Note: Descriptions are shown in the official language in which they were submitted.
CA 02272894 1999-OS-18
WO 98/25372 PCT/Q.97I00380
INFORMATION SECURITY METHOD AND APPARATUS
FIELD OF THE INVENTION
The present invention relates to methods and systems for securing
s information during communication.
BACKGROUND OF THE INVENTION
Method for securing information are known in art. Conventional methods
are based on encryption wherein secured data is processed according to a
predetermined encryption method or key to provide an encrypted fife. Decoding
~o the encrypted file, back to the original information requires processing
the
encrypted file backwards according to the encryption method or key.
Computers which are connectecl to WAN or LAN communication
networks are vulnerable to hostile intrusion by unauthorized persons or data
viruses which attempt to access classified files, download them and "crack"
their
~ s encryption.
The problem is significantly enhanced for portable computers. which are
also liable to be stolen along with the information contained therein.
Another major problem relates to securing access to data and devices
when in communication over a network. Unauthorized network users may attempt
zo to penetrate the secured system or try to send damaging software, such as
software viruses. Prior art software systems such as fire-walls and the like,
do not
provide a foolproof solution against such unauthorized attempts.
Another major problem relates to securing an organization's networks
and computers against virus programs. A number of products currently provide
Zs on-line scanning of incoming communications to identify damaging software
such
as viruses (such as WebShield of Finjan Software Ltd. of Netanya, Israel,
CA 02272894 1999-OS-18
WO 98/25372 PCT/8.97/00380
PCFireWall and WebScan of McCafee Inc.of Santa Clara CA). It will be
appreciated that scanning all incoming data and data changes during
communication consumes a great deal of resources and is generally not
performed at a full scale in real time.
s US patent no. 5,434,562 to David C. Reardon describes a manually user
operable switch for securing a device such as a hard disk from unauthorized
access from a network.
In computer systems, it is common to implement an audit log, to record
security related activities in the system. In this case, the recorded log
itself needs
~o to be secured against future alteration, which will deceive the auditor to
trust a
forged record.
It will be appreciated that an effective security log needs to be written on
a media which cannot be altered. A common method is to print the log on hard
copy. While hard copy is difficult to alter, it is also more difficult to
duplicate,
15 process and communicate in a computerized environment.
Another method is to write the log on a Write Once Read Many media
(such as Pinnacle RCD-1000, Pinnacle Micro Corporation). It will be
appreciated
that in practice Write Once Read Many data storage solutions are inferior to
common read-write technologies (such as magnetic hard disks) in both
2o performance and reliability. Furthermore, the installation of a Write Once
device
for the sole purpose of recording a log involves significant costs.
Special software applications are able to detect attempts of such hostile
intrusion to computer resources by unauthorized persons or data viruses. In
this
case, the computer has to be restarted (boot operation) from a "clean media"
25 which is often called a rescue diskette, since the hard drives of the
computer are
suspected to be contaminated. This clean media often includes removable media
such as a diskette or a CD-ROM.
-2-
CA 02272894 1999-OS-18
WO 98/25372 PCT/8.97/00380
SUMMARY OF THE PRESENT INVENTION
It is an object of the present invention to provide a novel device for
securing access to and from a compuvter station, which overcomes the
disadvantages of the prior art.
s It is a further object of the present invention to provide a novel method
for securing information contained in a computerized storage unit.
There is thus provided in accordance with the present invention a device
for protecting secured areas in a computer system. The computer system
includes
a storage unit. The storage unit includes a first storage area and a second
storage
~o area.
The device of the invention includes a first communication interface for
connecting to a first network) a second communication interface for connecting
to
the computer system, a first input-output (i/o) interface for connecting to
the
storage unit, a second input-output (i/o) interface for connecting to the
computer
~ s system, a managing controller connected between the first network and the
computer system via the first and second communication interfaces) the
managing controller also being connected between the storage unit and the
computer system via the first and second ilo lintertaces.
The managing controller provides the computer system with a selection
Zo between at least two modes. In a first mode, the managing controller
connects the
computer system to the first storage area and to the first network and in a
second
mode, the managing controller connects the computer system to the second
storage area.
The managing controller detect:> any reset signal followed by a
2s command to operate according to a selectedl mode, which may be provided
either
by a user, operating the computer system or by a software application. It will
be
noted that the command, to operate according to a selected mode, can be sent
prior to the reset signal.
-3-
CA 02272894 1999-OS-18
WO 98/25372 PCT/8.97/00380
According to one aspect of the present invention, the device may further
include a third communication interface for connecting to a second network and
a
fourth communication interface for connecting to the computer system.
According
to this aspect the device is connected between the second network and the
computer system via the third and fourth communication interfaces. The device
may enable or disable access to and from the second network, to the computer
system, according to a selected mode of operation.
According to another aspect of the invention, the device provides an
indication of the current mode of operation as well as indication relating to
various
~ o situations such as alert, halt and the like. Respectively, the device may
include a
display unit, an audio generating unit, a vibration generating unit and the
like.
Alternatively, the device may utilize the multi-media capabilities of the
computer
station to produce these indications.
The device may further include a first reset input-output interface,
connected to the managing controller, for connecting to an operating system
source unit and a second reset input-output interface, connected to the
managing
controller for connecting to the computer system. The managing controller is
operative to enable or deny the computer system access to the operating system
source unit.
2o The operating system source unit is selected from the group consisting
of a magnetic media drive, an optical media drive, an electro-optical media
drive,
a communication link and a non-volatile memory. It will be noted that non-
volatile
memory is selected from the group consisting of ROM, FLASH, EPROM,
EEPROM, battery supported RAM and the like.
25 In accordance with a further aspect of the invention, there is provided a
method for operating a communication controlling device. The device is
connected between at least one storage unit, at least one peripheral device
and a
computer station. The device is operable to provide a first predetermined mode
of
operation and at least an additional different mode of operation.
-4-
CA 02272894 1999-OS-18
WO 98/25372 PCTlIL97/00380
The method includes the steps of:
detecting a boot signal received from the computer station;
executing a menu procedure;
receiving an instruction from a user to operate according to a selected
s mode of operation;
enabling access of the computer si:ation to selected areas of the at least
one storage unit according to the selected mode of operation; and
disabling access of the computer station to non-selected areas of the at
least one storage unit according to the selecited mode of operation;
~o enabling access of the computer sl:ation to selected areas of the at least
one peripheral device, according to the selected mode of operation; and
disabling access of the computer station to non-selected areas of the at
least one peripheral device, according to the selected mode of operation.
The method of the invention may also include the steps of:
receiving an instruction from a user to operate according to another
selected mode of operation;
providing a restart command to the computer station;
detecting a boot signal received from the computer station;
enabling access of the computer si:ation to selected areas of the at least
20 one storage unit according to the other selected mode of operation; and
disabling access of the computer ~;tation to non-selected areas of the at
least one storage unit according to the other selected mode of operation;
enabling access of the computer station to selected areas of the at least
one peripheral device, according to the other selected mode of operation; and
2s disabling access of the computer station to non-selected areas of the at
least one peripheral device, according to the other selected mode of
operation.
-5-
CA 02272894 1999-OS-18
WO 98/25372 PCT/a,97/00380
The method of the invention may further include the steps of:
receiving an instruction from a user to operate according to another
selected mode of operation;
providing a restart command to the computer station;
s detecting a boot signal received from the computer station;
providing a boot command to the computer station;
enabling access of the computer station to selected areas of the at least
one storage unit according to the other selected mode of operation; and
disabling access of the computer station to non-selected areas of the at
~ o least one storage unit according to the other selected mode of operation;
enabling access of the computer station to selected areas of the at least
one peripheral device, according to the other selected mode of operation; and
disabling access of the computer station to non-selected areas of the at
least one peripheral device, according to the other selected mode of
operation.
15 The boot command may be a hardware boot command or a software
boot command. The boot command may be followed by resetting the memory of
the computer station.
In accordance with a further aspect of the present invention, there is
thus provided a method for operating a device for protecting secured areas in
a
2o computer system. The computer system includes a storage device having a
first
storage area and a second storage area wherein each the first and second
storage areas contains a master boot record (MBR).
