Note: Descriptions are shown in the official language in which they were submitted.
CA 022~4093 1998-11-10
FILF~ r ~ 1 " îS ~ r~J~
T~ L~TI~!
Pl 7056
Method for Protecting A Communications System from Unauthorized Access
The present invention concerns a method per the introductory clause of patent
claim 1.
In modern communications systems, great quantities of information (data and
programs) are stored that are necessary for the operation and particularly for the user-
specific configuration of the system. The information is distributed among various
functional units of the system. Specifically, it involves data that is identical for all users
(global data), personal data on the users, and device-specific data of functional units of the
system. These data must be protected against unauthorized access The management of
the information is preferably done in a central location whence it is transmitted when
necessary to the concerned functional units of the system via data connections. From EP 0
735 785 Al is known a communications system with a central system manager that can be
used as a dealer system. When the system is started up, the system manager ensures that
all functional units up to and including the terminal devices are supplied with the necessary
information. When the system manager, for example a commercial personal computer, can
be connected to the system via a known interface, the possibility that unauthorized third
parties can access the system cannot be excluded with absolute certainty.
Thus the task of the present invention is to preclude, under all circumstances,
unauthorized access to information stored in a communications system.
This task is solved through the measures given in the characterizing section of
patent claim 1. Advantageous embodiments of the invention are given in additional claims.
The comparison of the password stored in all functional units with a password that
, . ~ . . . . . ..
CA 022~4093 1998-11-10
P17056
is compulsorily transmitted during establishment of a data connection ensures that no
unauthorized access to stored information is possible. If a participating functional unit
determines during establiihm~nt of a data connection that the transmitted password does
not agree with the password stored in that unit, access to information stored in that unit is
denied. Additional implementation forms and advantages of the method can be seen from
the description below.
The invention is described in greater detail below with the aid of a drawing as an
example. The drawing shows a digital communications system that is constructed in
accordance with the principle known from EP 0 735 785 - Al with central and distributed
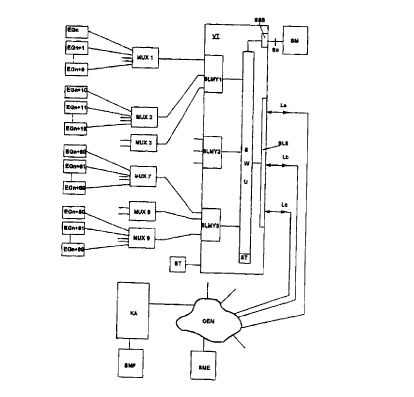
functional units. The communications system consists essenti~lly of a switching section VT
and a great number of terminal devices EG connected to the switching section VT. Also
connected to the switching section VT is a system manager SM. A computer with large
memory capacity and with a video display can be provided as the system manager SM.
The switching section VT is comprised of a circuit switching network SWU, to
which the circuit switching groups SLMY l . . . SLMY3 are connected. Each circuit
switching group SLMY is connected on one side via an 8 Mbit line to a circuit switching
network SWU and on the other side each via individual 8 Mbit lines to three multiplexers
MUX. The circuit switching group SLMY has a coupler for switching the voice, data and
signaling channels (time slots) coming from the circuit switching network SWU to the
multiplexers. Ten terminal devices EG are each connected via their own 2 Mbit line to
each multiplexer MUX. The multiplexers Ml JX have a coupler that switches the voice and
sign~ling channels of the 8 Mbit line coming from the circuit switching groups SLMY to
the appropriate terminal devices EG. The multiplexers MUX are controlled by the
associated circuit switching groups SLMY. The circuit switching network SWU is adigital coupler with a control unit ST that serves to switch connections. This configuration
.....
. ~.. .. . . . . . . ......
CA 022~4093 1998-11-10
P17056
makes it possible to connect any desired terminal devices EG with one another via the
circuit switching groups SLMY and the circuit switching network SWU, and to exchange
user information in the form of data or program code and also voice information through
these connections. An exchange of data between terminal devices EG takes place for
example when the current operating state of other terminal devices, such as the busy
condition, is to be indicated in a terminal device. Moreover, external lines, such as analog
or digital lines (trunks La, leased lines Lb and dedicated lines Ls) leading to the public
telecommunications network OEN, are connected via an interface module SLB to thecircuit switching network SWU so that the terminal devices EG can also enter into
connection via the switching section VT with partners that are not connected to this
communications system. The number of circuit switching groups SLMY, multiplexersMUX and terminal devices EG shown in the drawing is to be considered an example for
the purpose of the present explanation; of course another configuration of the
communications system realized in accordance with this principle is also possible.
