Note: Descriptions are shown in the official language in which they were submitted.
CA 02363629 2001-11-22
Safe Net
BACKGROUND OF THE INVENTION
1. FIELD OF THE INVENTION
2. DESCRIPTION OF THE PRIOR ART
The current state the Internet can be characterized as chaotic, uncontrolled
and insecure. Internet
users can "cloak" their identity, surf the net through anonymous proxy
servers, easily distribute
viruses and other damaging micro programs, and perform credit card fraud and
highly damaging
hacking activities. This is mainly due to the fact that the Internet is a
public network and is very
difficult to impose control over.
There are three general categories of computer networks with respect to their
utilization.
1. Private networks
2. Public networks.
3. Virtual private networks
Private networks are usually encountered in business enterprises or various
organizations. In
these networks the network administrators strictly control both access to the
network resources
and the content traffic between the network members.
In private networks, the operating hardware, computer protocols and the
network configuration
are strictly controlled and in most cases involve customized hardware and/or
software. When the
private network is constrained to one office, such networks are usually
referred to as Local Area
Networks (LANs). Wide Area Networks (WAN) utilize leased communication lines
to create a
private network over longer distances. However, the leased lines required are
often expensive.
Public networks are generally classified as networks where a broad-based
participation of users
is allowed and encouraged. The Internet and the World Wide Web that it
supports is one such
-1-
CA 02363629 2001-11-22
system. However, such networks are inappropriate for corporate communications
since there are
not limits on who can access the network.
Virtual Private Networks (VPN) are used by distributed enterprises that desire
the convenience
and security of a private network despite remote physical locations of the
enterprise components,
yet do not want to incur the extra expense of leased lines to implement a WAN.
A VPN operates
on top of an existing public network, yet provides the security features
normally associated with
a private network.
The following U.S. patents disclose methods for creation of VPNs over a public
network: US
Pat. No. 6,061,796 "Mufti access virtual private network" by James F. Chen et
al., US Pat. No.
6,078,586 "ATM Virtual Private Networks" by Andrew J. Dugan et al., US Pat.
No. 6,105,132
"Computer network graded authentication system and method" by Daniel Gene
Fritch et al., US
Pat. No. 6,178,505 "secure delivery of information in a network" by David S.
Schneider., US
Pat. No. 6,205,488 "Internet protocol virtual private network realization
using mufti-protocol
label switching tunnels" by Liam M. Casey et al., US Pat. No. 6,226,748
"Architecture for
virtual private networks" by Henk J. Bots et al., US Pat. No. 6,295,556
"Method and system for
configuring computers to connect to networks using network connection objects"
by Stephen R.
Falcon et al., and US Pat. No. 6,055,575 "Virtual private network system and
method" by Gaige
B. Paulsen et al..
Most private computer networks and VPNs are also connected to the Internet to
provide access
to the Internet for their members.
In computer networks, the security of the data and the communication channel
are a concern to
varying degrees. The embodiment disclosed relates to data and communication
safety/security
over public networks such as the Internet rather than private networks.
The general principle that is applied by the prior art to data/communication
security over the
Internet is shown in Figure A.
-2-
CA 02363629 2001-11-22
If the "user 1" is attempting to communicate with "user 2" over the Internet
then the User 1's
computer system or network gateway, through the use of appropriate hardware or
software
combination, attempts to find answers to the following questions:
1. Did I establish a connection with "User 2"?
2. Is the "User 2" really who it claims to be?
3. How do I prevent third parties from eavesdropping while the message goes
through the
Internet?
There is a wide body of prior art available describing unique methods that
generally try to
establish unique and innovative answers to one or more of the questions listed
above, for
example smart cards and their variants, and biometric technologies. Figure B
shows a more
general case of a user within a LAN interacting with another user within a WAN
through the
Internet.
In Figure B, the user 1 is protected from the Internet by the use of a
Firewall, which is shown as
Gateway 1. A firewall is a barrier between a LAN, a WAN or a standalone client
and the
Internet. Firewalls and gateways consist of software and hardware components,
which act as an
access filter. Many such filtering schemes exit. The filter checks requests
that arnve from the
Internet for a resource that is within the LAN or the WAN. The filter sends
the request to the
internal network if and only if the request is coming from an identifiable
source with the right to
access the information. If this check fails then the request is discarded.
The firewall filter attempts to answer the question of whether the user 2 is
who it claims to be by
the use of a process called authentication. This is generally achieved through
the use of tokens. A
token is a small piece of code that contains information about the user, their
machine, the
operating system identification, the Internet Protocol (IP) address and domain
names among
others.
