Note: Descriptions are shown in the official language in which they were submitted.
2140~6~
BACKGROUND OF THE INVENTION
Field of the in~ention
The present invention is directed to a teleco"~",~ tions access-control
system. More particularly, the present invention is concerned with an access-control
device and method for providing a password plotec~d intPrfase between a serving
system (as for eY~mple Private Branch FYch~nEe, Voice-Mail and Cellular systems)and a plurality of access codes resident in a user's memory device.
Des~ tion of the related art
Public and private co~ "~ tinn ntlwul~ use ~witchillg systems referred to
as Central Office and Private Branch Swilchillg (PBX) systems, for inlercoll,lecting
the calling parties with the called parties. Typically, a calling party is connected to
a ~wilching system which responds to dialling instructions gP.neratPA by the calling
party to selectively inl~l~;o~ Pctin~ the calling party with called parties iflPntified by
the ~ llinE instructions.
Swilchillg systems are inlefcollllected by commllni~tion netwolk~. In this
way a customer, who is conn-Pcted to calling parties of a ~wilclling system, can access
other s.~vitching systems over the communi~-~tion n~wolL
Cullelllly, in order to provide the telephone users easy access to long-distanceservices, the majority of PBX systems are configured such that many of the PBX'stelephones are ~siEn~Pcl various classes of services which provide for high calling
privileges, the user just dials the required number.
However, since the advances in COIll~Ulel technology have made electronic
info~"lation nelwol~ a highly effi~iPnt tool for business and private sector, the
problem of una~lthori__d access to the network has became more and more
~ignifif~nt This approach leaves the telephones vulnerable to various forms of
un~llthorized use, both intPrn~lly and PYPrn~lly, since under this configuration,
anyone can use the telephone and the caller can not be irlentifiP~
Most PBX's have the ability to employ "authori_ation codes", each
~lthori7~tion code with its own calling privileges. By issuing individual authorization
codes, each with its a~pn~iate access privilege, the telephones can be a~ nPd a
- 1 -
21405~4
more secure toll denied class of service and users making toll calls must prior to
(li~lline the telephone number, use their authorization code which tcmpol~ily
overrides the telephone's ~ign~ class of service.
The ~llthori7~tion code used to make the call can be inclll~ed in the call record
S which allows the call to be coll~lated to the person placing the call.
Nevertheless, even where ~lthori7~tion codes are used, they are usually kept
short (4-6 digits) making it easier for the user to enter the codes, but less secure. To
be effective, the codes should be longer (8 or more digits), as the longer the codes
are, the better p~teclion could be obtained.
In ~ ition~ the current method does not plcvent the unauthorized use of
another person's ~l~thori7~tion code.
Similar problems are encount~lcd by the user's of voice-mail and mllltimedi~
systems. Voice-mail and mllltim~li~ systems assign mailboxes to individuals, as well
as to system functions. Each mailbox has a number and a password. To access the
contenl~ of the mailbox, a user must first enter the mailbox number followed by the
It~ password.
As in the case of the PBX ~llthori7~tion codes, to f~-ilit~te user access to themailbox, the mailbox passwords are kept short. This approach makes it easier for the
user but jeopardizes the secwity of the mail system and its contcnls.
Cullcnlly, to access a voice mailbox, the user must dial the voice-mail
telephone number (usually 4 digits) followed by the mailbox number (4 or more
digits) followed by the mailbox password (4-16 digits). The use of this sequence of
12 to 24 digits discourages the use of longer mailbox passwords which, in turn,
produces a relatively insecure voice-mail system.
Also, as in the case of the ~llth~ri7~tion codes, this method does not plcvent
the unauthorized use of another person's mailbox password.
In case of the current genel~lion of cellular telephones a Mobile T~entific~tionNumber (MIN) is t~n~mitt~ to the cellular carrier at the beginnil-g of each call.
The MIN is stored in a resident nonvolatile memory and i(l~ntifi~s the user to the
cellular network for billing ~ul~oses.
