Note: Descriptions are shown in the official language in which they were submitted.
CA 02345107 2001-03-22
INFORMATION CARD AND INFORMATION CARD SYSTEM
BACKGROUND OF THE INVENTION
1. Field to which the Invention Pertains
US 009921663
The present invention relates to an information card and an information card
system. More particularly, it relates to an information card for use as a
credit card, a
cash-vending card, an ID card, etc. which employs Steganography, i.e., image
data
embedding, digital watermarking, information hiding, or digital picture
envelope
technology, and further to an information card system employing such an
information
card
2. Description of Related Art
One known type of the information card is heretofore an IC card for use as,
e.g., a credit card and an ID card. The IC card has an IC chip mounted on a
plastic
plate. The IC chip has either a microprocessor and a memory or a memory only.
The
IC card with the IC chip having both of the microprocessor and the memory is
what is
called an IC card, while the IC card with the IC chip having only the memory
Is
termed as a memory card.
The IC card for use as the credit card carries on its plastic plate surface
the
name of the card owner and the card number. The memory (ROM) in the IC chip
stores an authentication program, a password, and so on. In some cases, the
authentication program and the password for use by the authentication program
are
encrypted for protection against unauthorized access.
However, such conventional IC cards do not have a sufficient level of
security. More specifically, there have been cases where someone illegally
obtains
the password or decodes the encrypted data, and thereby illegally use the IC
card. In
addition, attempts have been made to forge the IC card as a whole. The use of
such a
forged IC card cannot be prevented once the password is obtained
United States Patent No. 5,636,292 discloses steganography methods
employing embedded calibration data in which an identification code signal is
impressed on a carrier to be identified in a manner that permits the
identification
signal later to be discerned and the carrier thereby identified. The method
and
AMENDED SHEET
CA 02345107 2001-03-22
20-11-2000 US 009921663
apparatus are characterized by robustness despite degradation of the encoded
carrier,
and by permeation of the identification signal throughout the carrier. In some
embodiments, the methods are utilized in order to embed a signal on a personal
cash
card, onto which is disposed a photograph of the card owner, in a manner that
the
card may be identified via interaction with a remote computer network
European Patent Number 334,616 discloses a method and system that utilize
a private key of a public-key cryptosystem key pair to encrypt a non-secret
password
into a digital signature. The password and the digital signature are then
encoded and
stored on a magnetic stripe or other memory device of the card. To effect a
transaction, the digital signature on a received card must be shown to have
been
generated from the password on the received card. The password preferably
includes
a digitized photograph of the authorized cardholder which is capable of being
displayed at the transaction terminal. This enables the operator of the
terminal to
verify the identity of the cardholder by visual inspection.
United States Patent Number 5,689,587 discloses a method and apparatus for
data hiding in images which increases and decreases parameter values at
randomly
selected host image locations assigned to respective first and second groups.
The
alteration modifies the statistical behavior of a test statistic equivalent to
a linear
combination of a large number of instances of respective functions, associated
with
the pattern, of the parameter values at first and second group locations. The
presence
or absence of the pattern in a test image is determined by comparing the
experimental
value of the test statistic associated with the pattern with the expected
value of the
same sum for an unaltered host image.
European Patent Number 638,880 discloses a card verification system that
allows for the reading of data from an EEPROM memory device. A photographic
type image is stored in the memory device. The data comprises a data table
containing randomly distributed unique serialized information and desired
verification data is downloaded from a central processing system. The system
uses
color cell compression for the acquisition, digitization and compression of
the
photographic-type image, which may be a facial representation, fingerprint,
signature,
l ~,
AMENDED SHEET
CA 02345107 2001-03-22
20-11-2000 US 009921663
voice print, eye retina or any other unique personal identification in a
compressed
form which may read by the decoding system to verify the positive
identification of
the presenter.
SUMMARY OF THE INVENTION
It is therefore an object of the present invention to provide an information
card and information card system which can completely be prevented from being
forged. This object is achieved by the subject matter of claims 1, 4, 5, 7, &
15
Another object of the present invention is to provide an information card,
15
25
1
AMENDED SHEET
CA 02345107 2001-03-22
20-11-?000 US 00921663
which can completely be prevented from being illegally used, and an
information
card system. This object is achieved by the subject matter of claims 1-3, 6,
and 8 -
14.
