Note: Descriptions are shown in the official language in which they were submitted.
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
Apparatus and method for performing and controlling encryption/decryption for
data to be transmitted on local area network.
The present invention generally relates to a technique for performing
compression,
encryption and transmission, and reception, decryption and decompression,
respectively, of data communication packages on an area network.
The most commonly applied technique for performing transmissions on a network
such as LAN (local area network) or WAN (wide area network} involves
performing
compression/decompression, encode/decode and transmission/reception of data
communication packages to establish a fast communication between stations in
the
LAN. Techniques are disclosed in following patents and published patent
applications
DE 3 606 869, EP 0 582 907, US 4 701 745, US 4 996 690, US 5 003 307, US 5 016
009, US 5 126 739, US 5 146 221, US 5 414 425, US 5 463 390, US 5 506 580, US
5
532 694, US 4 586 027, US 4 872 009, US 4 701 745 and US 4 988 998 describing
various aspects of compression/decompression and transmission from one unit to
another unit. Reference is made to the above patents and published patent
applications, and the above US patents are hereby incorporated in the present
specification by reference.
According to present technology it appears that no technique is currently
available
ensuring a secure communication in combination with a fast communication. To
secure data communication packages one must encrypt the data communication
packages according to a between stations known encryption key or keys. This is
a
time consuming process and therefor slows down and in particular delays the
transmission between two or more stations and consequently contradicts the
combination of a secure and fast communication. Furthermore, according to
present
technology operations such as compression, encryption and transmission, and
reception, decryption and decompression are performed consecutively and which
further slows the transmissions on the LAN as the data packages increase.
Since
computer networking becomes a more and more significant part of today's
computer
applications and communication on networks becomes everyday practise, it is
rendered necessary to develop an apparatus and method for performing secure
transmissions and increased transmission rates between stations in a computer
network.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
2
An object of the present invention is to provide a novel apparatus and method
for
securing data communication packages by encryption and simultaneously ensuring
a
fast communication between stations in a network such as LAN or WAN.
A particular advantage of the present invention is the significant reduction
or
substantially elimination of delays in transmitting data communication
packages
through a network by continuously insuring data is presented to the LAN or WAN
in an
encrypted state.
A particular feature of the present invention relates to the fact that the
apparatus
according to the present invention may be produced fully or partly in a
process
compatible with the production of integrated electronic circuits using any
appropriate
circuit technology involving VLSI, LSI, ASIC, FPGA, PLD production techniques
or any
combinations thereof.
The above object, the above advantage and the above feature together with
numerous
other objects, advantages and features which will be evident from the below
detailed
description of a preferred embodiment of the present invention is according to
a first
aspect of the present invention obtained by a communication controller for
performing
data encryption and data decryption of data communication packages to be
transferred in a network such as a LAN (local area network) or WAN (wide area
network), the data communication package containing a first section of non-
encrypted
data and a second section containing encrypted data, and comprising a session
key
LUT unit and a transmission and encryption section comprising:
(a) a data read transmission control unit (102) connected to a system bus of a
host
system and receiving input data therefrom and communicating with said
session key LUT (186), said session key LUT (186) providing a transmission
encryption key for said data communication package,
(b) a data compressing unit (118) providing compression of a part of said
input
data thereby producing a compressed part of said input data contained in said
second section of said data communication package,
(c) a data encryption unit (126) providing an encryption of said second
section of
said data communication package according to said transmission encryption
key transferred from said session key LUT (186) to said data encryption unit
(126),
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
3
(d) an integrity check value calculation unit (122) constituting a first
series
configuration from said data compression unit (118) intercommunicating
through said integrity check value calculation unit (122) to said data
encryption
unit (126),
(e) a network transmission controller (134) providing said data communication
package through a connection to said network, supplying said input data to
said network in a transmission rate determined by said network transmission
controller (134) and said network, and
(f) a first switch means (108) enabling switching between two modes of
operation,
a first mode of operation providing bypassing or disabling of said first
series
configuration and enabling communication between said data read
transmission control unit (102) and said network transmission controller (134)
for transferring said input data directly hereto and a second mode of
operation
enabling communication between said data read transmission control unit (102)
through said first series configuration to said network transmission
controller
( 134),
said communication controller further comprising a receiving and decrypting
section
comprising:
(g) a LAN receiving controller (140) providing a connection to said network
and
receiving a received data communication package from said network,
(h) a data receiving control unit (148) receiving said received data
communication
package through communication with said network receiving controller (140),
and communicating with said session key LUT (186), said session key LUT
(186) providing a reception encryption key for said received data
communication package,
(i) a data decompression unit (172) providing decompression of said second
section of said received data communication package,
Q) a data decryption unit (164) providing a decryption of said second section
of
said received data communication package according to a reception encryption
key transferred from said session key LUT (186} to said data decryption unit
(164),
(k) an integrity check value verification unit (168) receiving said received
data
communication package from said data decryption unit (164}, and constituting
a second series configuration from said data decryption unit (164)
intercommunicating through said integrity check value verification unit (166)
to
said data decompression unit (172}, said integrity check value verification
unit
SUBSTITUTE SHEET (RULE 26~
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
4
(166) transferring said second section of said received data communication
package to said data decompression unit (172),
(I) a data write unit (180) connected to said system bus of said host system,
supplying said system bus with said received data communication package,
and
(m) a second switch means (154) enabling switching between two modes of
operation, a third mode of operation providing bypassing or disabling of said
second series configuration and enabling communication between said data
receiving control unit (148) and said data write unit (180) for transferring
said
first section of said received data communication package directly hereto, and
a fourth mode of operation enabling communication between said data
receiving control unit (148) through said second series configuration to said
data write unit (180).
By incorporating several of the functions of the communication controller,
according to
the first aspect of the present invention, in a single electronic circuit the
time delay
from one unit to the next is considerable reduced compared to time delays
between
discrete electronic components.
The term unit is to be understood as a generic term including all equivalent
elements,
blocks and sections etc. The term unit may comprise a single entity or may
comprise a
multiple of entities into one self-contained and defined unit, element, block
or section.
in the communication controller according to the first aspect of the present
invention,
the transmission and encryption section further comprises a transmission FIFO
(first in
first out storage means) constituting an input section of the network
transmission
controller. Furthermore in the communication controller according to the first
aspect of
the present invention, the receiving and decrypting section further comprises
a write
FIFO receiving the received data communication package from the data receiving
control unit in the third mode of operation, receiving the received data
communication
package from the data decompression unit in said fourth mode of operation and
transferring the received data communication package through a connection to
the
data write unit, and a receiving FIFO receiving the received data
communication
package from the network reception control and transferring the data
communication
package through a connection to the data receiving control unit.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
Since the communication controller, according to the first aspect of the
present
invention, comprises storage means for transmission as well as reception of
data
communication packages, full compatibility is achieved between a host system
and the
network. Especially differences in reading rates between stations and network
5 transmission rates are compensated for. The host system may operate at one
frequency, while the network may operate at another without overloading either
the
host system or the network. This relieves processing time available to the
host system,
since delivering a data communication package to the controller frees the host
system's central processing unit to perform other tasks than waiting for
completion of
transmission and therefor optimises the transmission performed on the network.
The communication controller, according to the first aspect of the present
invention, for
receiving and transmitting data communication packages on a network provides
interrupt routines for units included in the communication controller hereby
insuring a
continuous data transmission on a network. The communication controller,
having the
data compression unit and the data encryption unit adapted to be operated
substantially simultaneously and controlled by the network transmission
controller. The
network transmission controller furthermore controls the transmission FIFO so
as to
guarantee the continuous supply of bytes from the transmission FIFO to the
network
transmission controller. This ensures that the transmission is extraordinarily
fast.
Furthermore, since the communication controller preferably is implemented in
accordance with a technique for producing integrated electronic circuits, a
fast internal
control of the operation may be achieved. By operating data compression and
data
encryption substantially simultaneously instead of operating consecutively
considerably improves the transmission time and reduces the delay for
transmitting a
secure data communication package.
The communication controller, according to the first aspect of the present
invention,
having the data read transmission control adapted to monitor the compression
and
encryption of the part of the input data for determining, whether or not, the
part of the
input data exceeds the amount of data containable within said second section
of data
communication package. By continuously monitoring if the data communication
packages processed are within the package specifications of the network, any
redundant operations are eliminated, and thus the number of data communication
package transmitted on the network is reduced.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
6
The communication controller, according to the first aspect of the present
invention,
wherein the integrity check value calculation unit performs a subtraction,
division,
multiplication or preferably a summation of the data contained in the second
section of
the data communication package to be transmitted, and adds a first integrity
check
value to the second section of the data communication package. Additionally,
the
communication controller, according to the first aspect of the present
invention,
wherein the integrity check value verification unit performs a subtraction,
division,
multiplication or preferably a summation of the data contained in the second
section of
a received data communication package. Hereby obtaining a second integrity
check
value and comparing the second integrity check value with the first integrity
check
value contained in the second section of the data communication package. The
integrity check value calculation and verification ensures that no excessive
time is
spent on corrupted data communication packages at the receiving end of a
transmission, therefor, implementation of this calculation and verification
may reduce
unnecessary data communication package processing.
The communication controller, according to the first aspect of the present
invention,
wherein the data read transmission control unit comprises control means for
controlling the first switch means in the two modes of operations.
Furthermore,
wherein the data receiving control unit comprises control means far
controlling the
second switch means in the two modes of operations. These switching means
ensures
a fast recognition of the clear text and consequently bypassing or disabling
of the first
and second series configuration, respectively.
The communication controller, according to the first aspect of the present
invention,
wherein the data read transmission control unit further comprising a
connection to the
data encryption unit, for transferring the transmission encryption key
provided by the
session key LUT from the data read transmission control unit to the data
encryption
unit.
The communication controller, according to the first aspect of the present
invention,
wherein the session key LUT comprising encryption key information is updated
according to a key management protocol by the host system. Encryption key
administration is entirely managed by the host system thus delegating this
cumbersome task to the host rather than a local processing unit on the
communication
controller. In an alternative embodiment of the present invention, the
encryption key or
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
7
keys may be updated through the data read transmission control of the
communication
controller. Further alternatively the encryption key or keys may be generated
locally by
the communication controller rather than by updating from the host system.
According to the basic realisation of the present invention the communication
controller, according to the first aspect of the present invention, is
implemented fully or
partly as an integrated circuit applying VLSI, LSI, ASIC, FPGA, PLD techniques
or any
combinations thereof. This provides considerable production cost reductions
since by
implementing the communication controller according to the first aspect of the
present
invention utilising these production techniques the production time and the
product
handling are greatly reduced, and furthermore, the amount of costly pin
connections
and component casings are subsequently minimised.
The communication controller, according to the first aspect of the present
invention,
wherein the data compression unit adds flag and fragment ID trailing the
compressed
part of the input data contained the second section of the data communication
package, and wherein the data decompression unit extracts flag and fragment ID
trailing the compressed part of the input data in the second section of the
data
communication package. The flag and fragment ID provides information as to how
the
data communication package is configured. The data compression unit comprising
two
modes of operation, a high compression mode of operation handling compression
of
the part of the input data substantially simultaneously to transmission of the
data
communication package, and a low compression mode of operation applying a
reduced compression efficiency to the compression substantially simultaneously
to
transmission of the data communication package, the high compression mode of
operation operating according to an amount of accumulated data in the
transmission
FIFO and the data compression unit being notified by the network transmission
controller in case of the amount of accumulated data in transmission FIFO is
less than
a predetermined value hence activating the low compression mode of operation.
The
capability of switching between two modes of compression enables the
communication
controller to perform at a maximum rate continuously and supplying the network
with
transmission data bytes until the end of the data communication package is
reached.
In this context the low compression mode may involve low compression, no
compression or even expansion or decompression.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
8
The above object, the above advantage and the above feature together with
numerous
other objects, advantages and features which will be evident from the below
detailed
description of a preferred embodiment of the present invention is according to
a
second aspect of the present invention obtained by a transmission and
encryption
section of a communication controller for performing data encryption and data
decryption of data communication packages to be transferred in a network (such
as a
LAN: Local Area Network, or a WAN: Wide Area Network), the data communication
package containing a first section of non-encrypted data and a second section
containing encrypted data, and said communication controller comprising a
session
key LUT unit, and comprising:
(a) a data read transmission control unit (102) connected to a system bus of a
host
system and receiving input data therefrom and connected to said session key
LUT (186), said session key LUT (186) providing a transmission encryption key
for said data communication package,
(b) a data compressing unit (118) providing compression of a part of said
input
data thereby producing a compressed part of said input data contained in said
second section of said data communication package,
(c) a data encryption unit (126) providing an encryption of said second
section of
said data communication package according to said transmission encryption
key transferred from said session key LUT (186) to said data encryption unit
(126),
(d) an integrity check value calculation unit (122) constituting a first
series
configuration from said data compression unit (118) interconnecting through
said integrity check value calculation unit (122) to said data encryption unit
(126),
(e) a network transmission controller (134) providing said data communication
package through a connection to said network, supplying said input data to
said LAN in a transmission rate determined by said network transmission
controller (134) and said network, and
(f) a first switch means (108) enabling switching between two modes of
operation,
a first mode of operation providing bypassing or disabling of said first
series
configuration and providing a connection from said data read transmission
control unit (102) with said network transmission controller (134) for
transferring
said input data directly hereto and a second mode of operation providing a
connection to said data read transmission control unit (102) through said
first
series configuration to said network transmission controller (134).
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 60/30262 PCT/DK99/00625
9
The transmission and encryption section of a communication controller,
according to
the second aspect of the present invention is new, and incorporates several of
its
functions in a single electronic circuit. Hereby considerably reducing the
time delay
from on section to the next compared to time delays between discrete
electronic
components.
The communication controller, according to the second aspect of the present
invention, wherein the transmission and encryption section further comprises a
transmission FIFO (first in first out storage means) constituting an input
section of the
network transmission controller. Since the transmission and encryption section
of a
communication coritroller, according to the second aspect of the present
invention,
comprises storage means for transmission of data communication packages, full
compatibility is achieved between a host system and the network. Especially
differences in reading rates between stations and network transmission rates
are
compensated for. The host system may operate at one transmission frequency,
white
the network may operate at another without overloading the host system or the
network. This relieves processing time available to the host system, since
delivering a
data communication package to the controller frees the host system's central
processing unit to perform other tasks than waiting for completion of
transmission and
therefor optimises the transmission performed on the network.
The transmission and encryption section of a communication controller,
according to
the second aspect of the present invention, for encrypting and transmitting
data
communication packages on a network provides interrupt routines for units
included in
the communication controller hereby insuring a continuous data transmission on
a
network. The transmission and encryption section, having the data compression
unit
and the data encryption unit adapted to be operated substantially
simultaneously and
controlled by the network transmission controller. The network transmission
controller
controls the transmission FIFO so as to guarantee the continuous supply of
bytes from
the transmission FIFO to the network transmission controller. This ensures
that the
transmission is extraordinarily fast. Furthermore, since the communication
controller
preferably is implemented in accordance with a technique for producing
integrated
electronic circuits, a fast internal control of the operation may be achieved.
By
operating data compression and data encryption substantially simultaneously
instead
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
of operating consecutively considerably improves the transmission time and
reduces
the delay for transmitting a secure data communication package.
The transmission and encryption section of a communication controller,
according to
5 the second aspect of the present invention, having the data read
transmission control
adapted to monitor the compression and encryption of the part of the input
data for
determining, whether or not, the part of the input data exceeds the amount of
data
containable within the second section of data communication package. By
continuously monitoring if the data communication packages processed are
within the
10 package specifications of the network, any redundant operations are
eliminated, and
thus the number of data communication packages transmitted on the network is
reduced.
