~epos~ed ~ t~e ~1~ o~ ret~e~ by t~e car~ holde~
t~e credit ~d is intercepted by a~ tbolise~ p~rs4~, that per$on m~
~y to carry o~t ~he v~ a~n proced~e, Eowever, wi~hout the PIN code
coIrespondin~ to the c~rd, there ~s liffle ch~nce of ~e validadon tra~sactio~
be~ sllcces~L 1 E ~e unauthoIised c~d holder s~ply presents ~e ~ard ~o
a vendor, the ~ard m~y be used success~ully only ~r ~sa¢~ons whi~
be1~w th~ ~mum leYel peImitte~ for u~u~hor~sed ~a~ ions 'rhis l~vel
~ ~e adj~sted ~om s~ ~4 time by the c~d Lssller ~ an attempt is m~de
, ~ ,
~, ~
, , ~',
~5~$~
to use ~e ~rd for a tr~nsa~ioIl involvL~ all amouut ~ ter tha~ ~e
m~um u~uthonsed level, the vendor ~ill be alerted to the fact t:hat the
~d is un~uthorised~ ~s descrl~ed above.
Tn order to protect c~edit ~d holders alld ~red~t c~rd issuers du~n~ ~eperiod in which newly issued cards are most li~ely to be fr~udulen~ly llsed~
th~t is, m the f~t fe~ mo:~s after bei~ isslled, the c~ed;t c~d 1ssuer ca~ ~et
a redllced una~thorised cre~it limit d~ say, the first three mo3lths of the
~d's l;~e. Fo~ ~mple, du~ the ~1 ~ee mo~ of l;he ~Lr~7s life a
~ec~t limii of R~,OO or ~ O,OO c~n be set, so ~ ~c~o~ inyolyin~
~o7~ts gre~t~ th~ t~s l~it must be allthon~ed. T~ ~vill ha~e the ef~ect
of reduc~n~ ~e total ~mo7~t involved ~ ~audulent ~sa~o~, ~d wi~l
result in a large rrurnber of ~audule~tly used cards bei}3g removed ~om
c~cula~o7l,
Alrern~tivel~ to the re~o~d bei~ deposited in the ATM7 it ~ be ~ssue~ to
the c2r~ holder eorLdllctiIIg the t~ns~ctio~ It ca~ then be req~ ed, duri~g
the period referred to above~ o~ ~r the li~e of the card, th~t the card be
Y~lidated in use b~ produ~o~ of the re~rd. Thi~ would ob~iate the need ~or
authoris~on VL~l ~he card issuer for traDsac~ions involving sInall amounts. For
~a~o~ volv~ l~er ~lOn~ no~ uthorisa~n proced~re
~mld st~ll be folowed.
~hile ~he above proced~e does not, at present, en~rely pr~ve:~lt fr~udul~nt
use of a~ ~tercepted credit card for tra~sa~tiorls involvin~ small amo~ts of
money, it does prevent ~audulellt t~sa~o~ ol~ing la~ger sums w~ch
re~ re a~or~sa~o~ nore ele~onic poin~ of s~le (~OS3 de~ices ~;re
l;nked to l~ve databases, ~w~r ~nd fewer Ilewly isslled ~ds will be usable
~a7~dulent:1y7 since a c~ec3~ o~ the validity of the ~ l c~ be made each ~me
~e ~d is use~ 1y, it is pos~ble to re~7~i~e th~ all credit ~rd
~ns~oDs ~e author~ed, ~nd rLot ~nly ~hose tr~io~s invoIv}ng ~ouIlt
larger ~h~n a predetermîned l~i~ Whether or not thi~ LS desira~Ie ~epends
la~gely on the exte~t of cle~ ~ d a~ L~g plao~ at .~ p~ tidal _,
~.
2065665
wei~hed a~inst t~e minor incoIlve~ierlce of tll& ~uthorisation proced~e.
No spe~al equ~pmen~ is re~ed to im~lemeIlt the met:hod~ wlli~h requires
only rel~tively mi~or procedulal ad~ ments ~d, possl~ly, reYi~ed sof~e~
For this ~eason~ o~ly ~n ext}emely sirnpl~ied ha~dwar&block d;agralEL îs shown
in Fi~e 1. Figure 1 shows ~ cen~l computer/data~ase of ~ ancial
ins~t~tion li~L-ed to ~nous te~min~lc, D~ U~ an ~TM, a poiIIt~f-~ale
(~OS) te~ l, and another termmal, wh~ch ~ould be 2 per~on~l computer
with a modem, an ele~ontc t~l, 0~ even ~ telephone. Ill the latter ~se, ~o~h
che f~st and second iden~i~a~on codes (ie. the ~CrOUIIt num~er alld P~
code) ~n be suppl~ed verb~ly by the s~rd holder to the ~ncial i~ n
via the telephorle, or the dialler or keyp~d of ~e telephone ~ be used to
~nput the codes. Alterna~vely, a tone generator supplied by ~ cial
f~tu~on~ :Eor 'rba~g hy p~one'l could be ~sed wl~:h ~e telephone. I~ t~e
l~er caSeS7 the accomLI mlmbe:E is s~nply read o~ the ~rd ~ the car~
holder.
Al~ough ~tems have beeIL proposed i~OI' i3lcreasin~ the se~ri~y of credit
tr~sac~o~, suGh ~tems generally rely on rela~vely hhi~h-tech" devices sucih
as "smart c~ds". Such ça~ds require ~ecial ~ard readers, with the result that
syster~s of ~s ~d are rel~vely expensi~e to impl~men~ It is a p~ar
ad~ ~e of ~he prese~t ~v~ntion ~a~ ple~ely co~p~ble ~i~
c~nven~o~l cred~t ca~ds, and wi~ ~e ~ardwa}e in e~is~ A~M's and other
term~nals which i:~clude ma~ne~c st~pe re~:lers.
~he l:ne~hod ca~ accol~nod~te sy~ems which allow a c~d holder to alt~r hi~
or her PIN ¢ode7 a~d ~ ~o be a~plie~ to foreigll ¢~d hold~rs visi~ing
coun~ which the method ~; ~ ed
'~