Note: Descriptions are shown in the official language in which they were submitted.
W0~3/21582 2 ~ 3 ~ 9 ~ O P~T/US93~03669
SYS~ OR PROTEC~IQN OF SOFTWARE
Field of the Invention
:~ m iS invention relates to software protection,
i.e. inhibition of unauthorized copying or use of computer
: 5 software. More~ particularly, his invention relates to a
:software-based software:protection system, which doss not
: re~ly on specialized hardware to protect the software.
Backqround of;the~Invention
Unauthorized ;:~copying and use of software
("software piracy"~)~ is a:problem that has cost software
publis~ers billions ~of:~dollars per :year since it became
common~for~ users~ to:;~purchase~standard software products.
S~ftware~is~ typically ~distributed on ~a removable storage
médiu~uch~as~a~magnetic or optical::disk or diskette, and
15~ ;s ~ ~ ter~s~may~be used in~erchangeably herein. It is
estimated~that for~every five units of sof~ware sold, four
:àre piraited.:~Thé~annual~loss to software publishers from
software piracy~ ~IS~ estimated at over S3 billion per year.
Two approaches have been used ~o~ attempt to
20~ protect~ oftware~::àga;inst~ piracy. ~:Hardware-based software
:pr:otection~ system~ include an:auxiliary piece: of hardware
which~is~ distributed~;with the software and which must b~
in~tal~led:in a:computer, such:as by being conneGted to an
O~port, to pe ~ it~ the computer to run the protected
2~5:;~ software.- Such~systems can be highly~effectiv~, since the
W093/215~2 PCT/US93/~3669
213`39 60 `~
: hardware "keys" can be made difficult to copy. However,
:: hardware-based software prote-tion systems are t~pi~ally
;expensive, and thus suitable for use only with expensive
software packagés. Sueh systems can permit use of the
: 5 sotware on different compu~ers while restricting the use
to one machine at a given time. Howeve~, it is often
inconvenient to remove the hardware "key" ~rom one machine
and install it on another.
Software-~ased software protection systems have
~ lO also been developed. Such systems are relatively
:~ : : ;ne~pensive, and therefore are more suitable for use with
1ess~expensive~, mas`s-marketed software. However, such
systems are~:generall:y ineffective, and may be defeatPd ~y
so~tware:programs;~su~h as COPY II PC whieh are readily and
:l5~ expe~ns~ively av`ailable. ~hile mass ~opying of software
for resa1e~is unusual:~:~in the United :States, small scale
opy~ing:~ is~ not.:::~:A~: person; may make a ~ew copies ~or
f~riends,~or:for`:~use~:on~ other machines at work, or to
pe~mit ~use of the same softwa:re at home and at work. The
20~ slml~1:ative efect~s~of: such smal~l-scale copying represent a
ma3~o~r~10ss~to softwar~e~publishers.~ :
Much ~ so~:twa~e that~ has~ been d~tributed with
software-based sof~tware protection:::has run into criticism
by~u:se~rs because~ i~t~is :time consuming to move the so~tware
:: 2S ~rom one computer::~:~to anoth~rO If a u:se;r uses the software
::at ~the office,~ ~i:t ~may ~:require 30 or 40 minutes to
:uninstall it a:t t:he~:off:i:ce and reinstall it a~ home.
:
:: : - : : ~:
; - :
: :::: : :
:: ::
: :
~ 093/21582 PCT/US93/03S69
21'3'3g`6~
Summar~_of the Invention
: It is there~ore a general object of the
invention to provide an improved software protection
mechanism.
It is another object of the invention to provide
a software protection mechanism which is highly effective.
:: ~
: It is another object of the invention to provide
~:: : a:software protection mechanism which is inexpensive, so
tnat it may be advantageously used to protect a wide ran~e
a~ :of software.
It is another object of t~.e invention to provide
protection for software on i~s distribution media, while
;installed~on a h~a;rd ~disk, and while in use in the
compute~'s:main memory.
;lS~ It i 5 ~another object of~this invention, that in
case~th~ user:'s;~instal~ed copy of the~protected sotware
;becomes~ not usable,~ the appl~icatio~ software may be
reinstalled ater~the:user calls:~the soft~are publisher
:for~data to allow the~r~installation.
It is~anot~her object of the invention to provide
a~:software protection mechanism which does not inte~fere
with~ other software protection me:chanisms wh:ich may be
used by a software~publisher.
~:: :: :
~: :
::
W~93/21582 2 1 3 3 9 6 0 PCT/US93/0366~
It is ano~her object of the invention to provide
a sotware protection mechanism which is easily employed
by a software publi:sher.
: : :
It is dnother object o- the invention to provide
a software~ protection mec~.anism which minimizes
inconvenience~in uslng protected software on different
machines at different times.
It is another object of the invention to provide
a:softwar~e protect;ion:mechanism ~;hich permits the user to
lO: run the protected~software in tne event that the ori~inal
: copy: becomes unusable.~
; The ~ p-eSeAt inven~ion i5 based upon the
recog:nition that:~ t~he;~software distribution medium itself
ha~s~or~ may~be provided~with physical attributes which are
l5~ :s~ufficiently :d~i~st~1~nctiYe and~ sufficient1y difficult to
copy~as~to~be u:séful~in a process for determining whether
a~ pa:rticular~dis:tribution me:dium is an original or
author~iz~ed;~copy~ or~:an unauthorized copy. `The p~esent
nvent~i~on~ provi~des:::software which~:operates in conjunction
20 ~ with:such~distribution: medium attributes to ;provide a
: ::n~vel software~pro~tect:i~n system.~
: This~ :in~ention provides a ~mechanism that
produces diskettes;~with~ a: scra.~.bléd,~: thus not usable
vers~ion ~of the~software publis.r.er's application:program.
:25 ~Thls diskette is~supplied to the ~ser with an INST~LL
program:that ver~ifies t~at the disY~ette is the original by
: the existence Oe bad spots (physically altered locations
::: : : ~:
: ~ ~
:~ ~: :: :
093/2
158 P~/US93~03~69
2~3~36~
on the diskette that will not properly record data) on the
diskette. . The INSTALL program veriies that the bad spots
are real by reading and writing to these diskette sector
locations. Acco~dingly products like COPY II PC which
copy diskettes including bad spot indications in the File
Allocation Table will copy the diskette, but the IN5iALL
program will not run because the indicated bad spots ~re
not really bad.
In a preferred embodiment, the pro~ram for bad
spot verification is made difficult to analyze and/or
bypass. According, the program code that reads and writes
to ~hese bad spots is unpredictably scattered throu~hout
the program to make it very time consuming for an expert
o~ debu~ and fool the program. In addition, a~ random
l5;~times~during~th~is wr~i~te~read process, the write/read tests
wil;~ e ~done by a~separate spawned program that will have
its own abili~y to stop the process if the results of the
write/read~s are not what is expected~by the spawned write/
read~program. This~makes it very d;ficult for a computer
20~expe;rt ~to block or alter the actions of this invention to
pro~ect~the softwarè~application. The order of re ds and
w~i~es ~is also not~ predic~able.~ ~ ~his ~makes it Yery
difficul~ to guess~ what the program expects from the reads
a~d writes. The locations of these bad s~ots are used in
the formulas to scramble and unscramble the application
p~rogram f ile . Thus, creating a diskette t~ look exactly
li~e the original as ar as formatting and ~ad spot
locations would take much more time than it is worth.
WO93/21~8~ 2 1 3 3 9 6 0 PCT/US93/03669 ~
The main ~alue of the above protection mechanism
is that the locaticr, of ~h~ b?d spots must be verified by
the I~STALL program as being in the same place as the
original. This is very difficult since the sectoring and
timing functions of the computer's formatting programs do
not start the tracks in the same p' ace. The probability
of ~reating an exact copy of a bad spotted diskette is
:very, very low. If someone does spend the time to copy a
diske~te~ he w~ll not be~able to mass distribute this copy
10 mechanism because the bad spots of the next diskette will
most probably not be in the same place.
In a preferred embodiment, there is a hidden
scrambled USER~RECORD on the diskette with other data that
;~ ~ is: used ~ in the scramble and unscramble formulas. This
:;l5~ means that this r;ecord,~ which `cannot be seen by the
c~mp~ut~g';s file sy5tem because the file system did not
write~ t, must be~located, read, and unscrambled. It must
then; be.;used to un:scramble the application program file.
T he~ sotware~pirate must find and unscrambIe the hidden
US~R~:RECOBV, ~which~ has values :to unscramble the
application~program~file. These values can be changed
per~iodically. ~The~order of the fields in this record may
also:be changed:per:iodically. One additional step to foul
the efforts of th~:software pirate is to actually change
the scramble and ;unscramble~ formulas. These things
:prevent~ a copy:~pro~tection break mechanism that will work
pas~ a short time.
In another aspect Qf the invention, a "ONCE
~:~ INSTALLED PROTECTION" capability is used to protect the
: ::
~ 0g3/21582 PCT/US93/03669
21~3~60
-7-
~;~ software Çrom piracy from the hard disk or from the
computer's main mPmory~ During the install process, a set
of dat~ unique to~this specific installation is stored in
a ONCE INSTALLED~ PROTECTION program. When the protected
5 ~ appli~cation~ pro9ram:~Ls~ run it spawns this program whîch
checks the cuFrent ~ c,omputer's file system information
about the software~applications program file. I the data
returned by the~computer'~s file system does not match the
data s~tored~in~the~ON~E INS~ALLED PROTECTION program, the
10 ' appl~icat~ion program ~file will be erased and ~he program
w~ not execute~ In~;addi~tion. the location of hard disk
;b~ad~sp~ts~alonq~ with~;the~status of these bad spots is used
to;~,v~er~ify that~t~his~;copy of the application is valid for
use~ This~ pr~otecti'on~ prevents the pirating of the3,~ l5~ appli~ca~tion~from;~th~e~installed h~rd disk or the computer's
main~;mémory.~ oth cases, the ONCE INSTALLED PROTECTION
mechan~`~sm,~which~requIr~es the; presence~ of the or,iginal
ha~r~d~ d'isk status to~run, must be present with a~ màtching
original ONCE INS~ALLCD~PRO~ECTION~PRCGRAM.;~ ~
~ In another~a~spect of~ the~ invention~, this bad
spot~vérif~ication~me~chanism~may~be u's~ed,in a~SOFTWARE KEY
diskette~ his~is an~option~for the~ software publisher
t~t,`~al;lows~thè usér~to install;a~not;usab~le~copy of the
application;on~more~than one ~computer at a t~ime. The
25~,',50FTWARE~ KEY~pr ~ ram~ has~the abili~ty~to;turn~the use of
t,he;~appl~ication~O~ on~ one computer ~and' ~ON on~ another
com,puter~ ~ The~ SOFTWARE KEY diskette in~sures that the
ap`plLcat:ion is u.a~ on only one~compu~ter at a time.~
W~ 93/21582 2 1 3 3 9 6 O : PCr/V!~i93/03669 ,~1~
--8~
In ano~ lier aspect of the invention, as an cption
to the sof tware publisher, an EME~GENCY US~ copy of the
application may be provided. This makes it unnecessary
for the user to copy the diskettes prior to installation.
5: This diskette is protected in the same manner as are the
~ APPLICATION DISKETTE and SQFT~ARE KFY DISKETTE. It also
: has the EMERGENCY RUN program on it that actually runs the
: rea} applic tion. This diskette must be ~he original to
run properly. I~ also has a limited number of ~ses that
10 allows the user to contact the sof tware publisher for a
:~ new copy of the application. This will allow the sof tware
publisher, who tracks the users for updates and
~: warranties, to track exc~ssive copies as well. Syste~ns
:~ ~ seldom crash and diskettes seldom ~ecome unreada~le.
:15:~ Other objects and features of the invention will
be ~: un~erstood with reference to the followlng
specification, claims,~ and drawings.
