Note: Descriptions are shown in the official language in which they were submitted.
CA 02308808 2000-OS-18
A SYSTEIVI AND METHOD TO DISCRIMINATE CALL CONTENT TYPE
CROSS-REFERENCE TO RELATED AP~LiCATIONS
This application is a continuation-in-part of U.$. Patent Application Serial
No.
091210,341 entitled TELEPHONY SECCTRITY SYSTEM filed December 11, 1998,
assigned to the assignee of the present application and incorporated by
reference in its
ent~rcty.
TECHNICAL FIELD
The invention relates generally to telecommunications access control systems
and,
more particularly, to a system and method which permits a telecommmications
firewall
to enforce a security policy based on discrimination between a plurality of
call content
types and to autonomously terminate the call in enforcement of the security
policy.
BACI~GROL ND OF THE Ih'VEIYTIOY
Data network users in today's corporations and government agencies can easily
add unauthorized modems to their computers to facilitate remote login. This is
often
done with innocuous intentions, but is a serious network security issue
nonetheless.
Rogue modems-modems that are not authorized by the organization, bui have been
connected to a computer system by an employee, circumvent the traditional
Internet
firewall, routers and intrusion detection systems.
CA 02308808 2000-OS-18
Attorney Docket No. 25647.119
With a rogue modem having opened the "back door" of the security perimeter,
the
organization's network is vulnerable to "hackers" or "phreakers" attempting to
access the
private data network via the Public Switched Telephone Network (PSTy.
Unscrupulous
individuals with Larcenous or malicious intent can use a war dialer to seek
out and
identify insecure modems, penetrate their computer systems and gain access to
the data
network beyond.
An additional vulnerability involves authorized users performing unauthorized
activities from within the prix ate network. This is of special concern in
high-security
environments where outside transmissions are normally carefully monitored to
ensure
corporate or government secrets are not inadvertently or deliberately
transmitted.
Telecommunication firewalls, such as the device described in U.S. Patent
Application Serial No. 09/210,347 entitled TELEPH~NY SECURITY SYSTEb~ are
recently-developed devices that protect an organization's data network from
access via
telephony resources. A telecommunications firewall is configured with a user-
defined
1 ~ secut~ity policy that is downloaded to ane or more line sensors installed
in-line on the
user's side of the demarcation line. A line sensor determines a plurality of
call attributes
comprising call source, destination and call content type from the call
passing through the
line sensor. Prescribed actions (including that of the line sensor allowing or
denying the
call} are performed based upon the call attributes determined and the security
policy.
Although the line sensor is capable of determining a plurality of call
attributes, the
call content type {e.g., whether the call content is voice, fax or data), is a
pivotal attribute
in the security rules that address many of the calls that a telecommunications
firewall is
designed to detect andlor terminate. For instance, a modem transmission Pram a
line that
is designated for only voice use is indicative of a rogue modem. A data
transmission to a
voice-designated line is indicative of a possible hacking attempt, or again, a
rogue
modem on the line. An after-hours voice call or modem transmission from a line
designated for fa.Y use is indicative of an unauthorized call or possible
espionage.
-2-
CA 02308808 2000-OS-18
Attorney Docket No. 25647.1 I9
Very clever hackers may attempt to penetrate data networks by emulating one
type of call to get past the firewall, then change to another type once the
colt is allowed.
Therefore, changes in call content type are highly suspect and a security
policy may
require termination of such a call.
However, some government agencies such as the FBI and the CIA, the military
and same NATO agencies, use a telephone encryption device known as Secure
Telephone
Unit-III (STL-III), to conduct classified conversations or transmit classified
data. A
STU-III may be used as a typical telephone to initiate a call, but when users
"go secure"
by fuming an encryption-activation key, the voice conversation is digitized at
the unit,
encrypted and then transmitted using a standard modem to the receiving STU-III
device
where the process is reversed. The term "STU-III-voice" is used herein to
refer to the call
content type of a STL-III encrypted voice transmission.
A STU-III device is also used as a modem to transmit data to another STU-III
location. In the ''data modem" mode, the data is encrypted before it is sent
to the
receiving STU-III device. The term "STU-III data' is used herein to refer to
the call
content type of a STU-III encrypted data transmission.
Obviously the change in call content type when a STU-III transmission goes
from
insecure voice to secure data would be permitted in a security policy.
