Note: Descriptions are shown in the official language in which they were submitted.
CA 02266390 1999-03-22
WO 98/13975 PCT/FI97/OOS73
Packet routing in a telecommunicatiolls network
Field of the Invention
The invention generally relates to packet routing carried out in a
5 packet-switched telecommunications network, particularly to the transfer of
IP packets (IP, Internet Protocol) through an ATM network.
Background of the Inventionl
IP is the most popular of the current network layer (third layer in
10 the OSI model) protocols, mainly on account of the great popularity of the
Internet. With the exponential growth of hosts connected to the Internet, the
throughput of IP networks has become ,3 bottleneck, and new ways are re-
quired to transfer IP traffic more rapidly than at present.
Figure 1 illustrates the typical structure of an IP network. In an of-
15 fice environment, personal computers P~'' or similar terminal equipment areconnected to local area networks LAN1...LAN3, which are typically Ethernet
networks. The local area networks in turn are interconnected with a back-
bone network (WAN, Wide Area Network), comprising routers (RT1...RT6)
as nodes. All computers that are in the same local area network have the
20 same IP network address. When a data packet is sent from a computer con-
nected to the local area network, the IF' layer of the protocol stack of the
sending computer checks whether the IP destination address is the same as
its own IP network address. If the address is the same, no routers are nec-
essary, but the packet is sent across the local area network to the computer
25 having that destination address. If the IP network address of the destinationis different than the IP network address of the sending computer, the com-
puter forwards the packet to a router that transfers the packet further to an-
other network.
The transmission links between the routers can be implemented
30 with PDH or SDH technology or with the packet network technique, for in-
stance (ATM, Frame Relay, X.25).
A router has two main functions: packet transfer and updating of
routing tables. The packet transfer process in principle operates in such a
way that the router first reads the network address of the destination from an
35 incoming IP packet. Thereafter it finds from its routing table the output port
associated with that address and sends the packet through said port to the
CA 02266390 1999-03-22
WO 98/13975 PCTIF197/00573
next router. The packets are transferred from router to router until one of the
routers finds that the destination address is the same as its own network
address, in which case it sends the packet to the destination host.
With the increase in transfer rate requirements, new technologies
5 have been introduced. ATM technology is used to an ever increasing degree
as a backbone network technique, as it enables high-capacity backbone
connections. In such a case, interfaces have been constructed in the routing
nodes towards the ATM network; packets are first reconstructed from the
cells arriving from the ATM network, the packets are routed, and thereafter
10 the packets are again disassembled into ATM cells for transfer in the ATM
network. A standard ATM adaptation layer (ML) performs the disassembly
and reconstruction of the IP packets. This will be described more closely
hereinbelow to provide a background for the description of the invention
which is to follow.
When a workstation in the above-described Ethernet local area
network sends data to a workstation in another local area network, the data
unit P1 formed by the application at the workstation is first encapsulated into
a TCP packet P2, for instance, as shown in Figure 2 (provided that the pro-
tocol used in the transport layer is TCP, Transmission Control Protocol). The
20 TCP packet is thereafter encapsulated into an IP packet P3 and the IP
packet further into an Ethernet frame P4 which is sent across the local area
network to a router connected thereto, having an interface towards the ATM
network as well. This router removes the Ethernet segment and disassem-
bles the IP packet into ATM cells in the ATM adaptation layer. It is to be
25 noted that the encapsulation may include insertions both in front and after
the packet (so-called trailer).
