Note: Descriptions are shown in the official language in which they were submitted.
21~2227
COMBINATION RADIOFRr;O~ Y IDENTIFICATION CARD -
rlN~r;KpRINT IDENTIFICATION SYSTEM
FIELD OF THE INVENTION
This invention is directed to a personnel identi-
fication system incorporating radio frequency identifica-
tion (RFID) proximity card or other RFID carrier reading
technology and fingerprint reading technology. More
particularly, this invention pertains to a novel person
recognition and identification system utilizing identifi-
cation cards or carriers incorporating RFID technology
electronic fingerprint recognition systems, wherein elec-
tronic fingerprint information is stored in programmable
memory means in the RFID card or carrier.
BACKGROUND OF THE INVENTION
Several mechanisms have been invented to secure
personal ID cards and to prevent any copying of an ID card.
Special printing methods such as W-printing, holographs,
etc., can be used to protect the card. These special
methods, on the other hand, require special printing
devices, so that ID cards can be produced only at a limited
number of locations.
During the past decade or so, a huge number of
"smart card" applications have flooded nearly every region
of distributed information handling. The so called "smart
cards" usually contain an ASIC-based microprocessor and a
certain amount of memory. Most of the smart cards avail-
able at reasonable cost use contact galvanic coupled access
between specific card reader equipment and electronic
devices located on the smart card.
An important drawback in using smart card tech-
nology is the limited size of available memory and the
significant increasing costs when memory space is enlarged.
This local resource shortage limits the use of a card to a
2192227
-- 2
single application such as a credit card, a telephone card,
a social security card, or a driver's licence.
In using any kind of ID card (passport, driver's
licence, social welfare, bank card, etc.), two major
problems have to be solved. First, it must be impossible
to duplicate the ID card. Secondly, it must be assured
that persons presenting their ID card for whatever purpose
are the right persons. It has been known for a long time,
from police and law enforcement work, that usage of bio-
metric parameters is best suited to solve those problems.
Out of possible uses of voice recognition, biometric
signature, retina measurements or hand geometry, as
examples, most reliable and useful nowadays is the recogni-
tion of fingerprints.
Today, "characteristics" of a person appear to bethe most acknowledged and foolproof security and identi-
fication system. An important advantage of such a system
is the independency of any arbitrariness of human factors.
The term "characteristics" describes unalterable and unique
biological items that are specific to any human being, such
as the vocal sound spectrum, signature dynamics, eye retina
and fingerprint patterns. These biological items are
unique, strictly bound to and vary widely between individ-
uals. According to medicare services and police forces,
even in huge populations, there are no two persons who
carry the same set of characteristics. Advantages and
disadvantages of these biological items are discussed
below.
ComParing Bioloqical Items
Biological items comparison is the first and best
choice for any method of identifying individuals, and have
the fewest number of disadvantages, compared to other
identification systems.
214~227
-- 3
Vocal sound system and signature dynamics depend
highly on psychological and physical conditions, ie.
temporary diseases, dispositions and environmental changes.
These dependencies can only be handled by increasing
efforts to implement tolerant and redundant testing sub-
systems, and as a result, this means a rise in costs and
times of performances, which are reasons to exclude these
items from further discussion.
Eye retina patterns which are unique to any
person can be computed and compared after a scan of the
corresponding organ. But this technique has three import-
ant drawbacks. First, a scan by a laser-beam touching the
human eye, is ill-received by the public, although it has
been proven to be harmless. A large number of people are
naive about, and adverse to technology, and thus tend to be
highly suspicious of such a technique. Second, the amount
of data that has to be handled in this case overruns any
requirement of performance. Third, a scanning system to
read the eye retina is expensive, compared to solutions
based on other biological items, such as fingerprints.
The recognition of fingerprint patterns has a
number of advantages and minor disadvantages that can be
accommodated and handled by any system of identification
based on biological items or characteristics. These basic
minor and rare disadvantages and expected misfunction-
alities are:
- occurrence technical errors which can result in
rejection of an enrolled person, or acceptance of
an imposter;
- missing requirements resulting from persons with
no fingerprint profile.
False rejections mostly occur due to incorrect
use of the recognition equipment. A fingerprint cannot be
2142227
scanned, for example, if the finger is presented to the
scanning device outside the tolerated limits of duration,
rotation or pressure. Thresholds to handle these situ-
ations individually can be adopted in wide ranges. This
type of rejection error occurs in 1 to 2 percent of all
cases and since no security demand can be violated, one can
reasonably expect people to run the test of identification
a second time in the rare case of rejection.
Experience and calculation prove a probability of
less than 1:106 for an expected average of false accept-
ance. No probabilities of appearances of missing finger-
print profiles are known. Difficulties may arise with very
cold temperatures, when the skin on the hands and fingers
is extremely dry and the finger does not make a good
contact on the viewing glass platen. A suitable platen
coating can be used to reduce this problem. "Problem
fingers" may be enrolled individually, with a lower verifi-
cation threshold, without endangering the security of the
identification system as a whole.
Attempts have been made by some unscrupulous
types to obtain fingerprint recognition with false fingers
such as dummies made of silicon, and even dead fingers.
This practice is thwarted by testing the finger's colour
spectrum, the so-called live finger test. A living finger
presents a different colour spectrum than a dead or false
one.
Any law enforcement officer would agree that if
fingerprinting is an infallible method of identification,
it is also an incredibly complex and time-consuming process
and frequently, time is the scarcest commodity. In spite
of all the technological advances and the iron clad will of
law enforcement officers worldwide to successfully appre-
hend a criminal and process his/her record, the sheer size
and nature of the task can lead to wrongly classified
2192227
-- 5
fingerprints and inaccurate databases. Access control,
personnel and time management applications pose problems of
their own. False acceptance and false rejection are a big
concern in any application using fingerprints.
Critics say fulfilling the objective of finger-
print identification or use of fingerprints in access
control or the banking industry can never be done so it is
necessary to settle for less reliable card technologies,
for example, magnetic stripes, bar codes, proximity cards,
weigand (embedded ferromagnetic wires) and smart cards.
Existing efforts in achieving satisfactory
analysis of a fingerprint scan, either from a remote site
or at location workstations using latent files or live
scan, have relied heavily on manual expert intervention or
lengthy and expensive computer intensive solutions. These
systems have typically employed scanners that range in cost
from thousands of dollars per station and may require
support systems which cost tens of thousands of dollars.
Currently, electronic fingerprint identification
systems employ variations of Raster scanning with typical
data sizes of 256 KByte to 500 KByte of storage require-
ments for each print. This can result in long transmissiontimes for remote applications and lengthy match times for
all Raster based systems, not to mention the problems
associated with calibration of the fingerprints since it is
not humanly possible for a person to place one's finger-
print in exactly the same manner and position every time.
Raster data is analogous to storing one or morebytes of data associated with each pixel displayed on a
monitor device. Monochrome Raster data can represent 256
levels of gray scale information in a single byte of data
(there are 256 possible combinations of data in an 8 bit
byte). A fingerprint scanning device with a hardware
21q2227
resolution of 512 x 512 pixels and 256 levels of gray scale
would require 256 Kbytes of storage per print (in uncom-
pressed format). With a scan resolution of 512 x 512 pixel
elements, this would result in a data size of 678 KBytes
per print.
The process of transmitting a Raster scan utiliz-
ing existing telephone lines or police radio communications
at 4800 Baud (480 bytes/second) would require over nine
minutes. Even with an efficient data compression algo-
rithm, it would still take approximately three minutes.
