Note: Descriptions are shown in the official language in which they were submitted.
CA 02375165 2002-03-08
Voice Data Privacy and Protection System
Field of the Invention
The present invention relates to a voice data privacy and protection
(VDP&P) system, which is an all voice structure that brings data security and
assurance to the voice environment.
Background and Summary of the Invention
Much work has been done to enable rigorous methods of securing digital
data originating in document-like format. The goal of these activities has
been
to enable cryptography methods that secure digital data and allow digital
signatures. Crypto systems such as PKI (public Key Infrastructure) provide a
method of encrypting/decrypting digital documents, ensuring originality
through
hashing, and binding of the data to an individual through private keys and
digital
signatures. In addition, a biometric device such as retinal scans, fingerprint
scans, and voice verification methods have enabled user identification based
upon a physical trait.
However, interactions and transactions conducted by voice present
unique challenges when attempting to implement a secure and private
environment for their conduct. There are challenges with regard to identifying
the parties involved in the voice transaction, and then properly recording,
securing, and storing the transaction. With an arm's length voice transaction,
identification of the parties involved cannot practically be done through
methods
such as retinal scans etc. As well, cryptography methods, including the
associated key management processes, do not fit neatly into the voice
environment. The challenge is to establish a direct and irrefutable linkage
between the cryptographic key and the user that holds the key. Typically this
is
achieved through the use of smart cards and other physical association
methods. However, in the voice environment it is more difficult to ensure the
identification of the individual and then verify the corresponding linkage of
that
person to their cryptographic key.
CA 02375165 2002-03-08
2
Despite these challenges, it is possible to build a data privacy and
protection system that is designed to work specifically within the voice
environment and still provide a significant level of security. This system can
enable voice data security and transactional non-repudiation. The issue of
user
identification can be addressed through the use of voice verification. The
issues
of securing and storing the recorded voice transactions can be dealt with by
the
use of a cryptographic method designed specifically for a voice environment.
Voice security solutions have typically focused upon providing secure
cryptographic channels in which to conduct voice interactions. As an example
cryptographic secure telephones have been used for many years that encrypt
and decrypt the voice within the phone for transmission on the telephone link.
These systems require unique phones and appropriate cryptographic methods.
These systems do not address the issue of secure data recording and storage.
As well, the underlying assumption of these types of systems is that the
individual in possession of the crypto key is who he or she says they are.
There
is no direct linkage, other than key possession, that identifies and binds the
individual to the voice transaction.
In the case of Voice over Internet Protocol (VoIP), voice transactions can
be conducted via the Internet and/or computer network infrastructure. In this
situation, a secure voice channel can be established between parties using
technologies such as Virtual Private Networking (VPN). Once again however,
this type of system does not address the issue of secure data recording and
storage and does not identify and bind the individual to the voice
transaction.
PKI is widely accepted as the commercial standard for high-end
cryptography and security of digital data. A PKI system requires that the user
have a private key that remains secret, and a corresponding public key that is
available to other PKI users via an external and open Certificate Authority
(CA).
The user can encrypt and digitally sign documents with their private key, and
then the document recipients can decrypt and validate the identity of the user
via
the public key.
CA 02375165 2002-03-08
Key management is a critical part of PKI both from the user and CA
(Certificate Authority) perspective. The user must retain and keep their
private
key secret. Typically the private key will reside on a Smart card that the
user
accesses via a card reader and password. An underlying assumption of the PKI
system is that the individual who holds the private key, and the password
required to access it, is indeed who they say they are. So the linkage from
user
to private key is based upon possession of the smart card and knowledge of the
password. The key management components of PKI do not allow direct usage
within a voice environment. It is not possible to enable the Public-Private
key
usage and exchange without additional resources such as smart card readers
and digital connectivity to the CA. .
