Note: Descriptions are shown in the official language in which they were submitted.
CA 02301383 2000-03-20
1
Monitoring the Transmission Quality
in a Digital Communications Network
This invention relates to a method of monitoring the
transmission quality in a digital communications
network and to a network element for a digital
communications network.
Digital communications networks are structured
according to a multilayer model, such as the 7-layer
OSI model. To monitor the transmission quality
("performance monitoring") in digital communications
networks and particularly in synchronous digital
communications networks, such as SDH or SONET
networks, it is common practice to determine
performance monitoring data in each layer, store these
data, and transmit them on request to a central
control unit, the network management system. To that
end, various parameters that characterize the
transmission quality are determined and counted over
predetermined periods of time, typically 15 min and 24
h. Typical parameters are: background block errors,
errored seconds, and severely errored seconds.
Performance monitoring takes place in network elements
of the communications network in which connections are
switched or terminated. The performance monitoring
CA 02301383 2000-03-20 .
2
data are stored as managed objects in a management
information base (MIB) of the respective network
element.
Frorn an article by T. Apostolopoulos et al, "On the
Implementation of a Prototype for Performance
Management Services", Proceedings IEEE Symposium on
Computers and Communications, June 27-29, 1995, a
performance-monitoring method for a TCP/IP network is
known which involves storing performance monitoring
data as managed objects in an MIB database and
transmitting them to a management facility. The method
is designed and suited for a single, homogeneous
network consisting of subnetworks which is under the
control of a single network operator and is managed by
a single central network management system.
In digital communications networks, the situation
described is becoming increasingly complex because of
the increasing number of network operators and service
providers, which are generally not identical. This
situation is shown by way of example in Fig. 3. A
customer 37 requests from a service provider 34 a
connection 38 from a location A, 35, to a location B,
36. The~'service provider 34 cooperates with several
network'operators 31, 32, 33, which each provide
subconn~ctions. The service provider 34 books the
subconnections at the network operators and
interconnects the subconnections at interfaces IF to
establish the connection 38 desired by the customer.
The service provider 34 makes the requested connection
38 available to the customer 37 and guarantees a
predetermined transmission quality. The network
operators 31, 32, 33 guarantee the service provider 34
a predetermined transmission quality for each of the
CA 02301383 2000-03-20
3
subconnections switched by them. Charges are made by
the service provider 34 to the customer 37 and by the
network operators 31 to the service provider 34 for
the services provided.
Each network operator has its own network management
system in which performance monitoring data can be
collected and retrieved. These data give information
about the actual transmission quality, and thus about
the quality of the service provided. So far neither
the service provider nor the customer has access to
the performance monitoring data of the individual
network operators, so that it has been impossible for
them to determine and monitor the actual transmission
quality.
For the service provider it is desirable to be able to
determine the actual transmission quality and, in case
of a dispute, prove to the customer and the network
operators that the service was actually provided. Such
proof cannot be furnished with the performance
monitoring data used so far, because such data are
manipulable. It is therefore an object of the
invention to provide a secure method of monitoring the
transmission quality. Another object of the invention
is to provide a network element for a digital
communications network which permits secure monitoring
of the transmission quality of a switched connection.
These objects are attained by the features of claim 1
and claim 6, respectively. Further advantageous
aspects of the invention are apparent from the
dependent claims.
One advantage of the invention is that the encryption
of the performance monitoring data precludes any
CA 02301383 2000-03-20
4
manipulation of the performance monitoring data, so
that the performance monitoring data can be used to
furnish proof that the service was actually provided.
The invention will become more apparent by reference
to the following description of an embodiment of the
invention taken in conjunction with the accompanying
drawings, in which:
Fig. 1 is a block diagram with the functions of the
monitoring device and the subsequent encoding
in accordance with the invention;
Fig. 2 is a block diagram of a network element in
accordance with the invention;
Fig. 3 shows the logical establishment of a
connection in a digital communications
network;
and
Fig. 4 is a flowchart of the method in accordance
with the invention.
A fundamental idea of the invention is to ensure the
integrity of performance monitoring data through the
use of an encryption process, e.g., through an
electronic signature.
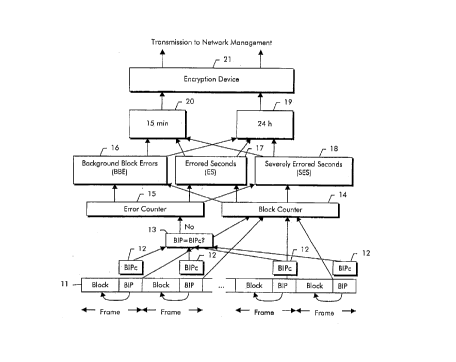
The determination of the performance monitoring data
at a network element of the digital communications
network is shown by way of example in Fig. 1. First,
however, the architecture of the network element will
be explained with the aid of Fig. 2. The network
element 27 has a number of input/output ports I/O, 25,
which are interconnected via a switching matrix 24.