-3-
CA 02363629 2001-11-22
There are many different kinds of tokens, filters and other schemes (token-
less identification,
biometrics etc.) that serve to answer the same authentication question. There
is a rich source of
published material on this subject. Some of the more popular references are:
Firewalls and
Internet security by S. Bellovin and W. Cheswick, Addison Wesley, Reading,
Mass., 1994,
Building Internet Firewalls by E. D. Zicky et al., O'Riley & Associates, 2000
and Computer
Forensics by W. G. Kruse II and J.G. Heiser, Addison-Wesley Pub. Co. 2001.
In credit card related transactions, the system functions on the principle
that the cardholder is the
gatekeeper and controls and polices the use of that particular card and hence
his credit card
number. Though this particular transaction system works reasonably well in
society where
physical goods and credit are exchanged on the spot it is not very effective
when it is applied to
the financial transactions on the Internet. Because the credit card number is
transmitted through a
highly insecure environment and goods and credit information is not exchanged
on a one-to-one
basis, the overall transaction is open to fraud and abuse.
Another problem with the use of credit cards on the Internet stems from the
purchaser's inability
to verify the legitimacy of the seller. In a real market place, generally the
existence, size and
quality of the physical establishment serves as a relative assurance to the
purchaser of the
legitimacy of the seller. On the Internet the apparent size and quality of a
web site has no
correlation to the legitimacy of the seller.
It suffices to say that our physical marketplace based credit card system is
not well suited for
financial transactions on the Internet.
SUMMARY OF THE INVENTION
An object of the present invention is to describe a parallel Internet where
user safety and data
security is guaranteed to a very high degree.
In accordance with the present invention, there is provided a completely
different approach to
Internet security as compared to the prior art. The underlying premise in all
prior art is that the
-4-
CA 02363629 2001-11-22
Internet is chaotic, uncontrolled and insecure. They devise ways and means to
operate securely
within this insecure environment through the use of firewalls, gateways, and
encryption schemes
etc.
The present invention attempts to eliminate the premise that the prior art is
built on, namely that
the Internet is chaotic, uncontrolled and insecure, by devising a method to
bring law and order to
the Internet. A much simpler method of user accountability and traceability is
provided as the
prime source for Internet security. With the present method, the Internet is
relatively orderly and
secure and therefore the need for firewalls and other methods is diminished
and could potentially
be eliminated in proportion to the general security provided by this method.
The current state of security on the Internet is very similar to the social
structure that existed in
the Middle Ages where city-states were surrounded by moats and high walls to
protect the
citizens from the outside chaos. Most trade and physical communication between
these cities
were considered insecure and when an absolute security was required a group of
soldiers were
sent along with the messenger.
If we overlay this social structure from the Middle Ages onto today's Internet
then it becomes
apparent that the city walls and moats are no more then firewalls, gateways
and filters of the
Internet. As well, the various encryption methods are mere protection schemes
for the message
that is being transmitted between the city-states (i.e. LANs, WANs or other
Internet users).
In modern societies we no longer need city walls, guards and messenger
parties. General law and
order eliminated the need for such devices.
In its most fundamental form, this invention attempts to move the Middle Age
like structure of
the Internet to the modern era.
The approach to network security that is prescribed in this application
differs radically from the
prior art. A simple analogy is people driving on highways without a driver's
license in heavily
-S-
CA 02363629 2001-11-22
armed convoys and tanks (current Internet security approach) versus licensed
drivers driving cars
(the proposed approach).
BRIEF DESCRIPTION OF THE DRAWINGS
These and other features of the preferred embodiments of the invention will
become more
apparent in the following detailed description in which reference is made to
the appended
drawings wherein:
Figure 1 is a schematic representation of a communication system.
Figures 2 through 5 are schematic representations of data structures used in
the
communication system of Figure 1.
Figures 7 through 10 are schematic representations of methods performed by the
correspondents of Figure 1.
DESCRIPTION OF THE PREFERRED EMBODIMENTS
1 S The visible Internet chaos stems from the difficulty in identifying hosts
that are on the Internet at
a given time.
The Internet Protocol (IP), the transport program (TCP) and User Datagram
Protocol (UDP) are
designed and used to transmit messages between different computer networks.