The transmission and encryption section of a communication controller,
according to
the second aspect of the present invention, wherein the integrity check value
calculation unit performs a subtraction, division, multiplication or
preferably a
summation of the data contained in the second section of the data
communication
package to be transmitted, and adding a first integrity calculation value to
the second
section of the data communication package. The integrity check value
calculation
ensures that no excessive time is spent on corrupted data communication
packages at
the receiving end of a transmission, therefor, implementation of this
calculation may
reduce unnecessary data communication package processing.
The transmission and encryption section of a communication controller,
according to
the second aspect of the present invention, wherein the data read transmission
control
unit comprises control means for controlling the first switch means in the two
modes of
operations. These switching means ensures a fast recognition of the clear text
and
consequently bypassing or disabling of the first series configuration.
The transmission and encryption section of a communication controller,
according to
the second aspect of the present invention, wherein the data read transmission
control
unit further comprises a connection to the data encryption unit for
transferring the
transmission encryption key provided by the session key LUT from the data read
transmission control unit to the data encryption unit.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
11
The transmission and encryption section of a communication controller,
according to
the second aspect of the present invention, wherein the session key LUT
comprising
encryption key information is updated according to a key management protocol
by the
host system. Encryption key administration is entirely managed by the host
system
thus delegating this cumbersome task to the host rather than a local
processing unit
on the communication controller. In an alternative embodiment of the present
invention, the encryption key or keys may be updated through the data read
transmission control of the communication controller. Further alternatively
the
encryption key or keys may be generated locally by the communication
controller
rather than by updating from the host system.
According to the basic realisation of the present invention the transmission
and
encryption section of a communication controller, according to the second
aspect of
the present invention, is implemented fully or partly as an integrated circuit
applying
VLSI, LSI, ASIC, FPGA, PLD techniques or any combinations thereof. This
provides
considerable production cost reductions since by implementing the
communication
controller according to the first aspect of the present invention utilising
these
production techniques the production time and the product handling are greatly
reduced, and furthermore, the amount of costly pin connections and component
casings are subsequently minimised.
The transmission and encryption section of a communication controller,
according to
the second aspect of the present invention, wherein the data compression unit
adds
flag and fragment ID trailing the compressed part of the input data contained
in the
second section of the data communication package. The flag and fragment ID
provides information as to how the data communication package is configured.
The
data compression unit comprising two modes of operation, a high compression
mode
of operation handling compression of the part of the input data substantially
simultaneously to transmission of the data communication package, and a low
compression mode of operation applying a reduced compression efficiency to the
compression substantially simultaneously to transmission of the data
communication
package, the high compression mode of operation operating according to an
amount
of accumulated data in the transmission FIFO and the data compression unit
being
notified by the network transmission controller in case of the amount of
accumulated
data in transmission FIFO is less than a predetermined value hence activating
the low
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO b0/30262 PCT/DK99/00625
12
compression mode of operation. The capability of switching between two modes
of
compression enables the communication controller to perform at a maximum rate
continuously and supplying the network with transmission data bytes until the
end of
the data communication package is reached.
The above object, the above advantage and the above feature together with
numerous
other objects, advantages and features which will be evident from the below
detailed
description of a preferred embodiment of the present invention is according to
a third
aspect of the present invention obtained by a method for transmitting and
encrypting in
a communication controller for performing data encryption and data decryption
of data
communication packages to be transferred in a network (such as a LAN: Local
Area
Network, or a WAN: Wide Area Network), said data communication package
containing a first section of non-encrypted data and a second section
containing
encrypted data, and said communication controller comprising a session key
storage
means, a transmission FIFO (first in first out storage facility) means, a data
read
transmission control means, a data encryption means, a data compression means
and
an integrity check value calculation means constituting a first series
configuration from
said data compression means interconnecting through said integrity check value
calculation means to said data encryption means, said method for transmitting
and
encrypting, comprising:
(a) receiving input data from a system bus of a host system by means of said
data
read transmission control means connected to said session key storage
means, providing a transmission encryption key for said data communication
package by means of said session key storage means,
(b) providing compression of a part of said input data thereby producing a
compressed part of said input data contained in said second section of said
data communication package by means of said data compressing means,
(c) providing an encryption by means of said data encryption means, according
to
said transmission encryption key transferred from said session key storage
means, of said second section of said data communication package transferred
from said data compressing means,
(d) supplying said data communication package to said network in a
transmission
rate determined by said controller means for network transmission and said
network by means of a connection to said network from a controller means for
network transmission, and
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
13
(e) switching by means of a first switching means between two modes of
operation, a first mode of operation providing bypassing or disabling of said
first
series configuration and connecting said data read transmission control means
with said controller means for network transmission and transferring said
input
data directly hereto and a second mode of operation providing a connection
from said data read transmission control means through said first series
configuration to said controller means for network transmission through a
connection hereto by means of said means for data encryption.
The method for transmitting and encrypting in a communication controller,
according to
the third aspect of the present invention, is new and ensures a secure and
fast
transmission. Furthermore by incorporating the means in a single method the
time
delays are considerably reduced.
The method for transmitting and encrypting, according to the third aspect of
the
present invention, further comprising constituting an input section of said
controller
means for network transmission by means of a transmission FIFO means (first in
first
out storage means). Since the method for transmission and encryption in a
communication controller, according to the third aspect of the present
invention,
comprises storage means for transmission of data communication packages, full
compatibility is achieved between a host system and the network. Especially
differences in reading rates between stations and network transmission rates
are
compensated for. The host system may operate at one transmission frequency,
while
the network may operate at another without overloading the host system or the
network. This relieves processing time available to the host system, since
delivering a
data communication package to the controller frees the host system's central
processing unit to perform other tasks than waiting for completion of
transmission and
therefor optimises the transmission performed on the network.
The method for transmitting and encrypting in a communication controller,
according to
the third aspect of the present invention, further comprising provision of
interrupt
routines for units included in the communication controller hereby insuring a
continuous data transmission on the network by means of the controller means
for
network transmission. The method for transmitting and encrypting further
comprising
substantially simultaneously operations of the data compression means and the
data
encryption means, and controlling by the controller means for network
transmission.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
W~00/30262 PCT/DK99/00625
14
The method for transmitting and encrypting, further comprising controlling the
transmission FIFO means by means of the controller means for network
transmission
so as to guarantee the continuous supply of bytes from the transmission FIFO
means
to the controller means for network transmission. This ensures that the
transmission is
performed extraordinarily fast. Furthermore, since the means incorporate
several
operations in the method a fast internal control of the operations may be
achieved.
Performing data compression and data encryption substantially simultaneously
instead
of performing the operations consecutively considerably improves the
transmission
time and reduces the delay for transmitting a secure data communication
package.
The method for transmitting and encrypting in a communication controller,
according to
the third aspect of the present invention, further comprising monitoring the
compression and encryption of the part of the input data by means of the data
read
transmission control means for determining, whether or not, the part of the
input data
exceeds the amount of data containable within the second section of data
communication package. By continuously monitoring if the data communication
packages processed are within the package specifications of the network, any
redundant operations are eliminated, and thus the number of data communication
packages transmitted on the network is reduced. If a data communication
package is
within the package size specification of the network the method prevents
further data
compression relieving the means hereby obtaining valuable processing time.
The method for transmitting and encrypting in a communication controller,
according to
the third aspect of the present invention, further comprising transferring the
transmission encryption key provided by the session key storage means from the
data
read transmission control means to the data encryption means by means of a
connection means.
The method for transmitting and encrypting in a communication controller,
according to
the third aspect of the present invention, further comprising operating the
data
compression means in two modes of operation, a high compression mode of
operation
handling compression of the part of the input data substantially
simultaneously to
transmission of the data communication package, and a low compression mode of
operation applying a reduced compression efficiency to the compression
substantially
simultaneously to transmission of the data communication package, the high
compression mode of operation operating according to an amount of accumulated
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
data in the transmission FIFO means and the data compression means being
notified
by the controller means for network transmission in case of the amount of
accumulated data in the transmission FIFO means is less than a predetermined
value
hence activating the low compression mode of operation. The capability of
switching
5 between two modes of compression enables the continuous performance of a
maximum rate and supply of transmission data bytes to the network until the
end of
the data communication package is reached.
The method for transmitting and encryption in a communication controller,
according to
10 the third aspect of the present invention, the communication controller
further
comprising receiving means, a data writing means, a data decompressing means,
a
data decryption means, a data receiving control means and an integrity check
value
verification means constituting a second series configuration from said data
decryption
means interconnecting through said integrity check value verification means to
said
15 data decompression means, comprising:
(f) providing a connection to said network and receiving a received data
communication package from said network by means of controller means for
network reception,
(g) receiving said received data communication package through a connection to
said controller means for network reception and connecting to said session key
storage means by means of a data receiving control means, providing a
reception encryption key for said data communication package by means of
said session key storage means,
(h) providing a decryption of said second section of said received data
communication package according to said reception encryption key transferred
from said session key storage means and providing a decrypted second
section of said received data communication package by means of a data
decryption means,
(i) providing decompression of a compressed part of said decrypted second
section of said received data communication package and providing a
decompressed part in said second section of said received data
communication package instead of said compressed part in said second
section of said data communication package by means of a data
decompression means,
(j) supplying said system bus of said host system with received data
communication package by means of said data writing means, and
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 80/30262 PCT/DK99/00625
16
(k) switching by means of a second switching means enabling switching between
two modes of operation, a third mode of operation providing bypassing or
disabling of said second series configuration and connecting said data
receiving control means with said data writing means and transferring said
received input data directly hereto, and a fourth mode of operation providing
a
connection from said data receiving control means through said second series
configuration to said data writing means.
By introducing receiving means to the method for transmitting and encrypting
several
advantages are achieved. By performing transmission and reception by applying
a
single method simplifies processes and enables common actions of both
transmission
and reception to be shared.
The method for transmitting and encrypting, according to the third aspect of
the
present invention, further comprising receiving said received data
communication
package from said data receiving control means in said third mode of
operation,
receiving said received data communication package from said data
decompression
means in said fourth mode of operation and transferring said received data
communication package through a connection to said data writing means by means
of
a write FIFO means, and receiving said received data communication package
from
said control means for network reception and transferring said data
communication
package through a connection to said data receiving control means by means of
a
receiving FIFO means.
The method for transmitting and encrypting in a communication controller,
according to
the third aspect of the present invention, further comprising updating
encryption key
information in the session key storage means according to a key management
protocol by the host system. Encryption key administration is entirely managed
by the
host system thus delegating this cumbersome task to the host rather than a
local
processing means on the communication controller. In an alternative embodiment
of
the present invention, the encryption key or keys may be updated through the
data
read transmission control means.
The method transmitting and encrypting in a communication controller,
according to
the third aspect of the present invention, further comprising performing a
subtraction,
division, multiplication or preferably a summation of the data contained in
the second
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
W O 00/30262 PCT/DK99/00625
17
section of the data communication package to be transmitted, and adding a
first
integrity check value to the second section of the data communication package
by
means of the integrity check value calculation means. Additionally, the method
for
transmitting and encrypting in a communication controller, according to the
third
aspect of the present invention, further comprising performing a subtraction,
division,
multiplication or preferably a summation of the data contained in the second
section of
a received data communication package. Hereby obtaining a second integrity
check
value and comparing the second integrity check value with the first integrity
check
value contained in the received data communication package by means of the
integrity
check value verification means. The integrity check value calculation and
verification
ensures that no excessive time is spent on corrupted data communication
packages at
the receiving end of a transmission, therefor, implementation of this
calculation and
verification may reduce unnecessary data communication package processing.
The method for transmitting and encrypting in a communication controller,
according to
the third aspect of the present invention, further comprising controlling the
first
switching means in the two modes of operations by means of the data read
transmission control means. The method transmitting and encrypting in a
communication controller, according to the third aspect of the present
invention, further
comprising controlling the second switching means in the two modes of
operations by
means of the data receiving control means. These switching means ensures a
fast
recognition of the clear text and consequently bypassing or disabling of the
first and
second series configuration, respectively.
The method for transmitting and encrypting in a communication controller,
according to
the third aspect of the present invention, further comprising providing
interrupt routines
for units included in the communication controller hereby insuring a
continuous data
transmission on the network by means of the receiving means for receiving the
data
communication packages on the network.
The method for transmitting and encrypting in a communication controller,
according to
the third aspect of the present invention, further comprising adding flag and
fragment
ID trailing the compressed part of the input data contained in the second
section of the
data communication package by means of the data compression means, and further
comprising extracting flag and fragment ID trailing the compressed part of the
input
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
18
data in the decrypted second section of the data communication package by
means of
the data decompression means.
The above object, the above advantage and the above feature together with
numerous
other objects, advantages and features which will be evident from the below
detailed
description of a preferred embodiment of the present invention is according to
a fourth
aspect of the present invention obtained by a network controller of a
communication
controller comprising means for producing a data communication package
comprising
a non encrypted first section including clear header, and a encrypted second
section
including a protected header, a data section, a fragment ID, flags, padding
and a ICV.
By placing flags and the fragment ID contrary to normal practice trailing the
data
section an improved configuration is obtained, since the transmission may be
initiated
without delay. Thus a significant reduction in transmission time is achieved.
The network controller of a communication controller, according to the fourth
aspect of
the present invention, further comprising means for producing the data
communication
package wherein the data section comprises compressed data, end of data,
padding
and uncompressed data. In case transmission data in non-compressed form are
larger
than a maximum payload of the data section then the transmission data are
compressed until the transmission data are smaller than the maximum payload of
the
data section. If the transmission data in compressed are larger than the
maximum
payload of the data section then the transmission data are transmitted
uncompressed.
Therefor the data section is configured as comprising compressed data as well
as an
uncompressed data. The compressed data part may contain 0 bytes of data. By
continuously monitoring of the compression of the transmission data delays in
the
transmission are eliminated.
The network controller of a communication controller, according to the fourth
aspect of
the present invention, may further advantageously comprise any of the features
of the
communication controller according to the first and second aspects of the
present
invention and may further advantageously be adapted to perform the method
according to the third aspect of the present invention.
The above object, the above advantage and the above feature together with
numerous
other objects, advantages and features which will be evident from the below
detailed
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO fl0/30262 PCT/DK99/00625
19
description of a preferred embodiment of the present invention is according to
a fifth
aspect of the present invention obtained by a data communication package
comprising
a data section including compressed data and uncompressed data.