2
AMENDED SHEET
CA 02345107 2001-03-22
20-11-2000 US 009921663
In the present invention, as defined in claim 1, the information card contains
the information data in the memory. The information data includes either image
data
or the acoustic data. The inherent data is embedded in the information data
according
to steganography. As a result, even if a third party is able to read the
information data
from the information card, since the inherent data is hidden in the
information data
according to steganography, the third party cannot recognize the presence of
the
inherent, secret, data Thus, it is possible to provide the information card
with a high
level of security. The information data may be of such a size as to allow the
inherent
data to be embedded therein according to steganography. The inherent data
shows
the legitimacy of the card owner of the information card.
In the present invention, as defined in claim 2, since the memory contains the
password for allowing the information data to be read from the memory,
password
checking can allow the information data to be read therefrom. Accordingly, the
security of the stored information data can be made high.
In the present invention, as defined in claim 3, the use of the customized key
enables the inherent data to be extracted from the information data. The
customized
key is not stored in the information card, and hence can be made highly safe
because
this key cannot be stolen.
In the present invention, as defined in claims 4 and 12, the information card
contains the information data. The information data has the inherent data
embedded
therein according to steganography. As defined in claim 8, the information
card
further stores a password for permitting the information data to be read from
the
memory. The data processing terminal checks a submitted password against the
password stored in the information card. When the submitted password
identifies
with the stored password, then the data processing terminal permits the
information
data to be read from the information card, and then outputs such retrieved
information data. For example, the read information data is
4
AMENDED SHEET
CA 02345107 2001-03-22
20-11-2000 _ US 009921663
displayed on a display unit, outputted as sounds, or transmitted as electronic
data
through a communication line.
As a consequence, the information data stored in the information card is
protected against retrieval therefrom by password checking because no
unauthorized
persons are allowed to access it.
In the present invention, as defined in claim 9, the information card retains
the
information data and the inherent data and the data processing terminal
extracts the
inherent data from the information data by means of a submitted customized
key.
The data processing terminal permits the inherent data to be extracted only
when the
submitted customized key is a legitimate customized key. Therefore, even if a
third
party is aware of the presence of the embedded inherent data, the third party
can be
prevented from extracting the inherent data because the third party does not
know the
customized key and further cannot randomly submit any key that is identical to
the
legitimate custonuzed key. Accordingly, the information card system provides a
high
level of security.
In the present invention, as defined in claim 10, the information card
contains
the password other than the information data, called the inherent data . The
data
processing terminal protects the information data by password, and further
protects
the inherent data by customized key. As a result, the inherent data is
protected
against extraction by double protection scheme.
In the invention, as defined in claim 1 l, the inherent data is read from the
host
and put into the data processing terminal, or is submitted from the external
source
into the data processing terminal. The read or submitted inherent data is
wholly or
partly checked against the inherent data that is contained in the information
card.
When these inherent data identify with one another, then the information card
is
possible to work as it is programmed. For example, it can function as a credit
card.
As a consequence, the information card system provides triple security, making
it
possible to eliminate forgery and illegal use.
In the present invention, as claimed in claim 12, the inherent data is
embedded
according to Steganography by the steps of converting the information data to
pure
5
AMENDED SHEET
CA 02345107 2001-03-22
20-11-2000 - US 009921663
binary code
a,
AMENDED SHEET
CA 02345107 2001-03-22
20-11-?000 US 0099216fi3
data, or converting the pure binary code data to canonical gray code data,
decomposing the pure binary code data or the canonical gray code data into bit
planes, and segmenting the bit planes into regions according to a complexity
measure,
and replacing complex region-forming data with the produced inherent data. As
a
result, the memory of the information card stores information data that has
the
inherent data embedded therein. In addition, the inherent data Is hidden so
that the
third parties are unaware of the presence of the inherent data..
In the present invention, as defined in claims 5 and 13 the inherent data to
be
embedded is subject to a conjugation operation. As a result, various files can
be
embedded.
In the present invention, as defined in claims 6 and 14, the memory of the
information card includes an IC chip. As a consequence, it is possible to
build an
information card, which serves as, what is called, either a memory card or an
IC card,
and a system of such an information card In this case, an inexpensive card
reader/writer can be provided as the data processing terminal.