However, this approach has some drawbacks. Anyone who has access to the
device can place calls and the costs will be applied to the owner of the device. If the
- 2 -
- 21~0S64
device is lost or stolen, it can be used to place calls. As well, a MIN can be easily
copied and used in clones of the device. This makes for a very insecure system.
Also, cellular phones that comle;l to PBX f~ilitiPs such as long~ Pnce
circuits, Direct Inward System Access (DISA), voice-mail or mllltimPAi~ mailboxes
5 will be confronted with the same access-control problems described earlier for the
PBX and voice-mail ~y~",s.
Although there are ~;u~ lly some memory-card based teleco"""l~ tion~
s~",s, such as that disclosed in U.S. Patent No. 4,759,056 to Akiyama, that can
be used to store access codes, it does not provide the user with local (l~ in~l level)
10 password protected access to the contellls of the card. Once the card is inserted into
the card reader, its conle~ are au~...~ lly ro~ ed, without user password
validation. The Akiyama system is convenient but certainly not secure enough forits application.
Another memory-card based system is disclosed in Application for ~n~ n
Patent 2,016,935 to Sato which teaches storing telephone numbers and IDs in a
"smart card". However, with this system, when the card is inserted into the cardreader the card's speech charge and/orID is aulu...~ lly displayed or uttered
without user password validation. The system has the co"vel~ience of storing
telephone numbers and user ID but it does not have the capability to provide secure
20 password access to the conlellls of the memory device.
SUMMARY OF THE INVENTION
Although the system of the present invention can be applied to any
telecommlmit~tion~ environmPnt the p~r~lled embcYlim~-nt~ will deal with the PBX25 e,lviroll",ent, voice-mail and cellular devices, such as cellular telephones.An object of the present invention is to provide individual users with a secure,password pr~cled easy-to-use method of carrying and lltili7ing a plurality of access
codes and passwords.
Another object of the present invention is to f~rilit~te the use of longer, more30 secure access codes and passwords.
2140564
Another object of this invention is to provide an enhanced seculity of the
PBX's te ..~in~l~ and toll circuits, since the tçrmin~l~ can be ~ nP~ a toll restricted
class of service which can be le~ uily overridd~Pn with an authorization code.
Still another object of the present invention is to provide teleco.. ~ tinns
5 ~dmini~tr~tors and managers with a secure, easy-to-use method of issuing and
~lmini~tçring user passwords and access codes, while se~uring the
teleco...l.lu,-i~tion~ systems from un~l-thorized use (hereinafter called toll fraud) both
intPrn~lly and eYt~Prn~lly.
The present invention provides a system and a method for solving the
10 shollcolllil gs or d~PficiP-n~iPs in the PBX ellvi~ ent, to fully restrict the
telecomm~mic~tions devices (telephones, etc.) and use long (8 or more digits)
~llthori7~tion~ codes that are securely stored in a password pr~cled "smart card" in
conjunction with an access-control module conll-P~;~d to the PBX t-prmin~ Such
system and method provides the user with a secure, password p~olecled, collvellient
15 and user friendly telecommuni~tions access-control system where the "smart card"
is used to store and rolw~d the user's ~uthori7~tion code which can lelllpoldlily
override the tP-....in~l's restrictions with the use(s) own restriction profile or calling
privileges.
In ~ lition, the present invention provides a system and a method for solving
20 the shol~lllillgs or dçfic;çnciçs in the voice-mail environment to use secure long (8
or more digits) mail-box passwords that are securely stored in a password protected
"smart card" and, in conjunction with an access-control module conn~ted to the
tçrmin~l~ provide the user with a secure (password prole.;led), convenient,
user-friendly access-control system to voice-mail where the "smart card" is used to
25 store and folw~d the user's mail-box number and password.