The VDP&P of the invention can operate in the telephony environment
including the Publicly Switched Telephone Network, Mobile Phone Networks,
Mobile Trunk Radio Networks, and Voice over IP (VoIP). The VDP&P
incorporates elements of Automated Speech Recognition (ASR) and Automated
Voice Verification (AW). The major components of the VDP&P are as follows:
- Automated voice verification. This component allows the automated
identification of an individual based upon the biometrics of their voice,
- Voice Security Token (VST). The VST is a small digital file that is
created from a recorded audio file. The VST is extracted based upon the voice
biometrics of the speakers recorded in the audio file. The VST technology is
disclosed in Canadian Patent Application 2,364,293, which is filed in the name
of the same applicant as in the present application, and of which disclosure
is
incorporated herein by reference. Further detail of the VST will be described
hereinafter.
- Data Cryptography Methods. This component enables the
encryption/decryption of the recorded audio files and the VST. The VST as a
voice derivative is used directly as a symmetric crypto key or can be
augmented
and/or modified with a crypto key 'salt'. A key 'salt' is an additional random
component which is added to another key in order to increase the size, and
hence the uniqueness, of the crypto key.
CA 02375165 2002-03-08
4
- Database storage and retrieval methods for the recorded audio files.
- Participation of a Trusted Third Party (TTP) for managing the audio
recordings and crypto components.
The VDP&P of the invention brings security, trust, and transaction
assurance into the voice environment. It provides an end-to-end voice security
system that permits voice transactions to be conducted between verified users.
As well all transactional details are recorded, encrypted, and stored.
Features of
the invention and advantages associated therewith are as follows:
- Users are verified by their voice bio-metric in order to gain access to the
system.
- There is a verifiable direct linkage created between the voice user and
their transactional data enacted through the cryptographic key management.
- Data privacy is ensured because users may only gain access to their
own voice transaction details.
- Authenticity and integrity of the recorded audio files is ensured by
creation of the VST.
- Encryption of the VST and audio files ensures data protection from
compromise.
- There is no external key crypto key management .
- The VDP&P can be implemented to operate over any telephony device
including landline, mobile, VoIP, and trunk radiophones.
Further understanding of other features, aspects and advantages of the
present invention will be realized by reference to the following description,
appended claims and accompanying drawings.
Brief Description of the Drawinqs
The embodiments of the invention will be described with reference to the
accompanying drawings, in which:
Fig. 1 illustrates a voice data privacy and protection engine in accordance
with one embodiment of the invention;
CA 02375165 2002-03-08
Fig. 2 illustrates a voice data privacy and protection engine in accordance
with another embodiment of the invention;
Fig. 3 illustrates a voice data privacy and protection engine in accordance
with yet anther embodiment of the invention;
5 Fig. 4 illustrates the overall architecture of an apparatus for uniquely
identifying an electronic transaction;
Fig. 5 illustrates a method of uniquely identifying an electronic
transaction; and
Fig. 6 illustrates an apparatus for uniquely identifying an electronic
transaction.
Detailed Description of the Preferred Embodiments)
The VDP&P of the present invention can be conceived of as having a
common structure and functionality, but sufficient flexibility in the
implementation
to allow for varying levels of security. The security requirements of a
specific
situation are determined by a number of factors related to the risk of data
compromise and the costs associated with such compromise. Therefore, the
VDP&P incorporates a tiered approach regarding the degree of data security
and this is reflected in the following embodiments of the invention.
Voice Data Privacy and Protection !Tier I)
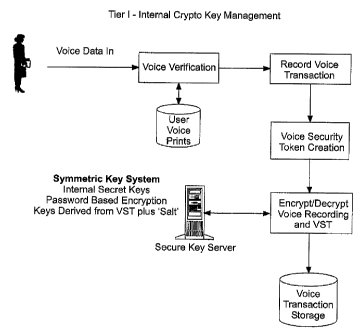
Fig. 1 shows a voice data privacy and protection engine according to one
embodiment of the invention. In this embodiment, the first tier provides the
foundational layer of security within the voice environment. The crypto system
in
place allows a good level of security, trust, and assurance. As illustrated in
Fig.
