Note: Descriptions are shown in the official language in which they were submitted.
IIEG. '!. l~yy 5:33fM SWAbJi;Y UG1LVY M'fL 514 ~S~ 83~~ 1VU, ~'l59 f. 4/13
-1-
HIERARCHICAL KEY CONTROL FOR ELECTRONIC LOCK$
Field of the Invention
The present invention relates to a hierarchical key control system for
electronic locks as well as to a method and apparatus for programming
stand-alone electronic door IockS using a set of special programming
keys.
Backgr~Und of tho Ittvantlon
Electronic locks ar~ commonly used for providing building
security. In such systems, ar,Cess to a building and secure areas within a
building Is achieved u$ing a data key device, such as a magnetic stripe
card, a proximity card, a smart card, a DaIIasTM key or the like. Given the
ease of use of such data key devices far ap~ning doors, the use of such
electronic door locks is convenient and . presents little burden to
authorized users. The door IockS are known to Include mortise dQOr
locks, latch release mechanisms mounted In the door frame far allowing a
locked mortise door lock to be released from the doer frame, magnetic
door release locks, and in certain circumstances, more sophisticated
a0 turnstile access gates. Such electronic aCCess locks are also used for
controlling the use of elevators.
In the building access security industry, such electronic door
locks fall into two general retegories, i.e. either networked locks or stand-
alone locks. In the networkEd configuration, there is a data network
between each electronic door lock and a central control computer_ In
such a configuration, a code read fr-vm a data key device is compared
with authorized codes entered in a database at the central control
computer to determine whether the door Jock should allow access to the
user. The central control computer also controls changes to access
according to time of day, and in case of an emergency, such as a fire, the
central Gvntroi may allow all doors to be unlocked.
In the stand-alone fype of electronic door lock, the eiectrpnic
door lock is not connected to a central network and must be programmed
by dir8ct manipulation of the individual electronic door lack. This Is
conventionally done by using a data Interface connection between the
stand-alone electronic door lack and a portable computer for canying out
the programming functions. Wh$re a door lock needs to be programmed
sa27~scaaR
decemnar 7, 1999
CA 02292014 1999-12-07
L li V , i . 1 J J J J ~ J J 1 11l U t I IS L li 1 V U 1 L Y 1 1Y11 L J 1 't L
U V V J U J a v, V I J J , 1 , J l 1 J
-2-
with the codes from a large number of data key devices in a facility, the
portable computer is typically canneCked to the electronic door lock in
order to communicate to th$ electronic door lock the codes of all valid
data key devic~s.
It is also known in the art to overcome the need to toad codes for
valid data key devices into an individual electronic door It~ck by using a
set ef codes in the data key devices which the stand-alone electronic door
lock can rECOgnlze as being valid as a result of a characterisfilc inherent in
the code information. In this case, a data key dev(ce from the set Of
14 acceptable data key devices can be barred access to the stand-alone
electronic door lock by using a complementary cannel key having a code
which the stand-atone electronic door lock automatically recognizes as
being the cancel code for the key device to be cancelled. In this known
art, it is necessary to use a set of C~Sdes with the clefs key devices such
that th~ stand-alone electrpnic door lock can recognize a valid access
card and recognize a valid cancel card for a particular access Card.
There is thus a need for a stand-along electronic door lack which
does not require the burden of a portable computer and data Interface for
carrying out programming functions and which does not Ilmit the lode to
2D the use of a predetermined set of codes recorded in the data key devices,
There Is furthermore a ne$d for such a stand-alone electronic door luck in
which the programming is simple, stepwise and flexible tp the needs of
small and medium facilities.
Summary of the Invention
It Is accordingly a first object of the present invention to provide
a stand-alone electronic door lock In which a set of Dearly identified
special data key devices are used for programming and control purposes,
in which a first special data key device acts as a start-up key for
initializing the lock with a code including a site cads. A second key device
in the set is used as a learn or program data key device. The start-up
data key device Contains an encrypted code which the leek decrypts using
a manufachrrer"s encryption key, and the remaining special data key
devices in the set use codes which can be authenticated by the lock us(ng
the site code data. Remaining special data key devices may be used to
cant' out such functions as lockout, emergency open, temporary unlock or
passage mode, card cancel mode and to inmate an audit trail download.
