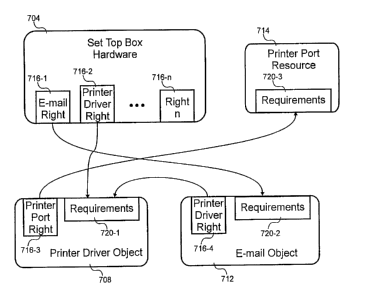
Note: Claims are shown in the official language in which they were submitted.
WHAT IS CLAIMED IS:
1. A method for securing information in a conditional access system
(100), the method comprising:
providing a unit of hardware, software, data, content or the like functional
unit (308, 604, 608, 612, 614, 616, 618, 620, 622, 624, 704, 708, 712, 714);
providing requirement data (508, 720) related to the functional unit (308,
604, 608, 612, 614, 616, 618, 620, 622, 624, 704, 708, 712, 714);
entitling a datastream or like transmission conduit to a set top box,
computer, information appliance, TV display, personal video recorder or like
content
receiver (108);
receiving rights data (408, 716) related to the-functional unit (308, 604,
608, 612, 614, 616, 618, 620, 622, 624, 704, 708, 712, 714);
correlating the rights data (408, 716) with the requirement data (508, 720);
and
checking the rights data (408, 716) against the requirement data (508,
720).
2. The method for securing information in the conditional access
system (100) of claim 1, wherein the functional unit (308, 604, 608, 612, 614,
616, 618,
620, 622, 624, 704, 708, 712, 714) includes at least one of a collection of
digital
information or the like object (308, 608, 612, 616, 618, 620, 622, 624, 708,
712) and a
physical device, an object or the like resource (308, 604, 608, 612, 614, 616,
618, 620,
622, 624, 704, 708, 712, 714).
3. The method for securing information in the conditional access
system (100) of claim 2, wherein the object (308, 608, 612, 616, 618, 620,
622, 624, 708,
712) comprises at least one of software, drivers, firmware, data, video, and
audio.
4. The method for securing information in the conditional access
system (100) of claim 2, wherein the resource (308, 604, 608, 612, 614, 616,
618, 620,
622, 624, 704, 708, 712, 714) comprises at least one of an object (308, 608,
612, 616,
618, 620, 622, 624, 708, 712) and a physical device (604, 614, 704, 714).
5. The method for securing information in the conditional access
system (100) of claim 1, further comprising authenticating a source of the
functional unit
(308, 604, 608, 612, 614, 616, 618, 620, 622, 624, 704, 708, 712, 714).
6. The method for securing information in the conditional access
system (100) of claim 1, further comprising authorizing use of the functional
unit (308,
604, 608, 612, 614, 616, 618, 620, 622, 624, 704, 708, 712, 714) if the right
satisfies the
requirement data (508, 720).
7. The method for securing information in the conditional access
system (100) of claim 1, wherein the entitling the transmission conduit
comprises
decrypting information passing through the transmission conduit.
8. The method for securing information in the conditional access
system (100) of claim 1, the method further comprising
a step of determining requirement data (508, 720) for the functional unit
(308, 604, 608, 612, 614, 616, 618, 620, 622, 624, 704, 708, 712, 714).
9. The method for securing information in the conditional access
system (100) of claim 1, comprising determining rights data (408, 716)
associated with
the content receiver.
10. The method for securing information in the conditional access
system (100) of claim 1, allowing inheritance of a right from a first
functional unit (308,
604, 608, 612, 614, 616, 618, 620, 622, 624, 704, 708, 712, 714) to a second
functional
unit (308, 604, 608, 612, 614, 616, 618, 620, 622, 624, 704, 708, 712, 714).
11. The method for securing information in the conditional access
system (100) of claim 1, further comprising sending rights data (408, 716) to
the
functional unit (308, 604, 608, 612, 614, 616, 618, 620, 622, 624, 704, 708,
712, 714).
12. The method for securing information in the conditional access
system (100) of claim 1, further comprising a step of correlating the rights
data (408, 716)
to the functional unit (308, 604, 608, 612, 614, 616, 618, 620, 622, 624, 704,
708, 712,
714).