1, the components of the system include the following:
- User voice verification
- Voice Security Token creation that assures the originality of the
recorded voice data,
- Encryption/decryption using symmetric (secret) keys, and
- Storage of the voice data, and
- Telephony and Web-based retrieval methods for stored voice data.
CA 02375165 2002-03-08
Because this system employs internal symmetric crypto keys it is not as
secure as the PKI enabled Tier II model.
Tier I crypto key management is all done internally including key
generation, key usage, key security, and key destruction. The benefit of
having
internal key management is that no additional external connectivity or
resources
are required specifically for key management activities. This reduces both
systems integration and operational costs. The disadvantage of internal
symmetric key management is that the system is relatively more vulnerable to
compromise, hence, the reduced level of security in comparison with PKI.
One important component in the VDP&P key management functions are
key generation and key security. Keys are generated through standard means
such as random number generation, password based encryption, and/or a VST
digest plus additional 'salt'. A key 'salt' is an additional random component
which is added to another key in order to increase the size, and hence the
uniqueness, of a crypto key. In this case, the VST itself can be used as a
crypto
key. However, to increase the level of security an additional 'salt' maybe
incorporated with the VST when used as a crypto key.
A separate secure key server manages key security and control. Crypto
keys are made available to the user session once the user is accepted into the
system via voice verification and password/PIN.
Voice Data Privacy and Protection (Tier II)
Fig. 2 depicts a voice data privacy and protection engine according to
another embodiment of the invention. In this embodiment, the VDP&P Tier II is
functionally the same as Tier I, however, it can provide a relatively higher
level of
data security as it incorporates the components of PKI.
Tier II provides an advanced level of security within the voice
environment. The PKI crypto system in place allows the highest degree of
commercial security, trust, and assurance. The components of the system
CA 02375165 2002-03-08
7
include the following:
- User voice verification
- Voice Security Token creation that assures the originality of the
recorded voice data,
- Encryption/decryption using PKI cryptography, and
- Storage of the voice data, and
- Telephony and Web-based retrieval methods for stored voice data.
A PKI cryptography system requires that the user have a private key that
remains secret, and a corresponding public key that is available to other PKI
users via the Certificate Authority (CA). The user can encrypt and digitally
sign
documents with their private key, and then the document recipients can decrypt
and validate the identity of the user via the public key.
Key management is a critical part of PKI both from the user and CA
perspective. The user must retain and keep their private key secret. Typically
the
private key will reside on a Smart card that the user accesses via a card
reader
and password. An underlying assumption of the PKI system is that the
individual who holds the private key, and the password required to access it,
is
indeed who they say they are. So the linkage from user to private key is based
upon possession of the smart card and knowledge of the password. In order to
migrate PKI to the voice environment a different method of private key
management is required.
In the Tier II model, it is proposed that a trusted third party hold the user
private keys in a secure key server. Users gain authorized access via voice
verification and Password/PIN. Therefore, the linkage of the user to the
private
key is instead based upon voice biometrics, rather than physical possession,
and the password requirement remains the same as in the standard PKI system.
The storage of user private keys in a third party secure server presents
additional problems in terms of ensuring adequate security and the potential
for
compromise. Nonetheless, it is possible that a rigorous secure network can be
constructed that would permit the management and usage of private keys within
CA 02375165 2002-03-08
g
the voice environment. All other aspects of the PKI system including
interaction
with CA's, digital signing of voice digital data, encryption/decryption of
voice
digital data, and distribution of the data to other PKI system users remain
the
same.
Multi-User Scenario
Fig. 3 shows a voice data privacy and protection engine according to
another embodiment of the invention. In this embodiment, the VDP&P Tier I
and II models have been illustrated from the perspective of an individual
voice
user. It is, however, possible to enable both the Tier I and II models in a
multi-
user scenario. The structures illustrated in Tier I and II above would remain
the
same. The difference in the multi-user scenario is in the method of access to
the
system.