The device includes a first input-output (i/o) interface for connecting to
the storage device, a second input-output (ilo) interface for connecting to
the
25 computer system, a managing controller connected between the storage device
and the computer system via the f rst and second i/o interfaces, wherein the
device connects the first storage area to the computer as a primary storage
unit
-6-
CA 02272894 1999-OS-18
WO 98/25372 PCT/8.97/00380
while denying access to the second storage .area. The method including the
steps
of:
disabling the computer system;
connecting the second storage area to the computer as the primary
s storage unit and connecting the first storage area to the computer as a
secondary
storage unit; and
starting the computer system from the primary storage unit.
The method of the invention may further include the step of detecting
the presence of unauthorized code, before the step of disabling, wherein the
step
~o of disabling is performed as a result of the step of detecting.
The method of the invention may also include step of executing a
predefined software, associated with said unauthorized code. The detection of
the
presence of unauthorized code can include detecting unauthorized data access.
_7_
CA 02272894 1999-OS-18
WO 98/25372 PCT/8,97/00380
BRIEF DESCRIPTION OF THE DRAWINGS
The present invention will be understood and appreciated more fully
from the following detailed description taken in conjunction with the drawings
in
which:
Fig. 1 is a schematic illustration of a network providing secured
information communication, constructed and operative in accordance with a
preferred embodiment of the invention;
Fig. 2 is a schematic illustration in detail of the server of Fig. 1 and the
communication controller, according to the invention;
~o Fig. 3 is a schematic illustration in detail of a node) shown in Fig. 1 and
a
communication controller therefor, according to the invention;
Fig. 4 is a schematic illustration in detail of another node shown in Fig. 1;
Fig. 5 is a schematic diagram of a method for operating a
communication controller so as to provide limited communication access to a
~ s computer, operative in accordance with another preferred embodiment of the
invention;
Fig. 6 which is a schematic illustration of a computer system and a
device for securing the computer system during communication, constructed and
operative in accordance with a further preferred embodiment of the invention;
2o Fig. 7 is a schematic illustration of a computer system and a device for
securing the computer system and its environment during communication,
constructed and operative in accordance with yet a further preferred
embodiment
of the invention;
Fig. 8 is a schematic illustration of a method for operating
2s communication controllers shown in Figs 1, 6 and 7, operative in accordance
with
a further preferred embodiment of the invention;
Fig. 9 is a schematic illustration in detail of a further node, shown in Fig.
1;
_g_
CA 02272894 1999-OS-18
WO 98/25372 PCT/IL97/00380
Fig. 10 is a schematic illustration of a computer station and a
communication device, constructed and operative in accordance with a preferred
embodiment of the invention;
Fig. 11 is a schematic illustration of a computer system, a storage unit, a
s communication device and a portable unit, for securing the computer system
during communication, constructed and operative in accordance with yet another
preferred embodiment of the invention;
Fig. 12 is a schematic illustration of a log unit, constructed and operative
in accordance with yet another preferred embodiment of the invention;
~o Fig. 13 is a schematic illustration of a method for operating the log unit
of
Fig. 12, operative in accordance with yet a further preferred embodiment of
the
invention;
Fig. 14 is a schematic illustration of a computer and a device,
constructed and operative in accordance with a further preferred embodiment of
15 the invention;
Fig. 15 is a schematic diagram of a method for operating an i/o and
communication controlling device so as to provide limited data and
communication access to a computer, operative in accordance with another
preferred embodiment of the invention; and
Zo Fig. 16 is a schematic illustration of a method for operating a device of
the invention, controlling a secure storage area and a public storage area,
each
containing a master boot record, operative in accordance with yet another
preferred embodiment of the invention.
_g_
CA 02272894 1999-OS-18
WO 98/25372 PCTIB.97/00380
DETAILED DESCRIPTION OF PREFERRED EMBODIMENTS
The present invention includes several aspects which define novel
principles for transmitting and storing data in a multiple computer system.
According to one aspect of the invention) secured areas and public
s areas are physically separated. Thus, a network system according to the
invention
shall include at least two communication networks wherein at least one of
these
networks is defined as a secured network, whereby confidential information is
generally transmitted via the secured area. There is no direct connection
between
the public network and the secured network.
~o According to another aspect of the invention, confidential transmissions
are physically divided into at least two elements wherein at least a
predetermined
one of them is required to reconstruct the original transmission. This
predetermined element is transmitted via a secured network and stored in a
secured storage area, both of which can be physically disconnected from a main
~s channel of communication.
According to a first implementation of the invention, the first element
includes a portion of the classified data and the second element includes a
complementary element of the classified data.
According to a second implementation of the invention, the first element
zo includes the classified data in an encrypted form and the second element
includes
the encryption-decryption software.
According to a third implementation of the invention, the first element
includes the classified data in an encrypted form and the second element
includes
the encryption-decryption key.
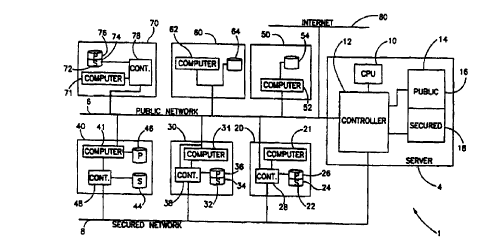
2s Reference is now made to Fig. 1 which is a schematic illustration of a
network providing secured information communication, generally referenced 1,
constructed and operative in accordance with a preferred embodiment of the
invention.
-10-
CA 02272894 1999-OS-18
WO 98125372 PCT/a,97100380
Network 1 includes a plurality of nodes, referenced 20, 30) 40, 50, 60
and 70, a server 4, a public network 6 and a secured network 8. All of the
nodes
20, 30, 40, 50, 60 and 70 are interconnected via public network 6.
According to the present example, nodes 20, 30, 40 and 60 are also
s interconnected via secured network 8. The public network 6 is also connected
to
an external network which in the present exannple is the Internet 80.
Server 4 includes a Central Processing Unit 10 (CPU), a storage unit 14
and a controller 12. The controller 12 is adapted to receive transmissions
from
networks 6 and 8 and write them in various locations in the storage unit 14.
The
~o storage unit is divided into at least two areas, a public area 16 and a
secured area
18. The public area 16 contains non-confidential information whereas the
secured
area 18 contains classified information.
Node 20 is a secured node which is able to transmit and receive
confidential information over the networks G and 8. The node 20 includes a
computer station 21, a storage unit 22 and a communication controller 28.
Communication controller 28 is connected to the computer station 21, the
storage
unit 22, the public network 6 and the secured network 8. The storage unit 22
is
divided into two storage areas, a public storage area 26 and a secured storage
area 24.
2o The communication controller 28 controls all communication to and from
node 20. The communication controller 28 provides access to the public storage
area 26 to both networks 6 and 8. The communication controller 28 provides,
only
the secured network 8 with access to the secured storage area 24.
At node 20, all of the communication with the public network 6 goes
2s through the communication controller 28. Thus) the communication controller
28
monitors and controls all communications Inetween the computer 21 and the
public network 6.
Node 30 is a secured node which is able to transmit and receive
confidential information over the networks. The node 30 includes a computer
-11-
CA 02272894 1999-OS-18
WO 98/25372 PCT/8.,97/00380
station 31, a storage unit 32 and a communication controller 38. Communication
controller 38 is connected to the computer station 31, the storage unit 32,
the
public network 6 and the secured network 8. The computer 31 is also connected
to the public network 6. The storage unit 32 is divided into two storage
areas, a
public storage area 36 and a secured storage area 34.
The communication controller 38 monitors all of the communication
transmissions received from the public network so as to detect access attempts
to
the secured storage area 34. When such an attempt is detected, the
communication controller denies access to the secured area 34 and executes an
~o alert procedure to alert the user of the node 30.
Node 40 is a secured node which is able to transmit and receive
confidential information over the networks 6 and 8. The node 40 includes a
computer station 41, a public storage unit 46, a secured storage unit 44 and a
communication controller 48. Communication controller 48 is connected to the
~ s computer station 41, the secured storage unit 44, and the secured network
8. The
computer 41 is also connected to the public network 6 and to the public
storage
unit 46.
