Note: Descriptions are shown in the official language in which they were submitted.
CA 02347865 2001-04-24
WO OOI27156 PCT/SE99/01717
-1-
METHOD OF AUTHENTICATING A MOBILE STATION HANDING-OFF
FROM AN ANCHOR EXCHANGE TO A SERVING EXCHANGE
BACKGROUND OF THE INVENTION
Technical Field of the Invention
This invention relates to a method of authenticating a mobile station, and
more
particularly to a method of authenticating a mobile station handing-off from
an anchor
IO exchange to a serving exchange.
Description of Related Art
Ever since their introduction on the market, mobile stations have changed the
way people communicate. Now, it is possible to reach a person almost anywhere,
using only one number. The number is no longer linked to a location, but is
rather
linked to a mobile station that communicates through a radio interface with a
cellular
network. So wherever the mobile station is located, i.e. within the cellular
network
coverage, it can originate or receive a call by means of the radio interface.
For
originating a call through the cellular network, the mobile station has to
identify itself
by providing its Mobile Identification Number (MIN) and Electronic Serial
Number
(ESN). The MIN/ESN allows the cellular network to recognize which mobile
station
is calling, so to charge fees incurred for the call appropriately.
A problem that has emerged with the ever-increasing popularity of mobile
stations is the cloning. The cloning is performed by "listening" to the radio
interface
to find a MIN/ESI\. and programming a second mobile station with the same
MIN/ESN. By doing so, the fees incurred for calls originated by the second
mobile
station are charged to the first mobile station. This method of fraud has
caused
important financial damages to cellular network providers and to owners of
mobile
stations.
To solve that problem, the security of cellular networks has been improved
with authentication procedures to which the mobile stations must participate.
In D-
AMPS networks, different authentication procedures have been developed: Global
CA 02347865 2001-04-24
WO 00/27156 PCT/SE99/01717
-2-
Challenge, Unique Challenge, Shared Secret Data Update, and Count Update.
These
authentication procedures rely on using an algorithm called CAVE, and in an '
exchange of parameters between the mobile station and an authentication
center. The
authentication center stores a set of data for each mobile station including
their MIN
and ESN, along with an A-key and a Shared Secret Data (SSD) also called
authentication data. The set of data is used as input parameters to the CAVE
algorithm
to verify authenticity of the mobile station.
More precisely, the Global Challenge procedure is performed on digital or
analog control channel at system access, and involves validation of the
authentication
data received from the mobile station.
The Unique Challenge is a procedure that can be performed on either control
or voice channel, and involves validation of the authentication data received
from the
mobile station.
The Shared Secret Data Update procedure is used to verify the mobile station's
A-key. The Shared Secret Data update procedure may be prompted by
administrative
procedures at the authentication center, expiration of an authentication time
interval
at the authentication center, or the detection of a possible fraudulent
situation. The
CAVE algorithm, the set of parameters and random values are used to perform
the
updating of the SSD. If the new value of SSD is the same after verification at
both
ends, then the mobile station has successfully authenticated and is still
allowed
service. The Shared Secret Data update involves sending a random number to the
mobile station to generate a new Shared Secret Data value based on the mobile
station's information and the random number received. The Shared Secret Data
Update
is usually followed by a Unique Challenge procedure to validate the new Shared
Secret Data.
Finally, the COUNT Update procedure is used to detect fully cloned mobile
stations, i.e. mobile stations that have the same A-key and Shared Secret Data
as their
legitimate counterpart. The COUNT Update procedure relies on incrementing
Count
value in the mobile station and at the authentication center after each
successful
authentication procedure. A consistency check is performed at the
authentication
center of the value of both counters, and any inconsistency may indicate a
possible
fraud or a fraudulent mobile station.
CA 02347865 2001-04-24
W~ 00/27156 PCT/SE99/0171'7
-3-
However, it has been noticed that when an inter-system hand-off occurs during
one of the authentication procedures, the tatter is not completed. The non-
completion
of the authentication procedure either results in allowing a call that may be
fraudulent,
or barring a call of a legitimate mobile station. Therefore, for mobile
station users,
S non-completion of authentication procedure is not desirable.
In order to overcome the disadvantage of existing solutions, it would be
advantageous to have a method which would allow completion of authentication
procedure during inter-system hand-off.
SUMMARY OF THE INVENTION
The present invention provides a method to allow completion ofauthentication
procedure during inter-system hand-off.