Raster scan analysis concepts generally employ
minutiae point analysis. Minutiae point analysis is a
process of locating unique identifiable micro features in
a fingerprint and their relationship to each other. There
are several inherent problems associated with fingerprint
identification using minutiae point analysis with live
scans, some of which are described and discussed as fol-
20 lows:
(a) The print needs to be scanned with a fairly tight
tolerance of orientation and position. Other-
wise, any type of computer analysis will require
considerably more time due to the number of
iterations required to shift the scanned X, Y
minutiae point coordinates and locate best match
cases from the database. As one can recognize,
the requirement for possible data rotation adds
a magnitude of complexity to the identification
process.
(b) Raster scan analysis is susceptible to "pressure
distortion" which occurs due to sideways pressure
exerted on the fingerprint during the scan.
This, in turn, can cause significant shifts in
the relative position of minutiae points to each
21~2227
other which can result in no match or, worse
still, a wrong match from the compared database.
(c) Raster scan analysis is very sensitive to "print
contamination" which result from skin surface
scratches or surface contamination.
U.S. Patents Nos. 4,284,716, 4,542,288 and
4,544,835 are relevant to this field of technology and
mentioned here for reference purposes. The patents relate
to the fabrication of optical cards.
U.S. Patent No. 5,222,152, June 22, 1993,
Fishbine et al., discloses a portable fingerprint scanning
apparatus for identification verification. The apparatus
can optically scan and record a fingerprint.
SUMMARY OF THE INVENTION
The invention is directed to a method of verify-
ing the identity of a person comprising: (a) presenting
to a radiofrequency identification reader, such as a
proximity reader, of a specified frequency a portable radio
frequency identification member containing a programmable
memory means, said member incorporating in said memory
means radio frequency data of the specified frequency of
the reader and relevant digitized individual data and
fingerprint data of said person, said radio frequency
identification reader reading said individual data and
fingerprint data and transmitting said individual data and
fingerprint data to a digital programmable computer means;
(b) presenting a fingerprint of said person to an elec-
tronic scanning means associated with said radio frequency
identification proximity reader, said scanning means
scanning said fingerprint and transmitting scanned finger-
print data to said digital programmable computing means;
and (c) digitally analyzing by means of said programmable
2la~.2,-~
computing means said fingerprint data transmitted by said
scanning means and said individual data and fingerprint
data transmitted by said radiofrequency identification
reader, and coordinating and verifying said fingerprint
data transmitted by said scanning means and individual data
and fingerprint data transmitted by said radiofrequency
identification reader, and provided the data matches,
indicating by said programmable computing means such a
match to the person, or another person, and if the data
does not match, indicating such mismatch to the person, or
another person.
In the method according to the invention, the
scanning means can take a raster scan of the fingerprint of
the person at an effective resolution of at least 500 dots
per inch to create a fingerprint pixel data image, a
computing means can make several passes on the raster data
image to optimize the image, the computing means then
optimizing the raster to a vector conversion to convert the
raster pixels into vector line types used to classify the
fingerprint in the computing means.
The fingerprint image can be recorded in a memory
means in the form of a template which can be comprised of
a high resolution scan taken of the finger pattern of the
person, the data being analyzed, digitized and converted to
a mathematical characterization on said template.
A copy of the template can be stored in the
memory of the programmable computing means. The math-
ematical characterization template of the fingerprint can
be stored in programmable memory chip in a portable radio
frequency identification card. The programmable computing
means can be located in the reader or in a remote location.
A finger of the person can be pressed against a
glass platen, scanned with an electronic camera to obtain
2142227
.
a scanned image, the scanned image can then be converted
into a first binary image, which can then be converted by
an algorithm into a mathematical representation of critical
characteristics of the fingerprint, and the fingerprint
image mathematical representation together with a personal
identification number, and other relevant optional data,
can be stored in a computer memory.
The fingerprint template can be recorded on a
silicon memory chip embedded in a portable radio frequency
identification card and a corresponding template of the
fingerprint can be stored in a computer memory of a central
computer memory, and when the person is to be recognized
and verified, a match comparison of the template stored in
the radio frequency identification card, and the template
stored in the central computer memory can be made.
In another embodiment, a terminal for reading the
card can contain a computer which can compare and verify
the fingerprint data in the card and data obtained directly
from the fingerprint of the person. The reader and finger-
print scanner can be located in a self-contained terminal
or linked to a central computer.
Information encoded in the RFID card can be
computed by the central computer and the information can be
converted and displayed on a television screen on the
proximity reader. The invention pertains to both passive
and active data carriers, as well as for non-contact smart
cards and inductively coupled or capacitively coupled
carriers.
The silicon memory chip in the radio frequency
identification card can contain a read only memory area and
an EEPROM area. The read only memory area can contain a
predefined unique number assigned to the specific person.
21~2227
-- 10 --
The radio frequency identification card can
contain microwires which can be connected to the silicon
memory chip, and the silicon memory chip can be activated
by an external radiofrequency emitter in the proximity
reader which can emit radiofrequency waves of a frequency
which corresponds with a frequency stored in the silicon
memory chip and the silicon memory chip can extract suffi-
cient energy therefrom to operate and transmit internal
read only memory information.
The external radio frequency emitter can transmit
radiofrequency waves through an antenna, which can emit
energy to power the silicon memory chip, and which can
function also as a receiver for receiving incoming informa-
tion from the silicon memory chip in the radiofrequencyidentification card.
The invention is also directed to an apparatus
for identifying and verifying the identity of a person
comprising: (a) a housing; (b) a computer means housed in
the housing, or electronically connected to the housing, in
which a digitized fingerprint identification system accord-
ing to vector analysis is stored; (c) a glass platen on a
surface of the housing against which platen the fingerprint
area of a finger of a person can be placed; (d) electronic
scanning means positioned behind the glass platen for
scanning the fingerprint of the person and transmitting
data from the scan to the computer means which reads the
fingerprint of the person according to a vector analysis
program which is stored in a computer memory in the com-
puter means; (e) a radio frequency identification proxim-
ity readable card containing a memory chip in which is
recorded digitized vector analysis data of the fingerprint
of the person; (f) a radiofrequency identification proxim-
ity means located on the surface of the housing, theradiofrequency identification means being capable of
reading digitized data programmed in the memory chip
21~2227
-
-- 11 --
embedded in the radiofrequency identification card; and (g)
a digitized program recorded in the computer memory of the
computer means which conducts a comparison of data read by
the electronic scanning means and converted to a vector
analysis of the fingerprint of the person and with corre-
sponding data stored in the radiofrequency activated
silicon chip of the identification card.
The identification card can have a write once,
read many optical memory device on the card, said device
having therein memory pools which digitally record assorted
information about the person.
The electronic scanning means can include means
for raster scanning the fingerprint to convert the finger-
print into raster pixels, converting the raster pixels into
vector line types which can be digitally stored in a
computer memory of the computer means and the memory chip
of the radiofrequency identification card.
The fingerprint scan of the person can be con-
verted to a template which can be recorded on a silicon
memory chip embedded in the portable radio frequency
identification card and a corresponding template of the
fingerprint can be stored in the computer memory of a
central computer memory, and when the person is to be
recognized and verified, a comparison of the template
stored in the radio frequency identification card, and the
template stored in the central computer memory can be made.
Information encoded in the radiofrequency identi-
fication card can be computed by the central computer and
the information can be converted and displayed on a televi-
sion screen on the housing.