Therefore a further
discrimination between the voice band data of STU-IIi encrypted call content
types and
that of typical data (modems and fax content types is needed.
A plurality of telecommunications fraud prevention devices exist which use and
determine call-type attributes such as if the call is made from a pay phone,
if it is cellular
originated or terminated, if it is made toffrom a number or country code with
a high
occurrence of billing fraud, if the call is long distance, toll free, a credit
card call, etc.
2~ However, call-type attributes such as these are not relevant to protecting
a private data
network from unauthorized access via the telecommunications network.
Additionally,
-3-
CA 02308808 2000-OS-18
Attorney Docket No. 25b47.119
devices such as these do not continue to discriminate content type after the
call is
connected.
Other devices are capable of detecting calls that violate a security policy,
but
cause time delays and a drain on manpower resources because they require
notices to be
sent to supervisory personnel for either approval to ternunate or for manual
follow-
through by personnel to ultimately terminate the call.
Still other devices include components for classifying telephone signals, but
none
of these devices comprise the comparable arrangement of single, combined
transmit and
receive signal processing, continuous content discrimination and autonomous
call
termination capabilities needed for the specialized task of protecting a
private data
network from unauthorized access via the telecommunications network.
Therefore, what is needed is a system and method by which an in-line sensor
conrinuously discriminates between call content types comprising voice, fax,
data
(modem), STU-III voice and STU-III data (modem) using inputs derived from
analysis of
the call passing through the sensor, and then autonomously enforces a security
policy.
SUMMARY OF THE IuIVEI~TION
The present invention, accordingly, provides a system and method for an in-
line
sensor to enforce a security policy by discriminating betty een call content
types including
voice, fax, data (modem), ST'G-III voice and STU-III data (modem), and to
continue to
enforce the security policy against an allowed call, discriminating content
type changes
after the call is connected_ Inbound and outbound calls are allowed or denied
(i.e.,
blocked or "hung-up") according to a security policy that is managed by a
security
administrator. If the call violates security policy at any time, the call is
autonomously
terminated.
To this end, in one embodiment, the line sensor processes the combined signal
from both the transmit and the receive side of the communication channel as
one single
CA 02308808 2000-OS-18
_l~ttorney Docket No. 251147 119
signal. Filtered tonal events as well as raw signal frequency and energy
indices are used
to discriminate between voice and voice band data (VBD} content type. Voice
band data
is considered herein to be any modulated data output by devices such as a fax,
modem, or
a secured STU-III. Further discrimination between voice and a plurality of VBD
content
types (fax, data modem and STU-III), is provided by a content type
discrimination state
machine which uses tonal event notices, the output of the previously mentioned
frequency and energy statistical analysis between voice and VBD, and
demodulated
signal analysis. The line sensor operates in a continuous processing loop,
continuing to
discriminate call content type after the call is connected.
A system and method for discriminating call content types far individual
telephone lines at a plurality of user sites outside of a Public Switched
Telephone
Network (PSTN) is described. The system may include: a database containing
security
rules for each of a plurality of extensions, the rules specifying actions to
be taken based
upon a call content type of the call an the extension, wherein the call
content type is
IS determined at the user sites outside the PSTN; and a line sensor within the
user sites
outside the PST~T for determining the calf content type of the call. The line
sensor
continuously checks the call content type to determine if the call content
type changes.
Alternate embodiments are contemplated whereby other VBD content types such
as transmissions from a teletypewriter (TTY) device (used by deaf or speech-
impaired
?U individuals), are discriminated from fax, data (modem), STU-III voice and
STU-III data
to allow additional content type-specific security policy rules to be
implemented.
In another alternate embodiment it is contemplated that discrimination of fax
and
data (modem) content type is further refined to discriminate transmission
protocols andlor
host-based applications, thereby allowing implementation of protocol-dependent
or
25 application-dependent security policy rules. Such rules require use of an
"organization
approved" or more highly secure protocols and applications in order for calls
to be
allowed.
CA 02308808 2000-OS-18
Attome~r Docket No 25b47 119
An additional alternate embodiment is contemplated whereby the information
from the transmit side and the receive side of the communication channel is
processed
separately instead of being combined into one single signal.
A technicat advantage achieved w ith the invention is the ability to
discriminate
between call content types comprising voice, fax, data modem, STU-III voice
and STL1-
III data, thereby providing call attributes that are critical to protecting a
data network
from access via telecommunications resources.