; : : ~
:: ::
~: ~ : Br it~_~n of the Drawings
The f low -~ charts and illustrations of the
~ ~ 2 0 drawi:ngs describe ~ the preerred embodiment of the
: ~ invention. The: step boxes in the flow charts are
~: : accompanied by numbers wh;ch refer to a place in the text
~: in the detailed ~ description of the invention that
desc~ ibes the stepO Pigures are as follows
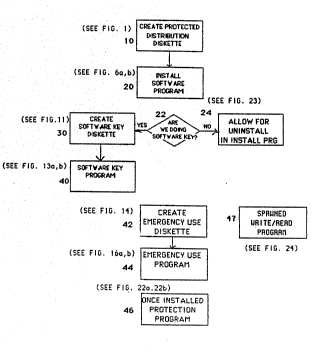
Figure l is a flow chart of the ten steps and
programs that comprise the invention~
~~VC~ 93/215~2 2 1 3 ~ 9 6 13 PCI/US93/û3669
_g_
Figure 2 is a ~low char~ ~f the steps used ~o
create the APPLICATION distribution diskette.
.
Figure 3 is a flow chart of the program steps o
the CREATE APPLICATION DISKETTE program.
Figure :4 is a flow chart of the scramble
mechanis~ used in the CREATE APPLIC~TION ~ISKETTE program.
: , .
:~ ~ Eigure S is a flow chart of the steps used by
he REATE APPLICATION DISKETTE program ts scramble, hide
and wrlt~e the USER RECO~D.
10: Figure:6a and 6b are a flow chart of program
steps of the IN~TALL;program.
Figur~ 7 :is~ a f low char t of the pro~ram steps
used~by~the INSTALL,~ SO~TWARE KEY, and EMERGENCY USE
programs that verify ~the bad spots on a diskctte.
igure~:8 is: a flow chart of lower level steps of
Figure 7. Thes~e~ ;steps randomly pick which write/read
:routine to use. ~
; Figure :~9; is a flow chart of the program steps
used by the: INSTALL,~ SOFTWARE KEY, and ~EMERGENCY USE
programs to find, ~verify, and unscramble the USER RECORD.
Figure:~10 is a flow chart of the steps to
: unscramble and install the application program.
:: :
:
.
WO 93J2158? 21 3 3 9 6 0 PCJ/US93/03669 ~ ~
--10--
Figure 11 is a flow chart of the steps used to
create the SOFTWARE KEY DISKE~TE.
~ ' .
E'igure 12 is a flow chart of the CREATE SOFTWARE
KE:Y DI SKETT PROGXAM ~
:~
5~Figures 13a and 13b are a flow chart of the
SOFTWARE KEY PROGRAM.
Figure 14 is a 10w chart of the steps used to
create the EMERGE2~CY: US~: DISKETTE.
Figure 15 is ~ a 10w chart of the CREATE
10 EME:RC~MCY USE DISKET?E PROGRAM.
Figures 1 6a and 16b a re a flow char t o the
EM13RGENCY USE P~OGRA15~. :
: ~ Figure 17: is~ an illustration of the INSTALL
P~OGRAM l)I SKE~TE .
~: 15: Figure 18 ~is~ an illus'cration of the SOFTW~RE KE:Y
DISKETTE~
Figure 19 is an illustratiorl of She EMERGENC:Y
: VSE ~D I SKET~E: . ~
Figure 2û is an illustratiorl of a process for
;~ ~ 20 creating bad spots on~ a diskette.
: :
. ~O 93/21582 2 13 3 9 ~ `~` PCr/US93/03669
Fiqures 21a and 21b are a f low chart of the
INSTAI,L PROGRAM steps . that create the ONCE INSTALLE~
PROTECTION .
~ igures 22a and 22b are a flow chart of the ONCE
5 INSTALLED PROTECTION PROG~M.
igure 23 is a ~low chart ~f the program steps
of the INST~LL PROGRAM to perform the UNINSTALL FROCESSo
:
Etigure~ 24 ~is a flow chart of the spawned WRITE/
READ p r og ~ am .
10: ~ ~ ~ Figure 2 5 ~ is a flow chart of the BUI~D SYSTE:kS
ERIF:Y~ D~A PROCESS~
Figure 26:: is a flow chart of the BUI~D ~IARI3 DISK
VERI~:~Y ~ DA~A PP~OCESS .~
igure 27~ ~:is: a flow chart of the SYSTEM VEP~Y
`15 ~ P~OC~SS~
igure 28 ~ is a f~ow chaxt of the ~ARD DI5K
VERI FY PP~OCESS .
,
igure ~29 ~ is a flos~ chart of the TURN ON PROCESS
: us~ed by the SOFTWARE :KEY program.
;: ~; 20 ~ ~ Figure 30~ is a fIow chart of the TURN OFF
PROCESS used ~y the SOFTWARE KEY program~
W093f21~2 2 1 3 ~ 9 6`0 ~CT/US93/~3669~
-12-
Figure 31 is a flow chart of the APPLICATION
EXEC~TE PROCESS.
: ~ Figure 3Z is a flow ~hart o the DOES NOT PASS
~: PROCEDURE used to destroy the ability to run if the
:: 5 appli~ation is found no~ ~o be a valid copy.
Figure 33 is a flow chart of the REINSTALL
PROCESS optionally used in the INSTALL PROGRAM.
Detailed Description
Int~roduction: ~ ~:
0 ~ : This i:nvention: comprises procedures and the use
of rom 2 to 9 omputer programs that provide usage
protection or a sof;tware publisher's:application program.
: : The first:p:rogram, called the CREATE APP~ICATION
:DISKETTE PROG ~ ,~puts~a scram~led~copy of the software
publisher~'s~ program~, ~ hereafter called the application, a
scrambled copy of the ~ONCE INSTALLE~ PROTEC~ION P~OG~AM,
and: ~ a~ copy of a~ small wri:te/read pxogram onto a
distribution medium, hereafter cal~ed the diskette. The
application program:is scrambled according to the location
20~of bad spots randomly~put onto the diskette and a modulus
factor that may ~be changed periodically to make
unscram~ g the application more difficult. The same
process is used t o copy the ONCE INSTALLED PROTECTION
PROGRAM to the diskette. This program also puts a
25 scrambled copy of a 'USER RECORD' onto the diskette in a
:Y093J21582 213 3 9 ~ ~ PCT/US93/03~69
-13-
hidden area of the diskette containing the modulus fzctor,
optional user inform~ti~n, and f~ags, such as the SO~l~WARE
KEY flag, which indicates if the publisher is using the
SOFTWARE KEY option. This record, located on the diskette
by the locations of the bad spots, must be ound and
unscrambled prior to unscrambling the application. This
~ record cannot be found using the standard file system
:: callable routines.
: The next program, called the INSTALL PROGRAM, is
distributed with the APPLIC~TION diskette and unscrambles/
inst:al~ls the application program on the user's computer.
It also checks the ~bad ~spots on the APPLICATION diskette
to :see if they are really bad. This prevents produc~s
: ;such as COPY II PC from being useà to successfully copy
lS~ the~ APPLICATION~;diske te. This program ~inds and
u~nscrambles the~USER RE~ORD. It then unscrambles the
appli:cat:ion as:it installs it on the user's ~omputer. It
: : als~ unscr~mbles and installs the ONCE INSTALLED
PROTECTION PROGRP~ he ONCE ~ INSTALLED P~OTECTION PROGRlW
: 2~ is copied~to the hard disk and data used in the once
installed p~ro~ection process is copied directly into the
ONCE INSTAL~ED PROTECTION PROGRAM.:
:
;This program has the ability to uninstall the
application if the:SOFTWARE KEY OPTION is not used. This:: 25~ is done by verifying that the appl:ication is valid by
~spawning the ONCE INSTALLED PROTECTION PROGRAM. If the
application is valid, it is destro~ed and data in the user
:~ data record on: the~ diskette is changed to show the
uninstall. ~ : :
W093/21582 2 1 3 3 9 6 0 PCT/~S93/03669
-14-
The next program, called the SOFTWARE KEY BVILD
PROÇ~AM, builds the SO~TWARE KEY diskette for the optional
SO~TWARE KEY facility provided to the software publisher.
If the software publisher has chosen to use the SO~T~ARE
S KEY option, the INSTALL PRQGRAM installs the application
: with the first part of the application replaced with a
small prog~am called the NOTON PROGR~M. If the
: ~ applica~ion is executed, the NOTON P~OGRA~ is really
executed. It will display a message telling the user that
the applic~tion i5 turned off. The SOFTWARE KEY BUILD
PROG ~ scrambles and hides the USER RECORD on the
SOFTWARE KEY diskette the same way the CREATE APPLICATION
DISKETTE PROGRAM does on the APPLIC.~TION diskette. It
then copies the NOTON progr~m, the SOFTWARE KEY PROGRAM,
15~ and:a scram~led copy of the first 512 bytes of the
application program to~the diskette.
The SOFTWARE KEY diskette contains the SOFTWAR
KEY PROGRAM which is~used to turn ON and OF~ application
that; has been installed on a computer. One of the major
~ 2G problems with most pas~ pro~ection mech3nisms is tha~ it
: :: :: i~:inconvenient and time consuming to ~ove th~ applicatlon
:: : : : `
~ : ~:o:another computer. If the SOFT~ARE KEY FLAG is set, the
::: ~ ` : :
INSTALL PR~G~AM~:allows for the installation of the
application on many computers. The SOFTWARE KEY PROGRAM
; 25 restrlcts use of ~he application to one computer at a
ti~ This progra~m verifies that a diskette is an
: original or ~erifies authorized copy by making sure that
the bad spo~s are reaîly bad. If the user is turning the
application ON on this computer, it makes sure that the
:
: ~ :
'~"O 93/21582 2 1 3 3 9 ~ ~ PCI/U~93/03669
-15
last thing the SOFTWARE KEY was used for was to turn the
application OFE-. Ir this is true, it replaces a portion
of the application, such as the first 512 bytes with the
real program~ the user is turning the application OFF,
S the first 512 bytes of the application are replaced by the
N(:)TON p~ogram.
This program spawns the ONCE INSTALLE:D
PROTECTION P~OGRAM: to ver~ify that the application program
to be turned off is valid. If it is not valid it is made
10 not usable.
:~
This program also gets a ran~om number and
stores it in the USER DATA record and the (:)NCE INST~LLE:D
PE~OTECTION PROGRAM when ~ the application is turned ON~
This~ can be used: at a later ~ime if the SOFTWARE KEY
lS: D:~SKETTE~ is needed t o ~ v erify that the installed
application program i:s ~really valid.
rke: oex:t p:rogram is the CREATE :EMERGENCY USE
DISKETTE P~.~G~AM, which builds the EMERGENCY USE DISE~ETTE
that~ optionally i9 ~ distributed with the application
20 ~ pack~age ~ :t:o~ provide: ~ emersency use~ of the application
capabilities~. Shoul;d ~ the: instal?ed version o the
application become not: usable, this diskette allows the
user to run the application a f ixed number of times . This
program and the process :that goes with i~t puts bad ~pots
:: ~ 25:: on ~ ~a d;skette and~ formats the diske:~tte, copies a copy of
he ~application program file to the dis3cette, copies the
NOTON program to t~he diskette, copies the scrambled first
: ~ block of the application pFog am to the diskette,
WO93/21582 ~1 3 3 ~ 6 ~ PCT/US93/0366
-16-
scrambles and writes the USER RECORD to a hidden place on
the diskette, and copies the EMERGENCY USE PROGR~M to the
diskette. It then replaces the first block of the
EMERGENCY USE PROGRAM file with the NOTON program, making
the application n~t usable.
Should the installed copy of the application on
the user's computer become unusable, the EMERGENCY USE
DISKETTE with the E~ERGENCY USE PROGRAM can be used to run
: the application. This program verifies its validity using
10: the bad spots: in the same way that the INSTALL PROGRAM
did. It fin.ds, reads and unscrambles the USER RECORD
which keeps track ::of the number of uses left for the
EMERGENCY USE PROGRAM. The number of uses are limited to
:: a ixed~ number defined by the software pu~lisher. It
15~ replace~s::the first block of the application program file
with~a~scrambled:file~containing the real be~inning of the
ile. ~t runs~the~ EME~GENCY USE appLication program. It
then ~replace the~f:irst:block of the application program
ile~:wit~:the NOTO~N progra~, making the app~ication f;le
20~ not:usable~
: : The next~ program is the SPAWNED WRITE/RE~D
ROGRAM.: This program is manually put on the INSTALL
: PROGR~M DISKETTE, the SOFTWARE KEY DISKETTE, and the
EMERGENCY USE PROG~AM DISKETTE. This program is spawned
25 by the INSTALL PROGRAM; the SOFTWARE KEY PRCG~AM, and the
EMERGENCY USE PROGRAM as part of the ~iskPtte verification
~: process. These~:programs do write/read tests o the bad
~:~:: s~pots on the diskette. At ra~dom time5 during this
process they will spawn this program to perform the same
:: :
-~093/21582 21 3 3 9 6 ~ Pcr/uss3/o366g
-17-
: tests. This being a separate prog~am makes it very
difficult fo; an exp2rt t~ terce~t this function and
nullify it. In addition, this program will take its own
: action to termina~e the current program that spawned it.