The terminal devices EG form the interface between the users and the
communications system. They make available to the user a great number of convenient
features depending on the application. For example, in an embodiment of the
communications system used for foreign exchange dealings in banks, the terminal devices
EG have for various inputs and outputs (such as destination selection) a keyboard with
program-controlled LCD (Liquid Crystal Display) legends. Furthermore, a display screen
with user guidance as well as handsfree and monitoring functions can also be provided in
the terminal devices EG. In order to fulfill all these functions, each terminal device EG has
its own processor that controls the relevant functions by means of software stored in an
associated program memory or data memory, respectively. The software involved isswitching software and operator software. The switching software controls all functions
connected with communication, such as the monitoring and switching of connections
~ . . ... ... ....... . ....... ..
CA 022~4093 1998-11-10
P17056
(voice channels) to the multiplexers MUX and the circuit switching groups SLMY. The
operator software primarily assumes control of the user interface with the keyboard and
the display screen.
S In the case of enhancements or user-specific modifications~ it can become
necessary to update information stored in functional units SLMY, MUX EG of the
system. Thus for example, information stored in the terminal devices EG (programs and/or
data) must be updated because users desire a different configuration or additional features
at their workplace. For this purpose, the appropriate information must be ll~ns.";lled to
the appropriate terminal devices EG Another possible update in the terminal devices EG
is comprised of the relabeling of a destination key because the associated line has changed.
In the course of enhancements to the communications system, it can also become
necessary to supply all terminal devices EG with new program versions. In this case, the
terminal devices EG must be supplied with new program code and/or data A change to
the data in a circuit switching unit SLMY relates, for example, to the activation of a
particular call forwarding route in the "night service" operating state.
The management of the information necessary for operation of the system and
user-appropriate configuration of functional units SLMY, MUX and EG are performed by
the system manager SM. The system manager SM forms the interface between the
operator and the system. It is connected to the circuit switching network SWU via a
special interface (So-interface with 2 B channels at 64 kbit/s and one D channel at 16
kbit/s) and an interface module SSB. The system manager SM has a large database, which
contains among other things the data and programs for the configuration of the circuit
switching groups SLMY, the multiplexers MUX and the terminal devices EG.
For the tr~n~mis.~ion of information to a terminal device EG, for example terminal
CA 022~4093 1998-11-10
P17056
device EGn, the operator (system a-lminislrator) initiates at the system manager SM a
function "Supply terminal device with new information". A loading procedure activated by
this establishes a connection via the circuit switching network SWU, the circuit switching
unit SLMYl and the multiplexer MUXI from the system manager SM to the terminal
device EGn, which is identified by a device number known to the system manager SM.
During this process, a free channel (time slot) is seized on the connection lines between
the circuit switching unit SLMYl and the multiplexer MUX1 and between the multiplexer
MUXI and the selected terminal device EGn, by which means the transmission between
the system manager SM and the terminal device EGn can take place via a data (point-
point) connection, for example with the HDLC protocol. As soon as the connection has
been established, the terminal device EGn delivers a readiness message to the system
manager SM, whereupon the transmission of the information to the terminal device EGn
begins. As soon as all information has been transmitted to the terminal device EGn, the
system manager SM receives an appropriate disconnect message from the terminal device
EGn, whereupon it terminates the connection with the terminal device EGn. In like
fashion, information can be transmitted from the system manager SM to selected circuit
switching units SLMY or multiplexers MUX using analogous procedures.
The system manager SM can in its simplest form be a commercial personal
computer that may be connected via a So-interface to the communications system. Access
from the system manager SM to the communications system requires knowledge of the
necessary procedures and protocols on the part of the human operator. Despite all
conceivable security measures, the possibility that unauthorized third parties can acquire
the necessary knowledge cannot be excluded with absolute certainty. Also for this reason,
unauthorized access to the communications system and its functional units SLMY, MUX
and EG cannot be completely excluded. For this reason, it must be prevented at all events
that unauthorized third parties can gain access to the system and extract any information
. , . .. .. ..... , . . . ~ .. . . .. . , . ... . .. ~ . . ...