In this situation, one or more users are involved in a voice transaction
such as in the case of a conference telephone call. Prior to accessing the
conference call, users would first have to be authorized and identified by
voice
verification. Once successfully verified, all parties would be linked to the
voice
recording and the completed recording would be processed in accordance with
the security model in place. All parties could receive copies of the voice
transaction as required by the circumstances.
According to the present invention, the VDP&P can be implemented to
allow use by an individual or by multiple users. Further, the VDP&P can allow
the distribution of recorded voice transactions in digital audio file formats
via
telephone, Internet, and email.
The VST will be described below in greater detail.
There are many challenges in today's electronic environment for business
exchange of goods and services. The traditional method for contracts to be
made between the buyer and seller was for the buyer to provide a signature
signifying that the buyer understood and agreed to the terms and conditions of
CA 02375165 2002-03-08
9
the sale, usually within a sales contract. This signed contract was the basis
for
any dispute surrounding the sale B non-repudiation. This paper-based trail has
been a challenge for electronic business because the contract and signature
may all be electronically agreed to. There have been recent advances in the
courts accepting digital signatures, but these have focussed on pen-based
signatures utilizing biometrics.
Natural language speech recognition allows for more commerce to be
completed using only voice and augments existing transaction systems. This
can be voice transmitted over Publicly Switched Telephone Systems (PSTN),
mobile or cellular traffic, two-way radio, campus systems and voice over
Internet
Protocol (Voice Over IP) B any medium that carries a voice stream. There are
advances in speaker recognition that have taken place, but there is nothing
that
captures the nature and intent and agreement around the verbal contract that
takes place in a voice transaction. In a voice transaction, there is no
effective
method to capture the transactional information for non-repudiation purposes
and that is what the VST solves. This is critical if the 'offer' is not
perceived to
be the same as the 'acceptance' in the transaction.
Today, call centres either record the transaction or do nothing. If they do
have the recording, they can use the tape to go back to play the original
'offer'
and 'acceptance'. If the call was of a significant duration, the portions of
the
contractual terms and conditions and acceptance of the terms and conditions
are captured using Computer Telephony Integration (CTI). These systems tend
to be used in higher value transactions that are less frequent because of the
cost to capture, store and more importantly, retrieve the correct information.
The problem is that either party (buyer or seller) can challenge the
authenticity of
the files.
In an Electronic Data Interchange (EDI) transaction, the Value Added
Network (VAN) assured the sender and receiver of the authenticity of the
message and gave each tracking tools to ensure the messages had been
received. VANs did not encrypt the information so there could be a challenge
to
CA 02375165 2002-03-08
l.0
the original seller's terms and conditions or to the acceptance by the buyer.
Virtual Private Network allow for the secure transaction of information with
each party having a trusted medium. There is an implicit assumption that the
buyer and seller are working in trusted environments but this does not solve
the
non-repudiation of the verbal contract.
The other challenge for businesses is to have an inexpensive process for
reconciliation. If the process is paper-based, then the process is expensive
because it is people intensive. Companies require an inexpensive system to
easily verify the original verbal contract.
Therefore, there exists a need for a cost effective method and apparatus
for uniquely identifying an electronic transaction that is not easily disputed
by
either the buyer or seller.
In general, the disclosed method and apparatus presents an assurance
mechanism for the buyer and seller in a verbal contract to verify the original
terms and conditions, ensuring the authenticity of the information. A voice
security token (VST) is a unique transactional identifier that is generated
from
the voice samples of the buyers) and sellers) in a digital format. The VST is
a
condensed representation of the original voice files containing characteristic
voice features of each the parties in the transaction. The VST is a unique
identifier to the specific verbal agreement. The VST is a 'fingerprint' of the
transaction and ensures no one can modify the offer and/or acceptance of the
terms and conditions that were agreed to in a verbal contract. The disclosed
method and apparatus also enables the buyer and/or seller to have their own
systems to capture the information for their own assurance systems.