The silicon memory chip in the radio frequency
identification card can contain a read only memory area and
21g2227
- 12 -
an EEPROM area. The read only memory area can contain a
predefined unique number assigned to the person.
The radio frequency identification card can
contain microwires which can be connected to the silicon
memory chip, and the silicon memory chip can be activated
by an external radiofrequency emitter in the proximity
reader which can emit radiofrequency waves of a frequency
which corresponds with a frequency stored in the silicon
memory chip and the silicon memory chip can extract suffi-
cient energy therefrom to operate and transmit internal
read only memory information.
The external radio frequency emitter can transmit
radiofrequency waves through an antenna, which can emit
energy to power the silicon memory chip, and which can
function also as a receiver for receiving incoming informa-
tion from the silicon memory chip in the radiofrequency
identification card.
It is possible to store on a programmable tag the
complete data of the characteristics of one or more finger-
prints of an individual. In an ID card issuing application
where new ID cards only are issued, a central database
fin~erprint search is required to make sure that no mul-
tiple ID cards for applications like food stamps, or social
welfare are issued. If the ID card is issued along with a
fin~erprint recognition system, then in most applications
such as in POS, only a simple 1:1 match is needed, not
requiring database lookup. This means large scale applica-
tions are not required and substantial savings in terms of
computer power, networking, leased and modem line costs are
minimized or avoided. Furthermore, the usage of technology
combining an RFID card and fingerprint recognition as
described above, allows an identity check to be made with
a portable unit in the field.
21~2~27
-
- 13 -
BRIEF DESCRIPTION OF THE DRAWINGS
In drawings which illustrate specific embodiments
of the invention, but which should not be construed as
restricting the spirit or scope of the invention in any
way:
Figure 1 illustrates an front view of the RFID
proximity card and electronic fingerprint recognition and
identification apparatus.
Figure 2 illustrates a schematic representation
of an RFID card and a proximity reader for reading the RFID
card.
Figure 3 illustrates a layout of a typical
fingerprint.
Figure 4a illustrates a side profile view of an
RFID card.
Figure 4b illustrates a front view of the front
section of the RFID card.
Figure 4c illustrates a front view of the middle
section of the RFID card.
Figure 4d illustrates a rear view of the rear
section of the RFID card.
Figure 5 illustrates a schematic system utilizing
the RFID card and fingerprint recognition system according
to the invention.
Figure 6 illustrates a schematic overview of
information capturing and transport in the phase of data
acquisition and local ID card production.
21~222~
-
- 14 -
Figure 7 illustrates a schematic representation
of an access and security identification network involving
the RFID card and the electronic fingerprint reading
technology of the invention.
DETAILED DESCRIPTION OF SPECIFIC
EMBODIMENTS OF THE INVENTION
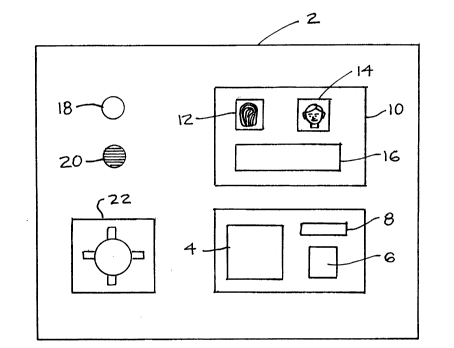
Figure 1 illustrates a front view of one embodi-
ment of the RFID proximity card and electronic fingerprint
recognition and identification apparatus according to the
invention. The apparatus 2 is a protective casing which
houses conventional computer electronic hardware and
software (not shown). The front face of the casing has
mounted thereon a conventional RFID card proximity reading
device 4, a glass fingerprint platen 6 and a data display
8. The front face also has mounted on it a conventional
colour television monitor 10. The monitor 10 displays a
fingerprint image 12, and a photographic image 14 of the
RFID card bearer together with personal data 16 of the RFID
card bearer as printed on the front panel of the RFID card.
The front face of the casing 2 also has mounted
thereon an alarm light 18, which can be a light bulb or
LED, a sound alarm 20, which can be a conventional piezo-
electric alarm, and a safe 22.
To use the RFID fingerprint card reading appar-
atus, the bearer of the RFID fingerprint card (see Figures4a, 4b, 4c and 4d) onto which personal data about the
bearer has been printed on the front face (Figure 4b), the
same and other data such as fingerprint data has been
recorded in the ASIC memory chip in the RFID fingerprint
card (Figure 4c) and optical data has been recorded in the
strip on the rear face of the RFID fingerprint card (Figure
4d), presents the RFID fingerprint card to the RFID card
21~2227
proximity reader 4. At the same time, the bearer presses
his or her finger with the applicable fingerprint on the
glass platen 6. A computer match with recorded data in the
apparatus 2 (or a remote central computer, if applicable)
is then performed, and if the data matches, an image 12 of
the bearer's fingerprint, a picture 14 of the bearer, and
other personal data 16 appears on the monitor 10. Also,
at that point, the safe 22, containing valuables, or the
like, can be opened. If a match cannot be made, the safe
22 remains closed, the alarm light 18 lights up, and the
sound alarm 20 activates.
A. RFID Card and Fingerprint Verification System
The subject invention involves hybrid RFID card
based technology, and a fingerprint identification technol-
ogy which offers up to 1,000 times more available memory
space than ordinary smart cards and at significantly lower
cost. Furthermore, the RFID card system features an
additional integrated, programmable ASIC driven memory of
up to 4kbit of memory that can be accessed by proximity
card readers. Contact card readers are not necessary.
The main advantages of this hybrid RFID finger-
print card system are listed as follows:
- lower cost than smart cards
- standard credit card size
- abundant memory space
- fault tolerant data storage
- data security by cryptology
- copy protection by an integrated hardware tag
- local offline operation
The listed advantages open the use of the tech-
nology to a wide area of applications, where a single card
can be used to store a large amount of necessary informa-
tion. As an example, a nation-wide RFID-card can store
- 21~2227
-
- 16 -
static and dynamic personnel data such as name, first name,
date of birth, sex, address, and so on of the person to
whom the card is issued. Along with these data, a bio-
metric fingerprint, a signature and a photo caption of the
person can be stored. Figure 3 illustrates a typical
fingerprint. This RFID card can be used further for
immigration desk applications where visa information can be
stored and retrieved offline. Military ID information can
be added to the personnel data, which makes the single card
also available as a military ID card. Furthermore, rel-
evant health care information such as blood group, dis-
eases, X-ray pictures, and so on, can be stored to make up
a medical health record. Only a single RFID card is
necessary to hold all these data.
The hybrid RFID card system, utilizing finger-
print registration and identification, can be the basis for
automatic personal identification used for different
applications, such as access to:
- sites and buildings
- bank accounts
- computers and data networks
- special function equipment (e.g. keys of encrypt-
ing units)
- automated teller machines
- funds for electronical transfer at points of sale
Data Com~ression and Selection of Patterns
Data compression, selection and restriction of
available information, i.e. patterns of biological items
such as fingerprints, make it possible to reduce all data
that will be needed for the process of identification to a
limit that allows some important decentralized storage.
Actually, patterns of biological items are not selected,
nor will their information be reduced, but they can be
transferred into so called templates, that match the item
21~2227
-
- 17 -
in question. It is even possible to reconstruct such an
item using a given template.
The latest available models of electronic finger-
print recognition are compact and of a very high reliabil-
ity. A suitable system is available from Jasper Consulting
Inc. of Bemidji, Minnesota, under the trade-mark FIDSTM.