This makes an effort by:an expert to intercept a returned
value from the WRITE/READ PROGRA~ of no value.
: The next program is the ONCE INSTALLXD
PROTECTION PRO~RAM, which protects the application after
it is installed on the computer's hard disk. This program
is spawned from the IMSTALL PROGRAM, the application
rogram, and ~;he SOFTWARE KEY PROGRAM to verify that the
insta~led application is the file installed by the INST~LL
PROGRA~. Data used in the verify process, such as the
phy~sical cluster addresses of the application progr~m ~nd
lS t~e ONCE INSTALLED PROTEC~ION P~OGRAM, the random number
s~tored~in the ONCE~INSTALLED PROTECTION PR~GRAM and the
:USER~DA$A record on:the diskette, and other file names are
physically stored in a scrambled manner in places in this
progr~am file rather :than stored in a separate file. This
20:: makes it ~ery di:ficul for someone to find this data and
~ try;~ to manipulate~ it without destroying other data or
: : ~ : : p~ogfam code.
Description of the Drawings
The procedures and programs of the invention
~provide a relia~1e copy protection mechanism for software
publishers. It comprises up to l0 major steps, set orth
in `Figure l. Not all steps ~re always used, as some are
~: ~ optional. Step~10 is the creation of the APPLICATION
:: :
:
WO93/215~2 2 1 3 3 9 6 ~ PCT/U~93/036~9
-l8-
DISKETTE, a protected diskette for distribution of the
a~plication proglam. ~his diskette contains a scrambled
ve~sion of the appiication program and a hidden scrambled
copy of a USER RECORD~. Step 20: is execution of the
INSTALL PROGRAM which unscrambles the application and
installs it on the user's computer. Step 30 creates tne
SOFTWARE KEY DISKETTE. Step 40 is execution of the
:~ SOFT'~ARE KEY program which allows the user to turn tr.e
~: application OFF and ON on different computers. Step 42
creates the EMERGENCY USE DISKETTE. Step 44 is execution
;~ ~of the EMERGENCY ~SE PROGR~M~ Step 46 is the execution of
the C)N~::E INSTALLED PROTEC~ION PROGRAM. Step 47 is the
SPAWNED WRITE/READ~ ~PP~OGRAM ~hich is used by 'che INST~LL
:
: ~ PROG~AM, ~he SOFTWARE KEY PROGRAM, and the EMERGENCY USE
PROGRAM ~o do write/reads of diskette sectors. Having
this ~ separate program makes the testing of bad and good
diskettes more sec~e.:
CREATE~ l~EPLICATION DIS~ETTE
:: :
Step l0 that creates the APPLICATION DISKETTE
20 consists of 7 lower leYel steps ~see:Figure 2)~ The first
of~ the.se (step; 50~ is to put physical bad spots on the
disket~e. Such bad~spots are se tions o~ the medium,. in
this case a magnetic diskette, that cannot be successfully
writ:ten to or read~::from. A~number of methods may be used
,
~: 25: to :accomplish this result. For instance,: a laser may be
: : used to burn a small hole in or otherwise flaw the read~
~: write surfac2 of the dis~ette. Creation of bad spots by
: la~er is illustrated in Figure 20. Step 50 may also be
accomplished mechanical1y by usin7 a sharp edge to scrape
:: .
~ ~93/21582 ~ ~ 3 3 9 6 0 . PCT/US93/03669
:.....
--19--
the surface of the disket~e. The laser method is believed
preferable in a mass pro~uction environment. Por reasons
that become more evident later, the effects of putting bad
spots on the diskettes in random locations is better than
:~ ~ 5: putting them in the same area on the diskette.
:
~ The next s~ep (s~ep 60) is to format the
,
diskette. Mos~:computers come with a software program to
:perform this~function~.~;The format function sets up the
dis~kette sectors and ~ tracks making it usable by the
10 ~ computer 's file system. In addition to this the format
unction creates; ~ ~ d~ FILE ~ ALLOC.~T~ON T~LE (PAT) on the
kette. ~he FAT is:used by the computer's file system
o keep~ track of::disk~sectors and how they are used. It
indica~es~ which sectors~are:f:re~ for use, which are in
15:~ ~ use~ a~d ~ which are~ ad . and cannot be used because the
physi~al;~status of~that~ section~o the ~disk is damaged~
This~ s~very~ 1mpor~tant~ in connection with the~present
in~:e~ntion~because~there~are.products on the mark~t that
will :~copy ;di~skettes ~as~they ar~e with the ~AT i~dicating
20~ bad~s~pots~:that were~on~the:origiAal:diskette. Prot:ection
me~hanisms~ that w~uld;~se the bad spots~:in the protection
echa~ism will still~think the bad spots:are val~d on the
copi e~d~:~ ve rsion .~
Step 62 copies the ONCE INSTALLE~ PROT~CTION
2~ ::PROGRAM to the diskette. : ~ :
Step 70~1~S ~o;copy tne application ~program to
the~diskette. This~:st~ep may use the copy facility that is
asually: supplied with the computer. In a production
: ~ :
W~93/21S82 2 1 3 ~ 9 6 0 PCT/VS93/03669~ ,
-; ;~, .
-20-
environment this step may be omitted and the program can
be copied dynamlcally in the scrambie procedure of step
O
: 5tep 74 is to copy the SPAWNED WRITE/READ
S PROGRA~ to the diskette, This program is used in the
diskette verification process.
:~ Step ~80 is to copy the NOTON program to the
diskette. This program, which may be very small, is used
to replace the first part of the application program if
the ~SOFTW M E KEY: option is desired by the software
publisher.
The CREATE APPLICATION ~ISKETTE PROGRAM (step
90) is then run~ This program consists of l0 lower level
steps:,~ which are~ shown in Figure 3 and described below~
l5~:CREATE~APPLICATION~DIS~ETTE PROGRAM
The first function of tnis ?rogram is to create
: or ~ead an exis~ing:~ customer reco~d ~step l00). Thi~
rec~rd ~ has: information about the application prog~am and
the de5ired opti~ns`~ of the software pub:lisher. This
~:~ 20 :~ecord can be created or modified ~en the program sta~ts.
It may contain a ~ flag indicating: tha~ the software
;pub1isher~ does: or~: does not wish to use th SOFTWARE KEY
:option
:: :
Step 110 ge'cs the diskette type information.
25 This is followed: by step 120 which reads the boot sector
::: ~
r~-~93/21S82 PCT/US93/03669
~ ~ 3 3 9 6 0
--21--
of the diskette. In this case, using an IBM PC
environment, 'hese two steps provide the information about
the d~ skette. Such things: as the number o tracks on the
diskette, the number of sectors per track and the number
:~ ~ 5 o~ sec~ors per cluster are provided in these steps.
: ~ The F~T sectors are read in step 130. This
tells the progr:am~which sectors are yood and bad. In the
embodiment shown, the first 20 bad spots are saved.
Step:140:asks for optional user information.
l0:; This step is:not part oE the:software protection aspect of
the invention but:is included as an additional feature for
the~;software:~publisher. It~contaiAs such things as name
and~addr:ess information, product serial number, and the
SOFTWARE~RE~F~AG~
15 ~ 5tep~:142~ uses a formula that uses ~he bad spot
:locati~ons and the~:;nùmber of times the appli~cation has been
reinstalled ~to~ produ~ce a number. ~This is done for a
number o~ reins~talls~a~llowed by the ~software publisher.
A~ this~ime;:this is just~a list o~:the~e nu~bers as they
2~ would be:genera~ted~b~y:the reinstall ~proce5~ This will
allow~the~user to::~al~1 the pu~lishe;r and ask E~r reinstall
; , capability should something happen to the user's installed
appl~cation~ This~number cou~d be given to~the user over
the~ph:one~allowing~the applicatioA to~ be reinstalled. If
25~ a~use~r:ca~1s with~such a request the publisher will record
the call and be able~to keep track of~the reinstalls. The
ormula could be~assigned a number~ and ~his number saved
: in the USER DATA RECORD.
:: : :
:
WO93/21582 PCT/VS93/03669~
21~
-22-
Step 150 takes a global modulus factor ! file
st_tus, and use ~alue that are in the customer record and
puts them into the USER RECORD which gets scrambled and
hidden on the diskette. Later, at install time, these
variables must be correct in order for the installation to
work properly.
The scramble and write function (step 160? uses
;the location of:the bad spots together with the modulus
factor in ~he USER RECORD to scramble the file. The
formulas used for this scramble may vary g~eAtly from what
is described here. This function consists of a program
loop that abes through the program file described below in
: steps 180 through 240 shown in Figure 4.
; ; Step 180~ reads 2 sector-sized blocks of the
5~::appl:ica;tion program file. Step 190 creates a scramble
: va~riable. This i;s put after the reads in the loop to
; allow for using the block number as a variable in the
ramble variable :calculatiQn, which however is not done
i:n the em~odiment:desc~ibed. The scramblP variable is
20~ used ~in the scramble algorithm to make the file not
usabl~u : ~
Step 200 takes the scramble variable number of
~i:bits in a 16 bit word and swaps them with the remalni~g
bits 0n the other side of the word. For example, the
25~ cluster number o~ the second bad spot on the diskette may
~ : be used as a basP, whicn is divided by 16 and the
:;:remainder added to the modulus in the USER ~ECORD to get
: :
:: :
.~ V093/21582 PCT/US93/03669
213`3360`
-23-
: the scramble va:riable. If this number is qreater ~han 16,
16 is subtracted rom it.
Step 210 ~further scrambles the block by swapping
~bytes in the blo k according to the scramble variable.
5~ Step 220 writes th~e ile by swapping the two blocks that
are~currently ln:memory.~ The pro~ram checks for the end
of file at step 230. If it is not at the end of file, the
r~outine returns to step 180. If it is at the end of the
~:: file, it continues to step 240 which returns to step 170.
10 ;~ There~ ar~e~a~large number Oe other algorithms in
addition to the one described here which would adequately
pèr~f~rm~the s~cramble~and write file step 160.
he prog~ram proceeds to step 170 of Figure 3,
which~;scr:ambles~the~;USER RECORD and; hides it on the
15~ di:sk~e~tte:. Thi:s record is hidden by u ing the bad spots as
the~ke~y~. ;The recor~d ls~ritten to a good sector on ~he
diskette~ The~:~ile:: system ~will not :know it is there.
Thi~s~step consists;~o~f lower level:steps 250 through 300
shown:~ n Figure~5~and descri~ed belov,~ :
20~ Step 250:creates~a scramble~:~variable just as was
done in s~tep l90 excep~ that the modulus number in the
:: h~ USER~ RECORD is ~not used. This: is~because the INSTALL
p~rogram will not: be able to get~ this ~ariable to
:unscramble itsel:f at in~tall ti~me. The USER R~CORD is
25~scrambled ln steps~260 and 270, such ~as in the same manr,er
~ that the: application program blocks were scrambled in
- ~: ~: : : : :
~ : :
:
W~93J21~2 2 1 3 3 9 ~ O pCT/~93/~36~9~ .
-~4-
Figure 4. The program finds the first 16 unused sectors
on the diskette in step 280.
In step 290 the program writes junk data~ This
i5 done to confuse someone looking for the data record.
The format procedure initializes the empty sectors~ which
means that any~hin~ that looks different may be the USER
: RECORD.
: Step 300 a tually writes the scrambled USER
: RECORD ~to the ~record corresponding to the scramble
: 10 v~riable in the 16 good sectors. ~9Z instance, if the
s:cramble variable is 7, the USER RECORD is written to the
~: 7th good s~ctor. :~
:
: : The p~ogram then returns to step 172 which
scrambles and writes~;the:INSTALLED PROTEC~ION PROG~AM to
the diskette in~:the same manner that:step 160 scrambled
:; and wrote the appIication file to the diskette.