Figure 3 illustrates the structure of one IP packet 30 (i.e., IP data-
gram). The minimum size of the packet header is 20 bytes, which is divided
into five four-byte "words", presented in consecutive lines in the figure. After30 the name of each field, the length of that field in bits is shown in the figure in
parentheses The header firstly comprises a 4-bit version field 31, indicating
the IP version that is used. This is followed by the length field 32 (IHL, Inter-
net Header Length), indicating the length of the header in 4-byte words. Type
field 33 indicates the type of service, and field 34 the total length of the data-
35 gram, including the header. Identification field 3~ is used to identify the IPpacket in conjunction with the reconstruction of the packet. Flags field 36
CA 02266390 1999-03-22
WO 98/13975 PCTIFI97100573
allows the system to deduce whether a fragment of a disassembled packet is
the last fragment of the original packet or not. The content of fragment offset
field 37 in turn indicates in what location in the original packet the fragment
belongs. Lifetime field 38 indicates the longest time that the packet may exist
5 in the network. Each router through which the packet travels deducts from
the value of this field. Protocol field 39 indicates the higher layer protocol of
the data carried by the datagram (e.g. TCP). Field 40 contains a header
checksum. Fields 41 and 42 are for thls source and destination addresses,
i.e. they indicate the address of the sending and receiving host in the form of
10 32-bit addresses. The address fields are followed by an option field 43 that is
seldom used. The data to be transpolted in this field generally relates to
network testing or troubleshooting; the data may for example define a given
route that the datagram should travel. The field is supplemented with stuff
bits when necessary, so that the number of bytes is divisible by four.
After the above-described header, the actual data in the IP packet
begins. The length of the data field may vary, but its upper limit is bounded
by the length of field 34, which means that the maximum length of the entire
packet is 216 bytes.
As stated previously, in the ATM network in accordance with Fig-
ure 1 the IP packets are transferred in the form of ATM cells. Figure 4a
shows the basic structure of one cell to be transmitted in the ATM network.
Each cell to be transmitted in the network comprises a 48-byte payload and
a 5-byte header, but the precise struchlre of the header (the content of the
header) is dependent on which part ol the ATM network is being used in
each case, as the ATM network architecture comprises a number of inter-
faces closely specified in the standards, and the header structure employed
in the ATM cell is dependent on which interface (i.e., which part of the net-
work) is concerned.
Figure 4b shows the cell header structure at the UNI interface
(User-to-Network Interface) of the ATM network, which is the interface be-
- tween the ATM terminal equipment and the ATM node. Figure 4c in turn
illustrates the cell header structure at the NNI interface (Network-to-Network
Interface) of the ATM network, which is the interface between two ATM
nodes, either within the network or between two networks.
The routing field of the cell header consists of the virtual path
identifier (VPI) and the virtual channel identifier (VCI). In the header structure
CA 02266390 1999-03-22
W 098/13975 PCT~ ~7/00573
shown in Figure 4b, which is thus used at the subscriber terminal only, a total
of 24 bits has been reserved for the routing field (VPINCI). In the header
structure shown in Figure 4c, which is used in all other parts in the ATM
network, 28 bits have been reserved for the routing field (VPI/\/CI). As the
name implies, the routing field serves as a basis for routing cells in the ATM
network. Primarily in the inner parts of the network, a virtual path identifier
VPI is used, which in practice often determines to what physical connection
the cell is to be routed. The virtual channel identifler VCI, on the other hand,is often used for routing merely at the boundary of the network. It is to be
noted, however, that it is the VPI and VCI together that unambiguously de-
fine the route for the cell.
The other fields in the ATM cell header, as defined in the specifi-
cations, are
- GFC (Generic Flow Control), a field intended for traffic supervi-
sion at the subscriber terminal, not yet precisely defined,
- PTI (Payload Type Indicator), mainly used to distinguish network
management cells from subscriber information cells, but it is possible to
additionally differentiate the subscriber information cells according to whethera congestion has been detected on the route or not,
- CLP (Cell Loss Priority), used to prioritize cells as regards cell
loss probability (largely corresponds to the DE bit in a Frame Relay Net-
work),
- HEC (Header Error Control), header checksum.
Of these other fields, primarily the PTI field relates to the present
invention; it is possible to use this field for monitoring the limit between pack-
ets. The last bit in the PTI field (bit number two in Figures 4a...4c) indicateswhen a new higher layer packet (IP packet) starts. When the bit has been set
to be 1, the last cell of an IP packet is involved, and in that case the next
packet starts with the next non-idle cell.