In one aspect, the present invention is a method of authenticating with an
authentication center a mobile station handing off from an anchor exchange to
a
serving exchange. The method sends authenticating parameters for the mobile
station
from the authentication center to the anchor exchange. The mobile station is
asked to
authenticate with the anchor exchange. While authenticating, the mobile
station hands-
off from the anchor exchange to the serving exchange. The authenticating
parameters
are forwarded from the anchor exchange to the serving exchange, and the mobile
station is asked to authenticate with the serving exchange. The serving
exchange
receives the authenticating results from the mobile station, and sends them to
the
authentication center.
In another aspect, the present invention is a method of authenticating with an
authentication center a mobile station. The method has steps of asking the
mobile
station to authenticate with a first exchange, and detecting hand-off of the
mobile
station from the first exchange to a second exchange. The method then forwards
authenticating parameters from the first exchange to the second exchange, and
asks the
mobile station to authenticate' with the second exchange. The second exchange
receives the authenticating results from the mobile station and sends the
authenticating
results to the authentication center.
CA 02347865 2001-04-24
- WO 00/27156 PC'I'/SE99/01717
-4-
BRIEF DESCRIPTION OF THE DRAWINGS
The invention will be better understood and its numerous objects and
advantages will become more apparent to those skilled in the art by reference
to the
following drawings, in conjunction with the accompanying specification, in
which:
S FIGURE I is a schematic diagram of a cellular telecommunications network;
FIGURE 2 is a signal flow diagram of an authentication procedure in
accordance with a first embodiment of the present invention;
FIGURE 3 is a signal flow diagram of an authentication procedure in
accordance with a second embodiment of the present invention; and
FIGURE 4 is a flowchart of a method in accordance with the -present
invention.
DETAILED DESCRIPTION OF EMBODIMENTS
The present invention relates to allowing completion of an authentication
1 S procedure in situations o.f inter-system hand-off. For doing so, the
invention provides
a new failure indication to identify that the authentication could not be
completed due
to an inter-system hand off. The method of the present invention also provides
forwarding messages so as to order completion of the authentication procedure
in the
new serving system.
Reference is now made to FIGURE 1 wherein there is shown a schematic
diagram of a cellular network 10. In the cellular network 10, a plurality of
switches,
also known as Mobile Switching Center (MSC) 12 or exchanges, are used to route
calls to and receive calls from mobile stations 16. The MSC 12 are sometimes
co-
located with a Visited Location Register (VLR) 13 such as shown on the FIGURE
but
may also consist of non co-located nodes. The mobile stations 16 communicate
with
nearly proximate base stations 14 through a radio interface 22. As known in
the art,
several base stations 14 can communicate with one MSC 12. Each base station
communicates with the MSC 12 through a pair of signaling and voice links 24.
To
allow seamless sen~ice to a mobile station 16 that travels from a base station
14
serviced by a first MSC 12A, called Anchor-MSC, to a base station 14 serviced
by a
second MSC I 2S, also called a Serving MSC, a pair of voice and signaling
links 26
connect the first and second MSCs 12.
CA 02347865 2001-04-24
WO 00/27156 PC'T/SE99/01717
-5-
The mobile stations 16 may travel within the cellular network and
consecutively communicate with different base stations 14. More particularly,
when
a mobile station 16 travels from an area that is serviced by a first base
station 14 to an
area serviced by another base station, the operation of transferring service
from the
first base station to the second base station is called a hand-off. When the
mobile
station 16 hands-off from a base station 14 linked to a first MSC 12A to a
base station
linked to a second MSC 12S, it then consists of an inter-system hand-off.
In the cellular network 10, a Home Location Register (HLR) 18 keeps
information on subscribers such as location and services subscribed to. The
HLR 18
may consist of a stand-alone HLR, or of a co-located Service Control Point
(SCP) as
shown on the FIGURE. The HLR 18 communicates with the VLRs 13 through a
signaling link 28. While the HLR 18 stores information for all mobile stations
16
subscribed to the cellular network 10, the VLRs 13 in turn store certain
information
on mobile stations 16 communicating through their co-operating MSC 12.
I S The cellular network 10 also has an authentication center 20. The
authentication center communicates with the HLR 18 through a signaling link
30. The
authentication center keeps information on the mobile stations 16 such as
Shared
Secret Data (SSD).
Referring now to FIGURE 2, there is shown a signal flow diagram of an
authentication procedure in accordance with a first embodiment of the present
invention. To initiate the authentication procedure, the authentication center
20 sends
either a Shared Secret Data (SSD) Update message or a Unique Challenge Order
message 40 to the HLR 18. The S SD Update message and the Unique Challenge
Order
message 40 are well known in ANSI-41 standard, which is incorporated by
reference
herein. The HLR 18 forwards the SSD update message or unique challenge order
message 40 to the VLR 13 of the serving system, which in turn forwards it to
its
associated MSC 12. The MSC I2 acknowledges receipt of the SSD update message
of unique challenge order message 40 by an appropriate return message such as
an
authdir message 42, that is sent to the AC 20 through the VLR 13 and HLR 18.
