Note: Descriptions are shown in the official language in which they were submitted.
~.~ t ~ ~ ~ ~ C ~ 0 0 ~ : 6 0 F M ~ 02329311 2000-10-19
a
C3R 98 P 1550
Description
E1~atronic device arid method for the authentication of a user
of said dpviap
v~wY dlrr~~~C~~~ ~y~~d ~r elecl:rvnlc device LUi' wtiic;h d ur~~x~ hdd
to be authenticated before it is used are known. Important
examples are eomputerE in variouo configurations (deviaeE for
i nformat i r.~n ~aroc~aAAi.ng) and t.Rl.ecommt~nics.tion device9, such as
mobile phones ror example. some Bevices are generally
protected against unauthorized use, for example by a password:
in the case of other devices, only certain functions are
protected agc.inAt unauthorized accoas (for example by a eo-
called Personal Identification Numbor, DIN). This also
innlud~s the prot.-.p~!t:i pn o.f, aoreR~s tQ certain data or services,
even if they are not made available by the device buL by other
devices in a computer network or communications network.
No doubt the moat frequent typ~ of input o~ authentication
information today is input via a keyboard or koypad of the
device. After input, trie correctn~s~ of the information input,
and consequently the authorization of the user Carrying out
the input, is checked by a checking means iiz the device or lu
a computer networlc or communications network. In the ca:e of
mobile phones conforming to the GSM standard, this tak~e plane
by a r7a.ra-pr~r..pssi.ng means on the so-call~d SIM card of the
device checking whethez~ the YIN input matches the information
stored on the SIM card. =.C l,hls id the case, the SIM Card
enables the mobile phone for use. The security of the
tolaphone customer ie enhanced here by the feet that the GSM
standard dogs nor. allow the PIN to be stored in the devico but
only in encxypted form on the SrM card.
-1-
Received Oct-11-00 03:36pm From- To-Smart & BiQQar Paae 002
~Ct~ll. 2~~~ ~~60PM ~ 02329311 2000-10-19 ~~.0161 P.
For some time, technologies which allow other forms vL ur~er
authentication have been available. These technologies are
based on the detection of user-speeifi,c biomctric
charact,eristirs by special sensors. Sensox~a for fingerprint
detection are an important example of this. Ot.-.her biometric
characa~rl~l,lcs, such as the texture o~ the retina of the
human eye or the characteristics o.C a human voice for example.
are likewise already used in some devisee.
The Characteristics c7a1-c~Ct-ed by the sensors are usually
t;mn~ared in a data-processing means of the device o.r. hr a
communications nel.wvrk with the known characteristiCS of an
authorised usQr, and if they coincide sufficiently, access to
th~a desired service, the required data or the chosen device
function 1~ enabled.
Iil LiG~ltLl~ types of device, it appears to be aQvisable to combine
the two types of authemticBLio~x w~utivned with one ano>rher.
For example in the case of mobile phones, it is undoubtedly
desirable not only that they can be used by their owner by
means of a f. i nga~rprint, ~ensor, but also that other persons who
have been notified of the rllV or who would like to use thR
device wil,h ~tieir own SzM card are in a position to us~ it
within the limits o~ the authorisation to which they dre
entitled. Tn addition, the authentication by means of a
fingerpri.nfi ovuld occasionally tail or not be possible, for
example because the hands of r_hR agar are soiled or the user
is wearing gloves. For thepe or similar ~'easons, it is
desirable or necessary that one ox more assts r~L t~ device can
authenticate themselves on it by different mee~ns. Hiometric
authentication, ire to be possible in th~se cases along with
authentication by PIN input. In the case of mobile phones
confomm~.ng to the c~SM r~t;a,ndard, it is additionally the case
Received Oct-11-00 03:36pm From- To-Smart & BIQQar Page 003
.. _._ ._,....a,.,d.. ~.._.. .. ..._..~_M~..,~....~,
".__~.,..~,.~,"."~.~y.."",~~..
~;50FM ~ 02329311 2000-10-19
that the standard prescribes the possibil~.ty of authentication
by p=N input ae mandatoz-y.