In the present invention, as defined in claims 7 and 15, the information card
carries a photograph on the card surface thereof. The information data or the
inherent
data represents the photograph. When image data is output and displayed, then
such
data can be checked against the photograph This makes the information card
highly
secure.
BRIEF EXPLANATION OF THE DRAWINGS
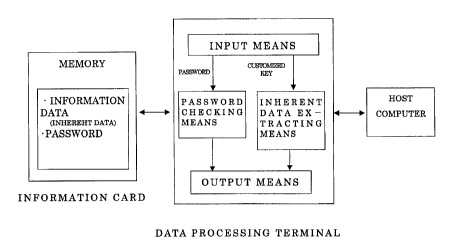
FIG. 1 is a block diagram, illustrating how an information card system
according to the present invention functions.
FIGS. 2(A) to 2(F) are simulative illustrations illustrative of a conjugation
operation according to the present invention.
FIG. 3 is a block diagram, showing an information card system according to
an embodiment of the present invention.
FIG. 4 is a block diagram, showing how the information card system
according to the embodiment is electrically constructed.
FIG. 5 is a block diagram, illustrating how an information card according to
6
AMENDED SHEET
CA 02345107 2001-03-22
20-11-?000 US 009921663
the embodiment is electrically constructed.
FIG. 6 is a flowchart, showing an embedding process (encoder program) in
one embodiment of the
6 x.
AMENDED SHEET
CA 02345107 2001-03-22
20-11-2000 US 009921663
information card system.
FIG. 7 is a flowchart, showing an authentication process (decoder program) in
one embodiment of the information card system.
DETAILED DESCRIPTION OF THE INVENTION
An information card system according to an embodiment of the present
invention will now be described FIG. 1 is a block diagram, showing the concept
of
the system according to the present invention. More specifically, the
information card
system includes an information card, a data processing terminal for exchanging
data
with the information card, and a host computer for exchanging data with the
data
processing terminal. The information card has a memory for storing data. The
memory contains information data and a password The information data has
inherent data embedded therein by a steganographic process. The data
processing
terminal has input means, output means, password checking means, and inherent
data extracting means.
According to the information card system, the data processing terminal can
read the information data by password checking. It can also extract the
inherent data
using a customized key. As a result, when the information card is used as a
credit
card, it is possible to completely eliminate the illegal use of the
information card by
any person other than the legitimate card owner. Further, it is also possible
to
completely eliminate illegal use of a forged information card.
Since the inherent data is embedded in the information data according to
Steganography (BPCS Steganography), it is possible to eliminate the card
forgery and
the inherent data extraction by unauthorized persons.
The BPCS-Steganography (Bit-Plane Complexity Segmentation
Steganography) is a process of replacing (embedding) a random pattern of image
data
with secret data, in view of the complexity (randomness) of a binary pattern
on a "bit
plane" that is obtained, e.g., by slicing the image data into bits. Whereas a
hiding
capacity of a conventional steganographic process is in the range of 5 to 10%,
the
BPCS-Steganography has a hiding capacity of about 50% or up to some 70% in
some
cases. Therefore, the BPCS-Steganography is capable of hiding with a very high
7
AMENDED SHEET
CA 02345107 2001-03-22
20-11-2000 US 009921663
hiding capacity. The BPCS-Steganography is based on the following
four basic ideas:
(1)Bit-plane decomposition is executed on a pure binary coded (PBC) image
data or a "canonical gray coded (CGC) image converted from the PBC image data
(2) A bit plane is segmented according to the "complexity measure" of a
binary pattern, and a complex pattern (random pattern) is replaced by the
secret data
(i.e., the secret data is hidden) . The secret data thus hidden is completely
unnoticeable for human eyes.
(3) Files to be embedded are subject to a "conjugation operation", so that any
ZO types of files can be embedded.
{4) The algorithm of BPCS-Steganography (encoder and decoder programs)
can be customized differently to different users. The customized BPCS-
Steganography algorithm establishes the security of embedded information with
the
use of a "customized key" that is different from the password.
The most advantageous feature of the BPCS Steganography is that it can hide
with a large hiding capacity. This feature is applicable to the following:
(A)Others do not become aware of that some secret data is embedded. It is also
impossible to see any difference between a secret data-embedded image and a
non-
embedded image.