According to one aspect of the present invention, there is provided an
access-control system for a teleco..~ tions network which connects a serving
telecomm--nit~tions system conn-P~tçd to a plurality of telecomm-mi(~tions access
t-Prmin~l~, compri~ing: (a) at least one portable memory device card, for storing a
30 resident PIN of an user and a COll~ i,ponding tr~n~ction profile defined by a number
of access authori7~tion codes and idçntific~tion data ~soci~tPd with each ~llthori7~tion
code, and for v~ ting a user's PIN; (b) an access-control module comprising: input
'-' 21~0564
means for receivillg said user's PIN and for s~1~ting a plef~ d tran~f~tion fromsaid tran~tion profile; means for reading said tran~tion profile from said card and
for reading a selected access allthori7~tion code and a~ ted idPntifi~tion data
collG~onding to said pl~r~ d tran~ction; display means for displaying said
5 tr~n~ction profile; means for conn~ting said module to a telecomm-mi~tions access
l~ ",inal for tran~"i~l;ng said selected access authori_ation code and ~ ted
ntifi~tion data to said serving teleco,lllll~lni~tions system over said
teleco"""~ tions network for eY~uting said pr~f~ d tran~ction; and control
means for controlling said input means, said means for reading, said display means
10 and said means for connecting, for tr~n~mitting said selected access authori7~tion code
and ~SQci~t~ idçntific~tion data to said means for conne;ling.
According to another aspect of the present invention, there is provided a
method for ~ ing and controlling a teleco...l,,llnic~tions network which connects
a serving telecommuni~tions system to a plurality of telecomm mir~tions access
15 le~ Illin~ls, compri~ing the steps of: writing in a portable memory device card, at an
authori7~d central issuing system, a resident PIN and a transaction profile for a user,
said tran~tion profile being defined by a number of access allthori7~tion codes and
Wontifi~tion data associated to each of said authorization code; introducing said card
into a means for reading provided at a teleco"""~ tions access t~rmin~l; i,~ulling
20 an user's PIN on input means at said teleco"""~lni~tions access tPrminal and
tran~mitting said users's PIN to said card; validating said user's PIN, reading said
transaction profile from said card and displaying said tranC~rtion profile on a display
means; selectinp a prerelled tran~ction on said input means; reading from said card
an access ~llthori7~tion code and associated i(iPntification data co~ onding to said
25 ~lcfellc d tran~tion; tran~mitting said select~d access authorization code and
~ci~tPd identification data for said ~ef~lled tran~tion to said telecon~",ll.-i~ ~tion
network.
Advantageously, the system and the method of the present invention provide
users with a more secure and user-friendly controlled access to teleco"""~l,-i~tion~
30 f~cilitiPs such as Private Branch FYchange (PBX) long-distance circuits, Centrex
long-distance circuits, cellular circuits, voice-mail and mllltimedia systems. This is
- 2 1 ~ 4
because the present invention greatly f~ilit~t~s the use of ~llthori7~tion codes, since
the user does not have to dial the preambles or long authorization codes.
The user need not even know their authorization code, since it is stored on the
"smart card" and autom~tir~lly dialled by the system when the user selects the
5 a~?pr~liate option to place a toll call.
The system and the method provided by the present invention also façilit~te
voice-mail access procedures since the user does not have to dial the voice-mailtelephone number, mailbox nu~bel and mailbox password. The PIN stored on the
"smart card" and verified by the user during the call introduces a second level of
10 se;uli~y previously not available. If the card is lost or stolen, it can not be used
without the user's PIN.
In addition, the system f~ilit~t~s and adds a level of security previously
unavailable for the distribution of access codes used in the PBX and voice-mail
environments, providing for a more secure means of storing and using access codes
15 and the like, than is cullclllly available, thus enh~ncing the s~;ulily of the PBX's,
mailboxes and cellular phones by use of much longer ~llthori7~tion codes.
