Note: Descriptions are shown in the official language in which they were submitted.
CA 02352001 2001-06-29
Method for Carrier Class Voice Security Token
FIELD OF THE INVENTION
This invention relates to a method or process for a carrier class product
which permits a
user initiated, voice transaction security mechanism.
BACKGROUND OF THE INVENTION
Despite ever-increasing usage of the Web, companies still receive more than
70% of their
orders through the appliance their customers prefer: the telephone. This
reflects both the
l0 ubiquitous nature of the telephone and the fact that customers remain
comfortable with, and
accepting of, the telephone as the primary tool in the conduct of business.
Yet, voice transactions conducted via the telephone lack the fundamental
guarantors of
security and data integrity which we have come to expect from other-means of
electronic
transactions. There currently exists no method for a telephone user to
initiate the recording,
15 storing, and securing of a voice transaction conducted over the telephone.
Furthermore, there is
no structured process in place to conduct dispute resolution when voice
transactions do not occur
as understood by both parties.
In financial services, the majority of voice transactions are not recorded. If
a dispute
should occur, then it is up to the customer to phone-in a complaint, which
becomes a "your word
20 against mine" situation. There are some brokerages that record
transactions, but do not offer
flexible file-management capabilities. There is currently no Garner class
product which permits a
user initiated, voice transaction security mechanism.
Call centers have taped either the whole portion of the call or the components
of the
transaction. If the call was of a significant duration, the portions of the
contractual terms and
25 conditions, and acceptance of the terms and conditions, were captured using
computer telephony
integration (CTI). These systems tend to be used in higher value transactions
that are less
frequent because of the cost to capture, store and more importantly, retrieve
the correct
information.
There is a need for a carrier class product which permits a user initiated,
voice transaction
3o security mechanism.
CA 02352001 2001-06-29
SUMMARY OF THE INVENTION
A method or process is provided for a Garner class product which permits a
user initiated,
voice transaction security mechanism.
The carrier class voice security token (CC-VST) integrates the following areas
of
technology:
- Initiation of the CC-VST process by a telephone user via a telephone keypad
entry
- Digital recording of wireline and wireless telephone calls
- Data storage, retrieval, and playback of recorded telephone interactions
- Digital signal processing (DSP) for converting time domain digital recording
to
1o frequency domain digital representation. Extraction of characteristic
frequency and intensity
features from frequency domain digital representation.
- Encryption methods of securing the recorded digital data prior to storage
and/or
distribution.
In accordance with an aspect of the invention, there is provided a method of
dispute
15 resolution for a telephone communication, the method comprising a
validation method wherein a
transactional identifier of said telephone communication is used to determine
the details of said
telephone communication and the authenticity of one or more parties to said
telephone
communication.
In accordance with another aspect of the invention, there is provided a
validation method
2o for a telephone communication wherein said method is telephone user
initiated, said telephone
communication is digitally recorded, said telephone communication can be
stored, retrieved and
played-back, and a transactional identifier of said telephone communication is
created and used
to determine the details of said telephone communication and the authenticity
of one or more
parties to said telephone communication.
BRIEF DESCRIPTIONS OF THE DRAWINGS
Embodiments of the invention will now be described with reference to the
accompanying
drawings, in which:
Figure 1 is a diagram depicting an embodiment of a carrier class voice
security token
3o infrastructure.
Figure 2 is a diagram depicting a voice transaction using the carrier class
voice security
token process.
2
CA 02352001 2001-06-29
Figure 3 is a diagram depicting a dispute resolution of a voice transaction
using the
carrier class voice security token process.
DETAILED DESCRIPTION OF EMBODIMENTS OF THE INVENTION
A fundamental aspect of certainty in commercial transactions is non-
repudiation - having
a system that clarifies the identity of the parties (authentication) and the
details of the transaction
(validation). This process provides transaction validation for voice. The
class Garner voice
security token (CC-VST) represents a new method to conduct commerce using the
phone.
Accessing the service is not dependent upon the hardware of the user - the
hardware resides on
to the network, and the service is available over any telephone.
The CC-VST works over any phone system to capture, create and distribute the
key
elements of the verbal transaction. The CC-VST is a voice security product
that validates voice
transactions by creating a secure digital representation of the key elements
of the verbal contract
designed to fit within network Garners. Key elements that are captured include
the identity of the
15 parties, the time and date, and the terms of the offer and acceptance. If a
dispute should occur,
the CC-VST can be used to determine what exactly was agreed to in the
transaction. In essence,
the CC-VST is a digital receipt for voice transactions.
How CC-VST works:
2o The proposed method presents an assurance mechanism for the buyer and
seller in a
verbal contract to verify the original terms and conditions, ensuring the
authenticity of the
information. The CC-VST is a unique transactional identifier that is generated
from the voice
samples of the buyers) and sellers) in a digital format. 'The CC-VST is a
condensed
representation of the original voice files containing characteristic voice
features of each the
25 parties in the transaction. The CC VST is a unique identifier to the
specific verbal agreement.