(B) Even if someone suspects that secret data might be embedded, he is unable
to
know, without a customized key, where and how the secret data can be
extracted.
The information card system according to the present invention employs a
steganographic card which has an IC memory mounted on a conventional card
(with a
photograph of the card owner thereon) . The IC memory has a storage capacity
of 8
KB or more. The stegariographic card is used as follows:
(1) The IC memory stores the data of the photograph of the card owner.
In order to read this data, the password for the card must be submitted to a
card
reader.
(2) The data of the photograph of the card owner contains personal data
regarding the card owner (e.g., fingerprints, a personal history, data of
relatives, data
8
AMENDED SHEET
CA 02345107 2001-03-22
20-11-2000 US 009921663
of hobbies, etc.). The personal data is embedded according to the BPCS-
Steganography.
(3) In order to extract the embedded information and display the extracted
information on a display unit, it is necessary to submit a correct customized
key. The
customized key is defined as follows:
(a) Only the card owner knows a portion of the customized key (a private
key).
(b) The remaining portion of the customized key (a company key) is
strictly and confidentially managed only by the card company. Only when the
card
company receives an on-line request for the company key from a facility (shop)
where
the card is used, the card company encrypts the company key and sends the
encrypted
company key to the facility. In order to recover the embedded information, the
private and company keys must be combined together.
(c)The card owner is unaware of the company customized key, while the card
company is unaware of the private key.
In the information card system according to the present invention, there are
four levels of security confirmation as to both a legitimate card owner and a
legitimate card. Each security confirmation level is as follows:
(Level 1 ) Visual checking of the card user against the photograph on the card
(in order to prevent stolen or found cards from being illegally used)
(Level 2) Requesting the card user to submit the "password", and visually
checking the photograph data displayed on the display unit against the
photograph on
the card (in order to prevent photographs on cards from being forged)
(bevel 3) Requesting the card user to submit the "private key", combining the
private key with the "company key" that is sent on-line from the card company,
and
confirming whether the personal data embedded according to the BPCS-
Steganography can be extracted (in order to prevent cards from being forged as
a
whole).
(Level 4) Checking of the card user against the legitimate card owner based on
the embedded personal data (e.g., fingerprints) {in order to prevent the
legitimate card
9
AMENDED SHEET
CA 02345107 2001-03-22
20-11-?_000 US 009921663
owner from renting the card to others)
Hiding and extraction of information according to the BPCS-Steganography
will be described below.
On the bit planes of a natural image, a noise-like area does not appreciably
affect the visual appearance to the viewer even if the data therein is
replaced with
other noise-like data. This phenomenon allows us to replace noise-like areas
in a
natural image with secret data. Since a criterion to determine whether the
noise-like
areas varies depending upon the natural image, it is necessary to establish a
suitable
threshold value for each natural image data.
When a binary image is analyzed by the local area of 2'° x 2°'
(normally m =
3), and some area has a complexity measure value a which satisfies:
a~<a
(where am represents a threshold), then the area is decided as an area for
secret data
hiding or embedding.
In order to embed a secret data file in a natural image, the secret data file
may be first divided into small file segments with 2~ x 2'" size (i.e., 2m x
2'° pixel
size), and then those small file segments may be embedded successively in
noise-like
areas of the same size in the image. However, not all small file segments have
a
complexity value greater than a~, The small file segments having less
complexity
value than the threshold a~ are converted to more complex segments by a
conjugation operation described below. Such a process makes it possible to
embed
any secret files in images. However, in order to recover all parts of the
embedded
secret files, it is necessary to save the "conjugation map" which indicates
the
conjugated segment areas.
Now, assume that a white pixel has a value of 0, but a black pixel has a
value of 1. P is assumed as an arbitrary binary image having white background.
W is
defined as a pattern where all pixels are white. B is taken as a pattern where
all
pixels are black. We is viewed as a checkerboard pattern where the leftmost
pixel in
the uppermost pixel row is white. Bc is taken as a checkerboard pattern where
the
leftmost pixel in the uppermost pixel row is black. (See FIGS 2a - 2fJ. The
binary
image P is regarded as an image with a foreground area having the pattern B
and a
AMENDED SHEET
CA 02345107 2001-03-22
20-11-2000 US 009921663
background area having the pattern W. On the basis of the above assumption,
the
"conjugated image" P* of the image P is defined as follows:
P* = P~Wc
where ~ represents an exclusive-OR operation on each pixel.