8027-56CAPF~
December T, 199
CA 02292014 1999-12-07
rli~;G, 'f, l~yy 5:,~3r~ SWAb~;Y ulilLVY M'fL 5n lda a~~~ Flu, ~'f5y r, ti/l3
-3-
It is furthermore an object of the present Invention to provide a
stand-2~Ione electronic door lock programming system which uses a set of
sp$cial data key devices which are identifred by numbsr, the start-up data
key device b~ing numbered #1, the learn data key device being
numbered #2, and remaining ones of the set of special data key devices
being sequentially numbered #3 and up.
It is furthermore an object of the present invention to provide a
stand-alone electronic door lock in which a master level data key device
can be programmed in addition to ordinary level user data key devices.
14 Preferably, white individual user keys can be cancelled with a
corresponding cancel key, master level keys cannot be cancelled by a
corresponding Cancel key, however, al) master level keys can be
cancelled using a master level cancel key from the set of special data key
devices used for programming and a~ntrol purposes. Preferably, a
. master level key Is allowed access at all times, and is able to unlock a
double-locked door, i.e. thp master level key preferably is able to unlock a
deadbolt,
It is a further object of the present Invention tv provide a method
for initializing and programming a number of stand-alone electronic door
locks installed in a facility in which a start-up data key device is used to
permanently set each stand-al4ne electronic door lock with a site code.
Preferably, the use of the start-up data key device is done with all looks in
the facility prior to programming each stand-alone electronic door lock
with each user access and user cancel key.
According to a first broad aspect of the invention, there is
provided a m~thod of programming a stand-atone electronic door look,
activated to open using a plurality of d2~ta key devices, and programmed
to accept new valid data key devices using a special data key device.
The method Comprises providing a set of special data key devices used
for programming and control purposes, reading a start-up data key device
to decrypt data therein and record a site code associated with the set of
special date key devices, reading a learn data key device to decrypt data
therein, comparing the decrypted data with the site code, causing the lock
to enter a new valid access data key learn mode when the comparison Is
3~ positive, reading a first previously unknown code contained in a first new
data key device while in the learn mode to record the first unknown code
as a valid access code for operating the lock, and reading a seC4nd
8027-56CAPR
DeCamber 7, 1999
CA 02292014 1999-12-07
~l>;~, J, ly~y ~:J4rM aw~n~r umLVr ~nlL X14 Cdr dJay uu. dl~~ r, I/iJ
-4-
previously unknown code contained in a second new data key device
while in the learn mode to retard the second unknown code as a c8rlcel
code paired with the valid access code of the first new data key device.
In use, the look is activated to open in response to the valid access code
of the first new data key device, and is activated to Cancel the recorded
valid access code in response to the cancel Gode of the second data key
device.
Brief Description of the Drawings
The invention will be better understood by way of the following
detailed description of a preferced embodiment with reference to the
appended drawing in which:
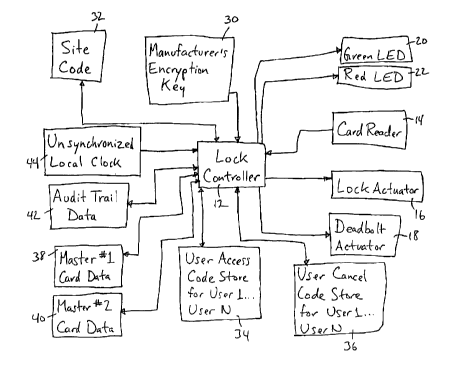
Figure 1 Is a schematic block diagram of the stand-alone
electronic door lock according to the preferred embodiment.
Detailed Description of the Preferred Embodiment
As illustrated in Figure 1, the stand-alone electronic door lock
according to the preferred embodiment can be adapted for the full range
of mortise and cylindrical lock chassis in which an electromechanical lock
actuator 16 causes the deer lever to engage a drive for retracting the
latch. A deadbolt actuator 18 likewise Is capable of causing the door
lever to retract a deadbolt within the lock. Although not shown in Figure
1, the l4Ck may be provided with a mechanical key override and may be
provided with a panic device for overriding the lock In an emergency
situation.