The communication controller 48 provides access to the secured
storage unit 44. The public network f has access to the public storage area 46
via
2o the computer 41.
Node 50 is a non-secured node having a storage unit 54 and a
computer 52, connected thereto and to the public network 6. Node 60 is a
non-secured node having a storage unit 64 and a computer 62. Both the storage
unit 64 and a computer 62 are interconnected as well as connected to the pubic
2s network 6.
It will be noted that nodes 50 and 60 are connected to the public
network 6 only and thus are not authorized to access any confidential
information
which is stored on any of the secured storage areas 34, 44, 24 and 18.
-12-
CA 02272894 1999-OS-18
WO 98/25372 PCT/a,97/00380
Node 70 is a locally secured node having a computer 71, a storage unit
72 and communication controller 78. The storage unit 72 is divided into two
storage areas, a public storage area 76 and a secured storage area 74.
The communication controller 78 is connected to the storage unit 72, the
s public network 6 and to the computer 71. T'he computer 71 is connected to
the
public network 6. When the communication controller 78 detects that the
computer 71 is in communication with the network 6, it denies any access to
the
secured storage area 74.
According to the invention, each of the communication controllers 12,
~0 28, 38, 48 and 78 monitors all of the communication transmissions received
from
the public network 6 so as to detect access attempts to a respective secured
storage area connected thereto. When uch an attempt is detected, the
respective communication controller denies access to the relevant secured area
and executes an alert procedure to alert any user using the node or server.
15 According to the present invention, all of the above three
implementations for determining~the first and second segments are available
for
the present example, wherein the first segment is stored in a public storage
area
of the receiving node and the second segment is stored in a secured storage
area
of the receiving node. It is noted that for such matters) a server can be
considered
Zo a node.
According to the invention, non-confidential data from any node to any
node can be transmitted over the public network 6 and stored in a public
storage
area of the receiving node. Confidential information can be transmitted over
the
public network 6, divided into a first and second segments and stored
accordingly
25 wherein the first segment is stored in the puk~lic storage area of the
receiving node
and the second segment is stored in the secured storage area of the receiving
node.
For example, retrieving confidential information from the server 4 is
performed by transmitting a retrieval request: divided into two segments where
the
so first segment is transmitted over the main network 6 and to the destination
node
-13-
CA 02272894 1999-OS-18
WO 98/25372 PCT/IL97/00380
and the second segment is transmitted to the destination node over the secured
network 8. Hence, only nodes which are connected to the secured network 8
receive the two segments which are required to reconstruct the classified
information.
s Thus, a request for altering data stored in the secured area 18 will only
be performed if received, at least partially, via the secured network 8.
Dividing a file into segments can be performed according to numerous
ways such as generating the first segment from all of the odd bits in the
original
file and generating the second segment from all even bits in that original
file,
~o splitting the file in half, splitting the file into a predetermined large
number of
segments, and the like.
According to one aspect of the invention, the public network 6 and the
secured network 8 are both implemented on the same communication medium, in
different ways. For example, the public network 6 is represented by a
modulated
15 transmission in a first predetermined frequency and the secured network 8
is
represented by a modulated transmission in a second predetermined frequency.
Furthermore, any of communication networks 6 and 8 may consist of cable
communication, wireless communication, optical communication and the like.
According to the present example, communication of confidential
Zo information between two nodes can be performed only between nodes which are
connected via the secured network 8. For example, when node 40 needs to
transfer confidential information to node 20, the confidential information is
divided
into two elements. The two elements are transmitted from node 40 to node 20
wherein the first element is transmitted over the public network 6 and the
second
2s element is transmitted over the secured network 8.
Reference is now made to Fig. 2 which is a schematic illustration in
detail of server 4 of Fig. 1 and the communication controller 12 according to
the
invention.
-14-
CA 02272894 1999-OS-18
WO 98125372 PCT/a,97/00380
The communication controller 12 includes a network interface 92,
connected to the public network 6, a netvvork interface 90 connected to the
secured network 8, an input/output (I/O) interi~ace 96 connected to the
storage unit
14) an I/O interface 94 connected to the CPU 10 and a managing controller 98.
s The managing controller 98 is also connected to the network interface 92,
the
network interface 90, the I/O interface 96 and the I/O interface 94.
The managing controller 98 provides access to the secured storage
area 18 only to access requests which are provided via the secured network 8.
According to the invention) an access request may include several data
~ o segments wherein some of these segments are received from the public
network
6 and the rest are received from the secured network 8.
The managing controller 98 combines these data segments back to form
the original access request and executes it.
Thus, information can be stored in the secured storage area 18 in two
~s cases, either if at least partially received from the secured network 8 or
if originally
determined as confidential information by one of the computers 20, 30 and 40,
connected to the secured network 8. It will be appreciated that security is
enhanced when all of the secured information is transmitted over the secured
network 8.
2o According to the invention, a confidential information file arrives at the
server 4 divided into at least two segments. This confidential information
file can
be stored either in the secured storage area 18 or both in the secured storage
area 18 and the public information storage area 16, according to several
storing
and retrieving modes.
2s According to one storing mode, the: managing controller 98 receives the
confidential information file divided into several segments. The managing
controller 98 then stores some of these segments in the secured storage area
18
and the rest of the segments in the public storage area 16.
-15-
CA 02272894 1999-OS-18
WO 98/25372 PCT/IL97/00380
According to another storing mode, the managing controller 98
combines all of the segments to form a single file and stores it in the
secured
information storage area 18.
According to a further storing mode, the managing controller 98 stores
s the confidential information file in the secured storage area in a segmented
form.
According to this mode, when requested to retrieve this information from the
storage unit 14, the managing controller 98 accesses the segments which form
the confidential information file and transmits them without any processing,
reassembling and the like.
~o According to another aspect of the invention, the server 4 reassembles
the original file of the confidential information from segments of the
classified
information and stores it as one file in the secured information storage area
18.
Reference is now made to Fig. 3 which is a schematic illustration in
detail of node 20 of Fig. 1 and the communication controller 28 according to
the
invention.
The communication controller includes a communication interface 150
for connecting to the public network 6, a communication intertace 154 for
connecting to the secured network 8 and a switching unit 152 for directing
data
inside the node 20. Communication of node 20 with any of the two networks 6
and
20 8 must be performed via the communication controller 28.
Reference is now made to Fig. 4 which is a schematic illustration in
detail of node 30 of Fig. 1.
The computer 31 includes a working station 33 and a communication
interface 35, connected thereto. The communication controller 38 includes a
Zs communication detector 162, a managing controller 160, a computer interface
166, an I/O interface 164 and a communication intertace 168.
The communication detector 162 is connected to the managing
controller 160 and to the public network 6 for detecting communications
received
by computer 31. The computer interface 166 is connected to the managing
-16-
CA 02272894 1999-OS-18
WO 98/25372 PCT/IL97/00380
controller 160 and to the computer 31. The I/O interface 164 is connected to
the
managing controller 160 and to the storage unit 32.
The communication interface 168 is connected to the managing
controller 160 and to the secured network 8.
s Communication interface 168 is a conventional WAN or LAN interface,
such as a modem or an Ethernet interface. ,According to the present example,
the
computer 31 can communicate over the public network 6 directly via the
communication interface 35.
The computer 31 receives access requests from public network 6 via the
~o communication interface 35. The computer 35 provides these requests to the
managing controller 160 via the computer interface 166. The managing
controller
160 retrieves the information from the public; storage unit 36 and provides it
to the
computer 31 which, in turn, transmits it to the public network 6 via the
communication interface 35.
15 The managing controller 160 also detects access requests directly from
the public network 6 and processes them. If the managing controller 160
detects
an information request which relates to information stored in the secured
storage
area 34, a corresponding request for this information provided by the computer
31
will be denied.
2o It is noted that non-restricted comrnunication between the public network
6 and the non-secured areas of node 30, such as the computer 31 and the public
storage area 36, is provided directly via the communication interface 35 and
as
such is not interrupted by the communicatioin controller 38.