Each Internet
interface is identified by a 32-bit Internet address. When the Internet
protocol (IP) was
standardized in 1981, these addresses were identified as two part objects: a
network identifier
and a host number within that network. The Internet numbering authorities
designate the network
numbers, which are unique worldwide. The network manager assigns the host
numbers within
their network. In 1984 a third hierarchical level called a subnet was added to
the structure. A
subnet is a division of the addressing space reserved for a network.
Though the uniqueness of host numbers, within one network, combined with
worldwide
uniqueness of the network numbers creates an impression of an ability to
uniquely identify hosts
that are on the network, generally this is not the case since Internet
addresses do not designate
hosts. They are identifiers of network interfaces. A host with several
interfaces will have many
-6-
CA 02363629 2001-11-22
addresses. Furthermore, the network topology can dynamically change over time.
Customers
may change providers, company backbones may be reorganized, and providers may
merge or
split. If the topology changes with time and if the addresses must somehow
reflect the topology,
then addresses will have to change from time to time. Therefore IP addresses
do have lifetimes.
An address whose lifetime has expired becomes invalid.
The IP is a highly effective protocol for providing connectivity between
various computer
networks, but it is extremely ineffective for determining who injected a virus
onto a network or
who was hacking into a network. The underlying reason for this is that the
Internet was built as a
network of computers, not people.
The proposed Safe Net will overcome these shortcomings of the Internet without
affecting the
richness and diversity of the Internet. There are two key founding principles
for the Safe Net:
accountability and traceability.
We utilize three key components to reduce to practice these principles.
1. Personal user number:
Members of every society need a passport number to enjoy the privileges of
citizenship
associated with that society all over the world. We need a health insurance
card number to be
able to access the health care system. We need a driver's license number to
have access to the
privilege of private transportation. All modern societies are built on the
concept of licensing
individuals for a privilege of access to a service or a right, and in turn
demand accountability
for individual action. Every time the society grants a privilege to one of its
members it also
provides an ID number, which acts as the linkage between that privilege and
the
accountability that necessarily follows it.
If we need to get a license to fish or own a dog, then why should we not need
a license to
have the privilege of access to the information highway?
CA 02363629 2001-11-22
Every user of the Safe Net will be fully registered and will be given a user
ID, also known as
a registration number or a personal user number, for use of the Safe Net. A
unique
registration number will be necessary for individuals to roam on the Safe Net.
This
registration number will be keyed to an existing credit card system so that a
physical person
can be traced in relation to an )D number.
Therefore the first underlying principle of the Safe Net, i.e. accountability,
is established
through the use of personal user numbers.
2. The TAG system:
Every user of the Safe Net will be fully registered and will have a user ID.
The host software
for the Safe Net will also carry a unique number (product ID). Every single
file that is
attempted to be transmitted across the Safe Net will be given a unique file
ID.
The host software will TAG all files with all three ID numbers, namely user
ID, file ID, and
product ID, as well as date and time. This TAG will not be destroyable even if
the original
file is deleted.
Every time a file is received via the Safe Net, it is checked for the presence
of a TAG. A file
without a TAG will preferably not be processed or alternatively the user will
be positively
informed about the file's suspect status. TAGless files are also forwarded to
the Safe Net
security system.
If the received file contains a valid TAG then its TAG will be modified
immediately by
adding the various ID numbers of the receiving person and the computer. The
TAGS record
an event history of every file that is created and are thus completely
traceable.
3. Central TAG archive
As soon as a user starts the Safe Net software it will send the user's TAG to
a central archive.
From this point on every activity of the user on the Safe Net will be logged
on the Archive
_g_
CA 02363629 2001-11-22
via modified TAGS. The Central Tag Archive consist of a set of servers located
on the
Internet for the purpose of monitoring TAG activity of all of Safe Net
members.
The TAG system and the Archive jointly provide full traceability of the
activities of all users
of the net.
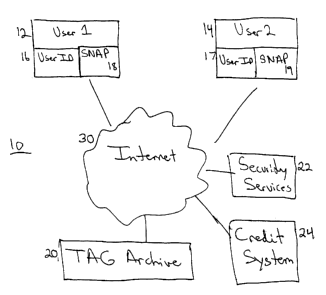
Refernng to Figure 1, a schematic representation of a network is shown
generally by the
numeral 10. A plurality of users, shown as a first user (User 1) 12 and a
second user (User 2)
14, for the sake of example, each have a respective User 117 16, 17 and a Safe
Net
Application (SNAP) 18, 19. The users are both connected to the Internet 30 for
communications. Also connected to the Internet 30 is a TAG Archive 20, a Safe
Net Security
Service 22, and a Safe Net Credit Company 24. The users 12, 14 communicate
with each
other over the Internet 30 by using the TAG Archive 20. The TAG Archive
comprises a
plurality of Safe Net servers. The Safe Net Security Service monitors
communications
1 S through the Internet 30 using the TAG Archive 20. The Safe Net Credit
Company 24
provides payment services to the users.