44. The above object, the above advantage and the above feature together with
numerous other objects, advantages and features which will be evident from the
below detailed description of a preferred embodiment of the present invention
is
according to a sixth aspect of the present invention obtained by a
communication
controller chip for performing data encryption and data decryption of a
multiplicity
of data communication packages to be transferred in a network such as LAN
(local
area network) or WAN (wide area network) and including a plurality of
processing
units, each of said multiplicity of data communication packages containing a
first
section of non-encrypted data and a second section containing encrypted data
and
each said of multiplicity of data communication packages having an associated
processing descriptor defining source, destination, process configuration of
said
plurality of processing units and processing of said data communication
package,
and said communication controller chip comprising:
(a) a bridge unit connecting said communication controller through a bus to a
central processing unit (CPU) or a host,
(b) a random access memory RAM for keys, processing descriptors and for
temporary storage of data,
(c) a data transmission control unit for providing access for said CPU to
information regarding general configuration of said communication controller,
(d) an in-queue unit comprising a plurality of queues for pointers referencing
processing descriptors for data communication packages in said RAM to be
processed by said plurality of processing units,
(e) an out-queue unit comprising a go-queue of pointers referencing processing
descriptors for data communication packages in RAM to be processed by a
plurality of processing units, which process is monitored and analysed by said
CPU or host system so as to establish if further processing is required, and
said out-queue unit comprising a complete-queue of pointers referencing
processing descriptors for data communication packages in said RAM having
completed processing in accordance with requirements of said CPU or host
system,
(f) a decompression processing unit included in said plurality of processing
units
providing decompression of compressed data of said second section of said
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
data communication packages thereby producing decompressed data in said
RAM or memory of said host in accordance with processing descriptors
associated with said data communication packages,
(g) a compression processing unit providing compression of said second section
5 of said outgoing data communication packages thereby producing
compressed data in said RAM or memory of said host in accordance with
processing descriptors associated with said data communication packages,
(h) a decryption processing unit providing a decryption of said second section
of
a data communication package according to a reception decryption key
10 provided in a decryption key space of said RAM, said decryption key space
being referenced by a key pointer included in said processing descriptors, and
said decryption processing unit providing generation of said second section of
said data communication package,
(i) an encryption processing unit providing an encryption of said second
section
15 of a data communication package according to a transmission encryption key
provided in an encryption key space of said RAM, said encryption key space
being referenced by said key pointer of said processing descriptors, and said
encryption processing unit providing generation said second section of said
outgoing data communication package,
20 (j) a bus designated as first in first out (FIFO) bus enabling
communication
between said bridge unit, said RAM, said data transmission control unit, said
in-queue unit, said out-queue unit, said compressing processing unit, said
decompression processing unit, said encryption processing unit and said
decryption processing unit, and
(k) a management bus providing signaling and configuration between said data
transmission control unit, said in-queue unit, said out-queue unit, said
compressing processing unit, said decompression processing unit, said
encryption processing unit and said decryption processing unit,
said communication controller allowing for parallel processing of said
multiplicity of
said data communication packages to be performed in any arbitrary order in
accordance
said processing descriptors in RAM.
The communication controller chip according to the sixth aspect of the present
invention provides a superior implementation of the invention according to
first,
second, third and fifth aspect of the invention, since the communication
controller chip
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO-00/30262 PCT/DK99/00625
21
allows for any combination of units and any combination of order in which the
units
operated thereby providing an extremely fast system.
The communication controller chip according to the sixth aspect of the present
invention further comprises:
(I) a first authentication processing unit providing calculation of an
integrity check
value (ICV) to be included in an outgoing data communication package, said
calculation utilising an ICV key provided in a ICV key space of said RAM, said
ICV key space being referenced by said processing descriptors,
(m) a second authentication processing unit providing verification of an ICV
to be
extracted from an incoming data communication package, said calculation
utilising a ICV key provided in said ICV key space of said RAM, said ICV key
space being referenced by said processing descriptors,
(n) a receiving media access control unit (RX-MAC) constituting an address
filter
for said communication controller and providing a receiving gate for said
network, said receiving media access control unit filtering all data
communication packages on said network and communicating incoming data
communication packages to a incoming data communication package space
in said RAM, said receiving media access control unit simultaneously
generating a processing descriptor for every incoming data communication
packages, said processing descriptor including a start address of associated
incoming data communication package in a incoming data communication
package space in said RAM, said receiving media access control unit
communicating said processing descriptor to said in-queue unit, and said
receiving media access control unit communicating an end address of said
incoming data communication package space in said processing descriptor at
completion of reception of said incoming data communication package, and
(o) a transmitting media access control unit (TX-MAC) providing a transmitting
gate for said communication controller on said network and performing a
transmission on said network of outgoing data communication packages
identified by said processing descriptors in said RAM, said transmitting media
access control unit performing evaluation of length of said outgoing data
communication package and writing said length in said first section of said
outgoing data communication package, and said transmitting media access
control unit communicating said processing descriptors to said complete
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
22
queue of said out-queue on completion of transmission of said data
communication package.
The RAM of the communication controller chip according to the sixth aspect of
the
present invention is constituted by SRAM, DRAM, or SDRAM or any combinations
thereof.
The compressing processing unit of the communication controller chip according
to the
sixth aspect of the present invention may be configured to detect compression
efficiency and in accordance to the compression efficiency continue
compression of
data or disengage further compression.
The communication controller chip according to the sixth aspect of the present
invention ensures that the management bus further providing signaling and
configuration for the first authentication processing unit, the second
authentication
processing unit, the receiving media access control unit, and the transmitting
media
access control unit, and the first in first out (FIFO) bus further enabling
communication
between the bridge unit, the RAM, the data transmission control unit, the in-
queue unit,
the out-queue unit, the compressing processing unit, the decompression
processing
unit, the encryption processing unit, the decryption processing unit, the
first
authentication processing unit, the second authentication processing unit, the
receiving media access control unit, and the transmitting media access control
unit.
The communication controller chip according to the sixth aspect of the present
invention includes the compressing processing unit having a maximum allowable
space on the RAM for compressed data included in the second section of the
outgoing
data communication package and includes the decompressing processing unit
having
a maximum allowable space on the RAM for decompressed data included in the
second section of the incoming data communication packages to be communicated
to
the CPU or the host.
As mentioned above the communication controller chip according to sixth aspect
of the
present invention is implemented having features of the communication
controller
according to features of the first aspect of the present invention, having
features of the
transmission and encryption section of a communication controller according to
second aspect of the present invention, being adapted to perform the method
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO DO/30262 PCT/DK99/00625
23
according third aspect of the present invention, having features of a network
controller
of a communication controller according to fourth aspect of the present
invention, and
having features allowing transmission of the data communication packages
according
fifth aspect of the present invention.
In the following the invention will be further explained with reference to the
drawing
and tables, wherein:
figure 1 is a schematic presentation of an encrypted LAN communication
package,
figure 2 is a schematic overview of a typical communication system having
incorporated a communication controller according to present invention,
figure 3 is a schematic diagram of a presently preferred embodiment according
to the
invention for data-encryptionldata-decryption,
figure 4 and figure 4B are a schematic presentations of data formats for a
compressed
payload,
figure 5 is a schematic presentation of an example on an advantageously and
presently preferred embodiment of a LAN communication package format according
to the invention.
Figure 6 is a schematic diagram of an ESP (Encapsulating Security Payload)
processing of an IP data telegram,
Figure 7 is a schematic presentation of a compression in accordance to IP com,
Figure 8 is a log diagram of the processing units and connecting ram,
Figure 9 is a schematic presentation of a virtual private network interfacing
to the
intranet and to the Internet,
Figure 10 is a block diagram of a network interface controller card consisting
of a
single Ethernet interface and a single set of processing units such as
compressing or
encryption units,
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO DO/30262 PCT/DK99100625
24
Figure 11 is a block diagram of a virtual private network showing logical
connections
and structures,
Figure 12 is a schematic presentation of a structure of a processing
descriptor,
Figure 13 is a schematic presentation of an example of a buffer indication in
the
processing descriptor and shows a processing descriptor configuration for
encryption
followed by authentication.
Figure 14 is a schematic presentation of a principle of signalling between
processing
units,
Figure 15 is a schematic presentation of a modes for the synchronisation
performed
between the processing unit,
Figure 16 is a schematic presentation of the main state machine of the
processing
unit, which controls the processing and the overall operation,
Figure 17 is a schematic presentation of a calculation of a virtual FIFO count
calculated as the difference between a source buffer end and source buffer
start,
Figure 18 is a schematic presentation of destination buffer control and
signalling
(destination buffer increment control signalling),
Figure 19 is a schematic presentation of signalling status (SIGStatus),
Figure 20 is a schematic presentation of a management bus and the attached
processing units and controller units,
Figure 21 is a schematic presentation of a state machine, which requests a
processing
unit,
Figure 22 is a schematic presentation of an encapsulated security payload
specification including padding at the end of the payload,
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO x0/30262 PCT/DK99/00625
Figure 23 is a schematic presentation of the activation of a processing
descriptor
which activation is controlled by the state machines, and
Figure 24 is a schematic presentation of an Ethernet frame format,
5
Table 1 summarises encryption algorithms currently suggested by the encryption
security payload and the requirements for confidentiality,
Table 2 lists the algorithms which are required by the authentication of
authentication
10 header and encryption security payload,
Table 3 lists State and Activity of a processing unit main state machine,
Table 4 lists State and Activity of source buffer end and virtual FIFO count
control,
Table 5 lists State and Activity of destination buffer control and signalling,
Table 6 lists State and Activity of signalling status,
Table 7 lists the implementation of the interrupt lines of the central
processing unit
(CPU),
Table 8 lists allocation of chip select in memory areas which allocation is
controlled by
the system controller which provides large flexibility regarding location in
the processor
memory space,
Table 9 lists the address fields of the register space layout,
Table 10 lists common processing units registers,
Table 11 lists source buffer increment layouts,
Table 12 lists identifiers for all the processing units,
Table 13 lists definitions of the currently identified signals to be
transferred on a
management bus
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 ~ PCT/DK99/00625
26
Table 14 lists the result/status of each command's last signal indicated by
the target,
Table 15 lists State and Activity of the processing unit's
request/arbitration,
Table 16 lists definitions of type,
Table 17 outlines the differences in handling of the header and source buffer,
Table 18 outlines the requirement regarding the alignment,
Table 19 lists common fields, which are common to most of the processing
descriptor
sections,
Table 20 lists the configuration of the base,
Table 21 lists Offset, Size, Type and Name of fixed fields,
Table 22 lists Offset, Size, Type, Name, Description of encryption processing
descriptor section,
Table 23 lists the configuration base of encryption processing descriptor
section,
Table 24 lists Offset, Size, Type, Name and Description of decryption
processing
descriptor section,
Table 25 lists configuration base of decryption processing descriptor section,
Table 26 lists value of the next header field in the encryption security
payload trailer of
description processing descriptive section,
Table 27 lists Offset, Size, Type, Name and Description of keyslinitialisation
vector
section,
Table 28 lists Offset, Size, Type, Name and Description of calculation
processing
descriptive section,
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
27
Table 29 lists configuration base of calculation processing descriptive
section,
Table 30 lists Offset, Size, Type, Name and Description of verification
processing
descriptive section,
Table 31 lists configuration base of verification base of verification
processing
descriptive section,
Table 32 fists Offset, Size, Type, Name and Description of authentication
algorithm
configuration,
Table 33 lists algorithms of the authentication algorithm configuration,
Table 34 lists Offset, Size, Type, Name and Description of compression
processing
descriptive section,
Table 35 lists configuration base of compressing processing descriptive
section,
Table 36 lists Offset, Size, Type, Name and Description of decompression
processing
descriptive section,
Table 37 lists configuration of decompression processing descriptive section,
Table 38 lists Offset, Size, Type, Name and Description of register interface,
Table 39 lists Offset, Size, Type, Name and Description of InQueue processing
descriptive section,
Table 40 lists configuration of InQueue processing descriptive section,
Table 41 lists State and Activity for a InQueue state machine used for
monitoring the
state of previous processing units,
Table 42 lists Offset, Size, Type, Name and Description of register's
interface,
SU8STtTUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO-00/30262 PCT/DK99/00625
28
Table 43 lists OutQueue pointer format of register's interface,
Table 44 lists configuration of register's interface,
Table 45 lists Offset, Size, Type, Name and Description of OutQueue processing
descriptive section,
Table 46 lists Offset, Size, Type, Name and Description of Ethernet
transmission and
IP compensation of processing descriptive section,
Table 47 lists configuration base of Ethernet transmission and lP compensation
of
processing descriptive section,
Table 48 lists Offset, Size, Type, Name and Description of Ethernet reception,
Table 49 lists configuration base of Ethernet reception,
Table 50 lists Offset, Size, Type, Name and Description of media access
control
address registers,
Table 51 lists Offset, Size, Type, Name and Description of receive media
access
control address filter configurations,
Table 52 lists media access control types,
Table 53 lists Offset, Size, Type and Description of source buffer register
interface,
Table 54 lists the results of a read operation performed with an external
memory
access command,
Table 55 lists Offset, Size, Type, Name and Description of destination buffer
registers,
and
Table 56 lists the results of a write operation performed with an external
memory
access command.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
29
A transmission between different stations connected in a network such as a LAN
(local
area network) or a WAN (wide area network) involves sending data communication
packages from one station to a connecting station or connecting stations and
receiving
data communication packages at one station from a connecting station or
several
connecting stations. Figure 1 illustrates a data communication package
designated in
its entirety by numeral 10 and comprising a section containing clear text 12
and a
section containing encrypted data 14. The section containing clear text 12
holds a 48
bit address or addresses of the receiving station or stations, respectively,
and a 48 bit
address of the transmitting station. Since all stations in the LAN should be
able to
maintain communication with each other an obvious solution would be that the
LAN
systems use a single encryption key for the entire system. This will ensure a
fast
working communication net but simultaneously undermine the security of the
transmissions since any station connected to the LAN will be able to decipher
any data
communication packages within the system. Therefor it is common practise to
have
communicating stations agree upon an encryption key or a set keys only known
to the
stations involved before transmitting data communication packages.
Multicasting
functions are provided for by having all the individual stations agree upon an
encryption key or a set of keys only known by the transmitting and receiving
stations
before a transmission is performed. Generally the communicating stations may
deduce
which encryption key to apply from the clear text of the transmission. The
receiving
station may locate an encryption key in a local key centre and recall the
encryption key
associated with the transmitting station, similarly the transmitting station
prior to
encryption may locate an encryption key in a local key centre and recall the
encryption
key associated with the receiving station. According to the addresses of the
receiving
and transmitting stations contained in the clear text 12 the correct selection
of an
encryption key may be performed.
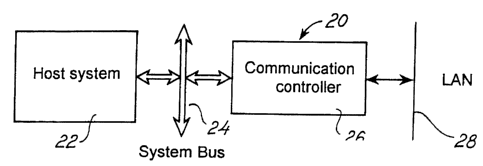
Figure 2 illustrates a schematic overview of a communication system,
designated in its
entirety by numeral 20, incorporating a communication controller 26 according
to the
present invention. The communication controller 26 is connected to a LAN 28
and to a
local system bus 24 of a host system or station 22. The host system 22 for
example a
computer or a router directs a data communication package in a raw state, i.e.
containing data which is not encrypted, to the system bus 24. This activates
the
communication controller 26, which subsequently encrypts the data and
initiates a
transmission of a data communication package through the LAN 28.
Alternatively, the
communication controller 26 receives a data communication package from the LAN
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO (10/30262 PCT/DK99/00625
28, performs a decryption of the data communication packages and places the
decrypted data communication packages on the system bus 24. The decrypted data
communication packages are then collected from the system bus 24 by the host
system 22. The communication controller 26 is an independent unit acting
between the
5 host 22 and the LAN 28 and performing the data communication encryption and
decryption thereby significantly reducing processing time of the host needed
for data
transmissions. Additionally, the communication controller 26 may be applied to
wide
area network (WAN) modes connected through high speed transmission lines.
