Note: Descriptions are shown in the official language in which they were submitted.
CA 02338890 2001-O1-29
WO 00107347 PCT/GE3991OZ243
1
A TELEPHONE
The present invention relates to a telephone and a
related method of using a telephone. Primarily, but not
exclusively, the present invention is concerned with
telephones which are connected via signal lines to a
Public Switched Telephone Network.
In recent years many countries have liberalised their
telecommunication systems. As a result, when a user
operates a telephone, the user increasingly has a choice
as to the telecommunication service provider who will
connect the user to the desired call destination.
The main service provided by the service providers is
routing calls from the originating telephone to the
destination telephone. In addition, however, other
auxiliary services may be provided such as, in the case
where the user at the destination telephone is not there
to answer the call, storing a message from the user of
the originating telephone which may subsequently be
accessed by the user at the destination telephone. _
A system is known in which a user, when desiring to make
a call, can first telephone a service provider by
manually inputting the call number of that service
provider. Alternative systems require the user to simply
press an access selection function button of the
telephone, in response to which the telephone
automatically generates the call number of the service
provider, and the user is then able to subsequently dial
the destination number required so that the service
provider determines onward routing of the telephone call.
The service provider utilises a call line identifier
signal generated by the local exchange through which the
CA 02338890 2001-O1-29
WO 00/07347 PCT/GB99/02243
2
user' s telephone call is directed to the service provider ,
in order to automatically generate billing information.
It is also known to provide routing modules connected in
line with a telephone so that the output line from the
telephone is input to the routing module, the output of
the routing module then being connected to the public
service telephone network. Such routing modules
intercept dialled numbers for outgoing calls from the
telephone and, depending upon the initial digits detected
in the outgoing call, determine whether the call is a
long distance call which could be more economically
routed via a service provider. The routing module then
automatically inserts an access code before transmitting
the user dialled call number. Such routing modules are
essentially transparent to the user who will have no
control over the routing decision taken by the module.
There therefore exists a need for providing an improved
telephone which is simple to use but which retains
flexibility and user control over the routing of
telephone calls.
A further aspect of the invention relates to
authentication of the origin of a user request for
services from a service provider. When the user is
connected to the service provider, the service provider
may in some instances prompt the user to send a personal
identification number ( PIN ) which identifies the user to
the service provider for the purpose of charging for
services provided. Once the service provider has
identified the user, a dial tone is presented to the user
prompting the user to enter the call number of the
desired destination.
CA 02338890 2001-O1-29
WO 00/07347 PCT/GB99/02243
3
Such reliance upon PIN is convenient for users who wish
to make calls from many different locations. A problem
exists however where a user makes frequent calls from a
single terminal in that the repeated use of PIN becomes
tiresome. A PIN may also be forgotten by a user. A PIN
may also become known to a third party who may make
fraudulent use of the PIN, the PIN system of
authentication thereby providing only a limited level of
security.
A further problem experienced by service providers is
that, where billing information is derived from a Call
Line Identifier (CLI) signal generated by a local
exchange to identify the location from which a call
originates, fraudulent use is possible by forging the CLI
signal.
The present invention seeks is to provide an improved
telephone and method of making calls via a node
associated with a service provider.
According to the present invention there is disclosed a
telephone compra.sing;
dialling means operable to output a dialled number
in the form of a signal representative of a destination
of a telephone call;
control means operable to control operation of the
dialling means;
a keypad responsive to user actuation to input a
user generated call number to the control means;
route determining means selectively operable to
determine an access code for routing the telephone call
via a preferred route;
CA 02338890 2001-O1-29
WO 00/07347 PCT/GB99/02243
4
the keypad comprising a user intervention means
responsive to user actuation to signal to the control
means a user intervention condition;
wherein the control means is operable in the absence
of said user intervention condition being signalled to
control the dialling means to output a dialled number
including the access code determined by said route
determining means followed by the user generated call
number; and
wherein the control means is operable in response
to said user intervention condition being signalled to
control the dialling means to output a dialled number
comprising only the user generated call number.
The telephone of a preferred embodiment has the advantage
that it is no longer necessary for a user to remember
every time a call is made to first dial the access number
of the service provider to press an access selection key.
The telephone of the present invention is suitable for
both home and work environments.
In the preferred embodiment, the preferred route
corresponding to the access code results in the telephone
call being directed to a predetermined node of a
telephone network, the telephone further comprises
authenticating means operable to receive an
authentication data signal from the predetermined node
and to automatically generate and transmit an
authentication response signal to the predetermined node
to confirm the identity of the communication terminal to
the predetermined node. The preferred embodiment has the
advantage that a user is not required to memorize a
personal identification number.
CA 02338890 2001-O1-29
WO 00/07347 PCT/G1399/02243
In the preferred embodiment, the telephone may further
comprise means for encrypting the received authentication
data signal using a predetermined encryption procedure
and an encryption key identifying the telephone in order
5 to form the authentication response signal.
The use of encryption thereby improves security by
providing an encrypted "handshake" procedure between the
callers telephone and the predetermined node, allowing
validation of the callers identity and ensuring correct
billing.