The system can be described as follows, in association with
Figure 1, and the following drawings Figures 2 through 7.
Based on a unique and extremely accurate
biometric measurement of the finger pattern, the FIDS
system proves that a person is who he/she claims to be.
Unlike cards, badges, electronic tokens, hand-held devices,
code numbers, passwords or even keys, the unique charac-
teristic of a fingerprint cannot be lost, stolen or given
away. The fingerprint system coupled with RFID proximity
readable card technology is the ultimate solution for a
fast, secure, user-friendly personal identification for
controlled physical or data access.
Accuracy and verification time are the most
important measures of the performance. Independent tests
show the false acceptance rate to be less than 0.0001~ with
only 2~ first attempt false rejection rate. Also, the
system offers a time-stamped transaction log, providing an
irrefutable audit trail. The nature and intimidation of
technology itself is a strong deterrent to would-be impos-
ters.
The proof of identity is simple, secure and takes
only 1 to 2 seconds verification time. During the enrol-
ment procedure of approximately 40 seconds, the electronic
fingerprint reader takes a very high resolution scan of the
finger pattern. Up to a quarter million pieces of informa-
tion so obtained are analyzed, digitized and converted to
a unique mathematical characterization called the template.
21~2227
.
- 18 -
The template is then stored in a local processor memory,
computer host memory or in a user definition table in a
trusted computer base. The template is also stored in the
RFID card. Later, access is allowed only when the scanning
process proves that the person's live finger matches this
stored template.
Fingerprint Reading Procedure
At enrolment, the finger is pressed against the
glass platen 6, scanned with an electronic camera and the
gray image, containing about 150 kBytes, including colour
spectrum information, is stored in a computer memory. A
typical fingerprint is illustrated in Figure 3. In a two-
step process, this image is converted first into a binary
image, then with an algorithm into a mathematical represen-
tation of certain fingerprint characteristics, with 64 bits
information. This fingerprint image conversion is then
identified as a "template". The template may be stored
together with a PIN or any other relevant optional data
(biographical data, access rights, validity, etc.) in a
computer memory.
Optical reading of the fingerprint is performed
with a CCD micro camera, scanning is triggered through
pressing a finger on the platen 6, which starts a micro-
switch. The live finger test is executed at the same time.
The finger, with its ridges and valleys, forms a clear
picture on the platen provided it is three-dimensional (a
paper copy of the fingerprint will therefore not work).
To ensure contact between the platen and finger, even with
dry fingers, the platen is coated with a contact enhancing
coating.
Image processing after scanning is done with an
ASIC programmable memory chip (see 36 in Figure 4c), and
2142227
- 19 -
the whole process is controlled by a Motorola 68000 pro-
cessor using a set of firmware.
The invention includes a new method of construct-
ing the templates mentioned above. The method reduces allnecessary information for a fingerprint recognition to 64
bits. Together with an acceptable speed of 1 to 2 seconds
for the scanning of fingerprints and the outstanding
advantages already described, it is clear that fingerprint
recognition is the first choice for an improved system of
identification.
When verification of a user is required, the
comparison of the template with the one in the database
takes just 1 to 2 seconds in total.
~ In the above form, the units are presented in a
strong robust housing 2 for the scanner (see Figure 1), to
be mounted on the outside of a door, a processor unit being
installed inside the protected zone. This identification
system has application in many high security areas, such as
nuclear power stations, banks, military premises, etc. The
same technology can be used for access control to computer
terminals, PC's and data networks.
In its simplest form, stand-alone units may be
connected to a PC to enlarge their memory. Systems with
multiple units can be bound together in a network, with a
host, and managed with complete access control software
packages, working on MS-DOS, MS-WINDOWS, OS/2 or X11/Motif,
even in combination with card readers.
RF-ID Finqerprint Technoloqy
A very simple method of copy protection is
provided by RF-Tag or RFID proximity reading technology.
RFID is an acronym for radio frequency identification. The
2142227
-
- 20 -
card using radiofrequency can be read by a proximity reader
and contact between the card and the reader is not necess-
ary.
Within the card (standard credit card dimen-
sions), an ASIC programmable memory chip 36 is implanted,
which, among other things, controls a ROM memory area of 64
Bit and an optional EEPROM area of typical lkbit which can
be extended up to 4kbit. The small area of 64 Bit contains
a predefined specific number that is guaranteed to be
unique during production process. This 64 Bit information
is used for a 48 Bit ID-number and 16 Bit information for
error detection and error correction.
This RFID card 24 circuit 36 is entirely passive
in that no built-in power supply such as NiCd batteries,
etc. is required in the RFID card. The necessary energy to
drive the ASIC memory chip in the RFID card 24 is captured
by an internal antenna device built into the card. For
this purpose, the card contains micro wires connected to
the ASIC. If an external RF emitter matches the proper
frequency, which is roughly 134 kHz, the ASIC through the
wires can extract enough energy to commence operation and
transmit the internal ROM and EEPROM information, also by
using the internal antenna device.
The necessary proximity reader device, as men-
tioned above, also contains an antenna device (see 26 in
Figure 2) that is used as an energy emitter on the one hand
and as a physical receiver for incoming information of an
RFID card. For this purpose, the antenna device is con-
structed to create an electromagnetic field of roughly 60
degrees. If an RFID card is present within this field, it
can be powered by this field of energy. The maximum
distance between the reader system and the card, allowed
for proper operation is about 40 cm. Figure 2 illustrates
2142227
.
- 21 -
a schematic depiction of the RFID Card and the Proximity
Reader, as described above.
RFID FinqerPrint Card Types
The RFID fingerprint card used in the invention
(see Figures 4a, 4b, 4c and 4d) is of the proximity type
using passive circuit technology. The memory chip circuit
(ASIC) 36 and internal antenna micro wires are enclosed in
a flexible plastic body of standard credit card 24 dimen-
sion (ca. 85mm x 55mm x lmm).
RFID Finqerprint Card Data Storaqe
Each RFID card of the invention contains a data
storage of 64 + 1024/4096 bits. The first 64 bits are of
PROM technology and cannot be overridden. During manufac-
ture, a unique code is written into this memory area of the
card so that all cards produced have unique ID's.
The second memory area of lkbits/4kbits is user
programmable within the system. Any information stored in
this area is transmitted to the proximity card reader with
integral error detection and error correction algorithms.
This information can be used to store system wide unique
user facility codes. Provisions are made to store addi-
tional information such as expiration date, compressed
fingerprints.
All user programmable data is encrypted, so no
forging is possible. The system (access controller) will
decrypt the information by PGV and check for consistency.
2142227
- 22 -
Multifunctional RFID Finqerprint Cards
The multifunctional RFID card of the invention
can be provided in an international ISO-standard for credit
cards. Its size is:
- Height: 55mm
- Length: 85mm
- Depth: lmm (approx.)
The weight of the card does not exceed the weight
of standard credit cards, which is approximately 6 grams,
and is therefore user friendly.
The built-in basic elements carry all necessary
information of the bearer and offer possibilities to store
even more information. These types of storage consist of:
- Human readable presentations
- A built-in ID tag
- An optical memory
With these kinds of information storage, a
multipurpose RFID card is realized, offering information
adapted to any specific situation, and far more than is now
available on ID cards and so called smart cards.