Refernng to Figures 2, 3, 4, and 5, exemplary TAGS for use with the TAG
Archive are
shown generally by the numerals 40, 40a, 40b, and 40c. Each TAG comprises a
USER 117 50,
SOa, SOb, SOc, a SNAP ID 51, Sla, Slb, Slc, and a Time Stamp 60, 60a, 60b,
60c. A permit
request TAG is shown in Figure 2. As shown in Figure 3, an activity TAG 40a
further
comprises a Pass 52a, an Activity Number 53a, and a URL 54a. As shown in
Figure 4, a
check and verify TAG 40b further comprises a Pass 52b, an Activity Number 53b,
another
USER ID 54b, another SNAP ID SSb, and another Pass 56b. As shown in Figure S,
an email
TAG 40c further comprises a Pass 52c, an Activity Number 53c, and an Email
Address 54c.
Referring to Figure 6, a method of logging on to the Safe Net is shown
generally by the
numeral 100. The first user 12 wishes to log onto the Safe Net. It is assumed
that the first
user has already registered with the Safe Net, and thereby obtained its User
ID 16. The SNAP
18 sends 102 a permit request TAG to the TAG Archive 20. The Archive verifies
104 that the
-9-
CA 02363629 2001-11-22
first user 12 is registered. If the first user 12 is registered, then the
Archive sends 106 a
permit to the first user 12. Then the first user 12 uses 108 the Safe Net. If
and when the
permit expires and the first user 12 is still on the Safe Net, then step 102
is repeated 110 to
obtain a fresh permit.
Refernng to Figure 7, a method of downloading a file through the Safe Net is
shown
generally by the numeral 200. The first user 12 wishes to download a file or
web page from
the second user 14. The first SNAP 18 makes 202 an activity TAG. The first
SNAP sends
204 the activity TAG to the TAG Archive 20. The first SNAP 18 then sends 206
the activity
TAG to the second user 14. The TAG Archive 20 stores 208 the activity TAG.
When the web
site receives 210 the activity TAG, it creates 212 a check and verify TAG. The
web site
sends 214 the check and verify TAG to the TAG Archive 20. The TAG Archive 20
verifies
216 the first user, and sends 218 the verification to the second user 14. The
second user 14
then sends 220 the file to the first user 12. The user then views 220 the
received file.
Refernng to Figure 8, a method of modifying a file obtained from the Safe Net
is shown
generally by the numeral 300. The first user obtains 302 a file through the
Safe Net. The
SNAP 18 then adds 304 a file number to the file. The file is then saved 306 to
the user's
storage means, preferably a hard drive. When an application opens 308 or
modifies the file,
the SNAP 18 modifies 310 the file ID in a predetermined manner to indicate the
activity
performed on the file.
Refernng to Figure 9, a method of emailing a file through the Safe Net is
shown generally by
the numeral 400. The SNAP 18 generates 402 an email TAG. The SNAP 18 then
sends 404
the email TAG to the TAG Archive 20. The SNAP 18 also sends 406 the email TAG
to the
second user 14. The second user 14 creates 406 a check and verify TAG and
sends 410 the
check and verify TAG to the TAG Archive 20. The TAG Archive 20 verifies 412
that the
first user 12 is registered with the Safe Net and sends 414 the verification
to the second user
14. The second user then views 416 the email.
- 10-
CA 02363629 2001-11-22
Refernng to Figure 10, a method of processing a credit card payment through
the Safe Net is
shown generally by the numeral 500. A seller sends 502 its seller ID and a
product ID to a
buyer. The buyer sends its buyer ID, seller ID, the product ID, and a price to
the Safe Net
Credit Company 24. The Safe Net Credit Company 24 sends 506 the bill to the
buyer and
sends 508 the payment to the seller. Upon receiving the payment, the seller
sends 510 the
goods to the buyer.
The following example will illustrate some of the characteristics of the TAG
system, the Tag
Archive and the communication protocol involved.
In this example, User 1 (U1) and User 2 (U2) are both registered members of
the Safe Net
and U1 downloads a file from U2's site, modifies this file and e-mails it back
to U2.
U1 logs on to the Safe Net by initiating the Safe Net APplication (SNAP) on a
local
computer.