10 Figure 3 illustrates the communication controller 26 according to the
present invention
in greater detail. The communication controller 26 is connected to the system
bus of a
host system through connections 100, 186 and 182. The connection designated by
numeral 100 provides transmission data from the system bus of the host system
as
input to a Data Read TX control 102. The Data Read TX control comprises DMA
15 (Direct Memory Access) means performing the collecting and reading of
transmission
data from the system bus. The first part of data communication packages are
transmitted without the application of an encryption procedure according to
the IEEE
standard, therefor a switching between an encryption mode and a non-encryption
mode must be implemented. Presently, there are two acknowledge standards for
20 encryption of data transmission, EEEE 802.10 and IPSec. Either of these
standards or
potential future standards may be applied in the presently preferred
embodiment of the
invention. A switch, designated in its entirety by numeral 108, is connected
to the Data
Read TX control 102 through connection 106 fulfils this requirement. The
switch 108
may be implemented by any gate means utilising semiconductor techniques. Since
the
25 beginning of each data communication package contains non-encrypted data
the
switch has an initial position 110. When the switch 108 is switched in the
position 110
encryption processing is bypassed through a connection 116 providing input
data
directly to a TX FIFO 130. However, when the switch 108 is switched in a
position 112
a connection 114 is established to a Data Compressing unit 118. As described
30 previously, the clear text 12 in the data communication package contains
information
regarding the transmitting and receiving addresses from which a correct
encryption
key may be deduced. When the Data Read TX control 102 obtains the address
information it extracts the appropriate encryption key in a Session Key LUT
182
through a connection 104 and delivers the encryption key to a Data Encryption
unit
126 through a connection 103. The switch 108 is brought in the position 112
thereby
connecting the Data Read TX control 102 with Data Compressing unit 118 through
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
31
connections 106 and 114. The Session Key LUT 182 comprises an external CAM or
a
binary searching means built into an IC in conjunction with an ordinary RAM
and
stores a copy of the session keys. Alternatively, the Session Key LUT 182
comprising
HASH means in conjunction with an ordinary external RAM. The session keys are
updated according to a key management protocol by the host system.
The security of a data transmission is typically improved by adding additional
data,
such as an additional header, padding and ICV (integrity check value), to data
communication packages before encryption. However, if the length of these
typical
data communication packages exceeds the maximum allowable data package size,
limited by LAN specifications, it becomes necessary to apply a fragmentation
procedure upon the data contained in the package. This consequently slows the
transmission rate considerably since more packages are introduced to the LAN
each
of which have copies of the first section added containing destination address
and
transmitting address. The introduction of these additional packages to the LAN
is
avoided by utilising data compressing means, such as the Data Compressing unit
118,
for the reduction of raw data to package sizes that comply with the LAN
specifications.
During the compressing procedure the data is transferred substantially
simultaneously
from the Data Compressing unit 118 to an ICV calculation unit 122 through a
connection 120. The ICV calculation unit 122 performs a calculation of the
integrity
check value by numerically summing the data part of the data communication
package. The ICV calculation unit 122 further adds the value to the end of the
data
package. The compressed data are continuously transferred and finally the
integrity
check value is also transferred from the ICV calculation unit 122 to a Data
Encryption
unit 126 through a connection 124. The Data Encryption unit 126 performs the
encryption of the compressed data and the integrity check value, and
continuously
transfers the result to the TX FIFO 130 through a connection 128. Depending on
which
standard is applied the ICV calculation and the data encryption process may be
interchanged, so as to enable data encryption prior to ICV calculation. The TX
FIFO
130 acts as a first in first out storage buffer ensuring that the LAN always
has data to
transmit. The TX FIFO 130 is partly filled before an actual transmission is
initiated
since the LAN only transmits with a predefined transmission rate and does not
wait for
data to be transmitted. A LAN controller TX 134 collects outgoing data from
the TX
FIFO 130 through a connection 132 and places them on the LAN through
connection
136. The LAN controller TX 134 ensures that the data continuously are loaded
onto
the LAN within LAN specifications.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
32
The LAN generally needs a continuous flow of data. Once a transmission session
is
initiated the data should be delivered to the LAN by the LAN controller TX 134
at
regular intervals and continue to do so until the transmission is complete.
The data
read rate of the Data Read TX control 102 of the communication controller 26
compared to the LAN transmission rate determines how the data transmission is
performed. If, the data read rate of the Data Read TX control 102 is larger
than the
LAN transmission rate then transmission data will temporarily need to be
stored in the
TX FIFO 130 while the LAN controller TX 134 transmits initial parts of the
data. The
LAN controller TX 134 may initiate the transmission as soon as the receiving
address
is extracted from data received from the host. If, on the other hand, the data
read rate
of the Data Read TX control 102 is slower than the LAN transmission rate then
the
LAN controller TX 134 needs to temporarily store transmission data in the TX
F1F0
130 before transmission of any of the data. The LAN controller TX 134 may
initiate the
transmission as soon as the TX FIFO contains sufficient transmission data to
allow for
a continuous flow of data in the LAN transmission. In either case, the data
read rate of
the Data Read TX control 130 being faster or slower than the transmission rate
of the
LAN, the communication controller 26 may perform the storing of transmission
data in
the TX FIFO 130 substantially simultaneously to operations such as extraction
of the
receiving address from the first section of the data package and collecting an
encryption key accordingly. Furthermore, the LAN controller TX 134 may
substantially
simultaneously calculate the amount of transmission data from the data
communication package that needs to be stored in the TX FIFO 130 before the
transmission is initiated on the LAN. The calculation performed by the LAN
controller
TX 134 may start when the LAN controller TX 134 has received the information
regarding the size of the complete data communication package. The calculation
is
based upon size of the data communication package, the efficiency of the Data
Compression unit 118 and the LAN transmission rate. if this calculation shows,
that
transmission time may be reduced by transmitting without compression of the
data the
LAN Controller TX 134 may order the Data Compression 118 through a connection
119 to shift from a high compression mode to a low compression mode.
When the data read rate of the Data Read TX control 130 is equivalent to the
transmission rate of the LAN a worst case station to station transmission time
arises.
Since no transmission data in this case necessarily is stored in the TX FIFO
130 the
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO-00/30262 PCT/DK99/00625
33
communication controller 26 cannot perform parallel operations and therefore
the
transmission time is the longest.
The time consumption allowed for the LAN controller TX 134 to extract the
encryption
key depends on the LAN transmission rate, the LAN type, the location of the
key
information in the data communication package, and the encryption algorithm.
The
following equation must be complied
Tpreamble+Twait~TGet Block'~'TEncrypt Block ( 1 )
and
1 O TGet Key=Tpreamble't'Twaif~'TTx Clear header-TRead Key ID-TGetBlock-
TEncrypt Block (2)
where
Tpreamble is the time necessary for transmitting the preamble part of the data
communication package on the LAN,
TTX Clew header is the time necessary for transmitting the non-encrypted
header
on the LAN,
TRead Key ID IS the time necessary for reading the data from which the
encryption key may be deduced,
TGet Key Is the time allowed for extraction of the encryption key,
TEncrypt Block is the time necessary for encrypting a block of data,
TGet Block is the time necessary for reading a block of data that needs
encryption,
TWa;t is the time the LAN controller TX 134 must wait before the transmission
may begin (can be 0).
In an IEEE 802.3 configured LAN with 10 basex the preamble part of the data
communication package comprises 8 octets having a transmission rate of
10Mbit/sec.
A Key ID comprises 6 octets for a destination address and a Clear header
comprises
12 octets for destination address and source address. The encryption algorithm
applying DES block mode using 8 octets and not transmitting fixed IV consumes
0.64psec for encrypting every block, equivalent to an encryption rate of
100Mbit/sec.
The data read rate of the Data Read TX control 102 might be 10Mbit/sec, if, in
combination herewith the TWa;t=Osec then equation (1) fails because
Tpreamwe+Twa~t=6.4pSec and TGet Block+TEncryPt Block=~.04p,sec. In this
situation the LAN
controller TX 134 must wait 2 octets or Twa~t=1.28~.sec before it according to
equation
(1) is allowed to initiate a transmission. If, the LAN controller TX 134
starts transmitting
when it receives the third octet then the elapsed time will be 8 octets of
preamble part
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
34
of the data communication package (Tp~eamb~e=6.4~sec), a wait state
(Twa;t=1.28p.sec)
and following 14 octets (TTX Clear header 11.2p.sec). Therefor 18.88wsec
passes before
the first encrypted data must be ready for the LAN. There must be 8 bytes of
data in
the Data Encryption 126 before the encryption can begin (T~et B~o~k=6.4wsec)
since a
DES encryption technique is applied and the data compression may be considered
as
time wise neutral. Subsequently the encryption is performed (TEncrypt
Block=0.64psec).
Key extraction is initiated as soon as the destination address is read from
the clear text
in the data communication package (TReaa Key ID=4~8~SeC). Hence the time
allowed for
extraction of the key from the Session key LUT 186 is, according to equation
(2), equal
to
TGet Key = 6.4 + 1.28 + 11.2 - 4.8 - 6.4 - 0.64 = 7.04E.~.sec
If, the T~et Key is smaller or negative then the LAN controller TX 134 must
wait until
there is a sufficient number of data in the TX FIFO 130 before initiating the
transmission.
The primary purpose of the Data Compression unit 118 is to compress the data
to a
state where any fragmentation may be avoided. Additionally, an improved
efficiency of
the LAN is obtained, if, the data read rate of the Data Read TX control 102 is
faster
than the LAN transmission rate then. The data compression may influence the
allowable time consumption of the LAN controller TX 134 however, this
influence may
be reduced significantly by following certain data compression methods.
A first method involves performing the data compression substantially
simultaneously
to performing the data transmission. However, the rate at which the data is
output from
the Data Encryption unit 126 is unpredictable. This is unacceptable since the
TX FIFO
130 must never be emptied during the data transmission. Therefor the data
compression function of the Data Compression unit 118 may be implemented as
dependent on the amount of stored bytes in the TX FIFO 130. Thus, if the TX
FIFO
130 is running low on stored bytes then the Data Compression unit 118 will
lower data
compression efficiency. When applying a data compression algorithm LZ1977 of
the
LZS type to data in the Data Compression unit 118, the implementation of the
lowering
of data compression efficiency may be implemented by having the Data
Compression
unit 118 ignoring its history buffer. The Data Compression unit will lower its
efficiency
as long as the TX FIFO 130 contains an insufficient amount of stored bytes.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
W O -00/30262 PCT/DK99I00625
In applying the first method in a LAN configured according to IEEE 802.3 one
might
experience difficulties. The last two bytes in a (media access control) MAC
header
normally contains information relating to the length of the data communication
package and this information is not known prior to the compression of the data
5 communication package. Therefor a precisely defined and vacant Ethemet type
may
substitute this information relating to the length of the data communication
package
(byte count). The original value is moved into a protected header in the data
communication package thus allowing the receiving station to re-establish the
information.
The first method might induce further difficulties when applying the IPSec
standard
since the length of the data communication package must be included in the IP
header. However, under certain circumstances one may employ the first method
if for
example the communications controller 26 engages in transmitting a IPSec data
communication package having a payload of 4,000 octets of data on a LAN
employing
IEEE 802.3 standard having a maximum data communication package size of 1,500
octets , when a fragmentation is likely to be required since the data in the
data
communication package cannot be compressed to a size within the limits. The
communications controller 26 therefore starts by transmitting a data
communication
package having maximum payload, and if the data compression unit 118
compresses
too much the data compression unit 118 stops compressing so as to ensure that
the
resulting length of the data communication package is identical to the length
of a data
communication package included in the IP header.
A second method involves compressing all the data before the transmission is
initiated
i.e. the amount of data contained in the data communication package and the
necessity for data fragmentation is known. If the primary purpose is to avoid
fragmentation of the data a following first scheme may be implemented. If the
data
communication packages are smaller than the maximum payload then they are
transmitted non-compressed at once. If the data communication packages are
larger
than maximum payload then they are compressed and if the size of the
compressed
part and the clear text part is smaller than the maximum payload, then the
data
communication packages are transmitted. However, if the Data Compression unit
118
is unsuccessful in compressing the data communication package to comply with
the
maximum payload then the data communication package may be transmitted non
compressed. The Data Read TX control 102 may check the progress of the
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
36
compression of the data in the Data Compression unit 118 and make a decision
as to
either continue or interrupt further data compressing of the data
communication
package. Alternatively, the LAN controller TX 134 may check the progress of
the
compression of the data in the Data Compression unit 118 through the
connection 119
and order a high or low compression mode.
In case the data read rate of the Data Read TX control 102 and the compression
speed of the Data Compression unit 118 is faster than the LAN transmission
rate a
second scheme may be implemented. Data communication packages, smaller than a
predetermined size, are transmitted non-compressed at once. Data communication
packages, larger than the predetermined size, are compressed and in case the
compression of the data communication package is progressing normally then the
Data Compression unit 118 continues the compressing procedure otherwise the
compression is interrupted and the data communication package continued as a
non-
compressed transmission. The receiving station or stations experience
compatibility
between the first and second scheme and may be implemented and used with most
relevant standards for data transmission . Figure 4A illustrates a data format
for a
compressed payload, designated by numeral 40 in its entirety, comprising a
first
section 42 containing compressed data, a second section 44 containing a bit
pattern
indicating the end of the compressed data section 42, a third section 46
containing
padding of 0-7 bits insuring the correct placement of the octets in the non-
compressed
data and a fourth section 48 containing the non-compressed data. The length
and the
bit pattern of the second section 44 describe which algorithm is used for
compressing
the data. Figure 4B shows an alternative format for a compressed pay load
designated
by numeral 41 in its entirety, comprising a first section 43 containing
compressed data,
a second section 45 containing uncompressed encrypted data including octets of
uncompressed data encrypted according to a compression standard, a third
section 47
containing a bits pattern indicating the end of the compressed data section 43
and
finally a fourth section 49 containing padding of 0-7 bits ensuring the
correct
placement of the octets in the non-compressed data.
When the data communication packages exceed a size compatible with the LAN
specifications or when the data communication package expand as a result of
the
compression then the data communication package may be fragmented into two or
more data communication packages. Expansion resulting from compression may
occur when the compression is applied to encrypted data. Normally, the maximum
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
37
expansion of the data due to compression relates to the compression algorithm
and
consequently the maximum expansion is known. Typically, an expansion
percentage
is in the range of 5% to 20%, depending on which compression algorithm is
utilised.
By having the Data Read TX control 102 continuously check the progress of the
Data
Compression unit 118 ensures that only the amount of data, which guaranteed
can be
contained in the package including protocol trailer, padding and ICV, is
transferred to
the Data Compression unit 118.
The protocol trailer is the last byte before the padding information in a LAN
data
communication package and is used for indicating if the LAN communication
package
is a fragmented package. Figure 5 illustrates an example on a LAN
communication
package format according to the invention, designated by numeral 50 in its
entirety,
comprising a first section 52 containing a clear text, a second section 54
containing a
protected header, a third section 56 containing data, a fourth section 58
containing
fraction ID, a fifth section 60 containing flags, a sixth section 62
containing padding 62
and a seventh section 64 containing ICV. The protocol trailer comprises
sections 58
and 60 containing fragment ID and flags and includes a byte having 6 reserved
bits, 1
bit indicating more segments and 1 bit indicating fragmentation. If the
fragmentation bit
is TRUE or logical '1' then a fragment identifier may be stored in the in six
bytes
situated from the seventh to last byte to the second to last byte in the data
section 56
in the LAN communication package 50. Alternatively, the flags 60 and the
padding 62
may according to normal practice be contained in the protected header 54.
Choosing
the fragmentation identifiers capacity this large ensures against reruns of
the identical
fragmentation identifier before the session key is changed. Utilising 6 bytes
to describe
the fragmentation identifier results in 120 years on a 1Gbit Ethernet LAN must
pass
before the identifier is rerun. Contrary to normal practise the first
compression method
places flags and fragment ID in the later sections of the LAN communication
package
50. The value included in the ICV section 64 of the LAN communication package
50 is
based on an ICV calculation including sections 54 to 62 illustrated by arrow
66.
Sections in the LAN communication package trailing the clear text section 52
are all
encrypted as illustrated by arrow 68.