Figure 4a illustrates a side profile view of the
construction of a three-layer RF-ID card according to the
invention. Figure 4b illustrates a front view of the RF-
ID card, and the front panel. Figure 4c illustrates a
front view of the middle section of the RF-ID card with the
ASIC programmable memory circuit. Figure 4d illustrates a
rear view of the back of the RF-ID card.
Human Readable Presentation of Characteristics
Human readable information about the characteris-
tics of the card's bearer are printed on the front side of
2142227
- 23 -
the card (Figure 4b). Similar to the main information
printed in a conventional passport, or ID card, this
information consists of the bearer's picture, his or her
full name, his or her residence, and the like. This visual
information serves for purposes of identification in cases
where card reading devices and the computer ID system are
not available.
Programmable Taqs
Programmable "tags" (the middle layer and ASIC
memory chip) as shown in Figure 4c are able to store
information of 64 bits read-only and 1 kbits/4kbits for
writing and reading. This makes it possible to store
internally in the card:
- all important information that identifies its
bearer
- one or more fingerprint templates
- unique codes for multiple encoding algorithms
Also, access to the memory in the ASIC is very
fast both ways, ie. for reading and writing, and it is
rewriteable as often as required. The time for reading and
writing is about lOOms. As all information is crypted
before stored, there is no way for unauthorized persons to
alter it, but it is very easy to handle and maintain by
administration personnel.
The first read-only information of 64 bits serves
as a unique card identification and as a unique key to
encode all other information, stored on the same RFID card.
The next read-and-write storage space of
kbits/4kbits hold the same information as the human read-
able one, which is printed on the front of the card, asdiscussed above. A misuse, e.g. an unauthorized copy of a
RFID card, is impossible, because, as the encoding and
21~2227
- 24 -
decoding of this information is not known and differences
between this information and the human readable one are
easy to recognize, there is no way to alter an existing
RFID card or build a new RFID card. This additional
storage space also holds one or more fingerprint patterns
to gain even more reliability for an identification of the
bearer.
Optical Memory (OMC)
Most of the rear side of the RFID card (Figure
4d) is covered by an OMC strip 38 of an optical memory
device. This device is of the WORM type (write once read
many), but, unlike a CD-ROM, not all memory space has to be
written and used in one step. It is possible to write
information into the free spaces at any time. The overall
storage of this device has a size of 6 MBytes (netto),
which is comparable to approximately 1,500 pages of unfor-
matted and uncompressed text.
This space may be logically divided into several
memory pools or areas, so that different information for
different purposes can be held therein. Each memory pool
can be encoded and decoded by separate algorithms, using
the same unique key, written into the read-only part of the
underlying tag. In this way, only parts of the access
allowable information may be encoded (ie. readable) so that
other information can be held in confidence.
A few basic possibilities for use of this divided
memory are:
- Personnel information (civil purposes, such as
police forces, government; military purposes,
private purposes such as qualifications)
- Medical information (medical characteristics,
such as blood group; diseases; last treatments)
2142227
-
- 25 -
- Repetition of the information stored in the
programmable tag
Physical Oualities of RFID Cards
Environmental influences in wide ranges exceed
the limits of almost all comparable ID devices. However,
the RFID card according to the invention is highly resis-
tant against:
- heat and low temperatures
- electromagnetic radiation
- radioactive radiation
- water
- thinned-out acids and lyes
- thinned-out solvents
Restoring information from mechanically damaged
RF-ID cards has been successfully carried out. After
damage caused by breaking an RFID card or by being run over
by a tank, it was possible to restore all information held
on the OMC.
RF-ID Card Applications and Advantaqes
If a nation-wide RF-ID card is to be issued,
several tasks have to be accomplished during the phase of
establishment. Long term and widespread use of the overall
system has to be ensured by technical features, as well as
by convenient organizational procedures.
In the case of combined RF Tag/OMC-ID cards, no
special printing technology such as holograms, etc. has to
be used. Ordinary low cost card printing facilities can be
used to personalize the RF-ID cards. A facial picture and5 textual data such as:
- ID number
- name
21~2227
- 26 -
- address
- occupation
- religion
- spouse's name
- expiration date
- issuing office
can be printed in high quality without special production
facilities. This gives the opportunity of instantaneous
card personalization in local offices. At that stage, all
data may be captured using computerized equipment such as
PC based input terminals, an electronic camera device and
a fingerprint reader. Optional voice recording and per-
sonal sign scanning can also be done locally, if desired.
This data could be transferred to a national computing
centre and optionally to regional sub-centers, as well as
stored in local electronic records.
A main advantage of this RFID fingerprint tech-
nology is the opportunity to produce duplicate RFID cards
containing all necessary information without any paperwork,
and additional work at once in the local office. Figure 5
illustrates a schematic system utilizing the RFID card
system according to the invention.
For the foregoing purpose, the OMC read/write
device is used to store the information including picture
and fingerprint representation (NCI) along with the textual
data (CI) on the OMC surface. If desired, the scanned
personal sign and some seconds of digital recorded voice
samples can also be stored in the data area. This amount
of data will occupy just a small percentage of the avail-
able memory area. The rest of the area can be left for
updates and other applications.
The integral tag reader/writer first reads
automatically the unique "tag" ID on the RFID which is used
to encrypt all the personal information. This provides
2142227
-
- 27 -
each RFID card with a unique key that is necessary to read
the stored information. If someone tries to copy an RFID
card, even if he has access to raw RFID cards ready for
personalization, the copied data will be unusable due to
an invalid hardware key.
In addition, the textual (CI) information is
stored in the tag memory area of the RFID card by the
integral tag read/ write unit. All information can be
transported to subsequent systems such as regional or
central databases electronically without any additional
paperwork being necessary. If applicable, all data could
be transported on digital media also.
Figure 6 represents a schematic overview of the
information capturing and transport in the phase of data
acquisition and local ID card production.
Figure 7 illustrates a schematic representation
of an access and security identification network involving
the RFID card and the electronic fingerprint reading
technology of the invention.
B. Finqerprint Identification System (FIDS)
The Fingerprint Identification System (FIDSTM) of
the invention uses a unique form of "Vector Analysis". A
suitable FIDS system is available from Jasper Consulting
Inc. of Bemidji, Minnesota, under the trade-mark FIDS. A
raster scan is taken at an effective resolution of 700 dots
per inch (DPI). Several passes are made on the raster data
to clean up and optimize the image. This is followed by a
raster to vector conversion process whereby raster pixels
are intelligently converted into vector line types which
are then used to classify the print.
21~2227
- 28 -
The vector conversion process is highly intelli-
gent. The system is trained to analyze and classify a
print in the same manner that a fingerprint expert would
(only better, easier and faster). FIDS identifies ridges,
valley, loops, double loops, spiraIs, ovals/circles,
bifurcations, rods, arches, deltas, core locations and
other pertinent distinguishing marks or relative character-
istics of the scanned print image. In addition, the
pattern area is classified according to industry accepted
rules.
All of the analysis is performed within the FIDS
unit in under two seconds and an encrypted data model is
generated for transmission to the central size for verifi-
cation. This model (once decrypted) represents a modifiedvector B-tree index key to the central database for lookup.
The result is that any print/image can be compared to a
database consisting of millions of prints in mere seconds.
FIDS "Vector Analysis" is immune to typical
problems associated with the angle of the scan. This can
be a very significant problem for any raster based sol-
utions. In the FIDS system, it does not matter at what
angle or degree of rotation the print is scanned. The data
will still be processed in under two seconds and the result
will be the same every time (provided there is a good scan
to be processed). A match record can be looked up in a
database.