In general, signals of various formats arrive at the ATM adaptation
layer, and the task of the ATM adaptation layer is on the one hand to form
these signals into the standard format required by the ATM network prior to
their being passed on to the ATM network, and on the other hand to recon-
struct these signals from the cells arriving from ATM networks prior to the
signals being relayed further to the user or control interfaces. Different typesof adaptation layers (ML1...ML5) have been standardized for different
CA 02266390 1999-03-22
WO 98/13975 PCT/FI97/00573
service classes (A...D). For example, AAL types 3, 4 and 5 offer transmis-
sion services for applications in which there is no time dependency between
the source and the destination.
Figure 5 iilustrates the segmentation of IP packets performed by
5 ML 5 into ATM cells and the reconstruction of packets from ATM cells, as it
illustrates the operation of the ATM adaptation layer in the exemplary net-
work shown in Figure 1. The ATM adaptation layer is generally divided into
two sublayers, which are referred to by the abbreviations SAR (Segmen-
tation and Reassembly Sublayer) and CS (Convergence Sublayer). The last-
10 mentioned sublayer performs encapsulation/deencapsulation of user dataunits (for example IP packets) and control data. The frame produced as a
result of the encapsulation performed bly the CS sublayer is referred to as
the CS-PDU (Convergence Sublayer Protocol Data Unit). The ML 5 encap-
sulation is performed in such a way that a trailer portion is added to the user
15 data unit (e.g. an IP packet), containing for instance an error check portion(CRC). The trailer portion has a length of 8 bytes. The length of the entire
CS-PDU corresponds to a multiple of 48 bytes, which is obtained by adding
when appropriate a padding field PAD having a length of 0...47 bytes be-
tween the trailer portion and the payload of the packet.
The SAR sublayer segments each CS-PDU in the transmit direc-
tion into segments of 48 bytes, which are referred to as the SAR-PDU
(Segmentation and Reassembly Protocol Data Unit). In the receive direction,
the CS-PDUs are formed by putting the ';AR-PDUs together.
The ATM layer beneath the ~TM adaptation layer is responsible
for adding five-byte header fields CH (Figures 4b and 4c) into the SAR-PDUs
to be transmitted, thus producing ATM cells 50 that are sent to the ATM
network. The ATM network only processes the cell header, the 48-byte pay-
load is not processed and not even read in the ATM network. In the receive
direction, the ATM layer removes the headers from the cells and supplies the
48-byte payloads to the SAR sublayer for assembly.
When in the network of Figure 1 the routers send IP packets, they
segment the packets into cells in the above manner and send the packets to
an ATM transmission link. The router at the opposite end of the link recon-
structs a packet from the cells in the above manner, makes a routing deci-
sion in the conventional manner on the basis of the IP address, and seg-
ments the packet again into cells for the next ATM link.
CA 02266390 1999-03-22
WO 98/13975 PCTIFI97/00573
Normally the routing decision on the packets is made by software.
When routing implemented with software is combined with the above-
described packet segmentation and reconstruction, the operation of the
ATM-based router network is slowed down considerably. This conventional
routing method is also expensive to carry out.
To alleviate these drawbacks, a method has been developed that
is termed IP switching. IP switching is based on the flow concept: a flow is a
series of IP packets that are headed from (generally) the same source to the
same destination. Hence, one flow (generally) comprises the IP packets
whose source and deslilldlion addresses are the same. For example a TCP
connection is a flow: when the TCP connection has been opened, a series of
packets is sent from the source to the destination. In IP switching, router
nodes identify the flows and request routers at the boundary of the network
to furnish the packets of each flow with a unique flow identifier, e.g. a uniqueVPINCI identifier. When the packets pertaining to a given flow are provided
with a unique VPINCI identifier, the routers within the network can carry out
packet relay on a cell level, using a normal ATM switching. Hence, the rout-
ing need not go as far as the third layer (IP layer), but can be performed in
the second layer (ATM layer).