Another technical advantage achieved with the invention is the ability to
discriminate if the call type changes after the call is connected, thereby
providing
protection from hackers emulating one call type and later changing once the
call is
connected, while still allowing STU-IiI calls.
Another technical advantage is the ability to autonomously terminate a call if
it is
in violation of the security policy, thereby eliminating unacceptable time
delays or
manpower mquitements.
Yet another technical advantage achieved with the invention is the ability to
process a single, combined transmit and receive signal, thereby achieving
efficient and
minimal use of processing resources.
BRIEF DESCRIPTION OF T'lIE DRAWINGS
The navel features believed characteristic of the invention are set forth in
the
appended claims. The invention itself, however, as well as other features and
advantages
thereof, will be best understood by reference to the description which
follows, read in
conjunction with the accompanying drawings wherein:
Fig. 1 is a schematic block diagram of an exemplary telecommunications
firevvall;
Figs. 2A and 2B illustrate a schematic block diagram of the preferred
embodiment
of the present invention;
Fig. 3 is a flaw diagram illustrating discrimination bet<veen voice and voice
band
data by the system of Figs. 2A and 2B;
-6-
CA 02308808 2000-OS-18
Attorney Docket No. 25647 I 19
Fig. 4 is a is a state transition diagram illustrating further discrimination
of voice
or voice band data content types by the system of Fig. 2B;
Fig. 5 is a schematic block diagram of the call termination circuitry for
analog
lines in the present inv ention;
Fig. bA is a schematic block diagram of one embodiment of the call termination
circuitry for T1 lines in the present invention;
Fig. 6B is a schematic block diagram of an alternate embodiment of call
termination circuitry for T1 lines in the present invention; and
Fig. 7 is a schematic block diagram of the call texmination circuitry for
ISDI~r
lines in the present invention.
DETAILED DESCRIPTION OF TAE PREFERRED EMBODIMENTS
The present invention can be described with several examples given below. It
is
understood, however, that the examples below are not necessarily limitations
to the
present invention, but are used to describe typical embodiments of operation.
Fig. 1 is a schematic block diagram of an exemplary telecommunications
firewall
similar to the one implemented as shown and described in U.S. Patent
Application Serial
No. 09/210,347 comgrising a plurality of line sensors 100 of the present
invention
(designated by a line sensor 102, 104 and 106), a firewall client 108, and a
firewall
management server 110; all electrically connected for interaction as described
below.
The firewall client 108 is a point of user interface for configuring a
security
policy, displaying and viewing teal-time alerts, printing event logs, reports,
and other
operational features of the telecommunications frewall.
The firewall management server 1 I0 receives the security policy from the
firewall
client 148 and pushes a copy of the security policy to each line sensor 100.
Each line
sensor 100 receives the security policy from the firewall management server I
10,
monitors incoming and outgoing calls, and allows, denies, or otherwise
manipulates calls
7_
CA 02308808 2000-OS-18
Attorney Docket No. 25647 119
in accordance with the security policy and based on a plurality of call
attributes including
cal i content type.
The line sensor l00 is connected in-tine, on the user's side of a demarcation
line
112 between a central office 114 and public branch exchange (PBX) 116, whereby
connectivity may be a combination of direct connects at line sensor 102, PHX
trunk-side
connections at line sensor 104, or PBX station-side connections at lint sensor
106. Line
sensors I04-I06 are not required at all of these points, but can be installed
in accordance
with the configuration of lines and the user's desired level of security
control.
Also in Fig. 1, numerals 118, 120, and I22 designate end user stations 124,
representing as examples, one or more modems i 18, fax machines 120, and
telephones
122. The modems 118 may be connected to a desktop or portable personal
computer.
Individual extensions I26 connect each of the stations 124 at line sensor 106
(or to the
PBX 116 if this configuration of line sensor is not present).
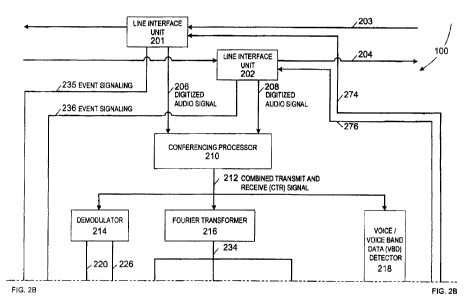
Figs. 2A and 2B illustrate the line sensor 100 by which inputs are made into a
1 S content type discriminator (CTD) 200, which operates to discriminate the
content type of
an inbound or outbound call passing through the line sensor.