The FIDS system logic consistently maps a scanned
print into a fixed coordinate system so the print always
has the same origin. This means that FIDS systems can be
used to generate index keys into very large, existing
databases. This is simply achieved by downloading scan
data from other systems and generating the appropriate
access keys in real time for subsequent lookups. With this
21~2227
- 29 -
process, FIDS has solved three significant fingerprint
industry problems.
- Scan angle: FIDS is not susceptible to original
angle of scan rotation.
- Integration: FIDS can be easily integrated into
existing fingerprint and/or image identification
systems.
- Data Compatibility: FIDS can be used as a bridge
for data exchange between different systems.
This is possible because FIDS generates a stan-
dard "data model" regardless of the scan origin-
ation.
Raster scan solutions generally focus on minutiae
points which are made up of micro features in a print.
This emphasis on micro features makes raster scan solutions
very sensitive to print distortion, skin scratches or other
forms of contamination such as dirt on the finger. FIDS
"Vector Analysis", on the other hand, tends to generalize
the print through standard classification methods and is,
therefore, very tolerant of micro feature changes or print
contamination. This built-in tolerance allows the FIDS
system to be used in applications where other identifica-
tion systems have failed.
FIDS is a totally self contained solution. This
means the system can be used independently for personnel
identification and access control applications without the
requirement for external support systems.
FIDS Instrument Packaqe
The FIDS instrument package provides for custom
end user application interfacing. The package contains
2142227
-
- 30 -
hardware drivers for the FIDS unit. A compiler and linker
is included for TSR utility program generation complete
with support for several run-time environments including
DOS, Windows, Windows NT, UNIX, OS/2 and others.
The FIDS system consists of several hardware/
software components which are detailed as follows.
A) Main FIDS Unit
The main unit contains all the necessary logic to
scan live prints, perform analysis and generate lookup
codes for matching to an on-line database.
Specifications and Features
1. A high speed RS-232 port for connection to an on-
line database server at data rates up to 62.5K
baud. The database server can be one of several
systems networked together to form a distributed
or redundant database system or it may be a
single central system. In either case, the
server will contain a Smart I/OTM card and will be
running on FIDS database software to perform
lookups.
2. A high speed parallel port for rapid transfer of
analysis of scanned print to the central server
for archive storage or from the scanner to the
FIDS unit for reprocessing. This interface
supports data transfers at rates up to 200 KBytes
per second and interfaces to the parallel port on
the Smart I/O card installed in a central server
(local PC). This interface is most commonly
utilized during the actual print model registra-
tion process.
21~2227
- 31 -
3. An expansion slot for network adapter option card
which supports RS-485 network communications up
to l-Megabaud at distances of 4,000 feet between
nodes with 32 nodes per Master port. The option
board also contains a front panel keyboard and
display interfaces.
4. An I/O interface socket for connection to the I/O
interface option card. This card has four
optically isolated input and four optically
isolated open collector outputs for sensing and
controlling cameras, lights, motors, etc.
5. A high resolution CCD video camera and precision
optics adjusted for optimum field of view at an
effective resolution of 700 DPI.
6. An automatic finger sensor logic for scan initi-
ation and LED indicators for power on, scan in
process and submit for re-scan.
7. A proprietary video processing PGA logic and high
speed RISC-CPU engine core.
8. A processing support logic consisting of 2 Meg
Host Ram, up to 1 MEg program ROM and quarter Meg
display capture RAM. FIDS is a self-contained
system, i.e. the FIDS system can scan, analyze,
process and identify prints without any external
support systems.
9. An analog monitor output interface for displaying
live prints during local model (print) registra-
tion or remote scan lookups.
10. A DC power adapter/connector and fuse holder.
21~2227
- 32 -
B) Smart I/OTM Card
The Smart I/O card of the FIDS system provides
the interfaces for one local registration unit and four
master interfaces for remote scanning stations. Each
master interface can support several hundred remote scan-
ning stations, subject only to reasonable system lookup
times relative to the actual application. Up to eight
Smart I/O cards can be installed in a PC which then sup-
ports up to eight registration stations and a 32 master RS-
485 network interface.
Specifications and Features
1. A high speed RS-232 serial port for connection to
a local FIDS registration unit at data rates up
to 62.5 K baud.
2. A high speed parallel port for rapid bi-direc-
tional transfer of images to and from the local
FIDS registration unit at data rates up to 200
KBytes per second.
3. An ID selection logic for configuring server
systems with up to eight Smart I/O cards.
4. A PC/AT bus compatible with on-board ROM bios
patch for transparent integration into existing
PC configurations.
5. A proprietary on-board communications processor
with 64K program ROM and 32K com buffer.
6. A 64K dual port buffer for Smart I/O to PC-host
communications.
21i2227
The smart I/O card configuration with the BBG
database software coupled with a PC forms a complete
central server for FIDS applications.
C) I/O Interface Card
The I/O Interface Card provides for the interfac-
ing and control of external systems.
Specifications and Features
1. Four optically isolated inputs which will accept
3 to 24 volts AC/DC. These inputs can be used to
sense whether a device is on/off, open/closed,
i.e. is a door open or closed, lights on or off,
etc.
2. Four optically isolated open collector outputs
designed to drive 12 volt relays at 275 ohms and
up to 24 volt relays at 600 ohms and up. The
relays can be mechanical or solid state types.
These outputs can be used to turn devices on/off,
i.e. door latches, lights, motors, cameras, etc.
3. Two 8 position quick connect/disconnect terminal
strips are provided for convenient hookup.
4. Four green LED indicators for input sense status.
5. Four red LED indicators for output control
status.
Application of the I/O Interface Card is pro-
grammed by the application generator section of the BBG
database software. The user can dictate what actions are
initiated by the I/O card for a successful or unsuccessful
database lookup.
21~2227
-
- 34 -
D) Network Adapter Card
The network adapter card is used for remote scan
configurations which can consist of up to several thousand
nodes. This card provides the necessary logic to interface
to a control server via a Smart I/O Card along with status
indicators. In addition, several other features are
provided.
Specifications and Features
1. One slave RS-485 network port for connection to
a master port on a Smart I/O Card or another
network adapter card. This port supports trans-
fer of data rates up to 1 Megabaud at distances
up to 4000 feet.
2. One master RS-485 network port for connection to
a slave port on another network adapter card.
This port has the same transfer characteristics
as detailed on the slave port.
3. Dedicated high speed communication CPU and
asynchronous communications interface adapters
for transparent network communications without
FIDS host CPU intervention.
4. NV/Ram option which supports up to 128 KByte of
non-volatile data storage for off-line process-
ing. FIDS utilizes this memory for storing up to
1024 data models which are compared to real time
scans for access control applications. This
option allows FIDS to be applied in stand-alone
configurations where central server is not
desired.
2142227
5. Top cover option board interfaces which support
data entry and display. Requires a top cover
option board.
E) Top Cover Option Board
The top cover option board interfaces to the
network adapter card and provides for data entry and
display via a 12 position sealed keypad and a 16 digit high
intensity alpha-numeric LED display.
Specifications
1. 12 position 3" x 4" sealed keypads with digits
"0-9", "*" and "#" keys for account #, pin code
and control data entry. Custom keyboard and
graphics are available.
2. 16 digit red LED alphanumeric display readable
from a distance of 8 feet and viewing angles of
+/- 50 degrees. Foreign language character sets
are available.