1. SNAP 1 sends the following TAG to the Archive
User ID 1 SNAP ID Time stamp
2. The Archive verifies that the U1 is a registered user and sends back a live
permit. This
permit allows the user to operate on the Safe Net. It is called live since
these permits are
created with a definite expiry duration that might vary from an order of
minutes to hours
or days depending upon the characteristics of the user. Upon expiry of the
permit, if the
user is still on the Safe Net and remains so, then SNAP automatically asks for
and
receives another permit from the Archive.
3. Upon receipt of the permit from the Archive SNAP 1 makes a new TAG
User ID 1 I SNAP ID1 Pass for U1 Activity # URL Time stamp
-11-
CA 02363629 2001-11-22
This TAG is sent by SNAP 1, both to the Archive and to the site that U1 wants
to view.
In this case the Activity number will correspond to "viewing a web site."
S 4. TAG Archive stores the activity under the User ID 1 database entry.
5. The site of U2 that is being visited by U1 picks up the TAG from U1 and
creates the
followin TAG
UID 2 SNAP ID 2 Pass for U2 Activity # UlD 1 SNAP ID 1
Pass for U1 Time stamp
And sends this TAG to the Archive. In this instance the Activity Number
corresponds to
"check and verify user".
6. The Archive checks this information against its database on U1 and verifies
its
authenticity. It then sends verification to the SNAP 2 of the user 2's site.
7. The specific resource that was requested by the user 1 is then displayed on
U1's
computer screen.
8. If U1 chooses to save this specific file on its hard drive then a file
number is added by
SNAP 1 to that specific file that is being created. This number can be
generated locally by
the SNAP by various means ranging from a high value random number to a time
stamp
based number. When combined with the U)D and SNAP ID the joint number becomes
unique for identification of this specific file.
9. If any application on U1's computer opens and modifies the file that was
downloaded
then the file >D number is modified in a predetermined manner by SNAP 1 to
indicate
-12-
CA 02363629 2001-11-22
this particular activity on the file. File ID numbers will remain with all of
the files that are
created or moved through the Safe Net.
10. The U1 now wants to send this file back to U2 through the use of e-mail.
In this case
SNAP 1 will generate the following TAG:
User ID 1 SNAP ID1 Pass for U1 Activity # e-mail address Time stamp
11. The process as shown on steps 3 - 7 will be repeated in a similar manner
to ensure
authenticity of both the user and its activities on the Safe Net.
Like all licensed activities in our society, Safe Net traffic will also be
open to a certain amount of
abuse and lawlessness. But over time, organizations and societies develop ways
and means to
minimize such activities.
It is important to note that the existence of Safe Net will detract absolutely
nothing from the
Internet, as we now know it. A user will be able to use the Internet and the
Safe Net
simultaneously through the same browser. The SNAP software will fimction as a
plug-in to all
available browsers. It will also be available a standalone program. The users
of the Safe Net will
be able to send and receive data from other users who are not Safe Net
members, but these files
will be clearly identified for the user's benefit. It is expected that, over
time, financial
transactions, official company business, and all other correspondence that
necessitates a more
secure environment will move through Safe Net. The Internet and the Safe Net
will exist
concurrently.
The Safe Net will feature two internal organizations:
1. Safety Net Security Service
-13-
CA 02363629 2001-11-22
This organization will function in a similar way to the police in our society.
It will
investigate all Network Security related issues. Any security infringement on
the Safe
Net that is traced and documented by the Security Service will be turned over
to local
authorities along with the evidence for the purpose of prosecution of the
invaders. The
Security Service will be bound by the same set of rules that the police
operate under.
2. Safe Net Credit System
The purpose of this organization is to establish and maintain a secure and
reliable financial
transaction service within the Safe Net.
The Safe Net Credit System differs from existing systems in a fundamental
manner and
follows a different credit flow pathway. Figure 10 shows this alternative
transaction
method.
Within the Safe Net Credit System, the "credit card number" of the purchaser
is never
released to the seller thereby completely eliminating the possibility of
fraud. Furthermore
each purchase is also correlated with a User ID and a SNAP ID. The Archive
also tracks
the interaction between the buyer and the seller prior to the finalization of
the transaction.
With these safety characteristics, the Safe Net Credit system will be the
transaction of
choice for purchases over the Internet.
Although the invention has been described with reference to certain specific
embodiments, various modifications thereof will be apparent to those skilled
in the art without
departing from the spirit and scope of the invention as outlined in the claims
appended hereto.
-14-