The serving MSC 12 initiates authentication with the mobile station 16 by
sending an SSD update message or unique challenge message 44 to the latter
containing authenticating parameters. The authenticating parameters may
include an
CA 02347865 2001-04-24
WO 00127156 PCT/SE99/01717
-6-
authentication algorithm version and a shared secret data, or an
authentication
response unique challenge and a random variable unique challenge. The
authentication
procedure takes place between the mobile station 16 and the AC 20 as known in
the
art, and as described in standards such as the ANSI-41, which is incorporated
by
reference herein.
During the authentication procedure, the mobile station hands-off (step 46)
from the serving MSC 12, which becomes an anchor-MSC (A-MSC), to a new serving
MSC (S-MSC) 12. Then, the A-MSC 12 forwards the authenticating parameters to
the
S-MSC 12 in, for example, a Facilities Directive (FACDIR) message 48. In the
event
that the S-MSC 12 does not support authentication, it returns a FACDIR return
result
message SO indicating so to the A-MSC. If the S-MSC is capable of supporting
authentication, it asks the mobile station 16 to authenticate in a manner
known in the
art. When the authentication is completed between the S-MSC and the MS 16, the
S-
MSC receives authenticating results from the mobile station. The
authenticating results
1 S may include a shared secret data update report or a unique challenge
report. The
authenticating results are sent to the A-MSC in a MSONCH message 52. The A-MSC
forwards the outcome of the authentication, or an indication of the incapacity
of the
S-MSC to support authentication, in an ASREPORT message 54 to the AC 20
through
the A-MSC, A-VLR and HLR 18.
Referring now to FIGURE 3, there is shown a signal flow diagram of an
authentication procedure in accordance with a second embodiment of the present
invention. In that second embodiment, the A-MSC informs the AC20 of the hand-
off
of the mobile station 16, and it is the AC 20 that instructs the A-MSC to
forward the
authentication parameters to the S-MSC to perform the authentication with the
mobile
station. In that second embodiment, the authentication with the A-MSC, up
until the
mobile station 16 hands-off to the S-MSC, is the same as for the first
embodiment.
When the mobile station hands-off to the S-MSC, the A-MSC detects the hand-
off,
and informs the AC 20 by means of an Authentication Status Report (ASREPORT)
message 60 of its incapability to complete the authentication due to a hand-
off. Then,
the AC 20 instructs the A-MSC to forward the authenticating parameters to the
S-MSC
in an order message 62. The A-MSC executes the order and sends the
authenticating
parameters to the S-MSC in an Authentication Directive Forward (AUTHDIRFWD)
CA 02347865 2001-04-24
WO, 00/Z7156 PCT/SE99/01717
-7_
message 64. The S-MSC performs the authentication with the mobile station, and
sends an AUTHDIRFWD return message 66 to the A-MSC that contains the
authenticating results. Then, as in the first embodiment, the A-MSC returns
the
authenticating results to the AC with the ASREPORT message 54.
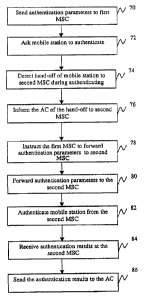
S Referring now to FIGURE 4, there is shown a flowchart of a method in
accordance with the present invention. That method starts in step 70, where
the AC 20
sends the authentication parameters to the A-MSC. Then, the A-MSC asks the
mobile
station 16 in step 72 to authenticate. While the mobile station 16 is
authenticating, the
A-MSC detects a hand-off of the mobile station 16 in step 74. The A-MSC
informs
the AC 20 in step 76 of the hand-off of the mobile station to the S-MSC. The
AC 20
instructs in step 78 the A-MSC to forward the 0 authentication parameters to
the
S-MSC. Then, the A-MSC sends the authentication parameters to the S-MSC in
step
80. The S-MSC asks the mobile station 16 to authenticate in step 82 and
performs the
authentication therewith. The S-MSC receives the authentication results from
the
mobile station in step 84, and sends these results to the AC 20 in step 86,
thereby
allowing completion of the authentication during an inter-system hand-off. It
is thus
believed that the operation and construction of the present invention will be
apparent
from the foregoing description. While the method and system shown and
described have been characterized as being preferred, it will be readily
apparent that
, various changes and modifications could be made therein without departing
from the
spirit and scope of the invention as defined in the following claims.