F) Analoq DisPlay Monitor
The display monitor connects to the FIDS analog
monitor interface and is typically used to view live
fingerprint scans during the print model registration
process.
G) BBG Database Software
The BBG database software manages print databases
and provides an interface between these databases and the
user's application. This system consists of the following
modules:
21~2227
- 36 -
(a) Main Database Manager which adds print models to
designated databases via the print model regis-
tration process. It performs real time or off
line matching of live print scans and supports 1
through N record matching for multiple identity
or law enforcement applications and 1:1 matching
for access control or financial transaction
applications.
(b) User Data Manager. This module allows the user
to define a unique record structure of user data
which is then associated with an individual's
fingerprint or prints represented in the data-
base. Up to 500 characters of free form informa-
tion may be defined in addition to required
system fields.
Required System Fields
Fields Comment
Unique ID# (System assigned)
Archive# (System assigned)
Software SN#/REV# (System assigned)
Hardware SN#/REV# (System assigned)
User ID# Must be unique,
(User/system assigned)
Finger ID# User assigned
Last Name User assigned
First Name User assigned
Middle Name/Initial User assigned
System assigned fields are filled in by the main
database file manager on completion of a successful model
registration and database record add process.
The unique ID# field is a system assigned number
which has no duplicates in the database. This ID# can be
auto-assigned to the user ID# field in lieu of the user's
21~2227
.
- 37 -
application providing a unique ID# (eg. a social security
number).
The archive# field is a unique system assigned
number which identifies the actual live fingerprint scans
used to generate the individual's database record. During
the fingerprint model registration process, the individ-
ual's live fingerprint scans are compressed and saved into
an archive file which has the same name as the archive#
field. These records should be archived off line for later
retrieval if required.
The archived scans may be used to regenerate new
database record updates whenever software upgrades are
released which may provide for additional function or
improved performance. This helps protect one's investment
in creating the original database.
The user ID# can be a user or system assigned
number which must be unique (has no duplicates in data-
base). The main database file manager should be allowed to
assign this field.
The finger# field is assigned as follows:
Right thumb = RT Left thumb = LT
Right index = R1 Left index = L1
Right second = R2 Left second = L2
Right third = R3 Left third = L3
Right pinkie = R4 Left pinkie = L4
The remaining name fields are self-explanatory.
In addition to the aforementioned required
fields, the user may define several additional data fields
up to a limit of 500 characters. The system prompts for a
field name and field length for each additional data field
required.
21~2227
- 38 -
Modes of Operation
The BBG-Database software can be configured to
run in two different modes:
(1) As a foreground application, the system is always
on-line performing local fingerprint model
registration and remote lookups. This is the
stand alone configuration mode.
(2) As a background application, the system is
activated by various hardware/software interrupts
to process model registrations or perform file
lookups. This is the TSR/multi-taking configur-
ation mode.
In either mode, file lookups initiate an update
of the results file. The results file is an ASCII file
which is used to exchange information between the BBG
database system and a user's application. In the case of
a file match, all of the information associated with the
match record will be copied into the results file. This
information consists of the required data fields followed
by user defined field data. The user's application may
subsequently read this data and process accordingly.
In the case of no match on file lookup, the
results file will contain the message ~no match found",
along with any other fields specified by the application
generator module.
H) Application Generator Module
The application generator module provides for
custom operation of a FIDS system according to the dic-
tates of the user. One section allows the use to definewhat hardware actions are performed by a specific (SN#) I/O
Interface board for a match or not match condition on file
21~2227
..~
- 39 -
lookup operations. Another section allows the user to
define which files should be updated with what data.
The file update definition section prompts the
user for file names to update and field names to update
them within either case of match or no match conditions.
Field names are pre-defined by the user data manager module
and the information they point to is supplied by the main
database file manager during the print model registration
process.
Example 1
As an example, the user may define user data
fields consisting of a PIN code number and function number
for a personnel tracking access control application. They
can then define that a file called "track" be updated with
the following fields whenever a live scan is processed.
1. Pin#
2. Last name
3. First name
4. Time (automatically filled in by the system. No
need to actually define this field as a user data
field)
5. Function #
6. Hardware serial #
Example 2
In this example, user could access the track file
to answer several possible questions such as:
What areas has an employee accessed, when and
what was the function performed there?
Who had access to a specific area during a
specific time interval?
21~2227
- 40 -
The function # field would be pre-defined accord-
ing to actual job functions to be performed (labour report-
ing). The hardware serial # field can be used as a site
ID# for access control applications since every FIDS unit
contains a unique hardware ID#.
Up to six file updated procedures may be defined
for a given user application. In a multi-tasking environ-
ment, the user's applications could monitor these files inreal time and process according to file contents. This
concept allows for very flexible and simple application
generation.
The system uses an ASCII file named "Source" to
store all the field information defined by the user data
manager. If the BBG database system is running as a TSR
(terminate and stay resident) or background application,
then the user's application must store the information
associated with these defined fields into the source file
prior to calling the BBG data base system during a print
model registration process. The main database file manager
will read the source file and associate this data with the
stored print record. As a stand alone or foreground
application, the main file manager provides the user with
the ability to enter and edit these fields.
The hardware application generator module allows
the user to define specific control responses to file
lookups via the I/O interface board. The I/O interface
board monitors four sense inputs and controls four outputs.
The inputs and controlled outputs can be interfaced to any
combination of AC or DC devices.
21422~7
- 41 -
Example 3
A general scenario for an access control applica-
tion program utilizing these hardware control features
would be the following:
FIDS Ask for PIN#
FIDS Scan print and process
BBG Database Lookup print for approval
FIDS Open door latch if approved
FIDS Turn lights on or off
FIDS Turn on cameras and record entry
Very elaborate applications can be generated
utilizing these simple processes with a minimum of techni-
cal know-how or programming ability. One simply needs to
know the application and understand the application gener-
ator concepts incorporated in the BBG database software
system.
The application generator modules build a program
through a menu selection process and the program is stored
in a file named "Aprogram.XXX", where "XXX" represents a
program number. This is an ASCII printable file and the
following statements are examples of valid program state-
ments:
Begin 1 Prompt Enter PIN#
Validate
Prompt Submit print
Lookup
Begin 2 If Lookup = True, then next,
else Begin 1
In Input, #1 = Off, then
Output, #1 = Wait, 5 sec.
21~2227
- 42 -
Time = 0
If Input, #2 = on, then
Output, #1 = Off
Time = Time + 5 sec.
If Time > 30 sec., then
Output #2 = On, and so on
As can be seen from this example, any authorized
user can prompt for data input, verify that input, sense
status of devices and control operation of these devices in
reference to time and results of a lookup. In addition,
system files on the central server are updated as defined
by the software application generator models.
Usaqe of OMC Based RFID Cards
Usage of the RFID cards according to the inven-
tion for verification can be done in several different
ways, in several combinations, distinguished by necessary
equipment.
1. Visual authentication tstand alone): As with all
other ID cards, the RFID card according to the
invention can be verified by visual inspection
due to the high quality surface print on the
front face of the RFID card. The textual data
on the front face (Figure 4b) can be checked for
plausibility and the photo image on the front
face can be cross-checked with the card holder's
face.
2. ~Tag" read authentication ~stand alone): Using
a low cost, RF proximity card reader, the "tag"
2142227
- 43 -
memory information in the ASIC chip in the middle
layer of the card (Figure 4c) can be retrieved
and displayed on a small television screen or
liquid crystal display. Due to the applied
encryption, only matching non-volatile key data
pairs will be displayed correctly. The displayed
textual information can be cross-checked with the
printed attributes such as name, address and so
on the front face of the RFID card. The necess-
ary low cost equipment can be installed in
locations such as offices, police cars, gate
entrances, etc.