The drawback of the last-mentioned prior art solution is, however,
that it presupposes a separate control protocol wherewith the nodes within
the network negotiate with the nodes in the incoming direction of traffic on
assigning a dedicated VPINCI identifier to a given flow. Such a solution will
render the network still more intricate and produce additional traffic that
loads the network.
Summary of the Invention
It is an object of the invention to remove the above drawbacks and
to provide a solution that will speed up packet routing without, however,
requiring any new flow control protocol to be applied.
This object is achieved with the solution defined in the independ-
ent claim.
The idea of the invention is to monitor flows formed by packets in
a node at the boundary of a network (receiving packets of an upper protocol
layer). When it is detected that a given flow meets the criteria for a dedicatedconnection, a dedicated lower protocol layer connection identifier is assigned
CA 02266390 1999-03-22
W O 98113975 PCT~ ~7/00573
to that flow. When the next node in the downstream direction receives a data
unit having a "new" connection identifier, it immediately knows that a flow to
which a dedicated channel has been assigned is concerned. The node per-
forms normal routing on the first packet on the basis of the IP destination
5 address, but all the following data units having the same connection identifier
are forwarded on the basis of the lower protocol layer connection identifier
only. Furthermore, the nodes have timle-out control that discards the dedi-
cated connections from use after no traffic pertaining to the relevant flow has
been received during a predetermined period of time.
In the most preferred embodiment of the invention, the lower-layer
data units are, in accordance with the Foregoing, ATM cells and the higher-
layer packets are IP packets, but the Imethod can also be implemented in
conjunction with other protocols or transmission methods.
On account of the solution in accordance with the invention, the
15 throughput of nodes can be increased, obviating the need for segmenting
and reconstructing packets in nodes wil:hin the network. Furthermore, this is
achieved in such a way that no extra flow control protocol is needed in the
network, and thus also the router nodes remain simpler and cause no addi-
tional traffic in the network.
Brief Description of the Dra~wings
The invention and its preferred embodiments will be described in
greater detail in the following with reference to Figures 6-11g by means of
examples in accordance with the accompanying drawings, in which
Figure 1 illustrates the environment in which the invention is used,
Figure 2 illustrates forming of packets prior to their being sent to the net-
work,
Figure 3 illustrates the structure of an IP packet,
30 Figures 4a4c illustrate the generic structure of an ATM cell,
Figure 5 illustrates packet segmentation into ATM cells as performed by
ATM adaptation layer 5 and reconstruction of packets from ATM
cells,
Figure 6 Illusl,dtes the operation of the method of the invention in three
successive nodes of the network,
CA 02266390 1999-03-22
W O 98tl3975 PCT/F~7/00573
Figure 7 is a flow chart illustrating the operation of the method of the inven-
tion in the first node of Figure 6,
Figure 8 is a flow chart illustrating the operation of the method of the inven-
tion in the second and third node of Figure 6,5 Figure 9 illustrates the structure of a gateway node,
Figure 10 illustrates the structure of a node within the network, and
Figures 1 1a.. . 1 1g show tables used in the node of Figure 10.
Detailed Description of the Invention
In the solution in accordance with the invention, segmentation of
IP packets is performed in a node at the boundary of the network (either
node RT1 or RT4 in Figure 1) in accordance with the above, and the ATM
cells are sent to the ATM transmission link.
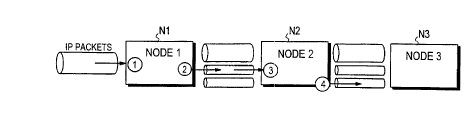
Figure 6 illustrates three ATM network nodes N1...N3 which are
15 located in succession on the route for the packets and which carry out the
method of the invention. In the figure, default channels between the nodes
are denoted by thick pipes and dedicated channels between the nodes by
thin pipes. The different steps of the method are denoted by circled figures.
The system initially only includes default channels, and when traf-
20 fic starts, the system starts assigning dedicated channels to connectionsaccording to need. Default channels extend from a node in all directions, and
packets having different source and/or destination addresses may travel in
one default channel (even though they have the same VPINCI identifier).