: It is important to note that this record and its
lo~:tion is not~ known to the ile syst~em or operati~g
:: : : :
5y5~em of ~he computerO` Unlike other pro ection
~:~ 20 mechanisms using hidden files: which may be ~o~ated by
: so~tware ~ programs, this data cannot be found and
identif;ed by s~oftware without knowing the finding
~ algorithm first~
:: :
:`
.
,
.~ g3/21582 2 1 ~; 3 g ~ 3/03669
--25--
INSTAI,L P~:OGRAM
The INSTALL program, illustrated in Pigures 6a
and 6b, uses the diskette that was created by the CREATE
, ,
APPLICA~ION DISKETTE: PROGRAM and allows the user to
:5~ install the application on his computer. If the SOFTW M E
KEY~option is being~:~used, the user~ may install the
application on many: computers in an unusable state. It
must be turned ON by ~ the SOFTWARE KEY before it can be
used.:
10~ In ste~ 302 the install program checks to see if
the~ use;r~wi:shes::~to~ uninstall the already installed
appli~cat:i~on~ pr~ogramO~; If ~ the user ~ does wish to do an
un~instal1~, control~is~;passed to step 3~04;:~ which ~is the
un:install~process~ This will;be de:s ribed later. If this
S~ `is;~ ot~t~he user's wish~the program checks:to see if the
us~er-~wi~shes to do~a~ reinstall in~step 306.~;:If this is the
casè:the~program~perfor~ms step 308~which is the rei:nstall
p~ocedure~ :this is not the case:control is passed to
step 310~which~:star~t~s~ the;install proc~ess. ~(Step 304, the
20~ U~INS~ALL~PROCESS~(Figur~e;233, and ~Btep ~08~ the REINST~L~
PROCEDURE~ :Figure~33~ are desc~ribed later.)~
The TNSTALL~program ~ust get the disk t~pe æata
and~ boot : sector~d~ata in thè ~same~way:that the CREATE
APPLICATION ~DISKETTE~PROGRAM` did in ste;ps 110 and 120, a:nd
:2~5~ read~ t~he FAT ;:sectors as was done~in step 130. It does
t~his~in steps 310 through 330. It then~ses through the
FAT ~o identify~the:bad spots (step 340).
,: ::::: ~ :
::: : :
WO93/~1582 213 3 9 6 0 PCT/US93~03669 ~ ?
-26-
Step 322 may appear out of place, but~has an
important value. Steps 322 and 324 a e used to .protect
against a user copysng the installed software in a
: ~ speciic manner. Once the application is installed, a
~ ~;5 user could copy the application program file and the
: spawned ONCE INSTALLED P~OTECTION PROG~AM file on a sector
by sector b~sis, keeping track of each sector and its
physical sector address.: The user could the~ run the
SOFT~ARE KEY PROGR~M to turn the application O~F. The
user could copy the sectors back to the disk, which leave~
~: it in an O~: condition. The user could then use the
SOFTWARE K~EY DIsKE$TE:to turn the application ON on
anoth~r ~compute~,: leavin~ 2 running copies. To prevent
this:~the~TURN O~F~function of the SOFT~ ME KEY PROGRAM
;15 changes ehe name of the ONCE INSTALLED PROTECTIQN PROG~AM
; and~truncates it.::~:The new name of the new file is stored
in -the USER D~A RECORD on:all of the diskett:es, but is
one o~ many, making the predictabilit:y difficult. This
process:~also exists:: if the SOFTWARE KEY OPTION is no~
Z0~ used.~ The uninsta11, install process will produce the
, same~ res;ults ~for~the user. Checking ~o 5ee if this file
exis~ts~in :step 322~ and:~ writing to it ~ in step 324 means
ha~, if ~ a user~wri'ses the ~iles back :to 'ch~ disk sectQr
by sector,: the~ONCE INSTALLED P~OTECTI~N PROG~AM f;le will
25 ! no~ be in :the: f le directory and the user may have
destroyed his file~direc~ory structure by writing over a
sm~ller file.: ~he: process that creates this smaller
truncated:file also:~writes many s~.all files to the disk to
increase the :probability of destroying the dire~tory
~; 30~ structure of the:~i1e system. It should be noted that
~: this process performs no actions outside of those normally
:
: :~
~ 093/21~82 2 1 3 3 ~ ~ ~ PCT/US93/03669
-27-
,
allowed by the computer's file system. It would ~e t~e
user's illegal action that is destructive.
In step 350 the program verifies the bad spots.
: I:t translates the bad spot cluster number that is stored
5 ~ in ~ :th~ FAT table into Head, Track, and Sector values.
: These values are used to do a physical write and read of
these: sectors. This is done without going through the
file system which is usually used to:read and write to the
;dis~kette.~ If the wr~ites:or the reads are not successful,
thQ d3;ske~te has a ve~y high probabili~y of being an
ari~ginal appllcation~di~stribution diskette and not a copy.
SQme~of t~he sectors: ~wi:ll return su~cessfully from the
wr~ites~ and :reads~,~ but i~ they are all good, the diskette
is~s~copy:.~There;are~computer experts capable, with a lot
;l5~:of:~time~and:work:,~of using DEBUG mechanisms to find places
in~`programs where~::input/output: functions are going onO
They`~ may~ examine~ what~ is happening here and chan~e the
program;to branch around this write/read:code, return the
éxpected~r~eturn;code~and continue. In ~his case, however,
20~the~program~9et~s~;~a~ra~ndom number and either performs the
wr~ite/read~rout;ine~on~a~known good~sector or a bad sector.
The~ rèturns f~rom a~:good sector must~a1ways:~be goodO If
they~ are not:the`program is:terminated.~ The return from
the;~bad sector wr~ite/reads can be good:or bad, but some
25 ~must;~be bad. ;Th~i~s;~makes~i~t very difficult for a person to
:m~ determin what is~expectéd by the program~ To further
make~:it:d;~ficul:t for a computer expert to avoid the copy
p:ro~ection~, the~program gets another random number. It
uses this number to~determine which of several, duplicate
30~ write/r ad routines that are distrlbuted throughout the
, : :
,
: :
.
:
WO93/21~82 21 3 3 9 6 0 - PCT/US93/03~9~-
-28-
program is used. This means that after an expert spe~ds
time finding the location of the code he wants to monitor,
he cannot predict if or when it will be used again, or or
what reason ~good sector test or bad sector test3 it will
~: 5 be used again.
One additional scheme adding to the problems of
the expert out to break~the protection is that at random
: times throughout the write/read test process the install
process will spawn a separate program to do the write/read
10~ test. (See ~Figure~:~8). Step ~70 gets a random number.
Step 472 reduces~ this random numb~r to a number used to
: make a:determination. ~Step 474 makes the determirlation of
which write/read~;rout;ine to use in the program, or to
spawn: a separa~te ~write/read program.
5~ he SPAWNED WRITEjREAD PROGRAM is shown in
Figur~ 24. Step 1710 does the write~read o~ the sector
pass~d as~ an argument~ This program can look at the ~AT
:and~determine if::~a~good write/read or bad write/read is
expected4 If the:wr~ite/read results are a5 expected step
20~ 1730 returns a:good~value. If they are not~ step 1740
e~ases the app1ication program. Then step 1750 returns a
bad value. This~makes it very difficult for the expert
ecause most debu:ggers will not work on two programs at
: the same: time~ Thi~s ~SPAWNED WRITE/READ PROGRAM can also
` 25 take~action on its:own;if the results from the write~reads
:
are n~t what was expected. This means that the expert's
actions to intercept the returns ~rom the spawned program
: will not allow the~ expert to bypass the application's
protection.
,
'~.. V093/21582 2 133 3 ~ P~T/US93/0366g
.
:
Step 360 tests the return from the routine that
verifies the bad spots. If the return indicates that all
of the bad spots are not really bad, the program stops and
will not continue with the installation. The verify bad
~::5~ s:pots step consis~ts of:lower level steps 420 through 466
shown in Figure 7.
Steps~420 through 466 perform the actual tests
of the bad sectors to:insure that some of the bad sector~
:~ are really bad. While this is happening some write/r~ ~
10 ;~o~f~ good:~sectors be~done;:to confuse any attempt to ool the
pr~g~am:by using a~DEBUG~mechanism to return an expected
retur~n ~code :from~ ~the write/read routines. There are
;severa:1 of these~routines~to make it more d:ifficult for
someone tryin~ to:break;;;the protection.
5~Step q20 sets~a:~random number. This can be done
wit~h~ random n;um~er ~eneration routin~ or~ simply by
get~lng~ the ~cu~rren~t: system: time ~if it in ludes a
mil~lisecond~va1~e~ ;If~the ~alue is e~en, a write/read
test~ w~ be perfor~med on~a good sector rather than a bad
C ~ O~ one~ If ~this ~mechanism is~ int:~ercepted :by a ~ DEB~G
mecha~ism,~:and;~à~`bad~return is~in~jected into the pr~ocess
by u5ing the D~BUGGER,~the program will ~terminate~. Step
:43~ passes contr;o1 ~to st;ep 460 ~-hich picks a write/read
rou;tin~e~or spa~Ds~ the;~WRlT~/READ PROGRAM to execute for
25~ th~e~ good sector.:~:There are severa~l~of these write/read
sec:tor routines in~t~he program in different p~aces to make
it~di~f~icult~ ~or~:anyone to predict which routine w:ill be
used.::~Step 460 is~comprised~ of lower le~el steps 470
through 480 show~ ln Figure 8.
: ~ ~ : . ........
W093/2~582 PCT/USg3~03~6~
21~39~
-30-
Step 470 qets another random number. Step 472
divides this number by the number of writejread routines
in. the program + 1. If the remainder i5 0, step 474
passes control to step 476, which spawns the WRITE/REA~
S PROGRAM. The remainder is used in step 480 to pick the
write/read routine to use.
: Step 462 actually calls the picked write/read
`~routine to test the good sector~ Step 464 tests to see if
the return was a good write/read. If it was, control is
: 10 ~as5ed~ :back to step 420 to continue and try again, else
s~ep 466~ returns an~ "invalid diskettei' code and the
progr~m will terminate.
If the nu~ber: generated in step 420 was odd,
control~passes to;step 432 which performs the pick write/
15~ r~ad~ sector rou~tine~:(steps 470 throùgh 480). Step 434
calls:~h:e write/re~ad of the possibly bad sector. Step 436
tests~;th ~return:~to see if the sec~or was bad. If it w~s
bad,~step:438 adds~l to a bad flag vari:~le. Steps 436~
i ~the:: r~etur:n was~good, and step 438~oth:~9O to step 440
to che~k~i:f it has:gone through enough bad spots (e.g. 20
:: in: the routine shown). If enough bad spots have not been
tested~ l is added~to:the number of tries in:step 450 and
the routine goes back to step 4~0 to get a new random
: :number. If enou~h bad:spots have been tested, a check is
25~ pe~rformed in step 4~42 to see if any o~ the bad sectors
: we~e:~really badO :If ~he answer is yes, a "valid diskette"
va~lue~ is returned~in step ~44, else an~"invalid diskette"
value is returned in step 446.
~ 93/215~2 2 1 3 3 ~ 6 ~ ` PC~/US93/03669
-31-
If the bad spots indicated in the FAT are al1
good, the program stops the installation in step 370. If
some of the bad spots are really bad the program continues
to step 380, which ~inds and unscrambles the USER RECORD.
Step 380 has lower level steps 490 throu9h 530 shown in
Figure 9.
:~ The unscramble formulas must be the reverse of
~ the scramble ormul~s u~ed in the CREATE APPLICATION
: :~ program. If they are rot, the application file will not
be usable after the install. In addition, the l~cation of
~: ::: the bad spots on the in~tallation diskette must ~e in the
sam~ places as they were during the CREATE APP~IC~TION
program. Also, the bad spots indicated:in the F~T mus~
: : contain~some sectors that are really bad~ In add~t~on,
~the USER ~RECORD must u~scramble to a valid record. In
addi~tion,~the modulus actor in the USER RECORD must be
;the:same as:~he~USER~RECORD modulus factor when:~he CREATE
APPLI~ATION program was run~ If any of the~e are not as
they~ should be, the unscramble will not work or will not
~20~ wor:k proper~y.