Tt follows from th~ situativrz described that use of
conventional biometric authentication mothods is not possible
in the case of mobile phones conforming to the GeM standard,
because P=N a~u~h~m~lc:a~ivrx with the S=M card is a mandatory
requirement for them for reasons of compatibility with the GSM
standard alone. The at firot ~seemix~gly obviouo poAaibility of
storing the DIN in the devise and transferr~.ng this stored PIN
to the SIM card for checking purposw~ if thprR ig a.r~ucce99fiu1
outcome of t~.e check Lo ascertain whether the detected
fiizgerpriut coinr:ldeb with t,xaa sl.vrec'i riugex~print of arz
authorized uecr is discounted because storage of the p=N ~,n
the mobile phon~ anywhere else than within the 8IM card is
prohibited by t-.hR GSM stand.axd for Security reasons. Hiometrie
auLhenzicazion would consequently only come into consideration
iiz these ca~s~s ae ate ac3,c~iCivual ~afeguard~. Such an additional
safeguard is not required, however, in view of the high
security of th~ authen.tieativn of the PTN input,and would
probably also not ba a.r_r_Rpt~~3 by ma.z~y u~aer9.
Thn invention is therefore based on the object of sQecirying a
technical teaching which allows the tpy1b111b11.lUIl Vf a biometric
user authentication with an authentication by PTN input even
in the case of mobil~ phones conforming to the GSM standard or
in similar circumstances, it being int-.endpd for one form of
authentication to be sufficient in each caste. l~he user is
consequently l:o txdve t;he choice of which type of
authentication he wishes to use, zt is coaceiva~ble, however,
that a specially distinguished user (for example the owner of
the device) is given the pc~araihil.d.t.y of sgttine~ the loc,~ic ~1ND
operation of the two types or authent1C3L7.On on trie CIeViCe.
-3-
Roceived Oct-11-00 03:36pm From- To-Smart ~ Biaaar Paao 004
Oct~11~ 2~~~ ~:61PM ~ 02329311 2000-10-19
This object ig achieved by a clevi.c:p or a method according to
one of the patent Claims.
The invetztion provides that biometric characteristics of the
user are detected by a sensor means and information acrving
for authentication is det~rmin~d with the aid of mathematical
mpthnc3~ f.rnm the detected biometriC Characteristics. Ae a
result, authezl>ricaczon information which can be checked by the
tjcllllC C:~I~C:kllli.~ means as authentication information input by the
user via an information itxput device (for ~xamplc ,~ keyboard
or keypad) is obtained at the ~nd of the evaluation of the
biometric characteristic: _ In the r~imp.L~!st rasa, r_he result of
the evaluation of the fingerprint is the same PIN which users
could also have input via ttie kCyJ;7oard or keypad. Thi~ FIN is
not stored in the device, however, but is calculated from
biomctric characteriaticc of a user detected by a sensor
means.
This type of evaluation of Lhe biomet:ric characteristics
detected by d seusv,~~ means makes this type of authentication
equivalezxt in outcome to the authcatication by meanp of
keyboard or keypad input, and,the customary interface for
checking the validity of the authentication .1_t,.f.ormsti nn aan
rRm~ri.n unr_hanged. In particular, it ie not necessary for any
requirements prescribed by ecandardi~ co be changed. The twv
methods of authentication can be used alongside one another
without a.ny diffiault:iec; the user has at any time dad is
every situation th~ free choice betwo~n the two methods. It is
of course also pn~~i b1 R t~n usc~ both in an AND combination, in
which only the user who successfully nego>riatea >rhe twv
authentication paths is given aecer~r~.
Received Oct-11-00 03:36am From- To-5mart ~ 6iaaar Page 005
~Ct~11~ 2~~~ ~:61PM ~ 02329311 2000-10-19 NO~~~5~ F~ 6
~t~he invention is described in more detail below on >rhe basis
o~ preferred exemplary ev~vdimCmt,r~ arid wi~ti Ltie e,id vL
figures .
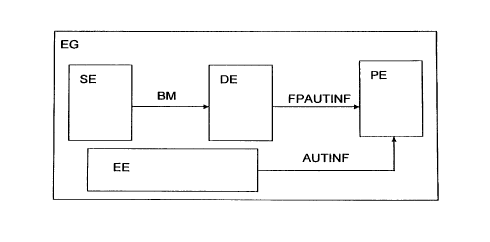
Figure 1 shows an exemplary embodiment of the invention in ,
which all the methods and means are integrated in one device.