Another advantage of this system is that it provides benefits to the
teleco"""~ ~tions a~lmini~tr~tors by f~cilit~ting the issuing, distribution and
~mini~tration of user pasi,~or~s. Each user is issued a "smart card" that contains
20 a user's Personal Tdentifi~tion Number (PIN) plus all of the user's passwords. The
telecomm~1nic~tions ~mini~tr~tors and managers are provided with a secure,
easy-to-use method which will f~.-ilit~te and extend the use of PYi~ting
telecommllni~tions featules such as authorization codes and voice-mailpasswords and
add an additional level of se~;ulily, or password, to prevent the lm~llthori7~ use of
25 passwords and access codes. The passwords can include: ~llthori7~tion code for
access to long-~ t~n~e circuits, Direct Inward System Access (DISA) password,
calling-card n~ he.l ~ telephone-station control password, voice-mail or mllltim~
mailbox password and account codes.
The card, when used in a cellular device, can also include, when and where
30 pçrmi~ihle, the Mobile IdPntifi~tion Number (MIN) that cellular phones or devices
trAn~mit to the cellular carrier at the beginnil-g of each call. The MIN identifies the
user to the cellular network for billing ~ul~ses.
- 2140$64
Still another advantage of the present invention is that since the authorizationcode is stored on the "smart card", the user does not have to copy his/her code,which in effect would be a coll~proll~ise.
BRIEF DESCRIPTION OF THE DRAVVINGS
These and other realuf~s of the invention will become more ap~ nt from the
following description in which reference is made to the appended drawings, wherein:
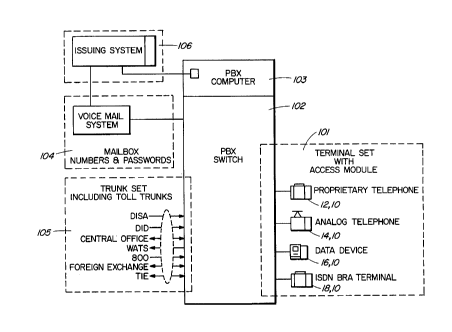
Figure 1 illl~str~tes a block lii~r~m of the system of the present invention, ina PBX and Voice Pnxes.~;ng ~llvilo~ nt~;
Figure 2 illu~tr~tes a block diagram of the system of the present invention, in
a cellular ellvilolllnent;
Eigure 3 shows a block diagram of an access module according to the present
invention;
F gure 4A is the first part of a flow-chart illl~$tr~ting the method for acces~ing
a serving telecommllnic~tion~ system using a password plu~i~d card and access
module of the present invention; and
Figure 4B is the second part of the flow-chart illustrated in E~gure 4A
DESCRIPTION OF TEIE ~REEl~RRED EMBODIMENI
Figure 1 illll~tr~tP.s a block ~li~r~m of the system for ~ce-s~ing a PBX and
voice pr~ccs~ g envin)lllllents using the smart card and the access module of the
present invention.
The smart card is a credit-card size plastic card embedded with a
miclu~lucessor and memory which conl~ s an ~-~thori7~tion code preamble, a card
holder's ~llthori7~tion code, mailbox number and password, and a PIN.
A telecû--------ni~tions termin~l~ generally ~le~ign~t~ with reference mlm~r~l
101 is equipped with an access-control module 10 which provides an easy-to-use
int~orf~- e be~weell the password pr~lecled "smart card" 100 and its resident access
codes, the user and the serving system.
As seen on Figure 1, the teleco,.. ui-iç~tion termin~l could be a proprietarytelephone 12, an analog telephone 14, a data device 16 or an i~legli1~P~I service digital
network aSDN) base rate access (BRA) termin~l 18. The access-control module 10
can be an add-on module conn~tçd to the eYi.~ting teleco.,....~ tions terminals or
2140~6~
-
fully inlegl~ed into the telecû~ tiQns t~- ..,;n~l~. In either case, the system has
a similar configuration. The teleco~ "-i~Ation termin~l is connected to the PBX
switch area 102 for conn~cting the call. A PBX colllpuler 103 monitors the switch
area 102, connecting the call to the voice mail system 104 or to the typical trunk set
5 105, which includes the toll trunks.