Embodiments of the invention will now be described by way
of example only and with reference to the accompanying
drawings of which:
Figure 1 is a schematic diagram of a communication system
according to a f first embodiment of the present invention;
Figure 2 is a block diagram showing the internal
structure of a communication terminal according to the
first embodiment of the present invention;
Figure 3 is a block diagram of the contents of the ROM
of the communication terminal illustrated in Figure 2;
Figure 4 is a block diagram showing the internal
structure of a routing device according to the first
embodiment of the present invention;
Figure 5 is a block diagram of the contents of the ROM
of the routing device illustrated in Figure 4;
Figure 6 is a block diagram of the contents of the RAM
of the routing device illustrated in Figure 4;
CA 02338890 2001-O1-29
WO 00/07347 PCT/GB99/02243
6
Figure 7 is a flow chart indicating the sequence of
events when a user operates a communication terminal as
illustrated in Figure 2;
Figure 8 is a flow chart indicating the sequence of
events when a routing device as illustrated in Figure 4
is contacted by an originating terminal;
Figure 9 is a flow chart indicating the sequence of
events when the communication terminal as illustrated in
Figure 2 carries out an authentication procedure;
Figure 10 is a flow chart indicating the sequence of
events when a routing device as illustrated in Figure 4
carries out an authentication procedure;
Figure 11 is a schematic f lowchart illustrating operation
of a further embodiment of a telephone in accordance with
the present invention in which no authentication
procedure is carried out;
Figure 12 is a schematic circuit diagram of a telephone;
Figure 13 is a schematic external view of the telephone
of Figure 12;
Figure 14 is a schematic flowchart illustrating operation
of a telephone as disclosed in Figures 12 and 13;
Figure 15 is a schematic representation of a further
embodiment comprising a mobile telephone; and
Figure 16 is schematic flowchart illustrating operation
of a mobile telephone as disclosed in Figure 15.
CA 02338890 2001-O1-29
WO 00/07347 PCT/GB99/02243
7
A first embodiment will now be described with reference
to Figure 1.
The communication system shown in Figure 1 comprises a
number of communication networks 5a, 5b, 5c, each of
which is connected to a number of local exchanges 3.
Figure 1 is schematic and is not intended to indicate
that the local exchanges 3 are distinct from networks,
since the local exchanges 3 themselves form part of one
or more of the networks 5a-5c. A number of telephones
1 are connected via respective signal lines 101 to each
of the local exchanges 3. An intelligent node 7 is
connected to the networks 5a, 5b, 5c.
Located at the intelligent node 7 is a routing device 70
which is operated by a service provider. When a
telephone la of a subscriber to the service provider is
connected to the intelligent node 7, the routing device
70 is able to route a call from the subscriber to any
other desired telephone lb-lg via one or more particular
networks 5a-5c to which the service provider has access .
In this embodiment, the service provider requires a
subscriber to maintain an account in credit, and
throughout a telephone call debits the cost of the call
from the subscriber's account. If, during a call, the
credit level of the subscriber approaches a minimum
credit level a warning signal is sent to the subscriber
from the intelligent node 7. If the credit limit is
reached the call is cut off.
When a subscriber at a telephone la wishes to call a
telephone le, the telephone la, in the absence of user
intervention, responds to the user lifting the handset
of the telephone la and a subsequent dial-tone issued by
CA 02338890 2001-O1-29
WO 00/0734? PCT/GB99/02243
B
the local exchange 3 by automatically sending a first
dialling signal, corresponding to the telephone number
of the intelligent node 7, to the local exchange 3 to
which the telephone la is connected via the signal line
101 thereby connecting the telephone la to the
intelligent node 7. An authentication procedure,
described in greater detail below is then automatically
effected by an exchange of encrypted signals between the
routing device 70 and the telephone la. The user then
manually dials a destination call number identifying the
telephone le resulting in a second dialling signal
corresponding to the destination call number being
subsequently sent from the telephone la to the
intelligent node 7. The intelligent node 7 then connects
the telephone la to the telephone le, the route of the
call between telephone la and telephone le being
illustrated by arrows 100 in Figure 1.
The networks 5a, 5b, 5c may incorporate any means for
transmitting information, for example wires, optical
fibres and satellite links. Examples of suitable
networks are those provided by telecommunications
companies such as British Telecom (Trade Mark) and AT&T
(Trade Mark). The Internet is another example of a
suitable network.
Figure 2 illustrates schematically the components of the
telephone la which is shown connected to the signal line
101 by means of a plug 13. The plug 13 fits within a
telephone socket and constitutes a connector providing
a direct connection to the local exchange 3 via the
signal line 101. Two wires for carrying two way signals
via the plug 13 are connected to a two to four wire
converter 11 via an off-hook switch 15, the two to four
wire converter separating in-going and out-going signals
CA 02338890 2001-O1-29
WO 00/07347 PCT/GB99/02243
9
on to a pair of output wires 18 and a pair of input wires
20 respectively.
The pair of wires from the plug 13 is also connected to
a ringer 17 to provide audible indication of incoming
calls. The off-hook switch 15 has contacts which are
closed when the telephone is actuated, typically by the
user lifting a handset prior to dialling, and the
contacts being open when the telephone is not in use,
i.e. when the handset is replaced.
The telephone is provided with a microphone 19 and a
speaker 21 which are typically mounted in the handset,
the microphone 19 being connected to the output wires 18
and the speaker 21 connected to the input wires 20 so
that during a telephone call, outgoing signals can be
generated by the microphone 19 and incoming signals can
be heard by means of the speaker 21. A tone generator
23 is also connected in series with the speaker 21 to the
input wires 20 to enable internally generated tones to
be delivered to the speaker 21, as described below.