A line interface unit (LILT 201, and a LILT 202 continuously monitors traffic
on
both a transmit side 203 and a receive side 204 of a plurality of
communication channels.
The LiUs 201 and 202 send a copy of a digitized audio signal 206 and 208 to a
conferencing processor 210. Although it is not shown, it is understood that in
some
telephone line protocols, both the receiving and transmitting signal are
present on the
same wire pair, thereby requiring only one LIU, If this is not the case, the
conferencing
processor 210 combines the separate signals into a combined transmit and
receive (CTR)
signal 212. The CTR signal 212 is sent to a demodulator 214, a Fourier
transformer 216,
2S and a v oice/voice band data (VIVBD) detector 218.
The demodulator 214 is representative of a plurality of moderns operating at
protocols comprising V.21 and Bell I03_ Y.21 demodulation is used to detect T-
30 flags,
which are indicative of fax handshaking. ~T.21 demodulated data 220 is sent to
a T-30
_g_
CA 02308808 2000-OS-18
Attorney Docket No. 2564?.119
flag counter 222, If a sequence of m T-30 flags is detected; where m is a
predetermined
number of a consecutive series of T-30 flags sufficient to indicate standard
fax
handshaking and not just random data equivalent to a T-30 flag; a T-30 flag
notice 224 is
sent to the CTD 200. Similarly, Bell 103 protocol is used tv detect STU-III
handshaking.
Bell 103 demodulated data 226 is sent to a STU-III validator 228. The data is
evaluated
against STU-III specifications, and either an invalid STU-III data notice 230
or a valid
STII-III data notice 232 specifying the type of STU-III content (STLT-III
voice, STU-III
data, or STU-III unspecified), is sent to the CTD 20(?.
In the Fourier transformer 216, an algorithm based on the Fourier transform is
I4 used to transform the CTR signal 212 into spectral components
(frequencylamplitude
pairs), that define the frequency content. A copy of the transform result 234
is sent to a
DTMF tone detector 238, an MF tone detector 240 and a general tone detector
242, each
of which filter and analyze the transform result 234 for the presence of
speciftc tonal
frequencies.
The DTMF tone detector 238 and the MF tone detector 240 fool' for the presence
of DTMF and MF tones. The general tone detector 242 analyzes the transform
result 234
for CNG (fax), ANS (modem), and 1800 Hz (STU-III) tones, as well as common
call
progress tones (ring hack, busy, andlor dial tone).
The presence of DTMF tones is reported to the CTD 200 and the V/VBD detector
218 via a DTMF notice 246. The presence of MF tones is reported to the CTD and
the
VNBD detector via an MF notice 248. The presence of general tones (GNG, ANS,
1800
Hz, ring back, busy, andlor dial tones) is reported to the CTD and the VNBD
detector via
a CNG notice 250, an A.NS notice 252, an 1800 Hz notice 254 andlor a call
progress
notice 255_ Additionally, the ANS notice 252 is sent to a timer 256. The timer
256 sends
a timeout notice 258 to the CTD 200 n millisxonds after receiving the ANS
notice 252,
where n is sufficient elapsed time for an 1800 Hz tone to be issued during
standard STU-
III modem negotiation.
_g_
CA 02308808 2000-OS-18
Attorney Docket No 25(47 119
The ~IIVBD detector 218 analyzes all inputs, to provide a voice detected
notice
260 or a VBD detected notice 262, (indicative of the presence of either voice
or voice
band data on the line), to the CTD 200.
The F.IUs 201 and 202 also send a copy of call event signaling 235 and 236 to
a
call state detector 237. The call state detector 237 reports "off hook" and
"on-hook"
events to the CTD 200 via a call state notice 244.
The CTD 200 analyzes all inputs to provide a content type discrimination
notice,
specifically either a content type "voice" notice 264, a content type "fax"
notice 266, a
content type "data" (modem) notice 268, or a content type "STU-III " notice
270
(indicating either STU-III voice, STU-III data, or STU-III unspecified).