: Step;490 of the unscramble USER RECO~D procedure
; gets :a ~scra~ble variable value based on the locat-on of
the:bad spots. This:step is the same as s~ep 250 ;n the
CREATE APPLICATION program. Step 500 is the same as step
25~ 280 in the CREATE:APPLICA~ION program and find~ the fi~st
2~0 good unused se~tors on the d1skette. Step Sl0 reads
the good sector corresponding to tr.~e scramble variable.
Step 520 unscrambles each 16 bit word in the reverse
.
manner that step 260 scrambled each 16 bit word did in the
~ :
WO93/21582 . ~ PCT/VS93~03669 .
213~9~
CREATE APPLICATION program. Step 520 reverses the e.fects
~f step 270. At this point the USER RECORD is in memory
and the modulus factor:may::be accessed.
Step 390 (Figure 62) checks to see if the USER
S RECORD is valid by checking the modulus for a valid value
be~ween 3 and 14. I~ can also be checked by using a check
digited serial number if the software publisher desires an
~ ~ additional level of valldation. Other validity checks may
: also be used. If the USER RECORD is not valid, the
l0~ i~nstallation is stop~ed at step 400. If the USER RECORD
is ~a~id the program proceeds to step 410. Step 410
:
: uns:cram~les and installs the application program file on
the user~'s compu:~er. Steps 540 through ~30 shown in
,
Figure 10 are lower:level steps of step 410.
;15~: :Step 540 asks the user what the n2me of the
pr~ogram to install is::and the path to install it to on the
use~ '~s : Gomputer . In~ a production mode ~he ~irst question
:~: would:~:not be asked ~as it would be built into ~he INSTALL
pr~gram. ~ ~
20: ~ Steps 550~ ~ through 600 are buil~ to unscramb~e
the scrambling done~ i~n steps }80 through 230 of the C~EATE
APPLICATION pro~ram (see Figure 103.; Step 550 rea~s two,
~512 byte blocks of the application program file. Step 560
creates the scrambl:e~variable from the location of the bad
spots and the USER RECORD modulus factorO step s70
: reverses the scra~ble number of bits in each word in the
vpposite manner than was done in step 200 of the CREATE
~PP~ICATION program~ Step 580 unscrambles the words
~-~vo 93/2~5g2 2 1 3 3 9 6 ~ PCT/U~93/03669
-33-
within the block in the reverse manner of step 210 of the
CREATE APPLICATION program. Step 590 writes ~he blocks,
~eversing the order of the two blocks it is working on, to
the file of the path the u~er specified in step 540. The
:5 pr:ogram checks ~or end of file in step 600. If end of
file has no~ been reached~ the program returns to step
s50.
When end of the file has been reached, the
program th~n checks the USER R~CORD to see if the SO~TWARE
~: 10 KEY opt;on is on for this software publisher's program.
If it is not, the program returns to step 410. If the use
o ~be SO~TWARE ~EY option is on, the program replaces the
fi~s:t 512 bytes ~of the installed program file with the
NOTON program. This~renders the program not usable and
l5~requires~the use of~;the~SOFTWARE KEY to turn it ON.
After ~the application file has been installed,
the:~INS~ALL program~performs the set ~p procedure, step
41:2, :~or: the ONCE ~IN5~ALLED SOFTWARE PROTECTION. This
consists of a spawned ONCE INSTALLED PROTECTION PROGRAM
: :20~ that~will be usèd:~to ensure that the:installed application
: program file is the one originally installed and not a
copy.~ ~ This program is written with some memory constants
set to specific values allowing the INST~LL program to
ind them and change them. These constants will be
~; 25 replao d with systPm values that identify the hard disk
: and the ;nstalle;d app~lication program ~ile as those
: originally instal}ed. This is done in step 412 which
:consists of lower level steps 1280 through step 1400 as
shown i~ ~igures 21a and 21b.
::
WO93/21582 213 3 9 6 0 PCT/US93/03669 ~.
Step 1280 unscrambles and copies the ONCE
INSTALLED PROTECTION PROGRAM to the installation disk from
the diskette. Step 1290 looks for the firs~ constant of a
: predetermined pattern in the file. The constants are set
at program compile time. The constant is replaced with
the ASCII character ~alue of the physical cluster address
of the beginning of the application file in step 1300.
: Step 1310 finds the next constant. step 1320 replaces
this with the ASCI:I character value of the first cluster
address of the ONCE INSTALLED PROTECTION PROGRAM f ile .
:~ This ensures that the program files are valid at execution
time because when the once installed protection check is
done these values must be equal to the current actual
cluster addresses~. ~Fun~tions in the UNINSTALL process and
SOFT~RE KEY process (changing the name of the ONCE
STA~LED PROTE~T~ON PROG~AM:file and shortening it) make
it nearly impossi~le to copy these iles off and replace
them. Steps 1330 through 1350 loop:, putting the names of
dummy file~s into the ONCE INSTAL~ED PROTECTION PROG~AM.
One of these :files will later ha~è needed data in it.
: : These files also w~ill create:problems or someone tryi~g
; : to copy off the application ile and ONCE INSTALLED
PROT~CT~ON PRO~gAM f ile and replace them after
~ unins~alling or~ turning the appli~ation O~. Step 1360
,~: 25~ creates and writes these files. Step 1370 does the BUILD
SY5TEM VERIFY DATA process. Most computers will tell you
: the version of ~he operating system now in use. This can
be used as one step in system veri~ication. If the
~:~ application is moved to a computer with a different
: 30 version of the operating system, this check will return a
bad value.
.
--~093/21582 ~ 13 3 9 ~ O PCT/US93/03669
-35-
There are 3 lower level steps to step .1370.
They.are shown in Figure 25. Step 1760 gets the operating
system version. Step 1770 gets the hardware
configuration. This ~ay be in the ~orm of a set of words;: 5 stored in the operating system or ma~ be gathered by
looking for registered peripher~ls. Step 1780 stores this
~: information in the U5ER DATA RECORD structure in memory.
Figure 26:~shows the 7 Iower level steps that
make up step 1380. : The function of this set of steps is
~o record a set of traits of ~he hard disk that may ~e
: ~ tested at a later time to determine that this hard disk is
he one that the applic2tion was installed on. This step
coll~ec~ts: data: used: to identify the hard disk that the
application i5 instal~led on. If the~application is ~opied
15~ ~ to a disk on another computer, it will not pass this test
and~will not run.~ Step 1790 :sets~ the location of a
: ; pre:determined~ num~er of bad spots or as many a may exist
;up to:this number.~ Step:1800 reads each bad spot a ~u~er
of~times:.~ Man~ hard ;disks are supplied by the
20~ manufacturer~ with~a list of bad spots. The fil~e system o
almost 311 computers ~will never ha~e raason to write to
:the~se~locationsO~ :A~trait of magneti:c disks is that a
secto~ t~a~ :is marginal may read bad some tim2s and good
;at other times. .~ The manufacturer usually tests these
spots to a finer margin than can the disk drive itse1f~
:When the disk is formatted, the format function will write
a recognizable pattern to the disk sectors. By reading
the~ bad spot a number of times, the amount o~ the sector
that is currently: not stable may be determined. Sectors
with small bad spots may often be able to be written to
W~93~1582 PCr/US93/03~6g,-.
2133960
-36-
and often su~cessfully. In their current state, these bad
spots will not read properly because they were left with a
bad block check character. A block check character is a
piece of data that is calculated from dat~ in the data
block written to the sector. This block check character,
often called the CCR, does not agree with the data in the
sector for these sectors. By determining i the bad
section of this sector is small, we can guess that there
is a good probability that if this sector is written to,
it will write and read correotly. ~Tests have verified
that this happens much of the time). I in the future
~: this sector is read, and the read is good (the data agrees
with the CCR), it ~.eans that this sector has been written
~: to indica~in~ that an individual sector by sector copy of
the disk has taken plac~. If the bad section of the ~d
: sector is small, control is passed to step 1830, which
: marks the sector as a ~'maybe good" bad spot in a data
: structure. If the bad section of the sector is large, the
::~;: sector is marked as a "should be bad" bad spot in the data
structure. Both steps 1830 and 1820 pass to step 1840
which sav~s ~he bit patent of a section of bits close to
the good sector pattern. This may later be tested to
determine the possibility that this sector was written to.
StQp 1850- store this data as a data structure~ Con~rol
is then passed to step 1390 which scrambles this data.
Step 1400 then writes it to a dummy file.
It can also be of value to put real data into
the good section of some o~ these sectors. Th;s will
~: serve to require that a sector by sector copy be re~uired
to read/write the bad spots as well as the g~od sectors.
,- ~W093~ 82 213~1~60 ; PCT/US93/03669
CREATE SOFTWARE KEY DISKETTE
This program, shown in Figures 11 and 12,
creates a diskette called the SOFTWARE KEY D~SKETTE. It
is used to turn the application that may be installed on
:5 many computers, ON and OF~ while insuring that it will be
ON on no more than~one computer at a time.
,
: ~ Step 6:40 consists of making physical bad spots
on the diskette in the same manner done in step 50 for the
CREATE APPLICATION: DISKETTE procedure. This diskette is
lO~ then formatted (ste:p~650) as in step ~0. Step 660 copies
th~ SOFTWARE KEY program to this diskette. Step 664
copies~ the SPAWNED WRITE/READ PROGRAM to th;s diskette.
S~ep~ :6~70 runs the CREAT SOPTW~RE KEY PROGRAM. This step
consists of lower:level steps 680 through 750 shown in
:lS; Fi:~ure 12.
,
CREATE 5~F~WARE KEY DISKE ~ E PROGRA~
his ~program copies the NOTON program and the
first ~512 bytes~:of~ the : application program (file
STBLK.ABC~ to the SOFTW ~ E KEY DISKE~TE. Step 680 reads
: 20 t~e custome~ reco~rd.~ Step 690 gets ~he disk type data.
Step 700~ reads the boot sector. Step 71~ reads the FAT
sectors and gets the first 20 bad spots~ Step 720 puts
: the~modulus factor and file status into the user record in
: me~mory. This data` is copi~d from the cus~omer record.
:: 25 Step 730 copies the NOTON program file to this diskette.
Step 740 copies the first block o the application program
to the diskette.~ ~t is put in a file called FSTBLK.ABC,
W093~21582 PCT/~S93/036~9 ~
2 1 3 3 9 6 ~ !;
-38-
; in the present example. Step 750 scrambles and writes the
: USER RECORD to a hid~:en location on the diskette and may use the method shown ln Figure 5.
Many o~the:above step function descriptions are
5 ~the same as steps in :the CREATE APPLICATION DISKETTE
:::~:: :~func:tions. ~ ;
SOFTWARE~KEY PROGRAM
, . :
~: :
:This~program, shown in Figure 13a and 13b, is on
the ~SOFTWARE ~KEY~; DISRETTE and is used to turn the
10 ~ nstalled~appli;cation~ON or O~F on~a computer.
:: Turning the:app1ication OFF invo1ves rep1acing
the~Çirst~5l2~byte block:of the:applicat~ion~;~program with a
smal1~:p~rog~ram that~tel1s the user that::the app1;cation is
turned~ :OFF. ~ The~ program: also updates the hidden VSER
15~RECORD~on~t~his~diskette setting: the~status to a value
indicat~ing~ ~tha;t~ t~h~e~ last thing ~it; ~did was turn the
application;OFF:;.~ ;;The s~tatus-~:must~be that~the last action
was:~to turn ::~the~app1ication OF~before i:t can turn the
app1ication~0N~on~an~:~rom*uter. Tur:ning thq application
20~0N ~involve;s read~ing~and~unscrambling~the file~;-FSTBLK.A8C,
which~is :the first~:~512 bytes~of ~he application program.
IE the status:::is~;correct, the~ SOFTWA~ ~EY PROGRAM
replaces~ the~NOTON pr~ogram~in:the ~irst~512: bytes ~of the
app1ication~progra~m fi~le with the re:a1 ~irst 512 bytes o
25~the~appl:ication~;program file~. ;Turning~ ~the: appli~cation on
: ::a1so ::gets a: ~:rand~m number that is stored in the ONCE
INSTALLED PROTECTION PROGRAM and the USER~ DATA record
:~:
~: :: :
~:~
:
~ W093/21~B2 2 13 39 ~-~ PCT/US93/03669
-39-
which is used for validity tests in other places. This
program also spawns the ONCE INSTALLED PROTECTIO~ PROGRAM
to verify that the installed application program is valid
and not a copy. It al50 performs functions that will
: 5: create problems for the user if other illegal copy schemes
: : are tried. The SOFT~ARE KEY PROGRAM description follows.