Figure 2 shows an exemplary embodiment of the invr~al:ion iii
Which the checking moans is not located within the device.
Figure.3 shows an exemplary embodiment of the invention in
whi.r_h a display device for the display of authentication
information is integrated in the device.
A gaits specific but important embodimcrit of the invention io
a mobile phone conforming to the GSM standard, which hara a
fingerprint sensor for user authentication. This fingerprint
sensor is a special case of the sensor means (g~) repre~ented
in Figure 1. It a user of the device (ECM) places a finger on
this fingerprint sensor ar~.d the device is awaiting an
authentication, ouch ac the input of a PZN or super PIN or
DIN2 (partly manufacturer.-dependent) ~or example, the
f 1 ngprpri nt ~Pn~nr c7at~r..t >~ t-.he r..~rr~sp~nc31 ng bi om~.tri r..
characteristics (HM) of the user concerned and passes triem to
a data processing means (DE).
Try the car~~ of the GSM mobile phoa~, this data processing
means is the processor already present in any case in the
mobile phone in conjunction with software running on it. On
tha other hand, however, the fingerprint sent~or (or more
generally: the sensor means) could aleso l:zave iLs vwrx prwc;eer~or
unit, on which a Qpccial software performing the fingerprint
detection runs, so that, in the sense of this invention, the
data processing means is fully or partly integrates into the
-5-
Racoivod Oct-11-DD D3:36pm Fram- To-Smart Z BiQQar Page OD6
~ C t ~ ~ ~ ~ L ~ ~ ~ ~ : 51 P M ~ 02329311 2000-10-19
sensor means . Since the f ingerpri.z~t deter._t i on i t ac~1 f , a s wc~11.
ae other meLhoda of detecting biometric charact~ristics and
their z~eali,zation on data processing means of different
configurations (and partitioning into aubayatemm or a~amcmbly
from known. hardware module) , are sufficiently ltnown to a
pereorl skilled in the art, this part of r~alizing tho
invention no doubt does not present any particular problems.
Accox~diry Lv Ltie preseiiL imveiiLl~u, 1.111s data processing
device then deteL-mines information suitable for the
authentication o~ the user ~rom the detected biometric
charactmristics. In th~ simplest case, thin ire the PIN (or
PIN2 or the like) of the user - accepted ae entitled - stored
in an encrypted form on the SIM card. This PIN is then
transferred to the SIM card for checking in the same way ae if
it had been input by the uper via the numeric keypad ,
(information input device) of the mobile phone. Th~ checking
process known to every person skilled in the art and provided
in the GSM standard than proceeds in zhe checking means of the
mobile phone (SIM card, if appropriate in conjunction with thG
data processing means of the dcvicc). If the authentication
information FPAU'fINF) ire oorr~ot, i.e. coincides with the PIN
storRd on i-.he STM card, t:he device function protected by the
authentication ( for example network acre~s, etc . ) is ~enabl ~ec3 _
A decisive advantage of the solution according to Llae
invention described ie that the fingErprint detection in the
case of the authorized user loads to transfer of the uaer~e
~'IN to the SIM Card, since this allows the a~ear_t~.ri i-.y
r~qul.~~emaixtd prescribed by the C~SM standard to remain
completely unchanged. Other, at first perYiapr~ e~eemingly
obvious solutionB do not have thin attributo. In any event,
any other an7.ut:i nn would rec,~.tire either ~n additional input of
the P2N via the keypad or a way of avoiding or changing the
6
Received Oct-11-00 03:36pm From- To-Smart & BIQaar Pale 00T
~Ct~ll. 2~~~ ~:52PM ~ 02329311 2000-10-19 ~~.0151 F.
GSM standard. As1 daditional input of the 8IN via the keypad
would only be moaning~ul i~ the fingerprint dete~ti~ix wGwC
conceived as an additiozsal security measure in addition to the
PIN i nput. .
such an additional authentication is of course also possii'lp
with the present invention. Isz Lhic~ case, it would be
nocesaary ~or the e~uthentication information determined from
the senoor data not to be transferred to the BIM card. Instead
of th.i~, a false PIN could, for exampl~, be deliberately Eent
Lo the sIM card or an input error or abnormal t:prmination of
the input or the like c;vuld be simulated. The eIM card would
then aga~.n regucat PIN znput. If the PIN input coincides or is
compatible with the one determined, the data processing means
(DE) could trana~er this PIN to the SIM card, whereupon the
latter would provide the enabling function.
o~ course, the PIN dot:G~w~irsed from the sensor data does not
have to be identical with the SIM card PxN. If the etarldard or
- in the case o~ other deviceE - the rcapoctively relevant
security protocols allow, f.he checking means could also cheek
two different items of authentication i.nfnrmat.ion to ascertain
whether they match one ailvl;>aer.