In the preferred embodiment, the lock microcontroller 12 is
connected to a magnetic stripe card reader 14 although other forms of
data key devices and readers 1~ are contemplated within the scope of the
present invention. The lock controller 12 controls a green LED 20 and a
re~1 LED 22 for providing feedback to the user during operation and during
programming.
In the preferred embodiment, the key Cards coma in two "packs",
namely, a starter pack which is the Set of special data key devices
including the start-up key card (number 1 ), the team key card (number 2) ,
a lockout key card (number 3), an emergency key card (number 4), a
passage key card (numb$r 6), a master level cancel key card (number 6),
and an audit key card (number 7). The data on these key cards is
8021-56GAPR
December 7, 1999
CA 02292014 1999-12-07
uLV. r. 1~5~ U.JW m UrrnuL~ vmLU mL ;J1~ LUU UJU~ uv, UrJ~ 1, U! 1J
-5-
encrypted with a random code and the code is unique for each starter
pack. Th~ user pack is a set of user access key cards and user cancel
key cards. The cancel key cards are preferably labeled with a cancel
symbol or appropriate text to clearly identffy those cards as cancel cards,
although these cards have the same encoding format (ABA format) and
the data on the user key cards is not encrypt$d. In the starter pack of key
Cards, the cards are preferably nurrlbered #1 through #7 with clearly
visible indicla and color coding with the cards being labeled with the
numbering recited.
In the preferred embodiment, there can be up to 200 master
level #1 or #2 users. The number of such users is merely limped by
memory and design choice, and any number of such users can be
provided.
When the start-up key card is used, the card reader 14 r$ads the
encrypted data on the Start-up card and the lock controller 12 decrypts
the data, using the manufacturer's encryption key 30 and extracts a site
code for the lack and stores it In a memory location identified as 32. If the
site cod~ memory 32 already contained a site code, the lock controller 12
would Ignore the start-up card. To move a lock from one facility to a new
facility, the site code memory 32 needs to be reset, which is done by
disabling the battery power to the lock for a sufficient period of time to
erase the memory. It will be appreciated that other means of erasing the
site code memory are possible. ~nc$ the lock controller has determined
the site code and stored the site code in memory 32, the lock is ready to
operate with any of the cards #2 through #7 of the start-Up key card set
and, of course, only those cards from the set of key cards determined by
the start-up key card will be functional with the lock.
In the presently preferred embodiment, the team key card
labeled as #2 is swiped in the Card reader 14 as the first step In
$0 programming the lock. The lock controller 12 decrypts the data on the
learn card using the site code and coni9rrns that the learn key card
belongs t4 the same pack as the startup Card. At this point, the lock
controller 12 enters the "learn" mode and waits for a subsequent card to
be swiped. In the presently preferred embodiment, the next magnetic
stripe card passed through th$ card reader 14 will be read and the
identification code on the key card will be memorized. If the next card
swiped through thra card reader 14 Is a different card having a different
eD27-58CAPR
Decem~r 7, 1989
CA 02292014 1999-12-07
uL~. I, 1~~~ J.JJmI JrrnLl:>, vmLm mL ;ll~ LUU UJUJ uv, U1;1~ t, ~/ IJ
_g_
code, then th$ controller 12 adds the first user card swiped to the list of
user access codes 34 and then adds the code of the second key card
swiped to the list of user cancel codes 36. If the same card is swiped
twine, the Jack controller 12 re~vgnizes that card as the master level #2
card whose code is ataretl in memory 40. If the same Card is swiped a
third time, then the l4ck controller 12 will recognize the card as the master
#1 card and store its code in memory 3B. Storage of card key codes in
memory can be deferred until the learn card key #2 Is swiped again,
Both master level key cards have the unique privilege of being
able to actuate the lock actuator 16 as well as the deadbolt actuator 18.