The communication controller 38 also provides a full separation security
Zs mode. According to this mode, when the communication detector 162 detects
that
the computer 31 is communicating with the public network 6, it physically
disables
the I\O interface 164 and the communication interface 168, thus eliminating
any
access to the secured storage area 34 and to the secured network 8.
-17-
CA 02272894 1999-OS-18
WO 98/25372 PCT/8.97/00380
Referring back to Fig. 1, there is provided a further aspect of the present
invention, in which node 40 is defined as a security supervising station.
Thus,
when a secured node such as node 20 wants to transmit data from the secured
storage area 24 to a non-secured node, for example to node 50, node 20
s transmits this data to node 40. Node 40, receiving this data, stores it in
the
secured storage unit 44 and also provides it to the supervisor. When the
supervisor provides his authorization, the node 40 transfers the data to
public
storage unit 46 and further transmits it to node 50. According to an
additional
aspect of the invention, node 40 operates as a "Store-and-Forward" buffer
~o whereby at any point in time, it is either in communication with the public
network
6 or with the secured network 8, but not to both networks. This means that the
communication controller 48 provides communication with the secured network 8
only when the computer 41, disconnects from the public network 6. According to
this aspect of the invention, there can be no on-line communication between
the
15 public network 6 and secured network 8, via node 40.
Reference in now made to Fig. 5 which is a schematic diagram of a
method for operating a communication controller so as to provide limited
communication access to a computer, operative in accordance with another
preferred embodiment of the invention.
Zo In step 200, the communication controller receives a transmission.
In step 202, the communication controller determines the type of request
contained in the received transmission. If the received transmission contains
a
write access request, such as alter data, format, delete, move, copy and the
like,
then the controller proceeds to step 204. If the received transmission
contains a
25 read access request, then the controller proceeds to step 220.
In step 204, the communication controller determines if at least a portion
of the transmission was received via the secured network. If so, then the
communication controller proceeds to step 206. Otherwise, the communication
controller proceeds to step 214.
-18-
CA 02272894 1999-OS-18
WO 98/25372 PCT/8.97/00380
In step 206, the communication controller determines a storing mode, as
described hereinabove, according to which the transmission will be stored and
proceeds to a respective step 208, 210 and 212.
In step 214, the communication controller determines if the requested
s destination of the transmission is the secured area. If so, then the
communication
controller proceeds to step 218. Otherwise, the communication controller
proceeds to step 216.
In step 216, the communication controller stores the transmission in the
public storage area.
~o In step 218, the communication controller executes an alert procedure.
Such an alert procedure can be denying ac~;,ess to the secured area, producing
an alert message or signal to the user operating the computer connected to the
communication controller, halting selected activities in the node including
the
communication controller, and the like.
~ s For reading , the communication controller determines (in step 220) if at
least a portion of the transmission was received via the secured network. If
so,
then the communication controller proceeds to step 222. Otherwise, the
communication controller proceeds to step 224.
In step 222, the communication controller retrieves data, according to
2o the access request contained in the transmission.
In step 224, the communication controller determines if the requested
destination of the transmission is the secured area. If so, then the
communication
controller proceeds to step 218. Othenr~ise, the communication controller
proceeds to step 226.
25 In step 226) the communication controller retrieves data, from the public
storage area, according to the access request contained in the transmission.
Reference is now made to Fig. 6 which is a schematic illustration of a
computer system, referenced 390, and a device, referenced 300, for securing
the
-19-
CA 02272894 1999-OS-18
WO 98/25372 PCT/a,97/00380
computer system during communication, constructed and operative in accordance
with a further preferred embodiment of the invention.
Computer system 390 includes a Central Processing Unit (CPU) 310, a
memory unit 314, a storage unit 316, a communication interface 312 for
~ connecting to a communication network 324 and a communication bus 322. The
device 300 according to the invention includes a processor 302 and a switching
unit 304 connected thereto.
The storage unit 316 is divided into two areas, a public area 318 and a
secured area 320. The device 300 controls the storage unit 316 so as to
provide
~o full access to the public area 318 via communication bus 322, to all of the
components of the computer system 390 such as the CPU 310 and the
communication interface 312.
The processor 302 controls the switch 304 so as to allow or deny access
to the secured area 320. According to one aspect of the invention, the device
300
~s provides analysis management during and right after communication. Denying
access to the secured area 320 can be implemented in several ways which
include denying full access) providing read only access and the like.
According to the invention, during on-line communication with the
network 324, the device 300 disconnects the secured area 320 from the computer
2o system and denies all access to it. In addition, the processor 302 monitors
all data
transfer on communication bus 322, detects data changes in the public area 318
of storage unit 316 and generates a log file therefrom.
When the computer system 390 is disconnected from the network 324,
the processor 302 retrieves an analysis software application from the secured
zs area, generates a security key and provides the security key to the
analysis
software. In the present example, the analysis software application is an anti-
virus
scanning software. Then, the processor 302 provides the analysis software
application to the CPU 310. The CPU 310 executes the analysis software
application according to the log file on all of the data changes in the public
area
so 318.
-20-
CA 02272894 1999-OS-18
WO 98/25372 PCT/IL97/00380
If the analysis software application does not detect any hostile software
or in that matter, any suspicious data change) it returns the security key to
the
processor 302. Then, the processor 302 operates switching unit 304 so as to
enable access to the secured area 320.
The device 300 is operative to deny access to the secured area 320
according to several methods and paramei:ers. According to one aspect of the
invention, the secured area 320 is defined physically according to address.
Thus,
access is denied to selected addresses and provided to all the rest. A
processor
for this implementation may consist of a few logical NAND gates which
~o automatically deny access to the secured arE:a addresses.
According to another aspect of the invention, the secured area 320 is
defined according to logical address, such as file name, directory name,
logical
attributes, and the like, to which access is denied.
Detection of an on-line communication situation is possible in several
~s methods. According to one method, detection is provided via a direct
connection
to the communication line via a dedicated communication interface, as
described
in conjunction with communication controller 28 of Fig. 3, thus monitoring all
activity therein. Alternatively, the device 300 is indirectly connected to the
communication fine, for example, by sensing the electromagnetic field produced
in
2o the vicinity of the communication cable, as indicated by reference 328,
thus
monitoring all activity therein. Further, either the computer system 390 or
the
communication interface provide information relating to the communication
status
to the device 300. Still further, a designated software application, such as a
communication software provides information relating to the communication
status
25 to the device 300.
Reference is now made to Fig. 7 which is a schematic illustration of a
computer system, referenced 490 and a device, referenced 400) for securing the
computer system and its environment during communication, constructed and
operative in accordance with yet a further prnferred embodiment of the
invention.
-21-
CA 02272894 1999-OS-18
WO 98/25372 PCT/8.97/00380
Computer system 490 includes a Central processing unit (CPU) 406, a
memory unit 410, a storage unit 416, a WAN communication interface 408 for
connecting to a WAN communication network 428 a LAN communication interface
424 for connecting to a LAN communication network 426 and a communication
s bus 422. The device 400 includes a processor 402 and a switching unit 404
connected thereto. It will be appreciated that this is a non-limiting example
and
that each of communication networks 428 and 426 can be any type of network
such as a WAN, a LAN, a wireless communication network, an optical based
network and the like.
~o The storage unit 416 is divided into two areas, a public storage area 418
and a secured storage area 420. The memory unit 410 is divided into two areas,
a
public memory area 412 and a secured memory area 414. According to one
aspect of the invention, the two storage areas 418 and 420 can be a single
storage unit which is divided into two parts, which is fully controlled by the
device
15 400.
According to another aspect of the invention, the two storage areas 418
and 420 are two separate storage units which are not interconnected, whereas
the device 400 fully controls the access to the secured storage area 418 and
is
adapted to perform an analysis procedure on the public storage area 420.
Zo According to a further aspect of the invention, each of the storage areas
418 and 420 includes several storage units.
The public storage area 418, the public memory area 412, the CPU 406,
the WAN communication interface 408 and the device 400 are interconnected via
the communication bus 422.
25 The secured storage area 420, the secured memory area 414 and the
LAN communication interface 424 are connected to the switching unit 404.