The receiving section of the communication controller 26 comprises several
functions.
A LAN controller RX 140 receives data from the LAN through a connection 138
and
stores the data in an RX FIFO 144 through a connection 142 at rates determined
by
the LAN specifications. The RX FIFO 144 acts like a storage buffer ensuring
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO~O/30262 PCT/DK99/00625
38
compatibility between LAN transmission rates and processing speeds of the
communication controller 26. If an error should occur during a reception of
data in the
LAN controller RX 140 the LAN controller RX 140 sends a message to the host
system
and to an RX control unit 148.
The RX control unit 148 extracts the information in the first section of the
data
communication package regarding the encryption key needed for the decryption
of the
received data, collects the appropriate decryption key from the Session key
LUT 186
through a connection 150 and provides the decryption key to a Data Decryption
unit
164 through a connection 165. The RX control unit 148 is capable of
translating a wide
variety of formats of data communication packages and the translation
algorithm may
be adjusted to any new or different formats of data communication packages. A
switch
154 has an initial position 158 directing non-encrypted data contained in the
first
section of a data communication package to a WR FIFO 176 through a connection
160. As the first section of the data communication package ends the switch
154
changes to a new position 156 directing encrypted data contained in the second
section of the data communication package to the Data Decryption unit 164
through a
connection 162 and a connection 152. The Data Decryption unit 164 decrypts the
second section of the data communication package and transfers the decrypted
data
to an ICV check unit 168 through a connection 166. The ICV check unit 168
performs
a verification of the integrity check value of the decrypted data by
calculating the
integrity check value of the decrypted data and comparing the calculated value
with
the value stored in the data communication package by the transmitting
controller of a
different station. If the ICV check unit 168 finds an error in the value it
sends a
message to the host system and the data communication package is discarded.
Depending on which standard is applied the ICV check calculation and the data
decryption process may be interchanged so as to enable data decryption before
ICV
check calculation. If the ICV check unit 168 finds that the two values are
identical then
the data communication package is transferred through a connection 170 to a
Data
Decompression unit 172. The Data Decompression unit 172 provides a
decompression of the verified data communication package and transfers the
result
through a connection 174 to the WR FIFO 176.
The WR FIFO 176 acts like a storage buffer ensuring compatibility between LAN
transmission rates and processing speeds of the communications control 26 e.g.
the
system bus 24 of the host system 22 and the LAN 28 are operating at a
different
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
39
speeds. The data communication package is subsequently extracted through a
connection 178 and placed on the system bus of the host by a Data Write unit
180
through a connection 182. If any errors occur during a reception the host
system is
notified through the Data Write unit 180 enabling the discarding of any parts
of data
received from the package and which are already stored in the host system.
The communication controller 26 co-operates with the host system 22 in
providing the
optimum performance and lowest costs regarding a data transmission system. The
host system 22 must comprise a powerful central programmable unit (CPU) and
include a large capacity of RAM for management of the encryption keys and for
the
updating of the Session Key LUT 186. Furthermore, the host system 22 collects
fragmented data communication packages in its RAM because this provides the
fastest solution. The communication controller 26 comprises relevant
algorithms
implemented in hardware, some CPU means and RAM. During a transmission
procedure the host system 22 may perform a interpretation in part of the data
communication package when the package format is complicated and transmit
relevant information to the communication controller 26 enabling the Data Read
TX
control 102 to quickly find the associated session key. During a reception
procedure
the RX control unit 148 performs an interpretation of the data communication
packages and extracts the relevant encryption keys without help from the host
system
22. However, the host system 22 may perform adjustments to the data
communication
packages before they are handed to the applications.
The term data communication package is a generic term for a datagram, data
telegram, data package and is to be construed as a complete data package to be
transmitted on LAN or WAN.
In the following implementation of the presently preferred embodiment is
further
described having standards IPComp and IPSec applied to the methods described
above. The implementation may be accomplished by configuring a network card or
a
virtual private network card (VPN).
The IPSec standard as defined in RFC 2401 provides a method for achieving
confidentiality andlor authenticity. In the presently preferred embodiment of
the
invention encapsulated security payload (ESP) as defined in RFC 2406 is used
as the
general technology. The ESP processing is performed on the entire IP data
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
communication package in transport- or tunnel mode and provides a new IP data
communication package. The ESP processing in transport mode shown in figure 6
essentially consists of generation of a new IP data communication package
comprising
a copy of the original header including an adjustment of the next header value
and
5 further consists of the application of ESP on the payload. This results in
the encryption
of data and the calculation of an ICV. The encryption is performed before the
ICV
calculation. The field defined as SPI in figure 6 is used as reference for
which
encryption key and which algorithm should be employed.
10 The IPComp standard (RFC 2393) provides the possibility for compression of
data as
shown in figure 7. A compression parameter index (CPI) designates which
algorithm
should be employed in accordance with RFC 2393. During transmission of data
the
compression must be completed before encryption since it is not possible to
compress
encrypted data.
An alternative and presently preferred embodiment of the invention provides
the
possibility for utilising IPSec and IPComp standards as ESP so that delays in
the
system is minimised. This is achieved by combining a central processing unit
(CPU)
for administration and set up of the processing of the individual data
communication
packages as well as dedicated processing units (PU). The PUs are characterised
by
firstly having access to local RAM (common between PUs) into which RAM data is
written and read at a position in the RAM, which is determined by a processing
descriptor (PD), thereby obtaining enlarged flexibility since the CPU is
enabled to
define data before and subsequent to a PU process. Secondly, the process of
data
may be accomplished synchronously between individual PUs thereby enabling
virtual
transfer of data from for example the data compression unit and the data
encryption
unit without significant delays in the system. Thirdly, the individual PUs are
able to
manage header and trailer in accordance with above mentioned standards,
thereby
allowing to define the entire processing of the data communication package
from clear
text to transmission. Fourthly, the processing descriptor PD for each data
communication package defines which process the respective PUs should perform.
Finally, a queuing system enables the communication controller to manage peak
loads
and further accomplishes an effective operation of the CPU.
Figure 8 shows a block diagram of the PUs and connected RAM, in which block
diagram the FIFO (first in first out) bus 80 provides access to a SRAM 82
(static
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
41
random accessible memory) shared by all PUs 92a, 92b, 94a, 94b, 96a, and 96b.
The
management bus 84 shown in figure 8 is used for signalling between individual
PUs
92a, 92b, 94a, 94b, 96a, and 96b for example for the synchronising described
above.
A bridge to CPU/host bus 86 provides access for the CPU to registers in the
individual
PUs 92a, 92b, 94a, 94b, 96a, and 96b, and the SRAM 82.
An external bus 85 may typically be a local bus whereto the local CPU has
access. If
the presently preferred embodiment of the invention is used as a network card
then
the bridge to CPU/host 86 further provides the primary path for transferring
to and from
a host system.
A control unit 88 provides access for the CPU to data relating to general
configuration
and surveillance of the system.
An inqueue unit 90a and an out-queue unit 90b comprises a collection of PDs
which
need to be processed by the CPU (out-queue 90b) and a collection which need to
be
processed by the PUs (in-queue 90a). The in-queue 90a enables the CPU to
insert
PDs as soon as they are ready for processing without having to wait for the
PUs to
become ready. Additional queues ensure that a busy PU does not block or
disable
initiation of a PD on a different PU. The out-queue 90b utilises a go-queue
and a
complete-queue. The go-queue is for inserting PDs as soon as a PU has produced
a
certain amount of data, thereby enabling the CPU to inspect for example an IP
header
on a received Ethernet frame. Further processing may subsequently be initiated
even
though all the data still has not been received. An interrupt is generated to
the CPU
when the go-queue contains a PD. The complete-queue is for inserting PDs when
the
processing of the PDs is finalised. PDs included in the complete-queue are
utilised by
a transmitting media access control unit (TX-MAC) 98a or by the CPU.
A decompression unit PU 92a and a compression unit PU 92b perform a
decompression and compression of data respectively. During compression of data
the
CPU sets up the header thereby ensuring that the complete data block is ready
by the
completion of the compression process. Both the decompression unit PU 92a and
the
compression unit PU 92b have a maximum allowable length of the data. In case
the
length of the data exceeds the maximum allowable length an interrupt is
generated
and transmitted to the CPU. This ensures that no data is over written during
the
creation of a data communication package. The end of data indication may
further be
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO fl0/30262 PCT/DK99/00625
42
applied for the detection of whether the compression has resulted in an
expansion of
the data. By specifying a limit for the compression required the decision as
to further
compression is accelerated. If a satisfactory compression is achieved then the
compression continues and if a non-satisfactory compression is achieved then
the
data will not be compressed and a second start address is applied. The
decision
regarding further compression may be taken without the involvement of the CPU.
A decryption unit PU 94a and an encryption unit PU 94b perform respectively
decryption and encryption of the payload as defined by ESP. A memory block
includes information on keys used for decryption and encryption and is
referenced by
the PDs. The memory block has allocated an ICV (integrity check value) field
for each
SPI (figure 6). The decryption unit 94a and the encryption unit 94b provides
the
possibility for using an ICV for a first set of data on a second set of data
using the
same key block in the memory referenced by the PDs. Further, the decryption
unit
94a and the encryption unit 94b provides an possibility for configuring the
process so
that decryption and encryption may be performed on fragmented data even though
additional processing of other data communication packages are initiated.
Two authentication units PU 96a and 96b perform calculation and validity
control of
ICV. A pointer included in the authentication units 96a and 96b points to a
memory
block including key. Typically a block will be allocated for each SPI
A transmitting media access control unit (TX-MAC) 98b and the RX-MAC 98a
transmits and receives data communication package via the network. At
reception of a
data communication package data is sequentially written to a large buffer and
a PD is
configured in accordance with firstly the start address and secondly the end
address.
As soon as a part of the data is received the PD is moved to the Go-queue
enabling
the CPU to detect the reception of a new data communication package. The CPU
reads the header of the data communication package and decides which form of
process is needed. If the first PU is available for carrying out this process
then the
processing may be initiated immediately. Consequently processing of the data
may be
performed simultaneously to the reception of data from the LAN. At a following
reception of a data communication package from the LAN the data is written to
a main
buffer. The main buffer is configured with a defined limit for amount of data
and in case
the limit is exceeded an interrupt is generate for the CPU, which configures a
new
buffer hereafter.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
43
In a virtual private network (VPN) reception of data communication packages
belonging to a LAN should be avoided. To prevent this an address filter is
implemented, which address filter determines from the MAC address whether the
data
communication packages should be received or not. The address filter may
operate in
a positive or negative mode designating which data communication packages
should
be received and designating which data communication packages should be
ignored.
Configuration of the address filter may be performed dynamically so as to
enable
compatibility with the network configuration used.
Before initiating a transmission the length of the data provided in a field in
the IP
header may be adjusted in accordance with the real length of the data
communication
package. In case of a new length of the data communication package a new ICV
is
calculated and inserted in the IP header. The adjustment of the length value
in the IP
header field may obviously be initiated only when the processing of the data
is
concluded that is that for example the compression of data is complete. If no
compression is applied to the data the transmission may be initiated as soon
as the
first data arrive at the TX-MAC 98b.
Compared to a standard PCI network interface controller card (NIC), the Safe
NIC
product will provided hardware assisted compression/decompression,
encryption/decryption and authentication which makes it possible to provide
full data
confidentiality and authentication without significant reduction in
pertormance - in
some cases even with improved performance due to compression and the on-board
IP
processing.
Key features of the board are:
~ PCI-bus interface compliant with PCI spec. 2.1. 32 bit/33MHz
~ 101100Mbit Ethernet interface. Autosense
~ Support for IPSec. RFC 2406.
~ Support for IPComp. RFC 2393
In a VPN configuration, the board will provide one half of the VPN
functionality. The
interfaces of the board is therefore one to the intranet and one to the
Internet. This
configuration is illustrated in figure 9.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
44
In figure 9, the interface is provided by means of an Ethernet interface but
other
physical interfaces are also possible by - optionally by means of the PCI
interface
although an integrated interface is preferred.
In this configuration, the board is primarily intended for the VPN pro to
provide
hardware based cryptography, authentication and compression. If the two
Ethernet
interfaces are used, all processing between the intranet and Internet is
performed on-
board whereby the PCI interface is not loaded by this traffic - only non-VPN
related
traffic is routed through the PCI-bus to the host system.
A MAC-address filter is provided on the local Ethernet channel in order not to
load the
system with Ethernet frames that are not intended for the VPN processing.
In short, the main features of the VPN-board are as follows:
~ PCI-bus interface compliant with PCI spec. 2.1 32 bits/33MHz.
~ 10/100Mbit Ethemet for local net. Includes MAC address filter.
~ 10/100Mbit Ethernet for Internet access.
~ Support for IPSec (ESP primary, possibly also AH). RFC 2406.
~ Support for IPComp. RFC 2393
Now the hardware design will be defined. The following subsections show the
overall
functional blocks and interconnections. Detailed descriptions of
implementation and
use are explained, and any interfaces are described.
The basic architecture is the same for the NIC as and the VPN board, and will
be
described in common in the following. Figurel0 and figure 11 show the block
diagrams
of the two configurations.
The architecture of the design is based on a number of processing units (PU)
which
performs the processing of the data based on a SRAM memory interface. These
PUs
are Authentication, En/decryption compressionldecompression and a
transmitlreceive
MAC.
Each on these processing units have access to SRAM which provides a virtual
FIFO
between the units - this memory is therefore also denote FIFO-RAM. The SRAM
and
the PUs are accessed by a bus which will be denoted Fifo Bus.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
Note, that for the SRAM for the inbound Internet processing IIP will be
denoted FIFO-
ram for this unit only, the SRAM of the outbound Internet processing IOP will
be
equivalent to external memory for the lIP since it can not be accessed by its
local
5 SRAM-bus.
This bus also provides access to the PC system memory by means of the CPU/PCI
bridge provided by the system controller. Each PU will operate on buffers
(identified by
a start and end pointer) in memory. The accessible memory may be divided in
three
10 sections:
~ System memory is accessible by means of the system controller. Accesses to
system memory should be limited to transfer of data to be transmitted/received
fromlto the host system.
15 ~ SRAM is primarily intended for processing by the PUs. Use of the SRAM for
this
processing will make it possible to process data at wire-speed of the network
connection (100Mbit). The amount of SRAM is limited since it only should be
used
as a temporary processing storage during processing of the datagrams. In the
VPN
configuration, the data should quickly be retransmitted (probably with a new
20 security association) to a new receiver. In the NIC configuration, the data
will be
transferred to/from an upper application layer.
~ Processor memory is intended to be working memory for the local CPU. The CPU
has access to all other memory areas by means of system controller.
25 To gain the maximum performance of the system, the PUs should work in the
local
SRAM.
The configuration of the PUs is based on a processing descriptor (PD) which
contains
all configuration information and may be located on any location in the FIFO-
memory.
30 A part of the PD is indication of source and destination buffers used for
the processing.
Two queue units are included in order to provide an efficient interface to the
CPU. PDs
which are to processed are placed in a queue. The InQueue will then initiate
processing as soon as the relevant PU is available. Similar, the Outqueue unit
will
collect the PDs (represented by a pointer to each) as they are processed by
the PUs.
35 Using these queues provides more efficient use of the CPU as well as the
PUs since
none of them have to wait for each other.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
46
In addition to the local bus is a management bus which is used to perform
communication between the PUs. An important part of the communication is
synchronization between the PUs whereby a pipelined processing may be
achieved.
Since the required processing cannot easily be deduced from the received
datagrams
a processor is provided to perform this analysis and configuration for the
processing.
