Note: Descriptions are shown in the official language in which they were submitted.
CA 02339373 2001-02-02
' PCT/AU99/00604
Received 23 December 1999
1
"DATA TRANSFER"
TECHNICAL FIELD
This invention relates to a work station which is selectively connectable to
one
of two or more computer networks of differing security classification. More
specifically,
the invention relates to the utilisation of the work station as a gateway for
the safe
transfer of data between computer networks of differing security
classification. The
invention has particular utility in the defence environment.
BACKGROUND ART
It is often necessary to transfer data between otherwise segregated computer
networks having differing security classifications. For example, certain
information may
from time to time be downgraded in security (eg. from "top secret" to
"secret", or from
"secret" to "confidential' and to implement such a downgrade it is necessary
to take
the information from the higher security network and release it to the lower
security
network.
If the respective networks were fully isolated from each other, such a
transfer of
2 o data from one network to another could occur via portable external buffers
such as
floppy discs, CD ROMS or the like. However, there are advantages, in both the
defence and commercial environments, to having connections between networks
and
more recently there has been a trend to utilise a single work station which is
selectively
connectable to the various networks to thereby provide a "gateway" between the
2 5 various networks.
Transfer of data between computer networks of differing security
classifications
can present problems in terms of security, especially when information is
being
downgraded, as there is a risk that additional information will be
inadvertently and
concurrently released from the higher system to the lower system together with
the
3 o intended release.
The present invention aims to provide a work station in which data can be
safely
transferred between computer networks of differing classifications. The
closest art
known to the applicant is Australian Patent 691102 (Commonwealth of Australia -
"the
'~~it- ., .~;,~ 'asii.::::T
4~_..~~~1
CA 02339373 2001-02-02
PCT/AU99/00604
~ Received 23 December 1999
2
Starlight patent") published 16 October 1996. It is known from the Starlight
patent to
utilise a work station which is selectively connectable to multiple networks
via a data
switch. The Starlight patent teaches a system in which information may freely
flow
from a lower security system to a higher security system, but in which the
flow of data
from the higher security system to the lower security system is prevented by a
data
diode.
DISCLOSURE OF INVENTION
L 0 According to one aspect the invention resides in a work station which is
selectively connectable to one of two or more computer networks of differing
security
classifications, the work station including:-
a vettable data transfer buffer; and
a data switch having a first state in which the work station is connected to a
first
computer network and in which data can be transferred from the first computer
network
to the vettable data transfer buffer, a second state in which the work station
is
connected to a second computer network and in which data can be transferred
from
the vettable data transfer buffer to the second computer network, and an
intermediate
state in which the vettable data transfer buffer is isolated from both the
first and second
z 0 computer systems and in which data in the vettable data transfer system
can be vetted
prior to release to the second computer network.
In a preferred form, the vettable data transfer buffer is configured to only
store
readable characters and the user is forced to examine the contents of the
vettable data
transfer buffer whilst the data switch is in the intermediate state and prior
to release of
the data to the second computer network. In one embodiment, the user must
scroll
through the vettable data transfer buffer whilst the data switch is in the
intermediate
state.
BRIEF DESCRIPTION OF DRAWINGS
Reference will now be made to the accompanying Figures which illustrate
preferred embodiments) of the invention and in which:-
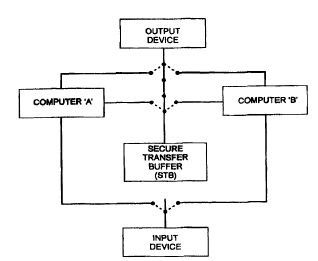
FIG 1 is a schematic illustration of a first embodiment of a work station; and
~. ".; ::;°; -, ,~._.._
' ~~%Iim..i~., . ",.
,
ir~~t;;.y....~.1
CA 02339373 2001-02-02
PCT/AU99/00604
Received 23 December 1999
3
FIG 2 is a schematic illustration of a second embodiment of a work station.
BEST MODE
With reference to FIG 1 there is schematically illustrated a first embodiment
of a
work station according to the invention.
The work station includes an input device (eg. keyboard/mouse), an output
device (ie. monitor), and a secure transfer buffer which are all selectively
connectable
via a switch to either computer A or computer B.
It will be understood that computer A and computer B may be individual
computers or networks of computers.
The three switches are ganged together for synchronised movement and each
switch has three positions. In practice, the user manipulates a single
actuator which
simultaneously actuates all three switches.
:.5 In FIG 1 the switch is shown in the intermediate position. It will be
understood
that when the switches are actuated to the left-most position, the input
device, output
device and secure transfer buffer are all connected to computer A. In this
configuration, the user can manipulate and view data in computer A.
Similarly, when the switches are all actuated to the right-most position" the
input
o device, output device and secure transfer buffer are all connected to
computer B. In
this configuration, the user can manipulate and view data in computer B.
In the intermediate position illustrated in FIG 1, the input device is
isolated, and
the secure transfer buffer and output device are connected together but are
isolated
from both computer A and computer B.
5 Operation of this systems is as follows and assumes that it is desired to
transfer
data from computer A to computer B. As discussed above, the critical transfer
is from
the higher security system to the lower security system. Accordingly, it is
assumed in
this example that computer A has a higher security classification than
computer B. It
will also be understood that the operator of the work station has a security
clearance
:3 o which enable them to work in the higher security environment.