Furthermore, in the presently preferred embodiment, the master level #1
data card is provided with an additional privilege, namely, it may place the
lock in an unlocked passage mode far a predetermined time peripd,
preferably nine hours. In the preferred embodiment, the master level #1
1 g card key is preferably used by a senior manager or smal) business owner
who "opens up sh4p" and may wish to unlock some doors for an entire
working day. The passage mode is entered using the master level #1
card key by swiping the card twice In short succession.
It will be appreciated that all of the magnetic stripe cards used
for aCbess may be any standard magnetic stripe card such as a bank card
or credit card. In the preferred embodiment, the master cards do not
have corresponding cancel cards, but rather, the master level cancel is
provided within the starter pack of key cards card for canceling all master
users. It will be appreciated that in an environment where a larger
number of master level cards is required, it would be possible to provide
for individual master level cancel carcls rather than a single master level
cancel card for removing ell master users.
Each time a user swipes a card through the card reader 14, the
lock controller 12 records the data read from the card, the time from the
unsynchronized local clock -0~4 as well as the status, such as access
denied, access granted, passage mode entered and user cancelled,
which audit trail data is recorded in memory 42. The memory 42
preferably stores sufficient data for a relatively gong period of time which
may vary from a week to several months. When the audit card is read by
the card reader 14, the lock controller decrypts its code and determines
whether the audit card read is from the same starter pack, i.e. whether its
site code matches the site code in the memory 32. If this is the case, the
802T-56CAPR
December 7, 1999
CA 02292014 1999-12-07
uL~, J. l~~y ;J~J;Jrm ~nriDD,I VmLm mL ;J14 G00 OJO~ uv, Of;l~ j, lU/1J
-7-
lock controller i 2 allows the audit trail data in memory 42 to be uploaded
via a bus (not shown) to a portable computer, When the controller 12
outputs the audit trail data, It reads the curr$nt unsynchrnnized local clock
and outputs the current local time whloh the portable computer matches
with its own real time clock, In order to provide an accurate time reference
for the unsynchronized local clock 4.4. In this way, th6 audit trail data 42
can be adjusted to represent real synchroni=ed time, While in the
preferred embodiment, tha adjustment t4 real time is done In the portable
computer, it could likewise be done in the lock controller 12 Itself by first
reading the real time from the portable computer, and then adjusting the
time data in the audit trail data 42.
Although in the preferred embodiment a single learn card is
used for learning both master level and user level cards, It would be
possible tG provide two separate learn Cards, orte for learning master level
cards and another for learning user level cards. This may be
advantageous In circumstances in which the arrival of a new employee
requires using the team G&rd at each stand-alone eleGtmnic door lock In a
facility along with the new employee's user card and user cancel card. To
avoid accidental dr intentional misuse of the single learn card which would
result in the Creation of a master level Gard, the provision of a user learn
level card can be used. Under such circumstances, the task pf learning a
new user level card can be delegated to someone who is not a master
level user without posing a security risk.
Although in the preferred embodlrrient the cancel card can be
any us~r key card, cancel cards can also be key cards (or other data key
devire$) which the lock controller 12 can identify as cancel Card keys.
This can be achieved either by using a header code or the like which
identifies the card to tha IOck as a cancel card. Likewise, the card key
code can be encrypted, and the information that the cancel card is a
genuine Cancel card can be det~rmined either from the successful
decryption of the cods recorded en the card key andlor by the presence
of a header code or the like. The lock controller 12 can then only accept
card keys, Identified as cancel cards, during enrolment or registration as a
cancel card. The controller can also refuse a G2rd key, identified as a
cancel card, during registration or enrolment as a user card. In this way,
there can be no confusion between user access cards and user Cancel
cards. It will also be appreciated that the same type of coding could be
8027-68CAPR
December 7, 1999
CA 02292014 1999-12-07
yLV, ~, 1~~~ J.JU1111 JttrilJl:l VU1LY1 1Y11L ;11~! LUU UJU~ 1V V, UIJJ 1,
1111)
used with master level cancel card keys, in the case that cancel card keys
are used for master level users.
It will be appreciated that many vartation6 to the preferred
embodiment described above aro possible within the spirit and scope of
the present invention.
8027-58CAPR
DecembQr 7, 1999
CA 02292014 1999-12-07