When making a telephone call, namely requiring an access code, the user
inserts the card into the access module 10 of the respective te~ ...inAl 12 to 16, which
pr~lllpt~ the user for his or her PIN. The user then enters his or her PIN. The PIN
is passed by the access-control module to the smart card which colll~ares the entered
10 PIN to the one stored in the card. If the entered PIN is vAlid~t~l by the "smart
card," the module retrieves from the card the user's transaction profile which
indi~tes what type of transactions are available to the user. The transaction profile
is displayed so that the user can then select the appr~pliate transaction key, which is
trAn~l~t~d by the module 10 to retrieve the applupliate access-control codes
15 (~lthori7~tion codes and the like), and associated information from the card and
trAn~mit the inrclllldlion to the system ~uppcllillg the telecomm~lniç~tions appal~tus
being used. If the subll~illed PIN is not valid, the user is pl~,lllpled again, until the
PIN attempt threshold is eY~ded at which time the card is disabled.
The system of the present invention can be used to support access to a voice-
20 mail system by fA- ilit~ting access to the voice-mail system. The security of the mail
voice system is enh~nced by storing the voice-mail telephone number, the user's
mailbox number and mailbox password on the same "smart card".
With the present invention, to access a mailbox 104, the user inserts the
"smart card" 100 into the telephone's access module 12 or 14 which will prompt the
25 user to enter his/her PIN. The PIN is passed by the access-control module 10 to the
smart card 100 which colllpalt;s the entered PIN to the one stored in the card. If the
entered PIN is v~ ted by the "smart card", the module 10 retrieves from the card100 the user's tr~n~ction profile which indi~tes what trAn~tions are available to
the user. The trAn~ction profile is in~ t~d on a suppollillg display unit. In this
30 case the tMn~A~tion profile is the voice-mail. The user can then select the appr~pliate
transaction key on a ~uppollillg key pad, in this case the voice-mail tr~nMction. The
tMn~A~tion is trAn~l~t~l by the module 10 to retrieve the a~pn~pliate access-control
2140~64
PIN. The transaction aulo...q~ q-lly fo~ ds the voice-mail telephone nul~bel to the
PBX 102 and the user's mailbox number and password are trqnQmitted to the voice-mail system 104.
Figure 2 illustMtes a block rli~r~m of the smart card of the present invention
S in the case of a cellular phone e.luip~ed with an access module 10. In thisembodilllellt the access module 10 is illteg,dl~d into the cellular phone whose display
202 and key pad 203 :~Up~?OllS the user interf~q,ce for the functions described in
connection with the previous embodiment. In the case when the access module 10
is used with cellular phones, the present invention provides that, when and where
p~rmiQQihle, the user's MIN will not be stored in the cellular phone's nonvolatile
memory, as is ~iullc~ ly done. It will be stored in the smart card 100 and loaded into
the device's memory 204 once the user has succesQfully entered the card's PIN.
To place a call with a cellular phone, according to the present invention the
user inserts the "smart card" 100 into the cellular device's access module 10 which
p~ollll?ls the user to enter his/her PIN. The access-control module 10 passes the PIN
to the smart card 100 which cGlll~an s the entered PIN to the one stored in the card.
If the entered PIN is vqlid~q~ted by the "smart card," the module retrieves from the
card the user's trqnM~tion profile which in~i~q~t~s what trqnQq~tions are available to
the user. In this case, it would in-lit qte cellular call and other transactions.
The trqnQ~ction profile is in~ qt~ on the ~ul)~ol~ing display unit 202. The
user can then select the appl~liale tr~nQ~ction key on the key pad 203, which in this
case it would be cellular call tr~nM~tion. The tr~nMction is tr,qnQ~qted by the module
10 to retrieve and send the user's MIN to the cellular device control circuits 204 to
be used in setting up the cellular connection. Once the call is established, the user
can also, if l~uil~d, access and use other transactions available on the smart card.
The module passes the access code to the cellular device which trqnQmitQ. the
informqtion.