The processor 402 controls the switching unit 404 so as to allow or deny
access to the secured storage area 420, the secured memory area 414 and the
LAN communication interface 424. Access is denied when the computer system
-22-
CA 02272894 1999-OS-18
WO 98/25372 PCT/8.97/00380
490 is in communication with the WAN network via the WAN communication
interface 408.
The device 400 operates generally similar to device 300. The device 400
is thus operative according to the method described hereinbelow with respect
to
s Fig. 9 whereas, as long as a security flag, determined in this method, is
on,
access is denied to the secured storage area 420, the secured memory area 414
and the LAN communication interface 424.
According to a further aspect of the invention, the processor 402 is
operative to execute an analysis software application in the secured memory
area
~ 0 414, which scans the public memory area 412 and the public storage area
418
after WAN communication is disconnected. Thus, the analysis software
application is never accessible to unauthorized elements such as hostile
programs or outside users.
According to the present invention, the device 400 can deny access to
~s any device connected thereto, during communication, so as to prevent
unauthorized access.
Reference is now made to Fig. 8 which is a schematic illustration of a
method for operating devices 28, 38, 48 (E=ig. 1 }, 300 (Fig. 6) and 400 (Fig.
7),
operative in accordance with a further preferred embodiment of the invention.
In
Zo the present example, the description refers. to device 300 and computer
system
390 of Fig. 6. The method includes the follo~roing steps:
In step 500, the device sets a security flag to off.
In step 502, the device 300 detects if the computer 390 performs on-line
communication. If so, the device proceeds to step 504. Otherwise, the device
Zs proceeds to step 507. Off line communication is defined either when the
communication interface (for example, the modem) is disconnected from the
network, or when the computer is disconnected from the communication
interface,
either temporarily, or permanently, while communication intertace stays
connected and communicating with the network.
-23-
CA 02272894 1999-OS-18
WO 98/25372 PCT/IL97/00380
In step 504, the device 300 disconnects the secured area 320 from the
rest of the computer system 390.
In step 506, the device 300 turns the security flag on and generates a
log file of the data changes which occur in the computer system 390 and its
public
s storage area, during communication, due to incoming data and the like. At
the
same time, the device proceeds back to step 502 for confirming that
communication is on-line.
In step 507, if the security flag is on) then the device proceeds to step
508. Otherwise the device proceeds back to step 502.
~o In step 508, the device 300 generates a security key and proceeds to
step 510.
In step 510, the device 300 retrieves an analysis software application
from the secured area, provides the security key to the analysis software
application and provides them both to the CPU 310.
15 In step 512, the CPU executes the analysis software application, on all
data changes which) according to the log file, occurred during on-line
communication. The analysis software application detects if any hostile
attempt
was made to damage the information contained therein. If so, the computer
system 390 proceeds to step 516. Otherwise, the system 390 proceeds to step
20 514.
In step 514, the analysis software application returns the security key to
the processor 302, which in turn enables access to the secured area 320 and
proceeds back to step 500.
In step 516, the computer system 390 provides the user with a warning
2s and halts.
The security key is preferably generated according to a momentary data
situation in the secured area 320. The security key can also be generated as a
one time key which is independent of the secured area 320, such as according
to
an internal random generator and the like. The main reason for this it to
minimize
-24-
CA 02272894 1999-OS-18
WO 98/25372 PCT/8.97/00380
and preferably eliminate all possible access to this security key from
elements
which are not authorized and which may attempt to try to provide this key to
the
processor 302.
Reference is now made to Fig. 9 which is a schematic illustration in
s detail of node 70 of Fig. 1.
The communication controller 78 according to the invention includes a
processor 602, a switching unit 604, a communication interface 606, an
input-output (I/O) interface 608, a computer intertace 610. Communication
controller 78 is connected to a network 6 via the communication interface 606,
to
~ o storage unit 72 via I/O interface 608 and to the computer system 71 via
computer
intertace 610. The storage unit 72 is divided into two major sections, a
public
section 76 and a secured section 74. According to the present example, I/O
interface is either an IDE-ATA or SCSI disk; controller.
The communication interface 606 is selected according to the type of
~ s network 6 and is selected from the group consisting of a dial-up modem, a
WAN
modem, a LAN modem, an optical modern, an ISDN modem, a cable television
modem, and the like. The communication interface 606 may also be an I/O
interface for connecting to a modem of any kind. The processor 602 controls
the
on-line physical connection of the computer station, the storage unit 72 and
the
2o network 6, therebetween.
The communication controller 'l8 is operative according to several
modes of operation. According to one mode of operation, the communication
controller 78, when receiving a communication request command from the
computer system 71, operates the communication intertace 606, so as to provide
2s communication with network 6. At the same time, the communication
controller 78
monitors all access requests to the storage unit 72, allows access to the
public
area 76 and denies access to the secured area 74.
According to a second mode of operation) when the computer system
71 provides the communication controller with a request to access the secured
so area 74, the communication controller 78 operates the switching unit 604 so
as to
-25-
CA 02272894 1999-OS-18
WO 98/25372 PCT/8.97/00380
disconnect the computer from the communication interface 606, while
maintaining
communication between the communication interface fi06 and the network 6.
At that point, the processor 602 scans the public area 76 as well as any
other storage unit in computer system 71 so as to detect harmful programs
which
s may cause damage to the secured area. If such programs are not detected, the
communication controller provides the computer system 71 with access to the
secured area 74. When the computer system provides the communication
controller 78 with a command to reconnect to the network) the communication
controller 78 reconnects the computer system 78 with the communication
~o interface 606 and simultaneously denies all access to the secured area 74.
According to a third mode of operation, the communication controller 78
terminates the communication with network 6 and the processor 602 scans the
public area 76 as well as any other storage unit in computer system 71 so as
to
detect harmfui programs which may cause damage to the secured area. If such
15 programs are not detected, the communication controller provides the
computer
system 71 with access to the secured area 74.
It will be appreciated that the processor 602 can either scan or execute
a scanning and analyzing software which is designed for this purpose.
According
to the present invention, the method described in Fig. 8, can be implemented
in
2o communication device 78.
It is noted that the processor 602, by controlling switching unit 604 and
communication interface 606, can disconnect the computer 71 from the network
either by providing communication interface fi06 with a command to terminate
communication with network 6 or by operating switching unit 604 so as to
Zs disconnect communication interface 606 from the computer 71 while
maintaining
the connection between the communication interface 606 and the network 6.
According to the invention, the processor 602 is also operative to
receive, from the computer 71, commands to disconnect communication between
the communication interface 606 and the network 6 or between the
so communication interface 606 and the switching unit 604.
-26-
CA 02272894 1999-OS-18
WO 98/25372 PCTI1L97/00380
Reference is now made to Fig. 10~ which is a schematic illustration of a
computer station and a communication device, generally referenced 650,
constructed and operative in accordance with a preferred embodiment of the
invention.
s Device 650 includes a communication interface 656, a storage unit 654
and a switching unit 662. Communication interface 656 is connected to
switching
unit 662 and to a communication line 658, which is further connected to a
communication network 660. Device 650 is connected to a data bus of a
computer 652 which further includes a processor 666 and a storage unit 670.
~o Communication interface 656 can be a conventional modem, a modem
emulator, a network communication card, and the like. Storage unit 654 can be
any type of data storage device such as ROM, RAM) flash memory, a disk, tape
and the like. Some implementations of the invention such as the first one,
require
dynamic read\write storage units such as RAM, flash memory, a disk and the
like,
~ s since the data stored in the secured storage unit is dynamic. Other
implementations such as the second and third ones can use less dynamic storage
units such as ROM, EPROM, EEPROM and the like, which are likely to simplify
the overall structure and reduce the cost of manufacturing the device 650.
The device 650 is operative according to several modes, which enhance
Zo the security of confidential information against unauthorized access
attempts from
the network 660. Disclosed hereinafter are a number of non-restricting,
exemplary
modes.
According to a first mode) any confidential data file which needs to be
secured is divided into two segments. The first segment is stored in the
storage
2s unit 670 of computer 652 and the second sE~gment is stored in storage unit
654 of
device 650. The division is performed so that reconstructing the original file
using
the first segment alone is likely to be extremely difficult which, in
practice, may be
considered impossible.