Referring to Figs. 4, 5 and 6, a seller presents an offer including terms
and conditions to a buyer. The buyer receives the offer and then accepts the
offer, and an electronic transaction is agreed upon. The offer including the
terms and conditions is saved as a first digital audio voice file and stored
in a
CA 02375165 2002-03-08
11
database. The acceptance of the offer is also saved as a second digital audio
voice file and stored in a database. The format of the digital audio voice
files is
preferably in time format. A voice security token in then created from both
the
offer and acceptance as saved in the digital audio voice file database. The
VST
is created where the digital audio files are sent through a pre-processor
program
in addition to the core system that features frequency feature extraction.
Since
voiceprints are unique, the VST is unique for each electronic transaction.
The VST is then sent to both parties. The VST may be sent by mail
receipt, email, fax, XML format, EDI format or any other user defined format.
The VST forms the core of the non-repudiation process and enables faster
lookup of the original files. There can also be a smaller token that can
points to
the VST if either party only needs a condensed confirmation. The VST is now
the basis of any non-repudiation claims if the buyer and seller disputes the
terms
and conditions that were agreed to.
The seller now goes through its normal process of delivering goods to the
customer that were ordered through the contract.
In one embodiment, a third party is used as a neutral party that stores the
information in the database in order for either party to have assurances as to
the
integrity and authenticity of the information. The third party dispute
mechanism
involves limited human involvement, as either party only has to submit the VST
to get access to the authentic originals. The system includes the ability to
regenerate the VST from original digital audio files and compare it with the
original buyerlseller VST. It will also highlight if there was any tampering
with the
original voice recordings of the contract, even though third party
participation is
used to reduce the likelihood of tampering of process by either buyer or
seller
While the third party option for capturing the voice files from both parties,
as a non-repudiation system is a preferred embodiment, the seller and/or buyer
can use the system for their own internal non-repudiation system.
CA 02375165 2002-03-08
12
In another embodiment, the system may also use middleware for
integration into business documents.
The disclosed method and apparatus is used for confirmation of a verbal
contract but can augment a traditional paper contract as well.
The VST integrates signal processing for analog-to-digital and Time-to-
Frequency conversion, Frequency elements for the VST, Data storage and
hosting, and encryption methods of securing the data. The VST interoperates
with existing login and user level security systems.
The previously described embodiments of the present invention have
many advantages including:
- the VST can be used by either the buyer or the seller or from a third
party;
- the VST is used at the individual level versus the company level so that
it creates an assurance mechanism based on biometrics to the individuals)
within the contractual agreements;
- the VST ensures the authenticity of the original 'offer' of the sellers) and
'acceptance' by the buyer(s);
- the VST is a mechanism to ensure that the record of the 'offer' and
'acceptance' has not been tampered with as the VST is given to both parties
and
it must match to ensure the validity of the originals;
- the VST is different for every transaction ensuring a high degree of
success to ensure that the VST cannot be duplicated without the original
information;
- the VST system is much faster than traditional methods as it is based on
database architecture speeds versus human intervention for non-repudiation
challenges;
- the VST is much lower in cost than traditional methods due to limited
human intervention;
- the VST is small in comparison to standard voice files and therefore can
be embedded within business transactions; and
CA 02375165 2002-03-08
13
- the identity of the users within the transaction can be authenticated with
the VST if the users have been through either an enrolment process in a
proactive stance or matched 'after the fact' by comparing a given voice
sample.
While the invention has been described with reference to several specific
embodiments, the description is illustrative of the invention and is not to be
construed as limiting the invention. Various modifications may occur to those
skilled in the art without departing from the true spirit and scope of the
invention
as defined by the appended claims.