This processor will also perform management related tasks such as negotiation
and
maintenance of the security association which shall be used for each
individual
connection.
Details about each of the blocks and functions is provided in the following
paragraphs.
Figure 10 shows a block diagram of the NIC-card. This configuration only
consist of a
single Ethernet interface and a single set of PUs. Figure 11 shows a block
diagram of
the VPN. This configuration contains two Ethernet interfaces - one for the
Internet
interface and one for the local network interface. Two sets of PUs is provided
- one for
inbound and one for outbound Internet data processing (IOP) and one for
inbound
Internet data processing (IIP)
Each section has its own memory and dedicated PUs. Configuration and
processing of
the two blocks are also independent.
Note, that the primary data-flow is between the local net and the Internet. In
order to
keep the processing in local SRAM, each set of PUs interfaces to the local
network
and the Internet. This means that the physical interfaces are shared between
the two
PU sets.
Analysis of the IPsec [1], IPComp [2], IPv4 [3J and IPv6 [4J shows that
processing of
the IP datagrams in hardware only will be very complex due to the header
analysis.
A local processor is provided to perform the above mentioned tasks. The use of
a local
processor puts less effort on the host processor and the network adapter will
appear
as 'black box' since the IPsec and IPcomp processing is performed by the board
itself.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
47
The NEC VR4310 [18j and the Galileo GT64115 [19j is chosen as the local
processor
and system controller.
Three memory devices are provided on the board:
~ SDRam which is intended for the program execution on the MIPS processor. The
code from the Flash should be copied to this area in order to provide faster
access
and thereby improved performance compared to the Flash. 16MB SDRam will be
provided on the initial version. This amount might be adjusted.
~ Flash which will provide boot-code for the local processor. This device must
be
programmed as a part of the initial test of the board. Later maintenance may
then
be performed by means of the PCI-bus and/or the local processor itself.
Several
MB may be provided.
~ SRAM is provided for each direction as shown on the block diagram. At least
128KB will be provided for each block in the diagram.
The CPU/Local bridge provides an interface between the device-bus and possibly
the
processor-bus and the FIFO-bus. This unit is additionally arbiter on the local
bus.
The main access types which are translated by this block is:
~ CPU/PCI bus access to the local SRAM
~ CPU/PCI bus access to configuration registers of the PUs and the bridge
itself.
~ Access to CPU-bus/memory by means of source and destination buffer
functionality. This will be implemented by means of DMA. The proccessor-bus
interface may be used as an alternative.
When a PU accesses memory, it may either be directly to the local SRAM which
may
be accessed at random or it may be to the processor memory/external RAM by
means
of a source and destination buffer functionality.
The source/destination buffer functionality may be seen as two independent PUs
which are configured only by means of a register interface and which must be
requested similarly to the other PUs. Two buffer PUs are provided - one for
read
(source buffer) and one for write (destination buffer).
The Buffer PUs can only be used for the source and destination data of the
processing
and thereby not for any configuration. All configuration data must therefore
be present
in the FIFO-RAM.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
48
Note: In earlier versions, it was the intention that memory access should be
fully
transparent by means of the bridge. This is now only the case for source and
destination data. Full transparency may be provided then the system is
integrated
further.
An address filter is integrated as a part of the RX-MAC PU. This filter will
be utilised in
the VPN configuration in order only to process packets which shall be routed
to the
Internet. The processor will thereby not have to analyze packets which are
intended for
the LAN and thereby not tunneling through the Internet.
For the use described above, only the MAC Address filter on the LAN-port will
be
utilized.
The Address Filter can operate in either positive mode or in negative mode. In
negative mode the Address Filter will discard the frame if the Destination
Address
Field in the received frame matches with one of the Destination Addresses
stored in
the Address Filter. In positive mode the Address Filter will discard the frame
if the
Destination Address Field in the received frame do not match with one of the
Destination Addresses stored in the Address Filter. In short positive mode
allows
reception of frames with an address match and negative mode allows reception
of
frames with no match.
The addresses of the filter is maintained by the following commands:
~ InsertAddress.
~ RemoveAddress.
~ RemoveAll.
The address filter operates on the data received from the MAC.
The addresses are stored in separate memory not shown in the block diagram of
figure 11.
The following sections describe the processing units, which may be a part of
the
pipelined operation.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
49
The InQueue is used to implement a queue of PDs which shall be processed. This
makes batch-processing more efficient and it simplifies the entry of a PD for
processing since this is done in a single point accessed by the CPU only.
The InQueue PU will process the PDs on a strict queue basis. Alternatively, it
may be
considered to improve the performance by selecting a PD further down the queue
if
the PU of that PD should be free.
The OutQueue is used to collect PDs in a queue during and after processing.
Two
queues will be provided:
~ A Go-queue which collects PDs where some amount of data has been processed.
This allows the CPU to inspect the result and initiate further processing
although
the processing has not completed yet.
~ A Complete-queue which collects PDs where processing has been completed.
An interrrupt may be generated when one or more PDs are available in the
queues.
Compression is in principle only related to IPComp. The algorithms are listed
in
section
4.4.5 in [6] and are:
~ Zlib deflate algorithm [9].
~ Stac electronics LZS [10].
None of the above algorithms are mandatory.
It is possible to use proprietary algorithms as well.
Both algorithms will use a history buffer which will be provided by separate
memory
not shown on the block diagram in figure 11.
Section 4.4.4 in [6] lists the encryption algorithms which currently are
suggested by the
ESP. Table 1 summarizes these algorithms and the requirements for
confidentiality.
Please refer to [6] for details and references to documents which describes
the
algorithms in detail.
The supported column in tabel 1 indicates whether the algorithm is supported
by the
hardware. Additional algorithms may be supported later.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
Table 2 lists the algorithms which are required by the authentication of
authentication
header (AH) and ESP as defined in [6] section 4.4.3 and 4.4.4:
5 The authentication PU will calculate the ICV and either write the data or
compare to an
existing value.
Additional algorithms may be supported later.
10 The Ethernet interface is provided by a MAC-controller with a MII
interface.
Embedding the MAC instead of using a standard external PCI Ethernet controller
allows a tight integration and thereby an improved pata-path to the PUs.
The block diagrams in figure 10 and figure11 does only define the overall
function.
15 Reset circuits, buffers etc. are not included.
The processing descriptor (PD) is used to configure the PUs. The PD is located
at an
arbitrary location in FIFO memory and has the overall structure shown in
figure 12.
20 The PD is logically divided in sections corresponding to a section for each
PU in the
pipeline Each section is denoted PDS (Processing Descriptor Section).
The NextPUID field wilt be present in (almost) all PDS and indicates which PU
follows
the current in the processing order.
An example of use of the PDs is provided in the following paragraphs.
Figure 13 provides an example of buffer indication in the PD. The desired
processing
is that the payload is encrypted (and trailer is implicitly added). The
authentication
value shall then be calculated for the header followed by the encrypted
payload, and
the result of the authentication shall be added immediately after the
encrypted payload
(special option for authentication).
The example contents of the PDS is illustrated in figures 12 and 13. The
result of the
encryption is written to an 'unused' location in memory, but it could also be
written
directly in the original payload (providing 'that the cleartext payload is not
required -
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
51
even in case of error). Note, that the configuration above results in a
continuos
datagram which could be transmitted if a IP header was added in front of the
ESP
header.
One of the optional functions of the encryption PU is to add the ESP trailer.
To indicate
the final length of the source buffer to the next PU, the pointer to the end
of the ESP
trailer is written to the SrcBufEndPtrfield of the authentication section.
The above example illustrates the buffer configuration. For the processing to
be
successful, one must ensure that data is processed in the correct order. This
is done
by letting a PU signal to the next PU as blocks of data become available in
the
destination buffer. The principle of this signaling is shown in figure 14.
The part above the buffer shows the terminology used for the destination
buffer (i.e.
the data production part of the current PU) and the part below the buffer
shows the
terminology for the source buffer (i.e. the part of the next PU which consumes
data).
The signaling takes place based on the values set for the SBI (Source Buffer
Increment) and DBI (Destination Buffer Increment), and consist of three major
phases:
1. The current PU produces data until DB11 words are available. A Go (first
go) will
then be signaled to the next PU. This will initiate the next PU which then
knows that
SB11 words of data are available.
2. Every time the current PU produces additionally DB12 data, a Go is signaled
to the
next PU. The next PU then increments the amount of data in the input buffer by
SBI2.
3. When the current PU has completed processing, it writes the end-pointer of
the
buffer to the SrcBufEndPtrfield of the next PU PDS. A Complete is then
signaled to
the next PU which now may read the final end of its source buffer from the PD
and
process the remaining data.
Step 1 and 2 may be bypassed if less than DB11 data is produced.
In practice, it is probably easiest to keep account of the available source
data by
means of a source buffer-end pointer (SBE) which is initialized to the
beginning of the
buffer and then incremented during the signaling. On completion, the final end
may be
loaded to the pointer.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
52
For the signaling to the next PU it may be preferred to use a counter which is
loaded
with the DBI value and decremented when data is produced. When the counter
reach
zero, it is reloaded and a Go is signaled to the next PU.
Figure 15 provides a model for an understanding of the synchronization which
is
performed between the PUs. The function of the modules in the drawing is as
follows:
SBE Source Buffer End. This unit keeps track on the end of the source buffer.
When
the unit is started with the first go, it is initialized to SBS+SB11. On the
following
Gos it is incremented by SB12.
When the previous PU is done (complete signaled), the actual buffer length is
read from the PD.
Note, that it is acceptable (although not desirable) to miss one or more of
the
following Gos since the final end of the source buffer is passed.
SBR Source Buffer Read. Pointer to the next data to read in the source buffer.
On
start, this is initialized to SBS and then incremented as data is read by the
PU
core.
VFC Virtual Fifo Count. This is calculated as SBE-SBR and does thereby provide
a
count on how many octets remains to be processed in the source buffer. The
operation of the PU core is controlled by this figure.
DBE Destination Buffer End. Keeps track on where the next data shall be
written.
This value is written in the PD on completion.
DBI Destination Buffer Increment. This block provides the signaling to the
next
PU.The counter is initially loaded with DB11. When the counter reach 0, a Go
is
signaled and the counter is loaded with DB12.
A Go-signaling scheme as illustrated in figure 11 is thereby achieved.
This unit may also be implemented by means of an incrementing counter and a
compare operation against DB11 and DBI2 if this is found to be more efficient.
The DB11 value depends on the typical load on the PUs.
A high value of DBI1 allows the current PU to perform a significant amount of
processing before the next PU is started. If the next PU is busy, this allows
the current
PU to produce a larger amount of data. If however the next PU typically is
idle, the DBI
should be set low in order to start the next PU as early as possible and
thereby reduce
latency.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
53
The values of the S811 and S812 for each PU is stored in registers of each PU.
A part
of the configuration of the PUs is to read this register from the next PU in
order to
determine the DB11 and DB12 values which will be used for this PD.
PU operation and state machines (SM) provides further details about the
behavior of
the PUs by means of state machines (SM).
The description is based on PUs which consumes data from a header and a source
buffer and produces data to a destination buffer. This does not apply for all
PUs, and
their state machines will therefore be simplified accordingly.
The initial state of all state machines is the Idle state. This state shall
also
unconditionally be entered if a Reset is signaled to the PU.
In order to simplify the transition conditions, they are numbered: "1:
Condition" the
transition with the lowest number always has the highest precedence and shall
be
issued if it is true.
A PU main state machine (MainPU) is the main state machine of the PU which
controls the processing and overall operation. Figure 16 shows a block diagram
of the
MainPU and table 3 provides states and activities of the MainPU.
A Source Buffer End and VFC control (SBECtrI) keeps track on the current end
of the
Source buffer (SBE). The SBE is dynamically increased as Go signals are
received
from the previous PU. From the SBE, the VFC may be calculated as the
difference
between the SBE and SBR as shown in figure 17. Further table 4 lists state and
activity of the SBE.
Since the final SBE is set when a complete is received from the previous PU, a
loss of
one or more Go is acceptable, but it will increase latency since the PU will
lack the
previous PU with more data.
A Destination buffer control and signaling (DBICtrI) shown in figure 18
controls the Go
and Complete signaling to the next PU. This SM does also implement the
request/grant protocol since the next PU must be granted before Go or Complefe
can
be signaled. Table 5 lists state and activity of DBICtrI.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
54
This SM additionally handles the Sync signal which is issued if this PU will
be the
producer of data to a next PU. This allows additional processing to be
initiated 'on the
fly'.
The ReqPU sub-state machine (SSM) will requestlarbitrate the next PU. The
arbitration protocol and ReqPU state machine is further described below.
A Signaling status (SigStat) shown in figure 19 is a simple state machine
which
monitors the progress/signaling state of the previous PU. States and
activities
of SigStat is listed in table 6.
The FIFO-bus interface of the PUs is intented for the actual data-transfer.
The
source/destination for these data-transfers is typically the FIFO-memory, but
may also
be access to registers or access to external memory. The type of access as
well as
the signaling is communicated by means of a management bus.
The ownership of the management bus always follows the ownership of the local
bus.
The default transaction on the FIFO-bus is access to FIFO-memory which will
take
place unless register-access or external access explicitly is indicated on the
management bus.
The control unit (CU) also operates as a device on the management bus and
allows
the CPU to perform signaling on the bus.
An overview of the management bus and the attached PUs and the CU is shown
figure 20.
The management bus is synchronous and consist of three signal groups (and
clock):
MSource This is the source of the bus-transfer which is controlled by the CU
only. Each
PU (and the CU) has a unique identifier (PUID) which is used for selection.
The PU indicated by MSource has the mastership of the bus for the active
clock period and must drive the MTarget and MData. All other units must tri-
state their drivers on these signals.
It may be considered only to drive the bus in the 2"d half of the clock period
in
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO DO/30262 PCT/DK99/00625
order to avoid multiple drivers during the Source decode phase.
MTarget The owner of the bus indicates the target for the management
data/command.
The Target shall respond on the MResult line with an indication of the result
of the transaction.
If no signaling shall take place and no logical PU exist for the transaction
(fx.
a simple access to FIFO-ram), the PUNorre may be used.
MData The owner places the data on these lines. These indicate the actual
signal/command.
MResult The result of the bus-cycle management command is indicated on this
bus
which is driven by the PU identified by MTarget.
The MSource is exclusively driven by the CU. Ownership of the bus is
determined by
an arbiter in the CU. Each PU has a request signal indicating that it wants
ownership
of the bus.
5
The arbitration is essentially based on a timeslot for each PU. If a PU is not
requesting
the bus, it is bypassed and the 'next' PU in the sequence will grant the bus.
A more
intelligent arbitration may be considered in order to reduce signaling
latency, but the
benefits will probably be limited.
A detailed description of the signaling/datatransfer on the management bus is
provided
below regarding management bus signalling.
The FIFO-bus is very similar to a typical asynchronous SRAM-bus consisting of
the
following signals.
Address Indication of the address for the access. This may be interpretated as
a
register address of a FIFO-memory address.
Data Data for the transaction. The driver of this bus depends on the Rd L and
Wr L signals.
The current inplementation uses a 32 bit databus and does only support 32
bit data-access.
Rd_L Active low read signal.
Wr_L Active low write signal.
Each transaction on the FIFO-bus is completed within one clock cycle.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
56
Interrupts is the way the PUs signals a need for attention from the CPU. Two
basic
types of interrupts are provided:
~ Fatal interrupts which are issued on errors which makes continuation of
processing
impossible/insensible. The PU will typically stop processing and hold the
interrupt
active until the cause has been resolved or the PU has been reset.
~ Service interrupts which is issued as an integrated part of the processing.