13. The method for securing information in the conditional access
system (100) of claim 1, wherein the entitling a transmission conduit
comprises
encrypting information passing to the transmission conduit.
14. The method for securing information in the conditional access
system (100) of claim 1, further comprising authenticating the functional unit
(308, 604,
608, 612, 614, 616, 618, 620, 622, 624, 704, 708, 712, 714).
15. A content receiver for a conditional access system (100),
comprising:
a set top box, computer, information appliance, TV display, personal video
recorder or like body (108);
an encrypted channel from a content provider to the body (108);
a unit of hardware, software, data, content or the like functional unit (308,
604, 608, 612, 614, 616, 618, 620, 622, 624, 704, 708, 712, 714) within the
body;
requirement data (508, 720) related to the functional unit (308, 604, 608,
612, 614, 616, 618, 620, 622, 624, 704, 708, 712, 714); and
rights data (408, 716) related to the functional unit (308, 604, 608, 612,
614, 616, 618, 620, 622, 624, 704, 708, 712, 714), wherein the rights data
(408, 716) are
checked against the requirement data (508, 720) to authorize use of the
functional unit
(308, 604, 608, 612, 614, 616, 618, 620, 622, 624, 704, 708, 712, 714).
16. The content receiver for the conditional access system (100) of
claim 15, wherein the functional unit (308, 604, 608, 612, 614, 616, 618, 620,
622, 624,
704, 708, 712, 714) includes at least one of an object (308, 608, 612, 616,
618, 620, 622,
624, 708, 712) and a resource (308, 604, 608, 612, 614, 616, 618, 620, 622,
624, 704, .
708, 712, 714).
17. The content receiver for the conditional access system (100) of
claim 15, further comprising a second functional unit (308, 604, 608, 612,
614, 616, 618,
620, 622, 624, 704, 708, 712, 714), wherein the rights data (408, 716) of the
functional
unit (308, 604, 608, 612, 614, 616, 618, 620, 622, 624, 704, 708, 712, 714)
are inherited
by the second functional unit (308, 604, 608, 612, 614, 616, 618, 620, 622,
624, 704, 708,
712, 714).
18. The content receiver for the conditional access system (100) of
claim 15, wherein a source of the functional unit (308, 604, 608, 612, 614,
616, 618, 620,
622, 624, 704, 708, 712, 714) is authenticated.
19. The method for securing information in the conditional access
system (100) of claim 1, the method comprising:
providing a first functional unit (308, 604, 608, 612, 614, 616, 618, 620,
622, 624, 704, 708, 712, 714) associated with first requirement data (508,
720);
providing a second functional unit (308, 604, 608, 612, 614, 616, 618, 620,
622, 624, 704, 708, 712, 714) associated with first right data;
initiating interaction between the first and second functional units (308,
604, 608, 612, 614, 616, 618, 620, 622, 624, 704, 708, 712, 714);
checking the first right data against the first requirement data (508, 720) in
response to the initiation of interaction between the first and second
functional units (308,
604, 608, 612, 614, 616, 618, 620, 622, 624, 704, 708, 712, 714); and
authorizing use of the first functional unit (308, 604, 608, 612, 614, 616,
618, 620, 622, 624, 704, 708, 712, 714) by the second functional unit (308,
604, 608, 612,
614, 616, 618, 620, 622, 624, 704, 708, 712, 714).
20. The method for securing information in the conditional access
system (100) of claim 19, further comprising authenticating a source of at
least one of the
first functional unit (308, 604, 608, 612, 614, 616, 618, 620, 622, 624, 704,
708, 712,
714) and the second functional unit (308, 604, 608, 612, 614, 616, 618, 620,
622, 624,
704, 708, 712,714).
21. The method for securing information in the conditional access system
(100) of claim 19, further comprising entitling a transmission conduit for
transporting at least
one of the first functional unit (308, 604, 608, 612, 614, 616, 618, 620, 622,
624, 704, 708,
712, 714) and the second functional unit (308, 604, 608, 612, 614, 616, 618,
620, 622, 624,
704, 708, 712, 714).