The content type notice 264-270 is sent to a security processor 272 that is
pre-
programmed with the security policy to meet the user's security needs, which
may
include terminating the call. If the security policy dictates that the call
should be
terminated, the security processor 272 sends signals 274 and 276 to the LIUs
201 and
202, thereby terminating the call. Configurations of the line sensor 100 call
termination
circuitry varies depending upon the line medium (e.g., analog, T 1 and ISDl~,
and are
discussed below- with reference to Figs. S, 6A, 6B and 7.
Fig. 3 illustrates the process 300 whereby the V/VBD detector 218
discriminates
the content type of a call as either voice or VBD based on the plurality of
inputs showy in
Figs. 2A and 2B. It is understood that the line sensor 100 is operates in a
continuous
loop, continuously and simultaneously discriminating call content type on a
plurality of
telecommunication lines/channels.
The V~'VBD detector 218 continuously receives the CTR signal 212, takesp
samples of the data stream and creates a frame, as shown in step 302, where p
represents
any predetermined number of samples- The V~'VBD detector Z18 also receives
notice of
the presence of any DTMF, MF, CNG, A~VS, 1800 flz, andlor call progress tones
from
the DTMF tone detector 238, MF tone detector 240 and general tone detector
242, as
shown in step 30'l.
_ 10_
CA 02308808 2000-OS-18
Attorney Docket No. 25Cr47.119
Copies of each frame ofp samples are simultaneously statistically analyzed in
steps 306, 308 and 310. In step 306, an algorithm is processed on each frame
to
determine the number of zero crossings within the frame. Voice content
generally has
lower zero crossing counts than data content.
In step 308, an algorithm is processed on each frame to determine the Root
:?Vlean-
Square {the energy) of the frame. If the frame contains mostly silence, this
value is low,
but if it contains a loud noise the value is high. Voice content generally has
lower ener~r
than data content.
In step 310, an algorithm is processed on each frame to determine the center
frequency of all the frequencies contained in the frame. If the frame contains
higher
frequency components, the center frequency is higher. Voice content generally
has a
lower center frequency than data content.
The frames are grouped into a window containing q frames in step 312, where q
represents the number of frames totaling approximately one second in duration.
The
1 ~ statistical results of step 306, 308 and 310 are tabulated for each frame
and used in step
314 to determine the following eight indices associated with each window:
1. Number of frames with zero crossing counts above a threshold;
2. Variance of the zero crossing counts in total (qj frames in window;
3. Number of frames ~,~ith RMS energy above a threshold;
?fl 4. Variance of the RMS energy in total (q) frames in window;
5. Number of frames with RMS energy below the mean RMS Energy in a window;
6. Number of frames with center frequency below a threshold;
7. Variance of frame center frequency; and
8. Number of other tones detected.
~5 The indices for each window are processed by a classification algorithm in
step
316. Hard thresholds are used to analyze the indices and provide a call
content type
output of "voice", "VBD" ar "unknown" for each window.
-11-
CA 02308808 2000-OS-18
Attorney Docket No. 25647 119
The "per window" voice outputs from step 3 I 6 are tracked and counted. If r
consecutive windows indicate voice in step 318; where r represents any
predetermined
number of windows; the call content type is classified as voice, and a voice
detected
notice 260 is sent to the CTD 200 in step 320.
If the 'her window" output from step 316 is "VBD", it is also tracked and
counted. If s consecutive windows indicate VBD in step 324, the call content
type is
classified as VBD and a VBD detected notice 262 is sent to the CTS 200 in step
326.
If the "per window" output from step 316 is "unknown", the counters for both
the
voice and VBD used in step 318 and 324 are reset to zero in step 328. In each
scenario
resulting from the classification output of step 316, a process loop is
applied whereby the
next consecutive window of frames is processed and classified, and outputs are
provided
to the security processor 272 accordingly.
In an alternate embodiment, use of a neural network is contemplated to "learn"
content type patterns and thresholds for use in discriminating between voice
and VDB, as
well as discriminating between fax, data {modem), STU-III voice and STU-III
data. The
neural network builds a feature map during an initial learning period of the
patterns and
thresholds associated with the call content types found in day-to-day telecom
usage.
It is also contemplated that the neural network may be operated in an adaptive
fashion. If a call content type falls outside known patterns and thresholds, a
verification
of the call content type is provided by administrators and the neural network
updates the
feature map to add new patterns and thresholds as they emerge over time.