Only the
OutQueue is able to generate such interrupts.
A register allows the software to quickly identify which interrupts are
pending and take
the appropriate action.
In case of an error, the SM must examine each of the PUs and resolve the
error.
Typically it will be necessary and probably easiest to 'clean up' the entire
pipeline in
order to start processing from a well-defined state.
Each PU will have registers defining its internal state. These registers will
be inspected
by the CPU to determine the cause of the interrupt and appropriate actions.
in the current implementation, the interrupt fines on the CPU are used
according to
table 7.
The CPLD provides glue-logic for the board and provides some debugging
facilities.
The UART allows attachment of a terminal which may be used during the test
phase of
the design.
Below describtion provides an overview of the memory organization in terms of
base addresses for various sections.
Care should be taken in connection with the configuration of the cache in the
processor.
The FIFO-ram area should not be cached since transactions are not propagated
to the
processor bus and the cache thereby not will be consistent.
Care should also be taken if the PUs are configured to operate in the SDRAM
memory
where consistency problems also may appear in case of write-back caching.
SUBSTITUTE SHEET (RULE 26j
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
57
Little endian is used for all registers/memory.This means that the least
significant byte
is at the lowest address. In processor memory mapping all memory areas are
controlled by the system controller which provides large flexibility regarding
their
location in the processor memory space. See [19] for details.
Table 8 lists the allocation of Chip-selects
The memory area of the FPGAs wilt consist of two major blocks:
~ FIFO-Ram which provides a direct access to the SRAM attached to the FPGA.
The
lower 2MB of the addresses are used for this purpose.
~ Register area. The upper 2MB block is used for this area.
Address bit 21 will be used to determine which area to access. This provides
2MBytes
for each area with the F1F0-ram at the lowest addresses. This will also mean
that the
areas will be mirrored if more than a 4MB window is allocated for this
purpose.
Regarding the PU memory map/view, the PUs shall primarily work in the local
SRAM,
it is however possible to have the source or destination buffer outside this
scope. Use
of external memory is indicated with dedicated bits in the PD.
Access to external memory is only allowed for:
~ Source bufferJheader where start and end pointer is defined - i.e. the
source data
may not be provided dynamically by a previous PU since the length is not known
until processing is complete.
~ Destination buffer.
Since the access to external memory is provided by the source and destination
buffer
of the bridge is it only possible for one PU to have read access and one PU to
have
write access at a time.
The above limitations implies that all configuration data (PDs, keys etc.)
must be in the
SRAM.
The actual access to external memory is pertormed by bridge-blocks which may
utilize
DMA or busmastering on the processor bus in order to perform the transfer.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 80/30262 PCT/DK99/00625
58
The PCI-interface is based on the Pajero system controller which provides a
bridge
between the PCI interface and the processor- and device-bus.
Access to external memory - including PCI-memory - is provided by means of the
BridgeRead and BridgelNrite PUs.
The BridgeRead and BridgelNrife will be arbited by a PU when it has a buffer
located
in external memory. After configuration of the entities, they will initiate a
DMA-transfer
and provide/consume the data from the PU.
The DMA-transfer may be to the local memory - such as SDRam or it may be to
the
PCI-bus whereby memory in the host system can be accessed.
Configuration of PCI space provides good flexibility regarding which memory-
spaces
should be present/configurable in the PCI configuration space.
See [19] for details.
Use of the Power-management configuration registers and boot-rom may be
considered.
The register regions in the register space consist of blocks of 256 words (8
word
address bits) - one block for each PU or other functional block. The order of
the blocks
for the PUs is determined by their PUID.
As mentioned earlier, address bit 21 is used to indicate access to the local
FIFO-ram
or register access. This results in the fields of the address fields listed in
table 9.
Common registers listed in table 10 are registers which are common to most
PUs.
Some of the above registers are described further in the following sections.
The
addresses are defined in the VHDL-files.
For the signaling of more data to make sense between the PUs, it is obvious
that:
CurrentPU.DBl1=NexfPUID.SBl1 and CurrentPU.DBl2=NextPUID.SBl2, it is therefore
only the SBI values which are stored for each PU since the destination DBI
easily may
be derived when the next PU is known.
SUBSTITUTE SHEET' (RULE 26)
CA 02350424 2001-05-11
W0 00/30262 PCT/DK99/00625
59
SB11 and SB12 are each represented by 8 bits as defined in table 11. The
fields define
the counter values in increments of 32 bits. It should be noted that at least
the
specified amount of data must be available before signaling of Go.
For proper signaling, it is required that SB12>0, but it is acceptable that
SB11=0 - this
will simply result in an immediate activation of the next PU.
Detailed configuration and operation information is decribed below in regards
to data
structures and registers of the board which are used for programming.
The table 12 lists identifiers - PUID - of all the PUs. These are used to
identify the
PUs and other units on the management bus and for identification in the PDs.
The (*) marked rows in table 12 are not implemented in the FPGA, but might be
included in ASIC - probably by means of a dedicated processor. These units
will
perform analysis of the header/decrypted data and setup processing. This task
is
currently performed by the local processor.
The following sections describe the signals which may be send on the
management
bus - first in terms of all the available signaling, and then sections which
defines
signaling protocols for specific purposes.
Refer to description above for a general description of the management bus.
The table 13 gives a signal overview, which defines the currently identified
signals to
be transferred on the management bus. For all commands except ExtMemAcc and
RegAccess, an access to the FIFO-memory will also take place. NOP transactions
on
the bus may be generated by deasserting Rd L and Wr L. Each command has a
source which always is the active master of the local bus and a target. Each
is
identified by their PUID. The command is identified by 4 bits.
The result/status of each commandlsignal is indicated by the target by one of
the
results listed in table 14. Note in table 13, that RegAccess and ExtMemAcc can
be
interpreted as a cycle-modifier on the local bus to force a register access or
read/write
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
to external memory. All cycles where one of these signals are not present will
be
interpreted as access to the FIFO-ram.
The identifiers of the source and target for the PUs follows the PUID.
5
The Control-unit provides a bridge between the Device-bus and the
FIFO/Management bus. The following access may be performed by the CPU:
~ CPU-access to the FIFO-ram. This is provided by means of a 2MB window.
~ CPU-access to registers. This is provided by another 2MB window.
10 ~ CPU-generated management bus cycles. These allows the CPU to reset and
resume individual PUs.
The request/arbitration of a PU is required before the actual processing of a
PD can
start. Since (almost) all PUs can request another PU, it must be ensured that
only one
15 grants the ownership and writes the PD pointer to the PDPtr register of the
next PU.
This requestlarbitration is achieved by means of the PUReq signal and the
following
result based on the following rules:
1. Any PU may send a PUReq (providing it actually wants the PU).
2. The target PU of the request will reply with an OK status if it can accept
the
20 request otherwise it will reply with Busy. The requesting PU uses this
status to
determine whatever the request was acknowledged or not.
A state machine (PUReq) which requests a PU according to the above rules is
shown
in figure 21 and the actions in the states are listed in table 15.
The target PU must obviously always respond to the PUReq signal. A OK will be
the
response if the PU is ready to process a new PD - otherwise the response shall
be
Busy.
Below describtion describes the processing descriptor (PD). The PD consist of
a
number of sections (PDS) where each section contains configuration data for a
PU.
The following sections provides an overview, further details are available in
the
specifications of each of the processing units.
The tables 16, 19 to 40, 42 to 53 and 55 defining the contents contains a
'type' column
which indicate who are intended to write to the field.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
61
Most of the PUs have some kind of source data and destination data. The source
data
may be represented as a header section and a source buffer. Splitting the
source data
in a header and a source buffer allows a fixed image to be used without the
need for it
to be continuous with the remaining data to be processed.
The matrix in table 17 outlines the differences in the handling of the header
and source
buffer.
A source buffer end pointer is written to the PDS section of the next PU when
the
current PU has completed processing. Passing the end of the buffer in this way
makes
it possible to setup a pipelined processing although it may not be possible to
predict
the resulting length of the output data when the processing is initiated.
The buffers is represented by a pointer to the first word and - in some cases -
a
pointer to the last word/octet. A buffer is empty if the start address is
greater than the
end address.
All read- and write operations is performed in units of 32 bits on aligned
addresses (i.e.
bit 1..0=00). Unaligned access does therefore add complexity to the hardware.
The
requirements regarding the alignment is defined in the matrix listed in table
18.
Since all headers seem to be an increment of 32bits, it should not be a
problem to
require alignment of header start and end. The start of a buffer should also
be aligned
whereas the end does not need to be aligned. It should be noted that the end
of the
buffer does not need to be aligned. Such a requirement would also require the
length
of the buffer to be an increment of 32 bits which would not be acceptable.
It should be noted that a full 32 bit write operation will take place at the
end of the
buffer although 32 bits of valid data might not be present. The remaining bits
are
therefore undefined.
The IP-header adjustment in connection with transmission is one exception
since
fields smaller than 32 bits needs to be adjusted in the header. A read-modify-
write
operation is used for this purpose.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
62
To simplify the following description, fields which are common to most of the
PDS are
described in table 19 and 20.
NextPUID3..0 Indication of the next PU in the processing order.
HdrExt The header is located in external memory. Does only apply if a header
is used by the PU.
SrcExt The source buffer is located in external memory.
DestExt The destination buffer is located in external memory.
Since some information always is required and some information needs to be
passed
from one PU to another, a number of fields have a fixed offset within the PDS.
These
fields are located in the beginning of each PDS and are listed in table 21.
To simplify the following description, fields which involve encryption PDS are
described in table 22 and 23.
ESPTrail 1: ESP trailer (Padding and Next header field) will be added as input
to
the encryption processing. The trailer will not be written to the source
buffer.
IVCopy 1: The initialization vector is copied to the destination buffer as the
very first data.
0: The initialization vector is not copied to any location.
1: The last block of data (typically 64bits) is written back to the IV-field
of the key-section. This provides an easy way to implement a reuse of
the last encrypted data as the initialization vector for the next
datagram.
0: The last data is not written to other locations.
NextHdr7..0 Value of next header field in ESP trailer.
PadLen7..0 Minimum padding length. 0 will add as little padding as possible.
Note: It must be possible to generate padding which at least is as long
as PadLen. This field should therefore not be set higher than 256-
BIockLen, where BIockLen is the block length of the encryption
algorithm.
It is recommended to set this field to 0 unless it is desired to hide the
actual payload length.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
63
The HW will not notify in case of illegal setting.
To simplify the following description, fields which involve decryption PDS are
described in table 24 and 25.
ESPTrail 1: ESP trailer (Padding and Next header field). When set, the ESP-
trailer will not be included in the destination buffer and the NextHeader
field will be extracted and written to the Status field
IVWB 1: The last data being read will be copied to the IV-field in the key
section. This allows continuation on a fragmented datagram.
0: The last data will not be written to any additional location.
IVSource 1: The first block of the data is used as initialization vector
(typically 64
bits).
0: The IV field of the key section is used as initialization vector.
NextHdr7..0 Value of next header field in ESP trailer.
PadLen7..0 Maximum expected pad-length.
Since the actual payload length is unknown until the padlength field is
decrypted, the PU will not report the last MaxPadLength+2 octets
ready to the next PU until the pad-length is determined.
A conservative setting is 255.
A optimistic setting assuming that no unnecessary padding is present
is BIockLength-1, where BIockLength is the block length of the
encryption algorithm.
See the detailed description regarding ESP trailer handling below for
details.
The KeyPtrfield of the PDS is used to reference a block containing keys and
initialization vectors. This is an efficient way to indicate the keys which
typically will be
reused for many datagrams (depending on the parameters of the security
association).
It also provides an efficient passing of initialization vectors.
The block contains the fields listed in table 27.
Care must be taken during handling of an ESP trailer, since the en/decryption
operation will typicGlly require that the data is some increment of a given
block size in
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
64
order to operate correctly. In the ESP specification [8), this problem is
solved by
adding padding in the end of the payload as illustrated in figure 22.
Since the length of the cleartext not necessarily can be predicted (for
example if it is
the result of compression), the software is not able to generate the padding
and place
the Next Headerfield correctly before the compression is complete. It is
therefore
desirable to have the padding and Nexf Header fields generated automatically
since
the processing otherwise would need to be stalled and resumed when the padding
is
added by software.
Similarly, it is desirable that the decryption algorithm only reports the
actual amount of
payload data to the next PU. The Next Header field is passed as a part of the
status
information in the PD, but may also be read from the destination buffer.
This hardware support does thereby provide a trailer handling without any
intervention
from the software.
During trailer generation in connection with encryption, it is decided not to
write the
contents of the generated fields to the source buffer because:
~ They will probably not be required for by any other processing.
~ They would be added to the source buffer of the encryption unit. This will
be
inpractical if the source buffer is a payload located in system memory which
not
necessarily has space for the additional data. This will typically be the case
if the
data is supplied directly from some upper application layer in the protocol
stack.
~ It would break the general rule of the source buffer being read only and the
destination buffer being write only.
The above functionality is specific for the ESP and will probably not be
usable for any
other protocols. The padding is an incrementing sequence of bytes starting at
1 as
defined in [8).
Although it probably generally is desirable to have as little padding as
possible, it is
possible to specify a minimum amount of padding for the encryption
(MinPadLength).
A similar field exist for the decryption (MaxPadLength). This field must be
present for
the decryption since the padding may not be passed to the next PU. This field
thereby
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
determines how many octets will be hold until the decryption is complete and
the
actual padding length is known.
It may be considered to perform padding verification on reception.
5 Authentication involves calculation PDS. To simplify the following
description, fields
which involve calculation PDS are described in table 28 and 29.
AIgID3..0 Authentication algorithm identification
KeyPtr Pointer to block with specific information for the authentication.
AuthStartPtr Start location of authentication value if AuthAppend=0.
AuthApp 1: Append authentication value to the end of the source buffer (i.e.
SrcBufEndPtr)
The SrcBufStartPtr of the next PU will be updated with the address of
the octet immediately after the authentication value.
0: Write the authentication value to location indicated by
DestBufStartPtr
Although the Authentication calculation unit does not have an explicit
destination
10 buffer, it shall behave as it had regarding signaling to the next PU. This
includes:
~ Perform arbitration of the next PU
~ Signal go to the next PU as data become available in the source buffer. This
may
be done by signaling go as data is being read.
~ Write the end of the source buffer - possibly including the authentication
value if
15 AuthApp=1 - to the SrcBufEndPtr field of the PDS of the next PU.
~ Signal Complete to the next PU.
This allows the next PU (fx. Ethernet transmission) to process data as soon as
they
are valid.
Furhter fields which involve verication PDS are described in table 30 and 31.
AuthStartPtr Start location of authentication value if AuthAppend=0.
AuthAppend 1: Authentication value is located at end of source buffer. (i.e.
Src8ufEndPfr)
0: Authentication value is located at AufhStartPtr.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 90/30262 PCT/DK99/00625
66
Although the Authentication calculation unit does not have an explicit
destination
buffer, it shall behave as it had regarding signaling to the next PU. This
includes:
~ Perform arbitration of the next PU
~ Signal go to the next PU as data become available in the source buffer. This
may
be done by signaling go as data is being read. If AuthApp=1, the
authentication
value shall not be regarded a part of the source buffer and may therefore not
be
included in the go-signaling.
~ Write the end of the source buffer. If AuthApp = 1, the authentication value
may not
be included in the end pointer value.
~ Signal Complete to the next PU.
This allows the next PU (fx. data decryption) to process data as soon as they
are valid.