In the case of other devices, wh~.ch are riot subject to tile GSM
starsc3arcl, the authentication information F1'AUTTNP' calculated
fz~om the sensor data could, even it the case of authentication
by sensor data alone tthat is to say independpnt.-..ly of and
along with PTN input), be diff~iwrst from the authentication
information A'UTINF input vi,~ a lceypad, as long as the chec:kirsg
means detects that the two match in the sense that they both
refer to the authorized user.
Recoivad Oct-11-00 08:86pm From- Tc-Smart 8. Bimmar Page OOA
~Ct~~~~ L~~~ ~;52FM ~ 02329311 2000-10-19
In principle, all mathematical representations (LuriCtioris)
which assign tc~ a fingerprint or other HM a PIN vi~ b~tne oLrmr
form of (generally alphanumerically encoded) authentication
information AUTINF arid satisfy the following conditions come
into consideration ae methods of calculation for
a.uth~rt-.1 rata nn i nforma.t.i..on FPAT1TTNF from a HM:
a) su=ficiently similar HMS lead to the same authentication
111LUt'~tle~l:iUn FPAUTINF;
b) suffxczently different DMa lead to different authentication
information FPAUTINF.
r_.) it. ire virtually impossible for an unauthorized user to
determine (for example guess) zhe authentication informar_inn
FPAUTTNF from the HM or without knowledge of the 8M.
The condition a) io intcndcd to ensure that the fingerprint
detection is sufficiently robust with rospect to minor
di:turhanr_efi_ nt:hprwi.ae, t:. he rejection rate of authorized
users would be too high. C:onditivn b) ensures that
fingerpxwinl.r~ vL different users lead to dlllerent
authentication iza,formation FPAUTINF with an adequately high
degree of probability. The significance of condition c) is
obViou9.
A person skilled in the art is familiar with various
mathematical xepreaentation6 whic;x~r~dtisfy these requirements
(poeEibly to a grcatQr or lesser e:ctent). A representation
with these attributeA is provid~d by sv-called vector
quantizaLion. This m~thr~d, which is actually known to a person
skilled in the art, is to be explained here only to the extant
which appoara to be reguired for an uuc~er~atanding of zhe
invention.
It this method is applied for the purposes of th~ prasprit
i~uv~rttivn, it ie firstly presupposed that the biometric
_g_
Roaoivod Oct-ii-00 08c86pm From- To-Smart S BIQQaf PaQO OOA
~Ct~~~~ ~~~~ ~:62PM ~ 02329311 2000-10-19
characteristics detected by the sensor means can be brought
into the form of a ao-called charav::l:Gi~ist,ie vector. Thip
assumption ig not a restriction in pz:actice, since the be,cxbow
data can always be represented as an ordered n tuple of n
measurement data (characteristic vectors). The characteriotic
vectors form an n-dimen~ional spar_P . Tn f~hi.s Space, a set of
charac~t;crisl.ic vectors (codebvok vectors) would exigt and a
degree of disparity (degree or similarity for biomeLric
characteripties) would be defined. For each sample vector
there is in this apace a sell, which io defined by the rule
that, for ~aeh r_harsrt.~ristic vector in a cell, the sample
vector of Lh~,p cell is trie nearest ~ample ver_t-.nr. i n t: he genes
of this degree oL aispdrity.
each sample vector ie assumed to be assigned an item of
information ~mixal~le in principle far authentication. A sample
vector is a~signed the correct authant:idation information (fcr
example the ar:~udl PIN). It is obvious from these explanations
that the dete~-rnination of the xiaa.zwr~t sample vector to a
ss.mple vector which eorrcsponda to the detected sensor data
leads to the correct information (actual PIN) in the cast of
the authorized user and otherwise supplieo false
authentication information. ~t~he error rates of t:hi ~ method can
be optimized :lr i~ is ensured Chat the characteris>rie vector
asoaCiatcd with the biomctric characteristi~:s yr the
authorized user is one of the sample vectoro. This can be
achieved by t'he gygtem adapting itself to the biometriG
characterieLics Ot the authori~pd user (codebook adaptatioxx)
in an initiaLi~at;ion phase.