Hence, a default channel is a channel using ATM only as a transmission
2~ path and in which routing is effected in the normal way at a higher level (IPlevel). For this reason, the traffic in the default channels is undesired traffic
that the system attempts to eliminate. Default channels must be used, how-
ever, because in practice a large majority of all traffic is of so short a duration
(possibly only a few packets are sent over the TCP connection) that there is
30 no use assigning to them a dedicated VPINCI identifier. It is only worth-while
to establish a dedicated virtual connection for that part of the traffic which is
of longer duration.
Only IP packets arrive at the first node (N1), which segments the
packets in the above-described manner into cells and relays the cells further
35 to node N2. Node N1 examines desired header fields (source and destina-
tion addresses and possibly also other fields) of the incoming IP packets in a
CA 02266390 1999-03-22
W O 98/13975 PCTAF~7/00573
known manner. When node N1 detects (circled one) that a given IP connec-
tion (packets having the same source and/or destination addresses) meets
certain predetermined criteria for a dedicated second-layer connection (OSI
layer 2), node N1 makes a decision to assign a dedicated second-level con-
5 nection (i.e., connection identifier) for that flow, which in the case of an ATMnetwork is a new VPINCI identifier.
The node may make the above decision for example as a result of
detecting that there is regular or heavy traffic over that IP connection (the
node counts incoming packets) or upon detecting that the IP connection
10 requires certain quality of service. The node may find, for instance, that anFTP transmission is involved which requires fast service. The above criteria
may be of a wide variety of types.
When after the above deciision the node N1 detects the first
packet, it selects an available second-layer connection identifier (VPINCI
15 identifier) on the basis of the IP header Df that packet.
For example, when the node has detected at the tenth packet that
the connection requires a dedicated se~cond-layer connection, the node N1
starts using the identifier appertaining to the dedicated second-layer connec-
tion in the cells it dis~-ssembles (circlecl two), starting with said packet. The
20 first nine packets have been forwarded in the default channel (in the form ofcells). The cells in each packet are senl: in succession in the default channel
in such a way that the discrete packets do not overlap.
After this, the next node (N2) in the downstream knows (circled
three), having received a cell carrying a VPINCI identifier that is "new" to the25 node (not used by any one of the flowsl, that a flow is concerned to which a
dedicated second-layer connection identifier has been assigned in the node
in the upstream direction. From this ce!ll the node reads the IP destination
address that is mapped, as can be seen from Figure 3, in segmentation in
such a way that it always has a fixed location in the payload bytes 13-17 of
30 the cell. On the basis of the destination address that has been read, the
node finds the identifier of the output port associated with that address from
the routing table and transmits the cell to that output port. Thereafter all cells
~ having the same VPINCI identifier are transmitted to the same output port.
The node only needs to check the first IP address, and it performs normal
35 routing (at the IP level) on the basis thereof. After this, it can perform
switching at the ATM level directly on th~e basis of the VPINCI identifiers and
CA 02266390 1999-03-22
W O 98/13975 PCTAF~7/00573
transmit the celis again with a new VPINCI identifier to the next node (circled
four).
Figure 7 presents a flow chart illustrating the operation of a node
at the boundary of the network (gateway node N1). In the figure, references
5 Tn in parentheses (n=15) are shown in the different steps' these refer to
tables used by the node, which are set forth below in Figure 9.
First, the node receives an IP packet, reads from its header at
least the source and destination addresses (step 71), and updates the
packet counter (step 72, Table T1) for that address pair (or the destination
address only).
After this, the node examines whether a dedicated connection has
been set for that address pair (step 73). This is done by looking up in the
table whether a dedicated channel pertaining to that address pair is set on
(Table T1), in other words, whether a dedicated second-layer connection
identifier has been assigned to that flow. If this is the case, the routing tag
associated with the connection is sought from the routing table (table T2);
the tag is the internal identifier of the ATM switching matrix on the basis of
which the ATM switching fabric performs switching to the correct output port
(step 74).