3. OMC authentication (stand alone): With an OMC
RFID card device (Figure 4d), all stored informa-
tion can be retrieved and checked. These units
contain an integral tag reading device and will
first read decrypt and check the tag memory
information automatically upon card insertion or
proximity reading, which will take l/lOth of a
second. All other information stored on the OMC
surface (rear panel Figure 4d) will be read
subsequently, decrypted and cross-checked auto-
matically with the "tag" memory information in
the ASIC. All inconsistencies will be reported
instantaneously. The textual information (CI),
as well as the compressed picture and the digital
fingerprint representation can be visualized on
a monitor. The monitor picture can be compared
with the printed picture representation on the
front face of the RFID card.
4. Tag read/fingerprint authentication (stand
alone): If a 64 bit fingerprint compression is
used (as described above), this small portion of
data can be stored within the "tag~ memory area
and therefore retrieved by any tag reading
21~2227
- 44 -
device. Using a local fingerprint reader, the
authentication can be cross-checked with bio-
metrical data of the card holder without any on-
line connection. This gives a high reliability
of authentication.
5. OMC/fingerprint authentication (stand alone):
Similar to the OMC authentication method de-
scribed in 3 above, all OMC based information can
be retrieved and cross-checked with the "tag"
memory information. In addition hereto, the
connected fingerprint reader output can be used
to compare stored information with actual parame-
ters of the card holder. This is a very secure
way of authentication that can be accomplished
without any on-line connections or local stored
information.
6. Terminal authentication (on-line): Like all
other ID cards, this RFID card holds printed text
information on the front face that may be used or
be typed in at on-line connected verification
terminals. The central database system (or
regional systems) will respond with complete
information and a digital photo image, that can
be displayed at the verification terminal.
7. "Tag" read authentication (on-line): Like the
terminal authentication method described above in
6, this method requires a connection terminal to
issue a request to a central system. But no
keying of data is required, although the at-
tributes of the data are read automatically by a
proximity card reader.
8. OMC authentication (on-line): As with the stand
alone authentication method described above (item
2142227
- 45 -
7), this method requires needs an OMC device
which is instead connected to the central (or
regional) database system. All stored informa-
tion including all digital pictures and finger-
print representation can be compared with the
central stored data. This verifies all ID card
information on a binary base which can be taken
as a real ID card proof.
9. Tag read/fingerprint authentication (on-line):
Without an OMC device available, a very efficient
method of on-line authentication can be con-
structed by a combination of a "tag" reader and
a fingerprint reading device. The key attributes
for central database look-ups are read by a
proximity card reader and transferred to a
central system on request. Upon receiving a
positive result, the RFID card holder has to
place his or her finger on a platen for automatic
local cross-check. The actual fingerprint is
compared with the central stored representation
to verify RFID card/card holder mapping.
10. OMC/fingerprint authentication (on-line): This
is the most secure way of authentication, which
not only verifies the stored information with
central stored data, but also authenticates the
RFID cardholder by biometric parameters that can
be compared with the retrieved representation.
Table 1 below summarizes the foregoing systems in
tabulated form and details equipment requirements.
21~2227
-
- 46 -
Table 1
ND Required Equipment Security
Authentication Method Tag OMC FP Link
5 1 Visual Low
2 Tag read (stand alone) X Medium
3 OMC (stand alone) X High
4 Tag read/fingerprint
(stand alone) X X High
10 5 OMC/fingerprint
(stand alone) X X Very high
6 Terminal (on-line) X Medium
7 Tag read (on-line) X X High
8 OMC (on-line) X X High
15 9 Tag read/fingerprint X X X Very high
10 OMC/fingerprint X X X Extreme
high
Due to the WORM technology based quality of the
OMC cards, no information stored on the RFID card of the
invention can be changed. Besides this, any data area can
be physically put to an invalid state, which allows storage
of temporary information on the cards. The huge amount of
space available can hold any kind of updated information.
If, for example, military service status has been changed
due to military needs, or the cardholder's age, or dis-
eases, the applicable portion can be updated without the
need to issue a new RFID card. Only when printed informa-
tion on the front of the card has to be changed is it
necessary to issue a new RFID card.
Such updates can be made upon request. On the
one hand, that means the RFID cardholder is asked to visit
an office for this purpose in order to get the updates
written to his or her ID card. On the other hand, any on-
line connected OMC device can write updates to the RFID
card without notice to the operator or the cardholder.
These hidden updates can be useful for military or visa
purposes, or in case of police searches.
2142227
- 47 -
Other Applications for the RFID Card Technology
The usage of RFID fingerprint cards can be softly
enforced by allowing other applications to use some amount
of the OMC memory area. If there are multiple applications
which use the national RFID fingerprint card for data
storage and for authentication, the need for a person
carrying the RFID card will rise significantly. As a
benefit, a citizen does not have to have and use multiple
ID cards for different purposes, which can be inconven-
ient. Some other potential applications are listed below.
Medical Card: The most important data such as
blood group, severe diseases, allergies, and the like, can
be stored partially in the "tag" memory area of the RFID
card. This allows easy access to this information with low
cost equipment in case of emergency. Hospitals or military
medical services can gain access very quickly. Besides
this, any relevant health care information can be stored in
the OMC memory area. This includes parameters, X-rays, and
the like.
Elections: One of the problems inherent in
general or regional elections is record keeping. This is
done typically in the form of lists to ensure a single vote
per citizen. Further on in the process, authentication has
to be performed to identify the person. An easy solution
to these problems is automatic authentication using the
tagged OMC RFID card of the invention. After a citizen has
voted, a marker can be stored within the OMC memory area of
the RFID card. Any further attempt to vote would prompt an
error and the appropriate election personnel would be
informed.
Driver's Licence: A very simple application
extension of the RFID card would be a driver's licence.
Most of the information required for a driver's licence is
21~2227
- 48 -
already stored on a typical ID card. Only very few addi-
tional attributes have to be added for this extension.
Insurance: In combination with an optional
health or driver's licence application, additional insur-
ance information can be stored on the RFID card of the
nvent lon .
Company/Employee ID Card: Many companies use ID
cards for their employees for proper identification and
authentication. To gain access to specific secured build-
ings, the RFID card of the invention can be used. If
additional information must be stored on the RFID card
(such as payroll information or security classification),
the OMC memory area can be used for this purpose.
Visa: All visa information that is now printed
or written in passport documents can be stored on the RFID
card. Automatic update of these data can be done very
simply by using OMC devices at airport counters, harbour
gates or border control.
Military: If desired, additional military
information, that is usually printed in separate documents,
can be stored in OMC memory area of the RFID card.
All these applications can use a single RFID
fingerprint card for common data storage. The different
applications can use stored data of other applications by
links if desired. For example, a driver's licence applica-
tion can use civil status attributes such as name, address,
and the like. On the other hand, data areas can be separ-
ated from each other by using different encryption algo-
rithms. Additional military information can be protected
from unauthorized access.
21~2227
-
- 49 -
As will be apparent to those skilled in the art
in the light of the foregoing disclosure, many alterations
and modifications are possible in the practice of this
invention without departing from the spirit or scope
thereof. Accordingly, the scope of the invention is to be
construed in accordance with the substance defined by the
following claims.