The CC-VST is a 'fingerprint' of the transaction and ensures no one can modify
the offer and/or
acceptance of the terms and conditions that were agreed to in a verbal
contract. In a third party
scenario, there is a neutral party that stores the information in order for
either party to have
assurances as to the integrity and authenticity of the information. The method
also enables the
3o buyer and/or seller to have their own systems to capture the information
for their own assurance
systems.
CA 02352001 2001-06-29
Advantages of CC-VST:
The CC-VST offers several key advantages and benefits for the end-user,
including:
~ Can be initiated by any individual with a telephone to provide a secure
transactional receipt of a voice transaction.
~ Easy to manage: At less than 0.4K in size, the files can be easily indexed.
This
creates a virtual audit trail, should a dispute occur.
~ Builds trust between transaction parties.
~ Fully secure, tamper-proof The transaction terms contained in the CC-VST
cannot be manipulated.
l0 ~ Language independent: The CC-VST works equally well in any language. This
is an important feature in a global economy.
The CC-VST offers benefits to the carrier including:
~ Bridges data services and voice services: The CC-VST allows for the
integration of systems like Public Key Infrastructure (PKI) into a voice
environment.
~ Creates trust building mechanism for telephone Garners: Like financial
institutions, the telephone carriers have long sought the mechanisms that can
build
trust and credibility with their customers.
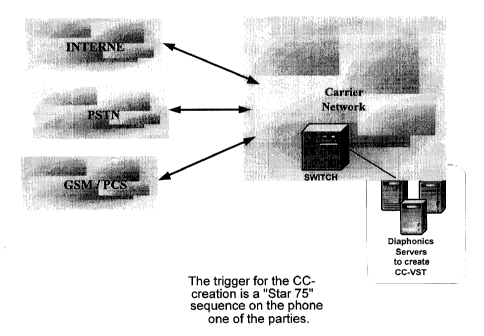
Figure 1 shows an embodiment of an infrastructure of the CC-VST. A trigger for
the CC-
2o VST creation may be, for example, a "Star 75" (*75) sequence on the
telephone of one of the
parties.
A digital recording is initiated from a wireline or wireless phone through a
key pad
sequence such as *75 (or another sequence as determined by the telco Garner).
The *75 sequence
is received by the local telephone switch and is passed through to a digital
data parallel network
called the SS7 network. The SS7 network routes the initiation sequence to a
server which is
connected to the SS7 and Internet networks. The server then initiates a call
bridge into the
existing phone call, records the call, and is then terminated by another key
pad sequence or when
the call in completed.
A server that records calls as described above interacts with a database
server to save the
3o calls as well. The calls can be saved to a typical database server or can
be forwarded to the
telephone users voice mail for later retrieval.
4
CA 02352001 2001-06-29
There are three prospective ways for retrieving the saved telephone calls. One
is to
integrate this retrieval with the users current voice mail service. The
recorded call is then played
back in the same fashion as voice mail. The second is to provide a retrieval
system using speech
recognition that allows a user to call into a server, be verified through
typical methods, and then
retrieve their recorded calls using standard queries. In this scenario, the
recorded call is played
back to them over the phone. The third method is to provide a web interface
which allows users
to retrieve the recorded device using a standard .wav player such as MS media
player.
Figure 2 shows an embodiment of the use of the CC-VST. The CC-VST is can be
used
for any transaction between a buyer and seller. For example, in a securities
transaction the buyer
l0 places an order for 100 of shares of stock ABC at the market price. The
seller asks the buyer to
confirm the accuracy of the transaction by repeating the attributes ("Confirm
you want to buy 100
shares of stock ABC at the market price"). This is known as the offer. If the
buyer agrees to the
terms, he or she confirms the transactions ("Yes, that is correct").
Meanwhile, the offer and
acceptance are recorded, time-stamped, signal processed, and stored. Key
elements of the offer
15 and acceptance, now in a digital encrypted format (CC-VST), are sent to
both the buyer and the
seller. The CC-VST is less than 0.4K in size.
Figure 3 shows an embodiment of the dispute resolution capabilities of the CC-
VST.
Should a dispute occur, the CC-VST is used to identify the terms of the
transaction. In the
securities example from above, the buyer may claim that the trade was not
executed accurately
20 (e.g., wrong security purchased, incorrect number of shares or incorrect
price limit). The CC-
VST is then used to confirm the validity of the transaction. The buyer matches
the token to the
information stored in the third party server. By matching the tokens, both
parties can be certain
that neither of the tokens have been altered. These tokens point to the
original audio file, which
is then played back to the buyer and seller. To further confirm the validity
of the transaction,
25 another copy of the CC-VST can be created and matched with the buyer CC-
VST. Both parties
can now be absolutely certain of the true terms of the transaction. The CC-VST
functions as a
digital receipt of a voice transaction.
Dispute resolution with the CC-VST can also involve neutral third party
participation.
Neutral third parties can guarantee the security and integrity of the recorded
wireline and wireless
30 phone transactions.
While specific embodiments of the present invention have been described,
various
modifications and substitutions may be made to such embodiments. Such
modifications and
CA 02352001 2001-06-29
substitutions are within the scope of the present invention, and are intended
to be covered by the
following claims.