-27-
CA 02272894 1999-OS-18
WO 98/25372 PCT/8.97/00380
According to another mode, confidential data contained in storage unit
670 is encrypted using an exclusive encryption key, wherein when the
encryption
is complete, the key is stored in storage unit 654.
According to a further mode, all of the confidential data is stored in
s storage unit 654.
The computer 652 is able to communicate with the network via the
communication interface 656, as indicated by the dotted line 668. When the
computer 652 does not communicate with the network 660, the switching unit 662
disconnects the bus 664 from the communication interface 656 and connects the
~o storage unit 654 to the bus 664, as indicated by line 672.
When the computer establishes a communication connection via
communication interface 656, switching unit 662 disconnects storage unit 654
from the bus 664 and connects the communication intertace 656 to the bus 664.
Thus, any party communicating with the computer 652 has limited data access
~s which is confined to the data stored in the computer storage unit 670 and
not to
the data contained in storage unit 654.
It will be appreciated that when the switching unit 662 disconnects the
storage unit 654 from the bus 664 it makes the storage unit and all of the
data
contained therein unavailable.
Zo The communication device 650 can be implemented as an add-on
internal card according to conventional standards such as an AISA, VLB, PCI,
PCMCIA and the like. The device can also be implemented as an external device
for connecting via a serial port, a parallel port and the like. Thus, for
example, the
device 650 can be implemented as PCMCIA modem card for a portable
25 computer. The user can remove the communication device from the computer
654 and use it as a key. It will be appreciated that as long as the
communication
device 650 is not connected to the computer 652, there is no access to any
data
contained inside storage unit 654.
-28-
CA 02272894 1999-OS-18
WO 98!25372 PCT/8.97/00380
According to the present invention, the method described in Fig. 8 can
be implemented in communication device 6.50.
Reference is now made to Fig. 11 which is a schematic illustration of a
computer system, referenced 890, a storage unit) referenced 810 a device,
s referenced 800 and a portable unit 850, for' securing the computer system
during
communication, constructed and operative in accordance with yet another
preferred embodiment of the invention.
The computer system 890 is coinnected to a communication network
892 and to the device of the invention 800. The device 800 is also connected
to
~o storage unit 810. The device 800 includes a processor 802, a switching unit
804
and a wireless transceiver 803.
The portable unit 850 includes a wireless transceiver 852 and a
processor 854, connected thereto.
The storage unit 810 is divided inbo five areas:
a log area 812, for managing a log file;
a buffer area 814, for intermediately storing data upon receipt but before
it is transferred into a secured area 820;
a public area 816, which is accessible at all times;
a read only area 818, for storing operating unit files, analysis software
Zo application and the like; and
a secured area 820 for storing confidential information.
The device 800 manages the storage unit 810 as follows. When the
computer system 890 is in an on-line communication with the communication
network 892, the device 800 enables full access to the public area 816 and to
the
25 buffer area 814, for reading and writing. The device 800 also enables
limited
read-only access to the read only area 818. Simultaneously, the device 800
updates the log area with information relatiing to data changes in the storage
unit
810 and data requests received from the computer system 890. The device 800
_2g_
CA 02272894 1999-OS-18
WO 98/25372 PCT/8,97/00380
denies access to the secured area 820. After the computer system 890 is
disconnected from the communication network 892, the device 800 retrieves an
analysis software application from the read only unit and executes it,
according to
the information contained in the log area 812, on the data contained in the
public
area 816 and the buffer area 814. Any data which is destined for the secured
area
820 is transferred from the public area 816 to the buffering area 814, scanned
and, if classified as harmless, transferred to the secured area 820.
According to the present embodiment, the device 800 is operable to
provide access to secured areas in the storage unit 810 only when an
authorized
~o user, wearing the portable unit 850, is in the vicinity of the device 800.
According to a wireless mode of the invention, the wireless transceiver
852 transmits a signal to the wireless transceiver 803. The wireless
transceiver
803 detects this signal and provides it to the processor 802 which regards it
as an
enable signal to provide access to the secured areas in storage unit 810.
According to this mode, if the user has left the premises and wireless
transceiver
803 does not detect the signal transmitted by the wireless transceiver 852,
the
device 800 denies access to the secured areas of the storage unit 810.
According to another wireless mode, the processor 854 provides the
wireless transceiver 852 commands to transmit a diferent signal from time to
time.
2o The processor 802 is then adapted to recognize the various signals or the
change
between them.
According to a further wireless mode, wireless transceiver 803 and
wireless transceiver 852 communicate using bi-directional communication. Thus,
the processors 802 and 854 are operative to exchange decoded signals, so as to
2~ enhance even more the level of security.
Reference is now made to Fig. 12 which is a schematic illustration of a
log unit, referenced 1000, constructed and operative in accordance with yet
another preferred embodiment of the invention.
-30-
CA 02272894 1999-OS-18
WO 98/25372 PCT/II,97/00380
The log unit 1000 includes a storage area 1002 and a controller 1004
connected thereto. The controller 1004 is operative to provide sequential
writing of
log entries in the storage unit as well as random-access reading of log
entries
contained therein.
According to the invention, when the controller 1004 receives a
write-command to register a new log entry, it ignores the address which may by
incorporated in the write-command and assigns an address which is in sequence
with the address of the previous write-command. Thus, an attempt to change a
preselected log entry with a write-command which includes a specific address
will
~o not be executed. According to one aspect of the invention, when such an
attempt
occurs) the controller 1004 produces an alert command to a computer (not
shown) connected thereto.
One of the main advantages of this log unit is that it does not permit free
writing access to the log area, thus preventing any deliberate change of a
preselected log entry.
When a log file is located in a fiinite size storage area, sometimes it
exceeds the limit of storage space. The common solution in this situation is
to
define the log file as a cyclic file, i.e. after writing the last possible
entry, at the end
of the log file, then start writing at the beginning of the log file. Thus) if
one wishes
Zo to change the log file, he may write as many log entries as are needed to
fill and
rewrite the entire log file.
The method according to the invention, overcomes this problem by
providing a minimum time period between two sequential log entry write
commands. Thus, writing over an entire log file is limited so that one cannot
Zs perform it in a short period of time.
Reference is now made to Fig. 1 ~3 which is a schematic illustration of a
method for operating the log unit 1000 of Fig. 12, operative in accordance
with yet
a further preferred embodiment of the invention.
In step 1050, the log unit 1000 receives a log command.
-31-
CA 02272894 1999-OS-18
WO 98/25372 PCT/8,97/00380
In step 1052, if the received log command is a write command, then the
log unit 1000 proceeds to step 1056. Otherwise, if the received log command is
a
read command the log unit 1000 proceed to step 1054.
In step 1054, the log unit 1000 retrieves a requested iog entry.
s In step 1056, if the time period ~t is greater than or equal to a
predetermined period of time T, then the controller 1004 proceeds to step
1060.
Otherwise, the controller 1004 proceeds to step 1058.
fn step 1058, the controller 1004 denies access to the storage area
1002.
~o In step 1060, the controller 1004, retrieves the log information from the
log command and proceeds to step 1062.
fn step 1062, the controller 1004 provides a log address which is in
sequence with the address of the previous write-command.
In step 1064, the controller 1004 writes a log entry containing the log
~s information at the log address.
According to a further aspect of the invention, step 1058 may also
include producing an alarm signal to alert a supervisor, and the like.
Reference is now made to Fig. 14 which is a schematic illustration of a
computer 1102 and a device, generally referenced 1100, constructed and
Zo operative in accordance with a preferred embodiment of the invention.
The device 1100 includes a managing controller 1122, two disk drive
input-output (i/o) interfaces 1118 and 1120, an i/o switching unit 1139, two
diskette drive input-output (i/o) interfaces 1137 and 1138, a first pair of
communication interfaces 1110 and 1112 for connecting the computer 1102 to a
25 public network 1136 and a pair of communication interfaces 1114 and 1116
for
connecting the computer 1102 to a secured network 1134, two communication
switches 1140 and 1142 and a display 1144, connected to managing controller
1122.