Fig. 4 is a state transition diagram illustrating the process 400 whereby the
CTD
200 further refines the discrimination of voice or VBD received from the V/VBD
detector
218, thereby determining if the VBD content type is fax, data (modem), STU-III
voice or
?S STU-III data, based on the plurality of inputs shown in Fig. 2B. It will
become evident
that the state of the CTD ?00 is fluid, transitioning from a start state 402
to a plurality of
other states as appropriate, in response to inputs derived from the call
passing through the
line sensor IUO. it is not shown nor stated below, but it is understood that
prior to
-12-
CA 02308808 2000-OS-18
Attorney Docket No. 25647 119
transitioning from the start state 402, a call state notice 244 reporting an
"off hook" event
is received by the CTD 200 from the call state detector 237.
Prior to call connection, the CTD 200 transitions to the start state 402_ If
the
voice detected notice 260 is received, the CTD transitions to a voice detected
state 404,
thereby providing the content type "voice" output 254. The CTD then
automatically
resets itself and transitions back to the start state 402 to detect any change
in the call
content type.
If the CTD 20(3 is in the start state 402 and receives either the CNG notice
250 or
the T-30 flags notice 224. The CTD transitions to a possible fax state 408. If
a second T-
30 hags notice 224 is received, the CTD transitions to a fax detected state
410, thereby
providing the content type "fax" output 256. When the call state notice 244
reporting an
"on-hook state" is received, the CTD returns to the start state 402.
However, if the CDT 200 is in the fax detected state 410 and the fax handset
is
used to place a voice call during the fax transmission, either the voice
detected notice
260, the DTMF notice 246, or the MF notice 248 is rxeived and the CTD
transitions to
the voice detected state 404, thereby providing the content type "voice"
output 264.
If the CTD 200 is in the start state 402 and receives a VBD detected notice
262,
the CTD transitions to a possible modem state 414. If a second VBD detected
notice 262
is received, the CTD transitions to a modem detected state 416, thereby
providing the
content type "data {modem)" output 258. If the call state notice 244 reporting
an "on-
hook state" is received, the CTD returns to the start state 402.
fVhen the CTD 200 is in either the possible modem state 414, the modem
detected
state 416, or the STL-III detected state 420, if either the CNG notice 250 or
the T-30
flags notice 224 is receiv ed, the CTD transitions to the possible fax state
408. As
previously discussed, if a second T-30 flags notice 224 is received, the CTD
transitions to
the fax detected state 410, thereby providing the content type "fax" output
266. if the call
state notice 244 reportins an "on-hook state" is received, the CTD returns to
the start state
402.
-13-
CA 02308808 2000-OS-18
Attorney Docket No. 25b47.119
If the CTD 200 is in the start state 402 and receives the ANS notice 252, the
CTD
transitions to a modem answer detected state 412. The C'TD then awaits
additional input
to discriminate between fax, data (modem) or STU-III content type. If a
timeout notice
258 is received prior to any other input such as the 1800 Hz notice 254, the
CTD
transitions to the possible modem state 414 and awaits further input. If the
1800 Hz
notice 254 is received, the CTD transitions to a possible STU-III state 418.
While in the possible STU-III state 418, the CTD awaits the collection and
validation of Bell 103 data by the STU-III validator 228. If the invalid STU-
III data
notice 230 is received, the CTD transitions to the possible modem state 414
and awaits
further input. If the valid STU-III data notice 232 is received, the CTD
transitions to a
STU-BI detected state 420, thereby providing the content type "STL1-III
voice", "STU-III
data" or "STU-III unspecified" output 270, as indicated in the valid STU-III
data notice
232. If the calf state notice 244 reporting an "on-hook state" is received,
the CTD returns
to the start state 402. However, if either the voice detected notice 260, the
DT"MF notice
246, or the IViF notice 248 is r~eived, the CTD transitions to the voice
detected state 404,
thereby providing the content type "voice" output Z64.
Additionally, although not shown, if the call ends or an "on hook" call state
notice
244 is sent from the call state detector 237 to the CTD 200, the state machine
to will
transition back to start. This can happen at any state, but for clarity is
shown only at
states 410, 4i 6 and 420.
Fig. 5 illustrates a schematic block diagram of a call termination circuitry
500 for
analog lines in the present invention. When the line sensor 100 is installed
in an analog
line, a tip conductor 502 is connected to a relay 504 and a ring conductor 506
is
connected to a relay 508. The relays are normally closed such that in case of
a power
failure or reset, the relays remain closed, thereby allowing calls to occur
without
interruption. if the security processor 272 determines a call is in violation
of the security
policy, it sends a signal 510 to the relays 506 and 508, thereby opening the
relays and
terminating the call. While not shown, it is understood that alternative
devices other than
- 14-
CA 02308808 2000-OS-18
Attorney Docket No. 25647.119
relays, including hut not limited to a transistor or switch, may be used to
break the
electrical connection and terminate the call.