A processor 27 controls operation of the telephone and
is connected to both the input wires 20 and output wires
18 for the purpose of receiving signals from and
outputting signals to the intelligent node ?. Incoming
audio signals from the intelligent node 7 are input to
the processor 27 by means of a zero-crossing detector 29
connected to the input wires 20, the detector 29 having
an output connected to a counter 31 whose output is
connected to the processor 27.
The zero-crossing detector 29 and counter 31 allow
detection of the presence of audio tones received at the
CA 02338890 2001-O1-29
WO 00/07347 PCT/GB99/02243
1. 0
input wires 20 and allow the frequency of the audio tones
to be detected and then interpreted by the processor 27.
The output of the zero-crossing detector 29 alternates
between two states each time the voltage at the input to
the zero-crossing detector passes from one side of a
hysteresis band located around ground to the other. The
counter 31 is an edge counter which is connected to
receive the output of the zero-crossing detector 29 and
which counts the number of times in a predetermined
period that an edge occurs in the output signal, the edge
being formed when the output signal of the zero-crossing
detector alternates between the two levels.
The output of the counter 31 is read at 4 ms periods by
the processor 27 and the counter 31 is then reset, the
processor 27 interpreting the output of the counter 31
to detect the audio frequency of signals present on the
signal line. The 2 to 4 wire converter 11 includes a
summing amplifier to isolate the signal being transmitted
by the PSTN and includes a two pole low pass filter to
remove high frequency (above 100 kHz) noise and
interference. The zero crossing detector 29 comprises
a comparator with a small amount of hysteresis whereby
the comparator trip threshold is increased by a small
amount after each positive output transition and
decreased after each negative transition. This
arrangement prevents signal noise from causing
oscillation as the input signal crosses the threshold
region.
The processor 27 is able to generate outgoing audio tones
for sending information to the intelligent node 7 by
means of a Dual-Tone Multi-Frequency (DTMF) generator 25
whose output is connected to the output wires 18.
CA 02338890 2001-O1-29
WO 00/07347 PCT/GB99102243
11
The processor 27 is connected to a keypad 33, a ROM 35,
a RAM 37, a clock 39, an ID chip 41 and the tone
generator 23. In this embodiment, the components within
the dashed square in Figure 2 are incorporated a single
unit, namely a PCD33xx family member core device. The
ID chip is a Dallas DS2401 which contains a unique 48
bit ID.
Figure 3 is a schematic diagram of the contents of the
ROM 35. The system manager 5I controls the operation of
the telephone 1. The authentication sub-routine 53 is
used to verify the identification of the telephone 1 to
the intelligent node 7. The encryption table 55 contains
an array of 256 memory locations, each memory location
storing a random 8-bit binary number. Identical
encryption tables are stored in each one of the
telephones 1 having a corresponding account with the
service provider and in the routing device at the
intelligent node 7.
The RAM 37 includes working space for the running of the
system manager 51.
As shown in Figure 4, a routing device 70 at the
intelligent node 7 comprises an input port 61 and an
output port 63 which are connected via a switching unit
65. The routing device is connected to the networks 5
including local exchanges 3 via both the input port 61
and the output port 63.
On each of the input port side and the output port side
of the switching unit 65 respective two wire to four wire
converters 67, 69 are connected in parallel with the
switching unit 65. The two to four wire converters 67,
69 are connected to a routing device processor 71 via
CA 02338890 2001-O1-29
WO 00/07347 PCT/GB99/02243
12
respective transmission systems 73, 75 and via respective
reception systems 77,-79. The routing device processor
71 is also connected to a ROM 81, a RAM 83 and a clock
85.
Included in the input transmission system 73 is a system
for transmitting signals to the telephones 1 which will
now be described with reference to telephone la in figure
2 when connected to the intelligent node 7. Frequency
shift key encoded signals are sent to the telephone la
using a binary code in which a "0" is encoded by the
routing device as 10 milliseconds of a 800 Hz tone and
a "1" is encoded by the routing device as 10 milliseconds
of a 2 kHz tone .
In this embodiment the counter 31 located in the
telephone la counts the number of edges in a 4
millisecond period and thereby the processor 27, by
monitoring the number of counts in successive periods,
identifies the input as a "0" or a "1" . This system
provides a simple alternative to including a DTMF
receiver in the telephone la at a reduced cost.
As shown schematically in Figure S, the ROM 81 contains
a control procedure 91 for controlling the operation of
the routing device, an authentication procedure 93 for
verifying the identification of the telephone la, a
random number generator 95 for generating a random number
used in the authentication procedure 93 and an encryption
table 97 that is identical to the encryption table 55
stored in the telephone la.
As shown schematically in Figure 6, the RAM 83 contains
an encryption key look-up table 102, containing data
identifying every telephone 1 which has a corresponding
CA 02338890 2001-O1-29
WO 00/07347 PCT/GB99/02243
13
account with the service provider and for each such
telephone 1 a respective encryption key, and account
information 103 detailing the current balance of the
account of each subscriber associated with a telephone
1. The RAM 83. also includes working space 105.
The sequence of events when a call is made by a user of
telephone la will now be described with reference to
Figure 7 which shows a number of steps carried out by the
system manager 51 for the telephone la and with reference
to Figure 8 which shows a number of steps of the control
procedure 91 for the routing device at the intelligent
node 7.
Firstly, at step S1 of Figure 7, the terminal goes off-
hook. This occurs when a user picks up the handset of
telephone la. At this point, the processor 27 activates
the tone generator 23 to generate a "comfort" tone to be
heard by the user via the speaker 21 while the system is
connecting itself to the routing device at the
intelligent node 7 and authenticating its identity. In
this way, the user does not have to listen to the
interchange of signals between the processor 27 and the
routing device which occurs at audio frequencies.