A process for producing a conjugated image is referred to as a conjugation
operation. The conjugated image P* is characterized as follows:
(1) The foreground area is identical in shape to the foreground area of the
image P.
(2) The foreground area has the checkerboard pattern Bc.
(3) The background area has the checkerboard pattern Wc.
The image P and the conjugated image P* have one-to-one correspondence.
The image P and the conjugated image P* satisfy the following properties:
(a) ~*)* - P
(b) P* # P
(c) a(P*) = 1 - a(P)
where "a(P)" represents complexity a of the image P.
The most important of the properties (a) through (c) is the property (c) . The
property (c) indicates that a simple image can be converted to a complex image
or
vise versa without losing its shape information. It is also possible to
restore the
original image from the converted image because of the property (a)
The BPCS-Steganography proposed by the present application includes the
following five steps:
Step 1:
A natural image of 2M x 2M, N bitslpixel is converted to an N-bit gray code
image.
This conversion step is based on the study by Eiji Kawaguchi et al. of binary
images
produced by bit-plane decomposition and their complexity.
Step 2
The gray code image generated in Step 1 is segmented into N binary images by
bit-plane decomposition.
Step 3
Z1
AMENDED SHEET
CA 02345107 2001-03-22
20-11-?000 US 009921663
Each of the N binary images is divided into partial images each having a size
of
2m x 2m. The partial images are represented by P;; i = l, 2, ~~~, 4M'~ The nth
bit-plane
image can be expressed by:
{p~°~ p2°~ ...~ p4aM.m)
Similarly, the nth "conjugation map" can be expressed as follows:
Cu {Q1°~ K2°~ ~..~ Qt~°M-m~
where each of Q,n, Q2°, -~~, Q4°M-m has a value of "0" or "i."
The value of "1" represents
an area where the conjugation operation
is applied The value of "0" represents an area where the conjugation operation
is not
applied.
Embedded data {expressed by E) includes a header, a body, and a pad. The
header
indicates a data size of the body. The body represents secret data (e.g., a
secret image)
which is embedded. The pad serves to shape the embedded data into the size of
2mx2'°.
E~ (j=1,2,-~~,~ represents a partial bit series ofthe embedded dataE whose
size is of 2°'x2°'
bits. When the partial bit series E~ is corresponded to a square area of 2mx2m
bit by bit,
based on the principle of raster scanning, then a binary image of
2°'x2°' can be generated.
The generated binary image is represented by makeS(E~).
With the threshold ar,., used, an embedding algorithm can be expressed below.
Each Q in the nth conjugation map C° is initialized to "0".
for (n--N, j=l;nzl&&j :T;n--) {
for (i=l;is4M'°'&&j<J;i++) {
if (a(P;°) z a.~ {
if (a(makeS(E~))za.LH)
P ° = makeS(E~)
else {
12
AMENDED SHEET
CA 02345107 2001-03-22
2C-11-2000 US 009921663
P,° = makeS(E~)*
Q 0 ~ t1 I tt
l
Since low-order bits are less significant on the image, the embedding process
is
carried out on bits successively from the least significant bit. When the
binary image
makes (E~) in an area is simple, i.e., when the complexity of the area is
smaller than
the threshold, then the conjugation operation is effected on the binary image
makes
(E~). In this case, Q~ in the conjugation map is set to "1."
Step 4
The N-bit gray code image is reconstructed from the N binary images where the
secret data is embedded.
Step 5
After the N bit pwe binary code is recovered from the N-bit gray code image in
Step 4, the image data file having the secret data embedded therein is
obtained.
The secret data embedded in an image may be recovered by the above
algorithm being reversed. In order to recover the secret data from the
embedded
image, it is necessary to know the threshold a.,.H and the conjugation map.
Next, an IC card system according to an embodiment of the present invention
will
be described with reference to FIGS. 3 to 7. FIG. 3 is a block diagram,
showing the
concept of the IC card system. FIG. 4 is a block diagram, illustrating a
schematic
structure of an IC card and an IC card reader/writer in the ID card system.
FIG. 5 is a
block diagram, illustrating another structural example of an IC card. FIGS. 6
and 7 are
flowcharts, showing programs to be executed in the 117 card system.