-32-
CA 02272894 1999-OS-18
WO 98/25372 PCTIB.97/00380
Disk drive input-output (i/o) interfaces 1118 and 1120 are connected to
managing controller 1122. i/o switching unit 1139 is connected to the two
diskette
drive input-output (i/o) interfaces 1137 and 'I 138 and to managing controller
1122.
Communication interface 1110 is. connected to communication switch
s 1142 and to the computer 1102. Communication interface 1112 is connected to
communication switch 1142 and to the public network 1136. Communication
switch 1142 is connected to managing controller 1122.
Communication interface 1114 is connected to the communication
switch 1140 and to the computer 1102. Communication interface 1116 is
~o connected to the communication switch 1140 and to the secured network 1134.
The device 1100 is connected to a storage unit 1124 via i/o intertace
1120. The storage unit 1124 is divided into .a plurality of areas: a menu area
1126,
a secured area 1130, a public area 1128, .a log area 1132 and a password area
1133.
15 The public area 1128 contains data and software which are not
confidential. The secured area 1130 contains data and software which are
confidential. The log area 1132 contains a log file architecture according to
conventional methods or according to the invention) as described hereinabove.
The password area 1133 contains passwords which may be utilized during
Zo various procedures by the managing controller 1122) such as switching
between
modes and the like.
The menu area 1126 includes a pre-operation system menu, which
manages the computer 1102 as the computer 1102 is booted up (i.e., started or
restarted). This menu is loaded into the connputer 1102, and the user is
requested
z5 to choose between working modes, a public mode and a secured mode.
If the user chooses to work in the secured mode, then the computer
provides this selection to the managing contraller 1122 which, in turn,
performs
the following actions:
connects the secured area 1130 to the computer 1102;
-33-
CA 02272894 1999-OS-18
WO 98/25372 PCT/IL97/00380
denies access to the public area 1128;
provides communication switch 1140 with a command to enable
connection between communication interfaces 1114 and 1116, thus connecting
the computer 1102 and the secured network 1134; and
s provides communication switch 1142 with a command to deny any
connection between communication interfaces 1110 and 1112, thus
disconnecting the computer 1102 from the public network 1136.
If the user chooses to work in the public mode, then the computer
provides this selection to the managing controller 1122 which, in turn,
performs
~o the following actions:
connects the public area 1128 to the computer 1102;
denies access to the secured area 1130;
provides communication switch 1142 with a command to enable
connection between communication intertaces 1110 and 1112, thus connecting
15 the computer 1102 and the public network 1136; and
provides communication switch 1142 with a command to deny any
connection between communication interfaces 1114 communication and 1116,
thus disconnecting the computer 1102 from the secured network 1134.
According to the present invention, the device is operable on one of
2o these two modes, the public mode and the secured mode. The public area 1128
and the secured area 1130 each includes an entire operating system. A change
of mode is possible only through resetting the computer 1102 and loading an
operating system from the selected area, according to the selected mode.
Conventional software, such as programs designed for IBM-PC
25 architecture, do not make any use of disk addresses which begin with 0,0,#
except 0,0,1, which contains the primary partition table.
According to a non-limiting example of the present invention, the
addresses beginning with 0,0,1 include the partition table of the secured area
-34-
CA 02272894 1999-OS-18
WO 98/25372 PCT/IL97/00380
1130, the addresses beginning with 0,0,2 include the menu procedure, the
addresses beginning with 0,0,3 include the partition table of the public area
1128,
the addresses beginning with 0,0,4 include a pointer to the log area 1132 and
the
addresses beginning with 0,0,5 include the password area 1133.
According to the present example, the managing controller 1122 denies
all write access to the addresses beginning with 0,0,2, which include the menu
procedure. It will be noted that) physically, the device controls all access
to all
addresses and is able to provide the computer 1102 with various access types
such as read) write and the like of selected addresses.
~o This arrangement provides considerable protection to the areas of the
storage unit) which are associated with addresses 0,0,2 and higher when the
storage unit 1124 is connected directly to another computer which does not
have
a managing controller. It will be appreciated that this arrangement is most
suitable
for portable hard disk drives.
According to the present example, the device 1100 detects when the
computer 1102 is reset and, at that point, provides access to the menu area
1126.
When the device 1100 receives the mode selection from the computer, it resets
the computer physically and connects it to either the public area 1128 or to
the
secured area 1130, according to the selected mode.
2o In conventional computer systems., the operating system can be loaded
from several alternative sources which, for example, are the local hard disk
drive,
a diskette drive, the CD-ROM drive, a network connected to the computer and
the
like. According to the present invention, some of these sources are
predetermined
as unauthorized to provide an operating system and thus are disabled from
doing
SO.
In the present example, the device 1100 can be adapted to secure the
computer 1102 from accidental loading of <~n operating system which is
received
from an unauthorized source.
-35-
CA 02272894 1999-OS-18
WO 98/25372 PCTIQ.97/00380
In the present example, the device 1100 controls the access to a
diskette drive 1135 which otherwise would be connected directly to the
computer
1102. When the computer requires loading of an operating system, the managing
controller 1122 detects this request and accordingly provides i/o switching
unit
s 1139 with a command to disconnect between diskette drive input-output (i/o)
interfaces 1137 and 1138, thus denying access to diskette drive 1135.
After the computer 1102 commences loading an operating system from
storage unit 1124, the managing controller 1122 provides i/o switching unit
1139
with a command to connect between diskette drive input-output (i/o) interfaces
~0 1137 and 1138, thus enabling the computer 1102 to access the diskette drive
1135.
According to a further aspect of the present invention (not shown), in
which the diskette drive 1135 is connected directly to the computer 1102, the
managing controller 1122 measures the time period Tmeas~~ed between computer
15 boot-up and loading of an operating system.
The access and data transfer rate provided by a hard disk drive are
considerably faster than those provided by a diskette drive. Furthermore,
initial
access to a diskette drive, before an operating system was loaded, is
considerably slower, compared with hard disk drives. Hence, Tmeas~ree would be
Zo considerably greater when accessing a diskette drive compared with
accessing a
hard disk drive.
Tboo, is a predetermined value which represents a predetermined
maximal time period required to load an operating system from a hard disk
drive.
Tboot of a hard disk drive is shorter than the Trot of a diskette drive. Thus,
if Tmeag~~d
Zs ? Tboo,, then the managing controller 1122 detects that an unauthorized
loading of
an operating system is in progress and hence, may take several preventive
measures, such as denying all access to storage unit 1124.
When the managing controller 1122 detects a diskette drive boot
attempt, it may operate to halt all operations and provide an alarm, using the
so computer 1102 multi-media capabilities or an external alarm device and the
like.
-36-
CA 02272894 1999-OS-18
WO 98/25372 PCT/8.97/0(1380
Furthermore, the managing controller 1122 can provide computer 1102
with a command which will disable operations therein, either fully or
partially. For
example) the managing controller 112:? can provide computer 1102 with a
constant boot command.
s Display 1144 indicates the currE:nt mode of the device. Display 1144 is
adapted to be attached to the computer 1102 to be seen by the user. According
to
one aspect of the invention, display 1144 is a light emitting diode (LED) or a
LED
array which either blinks differently or changes color in various modes.
According
to the invention, display 1144 can also be a liquid crystal display (LCD)
array)
~o displaying alpha-numerical messages and the tike.
It will be noted that, according to another aspect of the invention, the
managing controller 1122 detects all data received from the diskette drive
1135,
thereby enabling operating system loading access thereto in predetermined
cases, such as maintenance. Operating system loading access to diskette drive
15 1135, may be provided to the computer 1102 only if a predetermined password
is
provided thereto while executing the menu procedure.
Reference is now made to Fig. 15 which is a schematic diagram of a
method for operating device 1100 so as to provide limited data and
communication access to a computer, operative in accordance with another
2o preferred embodiment of the invention.
In step 1150, the managing controller 1122 detects a boot signal
provided by the computer 1102. This signal is provided when the user manually
boots up the computer or when the ca~mputer is turned on. According to the
present example, the managing controller 1122 regards the first attempt to
access
2s address 0,0,1, via the disk drive i/o interface 1118, as a boot signal.