CA 022~4093 1998-11-10
P17056
or undertake manipulations that cause service interruptions.
In principle, not only accesses that take place from a system manager SM
belonging to the communications system are possible. Accesses that originate from a
system manager SME connected to the public communications network OEN are also
possible. In addition, accesses are also possible from a system manager SMF connected to
a foreign communications system KA that can establish connections with the
communications system in question via the public communications network OEN. If these
are unauthorized accesses, they must be prevented under all circumstances.
The method in accordance with the invention satisfies this requirement. It provides
that a certain password is entered at the system manager SM which governs access to the
communications system that is managed by the system manager SM. At every startup -- at
the initial installation startup and at later startups -- of the communications system or of
parts ofthe system, at least one ofthe system's functional units affected by the startup has
transmitted to it an address with which this functional unit can establish a data connection
to the system manager SM. Preferably selected as address recipients are functional units
that can directly reach as many peripheral functional units of the communications system
as possible in a simple way. A centrally located functional unit is selected as the address
sender. In the case at hand, the address is sent by the control unit ST of the circuit
switching network SWU to the circuit switching groups SLMYI, ..., SLMY3. The
address is entered into the control unit ST upon initial installation startup via a central
control terminal BT that is used for configuration of the switching section. After receiving
the address, the circuit switching groups SLMY1, ..., SLMY3 each establish a connection
via the circuit switching network SWU to the system manager SM and prompt it to
transmit the current password. Then the password is transmitted through the established
connection by the system manager SM to the circuit switching groups SLMYI,
.~
.,, i . .. .... ... . . . . ., .. , .. . ~,
CA 022~4093 1998-11-10
P17056
SLMY3. Following termination of the connection between the circuit switching group
SLMY and the system manager SM, each circuit switching group SLMY transmits the
password to the associated multiplexer MUX via sign~ling channels and thence to the
connected terminal devices EG. The password is stored in all functional units SLMY,
MUX and EG of the communications system.
When a terminal unit EG is newly attached to a connection of the communications
system, the terminal unit is logged on to the associated circuit switching group SLMY
through a procedure initiated in the terminal unit, whereupon it transmits to the terminal
device the current password among other things.
Security can be additionally increased if the system manager SM checks, prior totransmitting the password to a requesting circuit switching group SLMY, using its source
address, whether the circuit switching group SLMY is authorized at all to receive the
password. Security can be further increased in that the system manager SM verifies an
entered password on the basis of various criteria (syntax, etc.) before accepting it.
Every time a connection is set up by the system's own system manager SM or a
foreign system manager SME or SMF for the purpose of exch~nging information withfunctional units of the communications system, the system manager must send the
password along with the connection request. Each functional unit involved in theconnection (circuit switching group SLMY, multiplexer MUX and terminal device EG)
verifies whether the password transmitted in the connection setup information agrees with
its stored password. If this is not the case, the functional unit denies access to the
inforrnation that is stored in it and is to be protected. Likewise, the password is verified
when functional units, such as two terminal devices EG, wish to exchange data with one
another.
CA 022~4093 1998-11-10
Pl 7056
The system administrator -- either a person authorized by the operator of the
system or a person authorized by the m~nllf~cturer of the system -- can enter the password
at the system manager SM and later change it either as needed or as prompted by the
system manager SM. It is also conceivable that the system manager SM automatically, i.e.
S without the participation of the system administrator, changes the password periodically or
at arbitrary times. In this case, the valid password is not known to anyone, which
considerably increases security against un~llthorized access.
When the password is changed at the system manager SM, it transmits the new
password with a change identifier as described to all circuit switching groups SLMY,
which then pass on the new password to all functional units MUX and EG of the
communications system that they can reach directly, where it replaces the old password.
To increase security, a further embodiment of the method provides for the old password
to be transmitted simultaneously with the new password when the password is being
changed, whereby the new password is only accepted in the affected functional unit when
the old password received agrees with the already existing old password.
.