The telephone la then checks in step S3 whether a first
dial tone, which is generated by the local exchange 3 to
which the telephone la is connected in response to the
telephone 1 going off-hook, is present since an outgoing
call cannot be initiated until the local exchange 3 makes
this response. If the first dial tone is present then
the procedure moves on to step S7. The processor 27
continues to look for detection of the first dial tone
during a time-out period measured using clock 39 and
advances the procedure to the next step S7 when detection
CA 02338890 2001-O1-29
WO 00/07347 PCTJGB99/02243
14
is sensed or the time-out period expires, as represented
by steps S3 and S5 in -Figure 7. The use of such a time-
out procedure is preferable in order to enable the system
to function when poor signal line conditions or other
operating difficulties prevent normal detection of the
first dial tone.
In step S7, the processor checks for user intervention,
i.e. whether the "#" button on the keypad of the
telephone 1 has been pressed by the user within a preset
time-out period of two seconds measured from the
detection of the first dial tone. If the "#" button has
been pressed, then the normal procedure is interrupted
and the system manager 51 moves to step S9 in which the
comfort tone is removed to be replaced by the first dial-
tone generated by the local exchange 3 and the user dials
the number of a destination terminal in the conventional
manner without accessing the intelligent node 7 or using
the services of the service provider. This feature is
incorporated to satisfy legal requirements relating to
emergency phone calls so that, for example, in the United
Kingdom a user may call the emergency services by
pressing "#" and dialling "999".
If the pressing of the "#" button by the user is not
detected in the preset period, i.e in the absence of user
intervention, the procedure continues normally at step
S11 by automatically telephoning the intelligent node.
This is achieved by using the DTMF generator 25 of the
telephone 1 to generate a first dialling signal
corresponding to a predetermined call number stored in
the ROM 35 and which identifies the location of the
intelligent node 7. The signal conforms to the lxxx
standard (known as the Easy Access Standard) whereby the
CA 02338890 2001-O1-29
WO 00/07347 PCT/GB99/02243
first digit sent is "1" followed by a number which
indicates the location-of the intelligent node 7.
The routing device at the intelligent node 7 detects
5 connection to the telephone la at step S25 of Figure 8.
The routing device further receives information providing
a preliminary identification of the telephone la. In
this embodiment, the preliminary identification is made
using the Call Line Identifier (CLI) system in which a
10 code identifying the telephone number of the originating
caller is generated by the local exchange 3.
Subsequently, in step S27, the routing device 70 sends
a connection confirmation signal to the telephone la in
the form of a continuous tone detected in the telephone
15 la by the zero-crossing detector 29 and the counter 31.
The system manager 51 of the telephone la checks, in step
S13, if the connection confirmation signal is detected.
A further time-out period of two seconds is measured from
the commencement of this detection checking step and the
processor 27 advances control to step S17 when either
detection is sensed or the time-out period expires, as
represented in Figure 7 by steps S13 and S15.
After the routing device has sent the connection
confirmation signal in step 527, the control procedure
91 moves on to step S29 in which the authentication
procedure 93 is activated.
In step S17 of the system manager 51 for the telephone
1, the authentication subroutine 53 is run. The
authentication subroutine 53 for the telephone 1 is shown
in detail in Figure 9 while the authentication procedure
93 for the routing device is shown in detail in Figure
10.
CA 02338890 2001-O1-29
WO 00/07347 PCT/GB99/02243
16
At step S43 of Figure 9, the telephone la sends a start
signal using a predetermined DTMF code signal to the
intelligent node 7 indicating the start of
authentication. The routing device 70 waits for receipt
of the start signal, at step S63, and subsequently sends
an authentication data signal in step S65 in the form of
a frequency shift key modulated tone.
An advantage of sending a start signal from the telephone
la to the routing device 70 to initiate authentication
is that it is easier for a separate procedure to be
initiated than to require the telephone la to
differentiate between the connection confirmation signal
and the authentication data signal.
The authentication data signal consists of a header, a
cyclic redundancy check (CRC) block followed by a data
block. The data block contains a 16-bit random number
generated by the random number generator 95. The routing
device sends the authentication data signal repeatedly
until a response is received from the telephone la.
The telephone la waits for the authentication data signal
in step S45 by looking for detection of frequency
modulated signals using the zero-crossing detector 29 and
the counter 31 and checks in step S47 whether an error
is present in the received authentication data signal
using the CRC block as a check against a CRC calculation
based on the data block. If an error is detected in step
S47, the authentication subroutine returns to step S45
to repeat detection and error checking of the
authentication data signal. If no error is detected in
step S47, the authentication sub-routine continues with
step S49.
CA 02338890 2001-O1-29
WO 00/07347 PCT/CI399/02243
17
In step S49, the processor 27 in the telephone 1 combines
the received random number in the data block of the
authentication data signal with an encryption key which
is formed by the lowest 16 bits of the 48-bit number
stored in the ID chip using a logic operation to create
an intermediate 16-bit number. The logic operation may
be any standard encryption function adopted for the
system, typically comprising a predetermined series of
simple arithmetic steps.