If no dedicated connection has been assigned yet, the next step is
to examine whether the criteria for a dedicated connection are met for that
flow (step 75), in other words, whether the traffic volume has exceeded a
given value during a measurement period or whether the quality require-
ments for the traffic in the flow are of a given type (i.e. require a high
throughput probability), for example. The node may utilize for instance the
connection type field 33 (Figure 3), indicative of the quality of service in
terms of delay, throughput, and reliability. If these criteria are not met, the
routing tag of the default channel for the relevant IP destination address is
sought (step 74, table T2), and routing is performed accordingly.
If it is found in step 75 that the criteria for a dedicated connection
are met, the output port associated with the relevant address pair or destina-
tion address (Table T2) and an available routing tag corresponding to the
output port (table T3), i.e. a routing tag that has not been assigned yet and
that corresponds to the IP address. are sought. Thereafter a dedicated
channel corresponding to the IP address is set on (table T1) and the routing
tag for that connection is updated in table T2. At the output port, an available
CA 02266390 1999-03-22
W O 98/13975 PCT~F~7/00573
11
VPINCI is sought for the new routing tag (table T5) and updated in the rout-
ing tag translation table (table T4).
After this, the method can proceed to step 78 in which the IP
packet is segmented into cells and the routing tag that was retrieved above
5 is attached to the cells. Thereafter the cells are transmitted to the output port
associated with the routing tag (step 79). Prior to sending of the cells to the
next link, the routing tag is replaced with the corresponding VPINCI identifier
(table T4).
Thereafter the method proceeds to receiving the next IP packet.
In addition, the node has a separate aging logic that discards
dedicated connections and connection data relating to them from use after
no traffic pertaining to that particular flow has been received during a prede-
termined period of time. It is preferable to use a similar mechanism in all
nodes, and hence the deletion of a dedicated connection is initiated from the
15 starting node. If the node has already discarded the dedicated connection
and there is traffic in the flow, the roul:ing decision is made as described
above similarly as for the "first" packet.
Figure 8 illustrates the operalion of a node within a network (for
example nodes N2 and N3). In the figure, references Sn in parentheses
20 (n=1...7) are shown in the different steps; these refer to tables used by the node, which are set forth below in Figures 1 0 and 11 a. . .11 g.
Initially the node receives a cell (step 80) and reads its header
(step 81). Thereafter the traffic counter pertaining to the VPINCI identifier isupdated (step 82, table S1). As a next step, the node examines whether a
25 default channel is concerned, i.e. whether the incoming VPINCI identifier is
marked as the default channel (step 83, table S1).
If a default channel is not involved, the next step is to examine
whether the flow is a flow for which a dedicated channel has been set on
(step 84, table S1), i.e. whether the incoming VPINCI has been marked as a
30 dedicated channel. If this is the case, the routing tag associated with the
incoming VPINCI identifier is taken (step 86) directly from table S3.
If, on the other hand, no dedicated channel has been assigned to
the flow yet, the method proceeds to sltep 88 in which the IP destination
address is read from the cell; this address is mapped, as is seen from Figure
35 3, in segmentation in such a way that it always has a fixed location in the
payload bytes 13-17 of the cell. On the basis of the destination address that
CA 02266390 1999-03-22
WO 98/13975 PCT/FI97/00573
12
has been read, the output port associated with this address (table S4) and a
corresponding available routing tag (table S5) are sought from the routing
table. In the output port, an available VPINCI identifier is sought for the
routing tag (table S7); this identifier is set in the routing tag translation table
5 of the output port (table S6). At the same time, the connection is marked as
dedicated and the data is updated in the tables (tables S1, S3, S4).
If it is found in step 83 that a default channel is concerned, the
traffic counter pertaining to the IP address pair or IP destination address is
updated (step 85, table S2) and it is examined on the basis of the counter
10 value whether the criteria for a dedicated connection are met for that flow
(step 87). If the criteria for a dedicated connection are not met, the cell is
routed in the normal way, i.e. a route (output port) for that particular IP desti-
nation address and a corresponding routing tag are sought (step 89, table
S4). If, on the other hand, the criteria for a dedicated connection are met, the15 procedure is the same as in connection with setting up a new dedicated
channel (step 88).