The transfer of data from computer A to computer B starts with the switches in
the left-most position. As discussed, in this position the input device,
output device
and secure transfer buffer are gall connected to computer A. The input device
is used
w
G~~;°:.'.:y mi."t ,:-;~~t_ P
i' ° ~:~il k:.i
CA 02339373 2001-02-02
4
PCT/AU99/00604
Received 23 December 1999
to select data from computer A and send the data to the secure transfer
buffer.
Once the selected data has been transferred to the secure transfer buffer, the
switch is moved to the intermediate position illustrated in FIG 1 in which the
data in the
secure transfer buffer is quarantined from both the origin computer A and the
destination computer B. It will be understood that the work station is
configured such
that any buffers or registers other than the secure transfer buffer are
cleared during
switching. Alternatively, the work station may have all other buffers or
registers
eliminated altogether. This ensures that the secure transfer buffer is the
only possible
repository of data sourced from computer A.
Whilst the data is quarantined in the secure transfer buffer, it can be viewed
via
the output device or vetted by other means.
In a preferred embodiment the secure transfer buffer is configured such that
the
quarantined data must be fully viewed before it can be released. One way of
ensuring
this occurs is to insist that a cursor under the control of the user must be
scrolled
through the entirety of the quarantined data before the data can be released
to the
destination computer. Preferably, the secure transfer buffer is configured so
that it can
only receive displayable characters. Thus, it is ensured that the viewer of
the output
device is able to review all data quarantined in the secure transfer buffer.
This
embodiment relies on the operator of the work station to view the contents of
the
2 o secure transfer buffer.
In other embodiments, this secure transfer buffer may be capable of receiving
non-displayable characters in which case it will be necessary for hardware or
software
to screen the quarantined data to ensure that there is no hidden data, viruses
or the
like.
Once the quarantined data has been satisfactorily vetted either by software,
hardware and/or by viewing on the part of the user, the switch can then be
actuated to
the right-most position at which the data can be released to the destination
computer
B. Once the data has been released by the buffer, the buffer is cleared.
It should also be noted that the act of switching causes a re-set or deletion
of
3 0 any data held in the input device or output device thereby ensuring that
only data
which has been quarantined and vetted in the secure transfer buffer can pass
to
computer B.
Referring now to FIG 2 there is shown a second embodiment which is largely
6~~:_~:!~.a ~
CA 02339373 2001-02-02
PCT/AU99/00604
' Received 23 December 1999
identical to the first embodiment: with the exception of the inclusion of a
second output
device which is dedicated to the secure transfer buffer.
Operation of this second embodiment is similar to the first embodiment however
it will be explained again below to ensure clarity.
5 Again, it is assumed that it is desired to transfer data from computer A to
computer B.
The process starts with all three switches in the left-most position in which
input
device, output device and secure transfer buffer are all connected to computer
A.
Data to be transferred is sent from computer A to secure transfer buffer. The
l0 switch is then moved to the intermediate position in which all other
buffers are cleared
and the secure transfer buffer i;s quarantined from all devices except for its
dedicated
output device. The dedicated output device has some means to enable the user
to
scroll through the data displayed on the dedicated output device.
As previously, in a preferred embodiment, the secure transfer buffer is only
capable of receiving displayable characters from computer A. Thus, it can be
ensured
that all data in the secure transfer buffer can be viewed via the dedicated
output
device. Again, there may be some mechanism to ensure that the user views and
vets
all of the data which is quarantined in the secure transfer buffer. This may
be done, for
example, by insisting that a cursor be scrolled through the entirety of the
data prior to
2 o release of the quarantine data being enabled.
It is again mentioned that, in other embodiments, vetting of the data
quarantined
in the secure transfer buffer may be conducted by hardware or software or the
like
rather than by viewing on the part of the user.
In the embodiment shown in FIG 2, once the user is satisfied that the data
5 quarantined in the secure transfer buffer has been scrutinised to an
acceptable level,
then the switch can be actuated to the right-most position in which the input
device,
output device and secure transfer buffer are all connected to computer B. The
vetted
data can then be released to computer B.
Once the data has been released by the secure transfer buffer, the buffer and
_s 0 dedicated output device are cleared.
Again, it is mentioned that the act of switching causes a re-set or deletion
of any
data retained by the input device and non-dedicated output device, thereby
ensuring
that the only quarantined and vetted data in the secure transfer buffer can be
released
~~,R~br, . "', 5 y r--.~
.. ~. 'J ic~.'y
~ry..~ r
CA 02339373 2001-02-02
6
PCT/AU99/00604
Received 2~ December 1999
to the destination computer.
In conclusion, the invention provides a work station for transferring data
between computers or computer networks in which the data is vetted prior to
release to
the destination computer or computer network.
In preferred embodiments, the vetting of the data is the responsibility of the
user
who is obliged to view the quarantined data prior to releasing the data to the
destination system. In other arrangements, the vetting of the data could be
done by
hardware or software. However, in either case, the data cannot be released to
the
destination system until it has been vetted.
1 o Furthermore, the system is designed such that data cannot pass by any
other
channel to the destination system thereby ensuring that only vetted data can
be
released to the destination system.
It will, of course, be realised that the above has been given by way of
illustrative
examples of the invention. Any variations, modifications, or omissions, as
would be
apparent to persons skilled in the art, are deemed to fall within the broad
scope of this
invention.
AME°;;::~~~ ~~;ma
4 ~: .._ , r