The intermediate 16-bit number is used in step S51 to
generate an authentication response signal by using the
first eight bits to address the encryption table 55 which
outputs the 8-bit number stored at that address to form
the first eight bits of the authentication response
signal. The second eight bits of the intermediate 16-bit
number are then used to address the encryption table 55
in the same way to form the second eight bits of the
authentication response signal. The authentication
response signal is transmitted by the telephone la to the
node 7 in DTMF form.
The routing device at the intelligent node 7 calculates,
at step S67, an expected authentication response using
an identical logic operation to that carried out by the
processor 27 of the telephone la to combine the random
number in the data block of the authentication data
signal with the encryption key for the telephone la . The
routing device processor 71 has knowledge of the
encryption key for every telephone 1 of a user who
subscribes to the service provider and for each
authentication process looks up the relevant encryption
key in look-up table 102. Subsequently the routing
device processor 71 generates the expected authentication
CA 02338890 2001-O1-29
WO 00/07347 PCT/GB99/02243
18
response signal using the encryption table 97 which is
identical to the encryption table 55.
The routing device waits, at step S69, for the
authentication response signal and when the
authentication response signal is received compares, in
step S71, the authentication response with the expected
authentication response. If the authentication response
is identical to the expected authentication response then
the identification of the telephone 1 has been confirmed
and the authentication procedure ends.
If the authentication response is not identical to the
expected authentication response then, in step S73, the
routing device processor 71 checks if a maximum number
of retries has been exceeded. If the maximum number of
retries has not been exceeded then the authentication
procedure returns to step S69. If the maximum number of
retries has been exceeded then, in step S77, the routing
device sends a signal to the telephone la indicating that
the routing device could not confirm the identity of the
telephone 1 and that the user of the telephone la must
place the telephone 1 on-hook again.
An advantageous feature of this authentication process
is that the routing device processor 71 calculates the
expected authentication response while the telephone la
is calculating the authentication response. Therefore,
when the authentication response signal is received by
the routing device 70, the routing device 70 is
immediately able to compare the authentication response
with the expected authentication response.
If the telephone la has been successfully identified in
the authentication procedure 93, then the control
CA 02338890 2001-O1-29
WO 00/07347 PCT/GE399/02243
19
procedure of the routing device 70 of the intelligent
node 7 proceeds to step 531, as shown in Figure 8, in
which the routing device processor 71 checks the account
information 103 to see if the customer has sufficient
credit to make a call. If the customer does not have
sufficient credit to make a call then the routing device
sends a credit warning signal, in step S33, informing the
customer of that fact. If the customer does have enough
credit, then the routing device 70 sends a second dial
tone to the telephone 1 in step S35.
In step S53 of the authentication subroutine for the
telephone la, the processor 27 of the telephone la checks
if the second dial tone is present. If the second dial
tone is present, this indicates that the telephone la has
been successfully identified and the authentication
subroutine ends. If on the other hand a signal from the
routing device 70 indicating that the customer does not
have enough credit to make the call is detected, the
comfort tone is removed and the credit warning signal is
passed on to the user via the speaker 21. If neither the
second dial tone nor the credit warning signal are
present, then the processor 27 checks at step S55 if a
time-out period has expired. If the time-out period has
2-5 not expired ti~en the authentication sub-routine returns
to step S53 to continue checking for detection of the
second dial tone. If the time-out period has expired
then the authentication sub-routine ends.
After the authentication sub-routine, in step S17, the
system manager for the telephone la proceeds to step S19
in which the comfort tone is removed and the user is
presented with the second dial-tone prompting the user
to dial the phone number identifying the call destination
telephone le. When the routing device receives the phone
CA 02338890 2001-O1-29
WO 00/07347 PCT/CB99/02243
number of the destination telephone le, the routing
device processor 7i controls the switching unit 65 to
connect the telephone la to the telephone le.
5 Compared with conventional telephones which have a
processor and a DTMF generator, telephones in accordance
with the present invention require minimal additional
components to perform the authentication procedures
described above, namely a receiver enabling the telephone
10 to receive signals sent from the routing device. The
embodiment described above has been designed with this
conversion in mind and by using a zero crossing
detector 29 and counter 31 as a receiver this conversion
is achieved at low cost while retaining good
15 functionality.
Other forms of receiver or low bit rate modems may
however alternatively be used.
20 It will be appreciated that in the first embodiment there
is no requirement for the destination telephone le to be
modified and could be any conventional telephone.
In the first embodiment, a preliminary identification of
the terminal la is made using the CLI system. The CLI
system may however not be available in some local
exchanges. In a second embodiment of the invention
therefore, the preliminary identification data is stored
in the telephone la and sent by the telephone la in DTMF
format with the signal for connecting the telephone la
to the intelligent node 7.
In a third embodiment of the invention, as another
alternative, the preliminary identification data is
CA 02338890 2001-O1-29
WO 00/07347 PCT/GB99/02243
21
stored in the telephone la and sent along with the start
signal.
A further embodiment is illustrated in Figure 11 which
illustrates in flowchart form operation of a telephone
having a circuit diagram illustrated schematically in
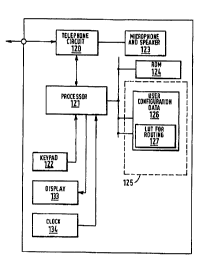
Figure 12. In this embodiment, a telephone circuit 120
comprises a two to four wire converter, tone generator,
DTMF generator, ringer and off-hook detector similar to
those described above with reference to Figure 2. The
telephone circuit 120 is controlled by operation of a
processor 121 which receives user actuated input from a
keypad 122. A microphone and speaker 123 are also
connected to the telephone circuit 120. The processor
121 is provided with a read only memory 124 and random
access memory 125 in which user configuration data I26
is stored, the configuration data including a look-up
table 127 containing an access code for directing calls
via a service provider, i.e. to a predetermined mode.