Connected to the switching matrix 24 is a monitoring
device CPU, 23, which performs the functions shown in
Fig. 1 for each switched connection. The switching
matrix 24 may, for instance, be a processor with
CA 02301383 2000-03-20
associated memory, with the functions being
implemented as parts of a control program. The
performance monitoring data determined by the
monitoring device CPU, 23, are fed to !an encryption
device ENCRYPT, 21, and subsequently shored as managed
objects in a memory 22 structured as a database. On
request, the encrypted data can be transmitted via an
interface Q-IF, 26. The interface may, for instance,
be the Q interface commonly used for network
management. The encryption device 21 may preferably be
combined with the processor serving as the monitoring
device 23 on a single chip. The network element 27 may
be a digital crossconnect or an add/drop multiplexer
of an SDH or SONET network, for example.
The monitoring device performs the functions shown in
Fig. 1. At one of the input/output ports 25 of the
network element 27, a message signal 11 is received
which is organized into frames. Each frame consists of
a payload block and a header. In the header, a
checksum BIP is transmitted. From each payload block,
a new checksum BIPc l2 is computed, which is compared,
13, with the checksum BIP contained in the header. If
a disagreement is detected, an erroneous block was
received. Both the received blocks 14 and the
erroneous blocks 15 are counted. From the counts 14,
15, the above-mentioned known parameters, i.e.,
background block errors (BBE) 16, errored seconds (ES)
17, and severely errored seconds (SES) 18, are
determined. An errored second is present if in a one-
second interval, errors are present, but less than 30~
of the blocks are erroneous. A severely errored second
is present if in a one-second interval, more than 30~
of the received blocks are erroneous. The parameters
are added over 15 min, 20, and over 24 h, 19. These
CA 02301383 2000-03-20
6
values 19, 20 represent the performance monitoring
data and are available as ASCII text.
The network element 27 generates such a record of
performance monitoring data 19, 20 for each connection
that is switched or terminated by it. Advantageously,
each data record 19, 20 is treated and stored as a
managed object.
According to the invention, the performance monitoring
data 19, 20 are encrypted with the encryption device
21 following the monitoring device 23. The encryption
device 21 converts the performance monitoring data 19,
so that their authenticity and integrity can be
checked later. To that end, the encryption device 21
adds an electronic signature to each performance
monitoring data record 19, 20.
An algorithm using a private key and a public key,
such as the well-known RSA algorithm, is particularly
20 suited for the encryption. The encryption device 21
will then load the required key via the communications
network. Each key is preferably generated and made
available by an independent, trustworthy organization,
such as the Deutsches Bundesamt fur Telekommunikation
(German Federal Office for Telecommunications). The
generally acknowledged integrity of this independent
organization additionally guarantees the integrity of
the encrypted data.
Through the electronic signature, the performance
monitoring data can be read, but not modified, by any
authorized person who has the key.
Each encrypted data record is stored as a managed
object in a management information base (MIB) 22 of
CA 02301383 2000-03-20
7
the network element 27, and can be transmitted on
request via the interface Q-IF, 26, to a network
management system. The encrypted performance
monitoring data for a particular connection can now
also be made available to service providers and
customers who are to be charged for the connection.
Fig. 3 shows the above-described logical establishment
of a connection 38 in a digital communications
network. A customer 37 requests a connection 38 from a
service provider 34. The service provider 34 has
rented subconnections, e.g., in the form of leased
lines, from three different network operators 31, 32,
33. The service provider interconnects the
subconnections at interfaces IF to establish the
requested connection 38, and makes the latter
available to its customer 37. To be able to guarantee
its customer 37 the required quality of the connection
37, the service provider receives from each network
operator 31, 32, 33 the encrypted performance
monitoring data of each subconnection. The service
provider can use these performance monitoring data to
prove to its customers and to the network operators
that the service was provided. If the required
transmission quality is not reached, this can be
offset, for example, by a reduction of the charges to
be paid by the customer and by giving a discount on
the rental charges for the leased lines.
In a particularly advantageous application of the
invention, a service provider that requests a
connection from a network operator specifies to the
latter a key for this connection. The key is only
valid for a requested connection. The service provider
can retrieve the performance monitoring data encrypted
with this key from the network elements or the network
CA 02301383 2000-03-20
8
management system of the network operator. In this
way, the service provider can control the actual
connection quality and has guarantee that the
performance monitoring data actually correlate with
the requested connection.
The sequence of steps in the method according to the
invention is shown in Fig. 3:
Step 1: A service provider or a customer requests a
connection from a network operator.
Step 2: The network operator establishes the
requested connection in its communications
network and makes it available to the
service provider or customer.
Step 3: A key is transmitted to each network element
by which the connection is switched or
terminated.
Step 4: In each network element, performance
monitoring data are determined.
Step S: In each network element, the performance
monitoring data are encrypted with the
transmitted key and provided with an
electronic signature.
Step 6: The encrypted performance monitoring data
are stored as managed objects in a database
of each network element.
Step 7: On request, the encrypted performance
monitoring data are transmitted to the
service provider or customer.