As shown in the above Figures, an IC card 100 as an information card according
to the present invention is capable of exchanging data with an IC card
reader/writer (data
processing terminal) 200. The IC card reader/writer 200 can exchange data on-
line with,
e.g., a host computer 300 at a credit card company. The IC card reader/writer
200 may
be equipped with a display unit 210 (display means) and an input means 220
(such as a
mouse and a keyboard).
13
AMENDED SHEET
CA 02345107 2001-03-22
20-11-2000 US 009921663
As shown in FIG. 4, the IC card reader/writer 200 includes a CPU to execute
arithmetic operation processing, a data memory for storing data, a program
memory for
storing programs, a buffer memory, the keyboard for entering data, a display
unit for
displaying results of the arithmetic operation processing, an interface for
controlling data
exchanged with the IC card, and a power supply.
The IC card readerlwriter 200 is able to read data from and write data in the
IC card
100. The CPU executes encrypting and decrypting processes and an
authentication
process. The program memory stores application programs.
The IC card 100 has an interface, a CPU, a program memory, and a data memory.
The power supply of the IC card reader/writer 200 supplies electric power to
the IC card
100.
The program memories and the data memories are nonvolatile types. These
nonvolatile memories include EEPROMs that is electrically erasable, or static
RAMS that
is backed up by a battery.
FIG. 5 shows another structural example of an IC card. More specifically, the
IC
card includes a CPU, a PROM for storing data, and a connector for connection
to an
external device (an IC card reader/writer). The CPU includes a control unit,
an arithmetic
unit, a ROM, and a RAM.
The IC card includes an IC chip that is mounted on a plastic plate member. The
plastic plate member carries the name of the card owner, the card number, and
an
expiration date, all of which are embossed on a surface thereof.
The IC chip stores, in a memory thereof having a storage capacity of 8 KB or
more,
password data, digital image data of the card owner's photograph, or digital
acoustic data
(information data). The information data contains personal data of the card
owner (e.g.,
fingerprints), a photograph of the card owner, and part of the personal data
(digital
signature image data), all of which are embedded according to the BPCS-
Steganography.
The iC card system enables both visual verification of the card user and
mechanical
authentication of the IC card at one time. People cannot perceive any secret
present in the
IC card. Even if someone suspects some secret data as being present in the IC
card, they
cannot extract such an embedded data from the IC card. The IC card may hide
digital data
14
AMENDED SHEET
CA 02345107 2001-03-22
' 20-11-2000 . US 009921663
or authentication data. The IC card system can properly readout such hidden
authentication data from the IC card, and properly can embed the same data
therein.
FIG. b shows a process (encoder program) in which data is stored in the IC
card
according to Steganography. Initially, the card owner's photograph data
(including indexed
photograph data) is produced in order to be written to the IC card memory (8KB
or more).
The produced photograph data is saved as a bit map file. In this case, the
photograph data
is set in size to be some 75% of the IC card memory. In addition, the above
photograph
data is produced from the photograph data of the IC card owner.
Then, personal authentication data (text data) is produced and then saved in
order
to be embedded in the photograph data. The text data is set in size to occupy
some 10%
of the photograph data. Both of the photograph data and the authentication
data are
selected and displayed. Then, the photograph data for the IC card is converted
to pure
binary code (PBC) data. The photograph data thus converted to the PBC data is
then
converted to canonical gray code (CGC) data.
Next, the photograph data thus converted to the CGC data is decomposed into
bit
planes (i.e., into N binary images). The personal authentication data (text
data) is
embedded in the bit-plane-decomposed photograph data. In this case, the
personal
authentication data is embedded according to the above algorithm, using a
customized key
(which consists of, e.g., 24 digits of data).
The photograph data having the embedded text data therein is then re-converted
to
PBC data. Further, the photograph data for use in the IC card is produced and
then saved.
Now, the IC card is inserted into the IC card reader/writer, and then any one
of the
photograph data is selected. Then, the selected photograph data is transferred
and saved
in the IC card memory. In order to protect the saved photograph data, a
password is set
and saved in the IC card memory. The password consists of, e.g., 4 digits of
data.
The IC card (for use as, e. g., an identification card) is now completed.
Thereafter,
a photograph of the card owner is printed out on the plastic plate surface of
the IC card.