In an alternate embodiment of the call termination circuitry for analog lines,
the
relays are normally open such that in case of a power failure or reset, the
relays remain
open, thereby interrupting all calls until transmissions is monitored by the
line sensor
100.
In another alternate embodiment of the call termination circuitry for analog
lines,
receiving and transmitting circuits are placed in-line with the telephone
line, allowing the
line sensor to manipulate the signal before re-transmitting it. This
configuration allows
i 0 "blanking" the call by transmitting silence or sending an audio message.
Fig. 6A illustrates a schematic block diagram of one embodiment of a call
termination circuitry 600 for Tl lines in the present invention. When the tine
sensor 100
is installed in a T1 line, signal receiving and transmitting circuitry is in-
line with the
existing T1 lint. In this configuration, the line sensor 100 electrically
receives and re
f ~ transmits the T1 signal traveling in both the transmit side 203 and the
receive side 204 of
the communication channel. The security processor 272 is capable of
manipulating the
T1 data that travels between the receiving and transmitting circuits. If the
call is allowed,
the security processor 272 does not abet the AB bits and the data is re-
transmitted the
same as it is received. If the security processor 272 determines a call is in
violation of the
20 security policy, the signals 274 and 276 are sent to the receiving and
transmitting circuits
and then transmitted, and contain altered AIB signaling bits plus voiceI~BD,
thereby
signaling the end of the tail to the central office 114 and the PBX 116.
Fig. 6B illustrates a schematic block diasram of an alternate embodiment of a
call
termination circuitry 6~0 for T1 lines in the present invention. Connections
and
25 configurations are similar to those described for Fig. 6A. The security
processor 272 is
capable of manipulating the TI data that travels between the receiving and
transmitting
circuits. If the security processor 272 detemlines a call is in violation of
the security
policy, the signals 274 and 276 are sent to the receiving and transmitting
circuits and then
-15-
CA 02308808 2000-OS-18
Attorney Docket No 25647 119
transmitted, and contain the AIB bits plus altered voieelVBD of digital
silence, an audio
message, or some other voice data sequence to convey termination to the call
parties. if
the call is allowed, the security processor 272 does not alter the data and it
is re-
transmitted the same as it is received.
Fig. 7 illustrates a schematic block diagram of a call termination circuitry
700 foe
ISDN lines in the present invention. Whea the line sensor 100 is installed in
an ISDN
line, signal receiving and transmitting circuitry is in-line with the existing
ISDN line. In
this configuration, the line sensor 100 electrically receives and re-transmits
the ISDN
signal traveling in bath the transmit side 203 arid the receive side 204 of
the
communication channel. The security processor 272 is capable of manipulating
the ISDN
data that travels between the receiving and transmitting circuits_ If the call
is allowed, the
security processor 272 does not alter the voiceIVBD nor the D channel
messages. If the
security processor 272 determines a call is in vialation of the security
policy, the signals
274 and 276 are sent to the receiving and transmitting circuits and then
transmitted, and
1 ~ include voicelV$D plus D channel messages altered to include an ISDN tear-
down
message, thereby signaling the end of the call to the central office 114 and
the PBX 116.
The line sensor 100 handles the response messages from the central office and
PBX in
order to prevent corruption of the link.
It is contemplated that the call drop circuitry described above with reference
to
Figs. 5, 6A, 6B, and 7 can be integrated into a large, integrated
communications device
such as a PBX or into another in-line device such as but not limited to a
surge suppressor,
repeater, CSLT (Channel Service Unit), or channel bank.
Alternatively, it is contemplated that the call drop circuitry described above
can
be controlled via wired or wireless connections.
2~ It is understood that several modifications, changes and substitutions are
intended
in the foregoing disclosure and in some instances some features of the
invention will be
employed without a corresponding use of other features. Accordingly, it is
appropriate
- Lb -
CA 02308808 2000-OS-18
Attorney Docket No. 25647.119
that the appended claims be construed broadly and in a manner consistent with
the scope
of the invention.
_17_