After the steps described above, the node has found the correct
routing tag and the cell can be routed to its correct output port (step 90).
Prior to sending of the cells to the next link, the routing tag is removed and
20 the header is provided with an outgoing VPINCI identifier (table S6).
As is apparent from the flow chart presented above, it is also pos-
sible to set up dedicated channels in a node within a network for example on
the basis of the destination address, as the traffic may be multiplexed from
several sources or parallel links to the same destination. If multiplexing is
25 employed on dedicated channels, this must be done preserving the order of
the packets.
Figure 9 illusl~dtes a possible implementation of a gateway node
in the form of a functional block diagram.
For temporary storage of incoming packets, a buffer 91 is provi-
30 sioned at the input of the node. A measuring and control block 92 reads theheader of the packet and finds, by means of the source/destination address
pair, from its table (T1) whether the dedicated channel parameter has been
set on for said address pair.
Retrieval block 93 receives the IP address from the measuring
35 and control block and, on the basis thereof. seeks from routing tables (T2) arouting tag that the retrieval block supplies to a segmentation block 95 in
CA 02266390 1999-03-22
W O98/13975 PCT~F~7100573
13
which the segmentation of cells and attac:hment of routing tags to segmented
cells is carried out.
Furthermore, bookkeeping units 98 that keep track of available
routing tags associated with each input and output port (table T3) are pro-
5 vided on the input side of the node.
The cell is sent with the routing tag from the segmentation unit to
an ATM switch 96, which connects the cell on the basis of the routing tag to
the correct output port 97. Hence, the routing tag is an identifier within the
switch, which is not sent forward in the network.
The measuring and control block measures the traffic in each flow
and deletes the parameters of a dedicated channel, such as the routing tag
and the VPINCI, when it has not detected any traffic pertaining to that flow
during a given period of time.
Figure 10 is a schematic repre'sentation of the structure of a node
15 within a network. The blocks in the node as the same as above, only the
tables used by the node are different from those of a gateway node. For this
reason, the different blocks are denoted by the same reference numerals as
the corresponding blocks in Figure 9. The tables S1...S7 used in the differ-
ent blocks have been separately set forth in Figures 11a... 11g.
Measuring and control block 92 maintains for each VPINCI pair a
counter and information on whether the relevant channel is a default channel
or a dedicated channel (table S1, Figure 11a). Furthermore, in order for it to
be able to transfer traffic of a default channel to a dedicated channel, it
maintains a counter for the IP address pair or IP destination address (table
S2, Figure 11b). Within the network, the traffic of the source/destination pair
may be multiplexed for example from palrallel links, or traffc may be mul-
tiplexed from several sources to a given destination address for which a
dedicated channel is set up.
The routing tags of the dedicated channels, corresponding to the
VPlsNCls, are provided in a separate table (S3, Figure 11c), wherefrom they
are available for use by the routing block. Furthermore, a routing table is
provided for all connections, in which an IP address is associated with an
output port and a routing tag (table S4, Figure 11d). This table is needed for
all routed packets in the default channel and for setting up a new dedicated
channel.
CA 02266390 1999-03-22
WO 98/13975 PCT/FI97/00573
14
Bookkeeping unit 98 keeps track of available routing tags associ-
ated with each input port and output port (table S5, Figure 11e).
The ATM output port has a translation table in which the routing
tag of an incoming cell is replaced with a VPINCI for the outbound cell (table
5 S6, Figure 11f). Furthermore, the output port keeps track of available
VPINCI identifiers (table S7, Figure 11g).
Even though the invention has been explained in the above with
reference to examples in accordance with the accompanying drawings, it is
to be understood that the invention is not restricted thereto, but it may be
10 modified within the scope of the inventive idea set forth in the appended
claims. For example, a flow may comprise, in accordance with the above,
traffic between the same source/destination pair or traffic bound to the same
destination.