In step 1152, the managing controller 1122 provides the computer 1102
with access to the menu area 1126. The computer 1102 retrieves the menu
software therefrom, executes it and proceeds to step 1154.
-3'l-
CA 02272894 1999-OS-18
WO 98/25372 PCT/8..97100380
In step 1154, the managing controller 1122 awaits to receive instructions
from the user, via the computer 1102, choosing between the various options of
modes (i.e: public, secured and the like). At the same time, the managing
controller 1122 resets a time counter t. The user is required to provide his
s selection within a predetermined time period T. If t>T, (i.e. the user did
not provide
his selection within a predetermined time period T) or the user selects the
secured
mode, then the managing controller 1122 proceeds to step 1162. Otherwise, the
managing controller 1122 proceeds to step 1156.
In step 1156, the managing controller 1122 executes a sequence of
~ o operations which determine the public mode) such as enabling access to
public
devices and denying access to non-public devices, such as secured devices.
Accordingly, the managing controller 1122 connects between the public area
1128 and the computer 1102, thus enabling the computer 1102 to load an
operating system from the public area 1128. The managing controller further
15 provides communication switch 1142 with a command to connect communication
interfaces 1110 and 1112 thus, connecting between the public network 1136 and
the computer 1102.
In step 1158, the managing controller 1122 turns on a public data flag
and turns off a secured flag. In the present example, both flags are memory
2o elements within managing controller 1122. The public data flag indicates
that the
current mode is the public mode. The secured data flag indicates that the
current
mode is the secured mode.
In step 1160, the managing controller detects if the user has provided
the computer 1102 with a command to switch to another mode. If so, the
Zs managing controller proceeds to step 1168.
In step 1162, the managing controller 1122 executes a sequence of
operations which determine the secured mode, such as enabling access to
secured devices and denying access to non-secured devices, such as public
devices. Accordingly, the managing controller 1122 connects between the
so secured area 1130 and the computer 1102, thus enabling the computer 1102 to
-38-
CA 02272894 1999-OS-18
WO 98/25372 PCT/8,97/00380
load an operating system from the secured area 1130. The managing controller
further provides communication switch 1140 with a command to connect
communication interfaces 1114 and 1116 l,hus, connecting between the secured
network 1134 and the computer 1102.
In step 1164, the managing controller 1122 turns on the secured data
flag therein and turns off the public flag.
In step 1166, the managing controller detects if the user has provided
the computer 1102 with a command to sv~itch to another mode. If so, then the
managing controller proceeds to step 1168.
~o In step 1168, the managing controller 1122 provides an operating
system shut-down-restart command to tl~e computer 1102. Accordingly, the
computer shuts down all applications as well as the operating system and
restarts
thereafter. Then, the managing controller 1'122 proceeds to step 1170.
In step 1170, the managing controller 1122 resets the computer 1102.
According to one aspect of the invention, this reset may be performed by
providing a further software boot command to the computer 1102. According to
another aspect of the invention, the reset is performed by providing a
hardware
boot command to the computer 1102. It is noted that, when reset, X86 based PC
computers reset most of the RAM except for the first Mbyte of memory, which
Zo may include undesired software. According to a further aspect of the
invention,
the managing controller 1122 provides a reset-all-RAM command to the computer
1102. After executing step 1170, the managing controller 1122 proceeds to step
1172.
In step 1172, the managing controller retrieves the current setting of the
25 security flag and the public flag. If the security flag is turned on and
the public flag
is turned off, then the managing controller proceeds to step 1156, so as to
switch
from the secured mode to the public mode. Otherwise, if the security flag is
turned
off and the public flag is turned on, then the managing controller proceeds to
step
1162, so as to switch from the public mode to the secured mode. It is noted
that
so when the system determines more than iv4~o modes, such as a plurality of
modes
_3g_.
CA 02272894 1999-OS-18
WO 98125372 PCTlB.97/00380
which define multi-level, multi-user, multi-client situations, the user is
required to
provide his mode selection.
Accordingly, the device 1100 can be adapted to support a plurality of
multiple level security modes, switching between them and enabling or
disabling
access to a variety of devices, links and data locations, respectively.
It is noted that in steps 1156 and 1162, after the computer 1102
commences loading the operating system from the chosen area, the managing
controller 1122 provides i/o switching unit 1139 with a command to connect
between diskette drive input-output (ilo) interfaces 1137 and 1138, thus
enabling
~o the computer 1102 to access the diskette drive 1135.
According to another aspect of the invention, a secured storage area
contains a master boot record (MBR) and performs as a clean media instead of a
removable rescue diskette, which) according to common practice, may not be
available when required.
Reference is now made to Fig. 16, which is a schematic illustration of a
method for operating a device of the invention controlling a secure storage
area
and a public storage area, each containing an MBR, operative in accordance
with
yet another preferred embodiment of the invention. In the present example, the
method is implemented for operating device 1100 of Fig. 14.
Zo In the present example, both the public area 1128 and the secured area
1130, contain operating system boot files.
In step 1200 the device determines a first portion of the storage area as
a primary storage unit and a second portion of the storage area device is a
non
accessible storage unit. In the present example the controller 1122 determines
25 the public storage area 1128 as the primary storage unit and denies any
access
to the secured storage area 1130. In a conventional PC system) the public area
1128 would appear as drive c:.
it will be noted that conventional PC systems are usually defined so that
drive C: is the drive from which the system boots up (i.e. loads an operating
-40-
CA 02272894 1999-OS-18
WO 98/25372 PCT/B.97I00380
system). Furthermore, determining a storage unit non-accessible can be
performed by denying all access to the storage unit, making it read only and
the
like, as long as any data modification operation is denied for that storage
unit.
In step 1202 the device 1100 boots from the primary storage unit. In the
s present example the controller 1122 introduces the public storage area 1128
to
the computer 1102 via I/O interfaces 1118 and 1120 , as drive c and the
computer
1102 loads an operating system from the public storage area 1128.
In step 1204 the computer 1102 detects the presence of unauthorized
code. Unauthorized code can be detected in many ways, such as detecting
~o access attempts, comparing data masks, and the like. It will be noted that
detection of such unauthorized code can be pertormed using anti-virus software
and the like. In the present example, the cornputer provides this information
to the
device 1100, although such information can be provided by a user or by the
device itself when operative to detect such unauthorized code.
15 In step 1206 the computer is reset. It will be noted that such a reset
command can be provided by the unauthorized code detecting software as well
as from the user operating the computer 110!2.
In step 1210, the second portion of storage device is determined as the
primary storage unit and the first portion of the storage device is determined
as
2o the secondary storage unit. In the present e~:ample controller 1122
determines the
secured storage area 1130 as the primary storage unit and the public storage
area 1128 as the secondary storage unit. Accordingly, the device 1100 provides
the secured storage area 1130 as drive c: to the computer 1102 .
The device 1100 also provides public storage area 1128 as drive d: to
25 the computer 1102.
In step 1212 the computer boots from the primary storage unit which
now is the secured storage area. In the present example, computer 1102 regards
the secured storage area 1130 as drive c: and boots therefrom.
-41-
CA 02272894 1999-OS-18
WO 98/25372 PCT/IL97/00380
In step 1214 the unauthorized code element, detected in step 1204 is
disabled. In the present example the computer 1102 executes the virus cleaning
software which is originally stored in the secured area 1130, so as to remove
the
unauthorized code element (i.e. virus software) from the public storage area
1128.
In step 1216 the computer is reset again so as to return to the original
setting wherein the public storage area 1128 is determined as the primary
storage
unit and the secured storage area is predetermined as a non accessible storage
unit.
In accordance with another aspect of the present invention the MBR of
~o the secured mode is contained within the managing controller 1122. 1t will
be
noted that the managing controller 1122 may include an internal storage area
or
an external storage area, such as an EEPROM and the like.
According to a further aspect of the invention, the activation of the clean
boot mode, as described in Fig. 16, can be done on a timely basis, at
predetermined intervals.
It will be appreciated by persons skilled in the art that the present
invention is not limited to what has been particularly shown and described
hereinabove. Rather the scope of the present invention is defined only by the
claims which follow.
-42-