Step 760 gets disk type information, as was done
in step 110 of the CREATE APPLICATION DISKETTE: programO
Step 770 reads disk set up information as was done in step
: ~ ~ 10 120. Step 780 ~read~s the FAT sectors and step 79C
identifies the f;rst 20 bad spsts and the fi~st 20 good
spots. ~ ~
: : Step 800~ verifies the bad spots as was done in
:step:~:50;of the INSTALL program and may use the me~hod
lS~ shown in ~igure 7. Step 8l0 passes control to step 820 i
the bad spots are not really bad. ~Step 820 stops the
- :p~ogram and does~::not change.the status of the application.
If some: o~ the ~ad:spots are really bad~ control goes to
step 830. Step~830 gets and unscrambles the USER RECORD
, ~ ~
2~ the same manner:that the INSTALL program did in step
:380.~ At this point step ~40 (Figure }3b)~checks the
validity o the:USER RECO~D. The modulus value must be
between 3 and 14 and the status code must be 23332 or
32223. If this t;es~ is not passed step 850 stops the
25:~program and :leaves the st~tus of~the application on this
: computer unchanged.
~ If the test is passed, the p~rogram proceeds to
- :: : step 85~ which spawns the ONCE IN5TALLED PROTECTION
:
WO93/2158~ PC~/US93/03~69~
2133~6~
-4Q-
PROGRAM. This step consists of the lower level steps 1410
through 1620 snown in Figures 22a and 22b.
This spaw~ed program tests data that was stored
in it during the install process with data retrieved from
the computer's file system. Step 1429 gets the physical
disk location of the ONCE INSTALLED PROTECTION PROGRAM.
: ~ Step 1430 checks to see that this location is equal to the
value stored in the ONCE INSTALLED PROTECTION PROGRAM. If
they ~re not, control is passed to step 1490 which can
erase the application program file and will return a bad
va:lue to the SOFTW~RE KEY:P~OGRAM which will not continue.
:~ If the test is good,:step 1440 will get the actual disk
clust~er of the~application program fiIe. This must match
~ with the data~stored in the ONCE INSTALLED PROTECTION
N~ 15 PROG~M or step 1450 ~passes co~trol to step 1490,
terminating the process. The disk location is used as a
al~i;dity ~test because only one file can have this disk
add~ress, thus a copy~ of the :application prog~am file
cannot: be turned~off. If this test is passed, step 1~50
2~0~ passes control to~step 1460, which will get the first X
bad: :spots .on the~ hard disk. Almost all hard disks have
: bad; : spots. The : ~:bad~ spots: provide a way of uni~ue~y
identi~y;ng~ the~ installed hard disk. Thus, copying the
~installed application program file:to another hard disk
2~ will make the SO~TWARE KEY PROGRAM not function. Step
:14~0~makes sure that the bad spots put into the ONCE
INSTALLED PROTECTION PROGRAM at installation time are on
the current hard disko If they are not, control is passed
to step -149~ to erase the application and return a bad
- 30 value. If they arev control continues to s~ep 15n~ which
:
~ V~93/~15~2 PCTJUS93/03~69
~133~6~
-41-
checks ~or the dummy file that should have the built
system verification data and hard disk verification data
:in a scrambled form. Step 1510 reads the dummy file and
unscrambles the data.~ Step 1520 does the SYSTEM V~RIFY
procedure. This step has 5 lower level s~eps shown in
Figure 2~.
St~ep l a 6 0 gets the current operating system
version. Step 1870 checks this aqainst the version that
was stored in the dummy record. If they are not equal, a
"not valid" value is re~turnedO If they are equal, con~rol
is pa~sed to step 1880 which checks the hardware list with
: the~ :lis~: stored in~ the dummy record. If they are not
equali a "not~valid" value is return~d; otherwise step
189~0 returns a "good~value".
l5~ : If ~the returned value is good, s~ep 1540 does
:;the~ Hard Di:sk Ver~ify~:procedure~ This procedure is made up
o~lower~level:stèps~ 1910 through 2060 shown in FIgure 28.
: The ~dummy :file which contains a data structure
:wi~h bad spot data~as been read. Step 1910 goes through
this st~ucture;: to~; see if there are any bad spots with
small bad:sections. If any "maybe ,ood" bad spots exist,
they are read in step 1930. If they read as "good" it
: ~ : means that: they :were never bad and we are not on the
original install hard disk or that:someone has w:ritten to
25 them, which means that someone has tried to break the
protection. In either case a "no good" value is retur:nedO
This "~o good" : value will require that the original
IN5TALL DISKETTE or SOFTWARE KEY DISKETTE be used to
: ~
.
::
WO93/21582 1 PCT~US93/036~9 ~,
2 ~
-42-
.
verify the installed application program. I~ the "maybe
go~d" bad SpOt:a re~d as~ "bad", c~ntrol passes to step
; 1920, which checks the~bad spot data structure for "should
be bad" bad~ spot~s. If~there are none of these, control
5~ passes to step 1930 which, returns a "good value". If
the~re are some "sh~ould be~ bad" bad spots. Step 1960 starts
a~loop to veriy these~bad spots~ The~ reason for this set
of~ s~eps is to ~ensure~ that someone does not copy the
enti~ré~hard~disk~ sector by sector, turn the application
10~ OFF or uninstall it so that it can be TURNED ON or
reinstalled~on another computer, and restore the hard disk
sector ~by~ sector~ ;Wh~n~ data ;s writt`en to ~isk bad
sectors~ data around the~bad part of the~sector changes to
a ~ ~ ticeab~le~degree.~ ;That is, it is possi~ble to~detec~
` ~jn~da~t~a is~writte~n to a bad~sector, even if it is the
s~ame~-~dàta~that was~read~from the sector.
Step 1960 reads the bad spot. Step 1970 does a
bit~;pàttern;~test~ T~his~tes~ts ~the~bi~ts~closest to the good
p~t~of~the bad~ sect~or.~This is~de~termi~ned by pi cking
20`~bits~close~ to~the~correct pattern~;w~r~itten~by formatting
p~og~ram.~ ``If~ the~di~f~ference ~etween~thesè bits and those
s:to~ed~ in~ the~:dat:a~structu~e is small, the test is passed
a~control;is~passed~to step 2~020~which~gets the~n~ext ba~
spot and continues~the loop. IE the test is not passed,
25; control goes to ~step ~1980, which determines if the bit
pa~t~tern~is close~a~nd~most likely good. (~ad spots do~ get
worse with-~time,~ This~step~notes the slow change in a bad
;spot.~ If the~test~is;~questionable,;not~pas~sing the test
in ~step 1970,; ~but not ~bad enough to go to step 2000,
30~ control is passed~-to~ step 1990. This s~ep takes -the
:: ~- ~ i :
: : ~
-~YO93/21582 ~ " `~CT/US93/~3669
213~9~
current bit pattern of the special section of the sector
and writes it ir.to ~he b~d spot dat~ structure. There is
then a new test bit patt rn for this sector. Tf the test
in step 1980 does not pass as questionable, control passes
:~ S to step 2000 which will verify that the sector is really
: ~ bad and most likely:has been written to. If the sector
: tests as "no good", 1 is added to bad totals in step 2010.
If this is not the case, control is passed to step 2020 to
cont;nue the loop. When the loop is an`end as determined
: 10 by step 2030, contr~ol passes to step 2040. This step
: calculates the percentage of sectors determined to have
been altered versus tho~e that have passed the tests in
:steps 1970, 1980,~ and 2000 as not a1tered. This
percentage is not tested against 0. It is possible, but
not ~expected, that the expectations be tested within
predetermin~d bounds.~ They may not exactly match the
e:xpe~tations~ because bad spots will not always act in a
predi~ct:ed:manner. ~If the "bad totals" are not within
~bou~ds, step ~050:returns a "no good" value. If the "bad
totalst'~ are ~ithi~bounds, step 2060 returns a "goodl'
,
alue. ; -~ .
Control;is returned to step lSSO o If the re~urn
va~lue~is "good"~ con~rol is passed to: step lSÇ0, which
returns a "good" ~:value to step 854. If the test is not
passed, control pas~ses to step 1570. The next set of
: steps is performed if the system verify test or hard disk
~ verify ~est are not passed. The system test and hard disk
:: test may fail on very rare occasions even though the user
:: has not trîed to steal the application software. If is
possible for the system verify test to fail if the user
WO93/21582 PCT/US93/03b69 ~-
2i~39~0 ~s
-44
installs a new operating system or adds new hardware to
the computer. The hard disk ver~fy may ~ail if the bad
spots take an unexpected~turn for t~e worse. (Bad spots
~ ~ do grow, but the system will, in most cases, k~ep track of
,~ ~ 5~a-nd~ ad~ust to the~changes of the bad spots.) Step 1570
checks to see i the SOFTWARE KEY o~tion is on. If it is,
co~tro1 is passed~ to step 1580, whi h requests the
SOPqW M E`~KEY DISKETTE. If not, step 1590 requests the
STALL DISKETTE.~ Both of these steps lead to step 1600,
10 ~ whIch~ does an ~absolute verify that the installed software
app~ication is~the;~valid current ve~sion or the origina1
prog~a~.~ ~ This~ ~is~done bv comp2ring the stored random
; nu'mbe~r`~stored l~n the~USER DATA RECO~D on he diskette and
n~the~ONCE INSTALbED PQOTECTION PROGRAM during the C~EAT~
lS~ ON~E~ STALLED~PROTECTION~ procedure. ~;If this test is
passed,,~step 16l0~r~e-crea~es the ONCE INSTA~LED PROTECTION
meé~ ni5mO~ If~the test is not passed,~step 1620 ~performs
the~"DOES NOT~ PASS"~procedure, which;ma~kes~ the application
n~t~usabl~
: ao~ Re~uIri~ng~the use of the~SOFTWARE KEY DISKETTE
oF~the~INST~LL DISKETTE for absolu~e ve:rification of ~his
Qpy~of~the application ensures tha'~the ailure of~ the
system~erifica,~ion~or har~d dis.k~ve~rification will not
k~ the~application~ hen they shou'~d not. This, however,
25~ shou1d~seldom happen.
ontro;l~ returns to ste~ 854. If a ~Ino good"
value:~is~:~returned~ control passès to step 850, which stops
:the program. If~ the return is "cood:" control passes to
step 860. ~
::: :
~093/21582 PCT/US93~03669
''-` 2f~96~'
-45-
I~ t~ test is passed, step 854 proceeds to step
860 w~lich asks the user if he wishes to turn the
application ON or OFF. Step 870 checks the user's intent.
I the user wants to turn the appli~ation ON step 880
checks to see if the status in the USER ~E~ORD, indicates
us that the last action taken by the SOFTWARE KEY program
was to turn ~e application OFF. If not, control is
passed to step 8~0. If yes, control passes to step 890
:~ : which checks to see if the program is already on. This
: lQ should not be possible. The chPck consists of searching
~:~ th~ first 512 bytes~of the application program file for
the string value, "THE~PROGR~M IS TURNED OFF". If this is
ound the NOTON program is the first block of the
application file, indicating us that the program is turned
15~ OF~ Con:trol is passed to step 900 which performs the
TUR~ 9N procedure. :This step is made up of the 9 lowe~
level: ~eps from 2070 to~150 shown in ~igure 29. Step
: 2070~ chec~ks to~see~he ON flag in the USER DATA re~ord is
on~ If i~t~is not,~:control passes to step 2100 and the
20:~proce~s can continue.: ~I it is ON, control passes to step
20;9:0, which checks to~see if the random number s~ored in
:the~: USER DATA re~ord is e~ual to the number s~ored in the
NCE~ IN~TALLED PROTECTION PROGRA~. This number was
~ . :
cr~ted and stored~:durin~ ~he last TUR~ 0~ processO If
the:ON flag is set and the numbers matchr t~is program is
:~ ~ already 0~ and~ valid. An error message is producPd in
step~2092 and step 2094 returns to step 8600 I the ON
~:
flag i5 set and the numbers do not ~atrh, this appliction
is on and not valid. In this case control passes to step
30~: 2~80 ~whIch performs the DOES NOT PASS procedure. This
: ~ procedure makes this copy of the~application not usable.