Th~ v~etor quantization io not the only method which can be
used in conjunrti,on with the invention. A person altillcd in
the art ip familiar w~.Lh otrier methods, w>1i c>a, t.herefore do not
have to be exp7.ained here.
_g..
Received Oct-11-00 03:36pm From- To-Smart 8 Biaaar Paae 010
0 C t . » . ~ ~ ~ 0 ~ : 5 2 P M ~ 02329311 2000-10-19 ~ O , p ~ 5 ~ F ,
If the literal ~enao is taken as a basis - the oa.lculation of
the authentication inform0.tion FBAUTINF from the biomei.ric;
characteristics of a user by vector quantiaation actually also
involves a "storage of the pIN" in th~ device, since each
~9ample veCtOr Of Lhe codebook is indeed assigned an item of
authentication informal.i,vu (FPAUT=NF) that its possible in
prinCxple. I~3owe~rer, in virtually all cases (apart from one,
namely that of the sample vector of the authorised uaei) this
is not really suitable ~or auth~ntication. For example, in the
case of a five-place alpha.m~mari.c PIN, in the ideal cave all
c:o~ic;eivable PZNs, and for each one a sample veor_or, ar_e
therefore stored in su~:h a~ wr~,y that only if there is
sufficiently aacuratc detection of the mample vector in tlm
tensor can the valid PIN be addreoaed. Although the correct
FIN is Cherefore arr_nrdi.ngly "stored in the device ~~ , it ie
lost among the great number of conceivshle 1?INs, and can only
be found for LhG person with the correC>r biometric
chaxacteristica. Thi~ ~tate of ~,LLdirs is not inCended when
the standard pxohibite the storage of the PIN in the device.
In the Case Of Lhe C3SM ~tandarc3, t:he storiz~ of the pIN in the
device is iivl. allowed. Often, however, a change of the DTN i.s
neceAaary, for example beoa~use it has become known to a LhirCi
party. If, however, the PIN is determined from thG fingerprint
(i.e, calculated), this initially appears to be impossible,
since iC is not possible tn change a fingerprint or other
biom~t,wlc; characters~ties. 1n order nRVertheless to givQ the
user the possibilitr~y yr changing his PIN, Lhe invention
provides in a preferred embodiment that, inst~a~i of only one
method of calculation, a whole oct of such methods are
available in the dsvirp_ Each individual method of calculation
ovuld be assigned a Consecutive slumber, so that. a user
authorized to do so could at any time change the method uBed.
Received act-11-00 03:36pm Prom- To-Smart & Riaaar Paae 011
2~~0 ~:6~PM ~ 02329311 2000-10-19 ~0~0151 P~ 12
S1 nr.R pac!h method (Ml, . . . , Mn) CalCUlates a different 1~11V
(FBAUTINFl, . . . , FPAUTrNFn) fvr ona and the r~attte fing~tyj~iuL
(HM) , the user can select rxwn ds ma>;1y PINS as there are
differerxt methods ~or their calculation.
Thic embodiment o~ the invention can likewise b~ realized with
vector quantization, although indeed not jus>r one Codebook but
a number of codebooks or sample vectors are to be provided.
Each codebook has a number and can be selected via this
number. Other methods peaeibly depend on a parameter. If thiE
parameter is changed, a dif~orent mathematical representation
is obtained. If the depenrience nn irhi~ para.mRtc?r is
sufficiently complex. it becomes virtually impossible to guess
how the dut,heiil,ir;aLion information changes when the parameter
changes.
Certain typos of neural networko (for example ao-Called multi-
layer perceptrone) are ssuitable for realizing representations
this type. zn the case of solutions based on such neural
networks, the PIN is actually not stored anywharo as a
sequence o~ characters but merely (implicitly encrypted) in
the network axohit~ctur~ and in th~ weight coefficients.