Next, the authentication of the IC card will be described with reference to
FIG. 7.
FTG. 7 shows part of a decoder program.
15
AMENDED SHEET
CA 02345107 2001-03-22
20-11-2000 US 009921663
Initially, the IC card is inserted into the IC card reader/writer. Then, the
IC card
reader/writer starts an initializing process in order to execute an
authentication flow. Next,
a password is submitted from a keyboard into the IC card reader/writer. The IC
card
reader/writer compares the submitted password with the stored password in the
memory
on the IC card. When the submitted password identifies with the stored
password, then the
IC card reader/writer reads the photograph data (information data) stored in
the IC
cardmemory, and displays it on the display unit. When the displayed photograph
data
indicates a photograph of the card owner, then the displayed photograph is
visually
checked against the photograph printed on the IC card surface and against the
card user
himself.
Then, a customized key is submitted. The customized key is used to embed the
personal authentication data. The customized key is known only to the
legitimate card
owner. The customized key is not stored in the IC card memory. The customized
key
works as parameters to control over embedding and extracting of the inherent
data.. The
inherent data is extracted from the information data only when the customized
key
submitted to extract the inherent data identifies with parameters that are
used for
embedding.
More specifically, the photograph data (information data) read from the IC
card
-memory is converted to pure binary code (PBC) data, and then the photograph
data thus
converted to the PBC data is converted to canonical gray code (CGC) data. The
CGC data
of the photograph is decomposed into bit-planes. At this time, the personal
authentication
data is extracted from the photograph data already decomposed into the bit-
planes, using
the customized key. In this manner, the embedded personal authentication data
(text data)
is extracted from the photograph data, and is then displayed
When the submitted password does not identify with the password in the IC card
memory, then no photograph data can be read from the IC card memory. Further,
when
the submitted customized key does not identify with the card owners customized
key, then
the personal authentication data cannot be extracted from the photograph data.
In case
such a password or customized key is incorrect, then the IC card is rejected
or confiscated
by the IC card reader/writer as being forged or illegally used.
16
AMENDED SHEET
CA 02345107 2001-03-22
20-11-000 US 009921663
In conclusion, the IC card system is designed to execute password checking
after
visually checking is made as to whether a card user is an authorized card
owner, and then
to allow the photograph data to be read from the IC card memory and the
photograph
image to be displayed on the basis of the photograph data. The displayed
photograph
image is compared with the photograph printed on the IC card, thereby checking
the
legitimacy of the IC card Then, the personal authentication data is extracted
from the
photograph data using a customized key. The extracted data is then displayed.
The
displayed personal data is compared with the card user's personal data,
thereby confirming
that the presented IC card is a legitimate card.
As evidencedby the above, apparent image data contains other image data,
acoustic
data., and text data, all of which are present in a visually imperceptible
manner.
These embedded data are checked to confirm that the card user and the card are
both
legitimate.
Pursuant to the present invention, since the third party cannot recognize the
presence of the inherent data, or rather the secret data, the information card
with a high
level of security is achievable.
According to the present invention, the inherent data is possible to verify
the
legitimacy of the information card. It is possible to hide the presence of the
legitimacy
data and the card owner data.
According to the present invention, the password enables protection of the
information data, with a consequential increase in security of the card.
According to the present invention, the customized key can protect the
inherent
data.
According to the present invention, the information data can be protected
against
retrieval by password checking.
According to the present invention, unauthorized persons can be prevented from
extracting the inherent data, thereby providing a high level of security.
Pursuant to the present invention, the information card can be prevented from
being
illegally used by means of the password and customized key.
Pursuant to the present invention, it is possible to provide triple security,
and thus
17
AMENDED SHEET
CA 02345107 2001-03-22
2~-11-'?000 US 009921663
to eliminate forgery and illegal use of the information card.
According to the present invention, the inherent data is embedded according to
stegnanography, and is thus difficult to decrypt. As a result, the inherent
data can securely
be hidden.
According to the present invention, various files can be embedded in the
inherent
data.
According to the present invention, it is possible to construct an information
card,
which works as a memory card or an IC card, and a system of such an
information card.
In addition, an inexpensive card reader/writer can be provided.
Finally, pursuant to the present invention, the image data can be checked
against
the photograph. The photograph can be prevented from being forged
18
AMENDED SHEET