~-:
;
2133960
W093/2~582 PCT/USg3/03~69
-46-
,
Th~e DOES:NOT PASS procedure is shown insteps
~: 2310 throu~h 2360. 5tep 2310 cnanges the name of the O~CE
`
INSTALLED PROTECTION PROGRAM. Step 2320 makes this file
shorter~ than it ~i~s. Step 2330 writes to this new file.
5 The: reason for thèse steps :is to leave the file system in
a ~uestionable s~tate::~if a special program tr es to copy
the program files off ~of the disk in a sector mode and
::late:r replace them in the same place. If this is done,.
~ the~file system~wi;ll~not find the ONCE~ INST~LLED PROGRAM
- ~ 10 in the same ~pla~ce~ Other checking functions will check
for this~file and wr~ te~to~it, destroying ~the overlayed
copy~of~the:ONCE:~INSTAL~ED PROTECTION PROG~AM. Step 2340
de~l:etes~a:ny dummy~fil~es~that may exist. :Step 2350 creates
;new~ dummy~ ~iles~whi~le~step 2360 write:s to them in volumes
15~ great~er~ than~1 clu~ster~ These steps raise the possibil~ty
that~ f~ es~ will~be~written in places where the old ONCE
INSTA~LED:PROT CTION:PROG~AM was. ~rf these :ile areas are
.ove~:r;written~ by~a:~ program restoring ~the ONCE INSTA~L~D
PROT~TION~PRORAM,~t~he~application~prog~ram will nat ru~O
20~:The~ O~E~ IN5TAL~E~ PROGRAM must be~complete, in the same
p~ace~as: befor:e~ access:ible by the file:system. The dummy
f~iles~ mus~ :exist`;~also ~for the appl:i~ation~to run as the
NE~INSTALLEV PROTECTION PROG ~ will look for them.
Step 21~00~writes over the file that re;placed the
25~ ONCE~: INSTA~D ~PROTECTIOM PROGRAM.:~ This will~make:a not
valid~copy of the;~ONCE~INSTALLED ~PROTETION PROGRAM ~ not
usa~le~ Step 2110~writes over the dummy files and deletes
:t~em.~ Thi:s also can~create problems if a user has :done
abnormal things to;~ the disk i~n an~effoEt to c~py the
3~0~ ~applic~tion program. Step 2120 ~does the BUILD SY5TEM
~ , ~
, .
~ ,
:: :
~ .
~093/21582 - PCT/US93/03669
2133~
-47-
VE~I~Y. Step 2130 does the BUIL~ HARD DISK VERIFY. These
functions must be done because the previous step destroyed
this data in the dummy~files. Step 2140 copies the first
block of the application back to th2 first block of the
~ 5 applic~tion program file. Step 2150 perform~ the ONCE
: INSTALLED PROTECTION process.
: ~ ~ If the user wants to turn the application O~F in
~ :step B70, control: goes to step 910 which checks the
: current status to make sure the last a~tion taken by this
program was to turn the application ON. I~ this is not
the ca~e, an error~message is returned to the user and
cont~ol is: passed~ to step 860. If this is the case,
cont~rol~:is passed to step 920 to see if the application
program~:file on this computer is ~lready OFF. I ît is an
e~rror~message is returned to the user and control is
:pa~ssed~: to step 8~0.~ If it is not, control passes to step
930~which~performs~:the TURN OFF procedure shown in ~igure
30 .; ~ ~ This step cons~ists of 12 lower level steps that turn
the~application OFF~i all vali ity chesks are passed.
:20;~ ~ ~ S~ep 2160 checks the on/off flag in the ~SER
DA~ re~ordO If it is OFF~ contrsl is passed to step 2162
which gives:the user an error message~telling him that the
: : S appli~ation is already off.: Step 2164 then passes control
::: back to step 8~0. ~f the flag was ON, step 2180 checks
25~ the random numbe~ that was stored in the~USER DAT~ record
:: :and the ONCE INSTALL D PROTECTION PROGRAM. If ~hese
numbers are not the same, there is~a problem that should
: : :not exist un~ess someone has tried to put together a not
: :
valid copy of the application. In this case control
W093/21582 21 -33~ 6~ i p~T/US93/03669 t~ ~ ~
: -48-
passes to step 2170 which performs the DOES NOT PASS
procedure. Th~s makes thls cop~ of the application not
: ~ : usable. This was described earlier. If the numbers are
equal control ~passes~-to s'tep 2190 which changes the name
5~ o~: the ONCE INSTALLÉD~PROTECTION PROGRAM. : S;tep 2200 then
sh~or~tens~ the : i~1e.~ As~described earlier, this step
pr~vents someone from~copying the application and ONCE
NSTALLÉD PROTECT~I~N: PROGRAM on a sector by sector basis
and`copying the flles~back after the turn ~OFF function.
10 ::St~ep~22:10 does~ a~S~YSTEM VERIFY while step 2220 does a HARD
DISK~VERIFY. If~ ei~ther::~of:these steps are not passed, the
DOES~;NOT~PASS~funct:ion is~performed in~step 2240 makinq
the-:~:app1ication u~n~u;sab~le~. If ~they are ;~ b~oth passed, the
N~TON~ pr~g~ram~ is;:~ ;copied to ~:the~ firs:t: bloc~ : of the
l5~app1ica;ti~on~program~:file~, making;~the~ application~ progra~
:unusab}e~ After;~the:~successful~execution of steps 900 or
930,~contro1~passes~ ~tD~:step~940 which~ updates the: USER
;RE¢ORD~ S`tep~9~50~ scramble:s:,~ writ~e~s~and hides the ~SER
ORD~or~the~d~skette.~ Step 960 ~terminates the program.
O~ CREATE EVERGENCY~USE"DISKETTE~
This ~p~rogam,;~ shown in~igures 14~ and 15,
créates ~a disk~et~te~alled the~EMERGENCY~USE~DISKETTE. It
:IS ~:used:to run:the'::~application:~in~ th:e event that the
installed copy,~of~ the::applicatlon;~ cannot be run.' The
Z5~ number:~of:~times~ 'that,~,~ the EMERGENCY~ USE copy of the
ppl~i~cat;ion~can~be run~is limit~ed. ;::
Step ~9,7~0~ consists:of making physical bad~spots
on:the~disk~tte in~:the same m~nner done in step 50 for the
~ 93t21582 2133`~ ; PCT/US93/03~9
49-
CREATE APPLICATION DISKETTE procedure. This diskette is
then formatted (step 580) as in step 60. Step 990 copies
the.APPLIC~TION PROGRAM to this diskette. Step 994 copies
the ~PAWNED WRITE,~READ PROGRAM to the diskette. Step l000
S runs the CREATE EMERGENCY USE DISKETTE PROGRAM. This step
consists of lower level steps l0l0 through l090 shown in
Figure 15.
CRE~TE EMERGENCY USE DISRETTE: PRO~RAM
This program copies the APPLICATION PROGRAM, in
l0~ a TURNED O~ mode, the N~TO~ program, and the first 5l2
bytes~ of the application program (FSTBLK.~C) to the
E~ERGENCY USE DISKETTE.
Step l0l0 reads the customer record. Step l020
gets the disk type da~a. S~ep 1030 reads the boot sector.
15~ 5t~ep 1040 reads the PAT sectors and~gets the first 20 bad
s~ots. Step l050 puts the modulus factor, file status,
and~ u:ses :value, which is the. number of times the
:app1i~ation on ;the EMERGENCY USE~DISKETTE will run, into
t~e:user record in~memory. This data is copied from ~he ;: 20 ~cus~tomer record. ~Step l06~ copies the~APPLICATION PROGRAM
f:ile:to t~is diskette. Step 1070~ copies ~he NOTON PROG~M
and ~the first block of the application program to the
diskette. It is put in a ~ile called FSTBLK.ABC~ Step
1080 replaces the ~first 512 bytes of the application
proqram with the NOTON program. Step l090 scrambles and
~: w~ites the USER RECORD to a hidden location on the
diskette.
WO93/21S82 PCT/US~3/~366~
2 ~ 91~6; 0~ ~
.. ~ ~.. .. . .
-50-
Many of the above step function descriptions are
the same: as steps in the CREATE APPLICATION DISKETTE
functions.
~MERGE~CY USE PROGRAM
This program, shown in Figures l6a and 16b, is
~` ~ on the EMERGENCY USE DISKETTE and is u~ed run the
application in emergency situations. It verifies that
: this diske~te is an original and not a copy. It then
:executes ~he APPLlCATION PROGRAM, low~rs the number of
l0~ USES left by one, and terminates.
:Step 1100 gets disk type in~ormation, as was
done~in step ll0 ~of ~the C~EATE: APPLICATION DISKETTE
:p~oyram. Step l~ll0:~reads dîsk set up information as was
done~in:step 120~ 5tep 1120 reads the FAT 5ectors and
15 ;s:tep ll30 identiies~the first 20 bad spots.
Step~ 1140; veriies the ~ad spots as was done in
step~ 3~50~ of the INSTALL program. Step~1l50 passes control
to ~s~tep 1l60 i~the b~d spots are not really bad. Step
:;1160; stops the:p~ogram and does not ~ha~ge the status of
: 20 :the application.~ some of the bad spots are really bad,
control goes to step~1l70. ~Step 1170 gets and unscrambles
:the ~SER RECORD:~in the same manner: that the INSTALL
progra~did in step 380. At this Doint step 118n (Figure
6b) checks:the validity of the USER RECORDo The~modulus
: 25 value mu5t be between 3 ~nd 14 and the statUs code must be
~;; 23332 or 32223. If this test is not passed st~p ll90
: :: :
j~;?~O~3/21582 PCT/US93/03~69
3~3~
stops the program and leaves the status of the application
on this computer unchanged.
,
: If the test is passed, the program proceeds to
: step 120~ which checks to see if there are uses left. IE
5~ there are no uses left, con~rol passes to step 1210 which
stops the program. If~here are uses left, control is
:passed to step 1~20 which reads the FSTBLK.ABC file. This
~ is:the~first 512 bytes of the application p~ogram file.
:: ~ Step 1220 unscrambles this data. Step lZ30 replaces the
10~:first ~block of the appli-ation pro~ram file on the
disk~ette to provide a ~runable copy of the ~pplication
program file. Step 1240 runs the application as a child
pr:o~ess.
~: : :: :
: When the application completes, control is
5~ returned~to the~EMERG ~CY USE program along with a return
code~ i;ndicating~ is~the :run was successful. Step 1250
subt~rac~ts l from the~USES value in ;the USER RECORD. The
USER~ RECORD is:t~hen scrambled and~hidden on the diskette
in s:tep 12~60.
20~ S~ep I270~:replaces the first 512 bytes of the
EMERGENCY US ~APP~ICATIO~ PROGRAM file with ~he NOTON
program making it ~ot usable without going through the
EMERGENCY USE PROGRAM
Figure ~23 shows: the flow :of the UNINSTALL
2S ~PRO~ESS. This process is needed for publishers who choose
: not to use the SOFTWARE KEY option~. It allows the user to
~ ~ move the application software from ~ne ~computer to
: ~:;: :
::
WO93/21~82 PCT/US93/036S9
' ~ X ~ i . ' ;,
2133960- -
-~2-
~: .
another. Step 1630 spawns the ONCE INSTALLED PROTECTION
PROGR~M, whicil performs all of the validity checks
desc~ibed earlier. I the installed application is not
valid, control passes to step 1650, which performs the
S DOES NOT PASS procedure, making the application not
usable. I~ the application is valid, step 1660 deletes
the application program. Step 1670 then performs the DOES
NOT PASS procedure~making the application not us~ble on
t:his computer:. Stèp 168~ marks the application as
uninstalled in the USER DATA record. Step 1690
unscrambles th~ first block of the application program on
: t:he INSTALL DISRETTE.~This is done because the block was
: rescrambled, scramb~led~twice, during the install process.
: S:tep 1700 scrambles~and~writes the USER DATA RECORD to the
15 ~d:iskette. The I~ST~LL DISKETTE is now ready to be
rei~nstalled.