The system of this embodiment provides similar functions and security benefits
as the emb~lim~ntQ. for the PBX and mail voce, plus the security and benefits derived
by also storing the user's MIN.
As it is now appa,~l~l, with the present invention the MI~ is not stored in the
device but is loaded into the device from the card, once the user has entered his or
g
' - 21~05~q
-
her PIN. If the cellular device is lost or stolen, it can not be used to place a call
since it does not have a resident MIN.
F~gure 3 shows a block rli~r~m of the access module. It comrri~.s a smart
card reader 301, conn~t~ to a microprocessor system 303 which provides intelligent
5 secure support for the transfer of data between the user interf~çe circuits, on the
module 304, the smart card 100 and the teleco,.l~ lni~tion network. The data to be
transferred may include an ~lthori7~tion code preamble, authori_ation code, voice-
mail directory number, user mailbox number and password, etc.
The user int.o.rf~ circuits 304 include a telephone type key pad 305 and a
visual display 306. The key pad 305 is provided with keys for ent~-ring the user's
PIN, and with selection keys for the user to select line, voice mail access or other
~ces~s. The visual display system 306 sll~?polls the user interaction with the module
through the microprocessor system 303.
The microprocessor system 303 co"""~"~ tes through interf~res, generally
de~ign~tY~ as 307, to provide access to various systems ~u~?polL~d by the accessmodule 10. In the embodiment ill--~tMted in Figure 3, the module 10 f~.ilit~tes
access to an analog telephone intP.rfA~e 308, proprietary telephone interf~ce(s) 309,
ISDN basic rate tlo.rmin~l int~.rf~te 310 and other interf~ces 311 for cellular
telephones, data devices, LANs, etc.
Figures 4A and 4B illustrate the method for using a pass-word protected
interf~-e belw~n a serving system and a plurality of access codes resident in a user's
memory device. With the present invention, to place a toll call, the user inserts the
"smart card" 100 into the telephone's access module in step 401, which pr~lllpl~ the
user to enter his/her PIN in steps 402 and 403. The PIN is passed by the
access-control module 10 to the smart card 100 in step 404. In step 405 the entered
PIN is colllpaled to the one stored in the card. If the entered PIN is vAlid~ted by the
"smart card, " the module 10 retrieves from the card 100 the user's transaction profile
in step 409, which indi-~tes what trAn~ctions are available to the user. In step 410
the trAn.~ction profile is send to the modllle, which displays it in step 411. In this
eY~mple, the trAn~~tion profile in-li~tes that toll-call and voice-mail transactions are
pe-",iLIed The trAn~tion profile will be in~i~ted on the supporting display unit306. The user can then select the a~p~ iate transaction key on the key pad in step
- 10-
21~056~
412, which will be tr~ncl~ted by the module's microprocessor to retrieve the
appropliale access-control codes from the card in steps 413 and 414. In this case, the
authorization code preamble and ~llthori7~tion code are read from card 100 and sent
to the PBX's control elem~nt in step 415.
If in step 403, the user enters an invalid PIN, a card "PIN atle"lpts" number
will be incremP-nted in step 406 and co",pa,ed the to a card's "PIN atl~",~l~
threshold" number in step 407. If the "PIN atl~",pl~" number is less than or equal
to the "PIN atlem~ls threshold" the user is pro",pled to reenter the PIN in step 402.
If the "PIN al~",~ts" nu",b~l is greater than the "PIN all#",pls threshold", the card
will be disabled in step 408 and the user will have to have the card re-enabled by the
system ~mini~trator.
Once the access module 100 has rol~ Lded the authori_ation code preamble
and authori_ation code, the PBX will co~pa-t; the a~lthori7~tion code received to its
~t~h~, of allthori7~tion codes and grant the calling privileges, assigned to the~llthori7~tion code, to the call. The user then dials the toll number from the
telephone's dial pad in the usual ",al~ner.
A record of the call, inclll-ling the authori_ation code used and the number
dialled can be produced. This provides the ability to assign toll calls to individuals,
via the authorization codes.
- 11 -