The processor controls 121 operation of the telephone
at step 110 in Figure 11 to detect an off-hook condition
being initiated and activates the tone generator to
substitute a comfort tone in place of the dial tone
provided by the local exchange so that the user is
presented with the comfort tone via the speaker 123.
The processor 121 then begins a time-out period measure
by means of a clack 134 during which the processor awaits
detection of actuation by the user of the * key of the
keypad 122. If during the time-out period, which in this
example is two seconds, the * key actuation is detected
at step 112, the processor 121 responds in "user
intervention mode" to control the telephone circuit 120
to output to the local exchange the subsequently entered
CA 02338890 2001-O1-29
WO 00/07347 PCT/GE399/02243
22
user dialled digits, i.e. without inserting any access
code, at step 113.
If however the time-out period is detected to have been
completed at step 114 without detection of the * key, the
processor 121 obtains an access code from the look-up
table 127 and outputs the access code at step 115 via the
telephone circuit 120.
At step 116, the processor 121 then controls the
telephone circuit 120 to allow further user dialled
digits entered via the keypad 122 to be output thereby
resulting in the call being routed via the service
provider indicated by the access code to the destination
indicated by the user dialled digits.
In the embodiment of Figures 11 and 12 as described, no
authentication procedure is performed.
A further embodiment based on the structure of Figure 12
will now be described using corresponding reference
numerals and with reference to Figure 14 which
illustrates the mode of operation of the telephone of
this embodiment as controlled by the processor 121.
Figure 13 illustrates an external view of the telephone
of this embodiment, showing in particular the layout of
the keypad 122 which includes function keys 128, 129 and
130 designated as F1, F2 and F3 respectively. The keypad
122 further includes numerical keys 131 and a set of six
operating keys 132 which provide further operating
functions such as last number redial (LNR), microphone
muting (mute ) , and additionally memory control keys SAVE,
RECALL, STORE, and memory (MEM) keys for use in entering
configuration data as described below.
CA 02338890 2001-O1-29
WO 00/07347 PCT/G899/02243
23
The telephone of this embodiment operates as illustrated
in Figure 14 by initially detecting at step 140 the
initiation of an off-hook condition in the telephone
circuit 120 and detecting at step 141 the first key of
the keypad 122 to be actuated by the user. In response
to this detection, the processor 121 controls the
telephone circuit 120 to mute the dial tone from the
local exchange presented to the user so that thereafter
the user hears only dial tones generated by key
actuation.
At step 143, the processor 121 determines whether the
first actuated key is the F1 function key 128 and, if so,
controls the telephone circuit 120 to output dialled
digits corresponding to any further numerical keys 131
actuated by the user, thereby enabling the call to be
routed to the desired call destination via the local
exchange and the convention public service telephone
network, without being routed to any selected service
provider. This mode of operation therefore corresponds
to one of user intervention in which the user, after
lifting the handset, depresses the F1 function key 128
in order to deliberately bypass the automatic routing
function of the telephone.
If at step 143, the first actuated key is detected not
to be F1, the processor 121 determines at step 145
whether the first actuated key is F2 function key 129,
and if so, at step 146 accesses the look-up table 127 to
obtain an access code AC1 of a first service provider and
controls the telephone circuit 120 to insert the access
code AC1 before outputting at step 147 further user
dialled digits defining the destination of a call.
CA 02338890 2001-O1-29
WO 00/07347 PCT/GB99/02243
24
If at step 148, the first key to be actuated is detected
to be a numerical key-having a value in the range 2 to
8, the processor 121 similarly at step 146 uses the
access code AC1 to direct the call via the first service
provider.
In this way, in the absence of user intervention (i.e.
if no function keys are pressed), local calls having the
first digit in the range 2 to 8 are automatically routed
via the first service provider, without the user having
to press any selection key for this purpose, and without
the user having to dial any access code. This mode of
operation is similar that described above with reference
to the telephone embodiment of Figure 11.
If however at step 149, the first actuated key is
detected to be number "0", the processor 121 awaits
detection of the second key actuation at step 150 before
deciding at step 151 on the resulting mode of operation.
If at step 151 the second actuated key is a number other
than "0", the user dialled call is determined to be a
national call which is to be routed via a second service
provider. In this mode, at step 152, the processor 121
accesses the look-up table 127 to determine the access
code AC2 of the second service provider and controls the
telephone circuit 120 to insert the access code AC2
before facilitating at step 147 the output of the user
dialled digits to follow the access code. The national
call required by the user is thereby routed to the
destination required via the second service provider.
If at step 151, the second actuated key is detected also
to be a "0", the processor 121 determines the call to be
an international call to be routed by the third service
provider. The look-up table 127 is accessed at step 153
CA 02338890 2001-O1-29
WO 00/07347 PCT/GB99/02243
to determine the access code AC3 of the third service
provider and the processor 121 controls the telephone
circuit 120 to insert the access code AC3 before the
further step 147 of outputting the user dialled digits.
5 The International call is thereby routed to the
destination defined by the user dialled digits via the
third service provider.
If however at step 154, the first actuated key is
10 detected to be the F3 function key 130, the processor 121
operates in a mode in which a telephone call is
automatically mode to a customer service point by
dialling a service call number. In this mode, at step
155, the processor 121 accesses the look-up table 127 to
15 determine the service call number and controls the
telephone circuit 120 to dial the service call number and
connect the user with the customer service point.
If at step 156, the first actuated key is detected as
20 being a numerical key of number 1 or 9, the processor 121
allows the user dialled digits to be directed to the
local exchange without insertion of any access code,
thereby allowing emergency calls to be processed by the
user dialling 999 and special function provided by the
25 public service telephone network by dialling numbers
commencing with numeral 1 to be accessed.
In use, the user is provided with a telephone which is
simple to use and yet provides the advantages of
automatic routing to preferred service providers for
local calls, national (long distance) and international
calls respectively without necessarily having to press
any keys other than the numerical keys of the telephone
number defining the call destination. If for example the
number dialled is a local call, for which the first
CA 02338890 2001-O1-29
WO 00/07347 PCT/GB99/02243
26
dialled number is in the range ?. to 8, the telephone
automatically inserts-access code AC1 at step 146 before
outputting the user dialled digits, without the user
having to press any function key of the telephone.
If alternatively the user dials a long distance (national
call) for which the first dialled digit is "0" and the
second dialled digit is a number other than "0", the
telephone automatically inserts the second access code
AC2 at step 152 before outputting the user dialled digits
at step 147, the call thereby being routed by the second
service provider network without the user having to press
any function keys or dial any number other than that of
the destination call number.
Alternatively, if the dialled number is an international
call number commencing with digits "00", the telephone
automatically inserts the access code AC3 at step 153
before outputting the user dialled digits at step 147,
thereby automatically routing the call via the third
service provider network without the user having to press
any function key or dial any number other than that of
the destination call number.
The user is however provided with further options to
improve flexibility in use of the telephone so that the
automatic routing function can be bypassed by user
intervention simply by actuating the F1 first function
key 128, the telephone thereby at step 144 outputting the
dialled digits without any access code being added.
The user has a second option of initially actuation the
F2 second function key, in which case the first access
code is automatically inserted, irrespectively of whether
the call is a local call, long distance call, or
CA 02338890 2001-O1-29
WO 00/07347 !'CT/GI399/02243
27
international call, at step 146, before outputting the
user dialled digits at-step 147.
Finally, a third option is provided of automatically
connecting the user to a service point. The user in this
instance simply actuates a single key, i.e. the F3 third
function key 130 and the telephone responds by
automatically dialling the telephone number to access an
operative at the service point at step.156.
In the above description with reference to Figure 14, the
numerical values in steps 148, 149 and 156 are specific
to operation within the United Kingdom. It is to be
understood that for operating in other countries where
reserved numbers for emergency services and public
service telephone network special services may be
different, the numbers utilised will need to be varied
appropriately. The telephone is therefore configurable
by the input of appropriate data to the user
configuration data 126 portion of the random access
memory 125 in Figure 12. This in information may be
programmed into the telephone at the time of manufacture
or may be updated by the user using the keypad 122 using
the operating keys 132 in a predetermined sequence in
conjunction with the numerical keys 132 for the input of
data.
Similarly, the data stored in the look-up table 127 for
the first, second and third service provider access codes
AC1, AC2 and AC3 may be preprogrammed at manufacture or
input or updated by the user using a predetermined
sequence of operation of the operating keys 132 and using
the numerical keys 131 to input data.
CA 02338890 2001-O1-29
WO 00/07347 PCT/GQ99/02243
28
Optionally, to assist the user in this configuring mode,
the telephone may include a display 133 as illustrated
in Figure 12 in order to confirm to the user the data
input and the status of the stored information. Such a
display may also indicate dialled numbers or other
information during normal use.
Figure 15 illustrates a further alternative embodiment
in which the telephone is constituted by mobile telephone
150 having an aerial 151 facilitating wireless
communication with a cellular mobile telecommunications
network. The internal structure of the mobile telephone
150 corresponds to the arrangement illustrated in Figure
12, subject to the telephone circuit 120 including a
transmitting and receiver for wireless communications and
being connected to the aerial 151.
As illustrated in Figure 15, the mobile telephone 150
includes numerical keys 131 facilitating the input by the
user of a number representing the destination of a
telephone call, a call start button 155 and a call end
button 156. The mobile telephone 150 includes additional
operating keys 152 which provide conventional operating
functions of mobile telephones, including access to a
menu of additional user functions, interactive access
being facilitated by display screen 133. The additional
operating keys 152 thereby provide multiple functions
selected according to a displayed menu.
In use, operation of the mobile telephone 150 is similar
to the method described above with reference to Figure
14. In step 140 however, reference to detecting the off-
hook condition corresponds to detection of actuation of
the call start button 155 of the mobile telephone to
initiate dialling and reference in step 141 to detecting
CA 02338890 2001-O1-29
WO 00/07347 PCT/GB99/02243
29
the first key actuation is to be understood as a
reference to subsequently detecting the first key
actuation of the numerical keys 131.
Further, it is apparent that in the case of the mobile
telephone 150, the signal representative of the
destination of the telephone call is output as a wireless
communications signal 153 fox reception by a receiving
aerial of a wireless communications system for ongoing
connection to other networks such as the public service
telephone network.
The mobile telephone 150 provides the facility of user
intervention by operation of the additional operating
keys 152. If the user decides to intervene in order to
prevent the automatic insertion of an access code by the
mobile telephone, the user selects display of the menu
of functions by depressing whichever one of the operating
keys 152 is assigned for this purpose by the mobile
telephone manufacturer. The display screen 133 then
displays the currently selected function and the user may
scroll through the menu of functions in order to arrive
at the function described as intervention to prevent
automatic insertion of a routing access code. for
conveW ence,--this function may be arranged to be the
first displayed function when the menu button is
initially pressed.
To signal user intervention, the user then depresses
whichever of the operating keys 152 is assigned for this
purpose, the display screen 133 indicating to the user
the correct button for this purpose.
If the user then proceeds to initiate a call by
depressing the call start button 155, the mobile
CA 02338890 2001-O1-29
WO 00/07347 PCTIGf399/02243
telephone 150 outputs subsequently user dialled digits
without adding an access code.
The user intervention function selected via the menu may
5 additionally provide the user with selectable options
corresponding to the F2 and F3 buttons on the telephone
described above with reference to Figure 13 in order to
provide functions corresponding to those described above
with reference to Figure 14. The functions provided by
10 the mobile telephone may thereby for convenience be
referred to as functions F1, F2 and F3 in order to
emphasise the commonality of function with the previously
described embodiment.
15 Figure 16 illustrates in flowchart form the operation of
a computer program of the mobile telephone 150 using
corresponding reference numerals to those of Figure 14
where appropriate for equivalent steps. Such a computer
program for implementing the steps of Figure 16
20 constitutes an additional aspect of the present
invention, including an embodiment of the program in a
storage medium or in electronic form such as a signal
transmitted by a network for subsequent installation in
a mobile telephone.
At step 140 in Figure 16, the processor detects
initiation of a telephone call by depression of a call
start button 155. In steps 143, 145 and 154 in Figure
16, the processor checks in RAM whether the user has
selected any one of the functions F1, F2 and F3 prior to
initial actuation step 140.
It is therefore apparent that operation of the mobile
telephone 150 by the user differs from actuation of the
telephone of Figure 13 since, if the user requires
CA 02338890 2001-O1-29
WO 00/07347 PCT/GB99/02243
31
intervention, the intervention function must be set prior
to step 140 in which the call start button 155 is
pressed.
A number of modifications can be made to the above-
described embodiments without departing from the
inventive concept of the invention. Some of these
modifications will now be described.
The embodiments described with reference to the structure
of Figure 12 may additionally include means for
performing authentication, as described with reference
to the embodiment of Figures 1 to 10.
While in the embodiments shown in Figures 2 and 13 the
telephone is placed off-hook by lifting up the handset
of the telephone la, it will be appreciated that the term
"off-hook" is a term of art used to indicate that the
telephone la is drawing current from the local exchange
3. Instead of lifting the handset, the telephone 1 may
alternatively be placed off-hook by pressing a button or
operating a switch, which is the case for telephones with
a speaker phone facility and which is also the case for
mobile telephones as described with reference to Figure
15.
Furthermore, while the embodiments describe a
communication system using of a telephone 1 or mobile
telephone 150, the same inventive concept could equally
be applied to other communication terminals which include
a telephone such as, for example, facsimile machines.
Alternatively the telephone 1 may be replaced by a
private exchange such as private automatic branch
exchange (PABX) or a network signal router. In this
instance, the off-hook event which initiates the above-
CA 02338890 2001-O1-29
WO 00/07347 PCT/GB99/02243
32
described procedures corresponds to an electrical signal
generated when a user initiates a call at a terminal
connected to the PABX or network signal router.
The invention can be applied to cordless telephones
having a handset and a corresponding base unit wherein
signals are transmitted via radio waves between the
handset and the base unit and the base unit is connected
to a PSTN using a signal line.
Although in the embodiment the service provider requires
the subscriber to maintain an account in credit, the
inventive concept could equally be applied to a system
in which a subscriber has a debit account with the
service provider.
It will be appreciated that rather than using the
combination of the zero-crossing detector 29 and the
counter 31 as a receiver in the first embodiment, a DTMF
detector could be used and all the communication between
the routing device and the telephone la may be carried
out using DTMF signals.
Preferably the start signal and the preliminary
identification information could be sent using the DTMF
tones corresponding to ABCD. This is preferable as most
telephones do not have ABCD keys and hence the tones
could not be input manually, thus providing an extra
layer of security.
In the first embodiment the telephone la checks to see
if there is a first dial tone present before starting the
period in which the telephone la checks if the "#" button
is pressed. However, as connections to the local
exchange 3 for the telephone la typically occurs in less
CA 02338890 2001-O1-29
WO 00/07347 PCT/GB99/OZ243
33
than two seconds, the telephone la may simply check for
a predetermined period after going off-hook if the "#"
button is presses and not check if the first dial-tone
is present at all.
Similarly, rather than checking if the connection
confirmation signal is present before sending the start
signal, the telephone la could simply wait for a preset
period of, for example, ten seconds as the vast majority
of connections to the intelligent node 7 will be made in
this time.
The identification number may alternatively be stored in
the memory attached to the processor 27 thereby obviating
the need for the ID chip 41. As explained previously,
the tone generator 23 is only present to provide a
"comfort" tone to the user and may be left out if this
facility is not required.
The described authentication procedure can be varied in
many ways without departing from the inventive concept
of the invention. One particular variation may be that
the routing device 7 sends an error detection and
correction block containing, for example, a Hamming code
instead of the error detection block containing the CRC
block.
Other types of signal modulation such as pulse code
modulation of a 2kHz tone may be used for transmitting
data from the node to the terminal 1.