In interrupt shall be generated if the authentication verification fails. The
processing
will stop to allow the CPU read the PD and take further action. It may be
considered to
indicate the failure in the PDS. This will reduce the overhead of the CPU in
case of
excessive authentication failures. This policy would however require that the
software
inspects the result of the result of authentication.
The authentication algorithm configuration involves a detailed configuration
of the
encryption and decryption algorithm, which is performed in a separate block
indicated
by the ConfPtr in the two authentication PDS. Table 32 and 33 list possible
configurations.
AIgID3..0 Authentication algorithm identifier. TBD
AIgOpt7..0 Further options for Authentication algorithm configuration. TBD
BIkLen2..0 Length of authentication check value. The length is given in
increments of 32 bits.
This value may be given implicity by the AIgID field in which case this
field is ignored.
BeginConf Configuration to perform before beginning of calcuation:
0: Do not perform configuration before start (used for continuation).
1: Do perform a complete configuration before start.
EndConf Configuration/state writeback after completion.
0: No action
1: Write internal configuration to Config field. Used to store state for
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO-00/30262 PCT/DK99/00625
67
continuation on a new buffer.
Key Key for the authentication algorithm. Interpretation and size depends
on the AIgID field.
Config Internal configuration data for the authentication algorithm. Use is
controlled by the StartConf and EndConf fields in combination with the
authentication algorithm.
To simplify the following description, fields which involve compression PDS
are
described in table 34 and 35.
AIgID3..0 Compression algorithm identifier.
Set to 0 for LZS.
AIgOpt7..0 Options for compression algorithm. Interpretation depends on AIgID
field.
None is defined for LZS.
Init 1: Perform full initialization of compression algorithmlhistory window
for LZS (i.e. 'empty history window}.
0: No initialization - typically used for continuation where the existing
history window is reused.
CompDet If 1, the first part of the compression will be monitored.
This PU does also provide support for an end indication of the destination
buffer. If the
destination data should exceed the destination buffer, an interrupt will be
generated.
This end indication may be used to detect if the compression of the data
results in an
expansion.
CompDet is used to enable a compression detection and determine if data should
be
compressed or not. If sufficient compression is achieved, all data will be
compressed
and written to the destination buffer starting at DestBufStart!'tr. If the
compression is
insufficient, all data will be copied to the destination buffer now starting
at
AItDestBufPtr. In addition the AItTxConfig will be copied to the Confrg8ase
field of the
Ethernet transmit PDS. Copying this field allows a pipelined transmission of
the frame
since the length can be predicted when compression is not being used.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
68
Use of the alternate destination buffer start allows fx. the compression
header to be
overwritten. The remaining processing can thereby take place without further
configuration from the CPU.
If CompDet is set, Go will not be signaled to the next PU until it is
determined
whatever the compression is sufficient (and - obviously DB11 data are
available).
The compression criteria is configured by the register interface of the
compression PU.
To simplify the following description, fields which involve decompression PDS
are
described in table 36 and 37.
AIgID3..0 Decompression algorithm identifier. TBD
AIgOpt7..0 Options for decompression algorithm. Interpretation depends on
AIgID
field. TBD
Init 1: Perform full initialization of compression algorithm.
0: No initialization - typically used for continuation.
The end-pointer for the destination buffer is primarily intended to avoid that
the
allocated memory is being overwritten. If the output data should exceed the
destination
buffer, it is possible to resume the decompression with a new buffer
configuration.
The InQueue and OutQueue are PUs which provides administration of PDs which
are
to be processed, are partially processed or which have been completed. The
Outqueue is also an important part of the PD allocation since it collects
completed PDs
which will be used by the Ethernet receive PU on reception of Ethernet frames.
The PD, register interface and operation of the InQueue is defined below.
f3egister interface
In order to avoid the problems related to mutual exclusion of the in queue
maintenance, new PDs to be inserted in the queue are added by writing the
pointer to
the PD to the queue register defined in table 38.
The HW will perform the maintenance of the queue. The Link field in the
beginning of
the PD is used to link the PDs.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
69
To simplify the following description, fields which involve inqueue PDS are
described
in table 39 and 40.
The PrevPU field is used to indicate which PU - if any is providing the data.
This field
is used only if synchronization with the previous PU is required. In this
case, it must be
ensured that the previous PU is either processing the data or that it has
completed the
processing of the PD (in which case the PrevPU field is redundant, and may be
set to
NoPU).
The processing of the PDs in the queue may be divided in two cases:
~ All Source data are ready for processing. This is typically the case if some
data is
to be transmitted from some upper application layer.
~ A previous processing unit is generating data. In this case the startup of
the next
PU requires special care since the PUs has not been synchronized from the
start.
It must be ensured that at least SB11 data is available for the Next PU before
the
PD is entered in the queue. This case typically applies to processing of
Ethemet
frames where the processing cannot be determined until the header is
available.
This may also apply to decryption and decompression where further processing
may start as soon as the header is revealed.
Each of the cases are detected by the hardware and handled as defined below.
Activation of the Next PD is controlled by the state machines shown in figure
23 and
the states for InQueue9 are defined as fisted in 41.
The InQueue2 state machine is used to monitor the state of the previous PU in
order
to detect whatever it has initiated processing of a new PD since InQueuel was
in the
LoadPUID state.
The PD, register interface and operation of the OutQueue is defined below.
Outqueue actually consist of two queues: a Go and a Complete queue. A PD is
placed
in the Go queue on the first Go (for each PD) and a PD is placed in the
Complete
queue on complete signaling.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
A PD is collected in the queue simply by indicating OutQueue as the next PU.
It is possible to configure whatever an interrupt shall be asserted when one
of the
queues contain PDs.
5 The Go queue is intended for the CPU to examine the first part of output
data in order
to determine the following processing of the data. The SBI1 value should be
set
accordingly for this purpose.
10 The OutQueue is used to collect PDs. New PDs are always appended to the end
of
the queue. Two registers are used for maintenance of the queue and these are
listed
in table 42. The format of the Addresslpointer field is listed in table 43 and
44.
GoEnb and ComplEnb are used to enable the Go and Complete queue. When the
15 queue is disabled, no PDs will be added.
Golntr and Compllntr are used to enable interrupt for the Go and Complete
queue. If
interrupt is enabled, it will be asserted as long as there are PDs in the
Queue.
20 GoRdy and CompIRdy indicates whatever the next element of the queues may be
read. This bit must be cleared before a valid read of the queue can take
place.
It is important to note, that scheduling a PD which is being processed in the
Inqueue
might imply that the final complete is not signaled to the Outqueue. This is
because
25 the active PU is forced to signal to an other PU in case of a sync command.
The outqueue only contains a field for the SrcBufEnd and a link field for the
Go queue.
The link field of the general section of the PD is used for the Complete
queue. Offset,
30 size, type, name and description is listed in table 45.
Below a detailed description of the Ethernet and address filter is provided
starting with
Ethernet transmission and IP compensation PDS. This processing unit provides
two
functions:
35 ~ IP header compensation. A length field may be written and a checksum
according
to IPv4 may be calculated.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO AO/30262 PCT/DK99/00625
71
~ Transmission of Ethernet frame. Some of the fields may be generated
automatically or the raw frame may be transmitted.
The PDS is listed in table 46 and 47.
IPChk 1: Checksum will be calculated on the header section and written
according to the IPv4 specification.
0: No checksum will be calculated and written.
A read-modify-write cycle is used to write the checksum.
IPLenCalc 1: The length field is calculated based on the transmitted data:
HdrEndPtr-HdrStartPtr+SrcBufEndPtr-SrcBufStartPtr + 2
0: The length is set to the value specified by Length.
IPLen 1: Datagram length will be written starting at location
HdrStartPtr+IPOfs.
0: No datagram length will be written.
The length field is 16 bits and is written by means of a read-modify-
write cycle, other PUs may therefore not have access to the header
while this PU is active.
IPOfs Offset relative to start of header indicating where length shall be
written as defined above. This field provides flexibility in the location
and may thereby be used for IPv4 and IPv6.
This is a byte-offset
LenT 1: The length field of the MAC frame is written based on the MAC-
payload length.
0: The value of the type is written to the type field of the MAC-frame.
DestAddr Destination MAC address of frame.
Pipelined transmission may take place if all data of the IP header is
available
otherwise transmission will not start until the final length is known. In case
of
transmission errors, an interrupt will be generated and further transmission
will be
suspended. The CPU must resolve the situation.
The Ethernet frame generation is described further in figure 24. The frame may
either
be passed as raw data including all the fields, or the hardware may build the
frame as
defined by the PDS. The interpretation and generation of the fields is as
follows:
SUBSTITUTE SHEET (RULE 26~
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
72
Preamble Bit sequence used to synchronize reciver.
SFD Start Frame Delimiter. Indicates start of frame.
Dest addr Destination MAC address of frame. This field is read from the
DestAddr field of the PDs.
Src Addr Source MAC address.
Length/Type This field has two interpretations: Either a length indication of
a type
indication.
LenT determines whatever a specified value shall be written or the
value shall be the length of the payload.
Payload Payload which consist of the header data followed by the source
buffer.
PAD This field shall be added for short frames.
FCS Frame Check Sequence. 32 bit CRC calculated on the MAC-frame.
For further details, refer to [17].
The interface to the MAC-controller is provided by transparent registers.
The Ethernet Receiver PU must always be able to receive data. A special buffer
arrangement is therefore provided. A register interface allows the CPU to
define a
memory space (in FIFO-memory) where received data shall be written. On
reception
of a PD, a PD will be fetched from the complete queue and the start, of the
buffer will
be written. When DB11 of Outqueue words have been received, it will be placed
in the
Go-queue for analysis by the CPU. When the entire Ethernet frame has been
received, Complefe will be signaled.
The reception of the next Ethernet frame will continue from the next word in
the
receive buffer. Two limits are defined for the buffer: An early warning limit
which
generates an interrupt to the CPU. This allows the CPU to configure a new
buffer
before the 'end limit' is reached. Writing will not take place beyond the end
limit.
The PDS of the Ethernet receiver is defined by tables 48 and 49.
NextPUID3..0 This field is initially ignored since the destination on the
first go always
will be Outqueue.
The software may configure this field according to the required
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
73
processing. This field will then be written when the PD is placed in
InQueue.
The MAC address of the transmit and receive section of the two processing
blocks are
defined by the registers listed in table 50.
Ethernet frames with the configured address will always be received
independently of
the Address filter configuration.
The transmit MAC address is added to frames which are transmitted.
Configuration of Receive MAC Address filter is performed by controlling the
address
filter by means of 2 registers to represent the MAC address and to provide
status/control information. Tables 51 and 52 list the registeres and controls.
CMD2..0 Command:
000: No operation
001: Insert address specified by the MACO register and MAC47..32 of
this register.
010: Remove address specified by the MACO register and MAC47..32
of this register.
011: Remove all addresses in the filter
No command may be issued while the Busy bit is set.
Mode Sets the operation mode of the filter:
0: Negative mode
1: Positive mode
Busy Indicates whatever a maintenance (Initiated by CMD) operation is in
progress:
1: Address filter maintenance is in progress
0: Address filter maintenance has completed.
New command may not be issued while this bit is set.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
74
The bridge provides access to external memory by means of a source and
destination buffer functionality. This is the only way the PUs can access
external memory.
The source and destination buffer are similar to the other PUs, they just lack
a PDS
and does not perform any processing themselves.
Configuration is performed by means of registers and read/write of data is
performed
by use of the ExtMem command. The following status of the cycle will indicate
whatever the transfer was successful or not.
All read- and write access is performed as a complete word. The lower two bits
of the
address is therefore ignored during addresssing, but they are included in the
determination of the byte level end of the source buffer.
The register interface and detailed operation is provided in below
description.
Source buffer register interface
The registers listed in table 53 are provided for the source buffer.
~,ource buffer operation
Before operation of the source buffer can start, it must be granted and the
start and
end address must be configured. The read operations are performed with the
ExtMemAcc command. The result may be one of the listed results in table 54.
The buffer will automatically be released (ready to be requested by another
PU) when
the end of the buffer has been reached.
Destination buffer regl is ers
The registers listed in table 55 are provided for the destination buffer.
Destination buffer op. re ation
The destination buffer must be granted and the start and end address must be
defined
before processing can start.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 60/30262 PCT/DK99/00625
The write operations are performed with the ExtMemAcc command. The result may
be
one of the results listed in table 56.
In opposite to the Source buffer, the destination buffer is not released
(ready to be
5 requested by another PU) when the end of the buffer is reached. This allows
an easy
'resumption where the BufEnd register is rewritten and writing to the buffer
may
proceed.
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
76
References
[1] IPSec, IP Security. Security Architecture for IP. RFC 2401
[2] IPComp RFC2393
[3] IPv4 Internet protocol version 4. RFC0791
[4] IPv6 Internet protocol version 6. RFC2460
[5] Conference papers provided by Kasper Langkilde.
[6] IPsec DOI: IP Security Domain of Interpretation. RFC 2407.
Provides further details about the requirements to the associations which are
established for IPComp and IPSec.
[7] IP Authentication Header. RFC 2402.
[8] IP Encapsulation Security Payload (ESP), RFC 2406.
[9] IP Payload compression using Deflate, RFC 2394
[10] IP Payload compression using LZS, RFC 2395
[11 ] Deutsch, P. Deflate compressed data format specification version 1.3.
RFC 1951.
[12] ANSI, American National Standards Institute, Inc., "Data Compression
Method for
Information Systems," ANSI X3.241-1994, August 1994. Describes the LZS
compression/decompression algorithm.
[13] PCI specification 2.2
[14] The ESP DES-CBC Cipher Algorithm, RFC 2405.
[15] IDT79RC32364 RISC Controller Hardware Users Manual, Version 1.0, Aug 98.
[16] IDT79RC32164 RISCCore 32300 Family system controller chip. Hardware
reference manual. Version 1.0 March 99
[17] IEEE 802.3, 1998 Edition. Part 3: Carrier sense multiple access with
collision
detection (CSMA/CD) access method and physical layer specifications.
(18] NEC VR4310 User's Manual. NEC Corporation Document No.
U10504EJ5VOUM00 (6~" edition), June 1999
[19] Galileo GT64115. Datasheet Revision 1.0 July 1, 1999.
Abbreviations
AH Authentication Header
ESP Encapsulated Security Payload
SUBSTITUTE SHEET (RULE 26)
CA 02350424 2001-05-11
WO 00/30262 PCT/DK99/00625
77
FSM Finite State Machine
IPSec IP Secure
LAN Local Area Network
NIC Network Interface controller/card. Also used to denote the NIC option
of the board.
SA Security Association
VPN Virtual Private Network Also used to denote the NIC option of the
board.
Abbreviations created for this document:
CU Control Unit
DBE Destination Buffer End (pointer)
DBI Destination Buffer Increment. Figure indicating how many data a PU must
produce
before Go can be signaled to the following PU.
DBS Destination Buffer Start (pointer)
IIP Internet Inbound Processing. Usually refers to hardware dedicated to the
processing c
data received from the Internet.
IOP Internet Outbound Processing. Usually refers to hardware dedicated to the
processinc
data to be transmitted on the Internet.
MAC Media Access Control
PD Processing Descriptor
PDS Processing Descriptor section. A section of the PD which configures a
given PU.
PU Processing Unit (such as compression, encryption etc.).
PUID Processing Unit Identifier, for example used in the PD.
SBE Source Buffer End (pointer)
SBI Source Buffer Increment. Increment value for each go. Divided in first and
following g
signals.
SBS Source Buffer Start (pointer)
SM State machine (effectively a FSMIFinite State Machine)
SSM Sub State Machine
VFC Virtual FIFO Count
SUBSTITUTE SHEET (RULE 26)