Figure 33 ::shows a flow of the ~EINSTAL~
PROCEDURE. This pr~ocess provides an option for publishers
to~be~able to allow user:s to reinstall the application
:: 20~should the curre~nt~: installed application program get
destroyed. The USER~DATA record will:have a field for the
number~ ~ o reinstalls~done~ and a~number representi~ a
speciflc formula~ The procedure starts by having ~he user
: mount the INSTALL~ DISKETTE in the floppy drive in step
25: 2370~ Step ~-2380 g~ets :and unscrambles the USER DATA
record.: Step:2390 calculates a number ~rom the number of
reinstalls already ~done. This ensu~es that the user
: cannot reinstall the application on several computers
because the calcu:lated number will change in an
;~ ~ 30 unpredictable fashion depending on the number of the
~:
~ 093/21~82 P~T/US93/03669
~ 21~3~9~6~
-53-
reinstall and the location of the bad spots on the
diskette. These nunlbers have be~n recorded by the
publisher when the INSTALL DISKETTE was created. The user
: had to call the publisher to get this magic number. The
R INSTA~L PROCEDURE asks the user to enter this number in
step 2400. Step:2410 checks to see iE the entered number
: is the expected number. I it is not, the reinstall
stops ~ I f the numbers are equal, l gets added to the
number of times the reinstall has been used in step 2430.
If another reinstall is needed in the future, the number
used in this one will not work in the next one. Step 2440
scrambles and wrLtes ~the:USER DATA record to the disk~tte.
: : The re;install then continues.
Figure 31 shows the flow of the installed
:: ~ 15~ application prog:ram t o start the ONCE INSTALI,ED PROTE~TION
PPOCESSi The application spawns the ONCE INSTALI,ED
PROTE~TION PROGRAM. ~ This program then tests to see if it
is on the hard disk. ~ This combined with other steps taken
during the ONCE INSTALLED:PROTECTION PR~RAM ensure~ that
20~ ;the~ correct versl:~ons~of the programs are being used. If
: the~ ONC~E INSTA~LED~ PROTECTION PRVG~ determines that
these are:not as:~they sh~ld be, the installed application
will become not~:usable. In addi~ion, a "bad't value will
e returned to the application program and it will
termina~e itself:. ~ If the return value is "~ood", the
application will~ continueO
Figures 17, 18, and l9 illust rate the . contents
;~ : of diskettes wh:ich may ~e produced in accordance with the
invention. Figure 17 shows an INSTALL PROGRAM DISKETTE
::
wo 93~2lsg2 2 1 ~ ~ 9 6 0 ~ `. ` i- P~T/U~3/036~9
-54-
which contains physical bad spots, hidden user ID
information, the SPA~NED WRITE/READ progra~n, the ONCE
INSTALLED PROTECTION program, a scrambled application file
program, and the INSTALL program. The INSTALL program
verifies the diskette as valid by writing to and reading
~rom bad spots, finds and unscrambles the used
information, unscrambles the application program filP, and
installs the application in a usable form on a user's hard
disk or diskette.
~ F igu r e l B s hows a SOFTWARE KEY DI SKETTE wh i ch
contains physical bad spots, hidden user ID information,
the ~ SOE'TWARE KEY PR~GRAM, the SPAWNED WRITE/READ PROGRAM,
: :and the~files NOTON,COM and ~STBLK.ABC. This diskette is
used to turn an installed application on or off. The
SOFTWARE KEY PROGRAM verifies the diskette as valid by
wrî~ing to and reading from bad spots, finds and
unscrambles the user information, copies the NOTON,COM
file ove:r the first block of the lnstalled application to
:turn~it off, and unscrambles~ and copies the FSTBLK.ABC
:20 : f~il:e~ over the:fir:st block of the installed application to
:
: ~ ~: turn: it ~n.
: : ~ ~ : :
Figure l9 shows an EMERGENCY USE DISKETTE which
may be used ~o run an application if the installed copy of
; the application is ~not usable. The diskette contains
25 :physi~al bad spots, hidden user ID information, a copy of
the appllcation in a turned off mode, the EMERGENCY USE
: programl the SPAWNED WRITE/READ program, and the NOTON.COM
and FSTBLK.ABC flles. The EMERGENCY USE program verifies
~: the diskette as valid by writing to and reading from bad
:
~ ~ 093/21582 2 1 3 3 g 6 0 ~ ~ PCT~US~3/03669
-55-
spots, finds and unscrambles the user information,
unscrambies and copies the FST~LK.ABC file over the first
block of emergency use program to make it usable, runs the
emergency use application program, and copies the
NOTON.COM file over the first block of the EMERGENCY USE
; P~OGRAM to make it not usable.
:
:~
: ~ :
~ :
: .
WO93/21582 . PCT/U~93/03~69.~
21~39;~
-~6-
FILES AND PROGRAMS
Files and programs as listed in the appendix and
described above are as follows.
EXAMINE.EXE - is a program file used as the application
: 5 program for this invention. Functionally the program
: dumps disk files to the screen.
FSTBLK.ABC - is a scrambled copy of the real ~irst 512
bytes of the application program.
MK~PPDSK.EXE - is the program file for the CREATE
:APP:LI~CATION DISKETTE program. This program creates the
d~isket:te that is dist~:ributed to the user
M~E~RAPP.EXE - is~ the EMERGENCY USE program that runs a
copy::`of:th2 application program a limited number of times.
:The~ ~application program run will not run without the
lS~EMEBGENCY~ US~ program~running it.
MKE~RGCY~.EXE ~ s~ ~the program file for the CREATE
EMERGENCY;~USE; DISKETTE program.~ ~ It creates a diskette
allowi~ the us~er~t~o~:run the application if something
~: : destroys the installed application.
20~ MKINSTAL.EXE - is~ the pro~ram ~ile for the INSTALL
: : ~:program. This program is distributed on or with the
APPLICATION DISKETTE and is used to install the
~ ~; application on the user's computer's storage media.
:::,
~093/~1~82 ~ D; . PCT/US93/03669
-5?-
MKONCE.EXE - is the program file of the program spawned by
the IN5TP~LL and SOFTWARE ~EY PLO9raI;IS tO ensure that the
installed application program file is the original and not
a copy.
MKONOPF.EXE - is the program Eile for the SCFTWARE KEY
program. This program file is on the SOFTWARE KEY
diskette and turns an application ON or OFF after it is
installed on a computer.
~ KSFTKEY.EXE - is the program file for the CREATE SOFT~ARE
:~EY ~ISKETTE program. This program creates the SOFTWARE
K~E~ diskette that is used to turn installed application
pr~ograms~ OFF on one computer and GN on~another.
NOTONoCOM~ ~ is the program file for:the NOT ON program.
:: : This i:s a small p~rogram that is u5ed to replace the first
15:~:pa~r~t~ of~ the appllcation program when the application is
turned~ O~F~ This~::pro~ram tells the user that the
application is not~usable and then terminates.
: W~ITR~AD.EXE - is :~the program file~f~r the WRITE/READ
:
PrO9Fam. This:program is spawned by the INSTALL, SOFTWARE
Z0~:::KEY~ and EMERGENCY USE p~ograms.
:::: : : :
':
:~ :
~: :
WO93/21582 ~ ~ PiCT/US93/03669'~,
-58-
CUSTOME~ RECORD
The following is the re~ord layout of the
customer record as it may be used in this invention~ It
is expressed in the 'C' language. In a production
environment there would be one such record Eor every
: product of a software publisher.
struct cur cust /*curr~ent customer data*/
:; {int modulos; /*changable value used in the scramble/
~: unscrambl:e calculations*/
char exext321;; /*path o~ application program file*~
char cust name(30]; /*software publisher name*/
c~ar cust addll30]; /*software publisher address*/
char cust add21301;~ :
: char cust cityf 20 ];
15 ~char :~ust s~atel3];
: char cust zip~lO~
` cha~ cust soft ey[2]; /*are w doinq a software key Y or
N*/
char cust mem protect~2]; /*are ~e doing memory protect Y
or~N not used*/
char user_fla~!:21;~:/**/
int:uses; ~*number af uses allowed ~o~ emergency use
: application*/
long disk made; /*number of diskettes produced*/}
: 25 ~cur cust;
~ :
::
i~Y 93/215~2 ~`133~` P~T/US93/03669
_59_
USE~ RECORD
The ~o:llowing is the record layout of the
cus:tomer record as it may be used in this invention. This
re~ord is on the various diskette5 and is required to qet
:5:~ the modulos factor:to:unscrambIe various iles~ It may
also be acces:sed ~y~he application at the option of the
softwar~ publisher.~ ~
struct user_id /*user data*/
{~int~modulos: /*value~used in unscramble calculations*/
char s~erial~I6]~;/*~optional serial number for use by the
appii~ca~tl~on*/~: :
char~;name[3~03; /*user~name~and address or optional use by
:: the~applica~ion*/
char~addl~30~
lS~ cha~r~add2[~3~0];
char:~city[~0~
char~s~ta~te[~3];
char~zi~p[~10]~
t:~;~um r:~ei:n:stal~l:s, /*used to:generat~ and veri~y code
20~ numbers~:that allow for reins~allation*/
:: in~t: r~einstall formul:a~;~:/*used:to allow~:fo~ variable
formulas~t~o~gene:rate a:reinsta~l code*j
int:~uninstall_flag;:/*c~oded flag to indicate that the
application~was last uninstalled*~
25~ char~cust soft_key[~;2]~;~ /*are we:doing~a software key*/
char~ cust mem protectl~2:1; /*are we doing memory protect*/
char::exex[32];~/*appl:ication path*/
unsigned status;~:j*status of the installed application
: program:file*~:: 30 int filler[200];}
user_id;
:
W093/2l582 21 3 3 9 6 Q ; PCT/US93/03669
-60-
GLOSSARY
Followi~g is a glossary of terms used in this
patent appllcation.
: application - is a program created for sale by a software
publisher.
: bad spots - are sectors:on a magnetic or optical media
that cannot be successfully written to and read from.
; ~When the media goes through a formatting procedure
required to:make:it usable on the computer the file system
o~f the~computer often pu~ a file allocation table on the
media that points to free space on ~he media and defines
sectors ~n:the media th~t are bad spots.
;:
~ : block: -~for: this invention is defined as 512 bytes of
:~ ~ :: data. ::
15~ check digited :- a number whose d;gits used in a formula
result in one digit of ~he number.
cluster - sequential disk sectors accessed by the
computer's file~system as a unit.
; : customer recor~d - is a data record that contains
20: in~o~mation about the software pu~lisher, the application,
and protection options the software publisher has chosen
for this application.
: ~
~093/21582 ~!- PCT~US93/03669
21 339 6~ 3~
-61-
diskette - is a magnetic or optical information media used
by many computers. Diskettes are usually removable and
::~ are used to distribute data and programs for computers.
~ . file - a set of data stored on a media such as a disk~
; 5 file allocation table (FAT) - is a table maintained ~y the
file sy~tem of most computers that specify which disk
sectors on a disk are~used, ree or use, or bad spots.
file system - the parts~ of a computers operating system
that dea~ with managing data on a stora~e media.
10: formatting - is a ~pr~cess, usually a program provided with
the computer, that makes diskettes usable tG the
computer's ~ile~ system. It consists of putting timing
ma:~ks~on the disk:ette,~finding and marking bad spots, and
defi~ning the track~and sectors on the diskette.
5~ pa:th;-:is an ascii st~ring describin~ the location and name
of a~file to a computerls file system.
protected software ~-:is a sotware program, stored as a
;ile~ ;on a mag~netic or op~ical storage mediay that is
protected from unauthorized copying and use.
:
software publisher -~produces software for sale. This is
often distributed on~magnetic diskettes.
software producer:- i5 the same as software publisher.
: : ~:
:~
W~93/21582 2 1 3 ~ 9 6~ P~T/US93/03669;~
-~2-
user - The person using the protected software.
VSER ~EG~RD - is a data record that is hidden on the
INSTA~LATION diskette and the SOFTWA~E KEY diskette that
contains ~nformation about the pur~hasing user. Included
: 5 in this record is the scramble modulus used to unscramble
data and the options chosen by the sotware publisher.
use :value - is a value in the USER RECORD that is used by
the EMERGENCY USE program to keep track of how many times
the EMERGENCY USE can be used.
While ~referred embodiments of the invention
have~been described, variations will no doubt occur to
those skilled in the art without departing from the spirit
a~nd~s~cope of the invention.
:` ~: :
:: :: ` :: :
`
:~`::: ~: :
:~
~: