Note: Descriptions are shown in the official language in which they were submitted.
CA 02338910 2001-02-28
METHODS, PRODUCTS AND APPARATUS FOR PROVIDING
MACHINE UNINTELLIGIBLE, HUMAN UNDERSTANDABLE
INFORMATION ON A COMMUNICATIONS NETWORK
FIELD OF THE INVENTION
The present invention relates to the processing of information for storage and
display on a
communications network, and, more particularly, to the disguising of
information by storing the
information in a media format so that the information is unintelligible by a
machine but
to understandable by a person.
BACKGROUND OF THE INVENTION
The Internet is causing a revolution in the way people communicate, conduct
business and
socialize. Businesses develop web sites to sell their products, promote their
services and for public
relations. Individuals and organizations develop web sites to promote their
identity, share
information and to provide entertainment.
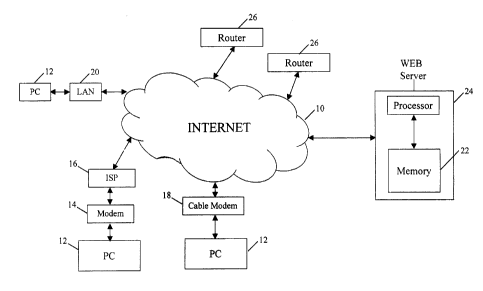
Fig. 1 is a schematic representation of certain portions of the Internet 10.
An individual may
access the Internet 10 to search for and view a web page via a personal
computer ("PC") 12
connected to the Internet 10 through a modem 14 and an Internet service
provider ("ISP") 16, a cable
modem 18 or a local area network ("LAN") 20, for example. Instead of a PC 12,
the Internet 10 can
2o be accessed through a television set through WebTV~, and through handheld,
personal digital
assistants (PDA's), such as a Palm Pilot~ (not shown).
Web pages are stored in the memory 22 of web servers 24, typically on a hard
disk. Other
types of memory may be used, as well.
Web pages are accessed through the World Wide Web network. The World Wide Web
rnay
be searched by an individual user via web browser software, such as Netscape
Navigator~ and
Microsoft ~ Internet Explorer~, using Hypertext Transfer Protocol ("HTTP").
Specific web sites and
web pages are identified by and located through their Uniform Resource Locator
("URL"). A typical
YOR9-1999-0476
CA 02338910 2001-02-28
URL address for a web page is in the following format:
httv://www.host.com/directoryl/filename html. The first portion of the address
"http://" indicates
the Internet Protocol which is used, here HTTP. The next part: www.host.com,
identifies the host
computer or web server where the web page is stored. The remainder of the
address indicates the
directory on the server, here DIRECTORY1 and the file name of the web page,
here FILENAME.
Routers 26 read the URL address and direct the request to the proper web
server, here the
HOST web server in the ".COM" domain. The web server 24 searches its
DIRECTORY1 for the
requested web page FILENAME, and sends that web page to the requestor via the
routers 26. The
web page is then displayed on the monitor of the PC 12 or other such device of
the requestor by the
web browser.
Electronic mail is a fast and inexpensive way to communicate through a network
such as the
Internet. Unfortunately, e-mail has lead to the development of the electronic
equivalent of junk mail,
referred to as "spam." Unwanted advertising, news or other such messages,
which are sent in bulk,
can fill a mailbox, requiring time to review and delete. The volume of spam is
so high that more
powerful and expensive servers are required to handle legitimate mail along
with the spam. America
Online~ stated in 1997 that one third of the e-mails received by its
subscribers were spam.
Schwartz, Alan R.; Garfunkel, Simon, Stopping Spam, O'Reily & Associates,
Inc., California, p. 4
( 1998).
E-mail addresses are collected by those businesses, organizations or
individuals interested
2o in sending spam through publicly available sources such as chat rooms, web
sites, mailing lists and
Usenet news groups. (Id. at pp. 40, 66). The text of a web page is stored on a
server in digital
format, such as ASCII (American Standard Code for Information Interchange)
text. Search engines,
referred to as harvesting programs, run by processing machines such as
computers are used to locate
and identify e-mail addresses and other personal information on web pages, by
reading the digital
text.
To identify an e-mail address, harvesting programs may search the text of each
page of a web
site for particular designations or symbols commonly used in e-mail or website
addresses. For
example, the harvesting program could search for a series of symbols in the
format of
NAME@ISP.COM, which is a typical format for an Internet or e-mail address. The
name to the left
YOR9-1999-0476 2
CA 02338910 2001-02-28
of the @ symbol is the username. The letters to the right of the @ symbol
identify the host name
or domain name of the computer where the user has an e-mail account. It may be
an Internet Service
Provider ("ISP") or an online service. If the user's e-mail account is through
a business network, the
name of the business may be identified. After the dot ".", the domain for the
type of organization
hosting the address is indicated. For example, ".com" refers to a commercial
organization. The
network directs the e-mail to the proper location within the network based on
the user name, to the
left of the dot ".".
A harvesting program could also merely search for the "@" symbol, or a dot
".", and collect
those symbols before and after those designations. Harvesting programs could
also search for
1o numeric Internet addresses, which are in the form of four sets of numbers,
each set being separated
by dots, i.e., 123.45.678.90. Standard formats for e-mail addresses are
defined in RFC822, issued
by the Internet Engineering Task Force. (Id. at pp. 46, 49). Hyperlinks are
also source of addresses.
The harvesting program could search a web page for the HTML hypertext command
"href', open
the site and search for addresses there. Harvesting programs can also be
programmed to search for
other personal information, such as names, addresses and phone numbers.
A variety of techniques have been developed to foil harvesting programs.
Filtering programs
are available which automatically delete e-mail according to defined criteria.
For example, the
filtering program can delete e-mail received from the address of a known
spammer. Filtering
programs can also delete mail with symbols typically used by spammers in their
subject matter
fields. (Id. at pp. 78-84). For example, spammers often use all capital
letters, exclamation points
and dollar signs in their subject matter fields. Filters can also delete all e-
mail except that received
from particular addressors. However, such filters present the risk of deleting
authentic messages,
however.
Another technique, referred to as "address munging" modifies an e-mail address
by inserting
words into the e-mail address appearing on a web page, which obviously should
be removed. For
example, an e-mail address for JOHN@AOL.COM can be listed on a web site as
JOHN@NOSPAM.AOL.COM. It would be apparent to a human observer of the web site
that
"NOSPAM" is not part of the actual web address. However, to a harvesting
program, the entire
address is in an acceptable format and would be acquired. Spam sent to
YOR9-1999-0476 3
CA 02338910 2001-02-28
JOHN@NOSPAM.AOL.COM would not be received by JOHN@AOL.COM.
Alternatively, the "." in the e-mail or web address may be replaced by the
word "dot", i.e.,
JOHN@AOL-DOT-COM. It is apparent that the word "dot" should be replaced by the
symbol
".". Where the substituted or added portion of the address may not be so
readily apparent, or to
ensure that the address is properly used, instructions for correctly modifying
the address can be
included on the web page. A harvesting program would not be able to read the
instructions. The
e-mail address can also be made part of a graphical image displayed on the web
page, which is
currently unreadable by a harvesting program. (Id. at pp. 69-79).
1o SUMMARY OF THE INVENTION
Address munging is an effective technique. However, as harvesting programs
become more
sophisticated, simple address munging may be overcome. For example, artificial
intelligence
incorporated into the programs may be able to identify certain modifications
to true e-mail addresses.
Sophisticated harvesting programs may also be developed which will be able to
read e-mail
addresses in graphical images by the application of optical character
recognition to the displayed
image, for example. Therefore, improved techniques for disguising information
stored on a
communications network will be required.
In accordance with one embodiment of the present invention, a method of
processing text
is disclosed comprising disguising the text and creating a graphical image
file of the text such that
2o the text is substantially unintelligible by a machine, but understandable
when displayed for viewing
by a person. The text may be disguised before, during or after creation of the
graphical image file.
The disguising step may comprise manipulating the characters of the text to
replace a character by
a similar-looking character, replace a character by a word or to insert
extraneous characters or words
into the text. The disguising step may also comprise processing of the
graphical image file to
provide a background with low contrast with respect to the text, a textured
background or an alpha-
numeric background. Preferably, both disguise techniques are used. The
character manipulation
may also be performed by processing the graphical image file. Character
manipulation may also
take place prior to or during creation of the graphical image file. The
graphical image file may be
YOR9-1999-0476 4
CA 02338910 2001-02-28
stored on a communications network. A harvesting program would require optical
character
recognition or some other technique to read the graphical image file. The
disguise of the text in the
image makes the accurate capture of the information by optical character
recognition more difficult
or impossible.
In accordance with another embodiment of the invention, a method of processing
text is
disclosed comprising disguising the text by creating a graphical image file of
the text and then
further disguising the text by processing the graphical image file such that
the disguised text is
substantially unintelligible to a machine, but understandable when displayed
for viewing by a
person. The processing of the graphical image file may involve either the
variations in the
1o background of the text or manipulation of the characters of the text, or
both, as discussed above.
In accordance with another embodiment of the invention, a computer readable
medium
storing a graphical image file of text is disclosed, wherein the original text
is disguised to be
substantially unintelligible by a machine but understandable when the
graphical image file is
displayed for viewing by a person. The text may be disguised in one or more of
the manners
described above.
In accordance with another embodiment of the present invention, a method of
processing
information by converting the information into a dynamic media such that the
information is to be
substantially unintelligible by a machine but understandable by a person, such
as audio or video, and
creating a media file of the information, is disclosed. In this case, further
disguise is optional. While
2o a machine could apply voice recognition techniques to attempt to capture
information from an audio
file, such techniques are not yet reliable enough to capture the information
with a high degree of
accuracy. Very high accuracy is required to capture the necessary information
(e-mail address) to
send spam. Further disguise of information in the form of audio may include
recording the
information at a speed faster or slower than normal, recording the information
with an accent and
recording the information with background sound, to further foil the use of
voice recognition
techniques by a machine. Further disguise of information in the form of video
to foil character
recognition may include any of the techniques discussed above with respect to
disguising text in an
image. The dynamic media file may be stored in a memory of a communications
network. In
another embodiment of the invention, a computer readable medium storing the
dynamic media file,
YOR9-1999-0476
CA 02338910 2001-02-28
is disclosed.
Other disclosed embodiments of the invention include software for processing
information
as described above, methods of designing a web page including information
disguised as described
above, software for designing such a web page, a server storing a graphical
image file or a dynamic
media file of disguised information, a web page displayed on a monitor
including an image of
disguised information, and a method of disguising information for display on a
web page.
An audio file containing disguised information may be provided along with a
graphical
image file or a video file containing the same information so that the
information will be
understandable by a blind or deaf person accessing the information.
to In accordance with another embodiment of the invention, information is
disguised by
encoding the information in a Java Applet. The information may be in the form
of text, which may
be further disguised by the techniques discussed above. Alternatively, the
information may be in
the form of audio or video for further disguise. The audio and video may also
be further disguised,
as described above. Further disguise of the information in the Java Applet may
also be provided by
converting the Java Applet to byte code format.
Each of the embodiments of the invention are particularly suitable for
disguising personal
information, such as one's name, address, web site and e-mail address or
telephone number.
The disguise techniques of the present invention make the capture of
information stored on
a communications network by a machine difficult or impossible. Overcoming the
techniques of the
2o present invention would require highly sophisticated and expensive machines
using highly
sophisticated and expensive harvesting programs, making it uneconomical or
impossible for most
parties desiring to acquire such information. The present invention is
therefore said to render such
information "substantially" unreadable by a machine.
DESCRIPTION OF THE FIGURES
Fig. 1 is a schematic representation of portions of the Internet;
Fig. 2 is a flow chart of a method in accordance with one embodiment of the
present
invention;
Fig. 3 is a simplified view of the layout of a web page on a computer screen
including basic
YOR9-1999-0476 6
CA 02338910 2001-02-28
HTML codes; and
Figs. 4-15 are examples of images of information, disguised in accordance with
the present
invention.
DETAILED DESCRIPTION OF THE INVENTION
Fig. 2 is a flow chart of a process for creating a web page including
information, such as
personal information, disguised to be substantially unintelligible by a
machine but understandable
when displayed for viewing by a person to avoid collection by a harvesting
program, in accordance
with one embodiment of the present invention. The text, images, sound and/or
movies, and any
other desired features of each page of the web site, may be selected and
arranged by the designer of
the web page, in Step 100.
Text may be laid out in a desired format on a computer monitor with a word
processing
program such as Microsoft~ WORD~ and Corel Word Perfect~, or a text editor,
such a Notepad~ for
Windows~ and Simple Text~ for Macintosh, as is known in the art, in Step 110.
The arrangement of the text on the web page may be defined through a software
package,
such as Adobe's Page Mill and Sierra Home Complete Web Studio 2.0 from Sierra
Home,
www.Sierra.com, or directly through Hypertext Markup Language ("HTML"), as is
known in the
art, in Step 120. See, for example, Morris, Mary E.S., and Simpson, John E.,
HTML for Fun and
Profit, Sun Microsystems Press, A Prentice Hall Title, 3rd Edition, 1998; and
Maran, Ruth, Creating
2o Web Pa es with HTML Simplified~, IDG Books Worldwide, Inc., 1999.
HTML codes or tags are added to the text laid out by the word processor or
text editor in Step
120 by the software or directly by a person, as is known in the art, to define
the position of the text
on the page and characteristics of text, such as its size and font. An HTML
editor may be used to
more easily add HTML codes to the text. HTML editors are available from Bare
Bones Software,
Inc., www.barebones.com, and Home Site' from Allaire Corp., www.allaire.com,
for example.
Software packages are also available for facilitating the creation of web
pages, including the
automatic addition of HTML codes. Internet Service Providers ("ISP") such as
America Online~
and portals such as YAHOO~ facilitate the creation of web pages, as well.
Fig. 3 shows a simplified layout of a web page with basic HTML codes as it
would appear
YOR9-1999-0476 7
CA 02338910 2001-02-28
on a computer screen. The document begins and ends with the codes <html>,
<lhtml>, respectively.
A head portion of the document, which includes the title of the document
listed in the directory of
the server but not appearing on the web site itself, begins and ends with the
HTML codes <head>,
</head>. The title itself AAAA is preceded and followed by HTML codes <title>,
</title>,
respectively. The body portion of the document, which is displayed on the web
page, is defined
between the HTML codes <body>, </body>. Here, the body includes the text XXXX.
If media, such as images, sound or movies, is to be used on the web site, the
subject matter
must be converted into a web compatible media format for use and display on a
web page. The
Multipurpose Internet Mail Extension ("MIME") defines acceptable formats for
use on web pages.
Non-MIME formats may require software in addition to that generally provided
with standard web
browsers, such as Netscape Navigator~ and Microsoft~ Internet Explorer~, for
play or display.
Images are converted into a graphics format for display on a web site, in Step
130 in Fig. 2.
Commonly used graphics formats include the Graphics Interchange Format
("GIF"), Joint
Photographics Experts Group ("JPEG") and Portable Document Format ("PDF") used
with Adobe~
Acrobat . An image in a graphics format is stored in a graphical image file.
An image, including an image of text, can be created in a graphics format or
converted into
an graphics format, and stored in a graphical image file through an image
editing program such as
Microsoft~ PowerPoint~, Paint Shop Pro~, Adobe Photoshop~ and Lotus
Freelance~, for example.
Images can also be converted into a graphics format and stored in a graphical
image file by scanning
2o the image. A digital camera can also be used to create a graphical image
file by taking a picture of
the image. A hand drawn image can be converted into a graphics format and
stored in a graphical
image file by scanning or digitally photographing the image, as well.
To position an image on a web page, the graphical image file of the image is
identified on
the computer screen at a location corresponding to the desired location of the
image on the web page
through HTML codes, also in Step 130 in Fig. 2. The HTML code for locating a
graphical image
file is <IMG SRC="filename.fileformat">. An HTML code for positioning a
graphical image file
identified as FILENAME in GIF format is <IMG SRC= "filename.gif'>. Fig. 3
includes a graphical
image file in GIF format identified as FILENAME1. During design of the web
page, the graphical
image file may be stored in a folder or subfolder on the computer. Web design
software such as Web
YOR9-1999-0476 8
CA 02338910 2001-02-28
Studio 2.0 from Sierra Home also facilitates the incorporation of images on a
web site.
If sound, such as background music, is to be provided on a web site, an audio
file of the
sound may be created by digitally recording the sound and converting the
digital recording to a
MIME format, such as WAVE, AU and BASIC SOUND. The digital recording can also
be
converted to MP3 and REAL AUDIO formats. Execution of audio files in MP3 and
Real audio
formats requires additional software to that generally provided with standard
web browsers, such as
Netscape Navigator~ and Microsoft~ Internet Explorer~. An example of such
software is Real
Player~ by RealMedia, Inc., www.realmedia.com. Sound recording programs, such
as Windows~
Sound Recorder and Macintosh~ QuickTimePro 4 from Apple Computer, enable the
recording of
1 o sound through a microphone connected to a computer. The programs convert
the digitally recorded
sound to an acceptable format for transmission over the web and display on a
web page by a web
browser. Sound already recorded on a CD-ROM may be converted to MP3 and WAVE
through
software such as Streambox Ripper 2.009,
www.streambox.com. Streambox Ripper 2.009 also enables conversion of Real
Audio format to
MP3 and WAVE. GoldWave v4.1 l,
www.~oldwave.com, enables the editing of WAVE and MP3 audio files.
An audio file is typically associated with a web page through a hyperlink on
the web
page. The hyperlink itself can be text or an image. The HTML codes for
locating a text
2o hyperlink for a sound file in WAVE format on a web page is <A
HREF="filenarne.wav"> TEXT
</A>. Fig. 3 includes a hyperlink of text YYY to a sound file in WAVE format
identified as
FILENAME2. The sound file may also be stored in a folder or subfolder of the
computer.
If moving images are to be provided on the web site, the images must be
converted into a
video MIME format such as MPEG (Motion Pictures Experts Groups) for animated
video, AVI
for Microsoft~ Windows~ or QuickTimePro 4 by Apple Computer, in Step 150 in
Fig. 2.
A video file is also typically associated with a web site through a hyperlink
on a web
page. An image hyperlink in JPEG format to a video file in AVI format, for
example, may be
created through the HTML code <A HREF="filename.avi"><IMG SRC =
"filename.jpg"></A>.
Fig. 3 includes a hyperlink to a video file in AVI format identified as
FILENAME3. The
YOR9-1999-0476 9
CA 02338910 2001-02-28
hyperlink is an image, which is identified as FILENAME4 in JPEG format.
Returning to Fig. 2, in accordance with one embodiment of the present
invention, information
which one does not desire to be accessible by harvesting programs, is selected
in Step 160 and
disguised by conversion into a media file in Steps 170, discussed in more
detail, below. The
information may be personal information such as a web site address, or the web
site creator's e-mail
address, home address, name or telephone number, for example. The information
may be in the
form of text and the media file may be a graphical image file. The information
can also be converted
into a dynamic media, such as audio or video, and the dynamic media converted
into a dynamic
media file. If a graphical image file is used, the text is further disguised
in one or several manners,
1 o as described further, below. If a dynamic media file is created, the
information is optionally further
disguised, also discussed further below. The graphical image file or dynamic
media file is
positioned on a web page with HTML codes, directly or through the assistance
of the web design
programs discussed above, in Step 180.
The web page may be posted onto the World Wide Web through a dial up
connection to the
Internet through a local Internet Service Provider ("ISP") and stored on a
computer readable
medium, such as a the hard disk or other memory of a web server though File
Transfer Protocol
("FTP"), as is known in the art, in Step 190. Software packages such as
Complete Web Studio 2.0
and web browsers facilitate uploading the web site to a server.
Steps 170 of Fig. 2 will now be described in more detail. To disguise
information in the form
of text in accordance with one embodiment of the invention, the information is
converted into text
in step 205. The characters of the text are then manipulated in step 210 to
disguise the text.
Manipulation of the characters of the text may involve replacing at least one
character of the
text by another character having a similar appearance. For example, Fig. 4
shows an e-mail address
JOHN(aOAOL.COM, wherein the letter "O" in JOHN has been replaced by the number
"0" (Zero).
In addition, in "AOL", the letter "L" has been replaced by a numeral "1" and
the letter "O" is
replaced by the number "0" (zero). The replacement of the letter "O" by the
number "0" is almost
imperceptible to a viewer. It would be obvious to most viewers that the "1"
should be an "L".
However, instructions may be provided in the image or on the web page to
explain to a viewer of
the web page how to correct the web address. The number "1" can also be used
to replace the letters
YOR9-1999-0476 10
CA 02338910 2001-02-28
"I" and "i". A "." (dot) can also be replaced by a "," (comma), and a ":"
(colon) may be replaced by
a ";" (semi-colon). Forward slashes (//) may also be replaced by reverse
slashes (\\) as in Fig. 5,
discussed further, below. These replacements are merely illustrative and other
replacements of
characters by similarly looking characters may be used, as well. In each case,
due to the
replacement, a harvesting program would collect an incorrect address.
Symbols, elaborate fonts and foreign language letters which are recognizable
to a viewer may
also be used to replace similarly appearing conventional characters to
disguise personal information.
Fig. 5 shows a proper web site address " http://www.fox(aOAENET.com", using
characters which are
difficult for optical character recognition to interpret. In addition, as
mentioned above, the "//" is
to replaced by a "\\" to provide further disguise.
Characters can also be replaced by words. For example, in the e-mail address
JOHN(aOAOL.COM, the "@" character may be replaced by the word "AT" and/or the
"." character
may be replaced by the word "DOT," as shown in Fig. 6. Separating the words or
names by dashes
("-") as shown in Fig. 6, may further disguise the text.
The graphical image of the personal information can also include words which
obviously
should be deleted. For example, the e-mail address in Fig. 4 may be provided
in the graphical image
as JOHN(aODELETEME.AOL.COM, as shown in Fig. 7. Instructions may be included
in the
graphical image or on the web page to explain to a viewer of the web page how
to convert the
displayed information to real information. Even if a sophisticated harvesting
program could read
2o the image, the program must also be able to remove the words "DELETEME", or
other such phrases,
which are obviously not part of the real e-mail address.
Returning to Fig. 2, a graphical image file of the text disguised through
character
manipulation is created in step 215. Such a file may be created by any of the
graphics software
packages described above, scanning of an image of the disguised text or
digitally photographing an
image of the disguised text. Creation of the graphical image file itself
provides a further level of
disguise of the text.
The graphical image file is preferably processed to further disguise the text,
in step 220.
Processing of the graphical image file may include providing a background to
the text which
provides insufficient contrast with the text for a harvesting program to
distinguish the text from the
YOR9-1999-0476 11
CA 02338910 2001-02-28
background, yet can still be distinguished by the human eye. For example, a
person can distinguish
contrast ratios of as low as 1.5 to 1. A harvesting program using optical
character recognition
currently requires contrast ratios of greater than 32 to 1. Contrast ratios
between the text and
background of less than about 32 to 1 and greater than about 1.5 to 1 is
therefore preferred in the
present invention. Since it can be expected that the abilities of optical
scanning recognition will
improve, contrast ratios at the lower end of the range are more preferred.
Contrast ratios between
the text and the background may be adjusted through software. The HP Office
Jet Manager for
Hewlett Packard Printers, for example, includes processing software which
enables the specific
adjustment of contrast ratios in scanned images and digital images created by
other methods.
1 o In Fig. 8a, the image of the graphical image file of the image of Fig. 4
has been processed
in step 220 to create a background of dark gray and the text of light gray.
While distinguishable to
a human observer, insufficient contrast is provided for a machine to
differentiate between the text
and the background using current techniques. Similarly, the graphical image
file of the image of Fig.
6 is processed in step 220 to create a graphical image file of the image of
Fig. 8b.
In Figs. 8a and 8b, different shades of the same color are used. Different
colors which
provide low contrast can also be used. For example, white text may be used
with a yellow
background, as shown in Fig. 9. Because such a low contrast ratio is provided
between the text and
background, character manipulation is not used in this example. Step 210 in
Fig. 2 is therefore
skipped, as indicated by the dotted line "a" in Fig. 2.
2o The graphical image file can also be processed in step 220 of Fig. 2 by
providing a random
alpha-numeric background of one color and the characters of the text of
information in another color
or shade of the color. In Fig. 10, for example, a phone number "212-555-2347"
is provided in black,
surrounded by blue numbers. Similarly, in Fig. 11, the web address
"http://www.anynet.net/ jgdoe"
is provided in black among random blue characters. A viewer of a website can
immediately
distinguish the phone number while to a harvesting program, the entire image
is an indistinguishable
string of numbers separated by dashes. Step 2 has been skipped in examples, of
Figs. 10 and 11, as
well.
The random alpha-numeric background can also be smaller or larger than the
real text. In
Fig. 12, the real text is larger than the background text. In this case, the
color of the personal
YOR9-1999-0476 12
CA 02338910 2001-02-28
information and the background can be the same. As in Figs. 8a and 8b,
character manipulation may
be provided in the examples of Figs. 10-12, as well.
The graphical image file may also be processed in step 210 of Fig. 2 by
providing a textured
background to the text of information, as shown in Fig. 13. Such texturing
blurs sharp edges
between the text and the background, making it difficult for a harvesting
program to differentiate
between the text and the background. In Fig. 13, the text includes a person's
name, phone number,
facsimile number, home mailing address, web page, beeper number and cell phone
number. The
character manipulation of step 210 may be provided, as well.
Step 220 may also include the processing of the graphical image file to
decrease the
1o resolution of the text. This can be accomplished by a variety of
techniques. For example, Fig. 14
shows text with shadows, which would be very difficult to read with optical
character recognition.
Again, the character manipulation step 210 in Fig. 2 has been optionally
skipped.
Multiple types of character manipulations may be provided in step 210, along
with the
processing step 220. In the image of Fig. 15, an obviously superfluous word,
"DELETEME", has
been added and several character substitutions have been made. In addition,
the graphical image file
has been processed to provide low contrast between the text and the
background, in step 220. The
alpha-numeric or textured backgrounds could be provided in step 220, along
with the multiple
character manipulations, as well.
The processing techniques described above are illustrative and other
techniques may also be
2o used to disguise the information to impede accurate capture by a machine.
The graphical image file is then saved in an appropriate format such as GIF or
JPEG in step
225 of Fig. 2, and the saved graphical image file is positioned with HTML
codes in step 180, as
described above.
The manipulation of the characters of the text (step 210), the creation of the
graphical image
file (step 215) and the processing of the graphical image file (step 220) may
all take place
concurrently through use of graphics software package, which typically creates
a temporary
graphical image file when a working screen is opened. The manipulation of the
characters of the text
may also be performed through processing of the graphical image file by
editing the file.
Alternatively, the characters of text can be manipulated during creation of an
image by drawing the
YOR9-1999-0476 ~ 3
CA 02338910 2001-02-28
image, for example. The drawn image may then scanned or photographed in step
215 to create the
graphical image file. That graphical image file may then be optionally
processed in step 220. The
drawn image may also include the low contrast between the text and background,
textured
background or low resolution text, in which case a separate processing step
220 would not be
needed.
As mentioned above, preferably, the characters are manipulated in step 210 and
the graphical
image file is processed in step 220, providing two levels of disguise to the
text, as in Figs. 8b and
15, for example. The creation of the graphical image file itself results in a
third level of disguise.
The multiple levels of disguise make the accurate capture and interpretation
of information
1 o increasingly difficult for a machine. A machine using a harvesting program
would require optical
character recognition or some other technique to read the graphical image. The
other levels of
disguising the text (character manipulation and processing of the graphical
image file), are directed
toward foiling the use of optical character recognition to read the text of
the graphical image, by
creating an image of the information wherein the information is disguised in
the image. As
additional layers of disguise are added to the personal information, the
sophistication of the
harvesting programs and the machines running them must increase, adding
insurmountable
challenges, or at least higher costs, to such programs.
While it is preferred to provide these three levels of disguise to the text,
two levels of
disguise may be effective in accordance with the present invention. As
indicated above, a graphical
2o image file may be created from the text of the information and the file
processed in step 210, without
manipulation of the characters of the text, as indicated by dotted line "a" in
Fig. 2. Processing of the
graphical image file would then yield images with backgrounds which make it
difficult for a machine
to read the text, such as the images ofFigs. 9-12, for example. Alternatively,
the processing step 220
may be omitted and the graphical image file of manipulated text may created
and saved, as indicated
by dotted lines "b" in Fig. 2, yielding graphical image files of images such
as the images of Figs. 4-7,
for example. Even if a harvesting program is able to read the text disguised
as in Figs. 4-7, it would
capture incorrect or undecipherable information. In both cases, creation of
the graphical image file
provides one level of disguise and either the character manipulation (step
210) or the processing step
(step 220) provides another level of disguise.
YOR9-1999-0476 14
CA 02338910 2001-02-28
Use of the graphical image file with either character manipulation (step 210)
or processing
(step 220), or both, should effectively foil all but the most sophisticated
harvesting programs
believed to be currently available or which may be developed in the near
future. It is possible that
such disguise may be overcome by highly sophisticated machines using highly
sophisticated
software, through the application of artificial intelligence, for example.
However, such sophisticated
programs could not be run on a conventional personal computer or mid-range
machine, and may
require a supercomputer to execute. The mufti-layered disguise provided by the
present invention
could, therefore, require such sophistication to overcome, the cost could be
prohibitive to most if not
all parties desiring to acquire such information.
1o Creation of graphical image files of the images of Figs. 4-15 will now be
described.
The image of Fig. 4 may be created with Microsoft~ PowerPoint~97, for example,
by opening
a working screen, creating a text box by pointing the mouse to the Rectangle
Autoshape Icon, and
clicking and dragging the rectangle onto the screen. The size of the rectangle
may then be adjusted
by clicking and dragging a border line of the rectangle. The outline of the
text box may then be
created by pointing the mouse to the Line Color Icon, clicking on the arrow
and selecting a color,
in this example, black. The desired text, including the replacement
characters, is then entered
(typed) into the text box. Correct text can be entered first and then edited,
as well. After saving the
image, the resulting graphical image file may be stored as a JPEG or GIF file
through a Local Save
and the selection of JPEG or GIF under the Save As Type. The image of Fig. 5
is similarly created.
The characters selected in Fig. 5 are readily available in graphics software
packages, such as Power
Point~97. The image of Fig. 6 is also similarly created, by entering the text
including the words
"AT" and "DOT" instead of the characters "@" and ".", or by entering the
correct text and then
editing the text to provide the substitutions. The image of Fig. 7 is also
similarly created, with the
extra words inserted as the text is entered, or afterwards.
The images of Figs. 8a, 8b and 15 may be created by creating a text box and
outline, as
described above. Text color may be selected by clicking on the Font Color Icon
and selecting a
color, in this example, light gray. The desired text is then typed into the
text box including the
replacement characters and superfluous words. To create the background, the
Fill Color Icon is
clicked and a displayed color is selected, here, in this example, gray. The
graphical image file is
YOR9-1999-0476 15
CA 02338910 2001-02-28
saved, as described above. As noted above, the replacement or additional
characters or words can
be entered directly or correct text may be entered and then edited. In
creating the images of Figs.
8a, 8b and 15, as described above, the character manipulation, creation of the
graphical image file
of the image and the processing of the graphical image file are performed
concurrently.
The image of Fig. 9 is created in a similar manner as Fig. 8a, except that the
text color white
and the background color yellow are selected.
The images of Figs. 10 and 11 can be formed in Power Point~97 by creating the
text box, as
described above, typing all the text in one color, highlighting the numbers
whose color is to be
changed, clicking on the Font Color Icon and selecting a different color.
Here, the entire text could
1 o be typed in blue, the real telephone number highlighted and then changed
to black. Alternatively,
the entire text could be entered using black font color. Then, the numbers
before and after the real
text can be separately highlighted and changed to blue. The graphical image
file is then saved, as
described above.
To create the image of Fig. 12, a text box and an outline are created, as
described above. The
15 desired text (JOHNna,AOL.COM) is then entered within the text box. To
create the alphanumeric
background, another text box may be created. Random text is entered into the
second box and
highlighted. The text is reduced by clicking on the Font Size Icon and
selecting the desired font size,
here, half the font size of the desired text. The second text box is dragged
over the first text box so
that the first line of text is positioned in the desired location. If the
second text box is dragged over
2o the top portion of the first text box, another line of random alphanumeric
characters may be entered.
Separate text boxes are then created and similarly filled with random
alphanumeric characters to fill
the portions of the first text box to the right, left and below the desired
text. The component text
boxes are then preferably grouped by clicking the mouse outside the text box
and dragging the
mouse across the image to select the various components. The mouse is then
released, the Draw
25 Icon is clicked and Group is selected. The image is then saved as described
above.
To create a graphical image with a textured background as in Fig. 13 in Power
Point~97, a
text box is created as described above. The color of the box is changed to No
Fill through the Fill
Color Icon. A small rectangle is created and repeated to fill the text box.
The lines around the
rectangles are removed by clicking on the Line Color Icon and selecting No
Lines. The colors of
YOR9-1999-0476 16
CA 02338910 2001-02-28
the boxes are changed through Fill Color by clicking on a rectangle or
rectangles and selecting a
desired color. The texture of the boxes may be changed through the Fill Color
Icon by selecting Fill
Effects, selecting Textures and clicking on the desired texture. The real text
can be typed directly
over the textured background after selection of the desired text color through
the Font Color Icon,
or a second text box may be created, the text entered in the desired color,
and the second box
dragged over the first box. The image is grouped as described above with
respect to Fig. 12, and
saved, also as described above.
The image of Fig. 14, with shadowed letters having decreased resolution, may
be created in
PowerPoint~ 97 by creating the text box and outline, and then clicking on the
Word Art Icon. An
1o appropriate Word Art Style is selected and the text is entered.
Resolution can also be decreased by shrinking the image to define the image
with fewer
pixels than the original image, then expanding the image back to the original
size. The edges of the
resulting image will be "fuzzy". Characters will have jagged edges and lack
the sharp boundaries
required for the harvesting program to interpret a symbol; straight, smooth
boundaries become
stepped. This is the "abasing" effect. The greater the size change, the
greater the effect. Converting
between format types also decreases resolution. For example, converting a JPEG
file to a bit-map
or GIF file and back to a JPEG file, multiple times, will result in fuzzy
images, including fuzzy
letters.
The description of the creation of the images of Figs. 4-15 with PowerPoint~
97 are merely
2o illustrative. The images may be created in PowerPoint~ 97 by other steps,
and may be created using
other graphics software packages by other techniques, as well.
As mentioned above, the image of the text may also be created and the text
disguised in Step
210 of Fig. 2 by drawing the image. A graphical image file of such an image
may be created in Step
215 by scanning the image or taking a digital photograph of the image, for
example, as discussed
above. The original image may contain all the desired disguise or the
graphical image file created
from the image may be further processed to manipulate the characters and/or
change the background
and text, for example.
The graphical image file containing the text may also be encoded in a Java
Applet, adding
an additional layer of disguise.
YOR9-1999-0476 17
CA 02338910 2001-02-28
Information, such as an e-mail address and other personal information, could
also be recorded
in the form of a dynamic media wherein characteristics of the information are
changing, such as
audio and video, in Step 230 of Fig. 2, to disguise the information. A media
file in digital format
may be created in Step 240, after or concurrently with the recording of the
information in Step 230.
An audio file of the information can be created by digitally recording the
information and
creating a dynamic media file from the digital recording for positioning on
the web site.
A web page harvesting program would require a voice recognition program to
read such an
audio file from a web site. Voice recognition is not yet accurate enough to
reliably translate personal
information such as web addresses and phone numbers, which must be exact.
Formation of the
1o audio file may therefore be sufficient disguise to foil most harvesting
programs currently in use.
However, additional disguise may be provided to further impede the capture and
interpretation of
the personal information by providing background sound such as music, speeding
up or slowing
down the sound recording, or having the recording made by someone with a
foreign accent, for
example, in Step 250 of Fig. 2.
A hyperlink text YYY to a WAVE file PERSINFO, for example, is established
through
HTML with HTML code <A HREF="persinfo.wav"> YYY </A>, which is also discussed
above.
A hyperlink image to the audio file, identified as filenames in JPEG format,
is established through
the HTML code <HREF="persinfo.wav"> <IMG SRC="filename5.jpg."> </A>, for
example.
Clicking on the hyperlink on the web page would activate the audio message
which includes the
2o information.
The information can also be stored as a video file in AVI format, for example,
which would
be very difficult for a harvesting program using optical character recognition
to capture and interpret.
In the video, the information can stream across the screen or the size of
words or lettering may
change, for example. If further disguise is necessary, Step 250 in Fig. 2
could include any of the
techniques discussed above with respect to further disguising information in
the form of text within
an image.
Since the disguise techniques involving the use of a graphical image file or a
video file could
be unreadable by a blind person, and the use of an audio file may not be
understandable by a deaf
person, an audio file containing the disguised information could be provided
in conjunction with the
YOR9-1999-0476 ~ g
CA 02338910 2001-02-28
graphical image file or video file, or both, on the web site.
Information in the form of text, a graphical image of text, audio or video can
also be encoded
within a Java Applet to be displayed or played as text or as a dynamic media
when the web page is
opened. The Java Applet can be programmed to open a window to display the
video or to play
audio. The location of the window may be defined within the Java Applet or
within the coding for
the web page, as is known in the art. The Java Applet may be in byte code
format, to further impede
capture and translation by a harvesting program.
As in the use of graphical images of text, to overcome the encoding of
information in the
form of a dynamic media or as a Java Applet, very sophisticated harvesting
programs run by very
to sophisticated machines would be required, rendering such information
impossible or uneconomical
to capture by most parties.
While the present invention has been described with respect to the initial
design of a web
page, it is applicable to existing web pages, as well. Information, such as
personal information on
a web page can be removed and replaced by a media file, prepared as described
above.
Web design software, such as Web Studio 2.0 from Sierra Home, could readily
incorporate
code for facilitating the creation of media files for information, including
further disguise techniques.
Web design software and graphics programs could also readily incorporate code
for converting
information on a pre-existing web site to a media file and to incorporate
further disguise, if
necessary.
2o Software may also be provided through the Internet for facilitating
replacement of particular
text on a web site, such as personal information, by a media file. The
software could convert the text
of information to a media file and facilitate editing of the web page.
While the invention has been described with respect to the storage and display
of
information, such as personal information on a web site accessible through the
World Wide Web of
the Internet, the present invention is applicable to the storage and display
of any type of information
on other types of communications networks, as well.
It will be apparent to those skilled in the art that various modifications and
variations can be
made in the processes, apparatus and products of the present invention
described herein without
departing from the spirit or scope of the invention. Thus, it is intended that
the present invention
YOR9-1999-0476 19
CA 02338910 2001-02-28
cover the modifications and variations of this invention provided they come
within the scope of the
appended claims and their equivalents. In this context, equivalents means each
and every
implementation for carrying out the functions recited in the claims, even if
not explicitly described
herein.
YOR9-1999-0476 20