Th~,s implementational variant of the present invention appears
tv ba of interest in particular with regard to the fact that
many people require a aeries o~ di~~erent passwords for quite
different purposes ox devices. It ie becoming incr~asingly
more difficult to remember thepe many passwords. Z~ a numbor
of methods (Ml,...Mri) (mathematical representation~) are used
for calculating a number of items of authentication
informata.vn (FPAUTINF1,...,FPAVTINFn) from a single
eharacterictic vector (or sEt of ocnaor data), this problem is
reduced to th~ detection of user-specific inalienable
biometric charac>rerisLics by suitable sensors.
Zs
R~c~ived Cict-11-00 03:36~m From- To-Smart a BiQaar Paae 012
~Ct.l~, L~~~ ~:6~FM ~ 02329311 2000-10-19 0.0151 F,
For the selection of a certain method, all that is necessary
is to input an identification number of such a method in a
context vL the u~ier ii'>,terface to be provided for thin purpose.
As a result, the data processing means can be correspondingly
set up by software.
of r_our~sa~, the biometric characteristiCS of a number of people
Could also be linked with the correct 8IN yr with a slumber of
correct; PINd~. IL, as an exception, the device is to be unable
oz~ly far one person, i . c . with on~.y j not one sIM card, the
enabling function may be additionally linked with further
safety mechani.gms ~t~rh as dwvir_A codes, etc. The inVentiOn
allows any kind of flexibility here, tvgethez~ with the highest
securil,y dud c:onyr~(;lLility with the standard.
6pecifiCally if a PIN is changed, a further useful embodiment
of the invention, in which a digpla.y i s proof ~Ipc3 .fnr
displaying an item of authentication information, may be
helpful. A display of this type is already present in any case
on mazxy devices of this type ai,nd can therefore also be used
for these purposes. If a uacr wiahco to change hiA
authentication information (AUTIN&'), for example the PIN, to
be input via the keypad and matching the ,SIM card or gt.ored. oxa
it, it is possible in the case of some methods of CalCUlation
that not all the conceivable character-digit cvmbinativna are
available to him as PINS, for example becauAe the codebook is
smaller than the number of all conceivable PINa. In this sass,
changing the parameter of the method of Galctllation used (for
example changing the codebook number, or changing a parameter
of a neural network) is sufficient to change the assignment of
the PINS to ~thc sample vectors and conaeguently the PIN
acaigned to itg individual sample vector. After that, he could
not change the PIN on the SIM card (or more gsanearally: th~a PTN
-12-
Received Oct-11-00 03:36pm From- To-Smart ~ Bia~ar Paae 013
~Ct. » . 2~~~ ~:S~PM ~ 02329311 2000-10-19
to be input) in the same sense without knowing i.t . Tri.s ins
ne~re~ssary, however, for further use in >rhe sense of our
object. ~hhe changed PIN is th~retore preferably divulged w
the autlmt~i~cci user by a come~ponding, poar~ibly one-off,
brief display of this PzN aftor the chs~nge on a display of the
device. Othcr oolutionc (for example mailing th~ new DIN) are
conceivable.
The invention its of Course not restricted Lo ~ttc~bil~ phones, in
particular ilol, t;o mobile phones conforming to the a9M
standard. It ie quite cvidcnt to a. person Skilled in the art
from the present description how the invention is to be
realized in th~ case of ot.laP.r davi r.RS or systems.
zn particular, the inventivr~ i~ mL restricted to the case in
which the checking unit (PE) is integrated into the device.
Figures 2 shows the important case of a devia~ which is
connected, for example via a communicat.iong nRtwnrk, tn at
least one other device, in which the Checking meari8 1s
located. However, even the data prvces~sing unit vx~ l;ha.l. p~xt~l.
of the data, processing unit (DE) which is reaponoible for the
calculation of the authentication information FPR~TTINF from
the biometric Characteristics HM of the user does not
ner..esg8.r, i 1y have tn 'hp 1 prat=r~ci in then device. Of course, the
device does riot have co have ari integrated sensor means (sE)
UW all 1I1LC4'~Z'iiLL°'d ~iCY);7C7~L'd or keypad (EE) . These moans
could of
course also be connected to the device in the form of cxtcrnal
modules. Theee embodiments of the invention are intend~d to be
prot:.ect.-.ed by t:he met.-.rod r..'1.a i mA .
-13-
R~coived tlct-11-00 03:36~m From- To-Smart & BiQQar Page 01d